16.0
Reporting Dashboard Revamp
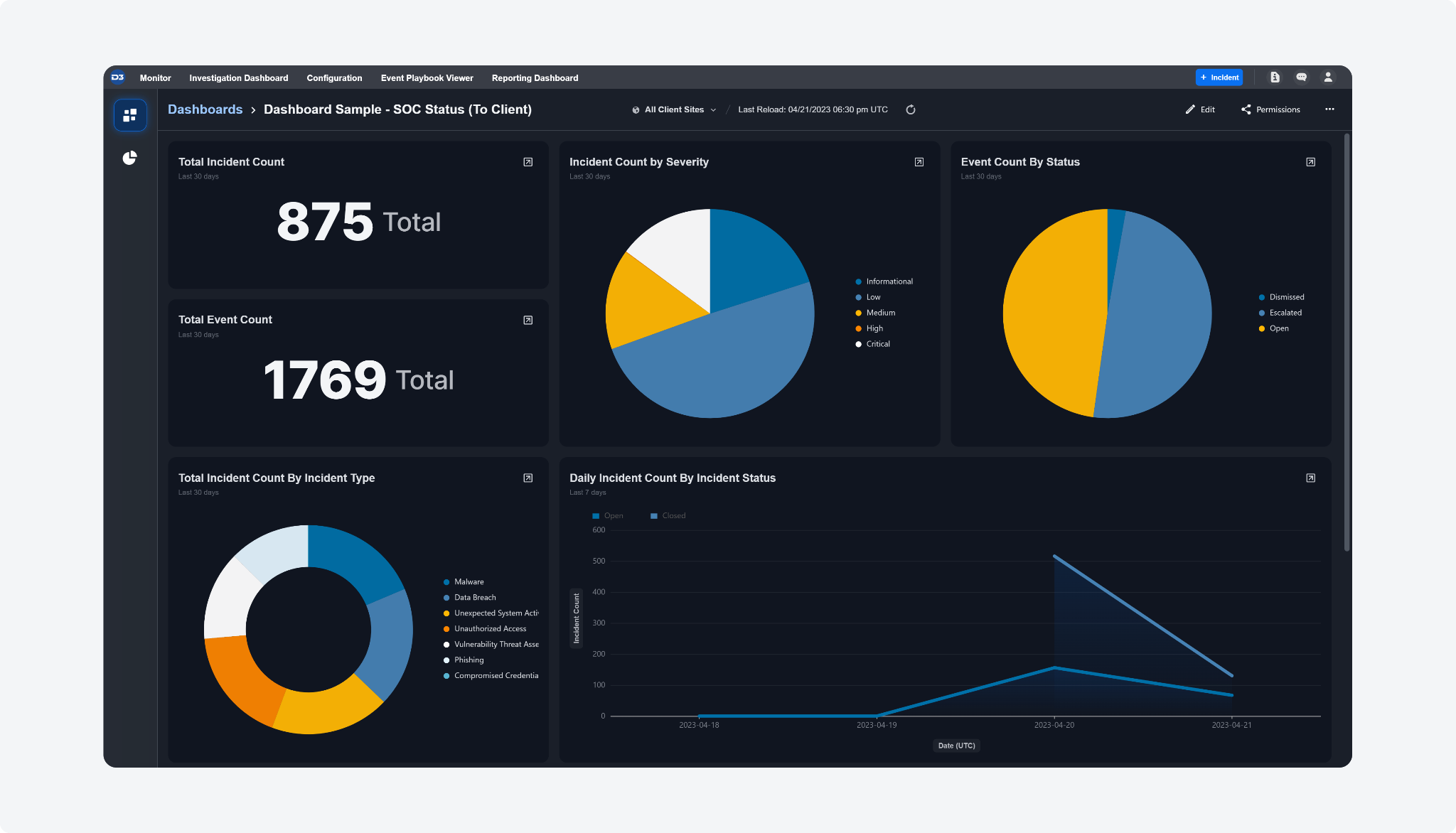
The Reporting & Analytics dashboard module has been completely revamped as the Reporting Dashboard, with a new user interface and new functionalities. The new reporting features offer personalized dashboards to security executives and managers to visualize and monitor their Key Performance Indicators (KPIs) in real time.
This module comprises two main parts: Widgets and Dashboards.
Widgets provide visual representations of data extracted from four sources: Artifact, Event, Global List, and Incident. You can create queries using the query builder to extract data from these sources and select specific time ranges and sites to display within the widget. Once created, these widgets can be added to Dashboards.
Dashboards are collections of widgets that can be tailored to meet different reporting needs, including KPI monitoring, SLA monitoring, and SOC team management. The dashboard view can also be filtered by sites and time range and exported as PNG.
In addition, you can use the email scheduler feature to automate the sharing of dashboards, by conveniently scheduling one-time or recurring emails to recipients. Recipients receive a viewable link in the email, providing easy access to the interactive dashboard without requiring additional logins, facilitating streamlined communication and data-driven decision-making.
MSSP Client Access Portal
The MSSP (Managed Security Service Provides) client portal is an innovative addition enhancing communication, visibility, and collaboration between MSSPs and their clients.
Once the MSSP client portal license is purchased and activated, MSSPs can create user accounts with customized roles specifically designed for their clients. These roles, configured with the "Client" access type, provide MSSP clients with limited access to the SOAR platform, including the investigation dashboard and reporting dashboard. Here are some highlighted key features:
Incident Review: Clients can view incidents and events from the investigation dashboard, allowing them to view summarized and in-depth incident details.
Interaction Capabilities: Clients can take limited actions, such as running ad hoc commands and responding to pending tasks that require SLA approvals.
Messaging: MSSPs can improve response times and promote collaboration by using the portal to communicate with their clients and request approvals via the message center.
Reporting and Analytics Dashboard: MSSPs can curate reports and data visualizations to provide clients with valuable insights into their security operations.
Investigations Tab: Clients can view insights on each incident curated by the MSSP, organized by Summary, Findings, Mitigations, and Recommendations.
The client portal serves as a centralized hub, consolidating all necessary functionalities for efficient and effective collaboration. It empowers MSSPs and their clients to seamlessly interact, share information, and work together towards their security goals.
Incident Workspace Enhancement
Key Fields
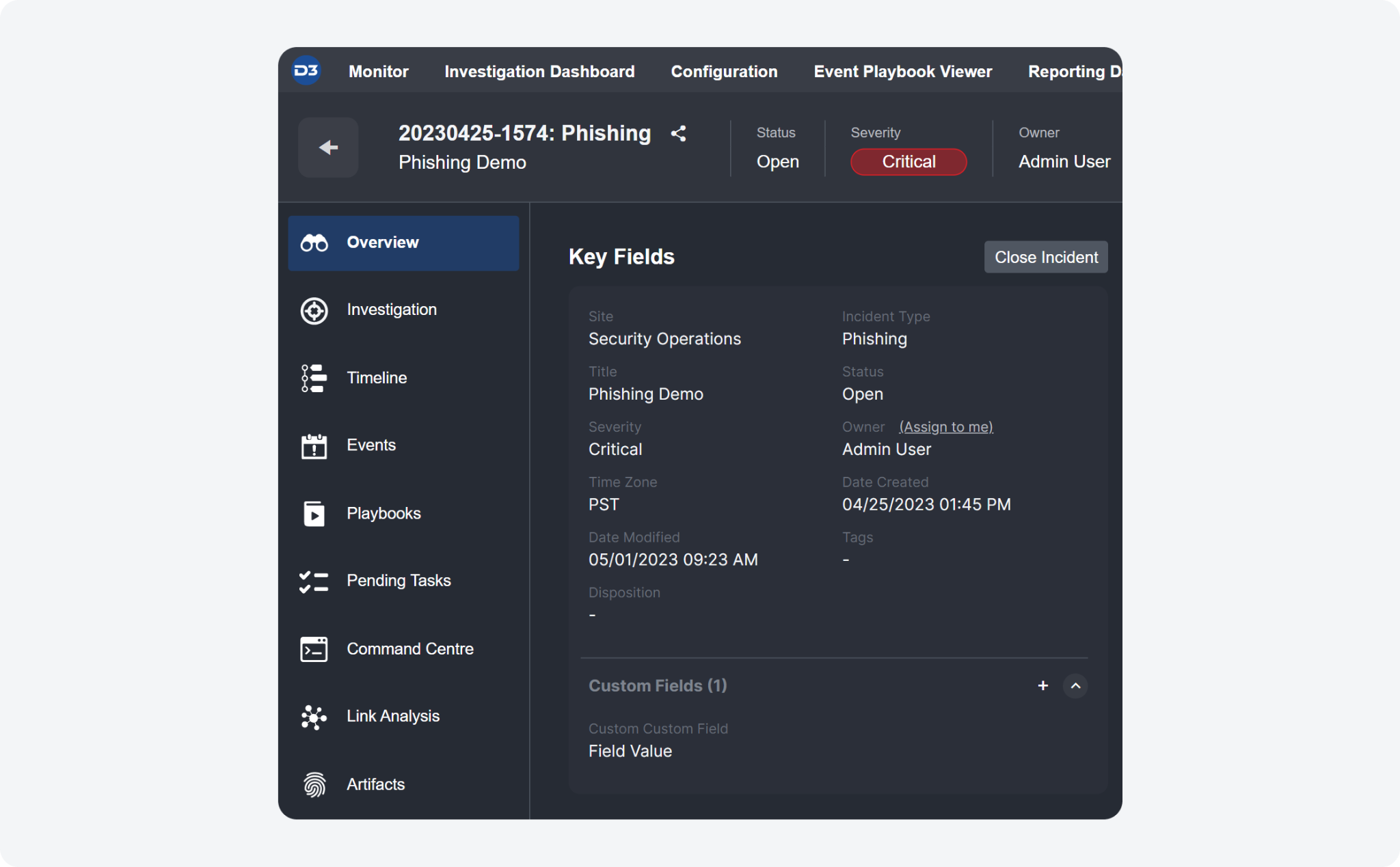
The Incident Summary section within the Overview Tab has been renamed to Key Fields, allowing for the inclusion of custom fields. Just like the previous Incident Summary section, Key Fields displays and allows you to edit the default incident fields filled in by an analyst or playbook during the event escalation or incident intake process. The notable enhancement is the introduction of the Custom Fields section, which provides flexibility in field mapping. Previously, these fields were limited to a predetermined set of system fields.
Your Pending Tasks
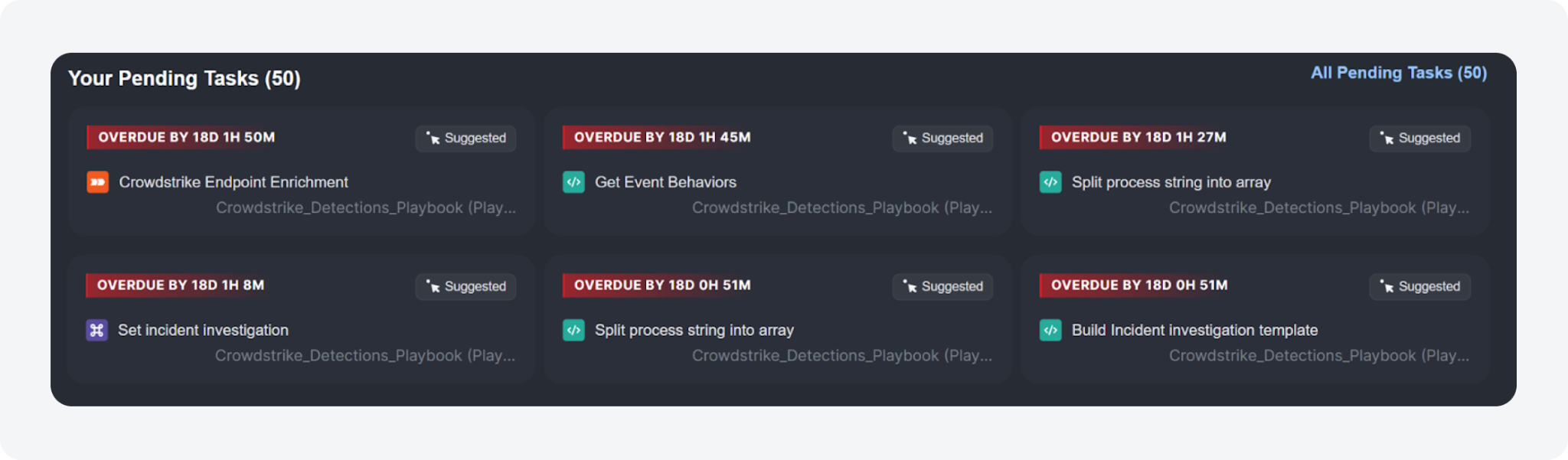
The Your Pending Tasks section provides an overview of your top six most urgent ad-hoc tasks and playbook tasks related to the selected incident. This section will only display tasks assigned to you.
The tasks are organized based on their due dates. From left to right, these tasks are colour-coded based on urgency, with red indicating the tasks past their due dates, followed by yellow for tasks due within one hour. Tasks without a coloured stripe are those with deadlines further in the future or no deadline. Tasks with a required tag must be completed before an incident can be closed, while suggested playbook tasks need your input to run or skip the task. Clicking on a task will bring up the full task details.
Investigations Tab
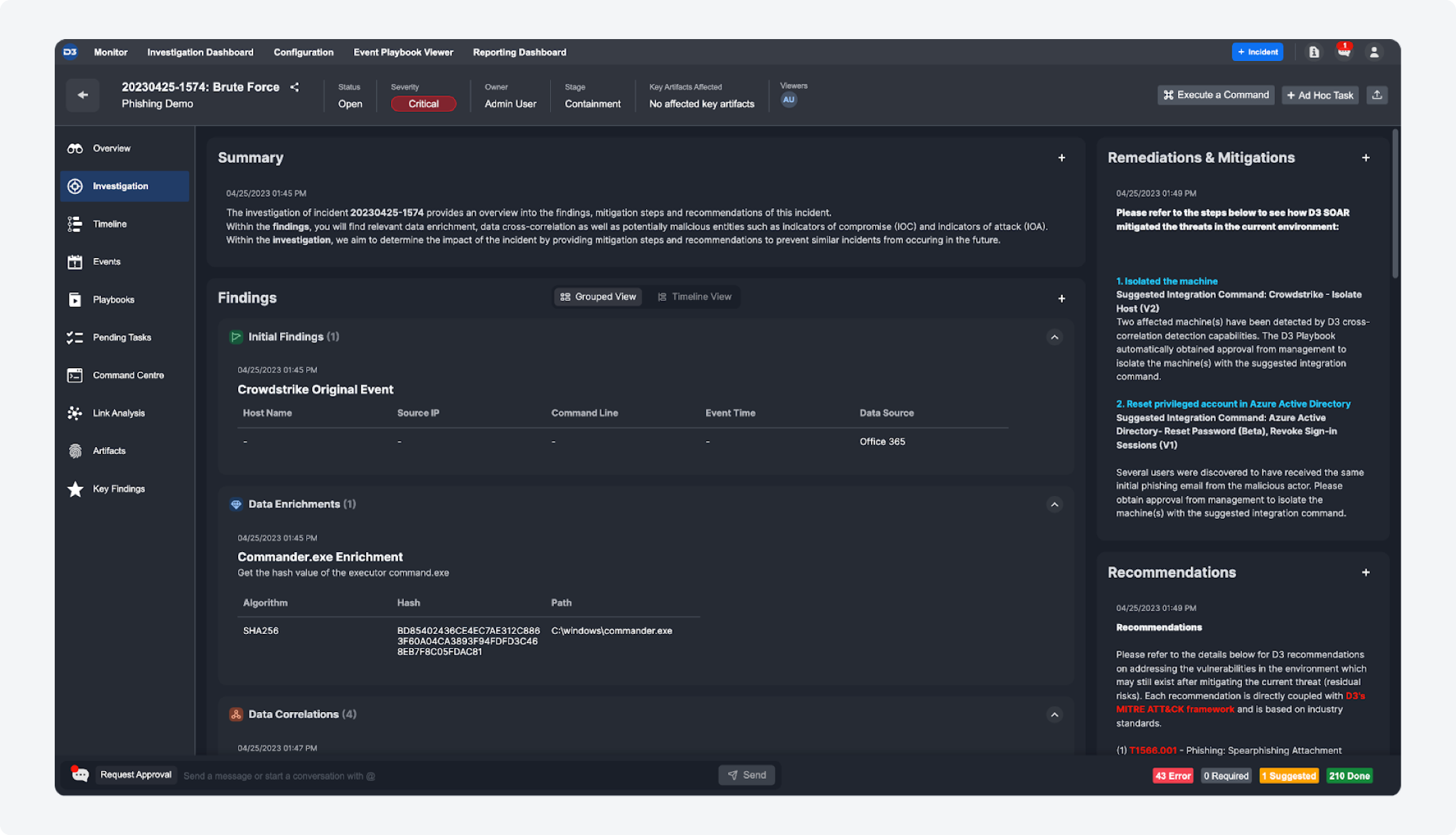
The Investigations Tab is a brand new tab added to Incident Workspace.
This tab is a centralized location designed for analysts to input and manage investigation information related to an incident. It consists of four sections: Summary, Findings, Remediations & Mitigations, and Recommendations. Analysts can input incident investigation information to the appropriate sections by using JSON-defined data tables or HTML, allowing them to record details such as notes, findings, and recommendations. The Findings section is further divided into subsections for Initial Findings, Data Enrichments, Data Correlations, Indicators of Attack (IOA), and Indicators of Compromise (IOC). Analysts can manually input information through the user interface or use utility commands in playbooks for automated data population, saving time and ensuring accurate capture of critical details.
Two new utility commands are available to help automate populating the investigation sections.
Export Incident Report Enhancement
The incident template has been revised to match the updated and new components of the Incident Workspace. These revisions apply to both the exported templates in Microsoft Word and PDF formats.
Incident Messaging
Incident messaging allows SOC analysts to communicate about investigations, and for MSSPs to collaborate with clients. New features include mentioning and direct messaging, requesting approval, and Slack integration. Plans for integration with other messaging services are in development for future releases.
Data Ingestion

MITRE TTP Search and Event Automation Rules Settings
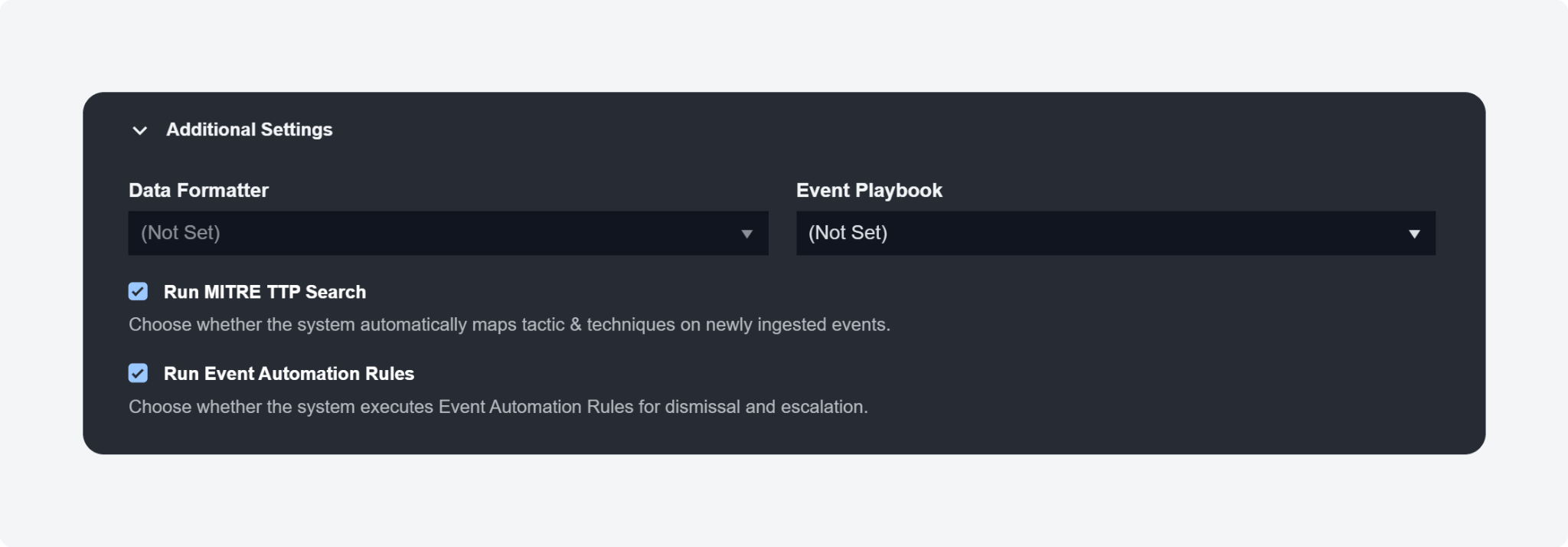
Upon configuring a new data source across different components in D3 SOAR, such as API Keys, JWT, Data Ingestion, Schedule, Upload File (from the Investigation Dashboard), and Ongoing Surveillance Task, two checkboxes will appear that allow you to customize the behaviour of ingested events. The first checkbox enables the automatic mapping of ingested events from the data source to MITRE tactics and techniques. The second checkbox enables event automation rules for event dismissal and escalation.
JWT Authentication

JSON Web Token (JWT) is an open and widely accepted industry standard, defined in RFC 7519. They provide a secure and efficient way of transferring claims between two parties, ensuring the authenticity and integrity of the data. JWTs can now be used to authenticate data ingestion and remote commands via webhook in D3 SOAR. Additionally, token creators have the ability to reassign, regenerate, rename, and delete tokens as needed.
To enable JWT authentication in D3 SOAR, navigate to Configuration > Application Settings > Web Config, and set the value of the "EnableEnhanceWebhookAuthentication" configuration key to True.
IOA/IOC Link Analysis
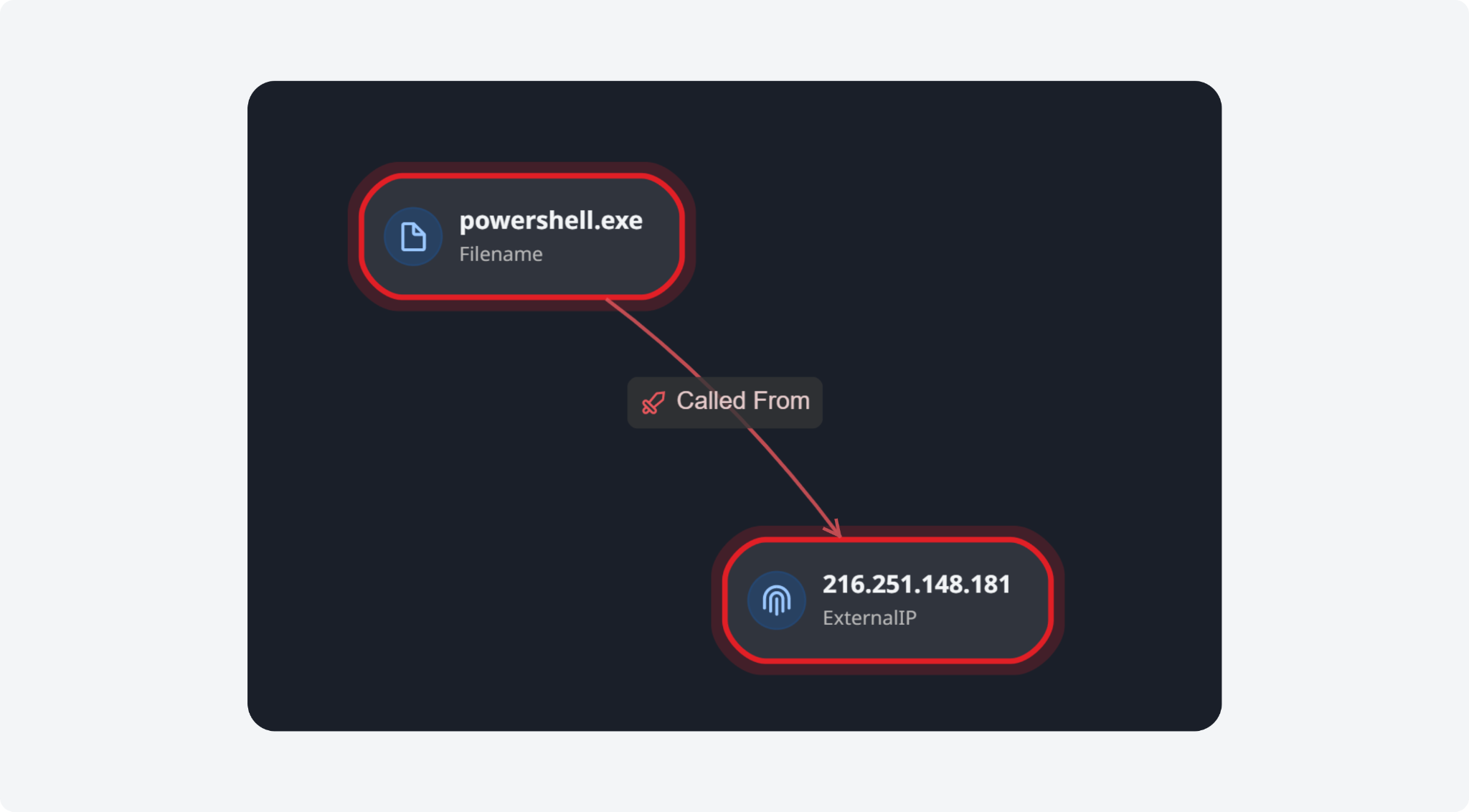
The IOA/IOC Link Analysis tab under the Investigation Dashboard visualizes the relationships between indicators of attack (IOAs) and indicators of compromise (IOCs) from events and incidents. You can view analyses from the past 7 or 30 days to gather historical attack patterns. Each node represents an artifact entity, coloured red (IOA), yellow (IOC), or both. Arrows show the direction of the labelled relationship. Clicking on a node reveals more information, and the "Add Investigation Details" command lets users define artifact relationships for automated link analysis.
Incident Playbook Enhancements

Trigger: On Incident External Action
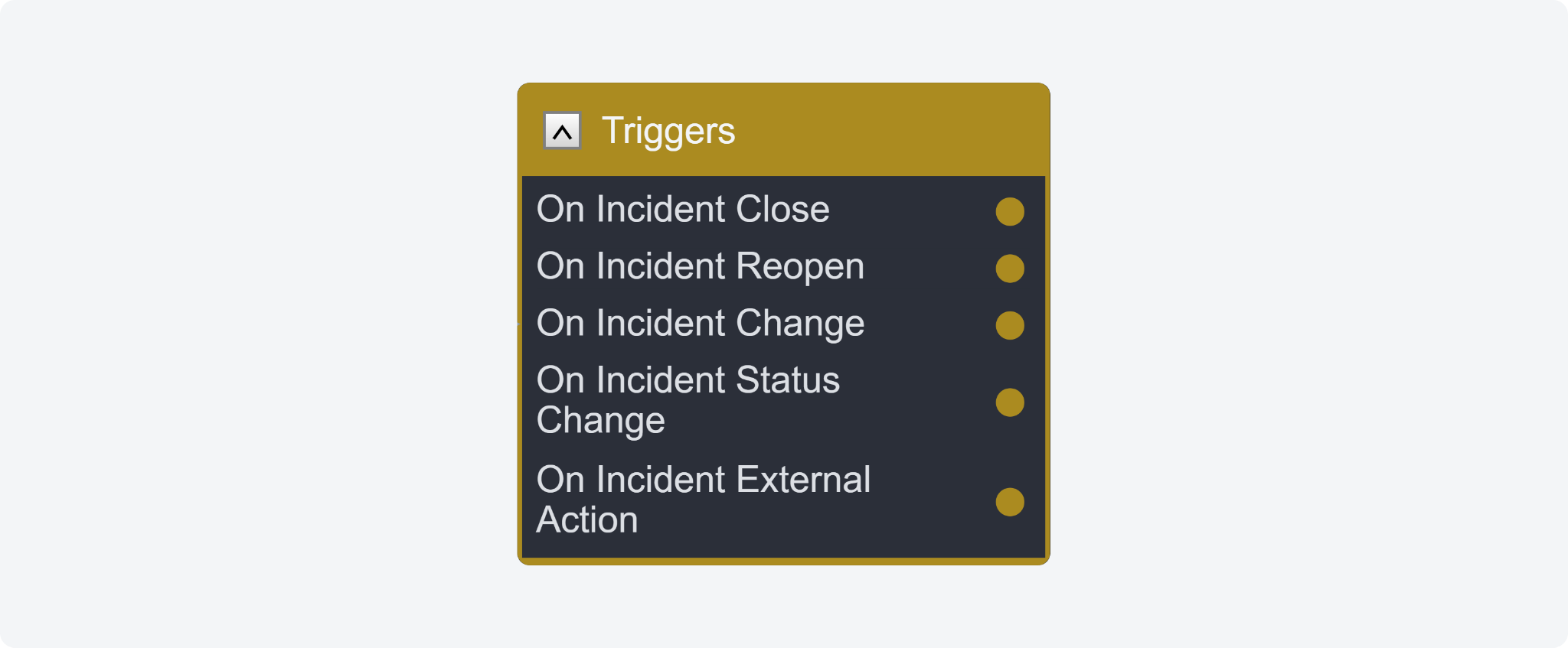
The On Incident External Action trigger in incident playbooks combines external action data with raw incident data, allowing users to perform a comprehensive investigation on an incident using a defined playbook workflow. By ingesting events through the D3 API with a unique key, multiple requests with the same key ID are aggregated into a single incident. This trigger feature enables users to initiate additional workflows for investigating a specific incident without the need to log into D3 SOAR directly.
Utility Commands Enhancements

The following utility commands have been added to this release of D3 SOAR.
Commands | Functionality |
Add Investigation Details | Adds investigation details in HTML rich text to the sections in the Investigation Tab. |
Add Investigation Table Content | Adds data tables defined in JSON format to the relevant Incident Workspace's Investigation Tab. You can use this utility command to populate any of the sections in the Investigation Tab, as well as highlight important key details. |
Get Incident Static Field | Returns all static incident fields and corresponding values of the specified incident, which are shown in the overview tab in Incident Workspace. |
Get Related Incidents by Artifact | Searches for incidents related to the specified artifact(s). |
Link Event To Incident | Searches for a pre-existing incident by applying a specific set of search conditions and updates the custom fields of the first identified incident that meets the search conditions. The corresponding event is also added to the same incident. If no matching incident is found, a new incident is created. |
Set Incident Field HTML | Adds HTML content to a specified incident's description, note or conclusion, which is shown in the overview tab in Incident Workspace. |
Trigger Incident External Action | Activates the "On Incident External Action" trigger in incident playbooks for the first incident that matches the specified search conditions. |
Connections Module Enhancement

The connections module now has a newly added Webhook Keys tab. This tab allows you to efficiently manage and view all the webhook keys you have created and are currently available for your account. This addition is especially beneficial for our MSSP (Managed Security Service Provider) users who need to manage webhook keys for various tenants and client sites. With the Webhook Keys tab, you can conveniently access and remove keys created from your account in a centralized location, streamlining your key management process.
Application Settings Enhancements

Dashboard Columns
With this new update, you can now easily manage the default and custom columns displayed in your investigation dashboard. When you add a new custom column, it will be automatically saved to the investigation dashboard. To enable or disable the column, simply click the "more" icon located on the top right corner of event and investigation lists.
Logo Customization
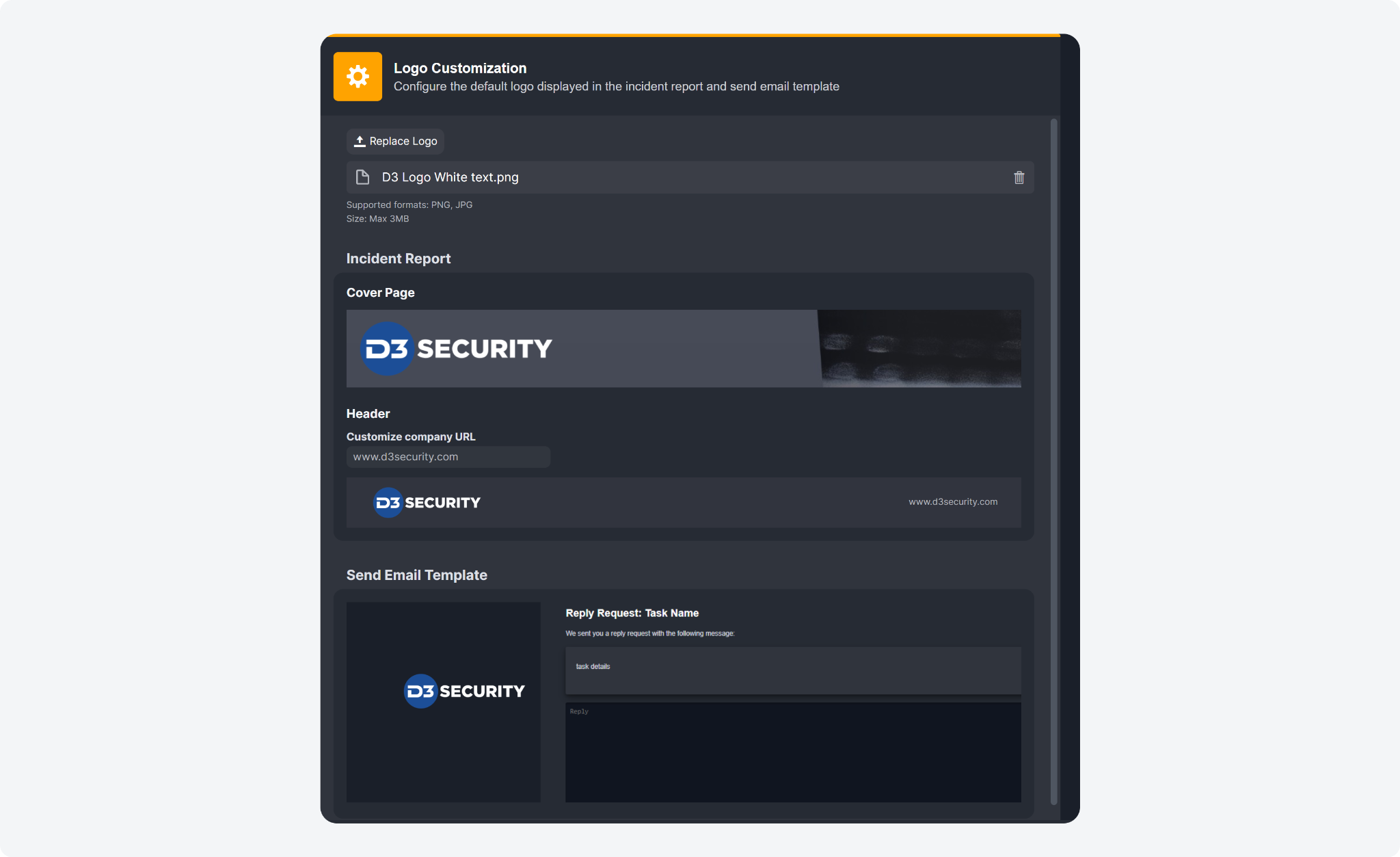
You can now customize the branding of your incident reports and email approval pages to better reflect your company or MSSP's corporate identity.
By default, the incident report and send email templates are equipped with D3's logo. You can now upload your own logo to replace the default one. Additionally, you can also include your company URL in the header of the incident report. Every time an incident report is generated or an email approval page is sent, your logo will be prominently displayed, providing your team and clients with a consistent and professional brand experience.
Proxy Agent Update

We have released a new version of the proxy agent along side D3 SOAR version 16.0. To ensure compatibility, please upgrade your proxy agent to version 16.0.18.0. For instructions on how to update a proxy agent, please refer to the Agent Management section in the user guide.
Integrations

New Integrations
The following integrations have been added to this release of D3 SOAR.
Integration Name | Description |
CrowdStrike Falcon Intelligence | Crowdstrike Falcon Intelligence enables organizations of all sizes to better understand the threats they face and improves the efficacy of their other security investments with actionable and customized intelligence to defend against future attacks, making proactive security a reality. |
CrowdStrike Threat Graph | CrowdStrike Threat Graph is the brains behind the Falcon cloud-native platform. The CrowdStrike Security Cloud leverages Threat Graph to correlate trillions of security events per day with indicators of attack, threat intelligence and enterprise telemetry from across customer endpoints, workloads, identities, DevOps, IT assets and configurations. The CrowdStrike Security Cloud creates actionable data, identifies shifts in adversarial tactics, and maps tradecraft in the patented Threat Graph to automatically prevent threats in real-time across CrowdStrike's global customer base. |
CyberInt | Cyberint, the Impactful Intelligence company, fuses threat intelligence with attack surface management, providing organizations with extensive integrated visibility into their external risk exposure. Leveraging autonomous discovery of all external-facing assets, coupled with open, deep & dark web intelligence, the solution allows cybersecurity teams to uncover their most relevant known and unknown digital risks - earlier. |
D3 Tool Kit | D3 toolkit is a collection of software development tools and resources that help developers increase their productivity and efficiency, improve the quality of their applications, facilitate collaboration among team members, and stay up-to-date with the latest technologies and trends in software development. |
Kaspersky Security Center OpenAPI | Kaspersky Security Center takes the complexity out of security administration and IT systems management. The API is for controlling Kaspersky Security Center administration tools. It also allows integration with the ability to periodically retrieve detailed information about events. |
Microsoft 365 Defender (Email & collaboration) | Microsoft 365 Defender, part of Microsoft's XDR solution, leverages the Microsoft 365 security portfolio to automatically analyze threat data across domains, building a complete picture of each attack in a single dashboard. This integration allows organizations to fetch security incidents, update security incidents and run advanced hunting queries to inspect unusual activity, detect possible threats, and even respond to attacks. D3's integration for Microsoft 365 Defender (Email & collaboration) is using Exchange Online PowerShell to provide the operation on the Tenant Allow/Block list, which allows the user to Allow/Block email addresses, domains, URLs, and files. |
Recorded Future - SecurityTrails | SecurityTrails is a total inventory that curates comprehensive domain and IP address data for users and applications that demand clarity. By combining current and historical data of all Internet assets, SecurityTrails is the proven solution for 3rd-party risk assessment, attack surface reduction and threat hunting. This integration enables organizations to query risk issues and correlate domain and IP address data for risk assessment and threat hunting. |
Screenshot Machine | The Screenshot Machine is explicitly built to capture a full-page screen or small website thumbnail or to create a PDF from web pages online. |
Sevco | Sevco is an Asset Intelligence platform to aggregate inventory of users and devices and the relationships between them and monitor the changes over time. This product is a newly identified Cybersecurity Asset Attack Surface Management (CAASM) as an emerging technology focused on enabling security teams to solve persistent asset visibility and vulnerability challenges. |
Sucuri SiteCheck | Sucuri SiteCheck scanner remotely checks any URL for security threats, malware, defacements, out-of-date CMS, blacklisting, and other important security issues. It visits a website like an everyday user would to verify the source code for malicious behaviour or security anomalies. |
unshorten.me | Unshorten.me is a free service to Un-Shorten the URLs created by URL shortening services. Unshorten.me can un-shorten URLs created by different services like goo.gl (Google), fb.me (Facebook), t.co (Twitter), bit.ly, TinyURL, ow.ly, among others. |
Updated Integrations
The following integrations have been updated in this release of D3 SOAR.
Integration Name | Changes |
AlienVault OTX | Converted all existing C# commands to Python |
Atlassian Jira Service Management | Enhanced user interface for authenticating connections. |
Atlassian Jira Software | New commands: List Fields, Get Account IDs Create Issue & Edit Issue: Added support for adding and updating custom fields Assign Issue to User & Edit Issue: Enhanced to support Markdown for the parameters Description, Summary, and Custom Fields. Add Comment to Issues: Enhanced to support Markdown for the Comment parameter. Converted eight existing C# commands to Python: List Projects, Add Comment To Issues, Create Issue, Delete Issues, Get Comment From Issues, Get Create Meta, Search Issues, Upload File To Issue |
BrightCloud Threat Intelligence | New command: Check File Reputation |
Checkpoint Firewall | New commands: Show Application Site Categories, Block Domains, Show Policy Packages, Block URLs, Discard Changes, Show Changes, Install Policy, Show Sessions |
Cisco Adaptive Security Appliance | Updated all commands to support SSH connections |
Cofense Vision | New commands: Search, Get Search Result, Get Attachment |
CrowdStrike | New commands: Search Vulnerable Hosts By CVE, List Vulnerabilities, Get Host Vulnerabilities, Get Vulnerability Details, Get Vulnerability Evaluation Details Converted eight existing C# commands to Python: Fetch Event, Download Files, Find Hosts, Find IOC Observed Host, Isolate Host, Resolve Detection, Upload RealTime Response Script, Execute Command On Single Endpoint(Deprecated) |
CrowdStrike Discover | New commands: List Assets, List Accounts, List Logins |
Darktrace | New commands: Get Device Info, Get Device Summary, List PCAPs, Create PCAP, Get Status, Tag Devices, Get Device Tags, List Actions, Create Actions, List Tags Acknowledge & Unacknowledge: Updated to remove key field results, which previously caused an error message to return. |
Kenna Security | New commands: Test Connection, Search Assets, listApplications |
KnowBe4 PhishER | Added the headers "User-Agent" and "X-KB4-Integration" for all commands, with the values being "KnowBe4/1.0/{Command Display Name}" and "Acme Integration" respectively. |
Maltiverse | Check File Reputation: Added support for MD5, SHA-1, SHA-512 hashes. |
Microsoft 365 Defender | New command: Fetch Event |
Microsoft Purview Audit Logs Activities | Get Audit Log: Added the "User Principal Name" parameter to allow for filtering retrieved logs by user principal name. |
Microsoft Sentinel | Fetch Event: The string representation of $.value[].alertDetails[].entities is converted into a JSON array and assigned to the $.value[].alertDetails[].entities_json property. Update Incident Status: Added an input parameter and a corresponding key field named "Close Comment" to input an incident close comment using the command. Fetch Incident: Added the "Update Field Mappings" parameter to support bi-directional syncing of incident data in D3 SOAR. |
Microsoft Teams | New command: Send Message V2 |
OpenCTI | New commands: List Connectors, Add Observable, List Observables |
Palo Alto Networks Firewall | New command: Retrieve Logs |
Proofpoint Targeted Attack Protection | New command: Get Threat Details |
Rapid7 InsightVM Cloud | New commands: Search Asset, Search Vulnerability, Get Asset by ID |
Splunk v2 | New commands: Upload Files, Start Search, Get Search Status, Get Search Result Updated commands: Fetch Event, Get Recent Notable Events, Search Fetch Event: Added support for fetching notable events. All field mappings have been updated accordingly to support this change. Submit Event: Enhanced to allow an event to be created with an event JSON object. Search & Get Recent Notable Events: Updated to trigger a 2-step API call, initiating a search using startSearch and retrieving results using getResult to obtain events. Search: Enhanced to handle more flexible search statements, including tstats. Converted all existing C# commands to Python |
Trend Micro Cloud One | Added the "User-Agent" header with the value "TrendMicroCloudOne-D3-Integration-v1" to each command sent, providing identification and information about the integration making the request. |
VirusTotal v3 | Get IP Report & Get Domain Report: Enhanced to parse and convert WHOIS data retrieved from the path $.data.attributes.whois into JSON format, displaying it under the field $.data.attributes.whois_json. This change is only applicable for raw data and context data outputs. |
Deprecated Integration Commands
The following integrations have been deprecated in this release of D3 SOAR.
Integration Name | Deprecated Commands |
AlienVault OTX | Get Pulse Details Search Pulses Check IP Reputation Get Domain Information Get URL Information Get File Information |
Azure Active Directory | Get Managed Device List Managed Devices |
CrowdStrike | Execute Command On Single Endpoint |
Microsoft Exchange Server | Block Email Fetch Event Search Email Remove Email |
Google Chronicle Search API | Fetch Event by Rule Run Rule Get Operation Status Update Rule Get Rules Results Get Rules Create Rule |
Google Cloud PubSub | Fetch Event |
iZOOLogic | List Authorised Executives List Clients Fetch Event List Brands |
MongoDB | Create DB |
Recorded Future | Check IP Reputation |
Sophos Central | Fetch Event |
Trend Micro Cloud One | Remove Domain Entries From Permit List Add Domains To Permit List Create Domain Filter Configuration List Domain Policy Configurations Distribute Permit List And Domain Filter To Appliances Update Domain Filter Config Status |
VirusTotal v3 | Get Sigma Analysis Reports |
Zendesk | Add User Fetch Event |
.png)