Microsoft Sentinel
LAST UPDATED: AUG 1, 2025
Overview
Microsoft Azure Sentinel is a scalable, cloud-native, security information event management (SIEM) and security orchestration automated response (SOAR) solution. Azure Sentinel delivers intelligent security analytics and threat intelligence across the enterprise, providing a single solution for alert detection, threat visibility, proactive hunting, and threat response.
D3 SOAR is providing REST operations to function with Microsoft Sentinel.
For example, you can use Microsoft Azure Sentinel to help reduce noise and hunt for security threats based on the MITRE framework. It combines AI capabilities with real-time data to ensure that alerts are significant/accurate and include critical contexts such as user profile, access rights, and environment-related information.
Microsoft Sentinel is available for use in:
Known Limitations
The following limits apply to incident commands in Microsoft Sentinel.
Number of characters per comment - 30K characters
Number of comments per incident - 100 comments
Minimum limits are supported per 5 minutes, and per subscription and endpoint.
Operation | Limit |
GET automation rules | 100 |
PUT comments | 75 |
GET comments | 100 |
GET incident alerts | 100 |
GET incident entities | 100 |
GET relations | 100 |
Please refer to Service limits for Microsoft Sentinel, Azure Monitor service limits and Throttling Microsoft Sentinel requests for detailed information.
Connection
To connect to Microsoft Sentinel from D3 SOAR, please follow this part to collect the required information below:
Parameter | Description | Example |
Directory (tenant) ID | The directory ID to authenticate the API connection. | nn0-***-***-***-*** |
Client ID | The client ID to authenticate the API connection. | hoA-***-***-***-*** |
Client Secret | The client secret to authenticate the API connection. | bYF-***-***-***-*** |
Subscription ID | The Azure subscription ID of the workspace to connect to. | kkQ-***-***-***-*** |
Resource Group Name | The name resource group name within the user's subscription. | YOUR_RESOURCE_GROUP_NAME |
Workspace Name | The name of the workspace to connect to. | YOUR_WORKSPACE_NAME |
API Version | The API version to use for the connection. Using the latest stable API version to run the commands is recommended. Please refer to Microsoft Sentinel's REST API documentation for the list of stable versions. | 2023-02-01 |
READER NOTE
The scenario outlined in this user guide assumes that you already have the following prerequisites:
An admin or higher user role from Microsoft Entra ID Protection tenant.
Microsoft Sentinel Account.
A Log Analytics workspace is required to house all of the data that Microsoft Sentinel will be ingesting and using for its detections, analytics, and other features.
Permission Requirements
Each endpoint in the Microsoft Sentinel API requires a certain permission scope. The following are required scopes for the commands in this integration:
Command | Required Permission |
Delete Incident Comments | Contributor |
Fetch Event | Microsoft Sentinel Reader |
Fetch Incident | Microsoft Sentinel Reader |
Get Alert Details By Incident ID | Microsoft Sentinel Reader |
List Alert Rules | Microsoft Sentinel Reader |
List Alert Rule Templates | Microsoft Sentinel Reader |
Search | Microsoft Sentinel Reader |
Update Incident Comments | Contributor |
Update Incident Status | Contributor |
Test Connection | Microsoft Sentinel Reader |
As Microsoft Sentinel is using role-based access control (RBAC), the API access token is generated based on a specific user account and the application. Therefore, the command permissions are inherited from the user account's role. Users need to configure their user profile from the Microsoft Sentinel console for each command in this integration.
READER NOTE
Microsoft Sentinel's specific user profiles are as follows:
Microsoft Sentinel Reader
Microsoft Sentinel Responder
Microsoft Sentinel Contributor
Microsoft Sentinel Playbook Operator
Microsoft Sentinel Automation Contributor
Please refer to Roles and permissions in Microsoft Sentinel for details on configuring user profiles.
Configuring Microsoft Sentinel to Work with D3 SOAR
Log in to the Azure Portal (https://portal.azure.com/) with your credentials.
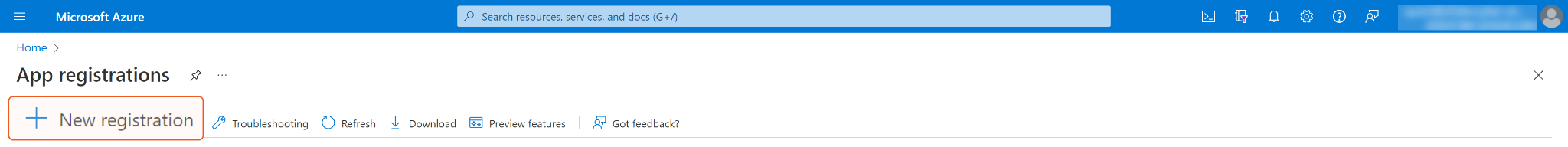
Navigate to the search bar at the top and search for "App registrations". Select App Registrations.

If you have already created Apps, you can use one of them and skip to step 6 to obtain the Client ID & Tenant ID.
If you do not have a created App, click + New registration to create one.
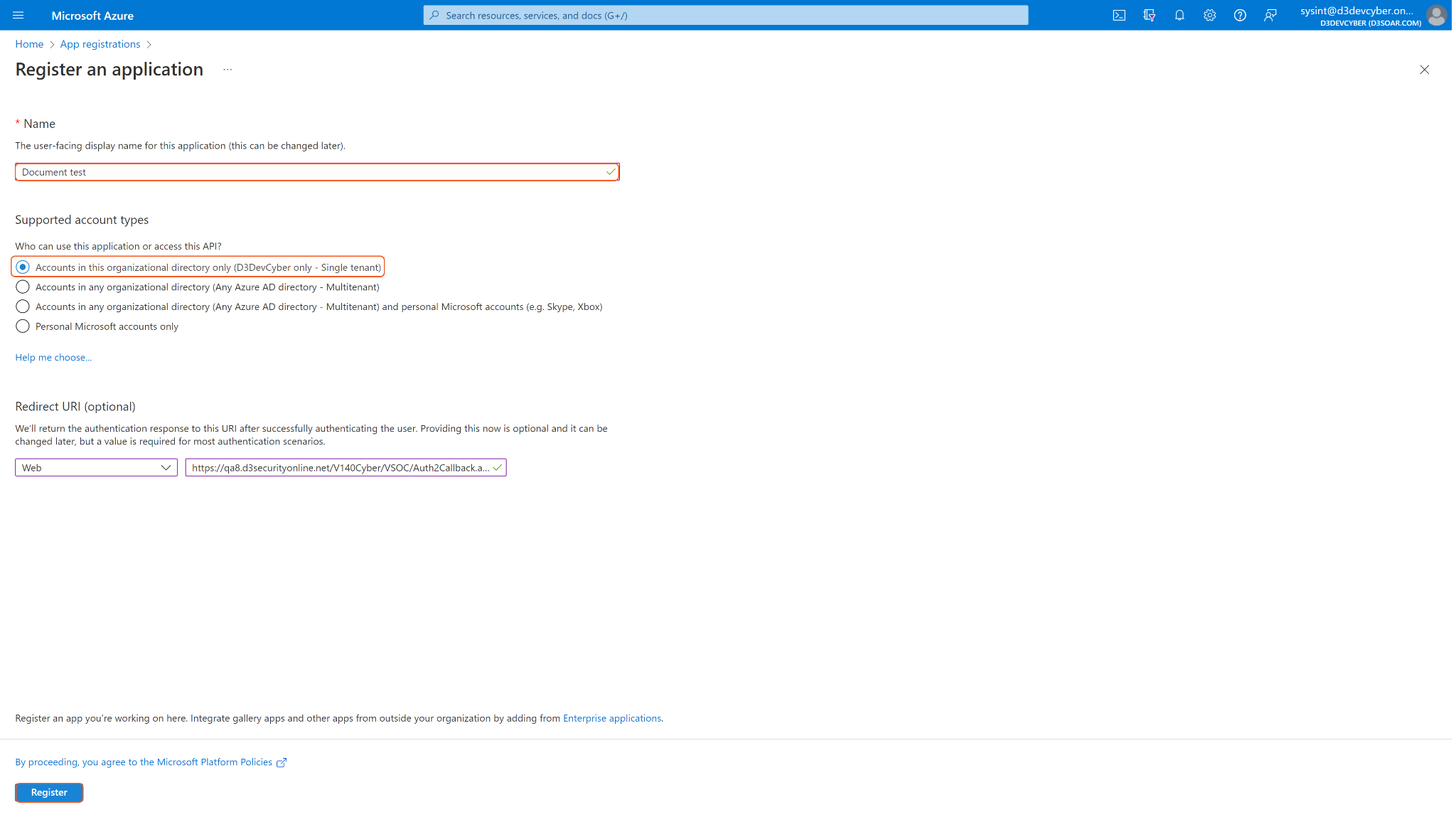
Provide a name for the App. If your target audience is internal within your organization, select the first option under Supported account type.
READER NOTE
Single tenant apps: These apps are only accessible within the tenant in which they were registered, also known as their home tenant.
Multitenant apps: These apps are available to users in both their home tenant and other tenants.
For more information on tenancy in Microsoft Entra ID Protection, see Tenancy in Microsoft Entra ID Protection.
It is recommended to use a single tenant app for your D3 SOAR connection.
In the App Overview tab, copy and save the Application (client) ID and Directory (tenant) ID for creating the SOAR connection.
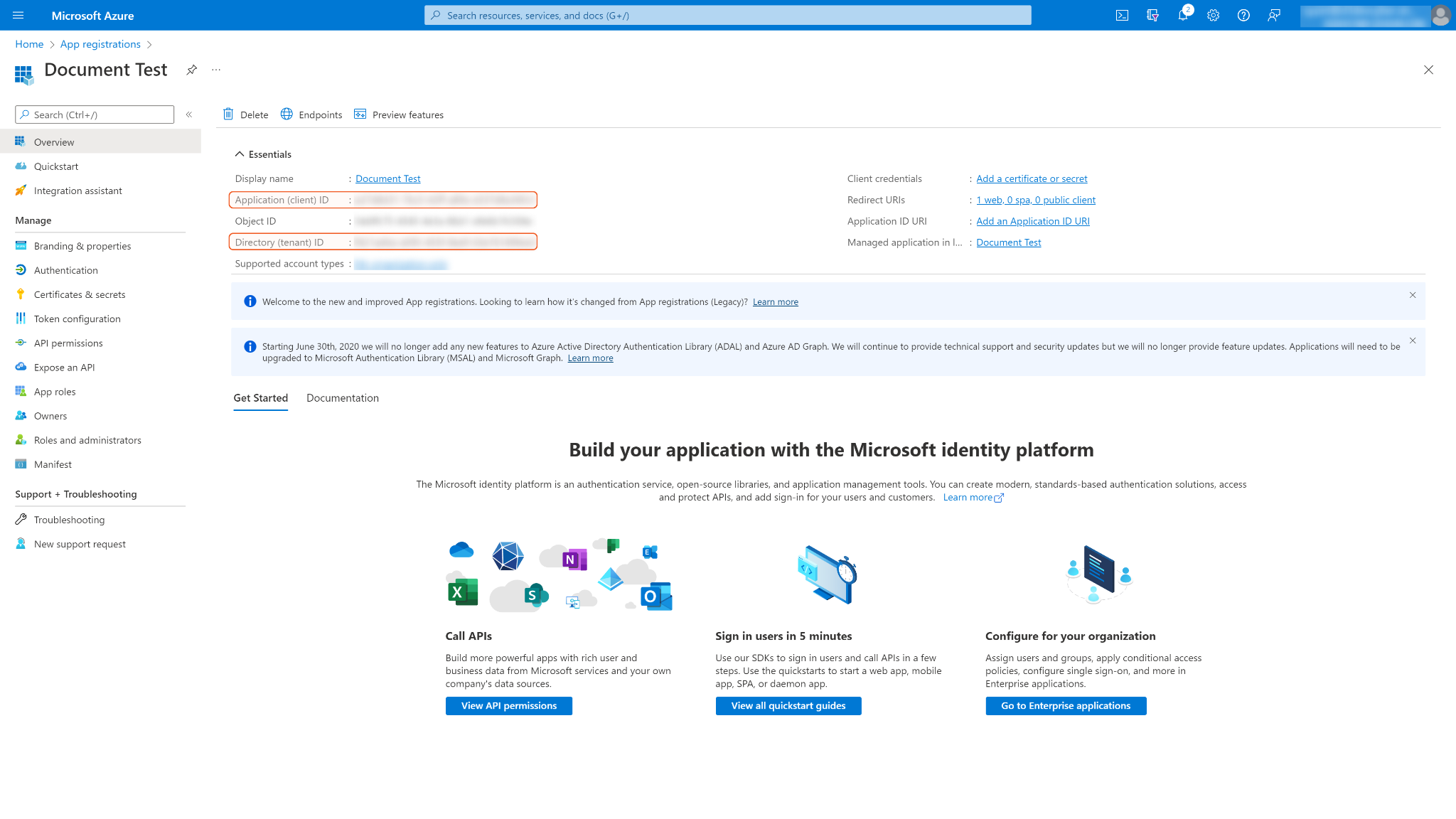
Navigate to Certificates & secrets in the left navigation column, and click + New client secret. Enter a description for the client secret and select an expiry period from the Expires dropdown menu. Keep in mind that the client ID will not be able to access API resources if the secret is expired. You must renew the secret after the expiry period to maintain the client ID's effectiveness. Finally, click Add at the bottom of the page.
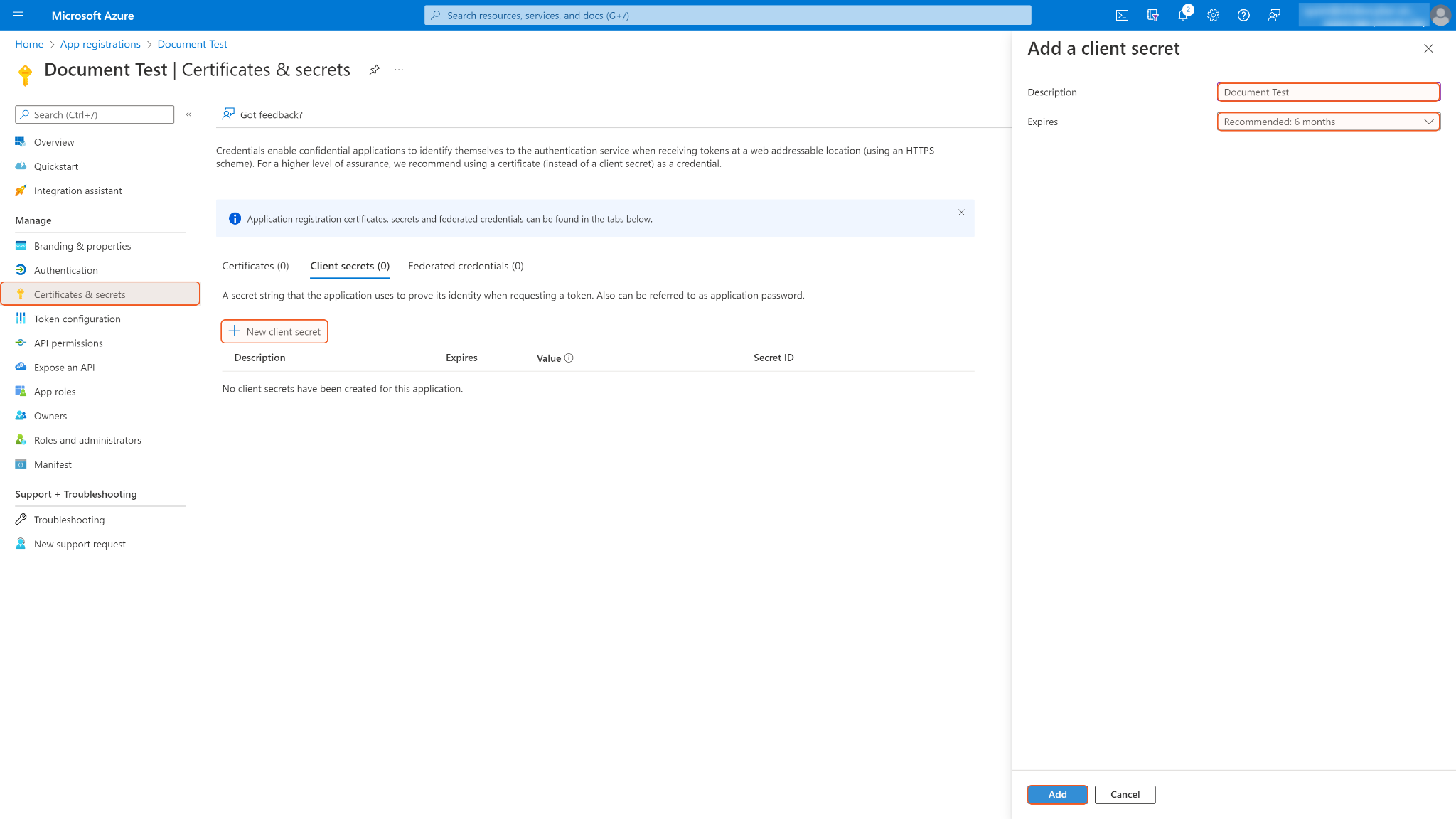
Copy and save the secret value for building the integration connection. Note: The secret value is only viewable once upon its creation, please store it in a secure location.
Return to the home page. Search and select Microsoft Sentinel.
Select the Microsoft Sentinel workspace you want to integrate with.
On the selected workspace's settings page, navigate to Settings > Workspace settings.
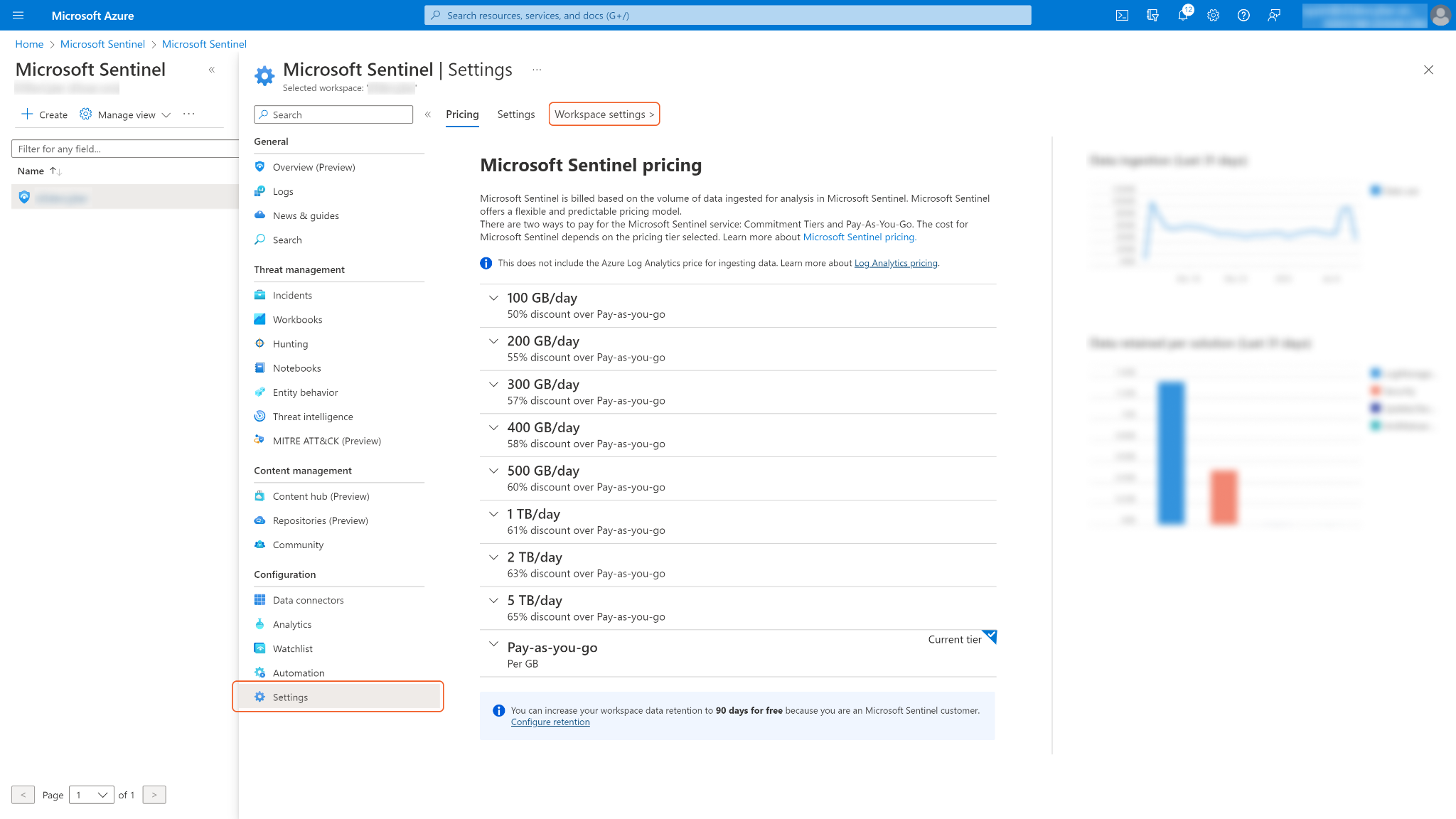
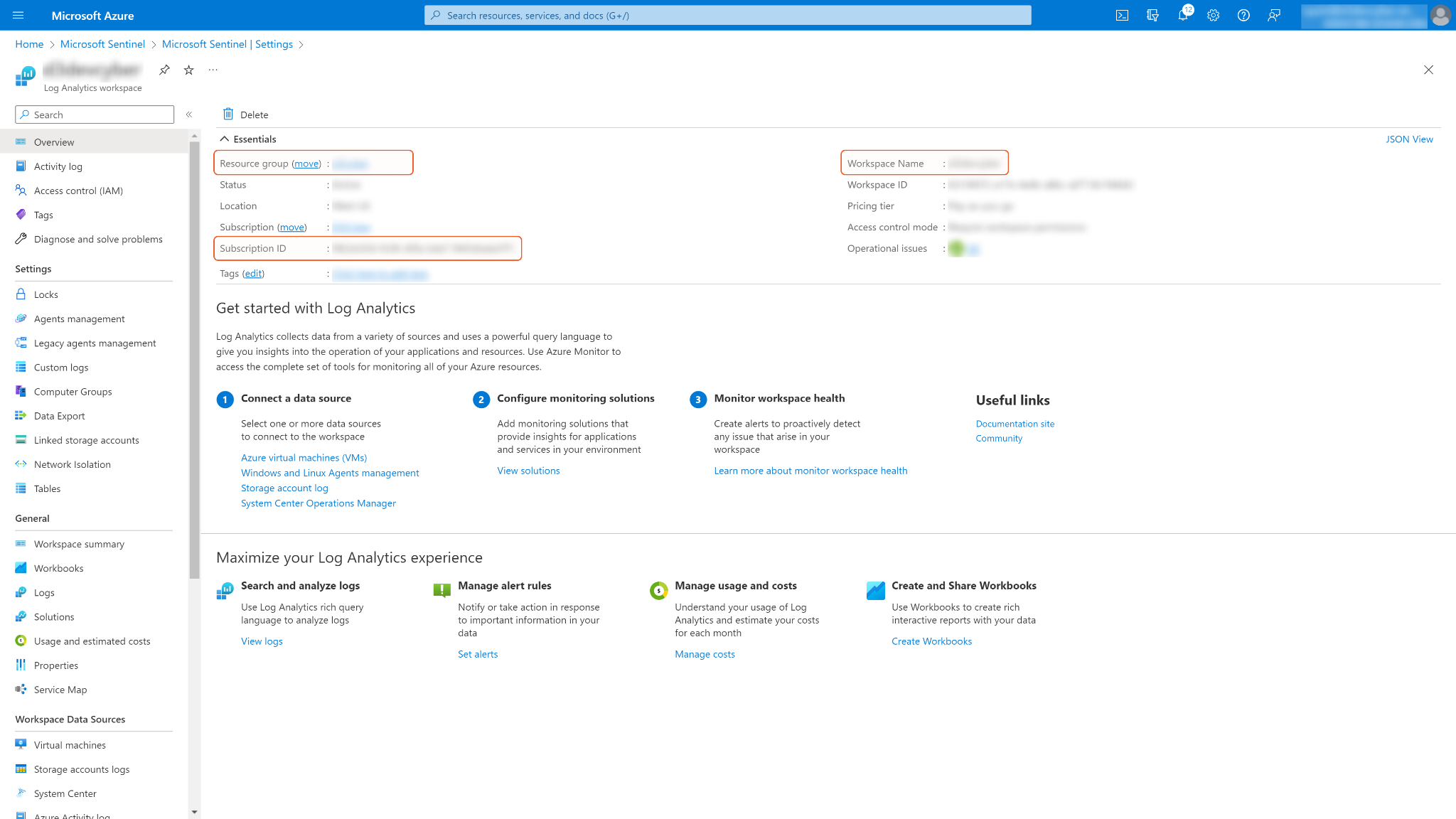
Save the values for Resource group, Subscription ID and Workspace name. They are required for building the integration connection in D3 SOAR.
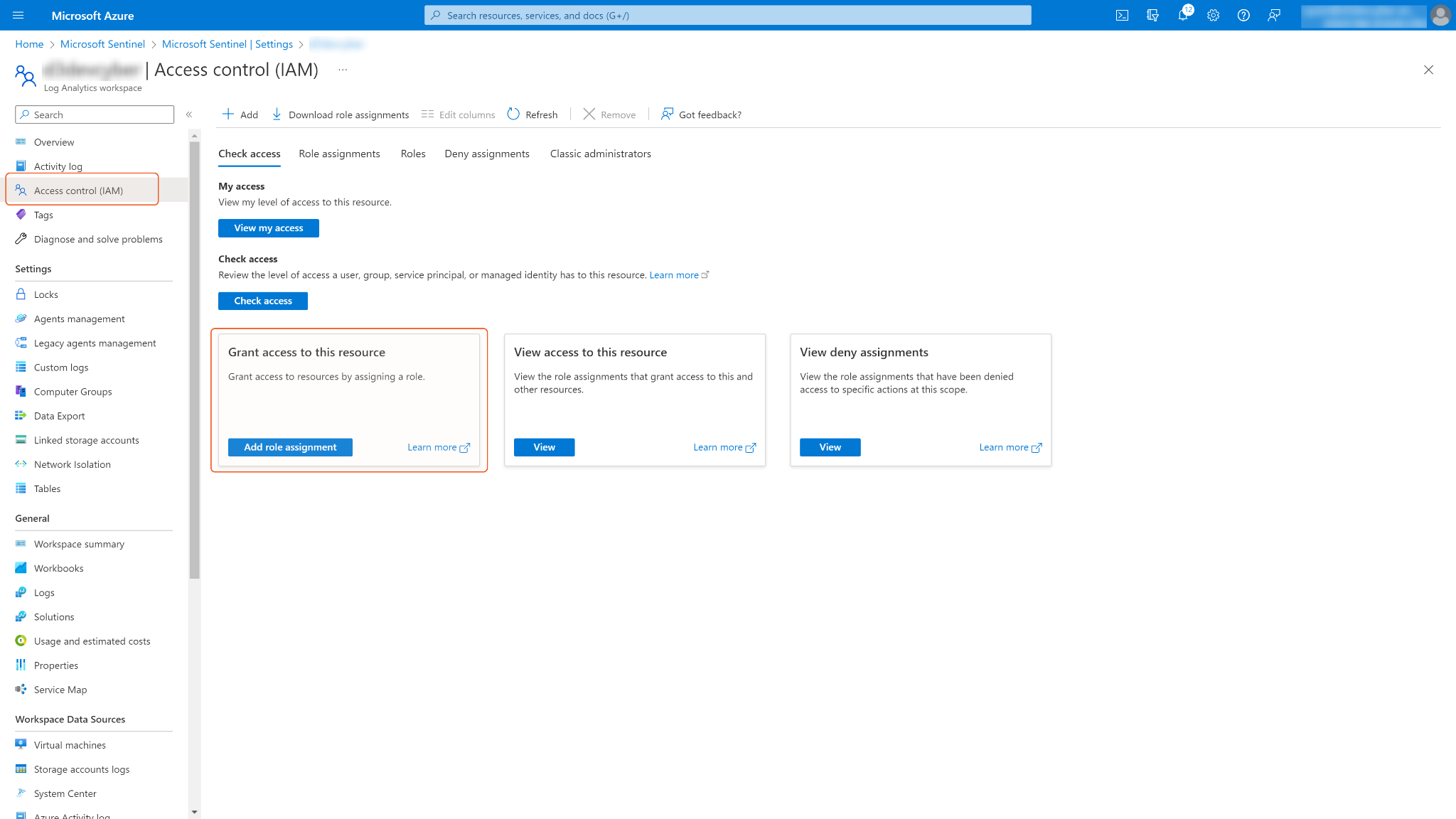
From the left navigation pane, navigate to Access control (IAM) > Add role assignment to grant access privileges.
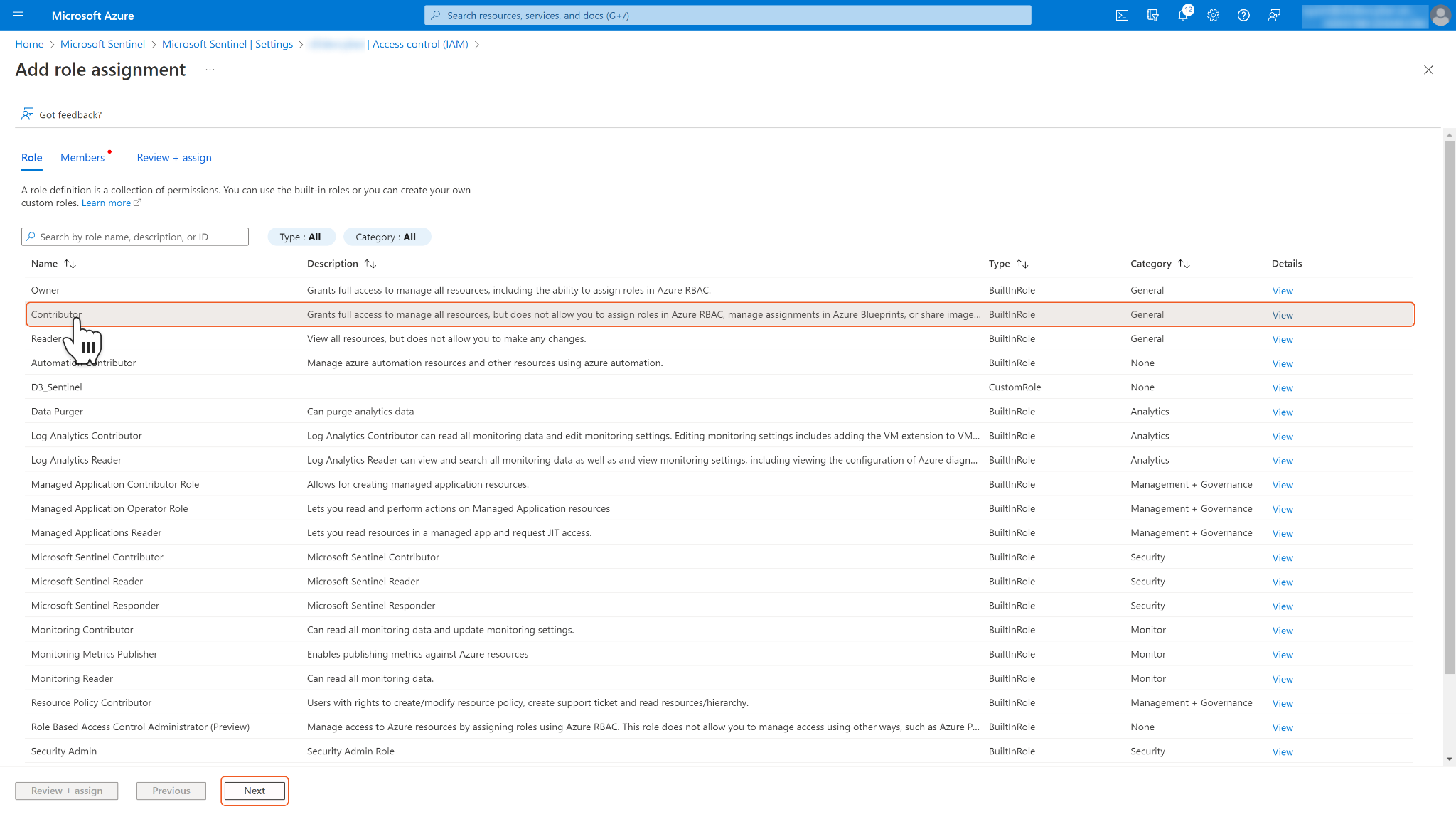
Select your desired roles and click Next. The Contributor privilege is sufficient to execute all Microsoft Sentinel's integration commands in D3 SOAR.
READER NOTE
Unlike Microsoft Graph permissions, Microsoft Sentinel uses Azure role-based access control (Azure RBAC) to assign built-in roles to users, groups, and services in Azure. For more information, refer to the Permissions in Microsoft Sentinel. It is recommended to allow the Contributor role for your D3 SOAR connection.
Under Assign access to, select User, group, or service principal. Click + Select members, and choose the App created in step 5. Finally, click Select.
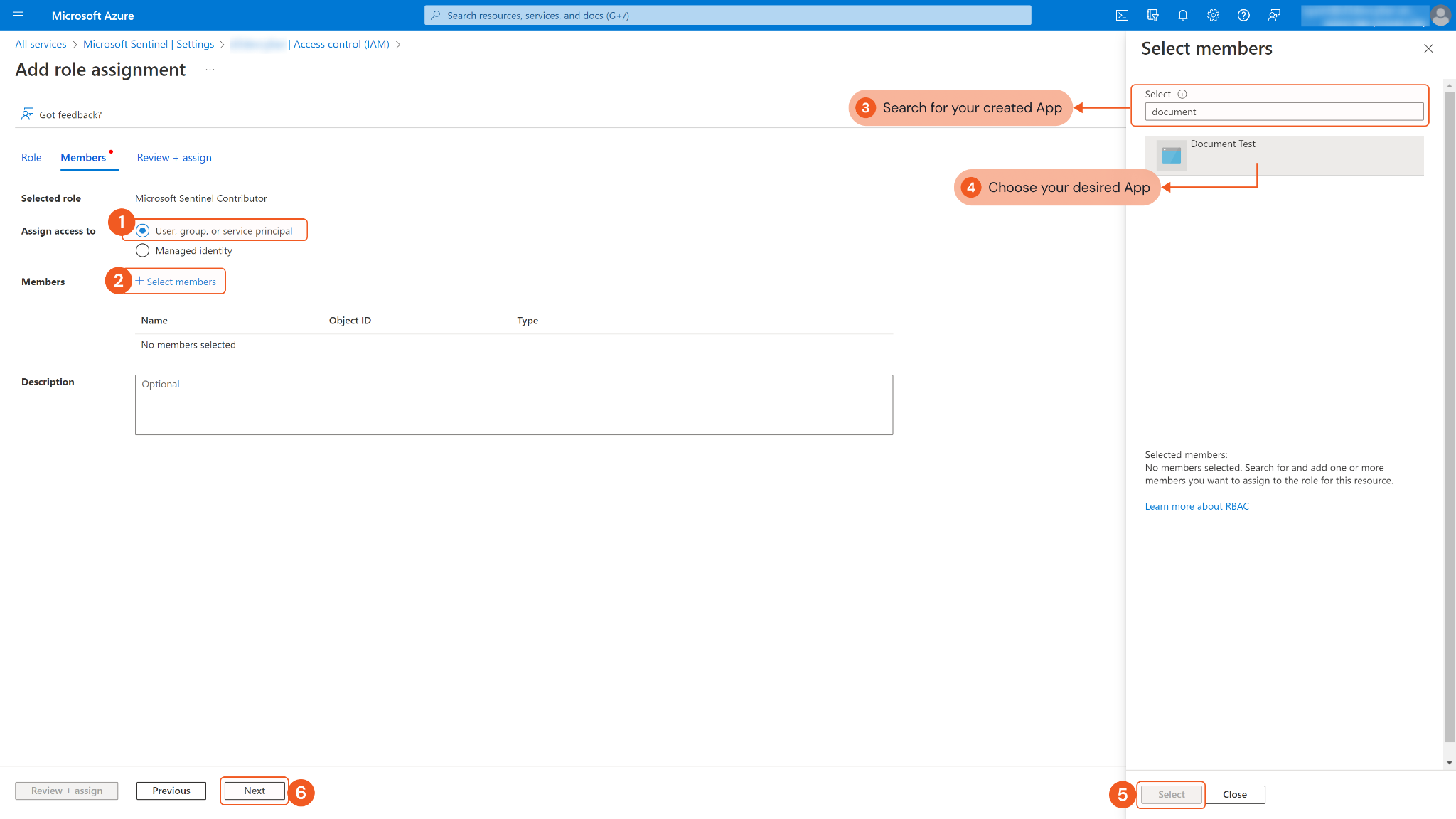
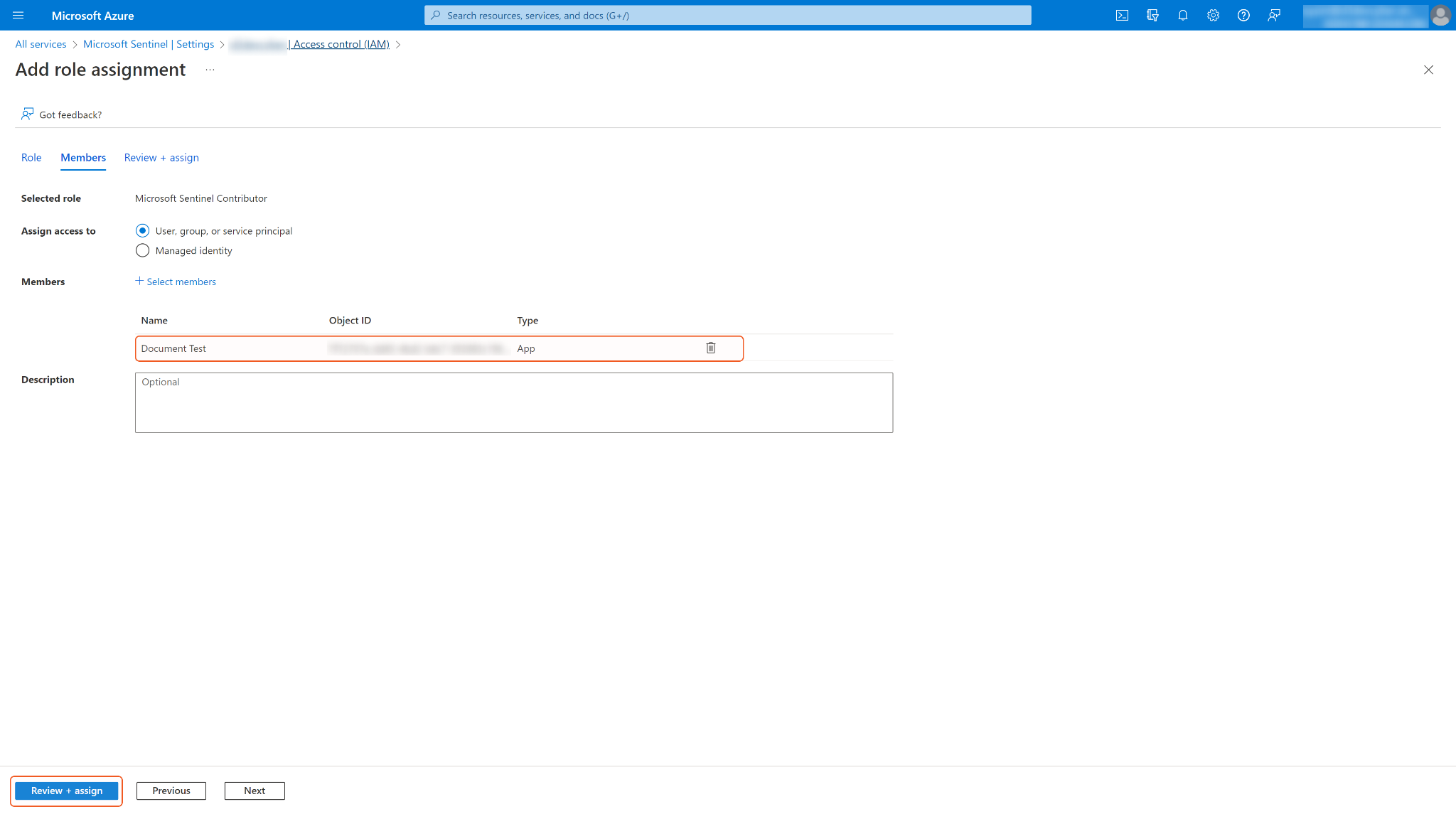
Click Next. Ensure you have selected the correct app, then click Review + assign.
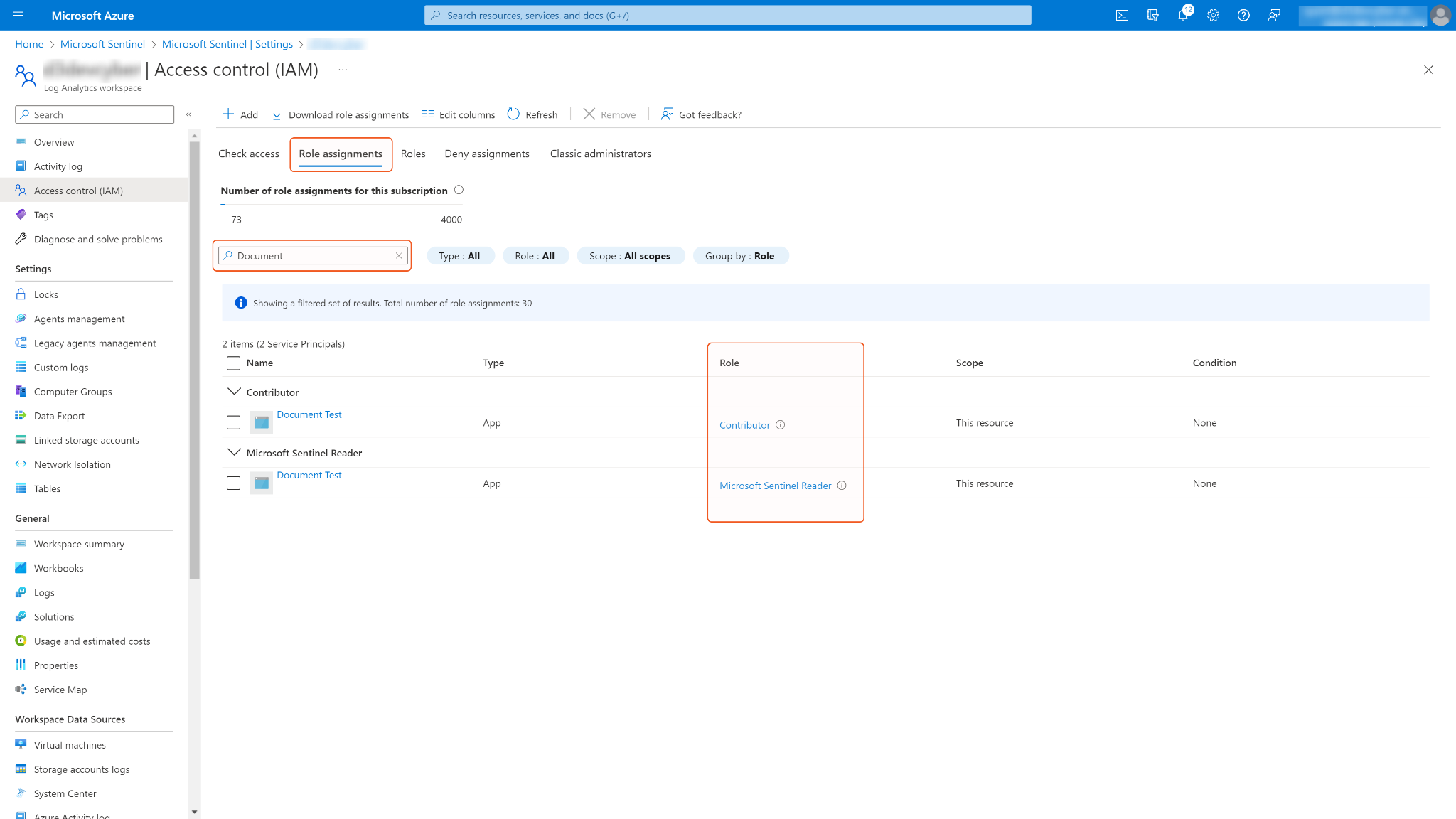
If you need to review or adjust your application's role assignment, go to Role assignments and search for your application. Select the role you want to remove.
Configuring D3 SOAR to Work with Microsoft Sentinel
Log in to D3 SOAR.
Find the Microsoft Sentinel integration.
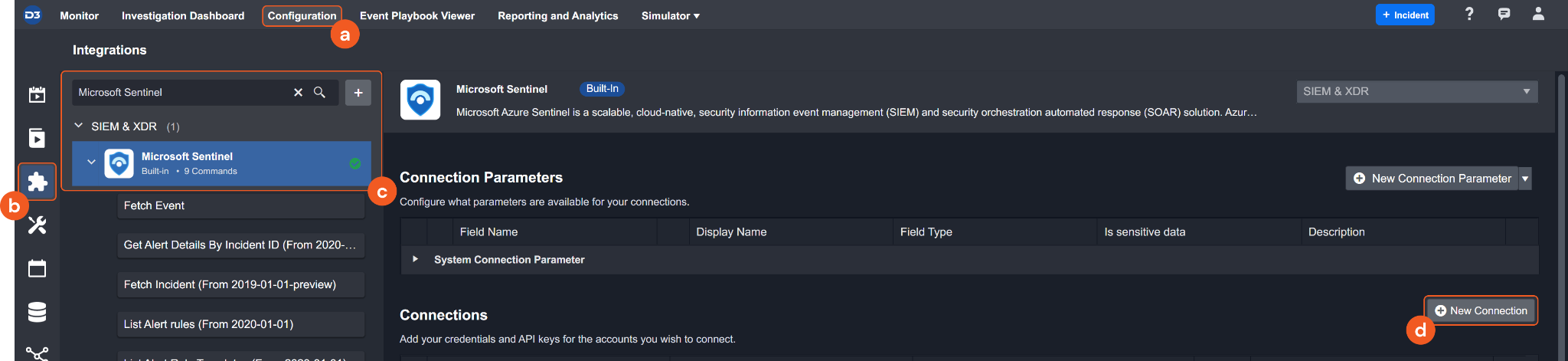
Navigate to Configuration on the top header menu.
Click on the Integration icon on the left sidebar.
Type Microsoft Sentinel in the search box to find the integration, then click it to select it.
Click + New Connection, on the right side of the Connections section. A new connection window will appear.
Configure the following fields to create a connection to Microsoft Sentinel.
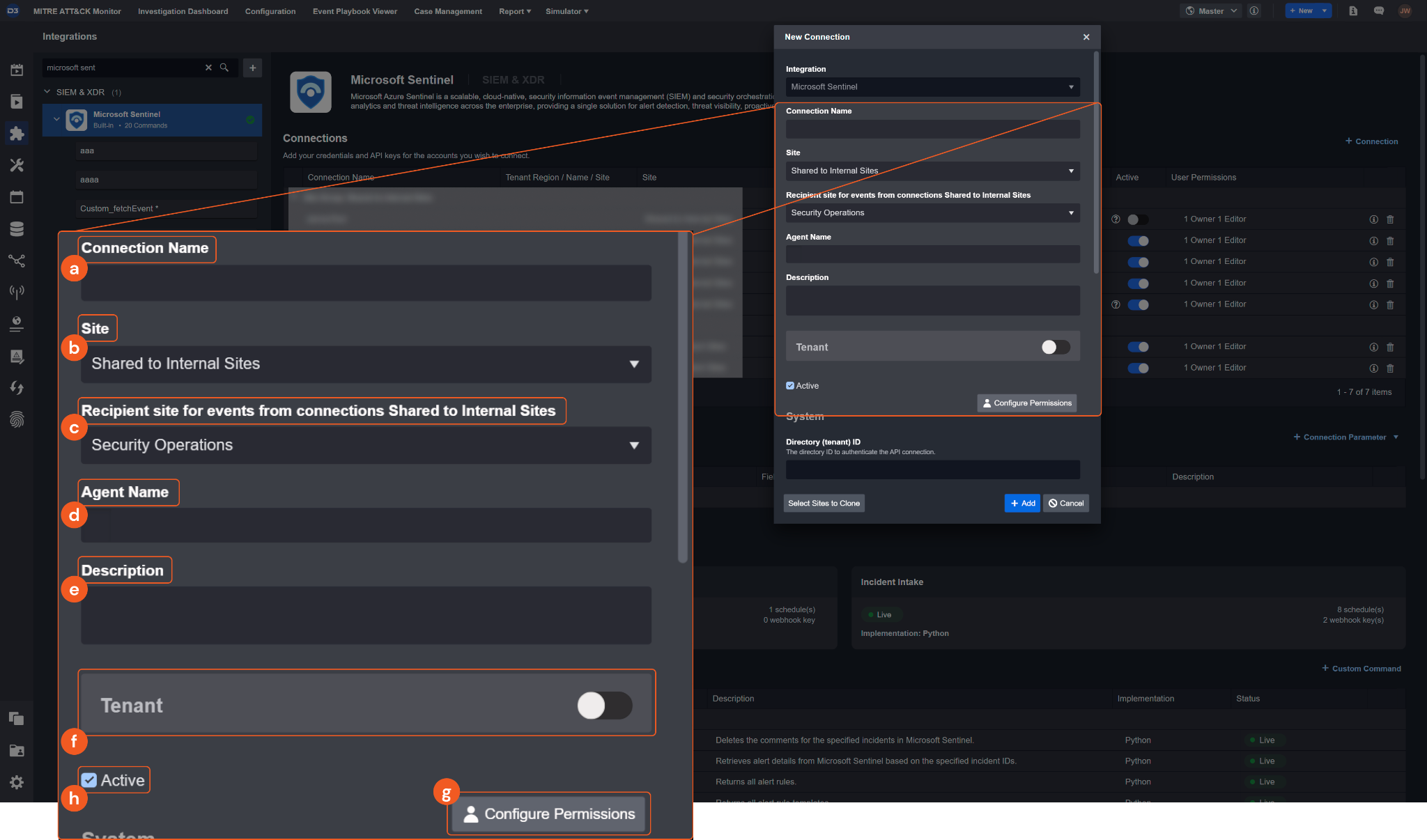
Connection Name: The desired name for the connection.
Site: Specifies the site to use the integration connection. Use the drop-down menu to select the site. The Share to Internal Sites option enables all sites defined as internal sites to use the connection. Selecting a specific site will only enable that site to use the connection.
Recipient site for events from connections Shared to Internal Sites: This field appears if you selected Share to Internal Sites for Site to let you select the internal site to deploy the integration connection.
Agent Name (Optional): Specifies the proxy agent required to build the connection. Use the dropdown menu to select the proxy agent from a list of previously configured proxy agents.
Description (Optional): Add your desired description for the connection.
Tenant (Optional): When configuring the connection from a master tenant site, you have the option to choose the specific tenant sites you want to share the connection with. Once you enable this setting, you can filter and select the desired tenant sites from the dropdowns to share the connection.
Configure User Permissions: Defines which users have access to the connection.
Active: Check the tick box to ensure the connection is available for use.
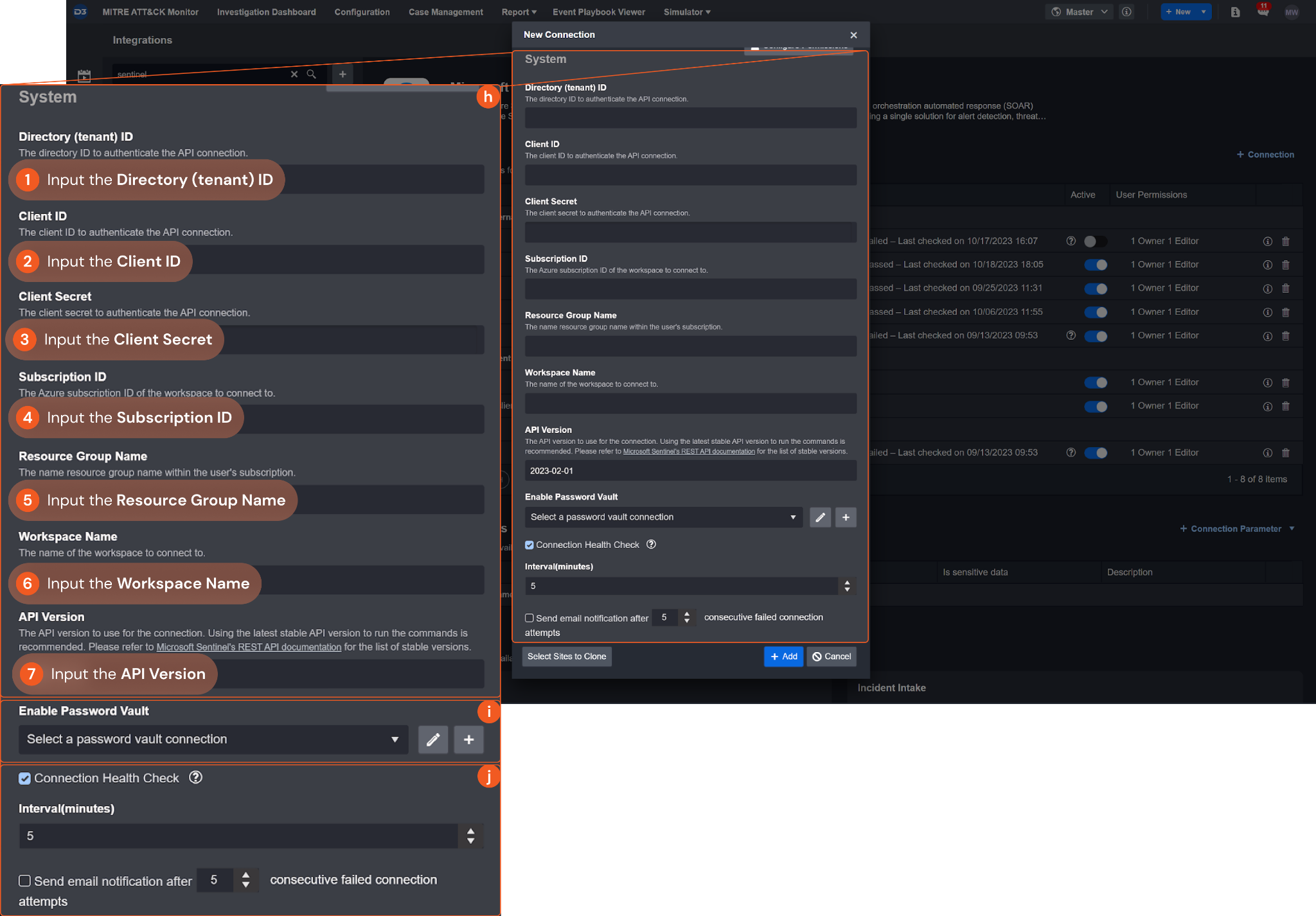
System: This section contains the parameters defined specifically for the integration. These parameters must be configured to create the integration connection.
1. Input the Directory (tenant) ID. See step 6 of Configuring Microsoft Sentinel to Work with D3 SOAR.2. Input the Client ID. See step 6 of Configuring Microsoft Sentinel to Work with D3 SOAR.
3. Input the Client Secret. See step 8 of Configuring Microsoft Sentinel to Work with D3 SOAR.
4. Input the Subscription ID. See step 12 of Configuring Microsoft Sentinel to Work with D3 SOAR.
5. Input the Resource Group Name. See step 12 of Configuring Microsoft Sentinel to Work with D3 SOAR.
6. Input the Workspace Name. See step 12 of Configuring Microsoft Sentinel to Work with D3 SOAR.
7. Input the API Version. The default value is 2023-02-01. Using the latest stable API version to run the commands is recommended. Please refer to Microsoft Sentinel's REST API documentation for the list of stable versions.
Enable Password Vault: An optional feature that allows users to take the stored credentials from their own password vault. Please refer to the password vault connection guide if needed.
Connection Health Check: Updates the connection status you have created. A connection health check is done by scheduling the Test Connection command of this integration. This can only be done when the connection is active.
To set up a connection health check, check the Connection Health Check tickbox. You can customize the interval (minutes) for scheduling the health check. An email notification can be set up after a specified number of failed connection attempts.
Test the connection.
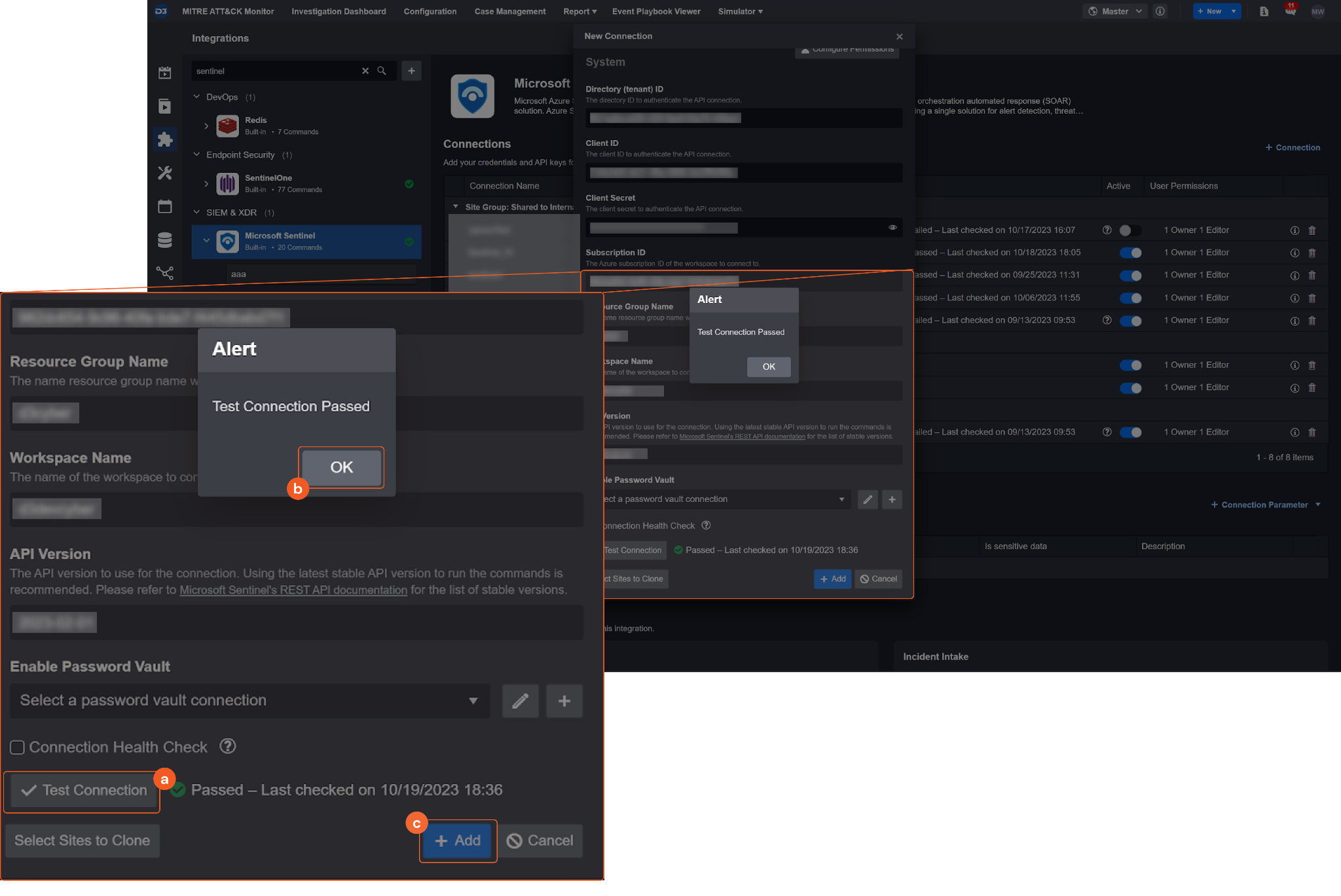
Click Test Connection to verify the account credentials and network connection. If the Test Connection Passed alert window appears, the test connection is successful. You will see Passed with a green checkmark appear beside the Test Connection button. If the test connection fails, please check your connection parameters and try again.
Click OK to close the alert window.
Click + Add to create and add the configured connection.
Commands
Microsoft Sentinel includes the following executable commands for users to set up schedules or create playbook workflows. With the Test Command, you can execute these commands independently for playbook troubleshooting.
Integration API Note
For more information about the Microsoft Sentinel API, please refer to the Microsoft Sentinel API reference.
READER NOTE
Certain permissions are required for each command. Please refer to the Permission Requirements and Configuring Microsoft Sentinel to Work with D3 SOAR for details.
Note for Time-related parameters
The input format of time-related parameters may vary based on your account settings. As a result, the sample data provided in our commands is different from what you see. To set your preferred time format, follow these steps:
Navigate to Configuration > Application Settings. Select Date/Time Format.
Choose your desired date and time format.
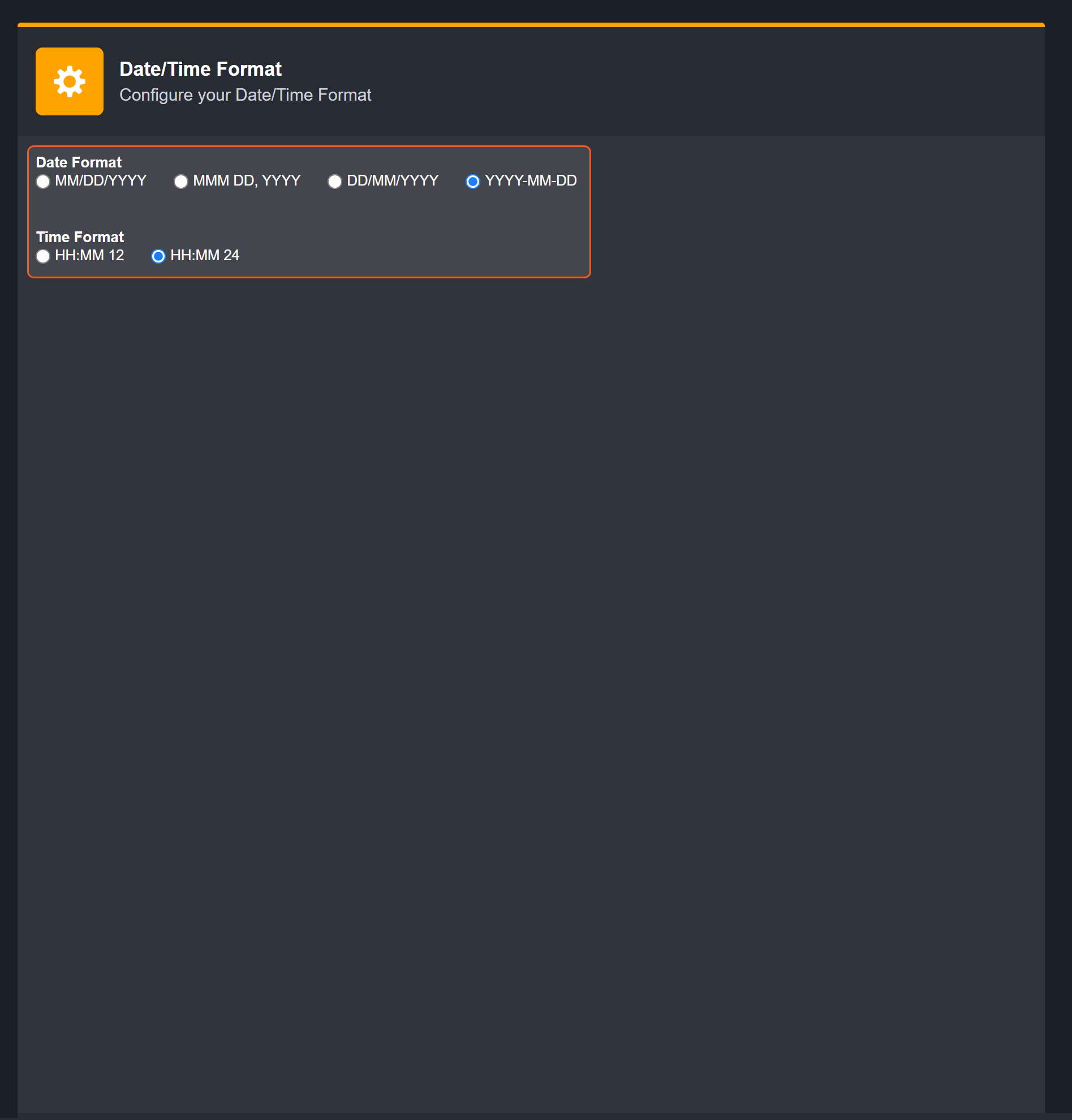
After that, you will be able to view your preferred time format when configuring the DateTime input parameters for commands.
Delete Incident Comments
Deletes the comments for the specified incidents in Microsoft Sentinel.
READER NOTE
Incident IDs and Comment Names are required parameters to run this command.
Run the Fetch Incidents command with defined filters to retrieve the desired Incident IDs and Comment Names. The Incident IDs can be found in the raw data at the path $.values[*].name. Comment Names can be found from the returned raw data at the path $.value[*].comments[*].name.
Comment Names must match the input Incident IDs. Not all incidents have comments.
Using the latest stable API version to run the commands is recommended. Please refer to Microsoft Sentinel's REST API documentation for the list of stable versions.
Input
Input Parameter | Required /Optional | Description | Example |
Incident IDs | Required | The IDs of the incidents to delete comments. Incident IDs can be obtained using the Fetch Incident command. | [**********************"] |
Comment Names | Required | The name(s) of the comment(s) to be deleted. Comment Names can be obtained using the Fetch Incident command. | [ "2023-03-18 12:44 PM" ] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Delete Incident Comments failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Microsoft Sentinel portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Incident IDs Not Found. |
Error Sample Data Delete Incident Comments failed. Status Code: 404. Message: Incident IDs Not Found. |
Fetch Event
Retrieves events from Microsoft Sentinel based on a specified Kusto query. Note: The default workspace retention time is 30 days for Analytics tables and 8 days for Basic tables. Events beyond this retention period will not be returned.
READER NOTE
D3 SOAR can fetch events from all available tables, including Azure tables and custom tables. As the Security Alert, Security Event, and Security Incident tables are the most commonly used, additional examples and field mappings for these tables are provided.
Using the latest stable API version to run the commands is recommended. Please refer to Microsoft Sentinel's REST API documentation for the list of stable versions.
Input
Input Parameter | Required /Optional | Description | Example |
Start Time | Required | The start time of the time range to fetch events by stored time in a workspace, in UTC time. | 2023-04-01 00:00 |
End Time | Optional | The end time of the time range to fetch events by stored time in a workspace, in UTC time. | 2023-04-02 00:00 |
Number of Event(s) Fetched | Optional | The maximum number of events to return. If the input value is 0, a negative number, or not specified, the command will return all events within the given time range. | 20 |
Search Condition | Required | The Kusto query to fetch events. For more information about the Kusto Query Language (KQL) syntax, see KQL quick reference. It is recommended to use the provided sample data as a template to build your own query by modifying the "where" clause based on your needs. Some common tables to query are SecurityAlert, SecurityEvent and SecruityIncident. Additional field mappings for these tables are provided. All keys in the returned raw data can be used as search keys. Use the ‘|' character to separate the table name and search condition (e.g. SecurityAlert | where AlertName != "Windows logon success"). Note: Do not include the limit, take, and time fields in your KQL query. If these fields are included, their values will be overridden by the values of the Top Recent Event Number, Start Time, and End Time parameters. | For SecurityAlert SecurityAlert | where AlertName != "Windows logon success" For SecurityEvent SecurityEvent | where ProcessName == 'C:\\Windows\\***\\***.exe' For SecurityIncident SecurityIncident | where Status == "New" and Severity == "High" For All tables TestCustomLog_1_CL|where ingestion_time() between(datetime(2022-12-08T08:11:15Z) .. datetime(2022-12-10T08:11:18Z))|project TimeGenerated, _TimeReceived, ingestion_time(),RawData |
Tolerance Scope | Optional | The tolerance scope in minutes of the query to fetch events between start and end time to avoid the loss of events. Events will be fetched between {Start Time - Tolerance Scope}. The default value is 0. | 10 |
Output
To view the sample output data for all commands, refer to this article.
Fetch Event Field Mapping
Please note that Fetch Event commands require event field mapping. Field mapping plays a key role in the data normalization process part of the event pipeline. Field mapping converts the original data fields from the different providers to the D3 fields which are standardized by the D3 Model. Please refer to Event and Incident Intake Field Mapping for details.
If you require a custom field mapping, click + Add Field to add a custom field mapping. You may also remove built-in field mappings by clicking x. Please note that two underscore characters will automatically prefix the defined Field Name as the System Name for a custom field mapping. Additionally, if an input Field Name contains any spaces, they will automatically be replaced with underscores for the corresponding System Name.
The Microsoft Sentinel integration in D3 SOAR has some pre-configured field mappings for the all tables, Security Event, Security Alert and Security Incident, which correspond to the Default Event Source, Event Source for Security Event, Event Source for Security Alert and Event Source for Security Incident mappings:
Default Event Source
Configures the field mapping which is specific to all tables related events. If a source field in the field mapping is not found, the corresponding field mapping will be ignored. The default event source has a "Main Event JSON Path" (i.e., $) that is used to extract a batch of events from the response raw data. Click Edit Event Source to view the "Main Event JSON Path". Click Edit Event Source to view the "Main Event JSON Path".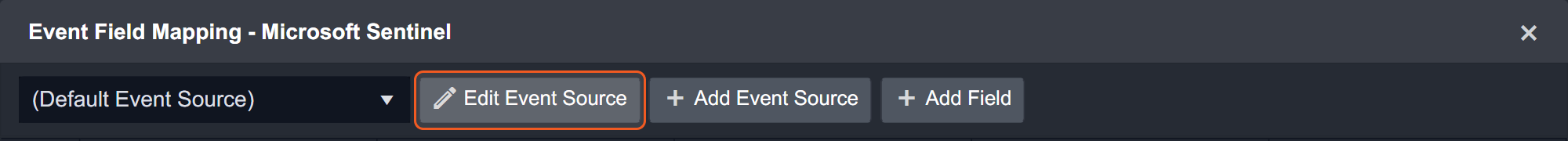
Main Event JSON Path: $
The Main Event JSON Path determines the root path where the system starts parsing raw response data into D3 event data. The JSON path begins with $, representing the root element. The path is formed by appending a sequence of child elements to $, each separated by a dot (.). Square brackets with nested quotation marks ([‘...']) should be used to separate child elements in JSON arrays.
For example, the root node of a JSON Path is $. The child node denoting the Event Type field would be Type. Putting it together, the JSON Path expression to extract the Event Type is $.Type.
Event Source for Security Event
Configures the field mapping which are specific to the Security Event-related events. If a source field in the field mapping is not found, the corresponding field mapping will be ignored. As the data of the Security Event-related events have a character that the value of the Type field is SecurityEvent, the Security Event-related events can be defined by the Search String: {$.Type}=SecurityEvent. Click Edit Event Source to view the Search String.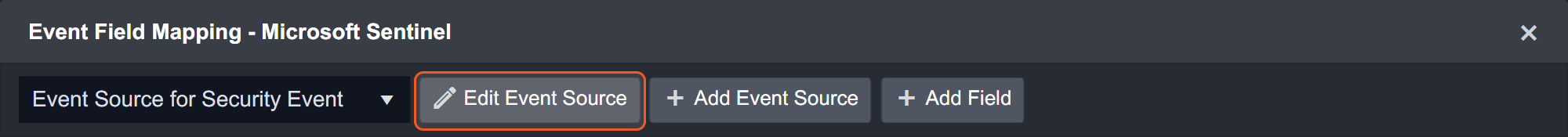
Event Source for Security Alert
Configures the field mapping which are specific to the Security Alert-related events. If a source field in the field mapping is not found, the corresponding field mapping will be ignored. As the data of the Security Alert-related events have a character that the value of the Type field is SecurityAlert, the Security Alert-related events can be defined by the Search String: {$.Type}=SecurityAlert. Click Edit Event Source to view the Search String.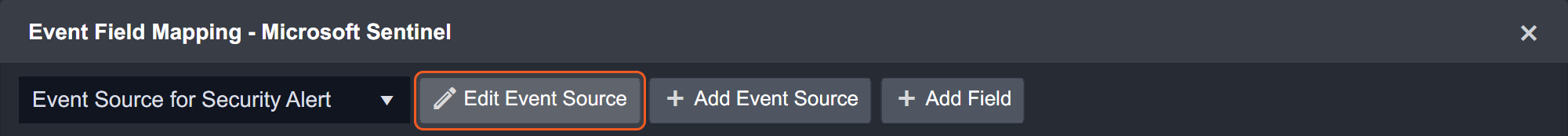
Event Source for Security Incident
Configures the field mapping which are specific to the Security Incident-related events. If a source field in the field mapping is not found, the corresponding field mapping will be ignored. As the data of the Security Incident-related events have a character that the value of the Type field is SecurityIncident, the Security Incident-related events can be defined by the Search String: {$.Type}=SecurityIncident. Click Edit Event Source to view the Search String.
The pre-configured field mappings are detailed below:
Field Name | Source Field |
Default Event Source (Main Event JSON Path: $) | |
Event Type | .Type |
Source System | .SourceSystem |
Start Time | .TimeGenerated |
Computer | .Computer |
Time Of Command | .TimeOfCommand |
Container ID | .ContainerID |
Target image | .image |
Event name | .Name |
Resource ID | ._ResourceId |
Log Entry | .LogEntry |
Source | .Source |
Event Log | .EventLog |
Event level | .EventLevel |
Unique Event Key | .EventOriginId |
Event Data | .EventData |
Event category | .EventCategory |
Username | .UserName |
Service name | .ServiceName |
Service ID | .ServiceId |
Role | .Role |
Message | .Message |
Management Group Name | .ManagementGroupName |
Rendered Description | .RenderedDescription |
Time Stamp | .Timestamp |
Alert ID | .AlertId |
Entity Type | .EntityType |
Evidence Role | .EvidenceRole |
Evidence Direction | .EvidenceDirection |
Folder Path | .FolderPath |
File Name | .FileName |
File Hash SHA1 | .SHA1 |
File Hash SHA256 | .SHA256 |
File Hash MD5 | .MD5 |
Filesize | .FileSize |
Threat category | .ThreatFamily |
Account Name | .AccountName |
Account Domain | .AccountDomain |
Device ID | .DeviceId |
Device Name | .DeviceName |
Local IP | .LocalIP |
Malicious IP Address | .MaliciousIP |
Remote URL | .RemoteUrl |
Email subject | .EmailSubject |
App | .Application |
Application ID | .ApplicationId |
Process Command Line | .ProcessCommandLine |
Registry key name | .RegistryKey |
Registry value name | .RegistryValueName |
Registry value data | .RegistryValueData |
Alert Priority | .AlertPriority |
Provider | .Provider |
Original Severity | .OriginalSeverity |
Alert Name | .AlertName |
Alert Description | .AlertDescription |
Resolved By | .ResolvedBy |
Last Modified By | .LastModifiedBy |
Alert State | .AlertState |
Time Raised | .TimeRaised |
Time Resolved | .TimeResolved |
Time Last Modified | .TimeLastModified |
Alert Context | .AlertContext |
Ticket ID | .TicketId |
Alert Unique ID | .AlertUniqueId |
WMI filter query | .Query |
Alert Rule ID | .AlertRuleId |
Resource Type | .ResourceType |
Resource Value | .ResourceValue |
Hostname | .HostName |
Alert Status | .AlertStatus |
Trigger ID | .TriggerId |
URL | .Url |
Comments | .Comments |
Template ID | .TemplateId |
Alert type | .AlertType |
Alert Title | .AlertTitle |
Command Line | .CommandLine |
Detection ID | .DetectionID |
Full Path | .FullPath |
Parent process name | .ParentProcess |
Child Process Name | .ChildProcess |
Subscription ID | .SubscriptionId |
Receipt time (UTC) | .ReceiptTime |
Device Product | .DeviceProduct |
Device Action | .DeviceAction |
Log Severity | .LogSeverity |
Device IP address | .DeviceAddress |
Destination IP address | .DestinationIP |
Destination port | .DestinationPort |
Source IP address | .SourceIP |
Source port | .SourcePort |
Remote IP address | .RemoteIP |
Remote port | .RemotePort |
Threat severity | .ThreatSeverity |
Threat Description | .ThreatDescription |
Threat Confidence | .ThreatConfidence |
Protocol Info | .Protocol |
Malicious IP Country | .MaliciousIPCountry |
Malicious IP Longitude | .MaliciousIPLongitude |
Malicious IP Latitude | .MaliciousIPLatitude |
Source hostname | .SourceHostName |
Source MAC address | .SourceMACAddress |
Device MAC address | .DeviceMacAddress |
Destination MAC | .DestinationMACAddress |
Account SID | .AccountSid |
Channel | .Channel |
Raw event data | .RawEventData |
Event code | .EventID |
Client IP | .ClientIP |
Category | .Category |
Identity | .Identity |
Resource | .Resource |
Resource Group | .ResourceGroup |
Raw Data | .RawData |
User Principal Name | .UserPrincipalName |
Event Source for Security Event (Search String: {$.Type}=SecurityEvent) The search string format is {jsonpath}=value. If the value of the Type key is SecurityEvent in the event object under raw data, then the Security Event-related events will use the field mapping below. | |
Unique Event Key | .EventOriginId |
Event Type | .Type |
Description | .Activity |
Status | .Status |
Start Time | .TimeGenerated |
Device IP address | .IpAddress |
File Hash | .FileHash |
Filepath | .FilePath |
Process ID | .ProcessId |
Process Name | .ProcessName |
Username | .UserPrincipalName |
Service name | .ServiceName |
Event Source for Security Alert (Search String: {$.Type}=SecurityAlert) The search string format is {jsonpath}=value. If the value of the Type key is SecurityAlert in the event object under raw data, then the Security Alert-related events will use the field mapping below. | |
Unique Event Key | .SystemAlertId |
Event name | .AlertName |
Event Type | .Type |
Severity | .AlertSeverity |
Description | .Description |
Status | .Status |
Start Time | .TimeGenerated |
Tactics | .Tactics |
Tactics | .Techniques |
Alert Name | .AlertName |
Alert type | .AlertType |
Alert Timestamp | .StartTime |
Extended Properties | .ExtendedProperties |
Confidence Level | .ConfidenceLevel |
Confidence Score | .ConfidenceScore |
Source Computer ID | .SourceComputerId |
Entities | .Entities |
Source System | .SourceSystem |
Product Name | .ProductName |
Product Component Name | .ProductComponentName |
Compromised Entity | .CompromisedEntity |
Raw event data | .DecodedAlertedEvent |
Event Type | .DecodedAlertedEvent[*].Type |
Source System | .DecodedAlertedEvent[*].SourceSystem |
Confidence Level | .DecodedAlertedEvent[*].ConfidenceLevel |
Confidence Score | .DecodedAlertedEvent[*].ConfidenceScore |
Device IP address | .DecodedAlertedEvent[*].DeviceAddress |
Device MAC address | .DecodedAlertedEvent[*].DeviceMacAddress |
Unique Event Key | DecodedAlertedEvent[*].EventOriginId |
Destination port | .DecodedAlertedEvent[*].DestinationPort |
Destination MAC | .DecodedAlertedEvent[*].DestinationMACAddress |
Event code | .DecodedAlertedEvent[*].EventID |
Product Name | .DecodedAlertedEvent[*].ProductName |
Product Component Name | .DecodedAlertedEvent[*].ProductComponentName |
Description | .DecodedAlertedEvent[*].Description |
Device Product | .DecodedAlertedEvent[*].DeviceProduct |
Event category | .DecodedAlertedEvent[*].EventCategory |
App | .DecodedAlertedEvent[*].Application |
Event Name | .DecodedAlertedEvent[*].Name |
Entities | .DecodedAlertedEvent[*].Entities |
Destination IP address | .DecodedAlertedEvent[*].DestinationIP |
Time Resolved | .DecodedAlertedEvent[*].TimeResolved |
Time Stamp | .DecodedAlertedEvent[*].Timestamp |
User Roles | .DecodedAlertedEvent[*].UserRoles |
Vendor Name | .DecodedAlertedEvent[*].VendorName |
Vendor Original ID | .DecodedAlertedEvent[*].VendorOriginalId |
Workspace Resource Group | .DecodedAlertedEvent[*].WorkspaceResourceGroup |
Workspace Subscription ID | .DecodedAlertedEvent[*].WorkspaceSubscriptionId |
Workstation Name | .DecodedAlertedEvent[*].WorkstationName |
Event level | .DecodedAlertedEvent[*].EventLevel |
Alert Name | .DecodedAlertedEvent[*].AlertName |
File Hash MD5 | .DecodedAlertedEvent[*].MD5 |
File Hash SHA1 | .DecodedAlertedEvent[*].SHA1 |
File Hash SHA256 | .DecodedAlertedEvent[*].SHA256 |
Start Time | .DecodedAlertedEvent[*].TimeGenerated |
Filesize | .DecodedAlertedEvent[*].FileSize |
Hostname | .DecodedAlertedEvent[*].HostName |
Parent process name | .DecodedAlertedEvent[*].ParentProcess |
Process command line | .DecodedAlertedEvent[*].ProcessCommandLine |
Trigger ID | .DecodedAlertedEvent[*].TriggerId |
Unique Token Identifier | .DecodedAlertedEvent[*].UniqueTokenIdentifier |
URL Entities | .Entities_json..[?(@.Type=='url')].Url |
User | .DecodedAlertedEvent[*].User |
User Agent | .DecodedAlertedEvent[*].UserAgent |
User Display Name | .DecodedAlertedEvent[*].UserDisplayName |
User ID | .DecodedAlertedEvent[*].UserId |
User IP Address | .DecodedAlertedEvent[*].UserIPAddress |
User Principal Name | .DecodedAlertedEvent[*].UserPrincipalName |
Tactics | .DecodedAlertedEvent[*].Tactics |
Techniques | .DecodedAlertedEvent[*].Techniques |
Time Of Command | .DecodedAlertedEvent[*].TimeOfCommand |
Time Raised | .DecodedAlertedEvent[*].TimeRaised |
Ticket ID | .DecodedAlertedEvent[*].TicketId |
Time Last Modified | .DecodedAlertedEvent[*].TimeLastModified |
Threat Confidence | .DecodedAlertedEvent[*].ThreatConfidence |
Threat Description | .DecodedAlertedEvent[*].ThreatDescription |
Resource Identity | .DecodedAlertedEvent[*].ResourceIdentity |
Resource IDs | .DecodedAlertedEvent[*].ResourceIds |
Resource Service Principal ID | .DecodedAlertedEvent[*].ResourceServicePrincipalId |
Resource Tenant ID | .DecodedAlertedEvent[*].ResourceTenantId |
Resource Type | .DecodedAlertedEvent[*].ResourceType |
Success IP Address | .DecodedAlertedEvent[*].SuccessIPAddress |
System Alert ID | .DecodedAlertedEvent[*].SystemAlertId |
Target | .DecodedAlertedEvent[*].Target |
Target Account | .DecodedAlertedEvent[*].TargetAccount |
Target Domain Name | .DecodedAlertedEvent[*].TargetDomainName |
Target Resources | .DecodedAlertedEvent[*].TargetResources |
Target User Name | .DecodedAlertedEvent[*].TargetUserName |
Target User Principal Name | .DecodedAlertedEvent[*].TargetUserPrincipalName |
Target User SID | .DecodedAlertedEvent[*].TargetUserSid |
Task | .DecodedAlertedEvent[*].Task |
Template ID | .DecodedAlertedEvent[*].TemplateId |
Status | .DecodedAlertedEvent[*].Status |
Subject Account | .DecodedAlertedEvent[*].SubjectAccount |
Subject Domain Name | .DecodedAlertedEvent[*].SubjectDomainName |
Subject Logon ID | .DecodedAlertedEvent[*].SubjectLogonId |
Subject Status | .DecodedAlertedEvent[*].SubStatus |
Subject User Name | .DecodedAlertedEvent[*].SubjectUserName |
Subject User SID | .DecodedAlertedEvent[*].SubjectUserSid |
Subscription ID | .DecodedAlertedEvent[*].SubscriptionId |
Role Name | .DecodedAlertedEvent[*].RoleName |
Roles | .DecodedAlertedEvent[*].Roles |
Score | .DecodedAlertedEvent[*].score |
Service Principal ID | .DecodedAlertedEvent[*].ServicePrincipalId |
Sign In Identifier | .DecodedAlertedEvent[*].SignInIdentifier |
Raw Event Data | .DecodedAlertedEvent[*].RawEventData |
Resource Value | .DecodedAlertedEvent[*].ResourceValue |
Resources | .DecodedAlertedEvent[*].Resources |
Result Description | .DecodedAlertedEvent[*].ResultDescription |
Result Reason | .DecodedAlertedEvent[*].ResultReason |
Result Type | .DecodedAlertedEvent[*].ResultType |
Risk Detail | .DecodedAlertedEvent[*].RiskDetail |
Risk Event Types | .DecodedAlertedEvent[*].RiskEventTypes |
Risk Level | .DecodedAlertedEvent[*].RiskLevel |
Role | .DecodedAlertedEvent[*].Role |
Resource Groups | .DecodedAlertedEvent[*].ResourceGroups |
Resource ID | .DecodedAlertedEvent[*].ResourceId |
Resource Display Name | .DecodedAlertedEvent[*].ResourceDisplayName |
Resource Group | .DecodedAlertedEvent[*].ResourceGroup |
Resolved By | .DecodedAlertedEvent[*].ResolvedBy |
Resource | .DecodedAlertedEvent[*].Resource |
Remote URL | .DecodedAlertedEvent[*].RemoteUrl |
Rendered Description | .DecodedAlertedEvent[*].RenderedDescription |
Remote IP Address | .DecodedAlertedEvent[*].RemoteIP |
Remote port | .DecodedAlertedEvent[*].RemotePort |
Provider | .DecodedAlertedEvent[*].Provider |
Provider Name | .DecodedAlertedEvent[*].ProviderName |
Raw Data | .DecodedAlertedEvent[*].RawData |
PIM Resource Group | .DecodedAlertedEvent[*].PIMResourceGroup |
Process | .DecodedAlertedEvent[*].Process |
Process Entities | .Entities_json..[?(@.Type=='process')].ProcessId,CommandLine |
Operation IDs | .DecodedAlertedEvent[*].OperationIds |
Operation Name | .DecodedAlertedEvent[*].OperationName |
Operation Name Value | .DecodedAlertedEvent[*].OperationNameValue |
Original Severity | .DecodedAlertedEvent[*].OriginalSeverity |
Malicious IP Longitude | .DecodedAlertedEvent[*].MaliciousIPLongitude |
Malware Entities | .Entities_json..[?(@.Type=='malware')].Name,Category |
Management Group Name | .DecodedAlertedEvent[*].ManagementGroupName |
Malicious IP Country | .DecodedAlertedEvent[*].MaliciousIPCountry |
Malicious IP Latitude | .DecodedAlertedEvent[*].MaliciousIPLatitude |
Local IP | .DecodedAlertedEvent[*].LocalIP |
Log Entry | .DecodedAlertedEvent[*].LogEntry |
Log Severity | .DecodedAlertedEvent[*].LogSeverity |
Logon Process Name | .DecodedAlertedEvent[*].LogonProcessName |
Logon Type | .DecodedAlertedEvent[*].LogonType |
Logon Type Name | .DecodedAlertedEvent[*].LogonTypeName |
Mailbox Entities | .Entities_json..[?(@.Type=='mailbox')].MailboxPrimaryAddress |
MailCluster Entities | .Entities_json..[?(@.Type=='mailCluster')].Query,Source |
MailMessage Entities | .Entities_json..[?(@.Type=='mailMessage')].NetworkMessageId,InternetMessageId,Sender,Recipient,Subject |
Malicious IP Address | .DecodedAlertedEvent[*].MaliciousIP |
Identity | .DecodedAlertedEvent[*].Identity |
Initiated By Display Name | .DecodedAlertedEvent[*].InitiatedByDisplayName |
Initiating User | .DecodedAlertedEvent[*].InitiatingUser |
IP Address | .DecodedAlertedEvent[*].IpAddress |
IP Custom Entity | .DecodedAlertedEvent[*].IPCustomEntity |
IP Entities | .Entities_json..[?(@.Type=='ip')].Address |
Last Modified By | .DecodedAlertedEvent[*].LastModifiedBy |
Group Name | .DecodedAlertedEvent[*].GroupName |
Home Tenant ID | .DecodedAlertedEvent[*].HomeTenantId |
Host Entities | .Entities_json..[?(@.Type=='host')].HostName |
ID | .DecodedAlertedEvent[*].Id |
Folder Path | .DecodedAlertedEvent[*].FolderPath |
Full Path | .DecodedAlertedEvent[*].FullPath |
Entity Type | .DecodedAlertedEvent[*].EntityType |
Event Data | .DecodedAlertedEvent[*].EventData |
File Name Entities | .Entities_json..[?(@.Type=='file')].Name |
File SHA1 Entities | .Entities_json..[?(@.Type=='filehash' && @.Algorithm=='SHA1')].Value |
File SHA256 Entities | .Entities_json..[?(@.Type=='filehash' && @.Algorithm=='SHA256')].Value |
Evidence Role | .DecodedAlertedEvent[*].EvidenceRole |
Failed IP Address | .DecodedAlertedEvent[*].FailedIPAddress |
File MD5 Entities | .Entities_json..[?(@.Type=='filehash' && @.Algorithm=='MD5')].Value |
File Name | .DecodedAlertedEvent[*].FileName |
Event Log | .DecodedAlertedEvent[*].EventLog |
Event Source Name | .DecodedAlertedEvent[*].EventSourceName |
Evidence Direction | .DecodedAlertedEvent[*].EvidenceDirection |
Device Name | .DecodedAlertedEvent[*].DeviceName |
Display Name | .DecodedAlertedEvent[*].DisplayName |
Domain Entities | .Entities_json..[?(@.Type=='dns')].DomainName |
Device Action | .DecodedAlertedEvent[*].DeviceAction |
Device Detail | .DecodedAlertedEvent[*].DeviceDetail |
Device ID | .DecodedAlertedEvent[*].DeviceId |
Container ID | .DecodedAlertedEvent[*].ContainerID |
Correlation ID | .DecodedAlertedEvent[*].CorrelationId |
Correlation IDs | .DecodedAlertedEvent[*].CorrelationIds |
Detection ID | .DecodedAlertedEvent[*].DetectionID |
Computer | .DecodedAlertedEvent[*].Computer |
Source Computer ID | .DecodedAlertedEvent[*].SourceComputerId |
Operation Name | .DecodedAlertedEvent[*].OperationName |
Command Line | .DecodedAlertedEvent[*].CommandLine |
Comments | .DecodedAlertedEvent[*].Comments |
Cloud Application Entities | .Entities_json..[?(@.Type=='cloud-application')].Name,AppId |
App Display Name | .DecodedAlertedEvent[*].AppDisplayName |
Application ID | .DecodedAlertedEvent[*].ApplicationId |
Category | .DecodedAlertedEvent[*].Category |
Child Process Name | .DecodedAlertedEvent[*].ChildProcess |
Client IP | .DecodedAlertedEvent[*].ClientIP |
ARM Template PIM | .DecodedAlertedEvent[*].ARMTemplatePIM |
Caller | .DecodedAlertedEvent[*].Caller |
Caller IP Address | .DecodedAlertedEvent[*].CallerIpAddress |
Channel | .DecodedAlertedEvent[*].Channel |
Alert Title | .DecodedAlertedEvent[*].AlertTitle |
Alert Type | .DecodedAlertedEvent[*].AlertType |
Alert Unique ID | .DecodedAlertedEvent[*].AlertUniqueId |
Alert State | .DecodedAlertedEvent[*].AlertState |
Alert Status | .DecodedAlertedEvent[*].AlertStatus |
Alert Severity | .DecodedAlertedEvent[*].AlertSeverity |
Alert Priority | .DecodedAlertedEvent[*].AlertPriority |
Alert Rule ID | .DecodedAlertedEvent[*].AlertRuleId |
Alert Description | .DecodedAlertedEvent[*].AlertDescription |
Alert ID | .DecodedAlertedEvent[*].AlertId |
Account Type | .DecodedAlertedEvent[*].AccountType |
Activity | .DecodedAlertedEvent[*].Activity |
Activity Display Name | .DecodedAlertedEvent[*].ActivityDisplayName |
Additional Details | .DecodedAlertedEvent[*].AdditionalDetails |
Alert Context | .DecodedAlertedEvent[*].AlertContext |
Account Name | .DecodedAlertedEvent[*].AccountName |
Account SID | .DecodedAlertedEvent[*].AccountSid |
Account Entities | .Entities_json..[?(@.Type=='account')].Name |
AAD Tenant ID | .DecodedAlertedEvent[*].AADTenantId |
Account | .DecodedAlertedEvent[*].Account |
Account Custom Entity | .DecodedAlertedEvent[*].AccountCustomEntity |
Account Domain | .DecodedAlertedEvent[*].AccountDomain |
Process ID | .DecodedAlertedEvent[*].ProcessId |
Process Name | .DecodedAlertedEvent[*].ProcessName |
Protocol info | .DecodedAlertedEvent[*].Protocol |
WMI filter query | .DecodedAlertedEvent[*].Query |
Message | .DecodedAlertedEvent[*].Message |
Registry value data | .DecodedAlertedEvent[*].RegistryValueData |
Registry value name | .DecodedAlertedEvent[*].RegistryValueName |
Receipt time (UTC) | .DecodedAlertedEvent[*].ReceiptTime |
Registry key name | .DecodedAlertedEvent[*].RegistryKey |
Service ID | .DecodedAlertedEvent[*].ServiceId |
Service name | .DecodedAlertedEvent[*].ServiceName |
Source MAC address | .DecodedAlertedEvent[*].SourceMACAddress |
Source hostname | .DecodedAlertedEvent[*].SourceHostName |
Source IP address | .DecodedAlertedEvent[*].SourceIP |
Source port | .DecodedAlertedEvent[*].SourcePort |
Source | .DecodedAlertedEvent[*].Source |
Sub Event | .DecodedAlertedEvent |
Email subject | .DecodedAlertedEvent[*].EmailSubject |
URL | .DecodedAlertedEvent[*].Url |
Username | .DecodedAlertedEvent[*].UserName |
Threat category | .DecodedAlertedEvent[*].ThreatFamily |
Threat severity | .DecodedAlertedEvent[*].ThreatSeverity |
Target image | .DecodedAlertedEvent[*].image |
Event Source for Security Incident (Search String: {$.Type}=SecurityIncident) The search string format is {jsonpath}=value. If the value of the Type key is SecurityIncident in the event object under raw data, then the Security Incident-related events will use the field mapping below. | |
Status | .Status |
Severity | .Severity |
Comments | .Comments |
Start Time | .TimeGenerated |
Description | .Description |
Event name | .IncidentName |
Event Type | .Type |
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Fetch Event failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Microsoft Sentinel portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The provided authentication is not valid for this resource. |
Error Sample Data Fetch Event failed. Status Code: 403. Message: The provided authentication is not valid for this resource. |
Fetch Incident
Retrieves incidents from analytics or custom tables in Microsoft Sentinel. Note: Security Alerts are from the SecurityAlert table, which is an analytics table. The workplace default retention time for analytics tables is 30 days. Therefore, ingested Security Alerts that are 30 days or older will not be returned.
READER NOTE
Using the latest stable API version to run the commands is recommended. Please refer to Microsoft Sentinel's REST API documentation for the list of stable versions.
If no optional parameters are defined, all created incidents within your specified time range will be returned.
Access the Test tab on the Fetch Incident command page. Run the command with the required parameters to analyze the format of the response data. From the response data, locate the JSON paths corresponding to the fields that need to be synchronized in both D3 SOAR and Microsoft Sentinel. To simplify this process, you can use a JSON path picker tool by copying and pasting the data into it.
After identifying the JSON paths of interest, input them into the Update Field Mappings input parameter.The configuration for the incident system fields and dynamic fields is defined by field mappings. In addition, default values can be established for these system fields. The keys defined in D3 SOAR for these settings are "D3SystemFields" and "D3DefaultFields". When dealing with a dynamic field, the structure will follow the format: "sectionName": {"fieldName": "JSON Path to the value"}.
For Microsoft Sentinel, you can follow the structure shown in the provided sample data below and customize it to your use case by adding or removing key-value pairs under each first-level JSON key (i.e., "D3SystemFields," "MS Sentinel Key Information," "Classification for Incident Closure," and "D3DefaultFields").
{
"D3SystemFields": {
"status": "$.properties.status",
"owner": "$.properties.owner.userPrincipalName",
"Severity": "$.properties.severity",
"Conclusion": "$.properties.classificationComment"
},
"MS Sentinel Key Information": {
"Incident Number": "$.properties.incidentNumber",
"Incident Status": "$.properties.status",
"Incident Severity": "$.properties.severity",
"Incident Owner": "$.properties.owner.assignedTo",
"Incident Creation Date": "$.properties.createdTimeUtc",
"Alert Product Name": "$.properties.additionalData.alertProductNames",
"Incident Comment Timeline": "$.comments",
"Incident URL": "$.properties.incidentUrl"
},
"Classification for Incident Closure": {
"Classification": "$.properties.classification",
"ClassificationReason|TruePositive": "$.properties.classificationReason",
"ClassificationReason|BenignPositive": "$.properties.classificationReason",
"ClassificationReason|FalsePositive": "$.properties.classificationReason",
"ClassificationComment": "$.properties.classificationComment"
},
"D3DefaultFields": {
"owner": "defaultOwner@d3security.com"
}
}Here is a more in-depth explanation on each of the first-level keys:
D3SystemFields: Maps the paths from the raw Microsoft Sentinel incident data to the four incident system fields in D3 SOAR: incident status, the user principal name of the owner, the severity of the incident, and any comments related to the classification of the incident. These system fields are static and cannot be modified.
D3DefaultFields: Specifies the default owner of the ingested incident in D3 SOAR, in cases where D3 SOAR cannot map the owner of the Microsoft Sentinel Incident to a user in the D3 platform.
MS Sentinel Key Information: Maps the paths from the raw Microsoft Sentinel incident data to the section names of the "Microsoft Sentinel" incident form created in step 2. Verify the keys with your created incident form, as they should be aligned. Refer to response data from the previous test run to identify the correct JSON paths.
Classification for Incident Closure: Maps the paths of the raw Microsoft Sentinel incident data to the section names of the "Microsoft Sentinel" incident form created in step 2 pertaining to the classification information of the incident when it is closed by an analyst. Verify the keys with your created incident form, as they should be aligned. Again, refer to the response data from your previous test run to accurately identify the correct JSON paths.
NOTE: Ensure the default owner identified by the "owner" key has been created and configured with the necessary permissions to access the configured client site. You can do this by navigating to Configuration > Organization Management > Users.
Input
Input Parameter | Required /Optional | Description | Example |
Start Time | Required | The start time of the time range to fetch incidents by the specified query time type, in UTC time. | 2023-04-01 00:00 |
End Time | Required | The end time of the time range to fetch incidents by the specified query time type, in UTC time. | 2023-04-02 00:00 |
Query Time Type | Optional | The time field (i.e. Created Time or Last Modified Time) to filter incidents by. If Created Time is selected, only new incidents will be ingested (excluding incident updates). If Last Modified Time is selected, both new and updated incidents will be ingested. If this parameter is not defined, Created Time will be the default value. | Last Modified Time |
Number of Incident(s) Fetched | Optional | The maximum number of the most recent incidents to return. If this parameter is not defined, all incidents matching the search condition will be returned. | 10 |
Search Condition | Optional | The condition to filter results. For more about the filter syntax, refer to Use query parameters to customize responses and Use the $filter query parameter. The available search keys can be accessed by using the keys under the path $.value[*].properties in the returned raw data. To search for sub-properties, use the '/' character. For example, to search for the status sub-property, the input search key would be properties/status. | (properties/status eq 'New') and (properties/severity eq 'High') |
Tolerance Scope | Optional | The tolerance scope in minutes of the query to fetch incidents between start and end time to avoid the loss of events. Events will be fetched between {Start Time - Tolerance Scope}. The default value is 0. | 0 |
Update Field Mappings | Optional | The field mappings for the incident system fields or dynamic fields. Also it can set the default value for the system fields. The D3 defined keys are "D3SystemFields" and "D3DefaultFields". The dynamic field structure will be "sectionName": {"fieldName": "JSON Path to the value"}. Please refer to the sample data for the detailed fields and values. | { "D3SystemFields": { "status": "$.properties.status", "owner": "$.properties.owner.userPrincipalName", "Severity": "$.properties.severity", "Conclusion": "$.properties.classificationComment" }, "MS Sentinel Key Information": { "Incident Number": "$.properties.incidentNumber", "Incident Status": "$.properties.status", "Incident Severity": "$.properties.severity", "Incident Owner": "$.properties.owner.assignedTo", "Incident Creation Date": "$.properties.createdTimeUtc", "Alert Product Name": "$.properties.additionalData.alertProductNames", "Incident Comment Timeline": "$.comments", "Incident URL": "$.properties.incidentUrl" }, "Classification for Incident Closure": { "Classification": "$.properties.classification", "ClassificationReason|TruePositive": "$.properties.classificationReason", "ClassificationReason|BenignPositive": "$.properties.classificationReason", "ClassificationReason|FalsePositive": "$.properties.classificationReason", "ClassificationComment": "$.properties.classificationComment" }, "D3DefaultFields": { "owner": "defaultOwner" } } |
Return additional Information | Optional | The additional information of the incident to return. The available values are "All", "Alert", "Comment", "Sub Event (Contain Alert)", "Comment & Alert" and "None". The default value is "All" which means the returned incident will contain the comment, alert and the events of the alert. If "None" is selected, then only the incidents will be returned. | All |
Workspace ID | Optional | The workspace ID which is used to search log analytics tables. You don't need to enter it and it will be obtained automatically. | *************************************** |
Output
To view the sample output data for all commands, refer to this article.
Incident Field Mapping
For this integration, the default incident fields in D3 SOAR are fixed with no built-in source fields. Users can specify the source fields as needed.
Event and Incident Intake Field Mapping
Please note that incident and event intake commands require both Event Field and Incident Field Mapping. These field mappings are the default event/incident field mappings for D3 system integrations. You can edit the provided mappings or create custom mappings as needed. Please refer to Event and Incident Intake Field Mapping for more details.
Incident Main JSON Path: $.value
Field Name | Source Field |
Title | User to define |
Description | User to define |
Severity | User to define, default is "Low" |
Incident Type * | User to define, default is the first Incident form in D3 SOAR system |
Incident Creator | User to define |
Incident Owner | User to define |
Incident Playbook | User to define |
Due In Date | User to define |
Unique Key | User to define |
Tactics | User to define |
Techniques | User to define |
Event Field Mapping
Main Event JSON Path: $.value
The event field mapping in Fetch Incident is the same as the one in the Fetch Event command.
Please refer to the Fetch Event command for details.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Fetch Incident failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Microsoft Sentinel portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The provided authentication is not valid for this resource. |
Error Sample Data Fetch Incident failed. Status Code: 403. Message: The provided authentication is not valid for this resource. |
Get Alert Details By Incident ID
Retrieves alert details from Microsoft Sentinel based on the specified incident IDs.
READER NOTE
Incident IDs is a required parameter to run this command.
You should already have your desired Incident IDs on hand to run this command. If you don't, you may use the Fetch Incidents command with defined filters to retrieve the desired Incident IDs. The Incident IDs can be found in the raw data at the path $.values[*].name.
Using the latest stable API version to run the commands is recommended. Please refer to Microsoft Sentinel's REST API documentation for the list of stable versions.
Input
Input Parameter | Required /Optional | Description | Example |
Incident IDs | Required | The list of incident IDs to return alert details. Incident IDs can be obtained using the Fetch Incident command. | ["*****"] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Alert Details By Incident ID failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Microsoft Sentinel portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The client xxxxxx with object id xxxxxx does not have authorization to perform action 'Microsoft.SecurityInsights/incidents/read' over scope xxxxxx or the scope is invalid. If access was recently granted, please refresh your credentials. |
Error Sample Data Get Alert Details By Incident ID failed. Status Code: 401. Message: The client xxxxxx with object id xxxxxx does not have authorization to perform action 'Microsoft.SecurityInsights/incidents/read' over scope xxxxxx or the scope is invalid. If access was recently granted, please refresh your credentials. |
List Alert Rules
Returns all alert rules.
READER NOTE
Using the latest stable API version to run the commands is recommended. Please refer to Microsoft Sentinel's REST API documentation for the list of stable versions.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Alert Rules failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Microsoft Sentinel portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The client xxxxxx with object id xxxxxx does not have authorization to perform action 'Microsoft.SecurityInsights/incidents/read' over scope xxxxxx or the scope is invalid. If access was recently granted, please refresh your credentials. |
Error Sample Data List Alert Rules failed. Status Code: 401. Message: The client xxxxxx with object id xxxxxx does not have authorization to perform action 'Microsoft.SecurityInsights/incidents/read' over scope xxxxxx or the scope is invalid. If access was recently granted, please refresh your credentials. |
List Alert Rule Templates
Returns all alert rule templates.
READER NOTE
Using the latest stable API version to run the commands is recommended. Please refer to Microsoft Sentinel's REST API documentation for the list of stable versions.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Alert Rule Templates failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Microsoft Sentinel portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The client xxxxxx with object id xxxxxx does not have authorization to perform action 'Microsoft.SecurityInsights/incidents/read' over scope xxxxxx or the scope is invalid. If access was recently granted, please refresh your credentials. |
Error Sample Data List Alert Rule Templates failed. Status Code: 401. Message: The client xxxxxx with object id xxxxxx does not have authorization to perform action 'Microsoft.SecurityInsights/incidents/read' over scope xxxxxx or the scope is invalid. If access was recently granted, please refresh your credentials. |
Search
Executes an Analytics or Basic query on analytics tables and custom tables in Microsoft Sentinel. Note: The default workspace retention time is 30 days for Analytics tables and 8 days for Basic tables.
READER NOTE
Using the latest stable API version to run the commands is recommended. Please refer to Microsoft Sentinel's REST API documentation for the list of stable versions.
This command does not require you to specify the tables to query like the Fetch Event command. Also, the data returned by this command will not be ingested as events in D3 SOAR.
Input
Input Parameter | Required /Optional | Description | Example |
Query | Required | The Kusto query to search for data. For more information about the Kusto Query Language (KQL), see Kusto Query Language (KQL) overview- Azure Data Explorer | Microsoft Learn. | set query_take_max_records=30001; set truncationmaxsize=67108864; SecurityEvent| where EventID == ***| summarize FailedLogins = count() by EventSourceName, IpAddress, Process, ProcessId, ProcessName, bin(TimeGenerated, 10m) |
Time Span | Optional | The range of time for which data from a table should be queried. The input time stamps are separated by "/". The time field used for this is TimeGenerated and the values are in ISO8601 format. This parameter is in addition to any time range specified in the query statement. If no value is provided, the default for basic tables is the past 8 days. | 2022-12-08T18:06:00Z/2022-12-08T18:10:00Z |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Search failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Microsoft Sentinel portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The provided authentication is not valid for this resource. |
Error Sample Data Search failed. Status Code: 403. Message: The provided authentication is not valid for this resource. |
Update Incident Comments
Updates the comments of specified incidents in Microsoft Sentinel. Please note, only the user that created the comment is allowed to edit it.
READER NOTE
Incident IDs is a required parameter to run this command.
You should already have your desired Incident IDs on hand to run this command. If you don't, you may use the Fetch Incidents command with defined filters to retrieve the desired Incident IDs. The Incident IDs can be found in the raw data at the path $.values[*].name.
Using the latest stable API version to run the commands is recommended. Please refer to Microsoft Sentinel's REST API documentation for the list of stable versions.
Input
Input Parameter | Required /Optional | Description | Example |
Incident IDs | Required | The IDs of the incidents to update comments. Incident IDs can be obtained using the Fetch Incident command. | ["********************"] |
Comment | Required | The contents of the updated comment. | Closed |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Incident Comments failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Microsoft Sentinel portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The client xxxxxx with object id xxxxxx does not have authorization to perform action 'Microsoft.SecurityInsights/incidents/comments/write' over scope xxxxxx or the scope is invalid. If access was recently granted, please refresh your credentials. |
Error Sample Data Update Incident Comments failed. Status Code: 401. Message: The client xxxxxx with object id xxxxxx does not have authorization to perform action 'Microsoft.SecurityInsights/incidents/comments/write' over scope xxxxxx or the scope is invalid. If access was recently granted, please refresh your credentials. |
Update Incident Status
Updates the status of the specified incidents in Microsoft Sentinel.
READER NOTE
Incident IDs is a required parameter to run this command.
You should already have your desired Incident IDs on hand to run this command. If you don't, you may use the Fetch Incidents command with defined filters to retrieve the desired Incident IDs. The Incident IDs can be found in the raw data at the path $.values[*].name.
Owner is an optional parameter to run this command.
To view a complete list of users, run the Microsoft Entra ID Protection integration's List Users command. You can also navigate to Users in Microsoft Azure to view the list of users.
Using the latest stable API version to run the commands is recommended. Please refer to Microsoft Sentinel's REST API documentation for the list of stable versions.
Input
Input Parameter | Required /Optional | Description | Example |
Incident IDs | Required | The IDs of the incidents to update comments. Incident IDs can be obtained using the Fetch Incident command. | ["*****"***************] |
Status | Required | The updated status of the specified incident(s). | Closed |
Title | Optional | The updated title of the specified incident(s). | This is a test |
Severity | Optional | The updated severity of the specified incident(s). | Informational |
Incident Classification | Optional | The reason for closing the incident(s). Note: This parameter is only required when you set the status of the incident(s) to Closed. If you want to change the incident status to New or Active, do not define this parameter. | Benign Positive |
Incident Classification Reason | Optional | The classification reason for closing the incident(s). Note: This parameter is only required when you set the status of the incident(s) to Closed. If you want to change the incident status to New or Active, do not define this parameter. | Suspicious But Expected |
Owner | Optional | The updated user that the incident(s) are assigned to. Valid user principal names can be obtained using the Microsoft Entra ID Protection integration's List Users command. You can also navigate to Users in Microsoft Azure to view the list of users. | *****@*****.com |
Close Comment | Optional | The option to leave a comment to justify the classification when closing the incident. Note: This parameter is only available when you set the Status parameter to Closed. | Keep Watching One more week! |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Incident Status failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Microsoft Sentinel portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The client xxxxxx with object id xxxxxx does not have authorization to perform action 'Microsoft.SecurityInsights/incidents/comments/write' over scope xxxxxx or the scope is invalid. If access was recently granted, please refresh your credentials. |
Error Sample Data Update Incident Status failed. Status Code: 401. Message: The client xxxxxx with object id xxxxxx does not have authorization to perform action 'Microsoft.SecurityInsights/incidents/comments/write' over scope xxxxxx or the scope is invalid. If access was recently granted, please refresh your credentials. |
Test Connection
Allows you to perform a health check on an integration connection. You can schedule a periodic health check by selecting Connection Health Check when editing an integration connection.
Input
N/A
Output
Output Type | Description | Return Data Type |
Return Data | Indicates one of the possible command execution states: Successful or Failed. The Failed state can be triggered by any of the following errors:
More details about an error can be viewed in the Error tab. | String |
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Test Connection failed. Failed to check the connector. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Microsoft Sentinel portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The client xxxxxx with object id xxxxxx does not have authorization to perform action 'Microsoft.SecurityInsights/incidents/read' over scope xxxxxx or the scope is invalid. If access was recently granted, please refresh your credentials. |
Error Sample Data Test Connection failed. Failed to check the connector. Status Code: 401. Message: The client xxxxxx with object id xxxxxx does not have authorization to perform action 'Microsoft.SecurityInsights/incidents/read' over scope xxxxxx or the scope is invalid. If access was recently granted, please refresh your credentials. |