Triggers
LAST UPDATED: JAN 7, 2024
Overview
Next-generation playbooks introduce the ability to add and remove triggers as needed, replacing the previous default inclusion of all triggers on the initial playbook node. Additionally, new trigger options have been added to support more varied workflows.
Adding a Trigger
Triggers can now be added individually based on user requirements and preferences.
Adding a Trigger to an Investigation Playbook
READER NOTE
The On Playbook Start trigger is included by default.
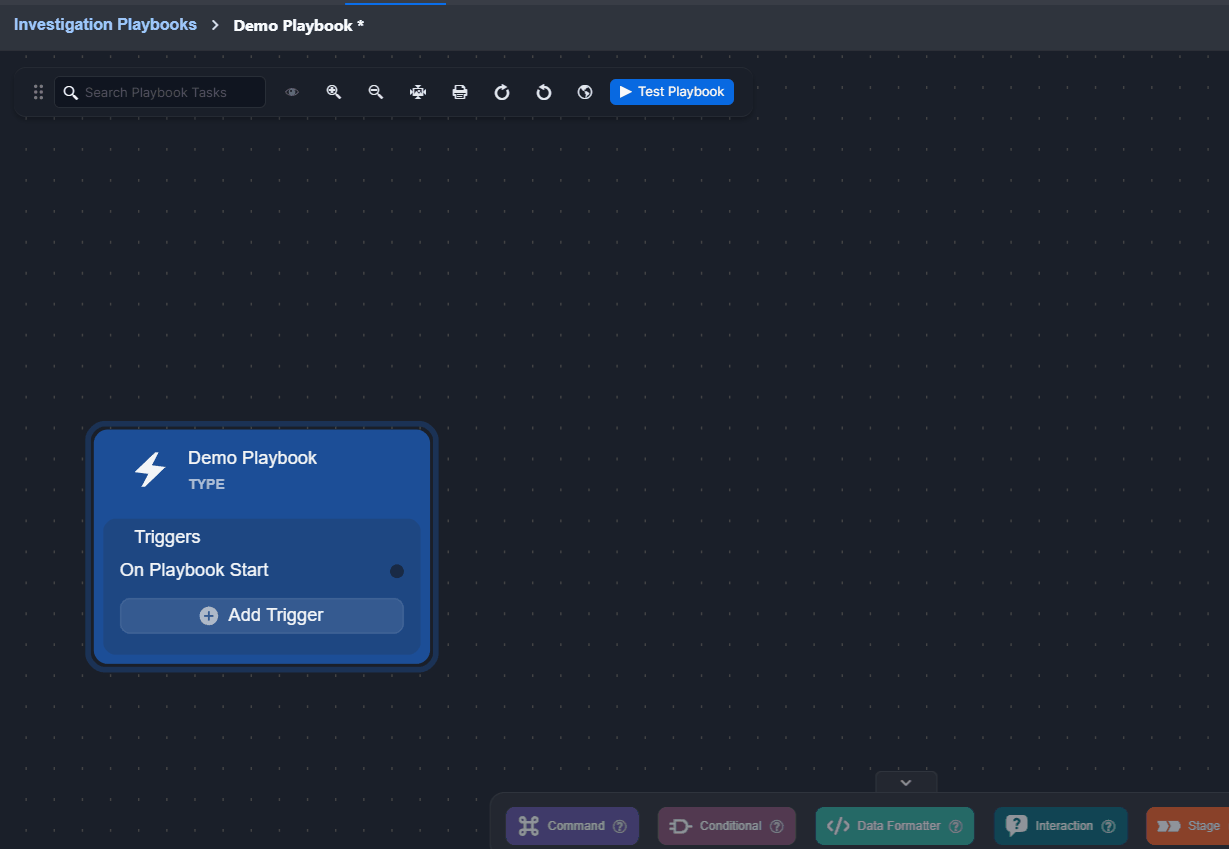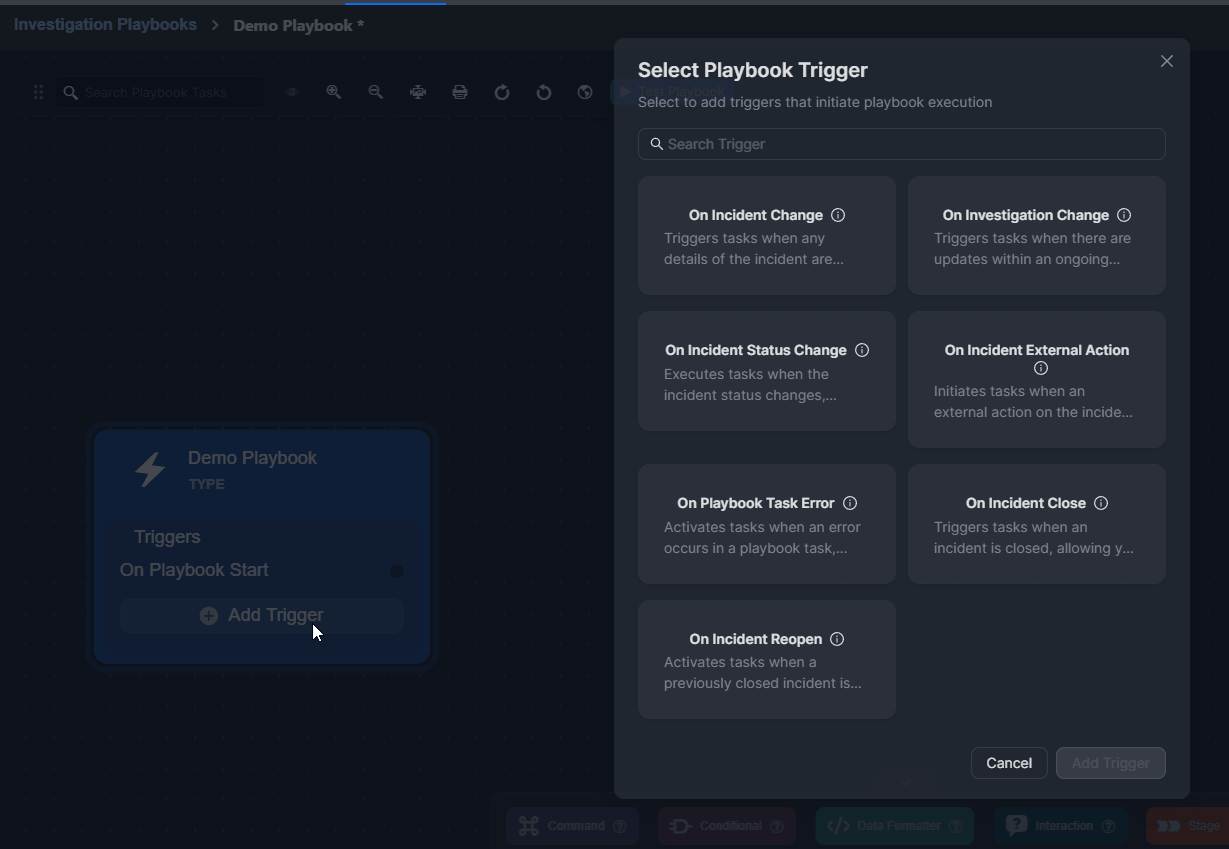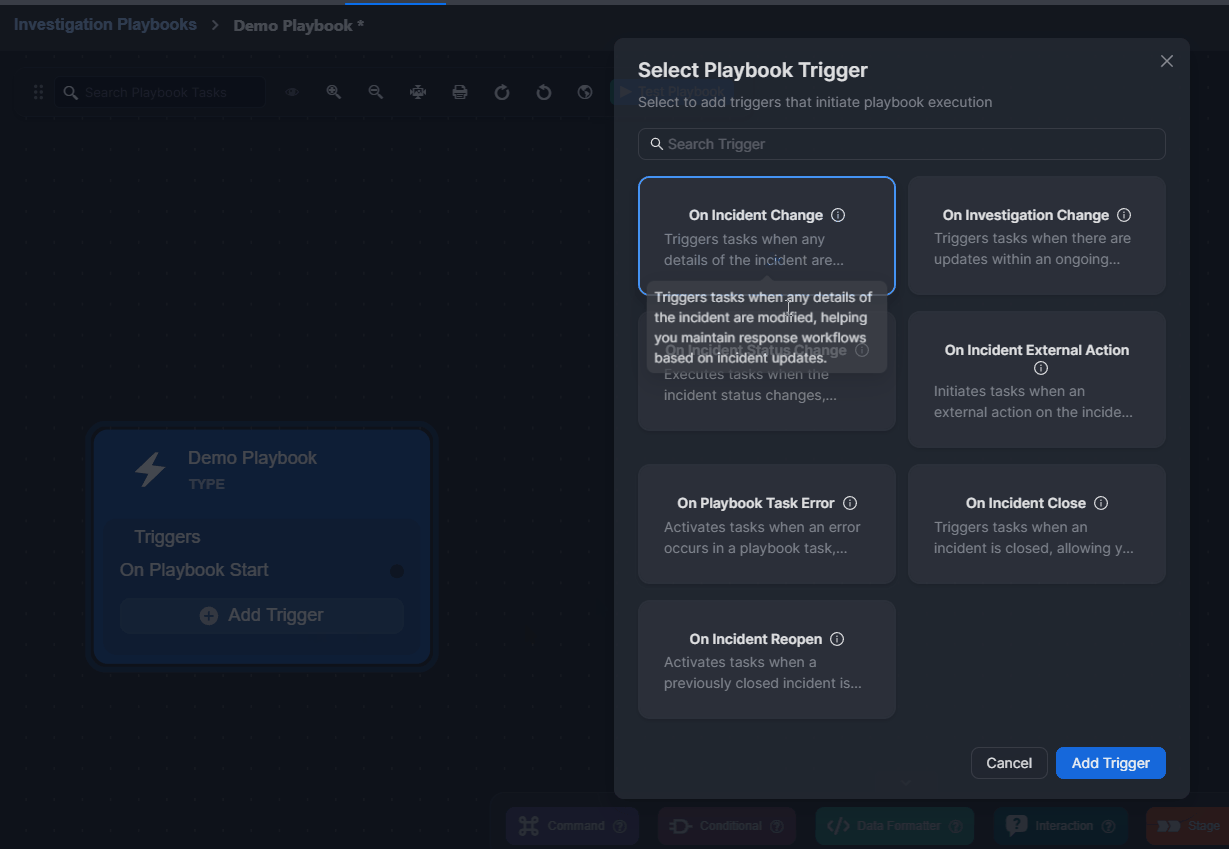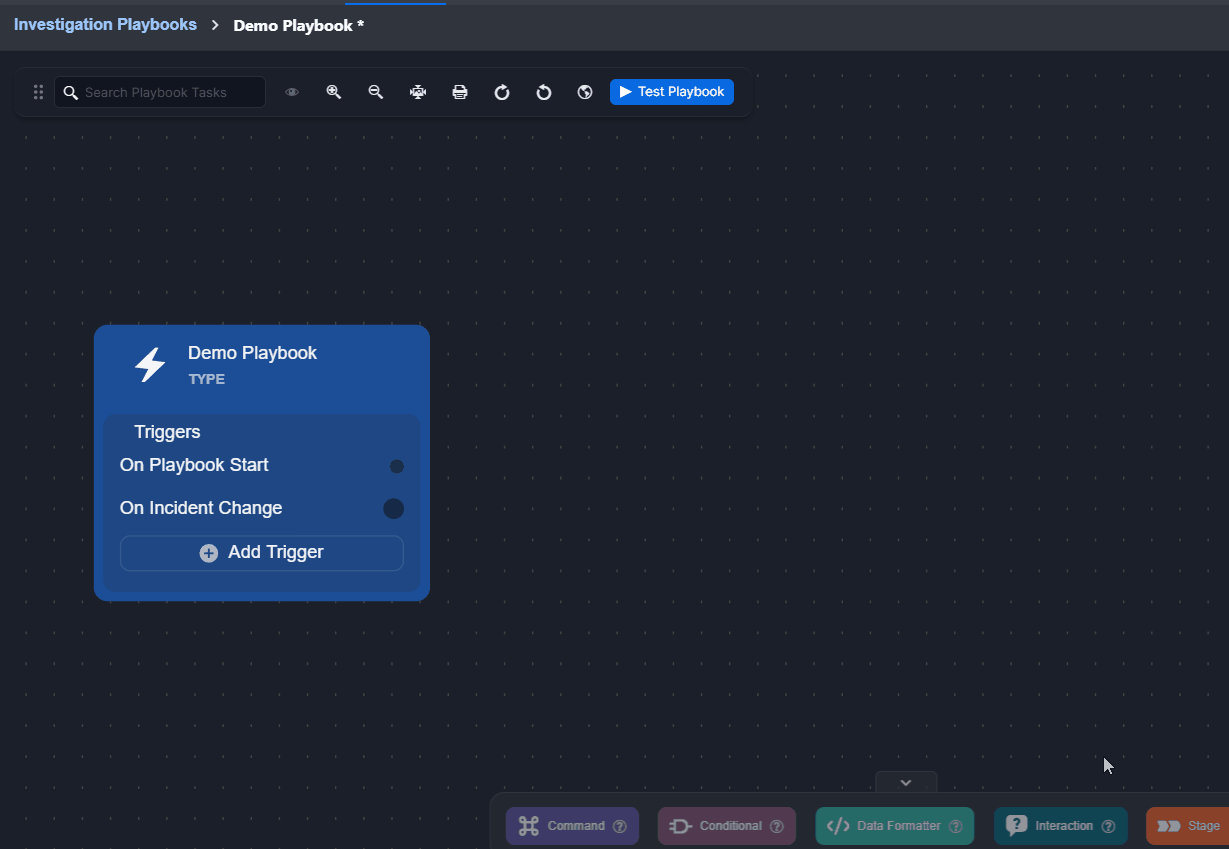
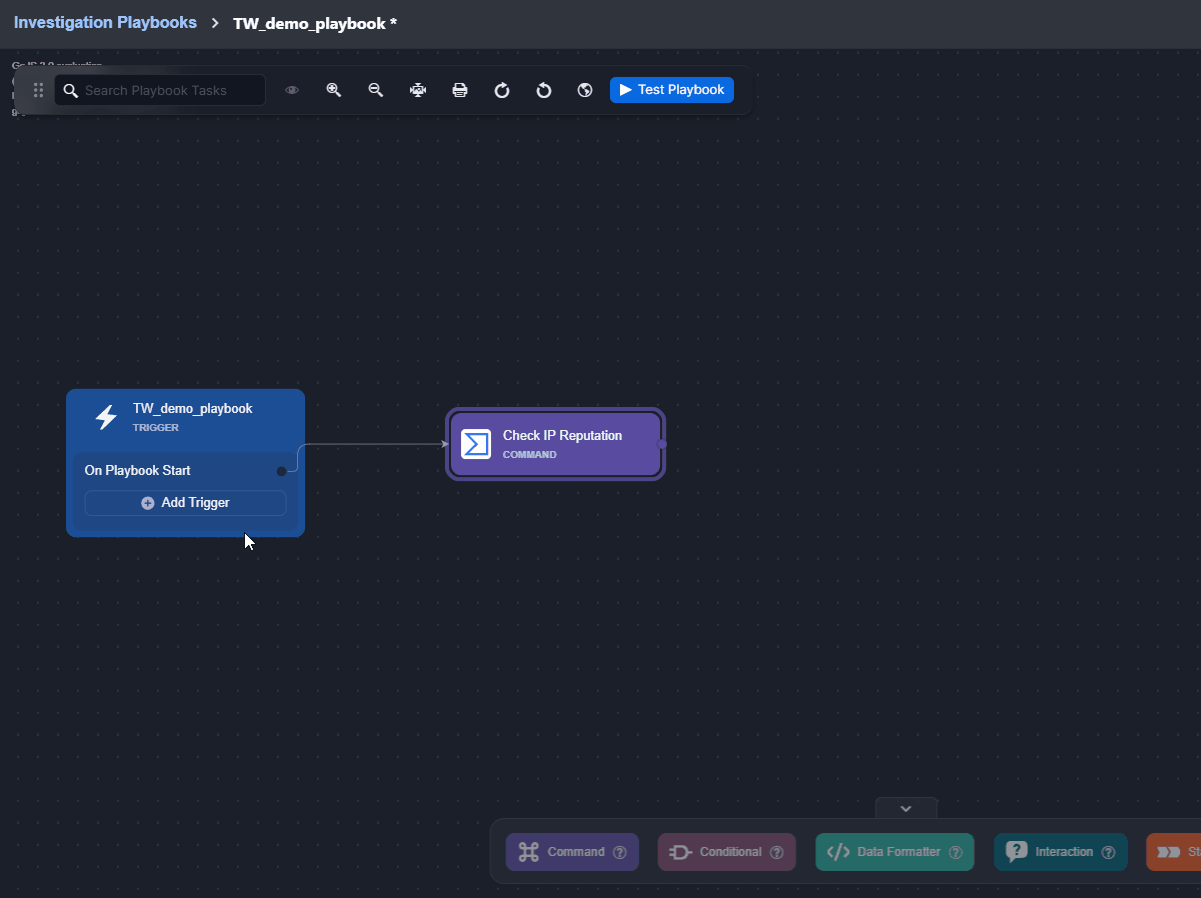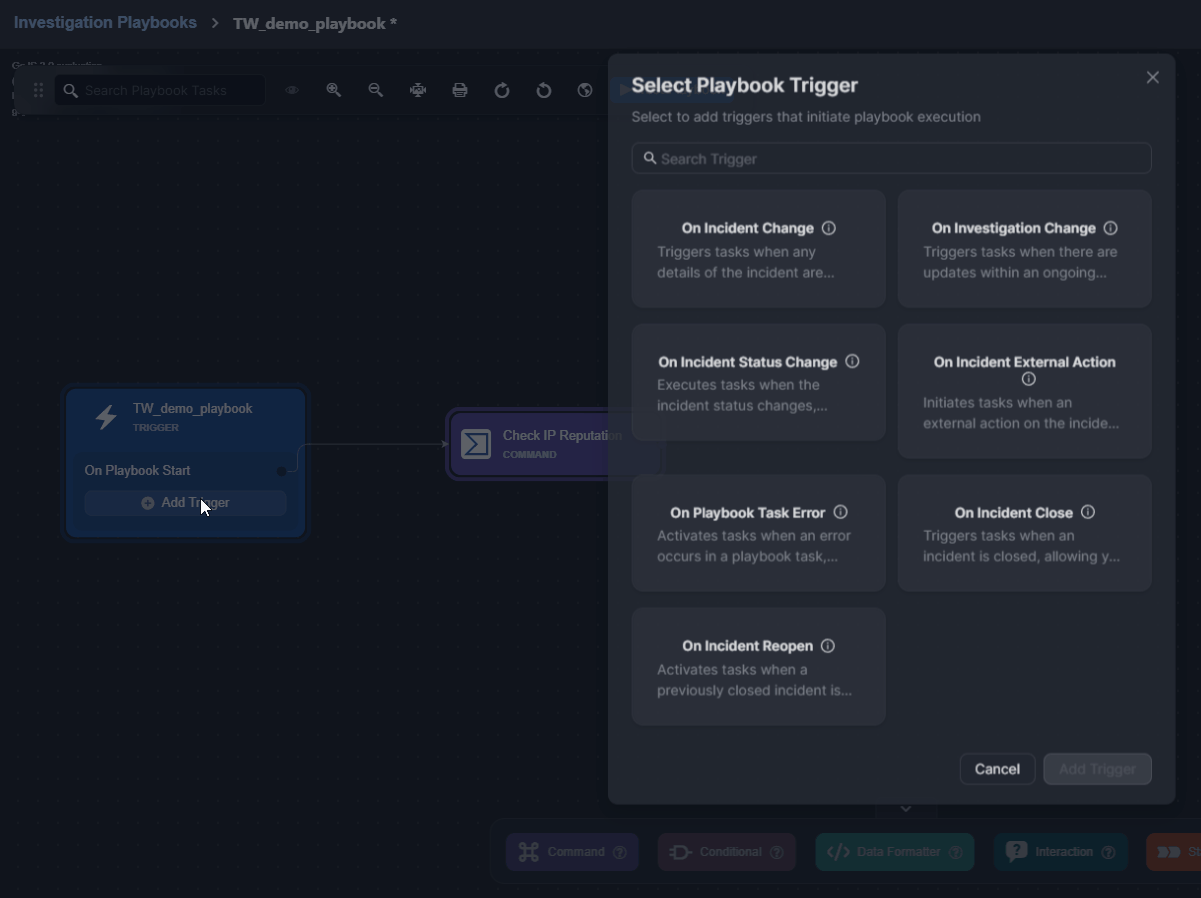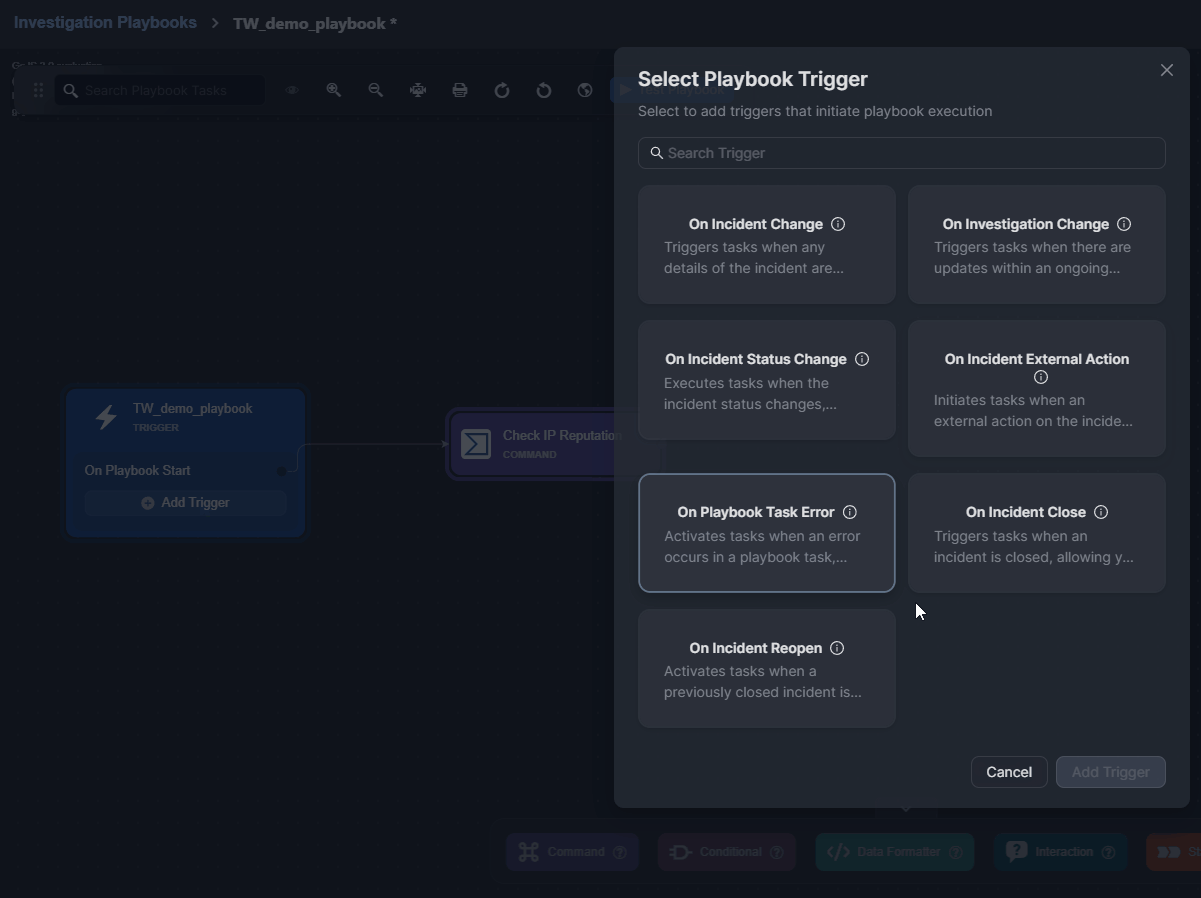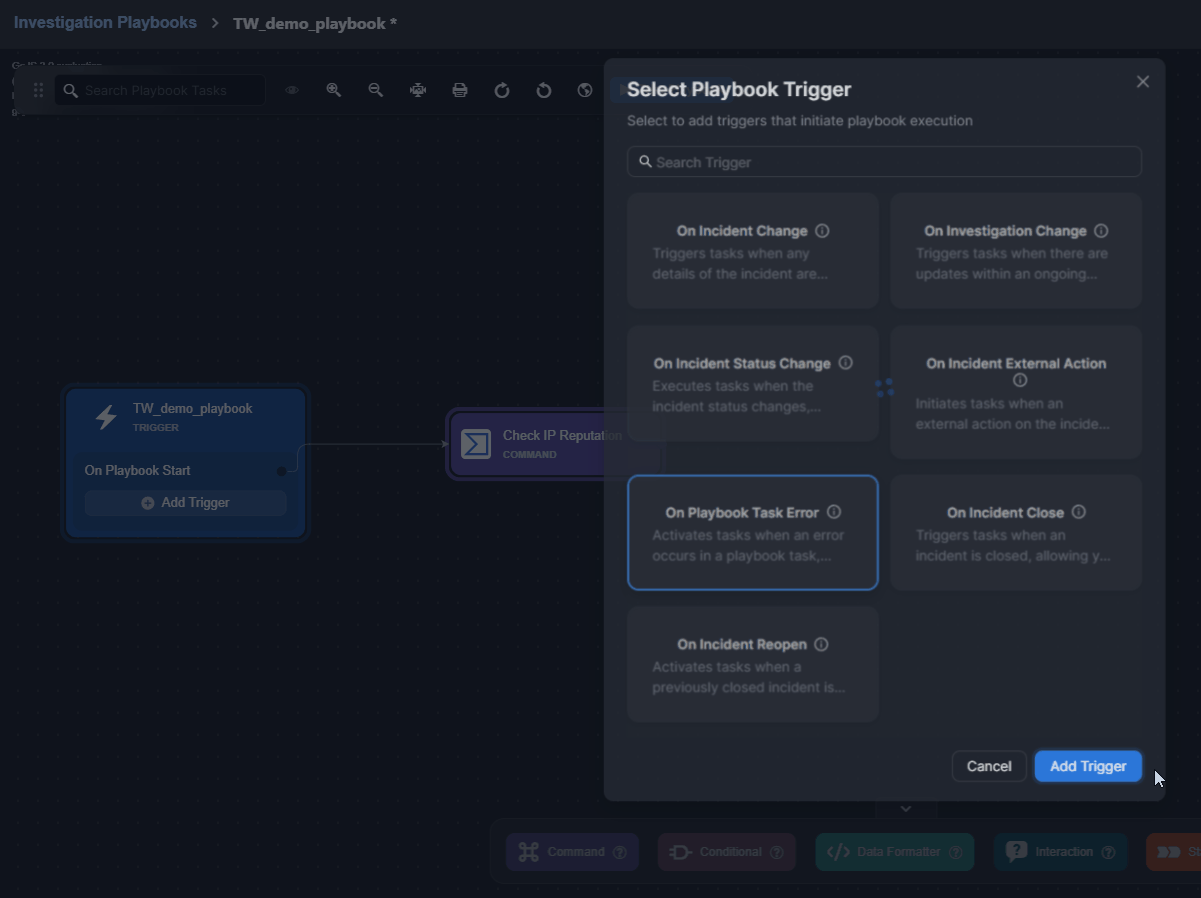
Click on the + Add Trigger button.
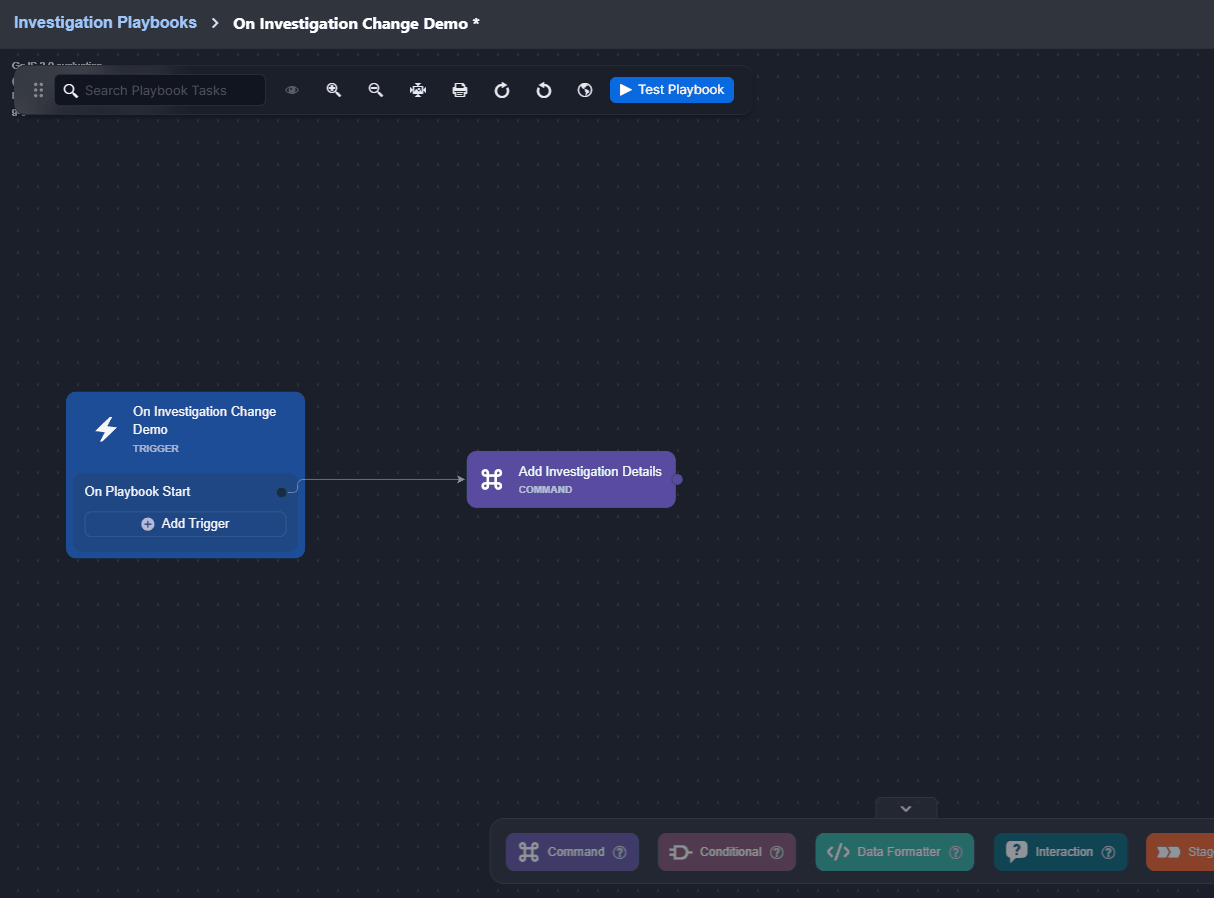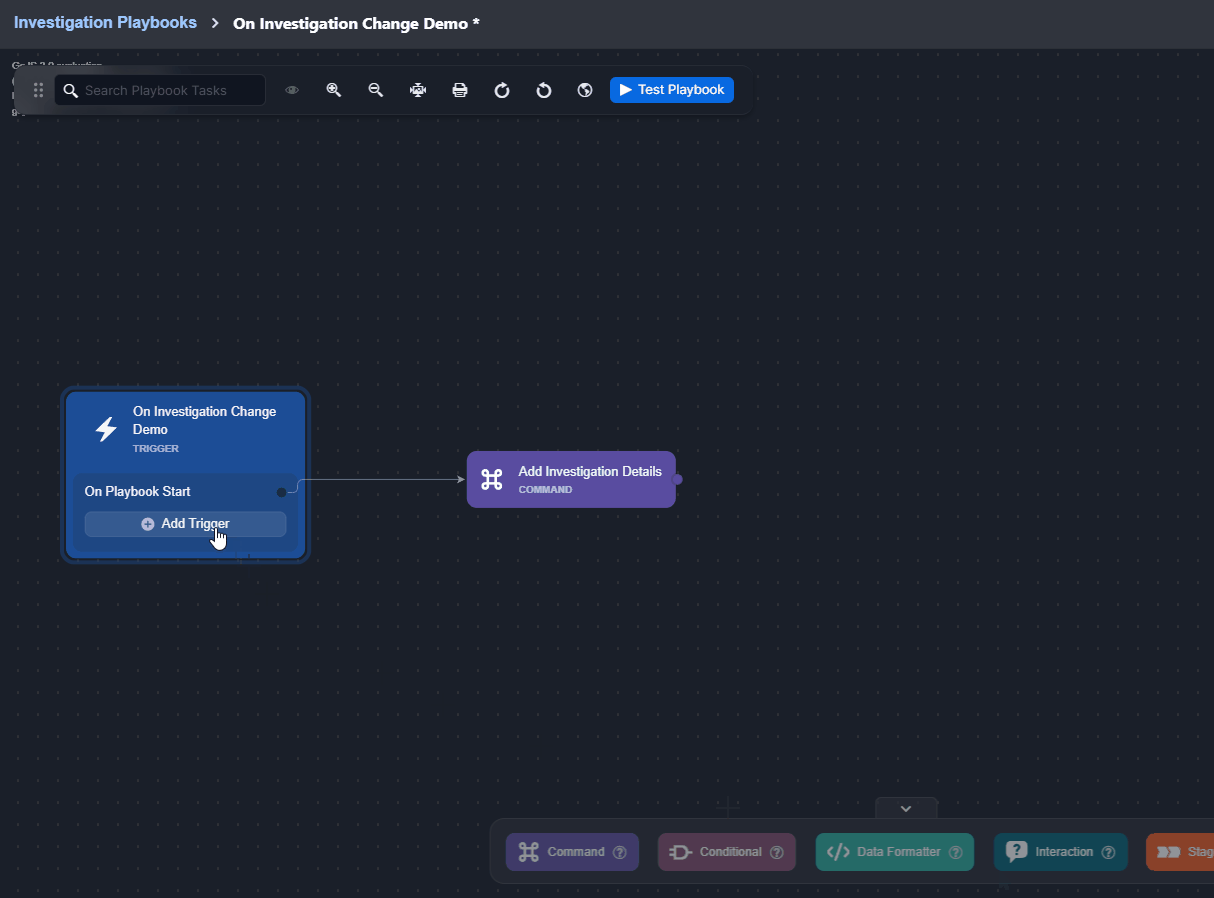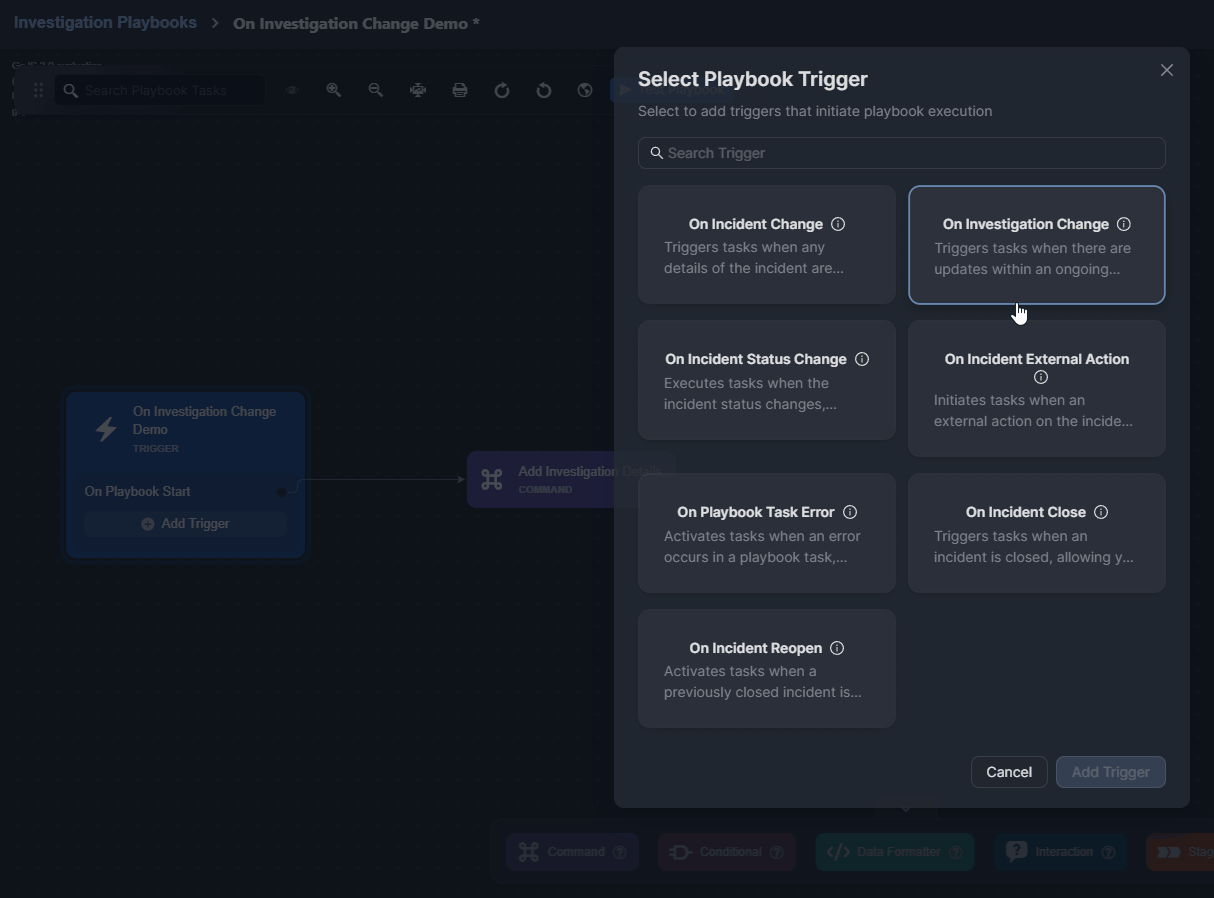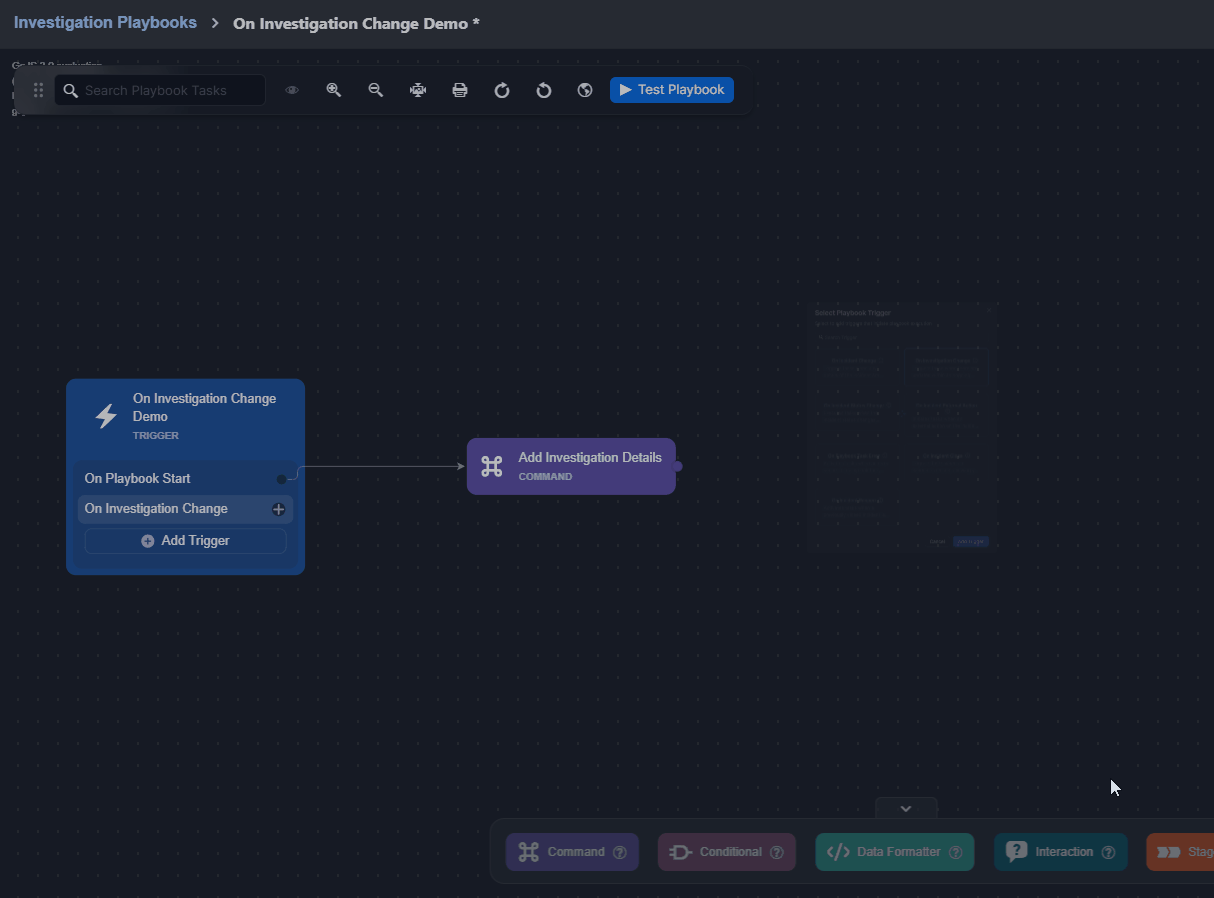
Select a trigger.
Click on the Add Trigger button.
Adding a Trigger to a Preprocessing Playbook
READER NOTE
The On Event Ingestion trigger is included by default.
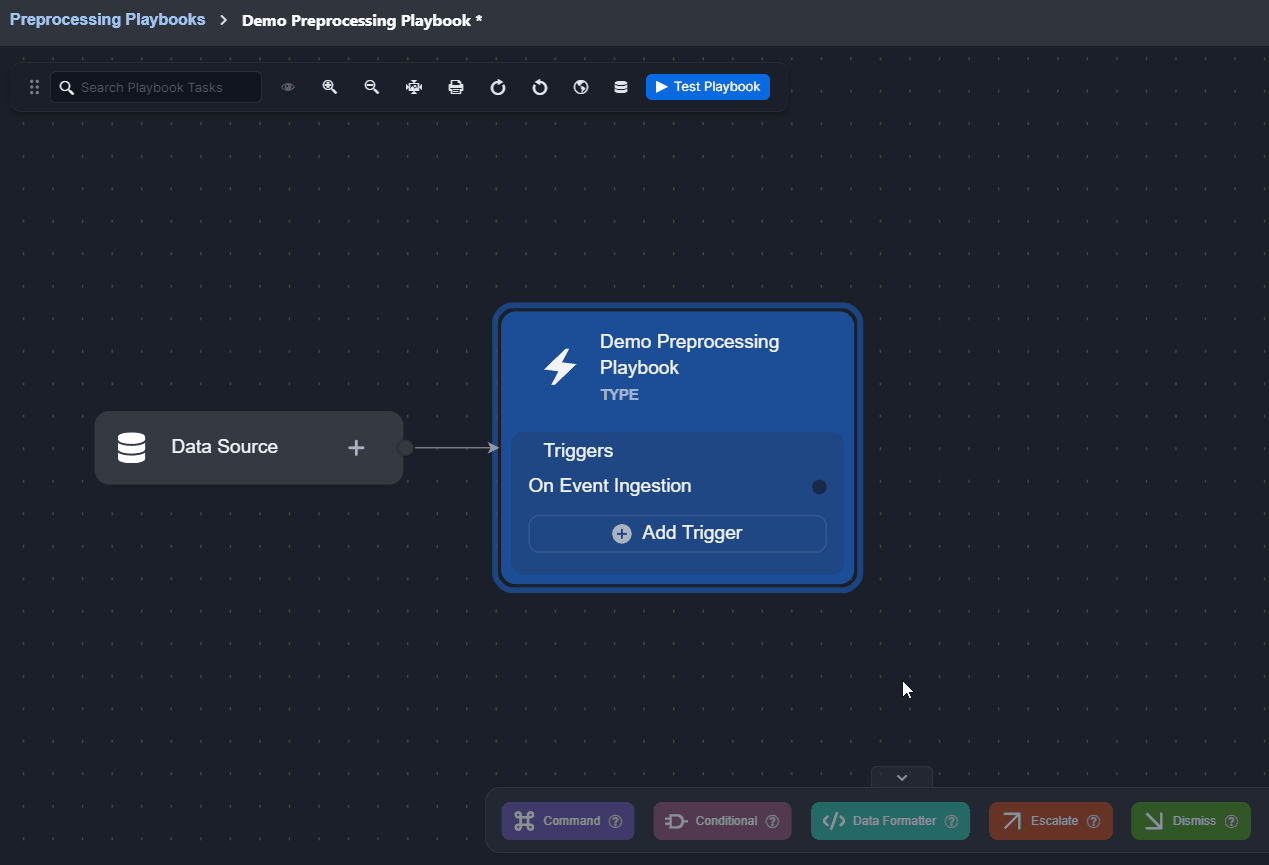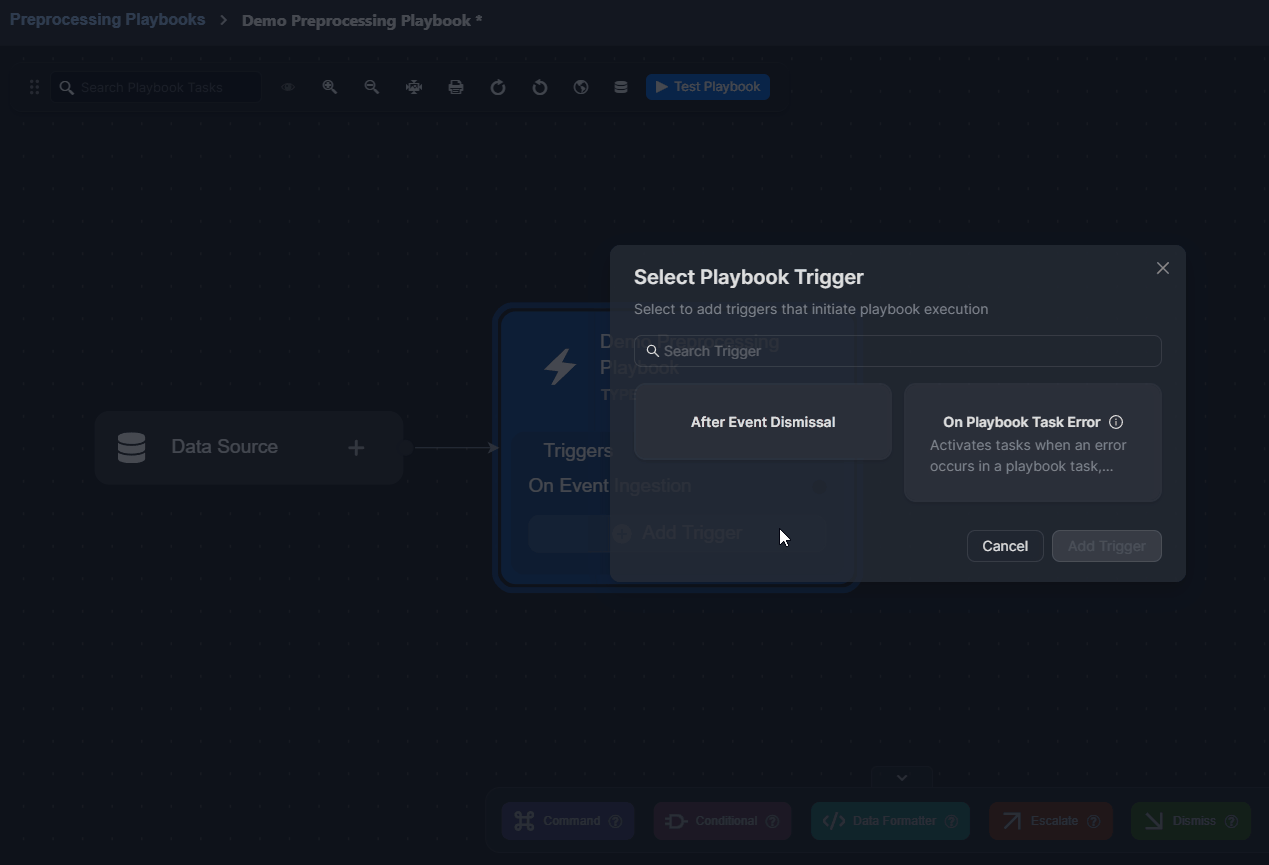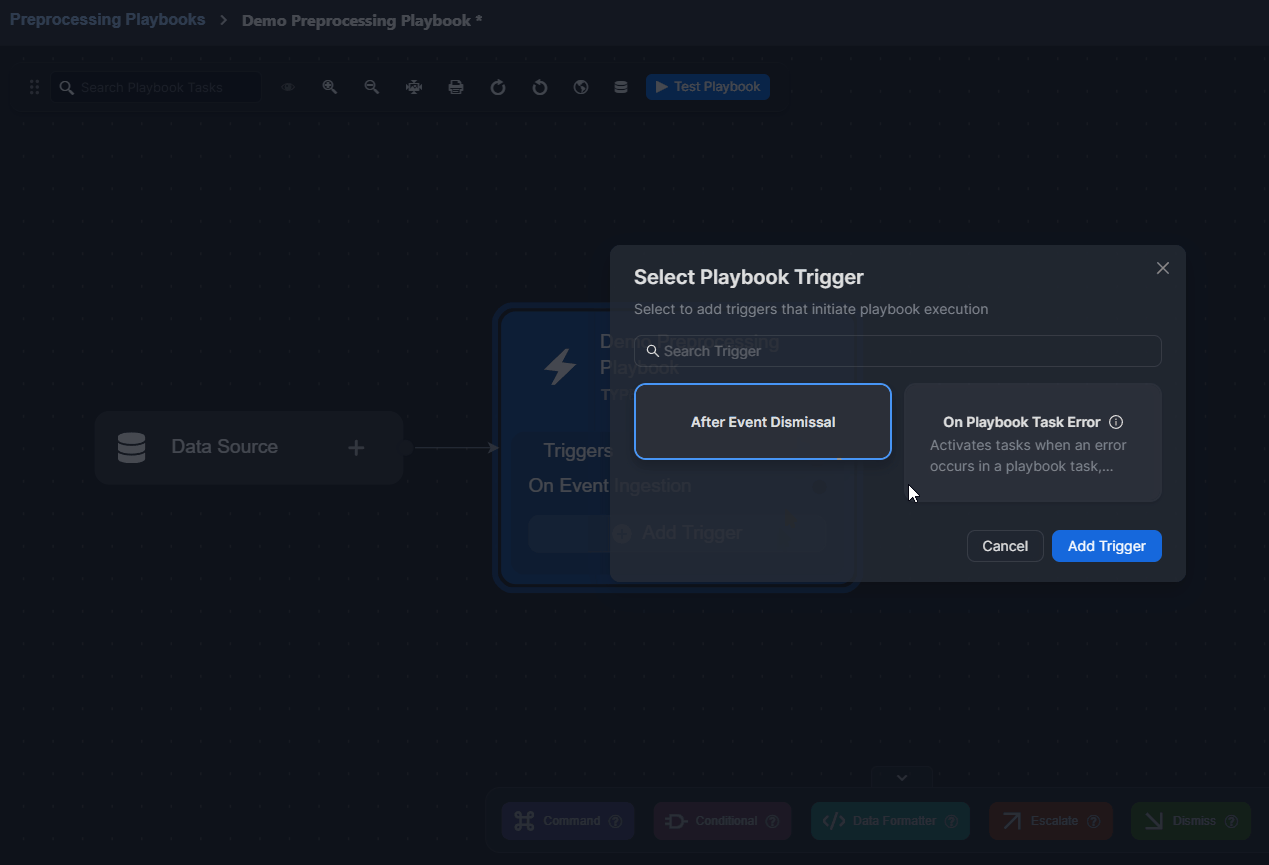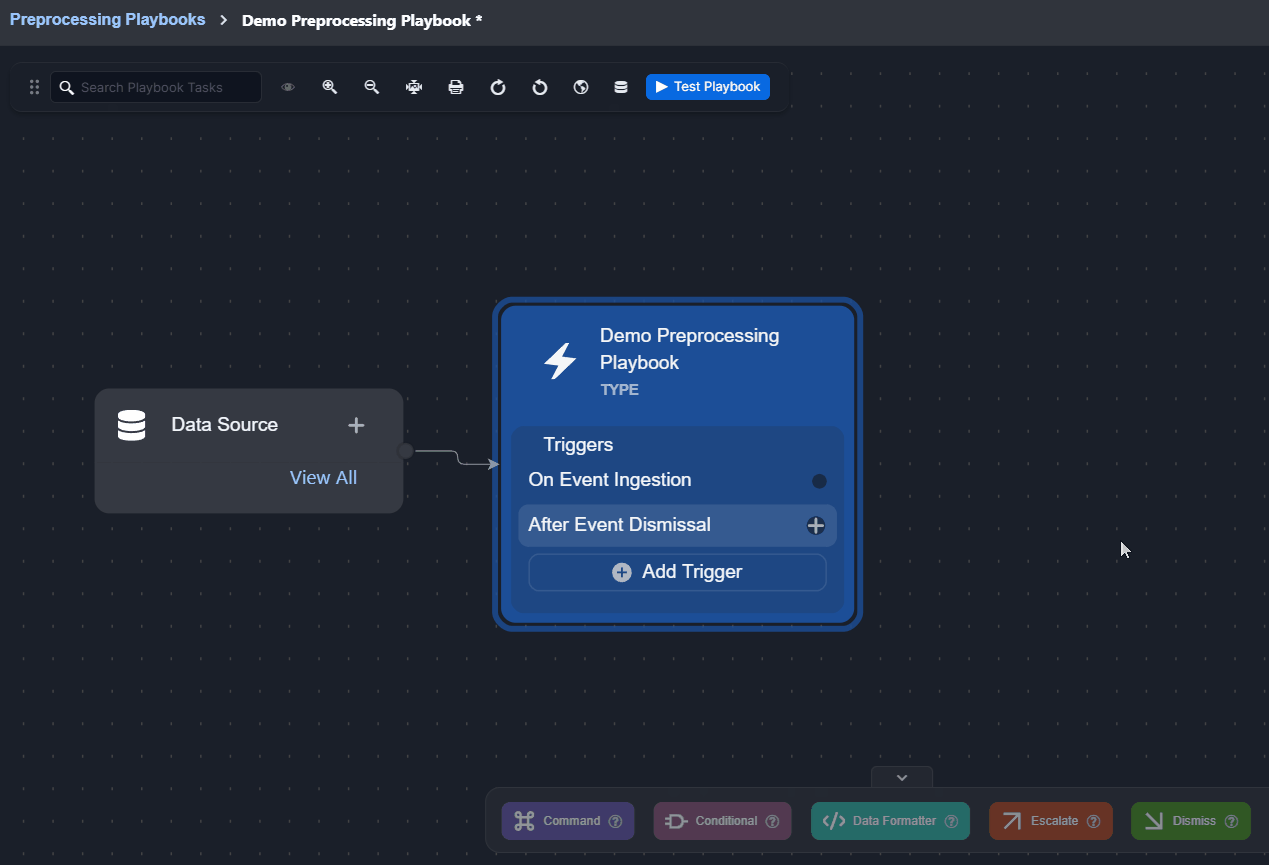
Click on the Add Trigger button.
Select a trigger.
Click on the Add Trigger button.
Deleting a Trigger
For both preprocessing and investigation playbooks, triggers can be deleted using the Delete Trigger button that pops up upon clicking on a trigger.
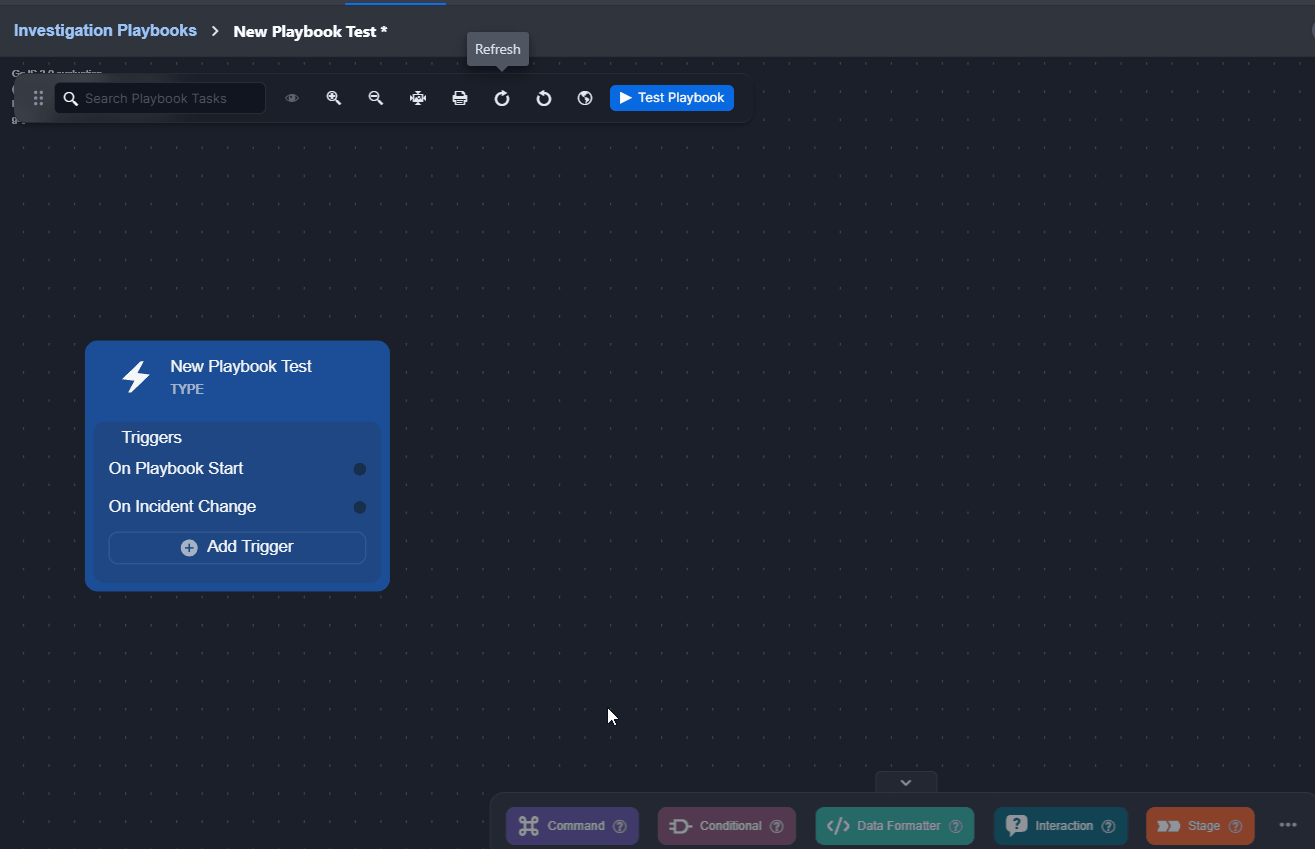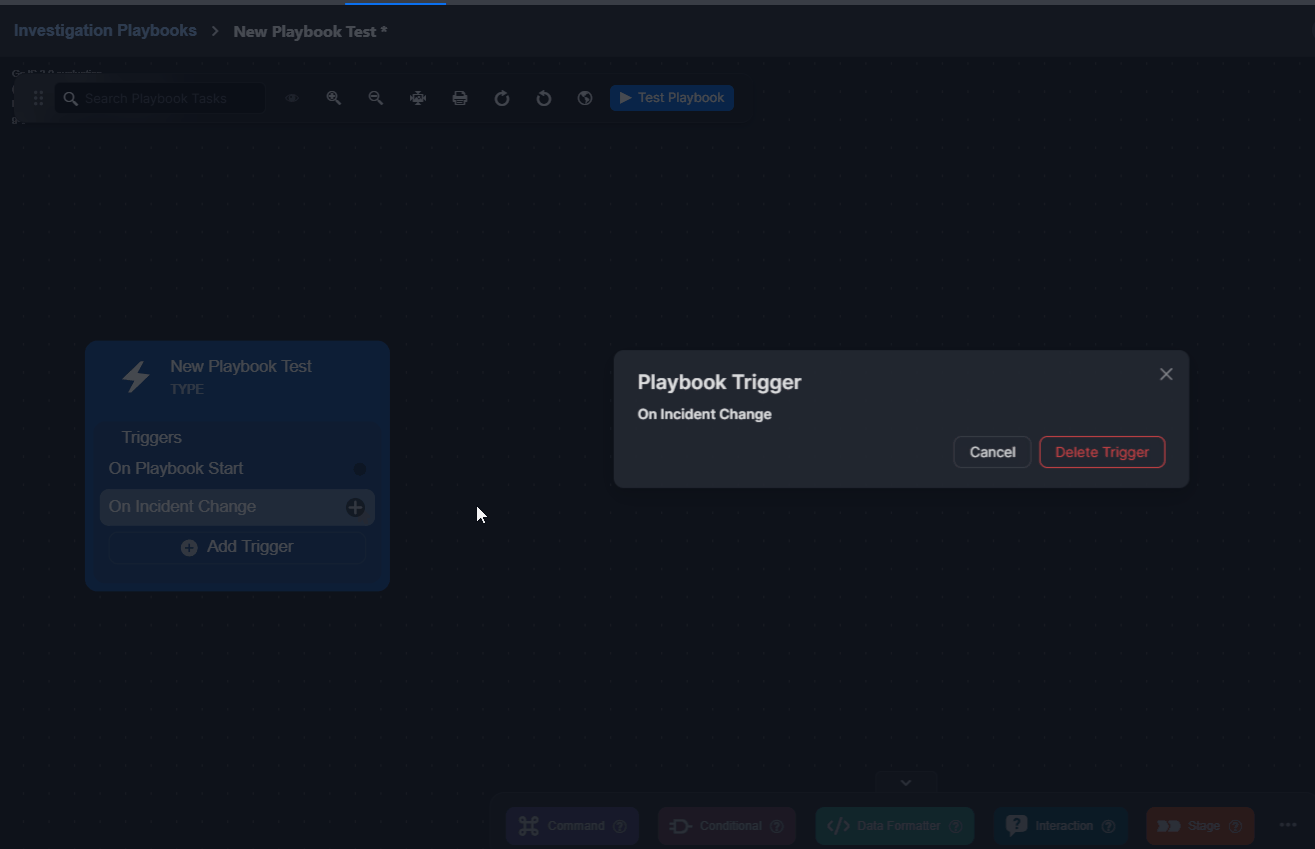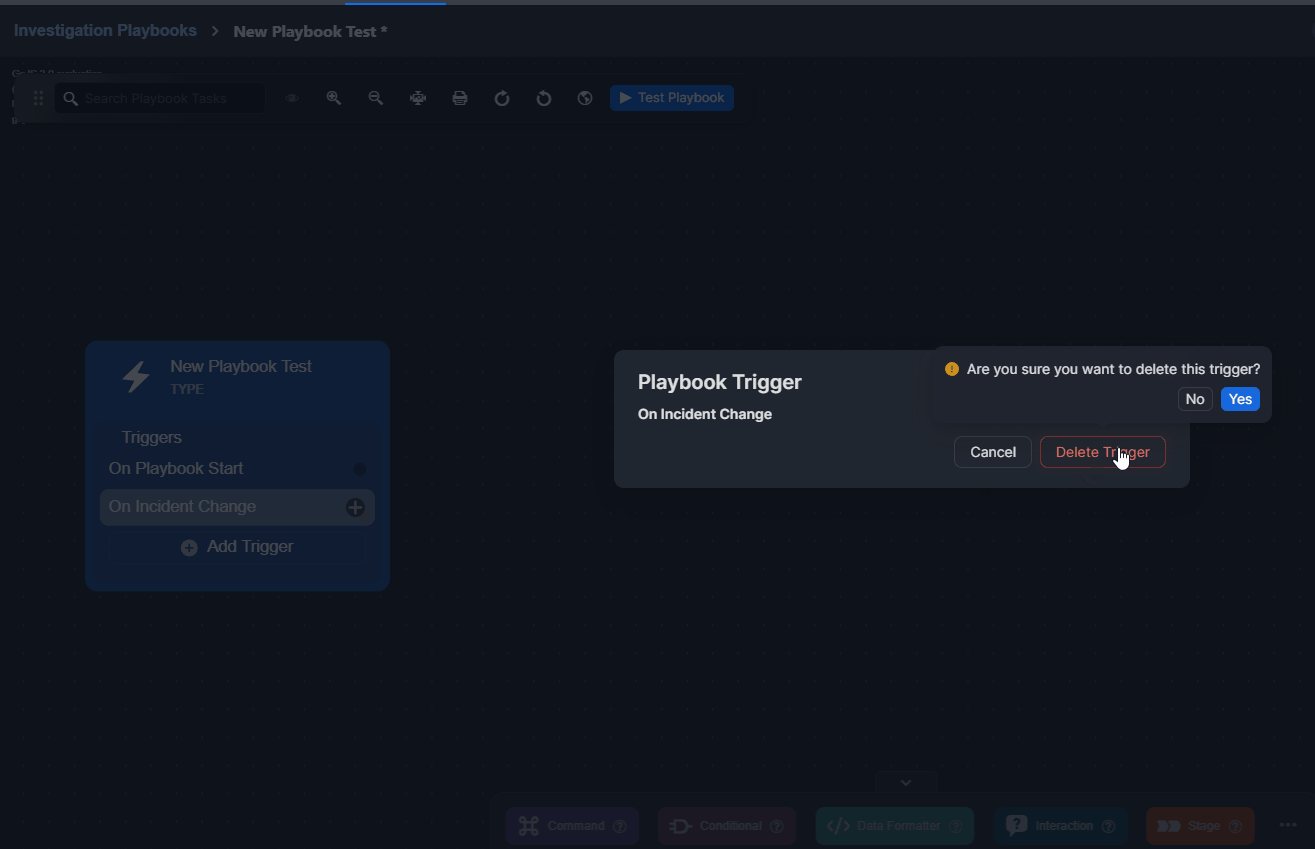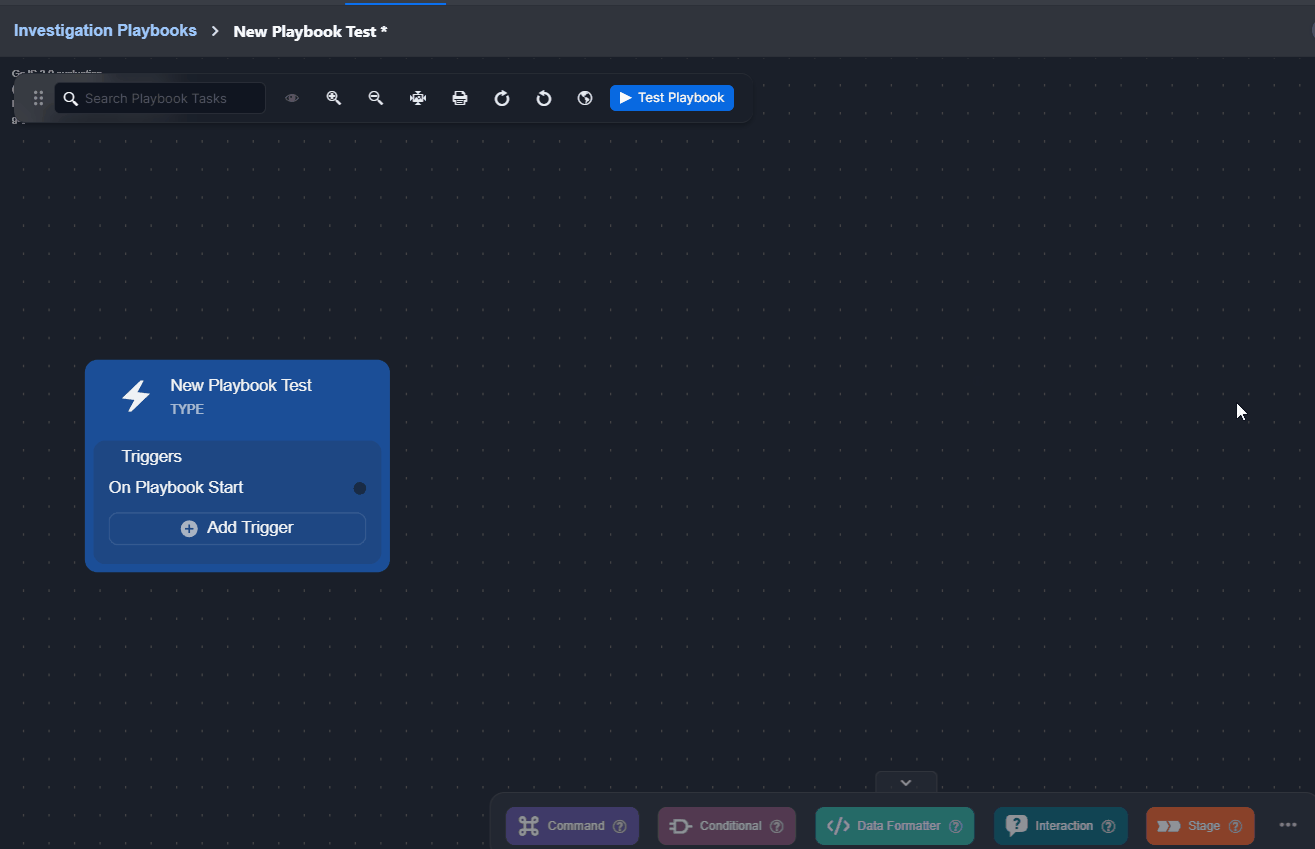
Click on the trigger to delete.
Click on the Delete Trigger button.
Click on the Yes button to confirm deletion.
READER NOTE
Triggers can be deleted unless they are depended by other nodes. In such cases, deletion can be handled in one of two ways:
Delete the dependent node(s) first.
Remove the linking arrow, leaving orphan nodes.
New Triggers
New trigger options have been added to both preprocessing and investigation playbooks, allowing support for more varied workflows.
Investigation Playbooks
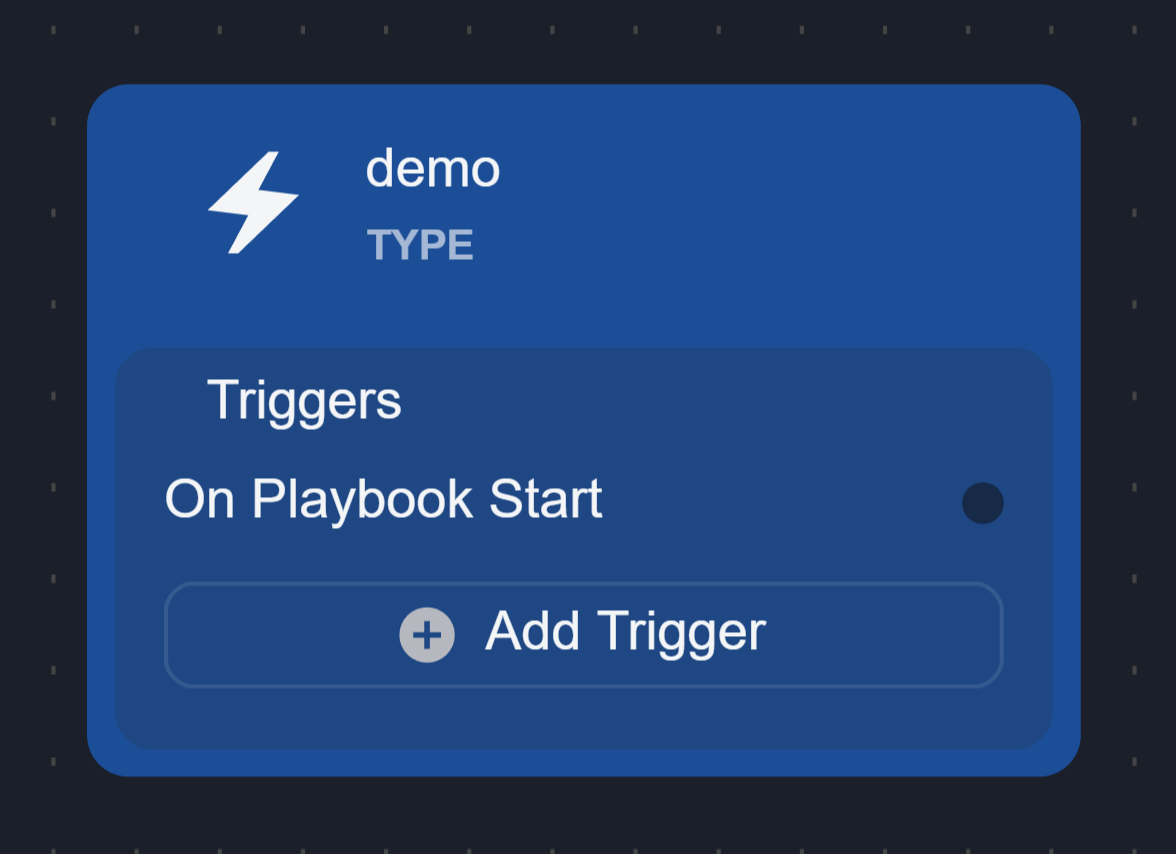
On Playbook Start
All existing playbook nodes previously connected to the header of the root node have been updated to flow from the On Playbook Start trigger node. This is the main workflow of an investigation playbook.
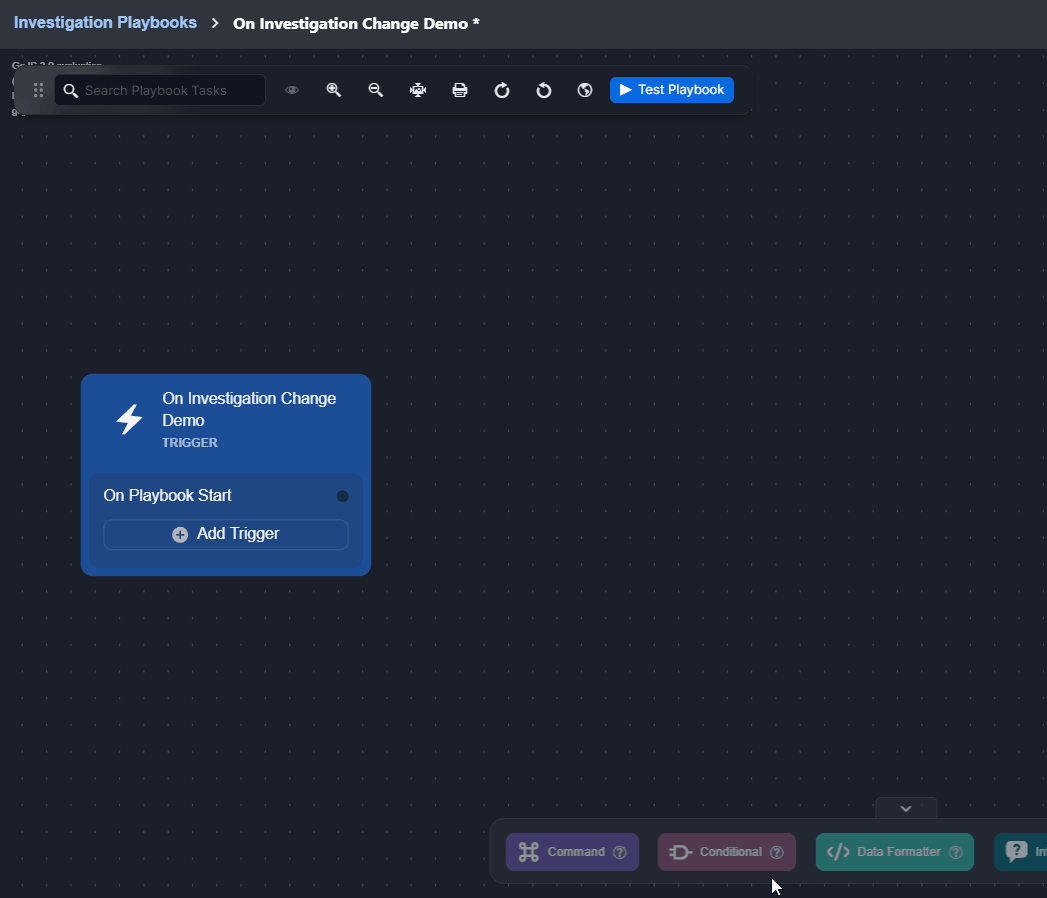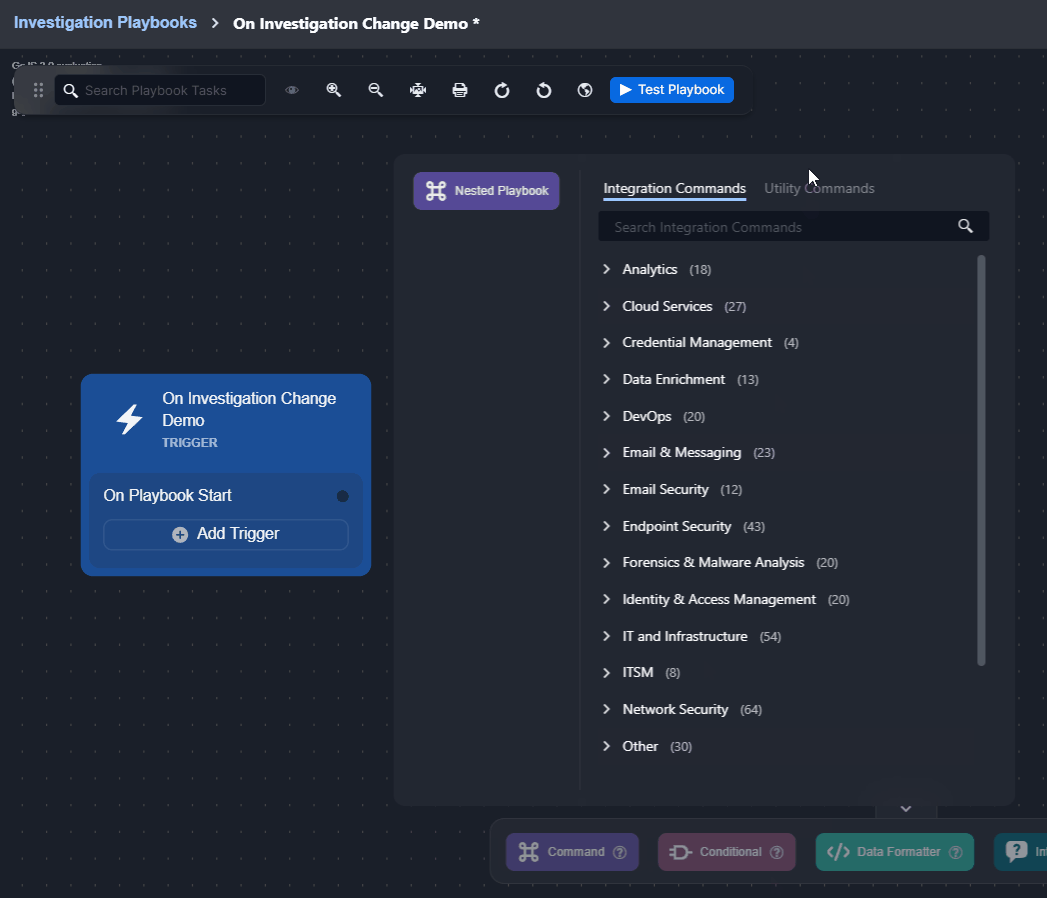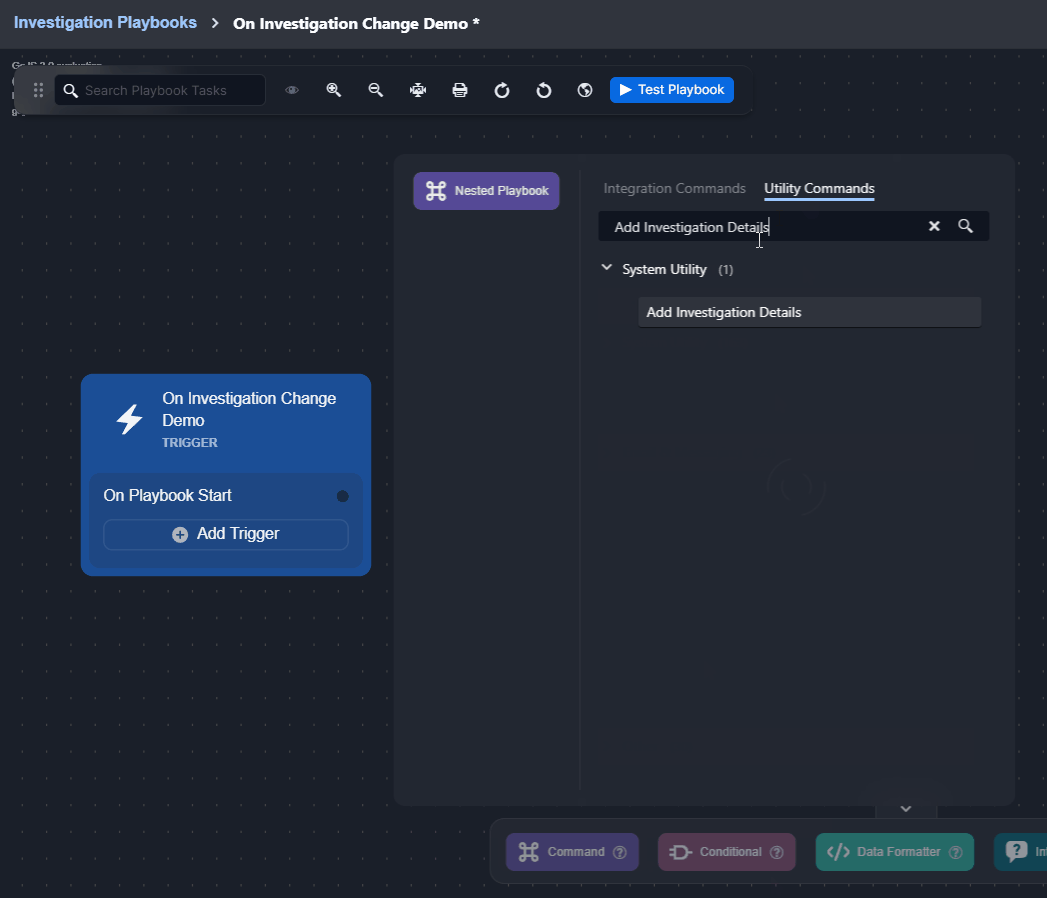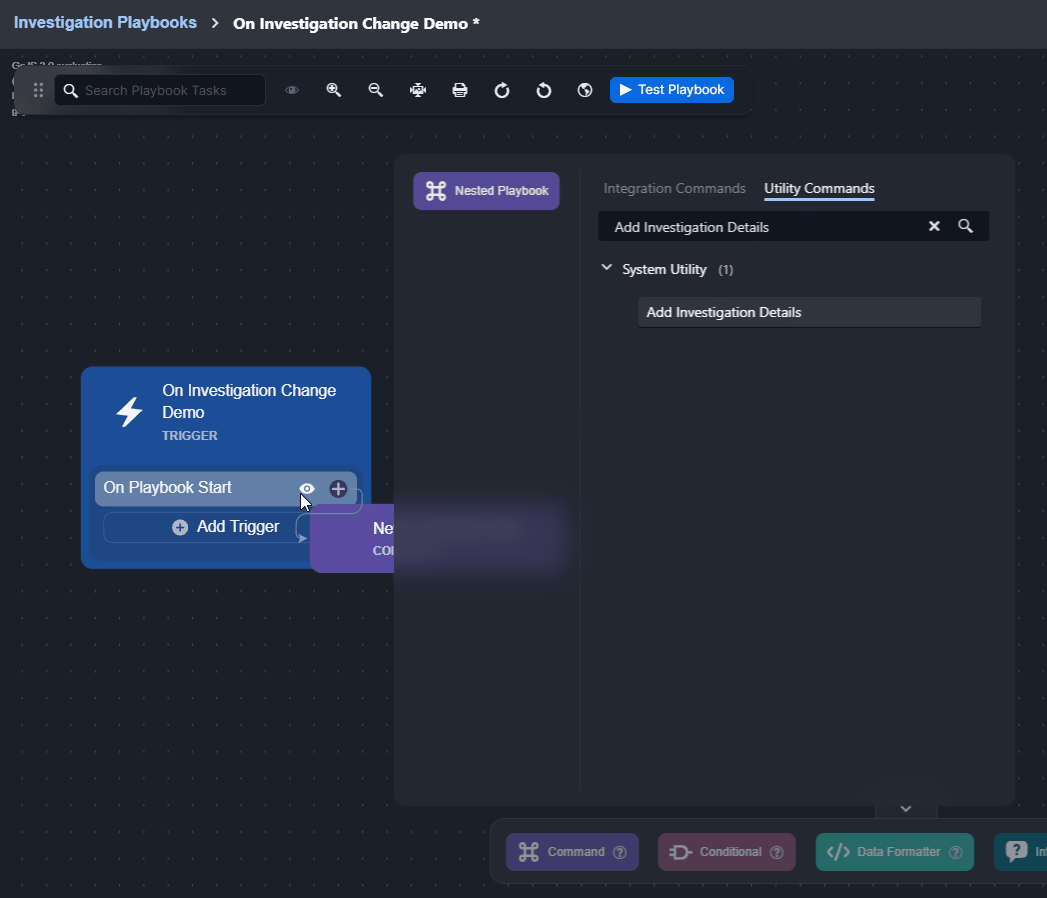
On Investigation Change
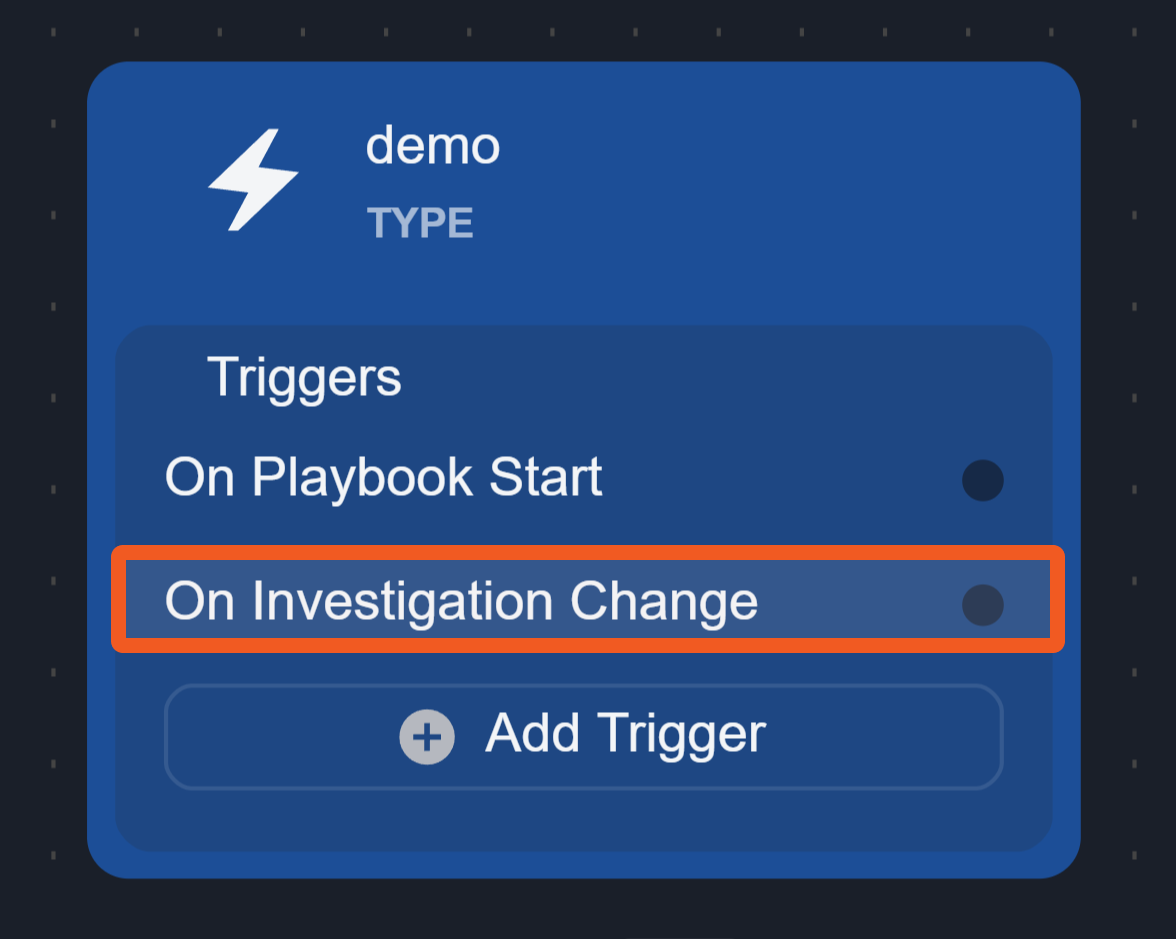
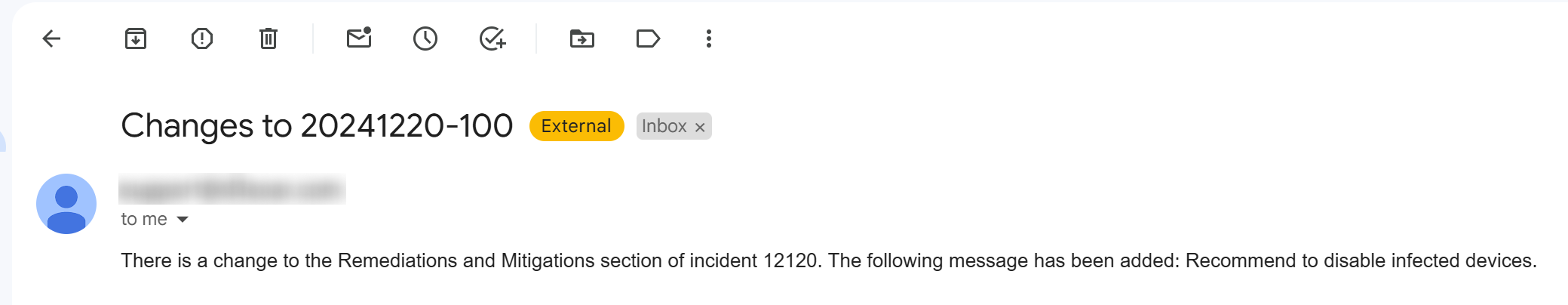
This trigger activates linked tasks when data in the Investigation tab of the Incident Workspace changes.
Data in the Investigation tab of the incident workspace can be updated manually or through a utility command.
Manual Updates | |
Updates are made using the buttons. | 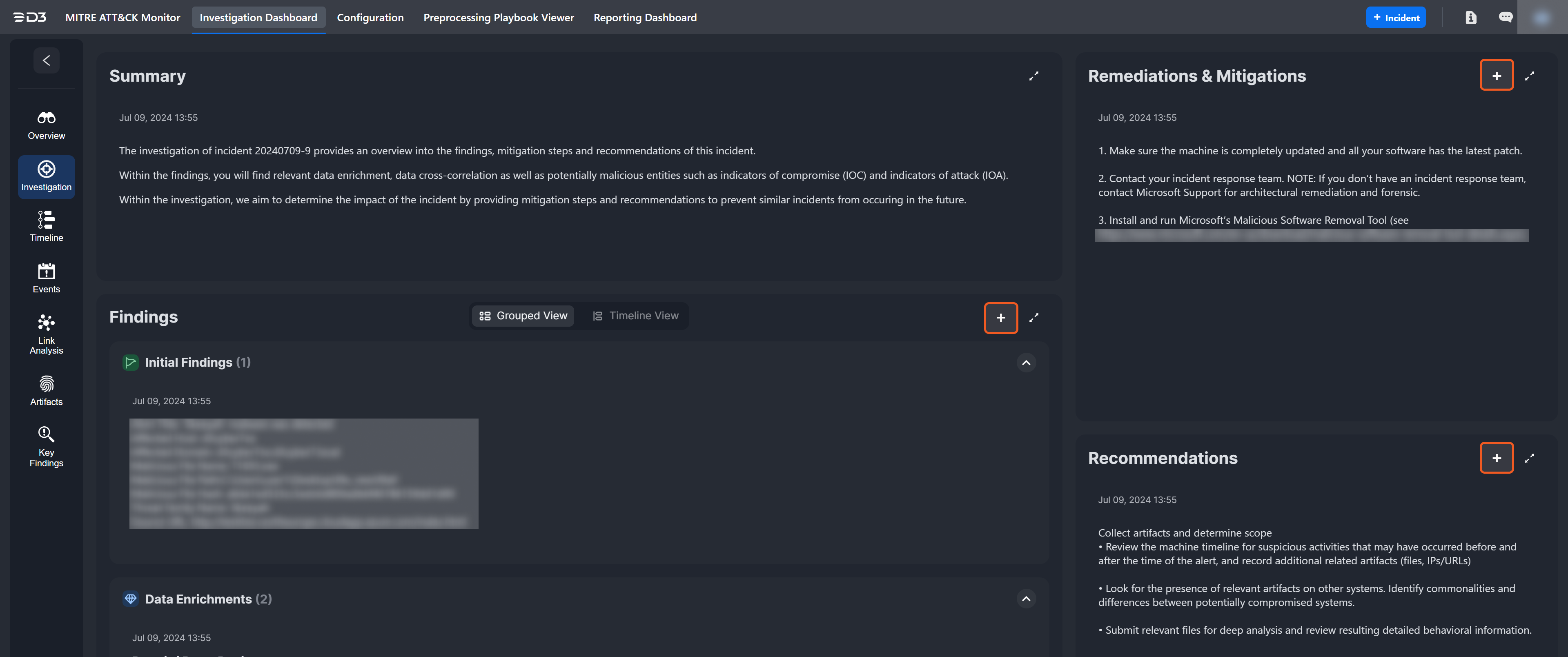 |
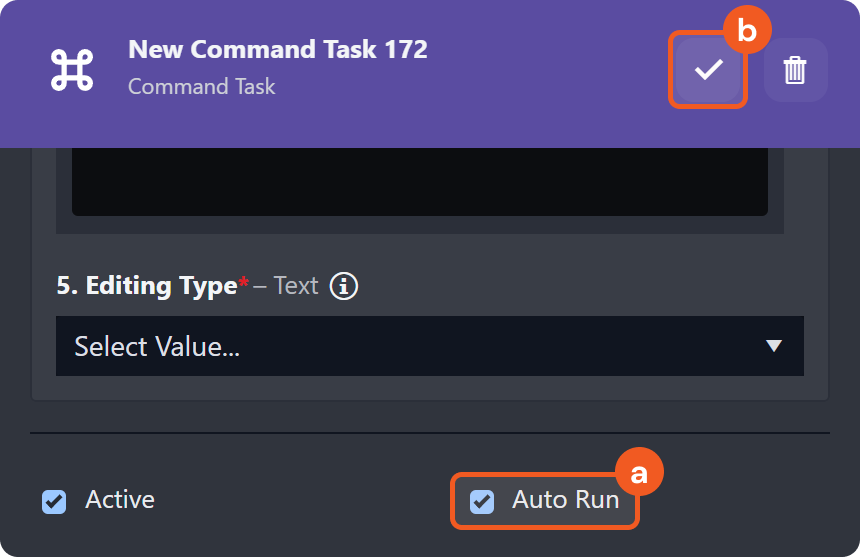
Edits to the investigation summary can be made by clicking on the | 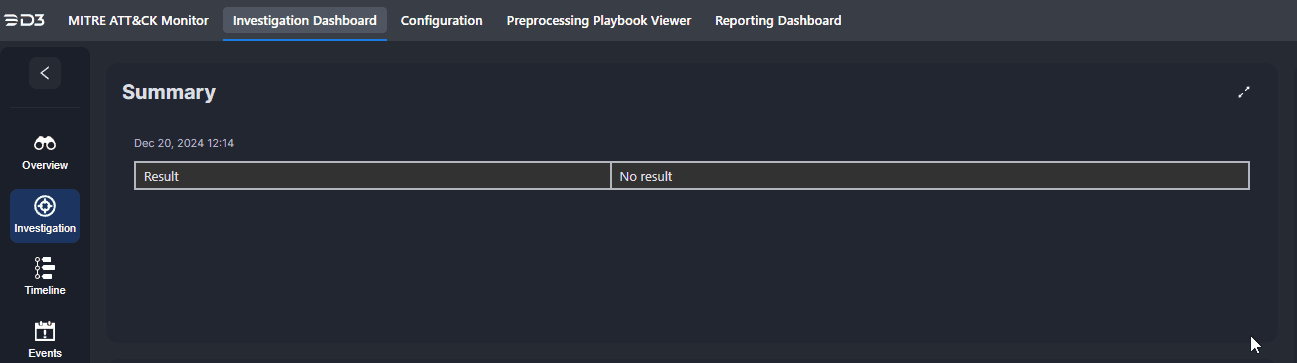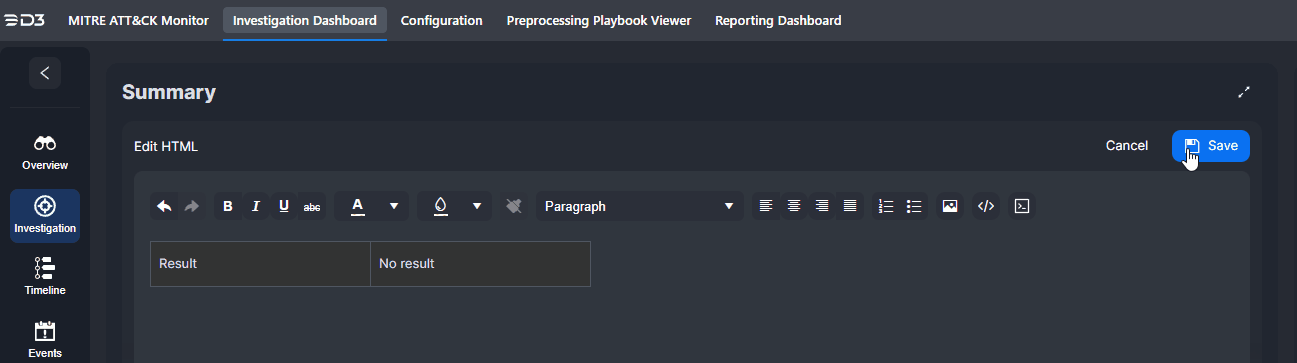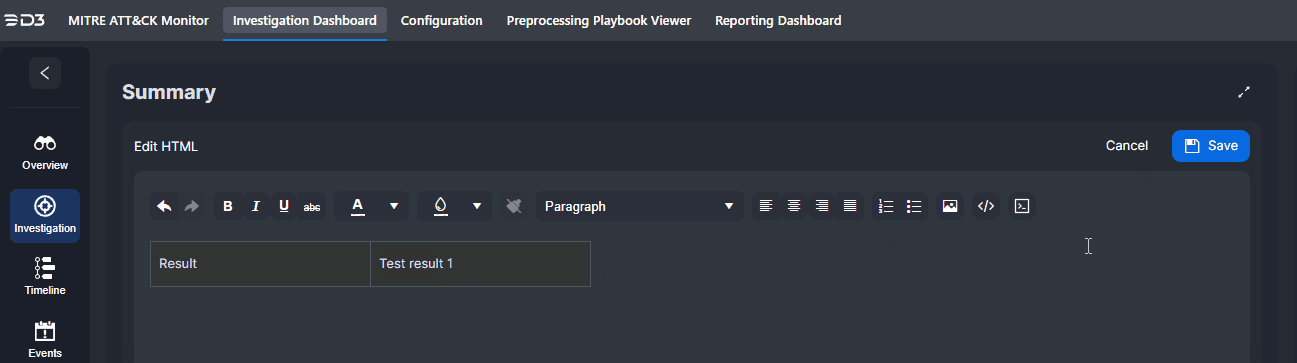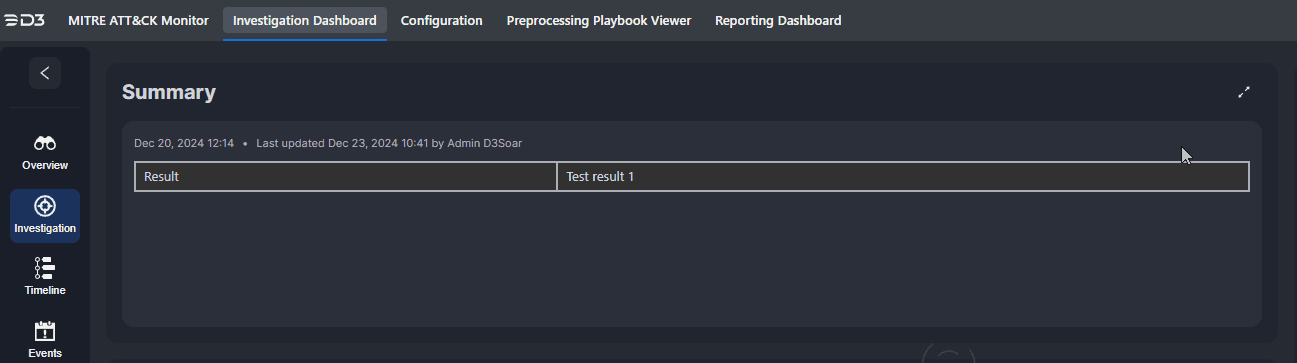 |
Edits to the Summary section can also be done within the Overview tab. Click on the | 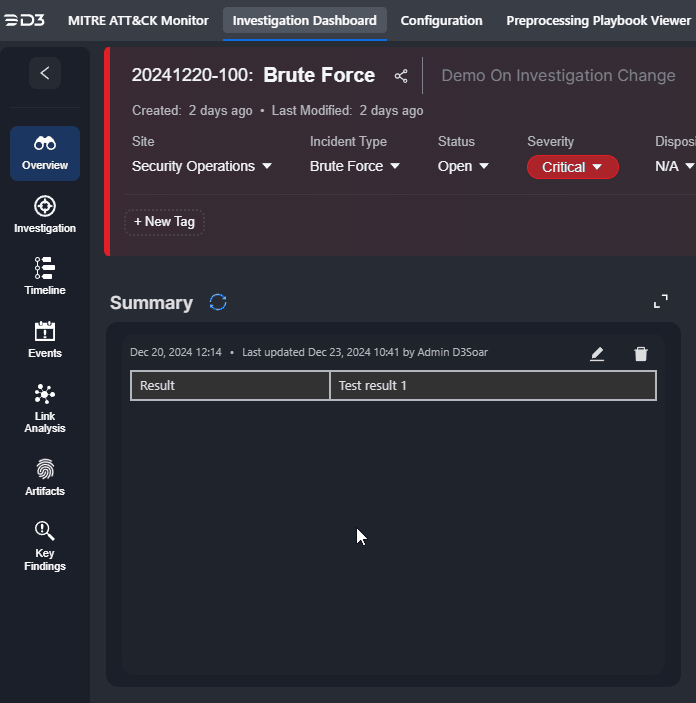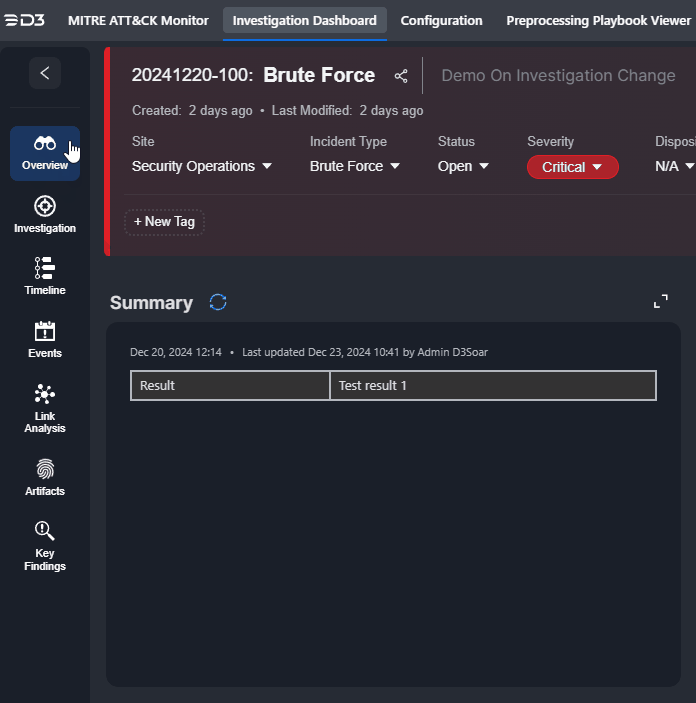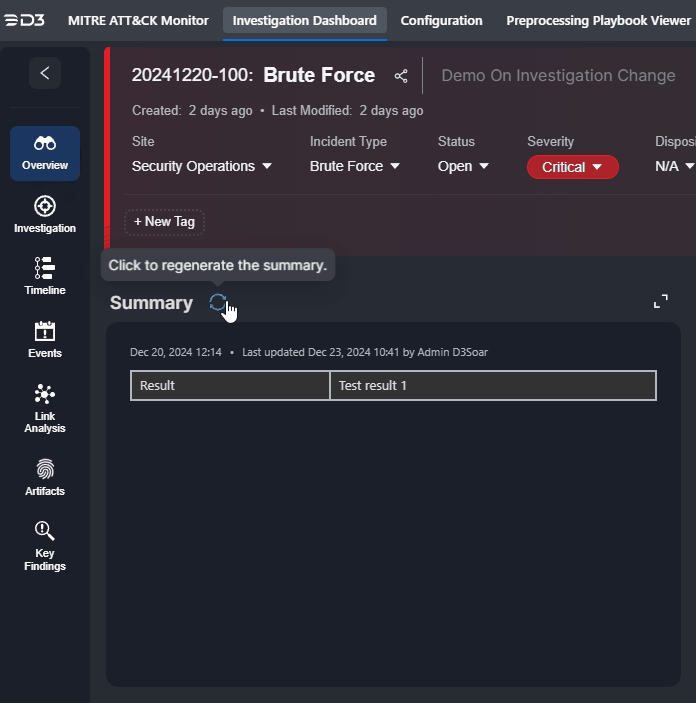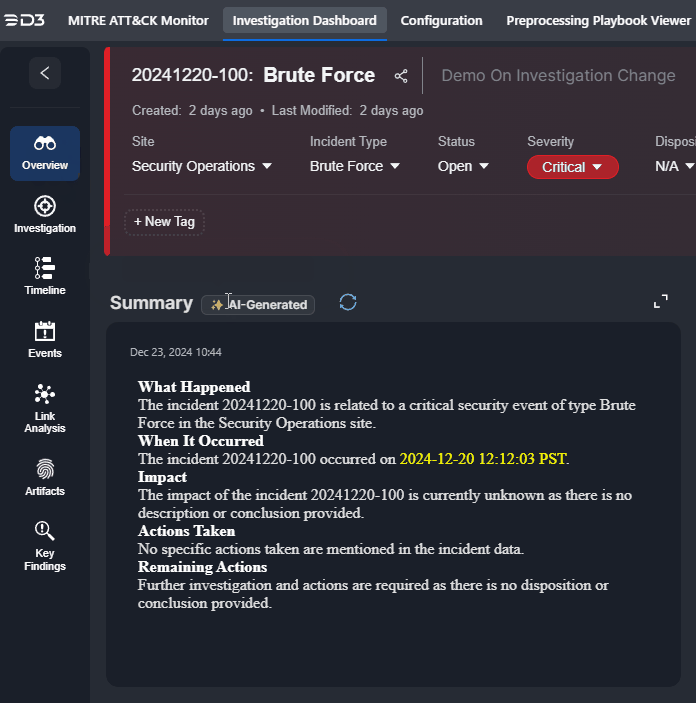 |
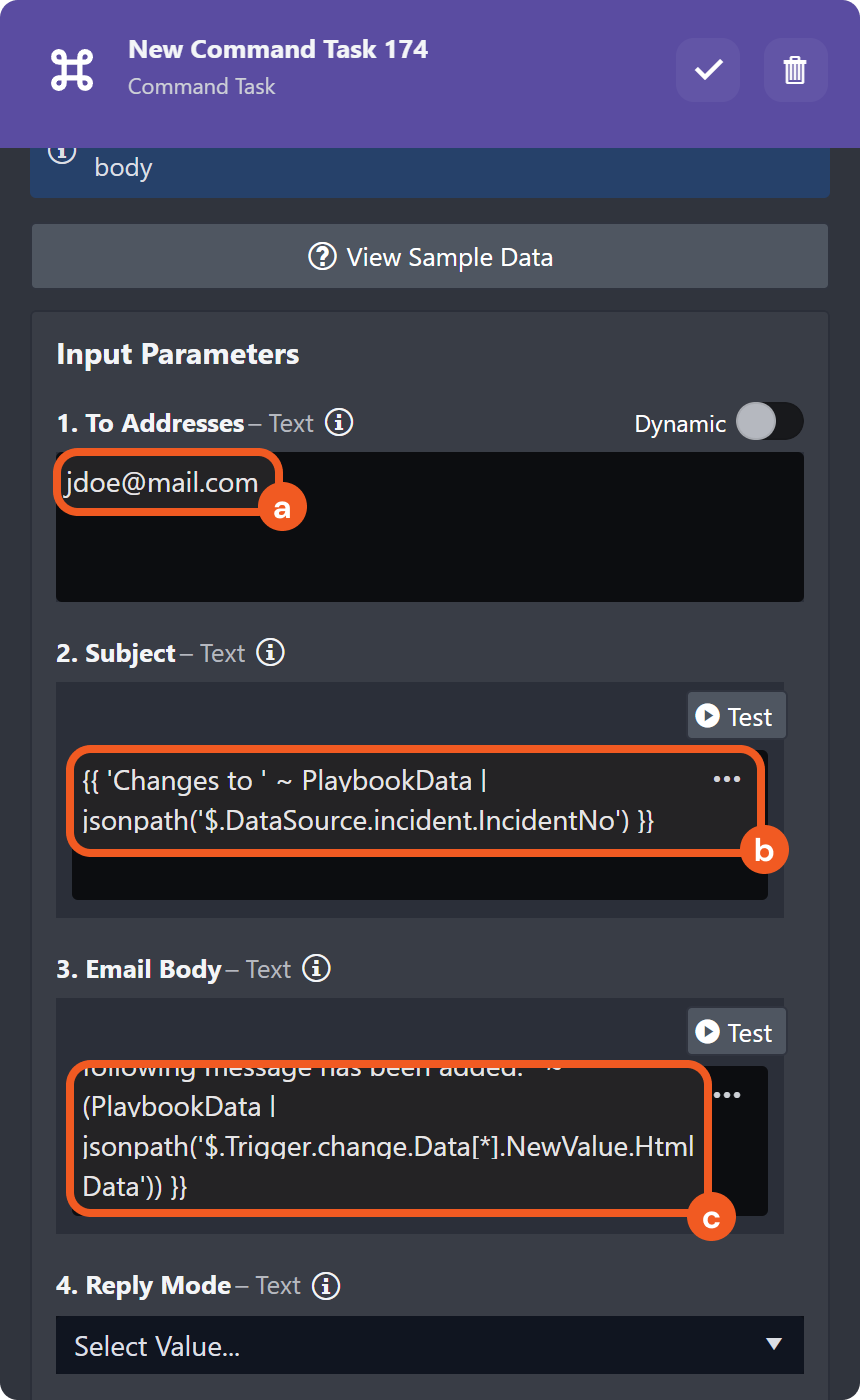
Updates via a Utility Command | |
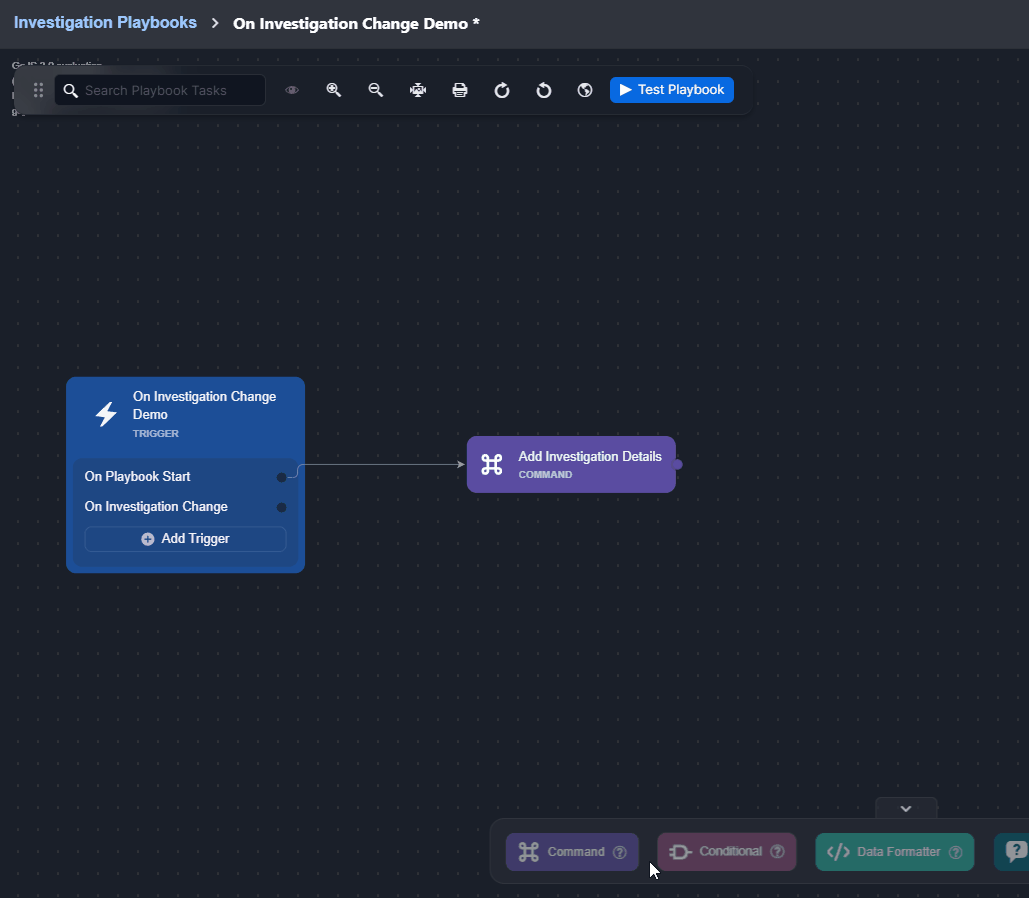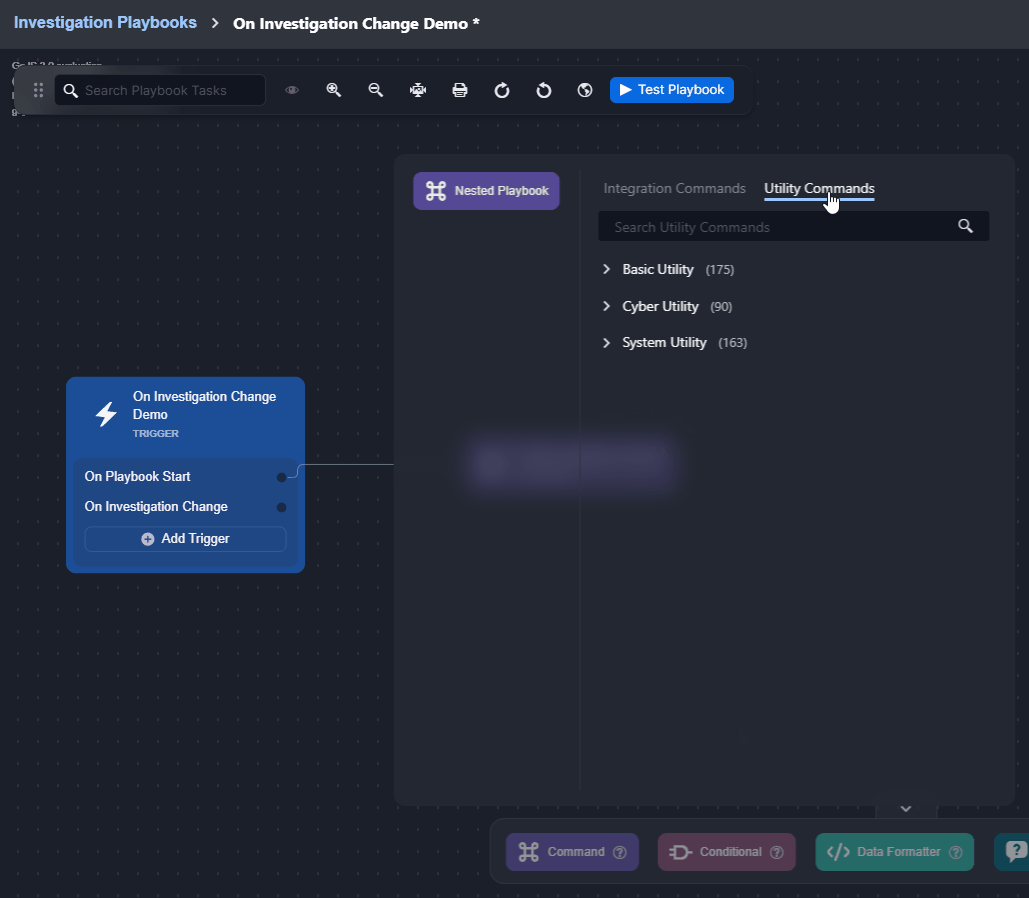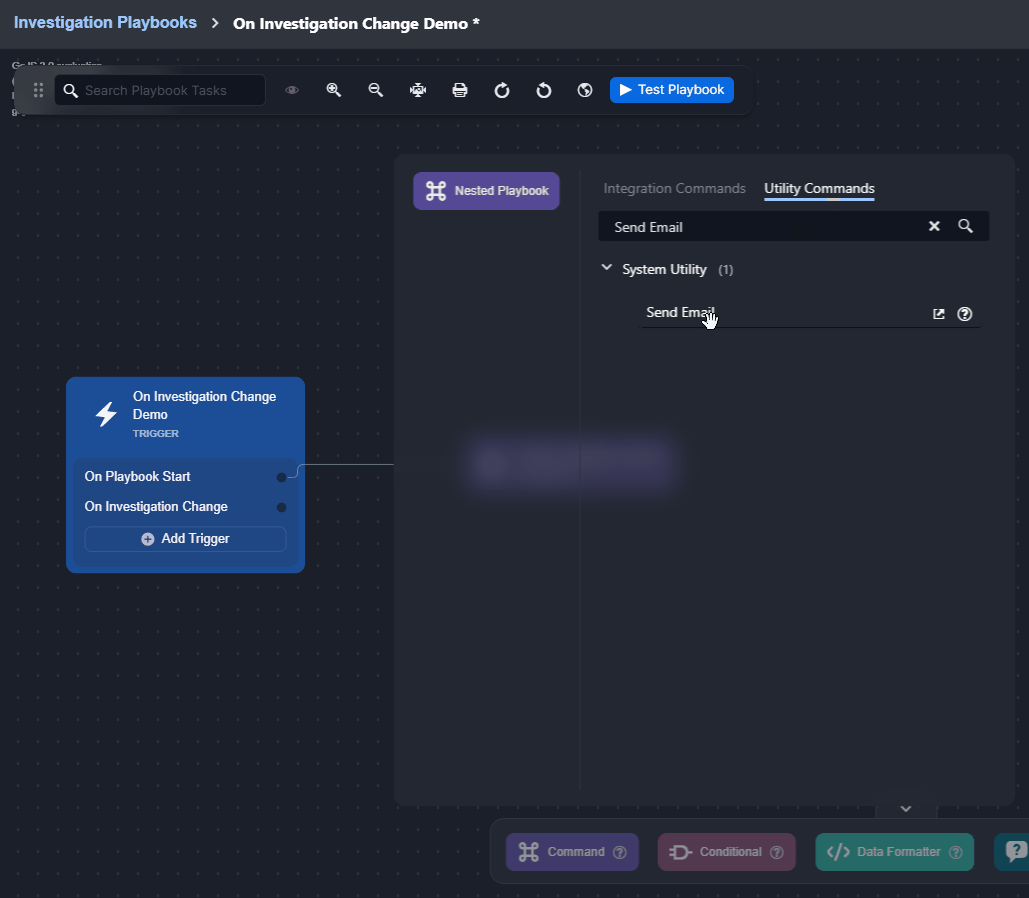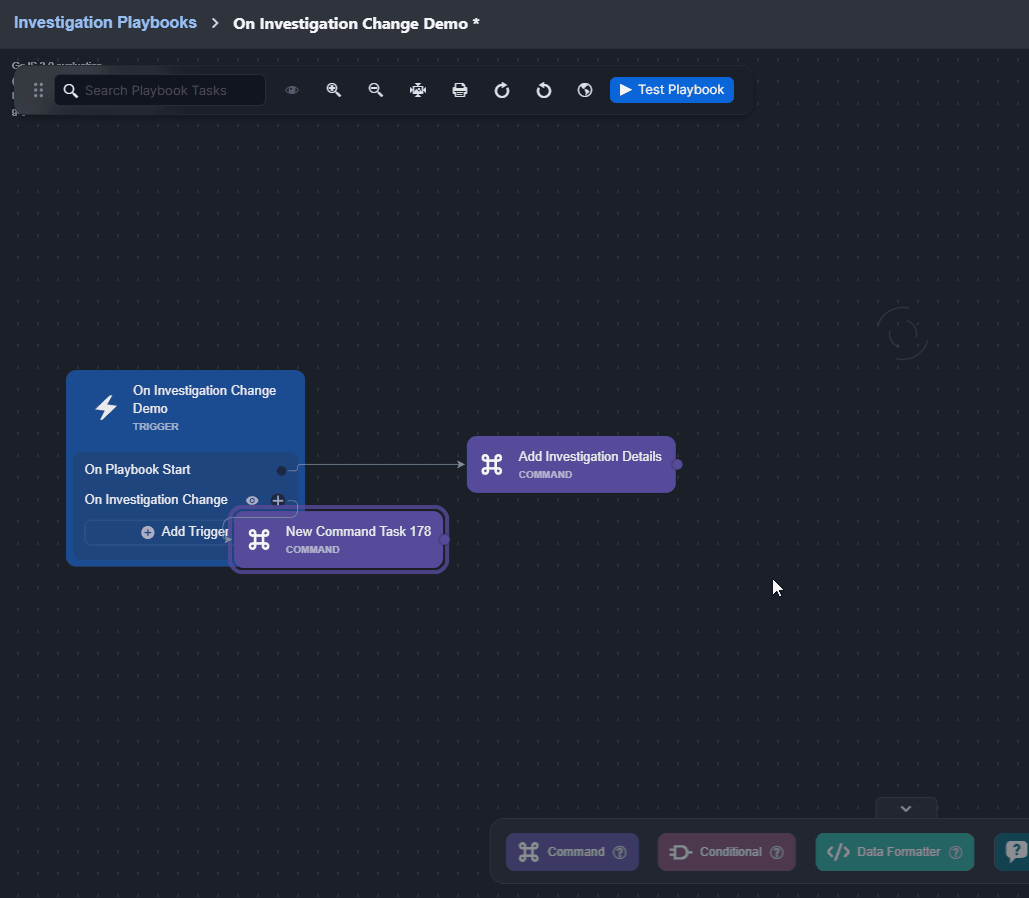
Changes to the data within the Investigation tab can be done using certain utility commands, such as Add Investigation Details and Add Investigation Table Content. See the demonstration for details. | 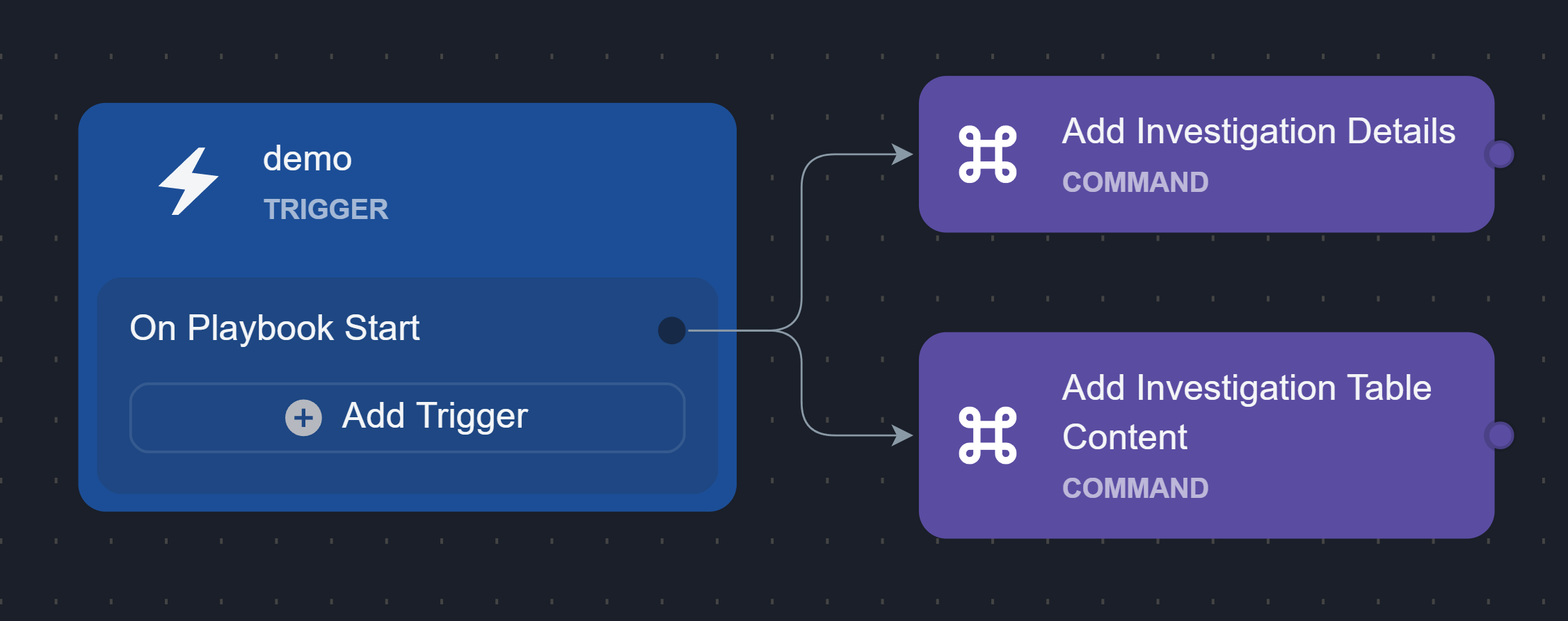 |
Demonstration
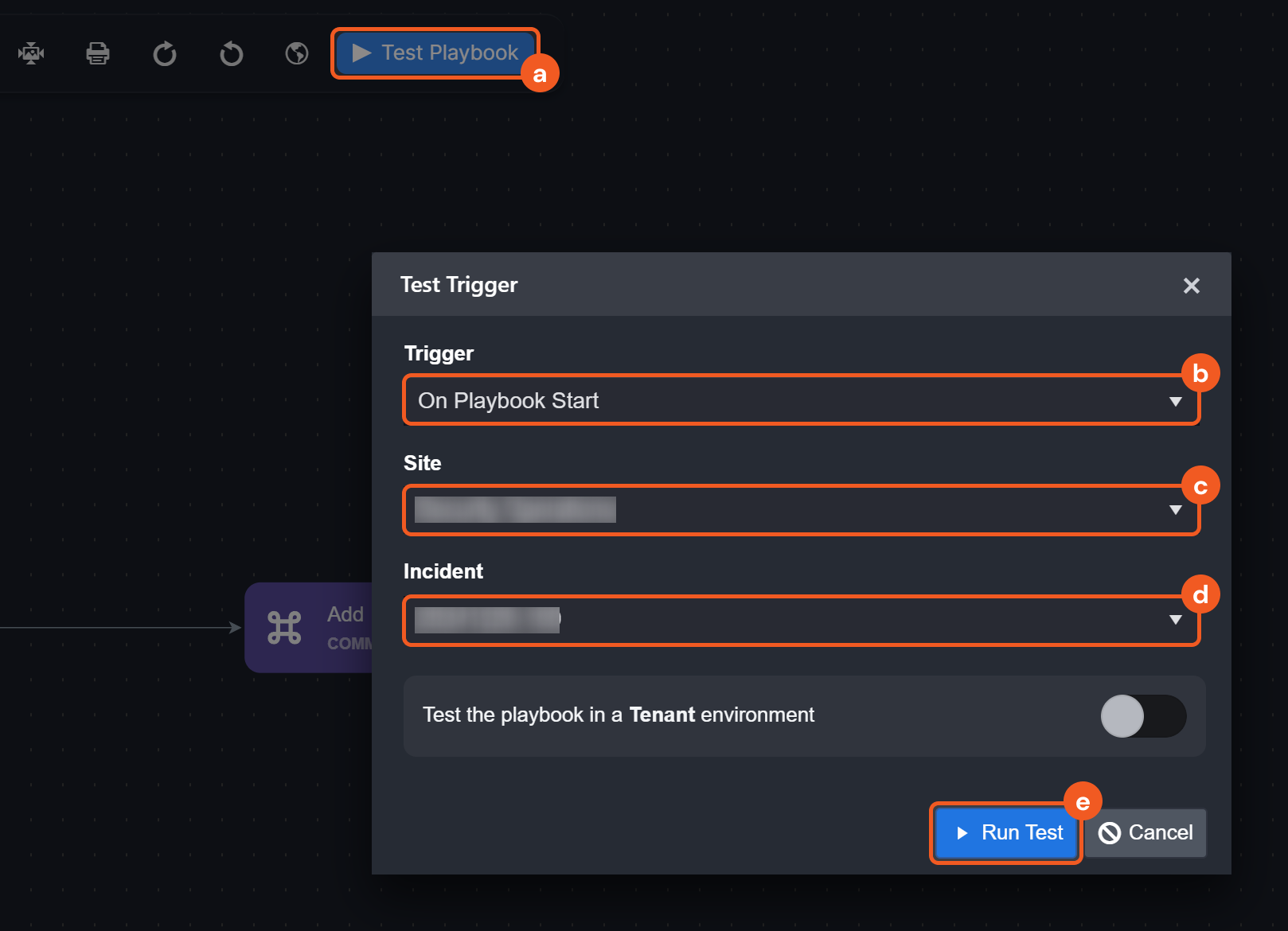
Observe how the On Investigation Change trigger automates responses when a playbook is assigned to an incident:
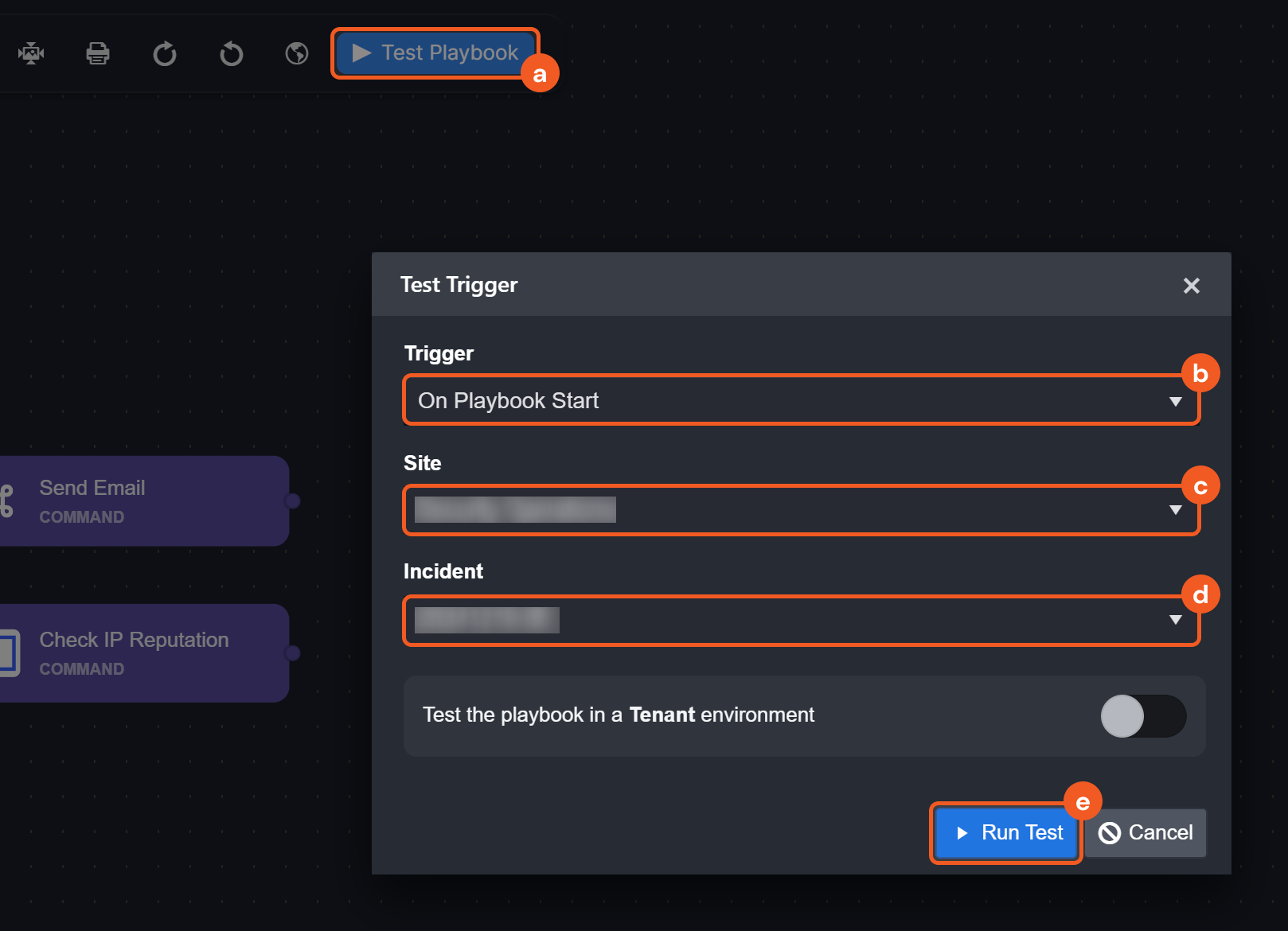
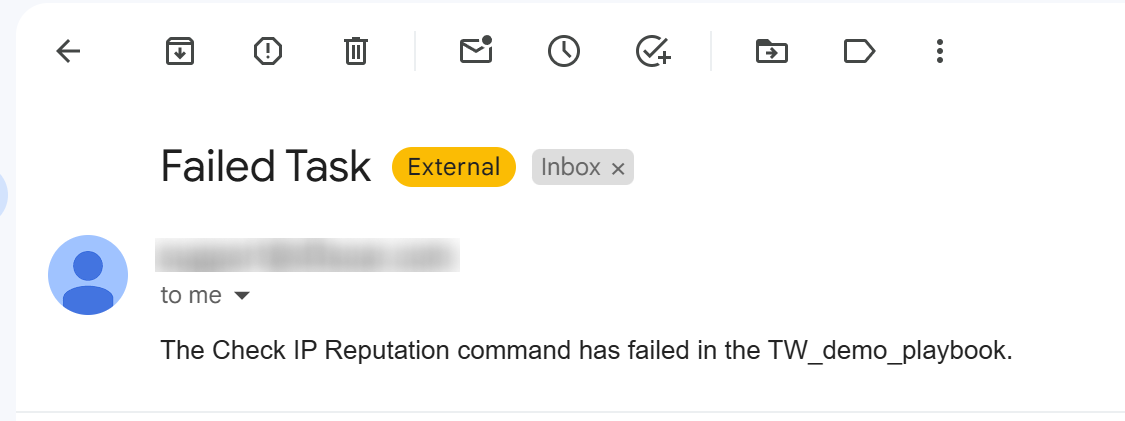
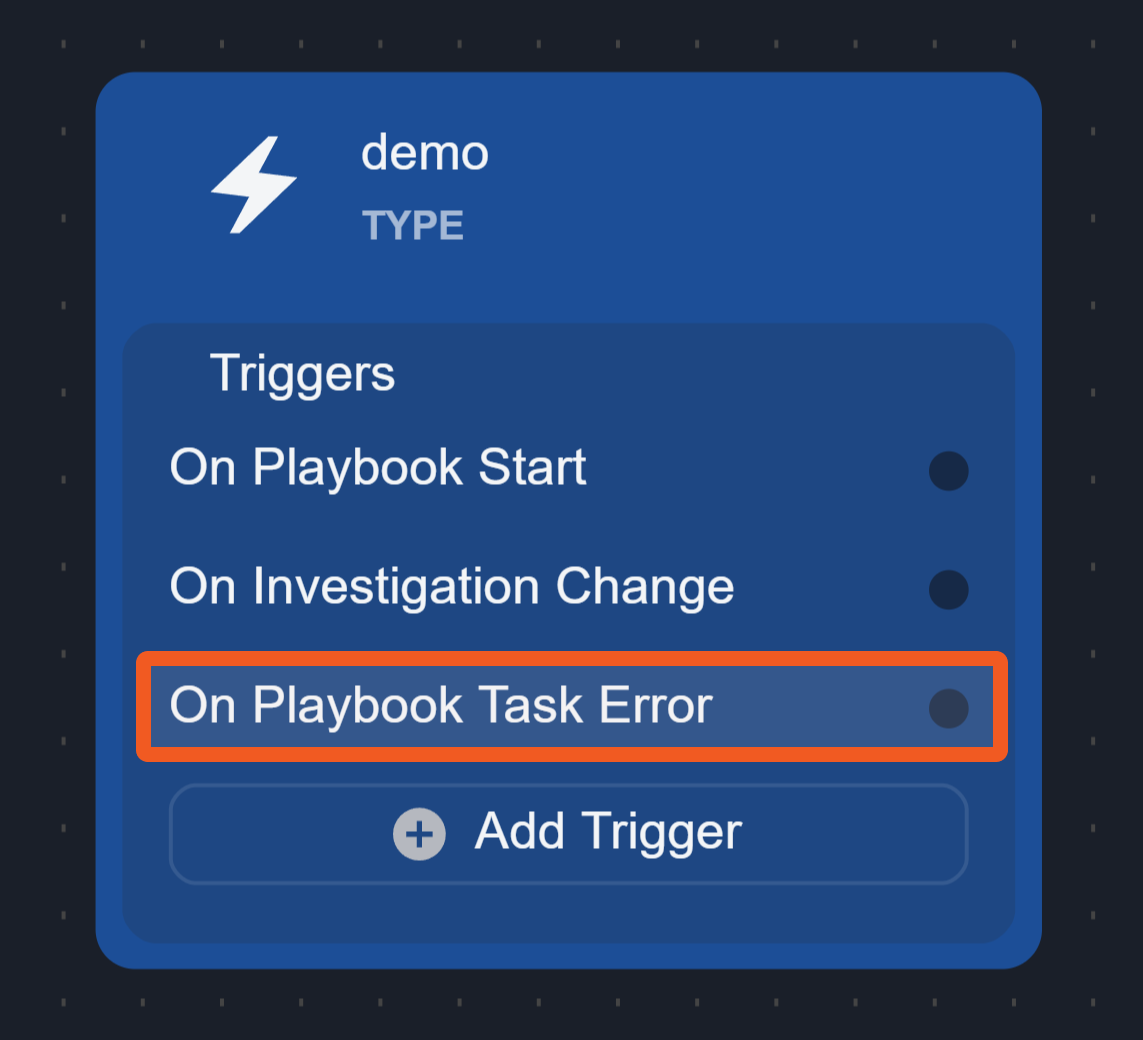
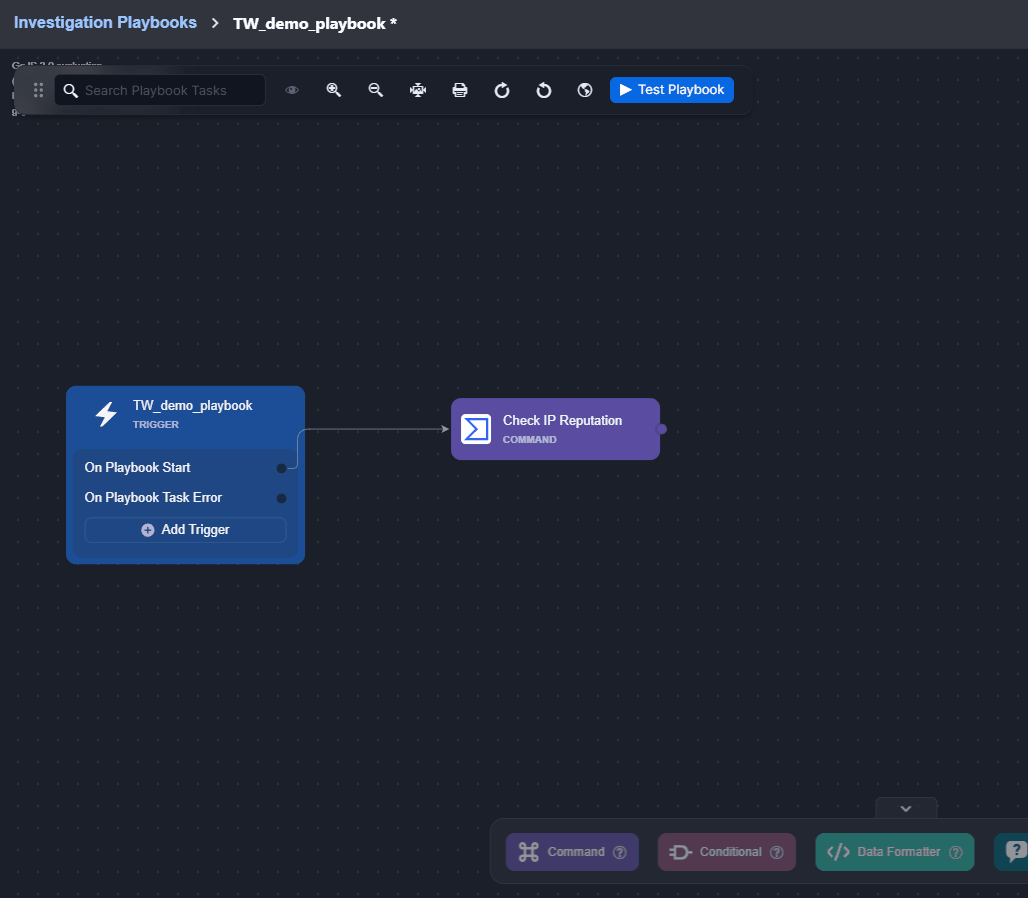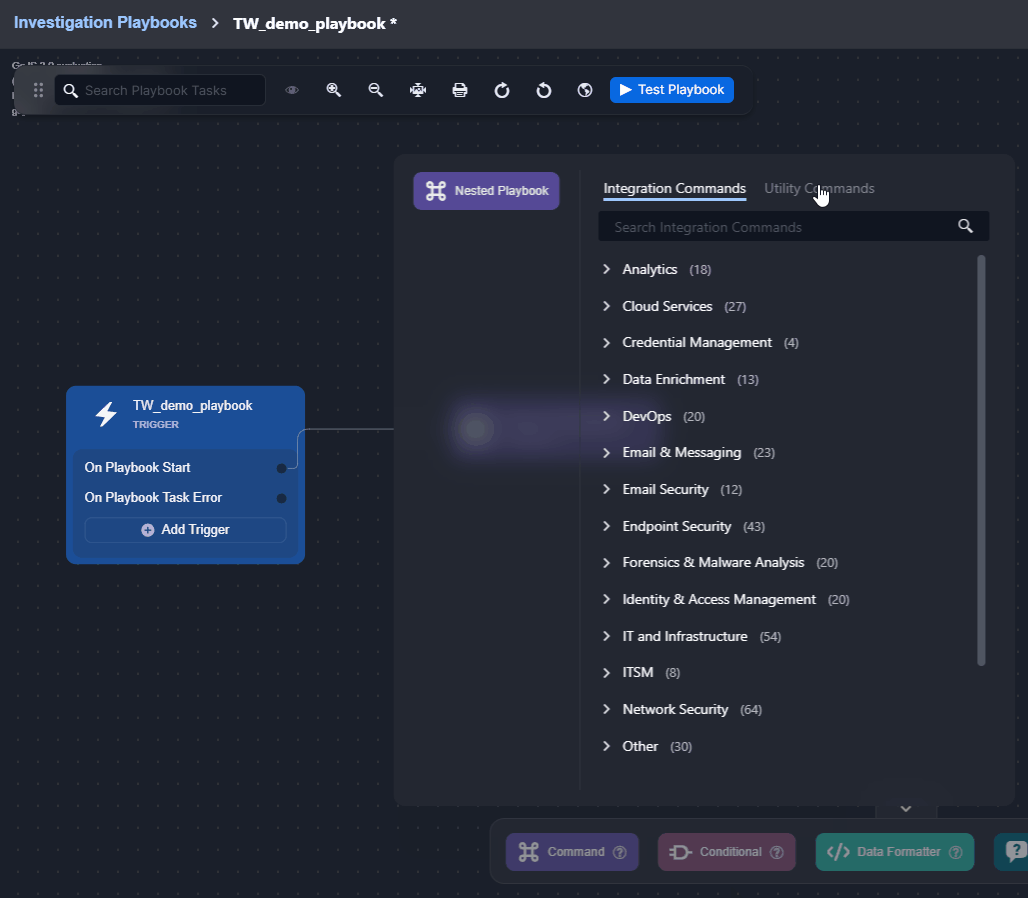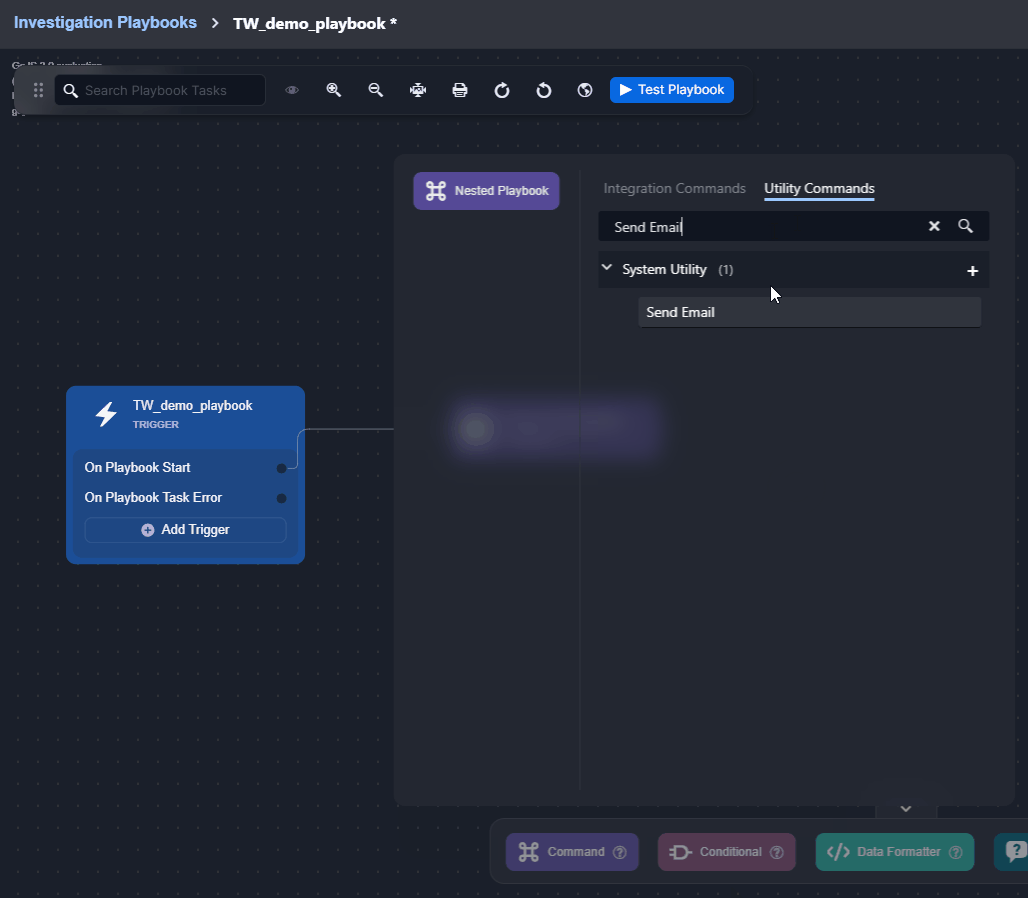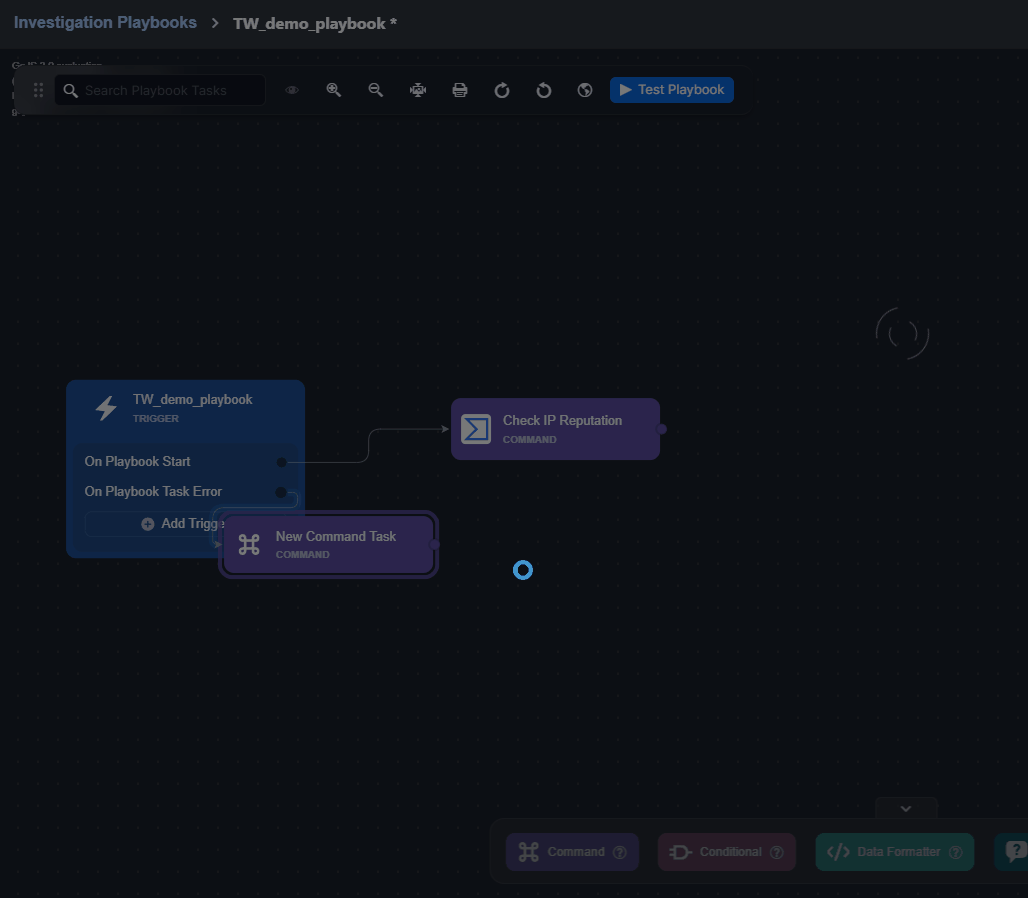
On Playbook Task Error
The On Playbook Task Error trigger initiates tasks linked to it when a playbook task has the Error Trigger checkbox selected (selected by default). Tasks on this path will not trigger additional error paths, ensuring simple error handling and avoiding loops.
This trigger node can be added to both Investigation Playbooks and Preprocessing Playbooks.
Demonstration
Observe how the On Playbook Task Error trigger supports troubleshooting below:
.png)
-20241223-224442.png?inst-v=260ff065-eacd-4502-b259-6f48de11932a)
-20241223-224556.png?inst-v=260ff065-eacd-4502-b259-6f48de11932a)
%201-20241223-222903.png?inst-v=260ff065-eacd-4502-b259-6f48de11932a)
-20241223-223130.png?inst-v=260ff065-eacd-4502-b259-6f48de11932a)
-20241223-223702.png?inst-v=260ff065-eacd-4502-b259-6f48de11932a)
%201-20241223-223447.png?inst-v=260ff065-eacd-4502-b259-6f48de11932a)
.png?inst-v=260ff065-eacd-4502-b259-6f48de11932a)
.png?inst-v=260ff065-eacd-4502-b259-6f48de11932a)
-20241223-231527.png?inst-v=260ff065-eacd-4502-b259-6f48de11932a)
.png?inst-v=260ff065-eacd-4502-b259-6f48de11932a)
.png?inst-v=260ff065-eacd-4502-b259-6f48de11932a)
.png?inst-v=260ff065-eacd-4502-b259-6f48de11932a)
.png?inst-v=260ff065-eacd-4502-b259-6f48de11932a)
.png?inst-v=260ff065-eacd-4502-b259-6f48de11932a)