Investigation Playbook Triggers
LAST UPDATED: JAN 10, 2025
On Playbook Start
-20250110-200013.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
Executes tasks either during the playbook’s test run or after the playbook is added to an incident— via utility commands, the Escalate playbook task, the playbook automation widget, or the .png?inst-v=05328674-b079-4c01-ba41-8dd92707b455) button.
button.
Commands used to for event-incident correlation:
SCENARIO A manager has requested to be notified whenever an incident is created. To fulfill this request, the analyst will perform the following tasks.
Task 1: Add the Send Email Utility Command
The analyst will begin by adding the Send Email utility command task to the On Playbook Start trigger in an investigation playbook.
Add the Send Email utility command to the trigger.
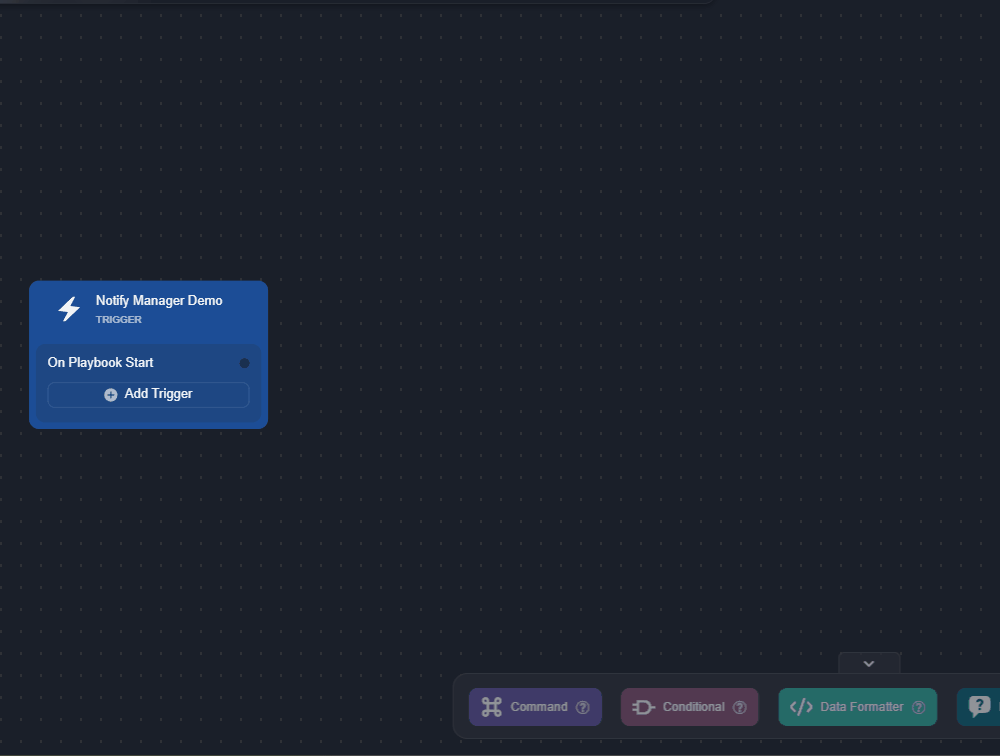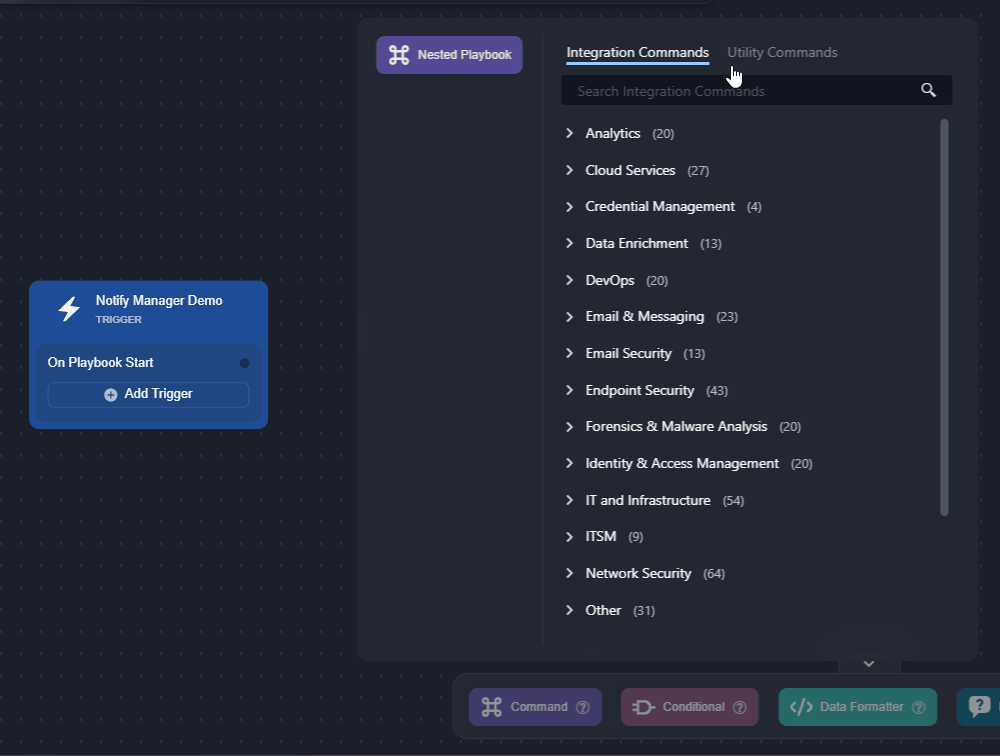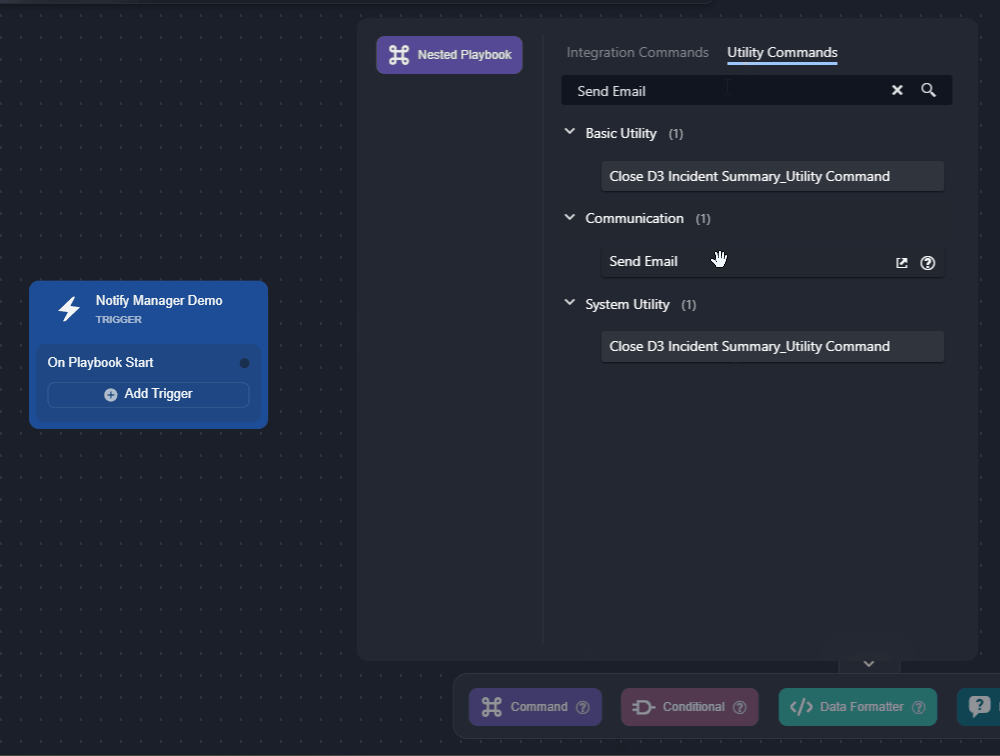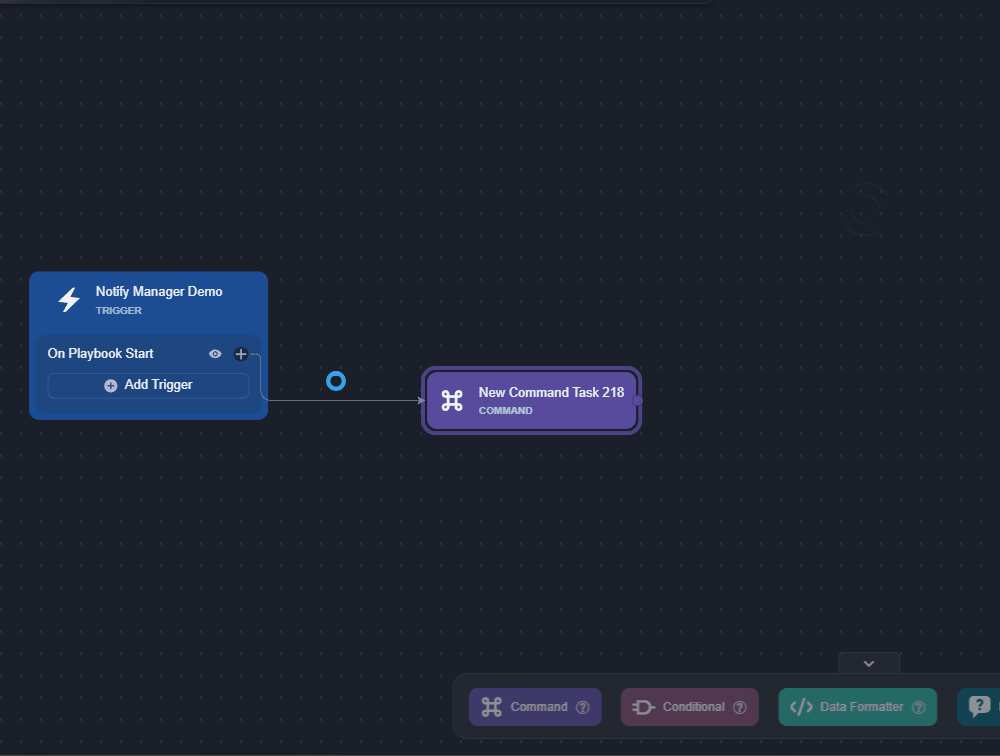
Configure the fields as necessary.
.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
Enter the task name.
Input the manager’s email address.
Enter the email subject.
Enter the email body containing a static message combined with the dynamically retrieved incident number.
CODE{{ "A new incident has been created: " ~ (PlaybookData | jsonpath('$.DataSource.incident.IncidentNo')) }}
Check the Auto Run checkbox, then click on the
 button to save.
button to save.
Click on the Submit button, then confirm the playbook submission.
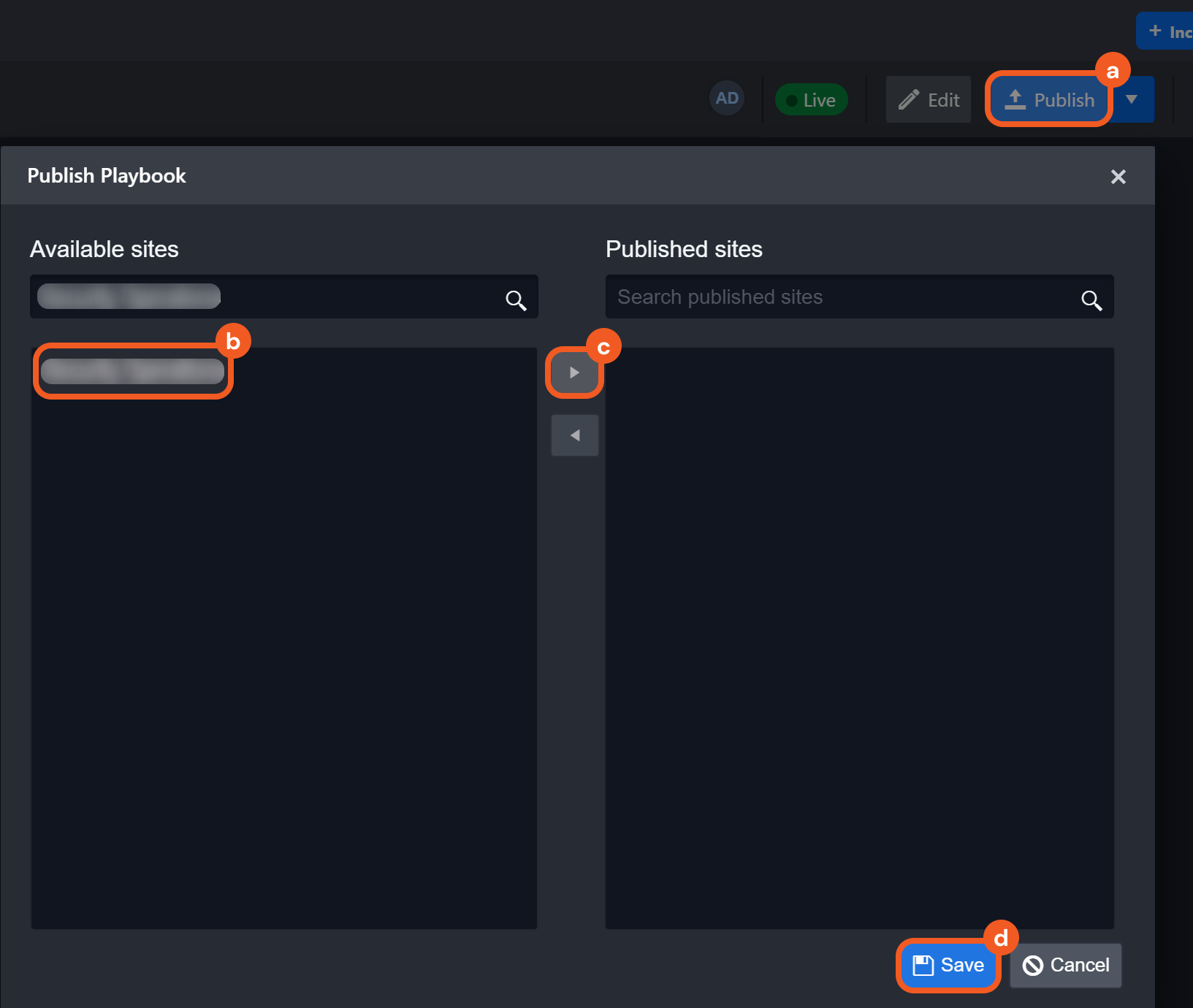
Click on the Publish button, select a site to which to publish the playbook, then click on the Save button.
Task 2: Use the Investigation Playbook in a Preprocessing Playbook
After publishing the investigation playbook, the analyst will use it in an escalate task within a preprocessing playbook. They have already completed most of the preprocessing playbook workflow, with only the escalate task remaining to be configured.
Click into the escalate task.
Configure the fields as necessary.
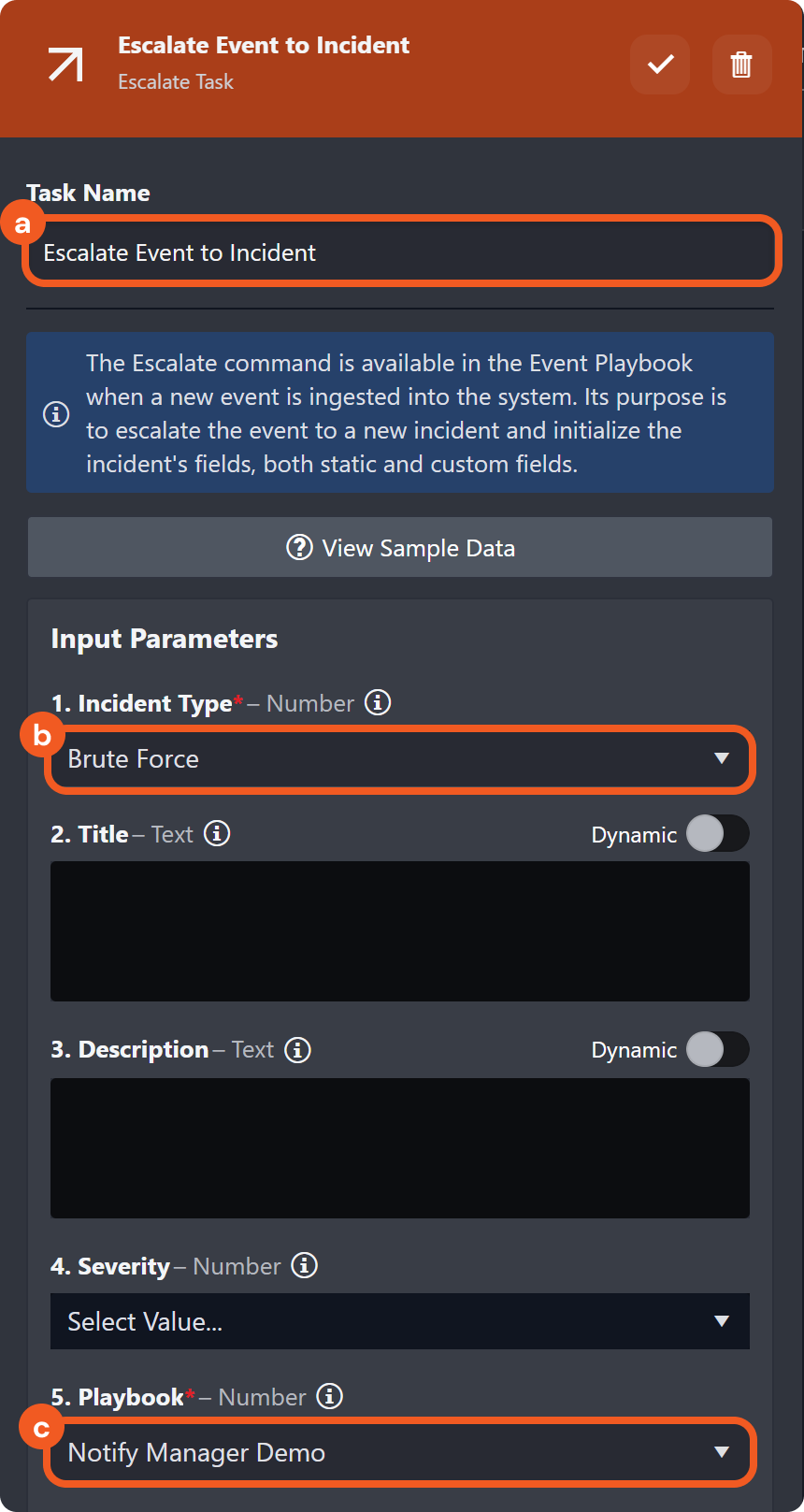
Enter the task name.
Select an incident type.
Select the previously created investigation playbook.
Check the Auto Run checkbox, then click on the
 button to save.
button to save.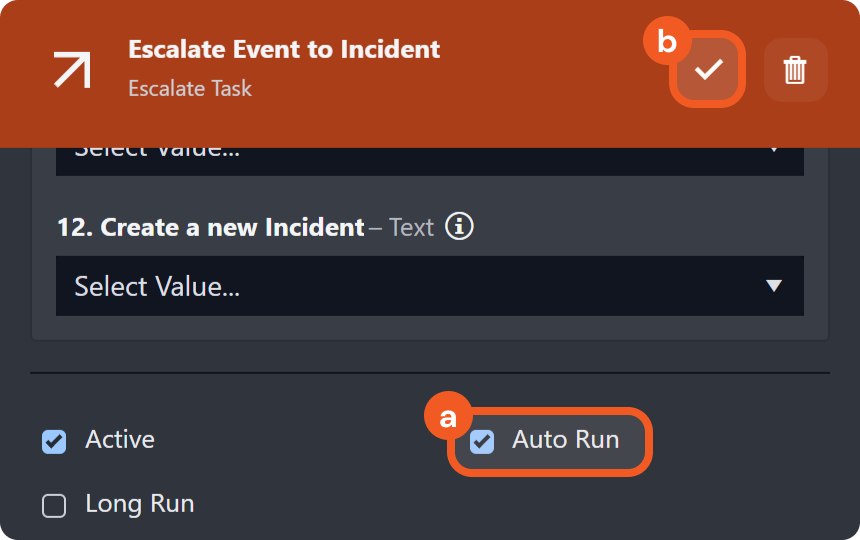
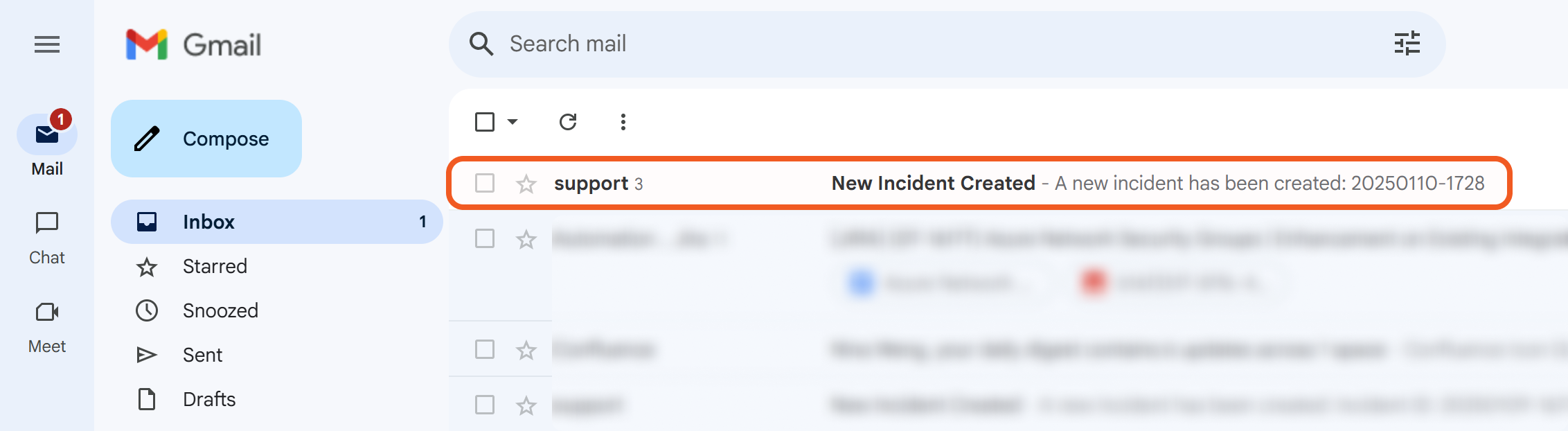
RESULT
Whenever a new incident is created through the preprocessing playbook, the investigation playbook configured in task 1 will execute automatically.
On Incident Close
Executes tasks after:
Manually closing an incident
Manually performing batch closures of incidents
Closing incidents using utility commands, either manually or automatically
Commands for closing one incident:
Commands for closing multiple incidents:
-20250110-200216.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
On Playbook Task Error
-20250110-195027.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
Executes tasks when a current-level task or nested playbook command encounters an error.
Create a Codeless Playbook utility command.
-20250110-002910.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
Setup a task that would result in an error.
-20250110-004014.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
Enable its use as a command task.
-20250110-011541.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
Use a
-20250110-020837.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455) passdown task to emit an error message to the parent playbook.
passdown task to emit an error message to the parent playbook. -20250110-020555.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
Submit this utility command.
-20250110-004926.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
Create an incident (investigation) playbook.
-20250110-011805.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
Set up the Demo Nested Playbook Utility Command task.
-20250110-021551.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
READER NOTE
Ensure that the Error Trigger checkbox is ticked.
-20250110-192902.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
Set up a Send Email utility command task for the On Playbook Task Error trigger.
-20250110-022452.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
Test run this playbook, ensuring that the Demo Nested Playbook Utility Command task results in
%202-20250110-022826.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455) , and the Send Email task results in
, and the Send Email task results in %203-20250110-022810.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455) .
.%201-20250110-022606.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
Check the email for the error message.
-20250110-023018.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
Common use cases include notifying relevant stakeholders of task failures and automatically retrying the task.
On Incident Reopen
Executes tasks whenever a previously closed incident (i.e. Status: Closed) is manually or automatically reopened (i.e. Status: Open).
Commands for updating the incident status to Open:
-20250110-195200.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
On Incident Change
-20250110-195310.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
Executes tasks whenever changes are made to the content within the Overview section of the incident workspace.
Changing the site
Changing the title
Changing the severity
Changing the owner
Changing the date occurred
Changing the disposition
Changing the incident type
Changing the date ended
Adding a custom field
Modifying a custom field’s value
Deleting a custom field
Adding a description
Modifying a description
Deleting a description
Adding a conclusion
Modifying a conclusion
Deleting a conclusion
Adding a Tactic & Technique / Adversary Lifecycle
Deleting a Tactic & Technique / Adversary Lifecycle
Adding a playbook
Deleting a playbook
Adding investigation team members
Deleting investigation team members
Adding files
Deleting files
Adding notes
Modifying notes
Deleting notes
Inputting dynamic field values
Modifying/Clearing and saving dynamic field values
Adding a JSON table
Modifying a JSON table
Deleting a JSON table
Adding tags
Deleting tags
On Incident Status Change
Executes tasks whenever an incident's status transitions between the following states:
Open
In Progress
On Hold
Commands for changing the incident status:
Common use cases:
Automatically assign tasks based on the new status
Notify relevant stakeholders of the status change
-20250110-195440.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
On Incident External Action
-20250110-195610.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
Executes tasks when the Trigger Incident External Action utility command identifies an incident that matches a specific search criteria—facilitating cross-incident automation and coordination.
The On Incident External Action workflows of all playbooks associated with the first matching incident will be executed.
Create a Demo Trigger investigation playbook with an auto-running task connected to the On Incident External Action trigger.
-20250110-201041.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
Submit the playbook.
-20250110-201630.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
Publish the playbook.
-20250110-202652.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
Create three incident having the following characteristics:
Title: Demo Incident 1, 2, or 3
Type: Suspicious Network Activity
Severity: Medium
-20250110-203418.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
%201-20250110-215432.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
Ensure the Demo Trigger investigation playbook is attached to each incident.
-20250110-214923.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
Navigate to the Trigger Incident External Action utility command.
-20250110-204745.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
Test the utility command with the following for the Search Condition input parameter:
JSON{ "Type": "Suspicious Network Activity", "Severity": "Medium", "Title": { "$regex": "Demo Incident" } }-20250110-220153.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
Verify that the Demo Trigger playbook has completed execution only within the first incident (Demo Incident 1).
-20250110-221928.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
-20250110-221219.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
On Investigation Change
Executes tasks whenever summary, findings, remediations & mitigations, and recommendations data within the Investigation tab of the incident workspace changes.
Common use cases:
Notifying the team of new evidence
Re-evaluating the incident based on updated investigation details
-20250110-195743.png?inst-v=05328674-b079-4c01-ba41-8dd92707b455)
