D3 Glossary
LAST UPDATED: JAN 27, 2025
A
Ad-hoc Command
An integration command or utility command that can be executed outside of a playbook.
Ad-hoc Task
A manually created incident response task within an incident workspace, requiring a task name and assignee, with optional fields for task type, description, due date, and mandatory completion before closure.
Artifact
A piece of evidence or data extracted from external systems that can be linked to D3 events and incidents to support analysis and automation.
Automation Rule
A user-defined set of criteria and actions used to automatically evaluate, categorize, escalate, dismiss, ignore, or link events and incidents within D3.
B
C
Codeless Playbook
A method for implementing utility and integration commands in the form of a playbook.
Command
A directive that can execute actions in automation workflows or as standalone tasks.
Command Task
A type of playbook node that executes a specific integration or utility command.
Configuration
The set of properties, parameters, rules, or keys governing how one or more components operate within the platform.
Connection
A link that enables communication and interaction between D3 and an integration.
Correlation (Event-Incident)
The process of evaluating ingested activity data against escalation criteria to determine its significance and later, if the criteria are met, linking an event to an incident.
Custom View
A tailored view of data within the Investigation Dashboard, presenting a table with uniquely selected attribute columns, groupings and sorting criteria to organize information and enable quick navigation to the desired details.
D
D3 Forms
A web-based tool for incident reporting and escalation of suspicious activities.
Data Formatter Task
A type of playbook task for creating, selecting, and manipulating data.
Dynamic Form
See Incident Form.
E
Enrichment
The process of augmenting raw data with additional context to enhance its value and relevance for analysis.
Escalation
The initial association of an event with an incident after it is identified as a potential security threat requiring further investigation and response.
Event
A subject of correlation—generated after preprocessing playbook execution, searchable within the investigation dashboard—that represents detected system activities (data access, changes, transfers, etc.) that may violate security policies and impact organizational objectives and reputation.
Event Field Mapping
The process of mapping data fields within fetched JSON data to user-defined and D3 data model fields, through the use of the Fetch Event command.
Event Log
A tab in the Event Details pop-up that displays the event's raw data.
Event Overview
A tab in the Event Details pop-up that summarizes the event and allows users to add tactics, techniques, and notes.
Event Source
A modular, customizable set of field mappings defined by the origin and structure of data, automatically applied for data normalization according to search conditions.
F
Fetch Event
A command that retrieves data from an integration and encapsulates it into a D3 event.
Fetch Incident
A command that retrieves data from an integration and encapsulates it into a D3 incident.
Field Mapping
The process—during ingestion—of converting JSON keys of the fetched (raw) data into user-customized fields and D3 data model fields.
Format Builder
A tool for dynamically retrieving values along a playbook task's execution path, from the Local Shared Data, or the Global List.
G
Global List
A centralized repository for storing reusable JSON data sets to support dynamic operations.
Group
A collection of users with an assigned security level (1–10) that enforces access control across various modules.
H
I
Incident
A unit of investigation—created either manually through D3 Forms or the ![]() button on the vSOC navigation bar, or automatically via a preprocessing playbook—containing information necessary to facilitate response and remediation.
button on the vSOC navigation bar, or automatically via a preprocessing playbook—containing information necessary to facilitate response and remediation.
Incidents are used to run investigation playbooks.
Incident Field Mapping
The process of mapping data fields within fetched JSON data to user-defined and D3 data model fields, through the use of the Fetch Incident command.
Incident Form
A built-in or user-created template used to collect a specific set of incident information. The template's name generates an incident type, and incidents assigned that type will inherit the template's defined fields.
Incident Type
A classification that defines the context of an incident. Incident types are generated from incident forms.
Incident Workspace
A centralized space for investigating and managing an incident, customized via the incident workspace builder.
Ingestion
The processes of transferring external activity data into the D3 SOAR platform—supported by scheduled pull requests and webhook pushes—and performing field mapping.
Integration
A third-party application whose functionalities are accessible within D3 SOAR.
See D3’s integration documents.
Integration Command
A command—tied to a specific integration—that facilitates interaction with external systems (SIEMs, firewalls, and ticketing platforms, etc.).
Investigation Dashboard
A space for viewing dashboards, events, incidents, pending tasks, artifacts, playbook errors, and IOA/IOC link analysis.
Investigation Playbook (previously Incident Playbook)
A playbook used for automating the analysis and response of incidents, tailored to specific use cases such as phishing email handling, malware investigation, and endpoint protection.
J
Jinja
A Python-syntax-inspired templating language used within D3 playbooks to dynamically retrieve, manipulate, and present data.
JSON Path
A syntax used to traverse and query elements within a JavaScript Object Notation (JSON) document. It defines the path to a particular value within a nested JSON structure, allowing users to extract or reference specific data based on its hierarchy.
K
L
Linking (Event / Incident)
See Correlation.
Local Shared Data
JSON data specific to a single playbook, shared among all tasks within that playbook. Locally shared data can be viewed via the ![]() icon within the secondary playbook action bar.
icon within the secondary playbook action bar.
Login Authentication
The process by which D3 verifies the identity of a user attempting to log in.
See the Login Authentication Configuration Guide.
M
Merge Task
A type of playbook task that helps consolidate data from selected playbook execution paths into a single array, aiding data management and processing.
Also see Unwind Task.
MITRE
An American not-for-profit organization that addresses challenges in defense, cybersecurity, and other sectors. The MITRE Corporation is responsible for the development of the MITRE ATT&CK framework.
MITRE ATT&CK
A universally accessible and continuously updated knowledge base of adversary tactics and techniques designed to support threat detection, response, and the development of threat models and methodologies.
D3’s MITRE ATT&CK Monitor is a security workspace built around the MITRE ATT&CK framework, offering organizations a global view of their security posture.
Multi-tenancy
A feature consisting of independent sites, each with isolated data, workflows, and configurations, designed to help organizations manage multiple client and business units.
N
O
Organization Management
A module that enables administrators to configure users, groups, roles, and sites to manage access control within D3.
Owner (Incident)
A user who is assigned to investigate an incident.
P
Passdown Task
A type of playbook task that processes or prepares return data from the playbook for use in other destinations.
Pending Task
Any playbook task that is in a 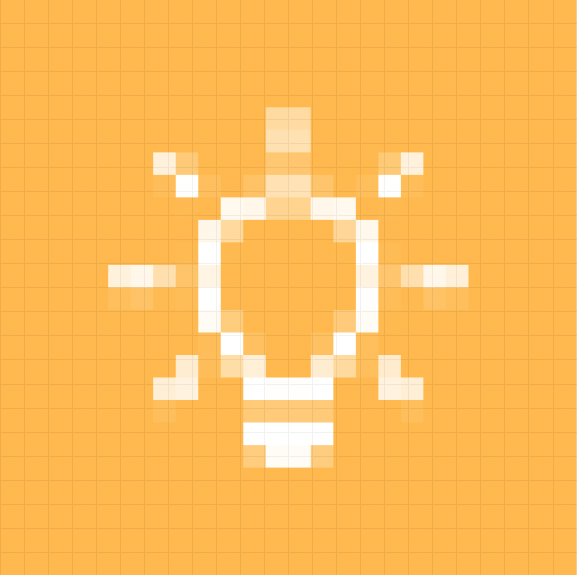 (pending) state, thereby preventing the execution from advancing to subsequent playbook tasks.
(pending) state, thereby preventing the execution from advancing to subsequent playbook tasks.
Pending tasks can arise from an unticked Auto Run checkbox, interaction tasks awaiting user input, incomplete internal tasks within a Codeless Playbook command, or commands depending on an upgrading agent.
Playbook
A predefined, automation workflow consisting of task nodes working together to perform security operations.
Playbook Data
The information accessible to a specific playbook task, restricted to data from the data source and other tasks along the execution path leading to that task.
Playbook Errors
Issues encountered during the execution of a playbook.
Preprocessing Playbook (previously Event Playbook)
A playbook used to automate preparatory operations on raw activity data—primarily enrichment, false positive filtering, and correlation—useful before deeper analysis begins.
Preprocessing Playbook Viewer
A space for checking data ingestion jobs, viewing the status of event-triggered playbooks, and reviewing playbook task details.
Proxy Agent
An application that runs on a D3 customer’s server, acting as a liaison between the server and the D3 SOAR platform to ensure security and stability for data ingestion.
See Agent Management.
Q
R
Raw Data
The unprocessed and unformatted information ingested from integrations.
RBAC
A security model that allows the enforcement of access policies by defining roles and assigning them to users.
Reporting Dashboard
A module used to consolidate key metrics and visualizations to empower users across different levels of organizational hierarchy to extract security insights, track performance metrics, discern trends, predict future outcomes, and make informed decisions.
ROI
A performance metric used to evaluate the value gained from implementing automation and orchestration within their security operations.
Also see SLA and ROI Widgets.
Role
A set of permissions that restricts user actions and resource access to those required for their responsibilities.
Runtime
The time interval during which a task or playbook is actively executing.
S
Schedule
A configuration that automates the periodic execution of integration and utility commands.
Also see Schedules.
Severity
The level of impact or criticality assigned to an incident, used to prioritize response efforts. In D3, severity is categorized into five tiers: Critical, High, Medium, Low, and Informational.
Site
An organizational unit, such as a department, subsidiary, or client, operating independently with isolated data, workflows, and configurations. Sites ensure data privacy and facilitates distributed multi-tenancy.
See Multi-Tenancy.
Status (Incident)
The current state of an incident within its lifecycle (Open, Closed, In Progress, or On Hold).
T
Tactic
The objective or intent driving an adversary's actions during a cyberattack.
Task
The building blocks of a playbook, linked via a control flow, performing specific actions or functions. Tasks often process input data, return output data, or execute other operations as defined by the playbook logic.
Task Status
The current state of a playbook task during testing or live execution.
See the Task Statuses.
Technique
An action or method used by adversaries to achieve their objectives during a cyberattack.
Tenant
A distinct entity within a multi-tenant system, such as an organization or business unit with its own isolated data, configurations, and workflows.
Also see Multi-Tenancy.
Tolerance Scope
A time window (in minutes) that extends the time range for fetching events by subtracting from the specified start time. Tolerance scope helps prevent data loss by accounting for vendor API response delays arising from temporary server-side data unavailability during processing and synchronization.
With the tolerance scope applied, events will be fetched within the range of (start time - tolerance Scope) to end time. By default, the tolerance scope is set to 0.
Triage
The process of prioritizing events or incidents to determine an appropriate and timely response.
Trigger
A condition that initiates a playbook workflow.
Trigger Output Data
The JSON data—generated behind the scenes during field mapping, refined in the On Event Ingestion preprocessing workflow, and accessed via the ![]() icon in the secondary playbook action bar—that contains all information required to create and escalate or dismiss a D3 event.
icon in the secondary playbook action bar—that contains all information required to create and escalate or dismiss a D3 event.
U
Unwind Task
A type of playbook task that breaks down a given array into its individual elements. Each element then triggers a run of the downstream tasks, leading to the formation of multiple execution paths and the individual processing of each element.
The Unwind task is often used in conjunction with the Merge Task.
User
An individual with access to a system identified by their unique credentials, roles, and groups.
See Creating Users.
Utility Command
A command—not depending on external integrations or connections—capable of performing operations at varying levels of abstraction and scope.
V
W
Web Config
A configuration interface that allows users to modify system-wide settings to tailor the application’s functionality and behavior.
Webhook
A mechanism for real-time communication between applications using HTTP requests. In D3, it refers to pushing data into D3 using the POST method.
Widgets
Visual components within the incident workspace and Reporting Dashboard that display data and can be repositioned or removed.