Trellix McAfee ePO
LAST UPDATED: AUG 5, 2025
Overview
McAfee ePolicy Orchestrator (McAfee ePO) centralizes and streamlines the management of endpoint, network, data security, and compliance solutions.
D3 SOAR is providing REST operations to function with Trellix McAfee ePO.
Trellix McAfee ePO is available for use in:
D3 SOAR | V12.7.83.0+ |
Category | Endpoint Security |
Deployment Options |
Connection
To connect to Trellix McAfee ePO from D3 SOAR, please follow this part to collect the required information below:
Parameter | Description | Example |
Server URL | The URL of the Trellix McAfee ePO server. | https://1.1.1.1:8443 |
Username | The username for authentication. | admin |
Password | The password for authentication. | D**ec**it** |
Permission Requirements
Each endpoint in the Trellix McAfee ePO API requires a certain permission scope. The following are required scopes for the commands in this integration:
Command | Permission Set | Required Permissions |
Add Tag | N/A | Administrator |
Assign Policy To System | N/A | Administrator |
Check Latest DAT | Software |
|
Check Repository Compliance | Software |
|
Determine Repository | Software |
|
Fetch Event | Queries and Reports | Queries and Reports: Use public groups; create and edit private queries/reports |
Find Client Task | McAfee Agent | McAfee Agent (Tasks): View settings |
Find Group | System Tree access | Select My Organization |
Find Groups | System Tree access | Select My Organization |
Find Package | Software | Master Repository: View packages |
Find Policy | Data Loss Prevention |
|
Find Repository | Software |
(These permissions will only return limited information, only the Administrator access can return all repository) |
Find System | Systems | System Tree: View "System Tree" tab |
Find System By Tag Name | Queries and Reports | Queries and Reports: Use public groups |
Find System In Group | Queries and Reports | Queries and Reports: Use public groups |
System Tree access | Select My Organization | |
Find Systems By Group IDs | Queries and Reports | Queries and Reports: Use public groups |
System Tree access | Select My Organization | |
Find Tag | Systems | Tag use: Apply, exclude, and clear tags |
Get Device Info | Queries and Reports | Queries and Reports: Use public groups |
System Tree access | Select My Organization | |
Get DLP Incident | Incident Management |
|
Queries and Reports | Queries and Reports: Use public groups; create and edit private queries/reports. | |
Get Task Info By Product Object | Endpoint Security Threat Prevention | Endpoint Security Threat Prevention (Tasks): View settings |
Get Threat Events | Queries and Reports | Queries and Reports: Use public groups |
Threat Event Log | Threat Event Log: View events | |
Get Version | N/A | Administrator |
eList All Server Task | Server tasks | Server tasks: View Scheduler tasks; view Scheduler task results in the Server Task Log |
List Database | N/A | Administrator |
List Data Type | Queries and Reports | Queries and Reports: Use public groups |
List Permission Set | N/A | Administrator |
List Query | Queries and Reports | Queries and Reports: Use public groups |
List Repository | Software |
|
List Running Server Task | Server tasks | Server tasks: View Scheduler tasks; view Scheduler task results in the Server Task Log |
List Sub Task History | Server tasks | Server tasks: View Scheduler tasks; view Scheduler task results in the Server Task Log |
List Table | Queries and Reports | Queries and Reports: Use public groups; create and edit private queries/reports. |
List Task History | Server tasks | Server tasks: View Scheduler tasks; view Scheduler task results in the Server Task Log |
List User | N/A | Administrator |
Remove Tag | N/A | Administrator |
Repo List | Software |
|
Retrieve Current DAT Version | Software |
|
Run Client Task | N/A | Administrator |
Scan End Point By IP | Software |
|
Scan End Points By Group Name | System Tree access | Select My Organization |
Scan End Points By Tag Name | N/A | Administrator |
Search Threat Events | N/A | Administrator |
Update Endpoints | N/A | Administrator |
Update Repository | N/A | Administrator |
Wake Up Agent | Systems | Actions: Wake up agents; view Agent Activity Log |
Test Connection | N/A | No permissions needed |
As Trellix McAfee ePO is using role-based access control (RBAC), the D3 connector will be generated based on a specific user account and the application. Therefore, the command permissions are inherited from the user account’s role. Users need to configure their user profile from the Trellix McAfee ePO console for each command in this integration.
READER NOTE
The Administrator role is required to run certain commands. Refer to step 3d of the Creating a User section for more information.
The Find Repository command required the Administrator role to retrieve all results. The minimum permissions listed in the table above will only yield partial results.
Configuring Trellix McAfee ePO to Work with D3 SOAR
Creating a User
Once logged into your Trellix McAfee ePO environment, navigate to User Management > Users.
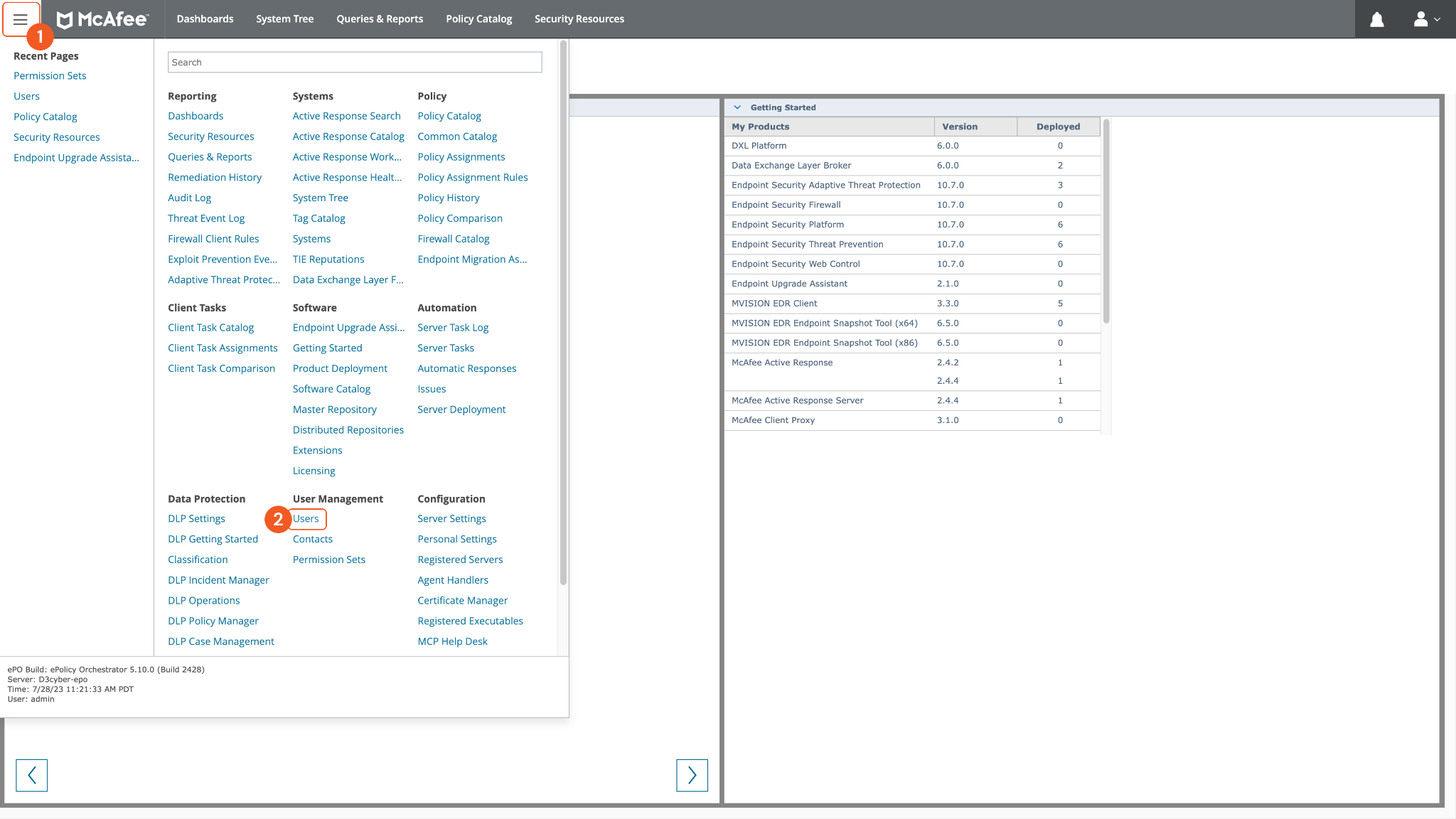
Click on New User.
Configure the new user.
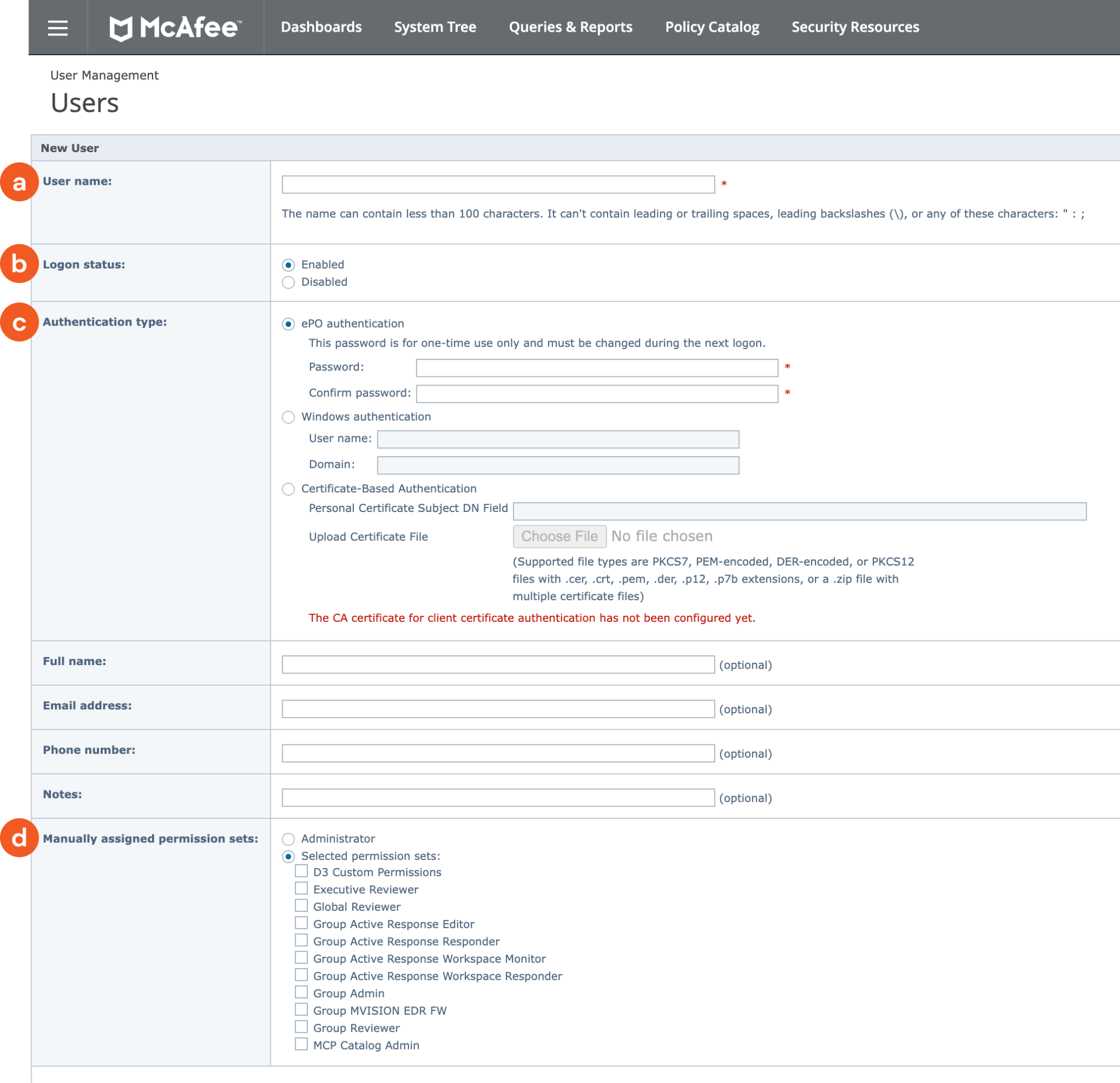
Enter a user name. This will be the username used to establish and authenticate your connection in D3 SOAR.
Determine whether to enable or disable the logon status for this account. If the account is for someone who is not yet part of the organization, disabling it might be preferable.
Select ePO authentication. Enter a temporary password for the user account. The password must be changed upon initial login, which will also be used to establish and authenticate your connection in D3 SOAR.
Decide whether to grant administrative privileges or select appropriate permission sets for the user.
Click Save to complete the process.
Adding and Editing a Permission Set
Once logged into your Trellix McAfee ePO environment, navigate to User Management > Permission Sets.
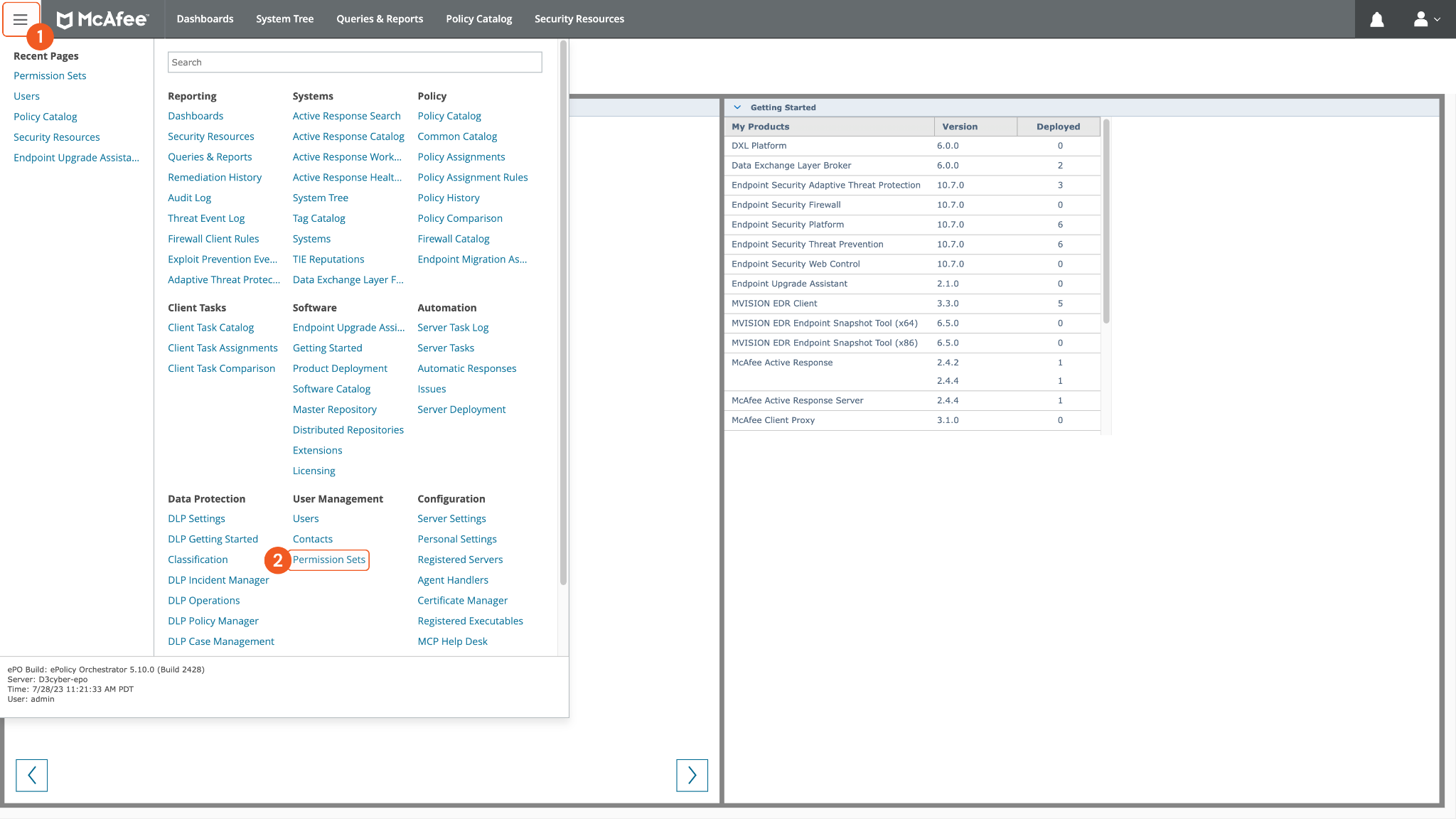
Add or edit a permission set.
Add a permission set:
Click New Permission Set.
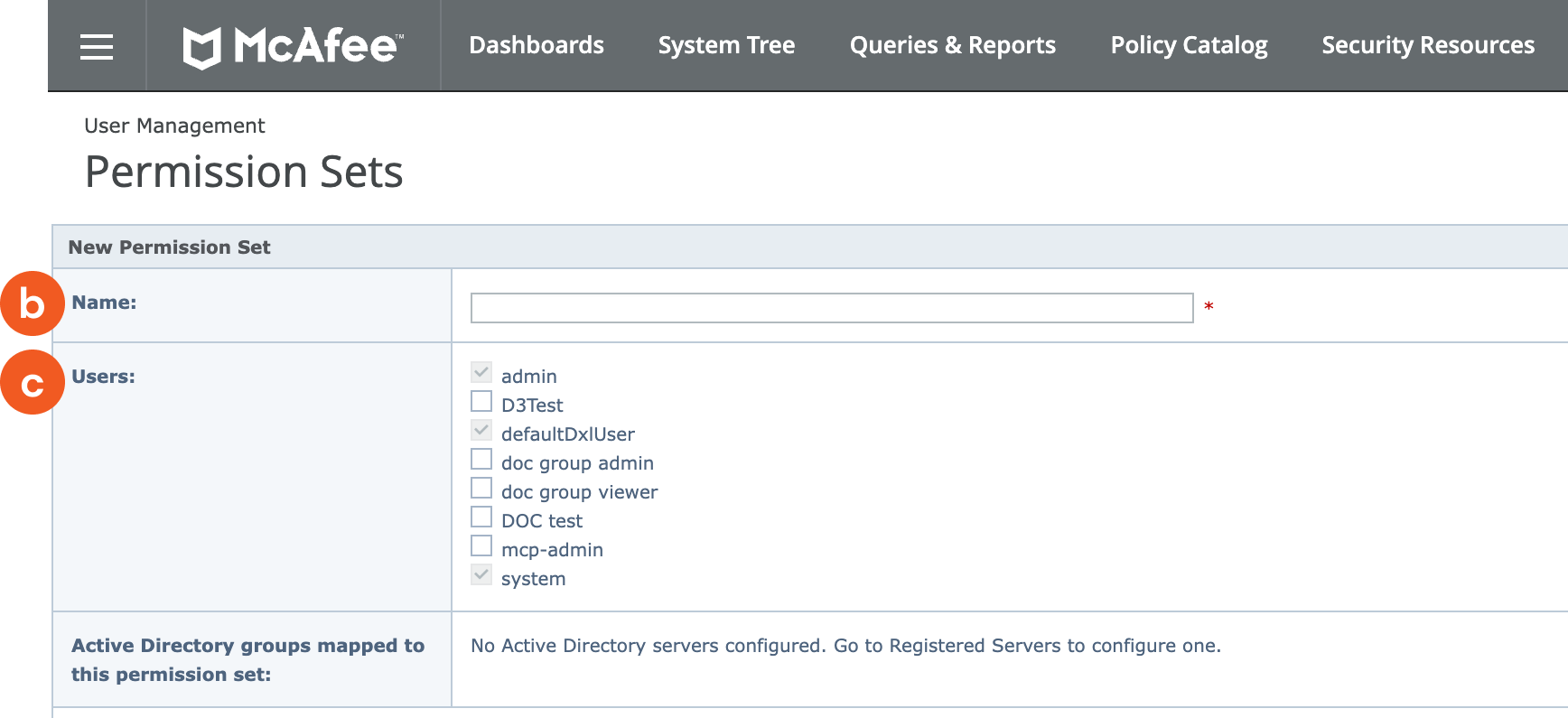
Enter a unique name for the new permission set.
Assign specific users to this permission set by selecting their usernames.
Click Save.
Edit a permission set:
Select the desired permission set to modify.
Locate the Name and users permission. Click Edit to add or remove permissions to the user. Click Save.
Repeat the same steps to modify other permissions within the permission set.
Configuring D3 SOAR to Work with Trellix McAfee ePO
Log in to D3 SOAR.
Find the Trellix McAfee ePO integration.
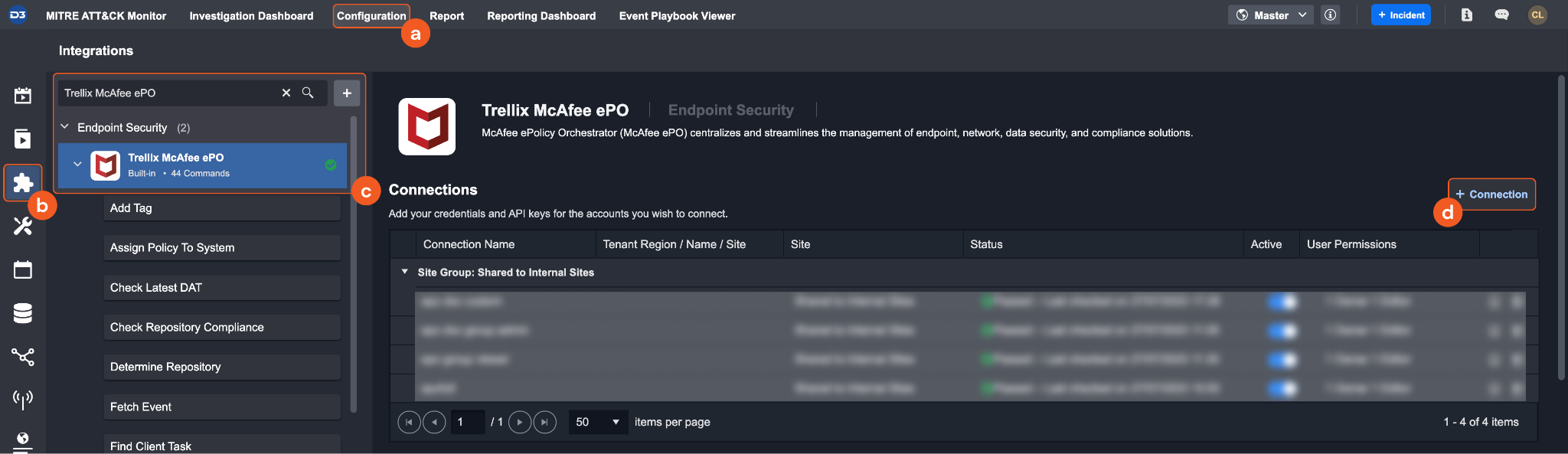
Navigate to Configuration on the top header menu.
Click on the Integration icon on the left sidebar.
Type Trellix McAfee ePO in the search box to find the integration, then click it to select it.
Click + New Connection, on the right side of the Connections section. A new connection window will appear.
Configure the following fields to create a connection to Trellix McAfee ePO.
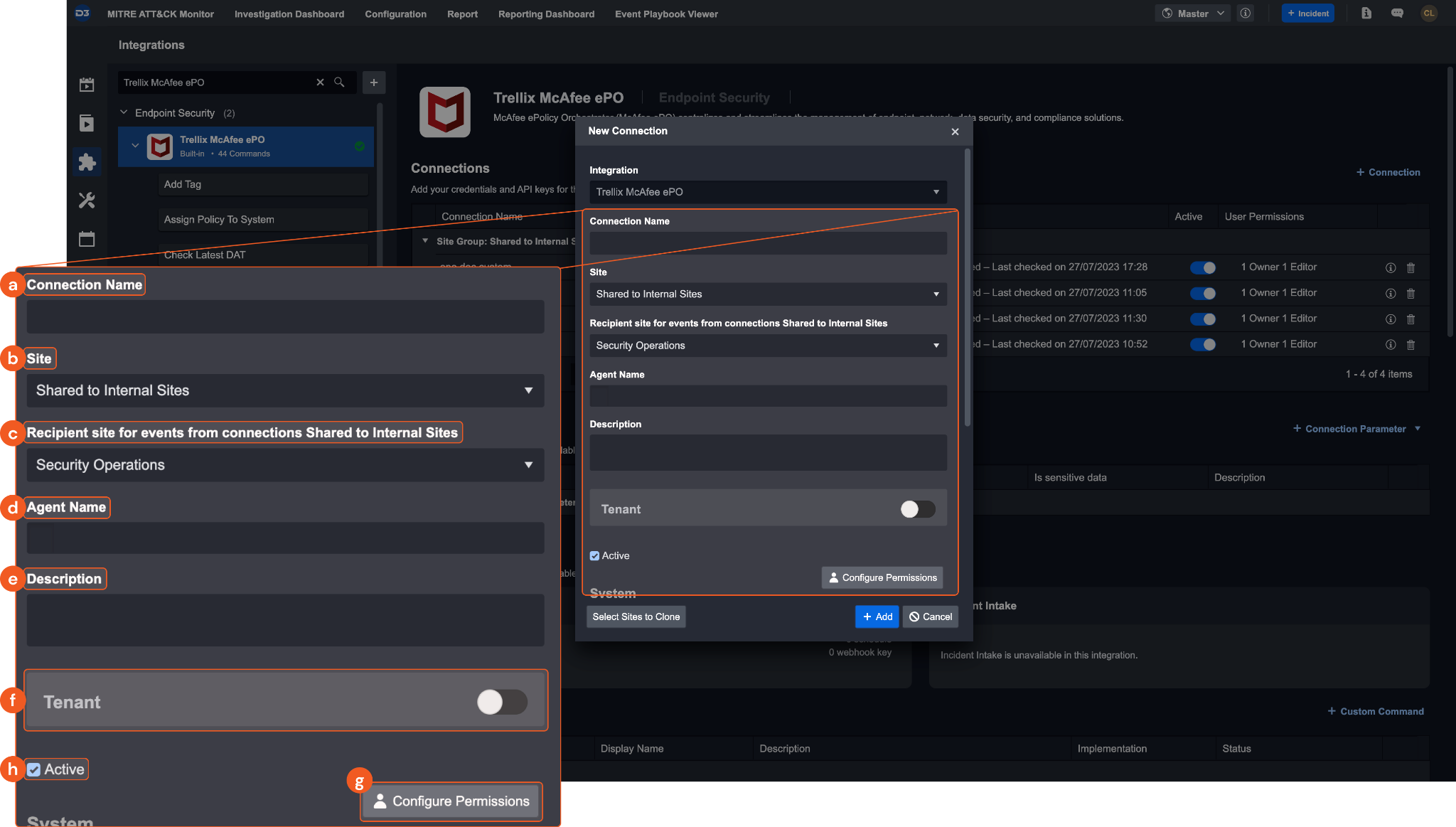
Connection Name: The desired name for the connection.
Site: The site on which to use the integration connection. Use the drop-down menu to select the site. The Share to Internal Sites option enables all internal sites to use the connection. Selecting a specific site will only enable that site to use the connection.
Recipient site for events from connections Shared to Internal Sites: This field is displayed when Share to Internal Sites is selected for the Site field, allowing selection of the internal site for deploying the integration connection.
Agent Name (Optional): The proxy agent required to build the connection. Use the dropdown menu to select the proxy agent from a list of previously configured proxy agents.
Description (Optional): The description for the connection.
Tenant (Optional): When configuring the connection from a master tenant site, users can choose the specific tenant sites with which to share the connection. Once this setting is enabled, users can filter and select the desired tenant sites from the dropdowns to share the connection.
Configure User Permissions: Defines which users have access to the connection.
Active: The checkbox that enables the connection to be used when selected.
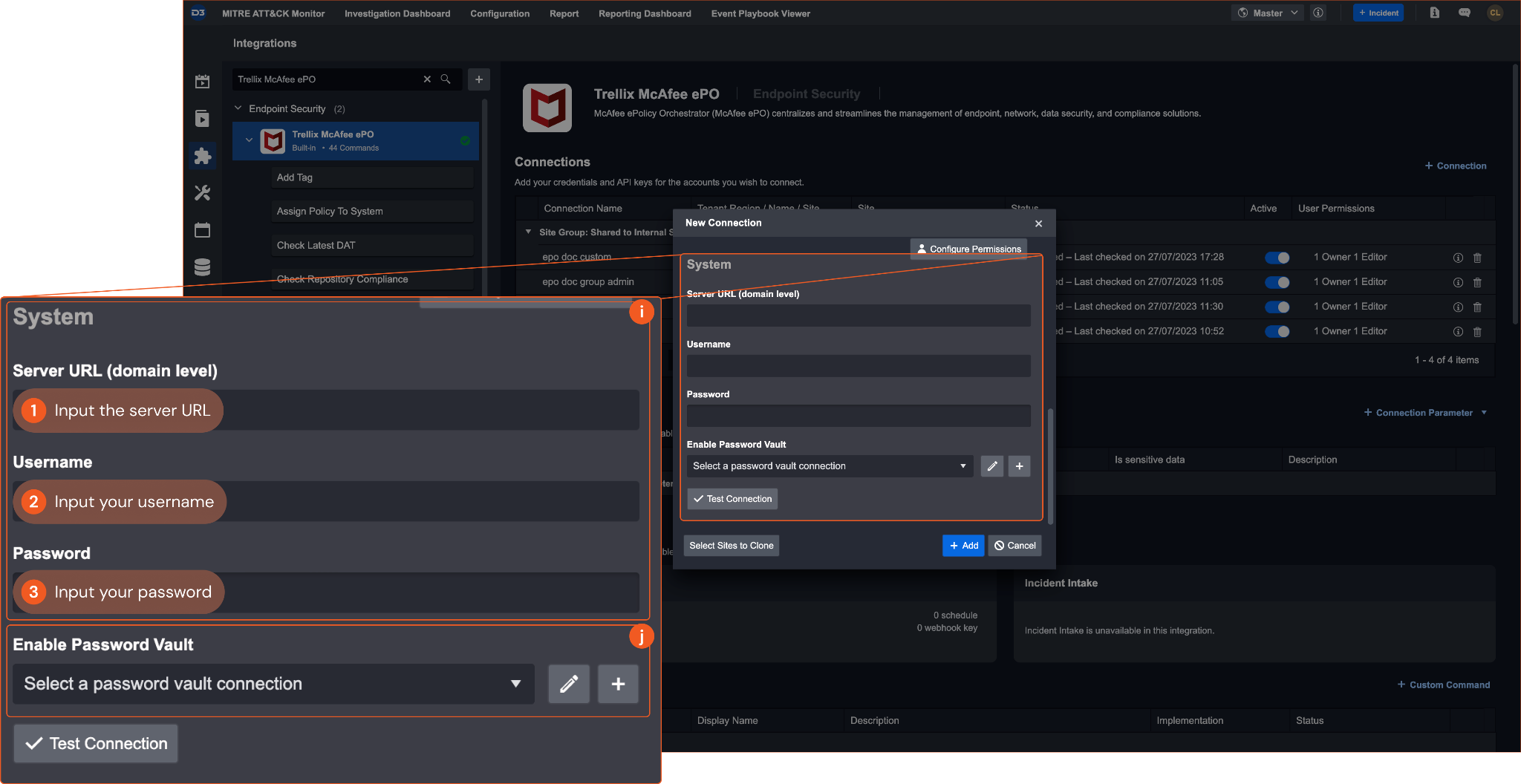
System: This section contains the parameters defined specifically for the integration. These parameters must be configured to create the integration connection.
1. Input the Server URL of your Trellix McAfee ePO environment.
2. input your Username.
3. Input your Password.Enable Password Vault: An optional feature that allows users to take the stored credentials from their own password vault. Refer to the password vault connection guide if needed.
Test the connection.
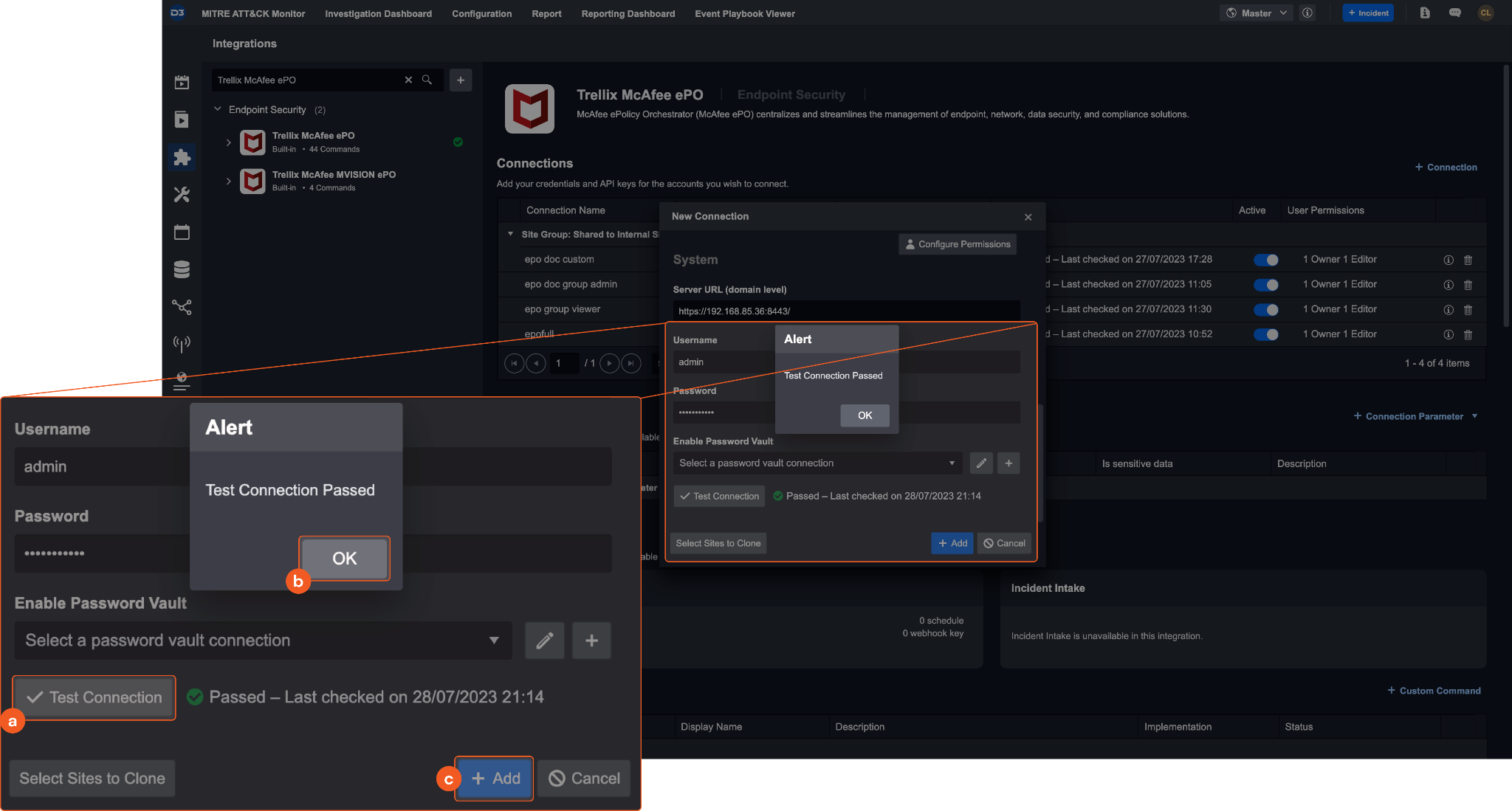
Click on the Test Connection button to verify credentials and connectivity. A success alert displays Passed with a green checkmark. If the connection fails, review the parameters and retry.
Click OK to close the alert window.
Click + Add to create and add the configured connection.
Commands
Trellix McAfee ePO includes the following executable commands for users to set up schedules or create playbook workflows. With the Test Command, users can execute these commands independently for playbook troubleshooting.
Integration API Note
For more information about the Trellix McAfee ePO API, refer to the Trellix McAfee ePO API reference.
READER NOTE
Certain permissions are required for each command. Refer to the Permission Requirements and Configuring Trellix McAfee ePO to Work with D3 SOAR for details.
Note for Time-related parameters
The input format of time-related parameters may vary based on user account settings, which may cause the sample data in commands to differ from what is displayed. To adjust the time format, follow these steps:
Navigate to Configuration > Application Settings. Select Date/Time Format.
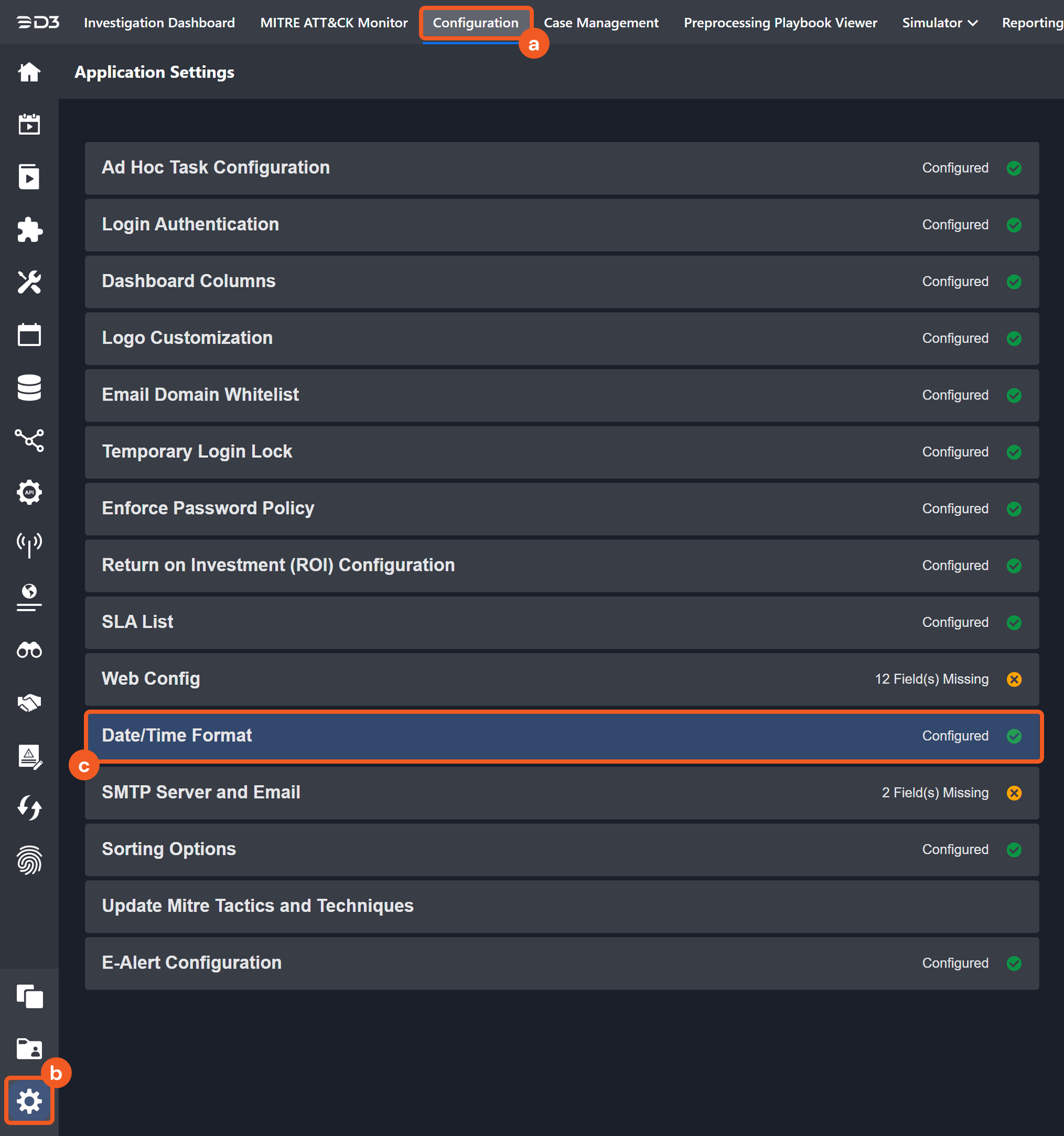
Choose the desired date and time format, then click on the Save button.
The selected time format will now be visible when configuring Date/Time command input parameters.
Add Tag
Adds a tag to an endpoint in McAfee ePO.
Input
Input Parameter | Required/Optional | Description | Example |
Endpoint | Required | The endpoint to add a tag. | dc_auto_mtrg |
Tag Name | Required | The name of the tag to add to the specified endpoint. | YABINGUO |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Add Tag failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Error 0 :\r\n\r\n. |
Error Sample Data Add Tag failed. Status Code: 400. Message: Error 0 :\r\n\r\n. |
Assign Policy To System
Assigns a policy to specified endpoints.
Input
Input Parameter | Required/Optional | Description | Example |
Endpoints | Required | The list of endpoints to assign a policy. | d*****-dc |
Product ID | Required | The product ID to assign to the specified endpoints. | 1 |
Type ID | Required | The type ID to assign to the specified endpoints. | 69 |
Object ID | Required | The object ID to assign to the specified endpoints. | 1 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Assign Policy To System failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unable to take action on the computer because it may not exist. |
Error Sample Data Assign Policy To System failed. Status Code: 404. Message: Unable to take action on the computer because it may not exist. |
Check Latest DAT
Returns the latest DAT version.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Check Latest DAT failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Check Latest DAT failed. Status Code: 401. Message: Unauthorized. |
Check Repository Compliance
Checks repository compliance based on the specified DAT version.
READER NOTE
Required DAT Version is a required parameter to run this command.
The latest Required DAT Version can be found from the Check Latest DAT command in the returned raw data at the path $.LatestDATVersion.
Input
Input Parameter | Required/Optional | Description | Example |
Required DAT Version | Required | The DAT version number to check repository compliance. | 9472 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Check Repository Compliance failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: could not convert string to float. |
Error Sample Data Check Repository Compliance failed. Status Code: 400. Message: could not convert string to float. |
Determine Repository
Returns details of the specified repository.
Input
Input Parameter | Required/Optional | Description | Example |
Repository Name | Required | The name of the repository to retrieve details. | ePO_***-AD |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Determine Repository failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Determine Repository failed. Status Code: 401. Message: Unauthorized. |
Fetch Event
Retrieves events from Trellix McAfee ePO based on the specified criteria.
Input
Input Parameter | Required/Optional | Description | Example |
Start Time | Optional | The start time of the time range to fetch events after the specified time stamp, in UTC time. | 2020-01-01 00:00 |
End Time | Optional | The end time of the time range to fetch events before the specified time stamp, in UTC time. | 2020-10-01 00:00 |
Number of Event(s) Fetched | Optional | The maximum number of the most recent events to return. | 100 |
Search Condition | Optional | The query string defining the search condition for fetching events. For more information about the query syntax, refer to the Trellix McAfee ePO API documentation. Note: The input severity value must be an integer. The severity values are defined as follows: 0-Info, 1-Warning, 2-Minor, 3-Major, 4-Critical. | Condition for search Events: (where (eq EPOEvents.ThreatType "trojan" )) Condition for search DLP Incidents ( where (and (eq UDLP_Incidents.Severity "3") (eq UDLP_IncidentStatuses.StatusKey "NEW") ) ) |
Is DLP Incident | Optional | The option to fetch DLP incidents as events. The default value is No. | Yes |
Output
To view the sample output data for all commands, refer to this article.
Fetch Event Field Mapping
Please note that Fetch Event commands require event field mapping. Field mapping plays a key role in the data normalization process part of the event pipeline. Field mapping converts the original data fields from the different providers to the D3 fields which are standardized by the D3 Model. Please refer to Event and Incident Intake Field Mapping for details.
If you require a custom field mapping, click + Add Field to add a custom field mapping. You can also remove built-in field mappings by clicking x. Please note that two underscore characters will automatically prefix the defined Field Name as the System Name for a custom field mapping. Additionally, if an input Field Name contains any spaces, they will automatically be replaced with underscores for the corresponding System Name.
The Trellix McAfee ePO integration in D3 SOAR has separate pre-configured field mappings for events and DLP incidents since the returned raw data to both fields are different, which correspond to the Default Event Source and DLP Incidents mappings:
Default Event Source
Configures the field mapping which are specific to the events. If a source field in the field mapping is not found, the corresponding field mapping will be ignored. The default event source has a “Main Event JSON Path” (i.e., $) that is used to extract a batch of events from the response raw data. Click Edit Event Source to view the “Main Event JSON Path”.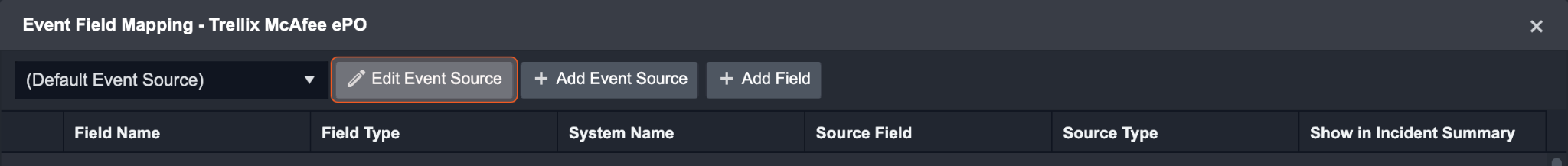
Main Event JSON Path: $
The Main Event JSON Path determines the root path where the system starts parsing raw response data into D3 event data. The JSON path begins with $, representing the root element. The path is formed by appending a sequence of child elements to $, each separated by a dot (.). Square brackets with nested quotation marks ([‘...’]) should be used to separate child elements in JSON arrays.
For example, the root node of a JSON Path is $. The child node denoting the Unique Event Key field would be AutoGUID. Putting it together, the JSON Path expression to extract the Unique Event Key is $.AutoGUID.
Event Source for DLP Incidents
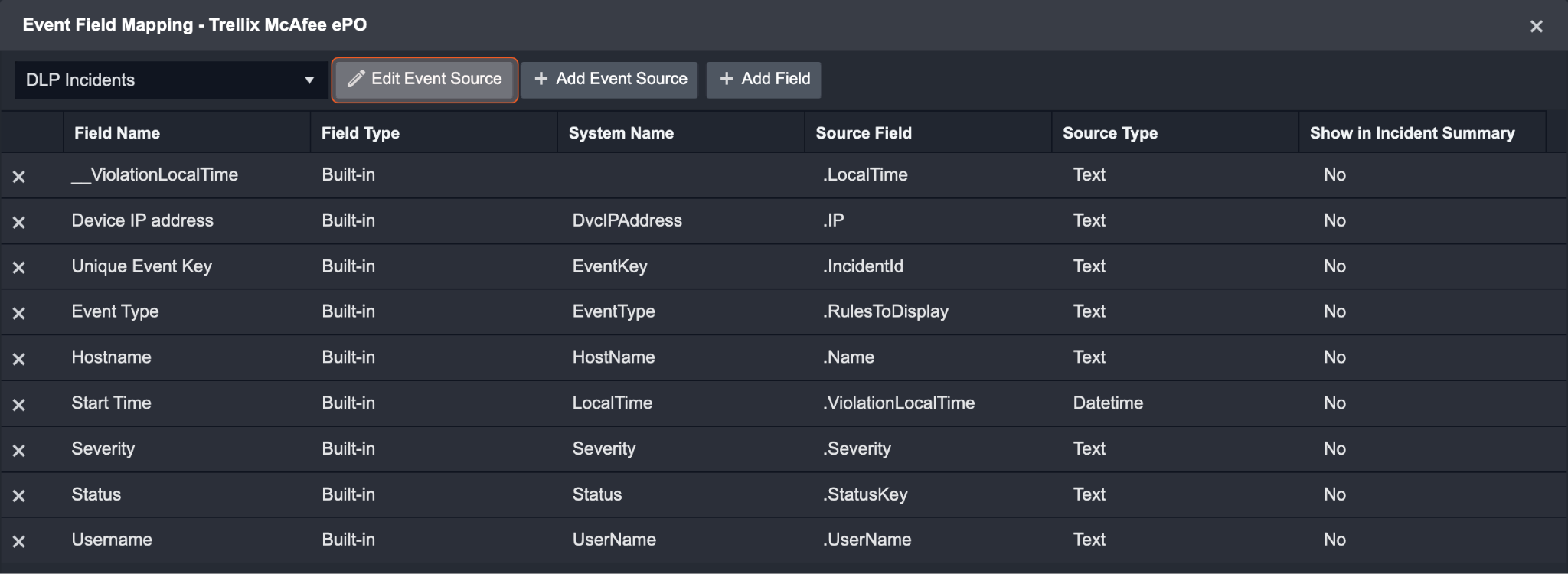
Configures the field mapping which are specific to the DLP Incidents. If a source field in the field mapping is not found, the corresponding field mapping will be ignored. As the data of the DLP Incidents have a character that the value of the IsDLPIncident field is True, the DLP Incidents can be defined by the Search String: {$.IsDLPIncident}=True. Click Edit Event Source to view the Search String.
The pre-configured field mappings are detailed below:
Field Name | Source Field |
Default Event Source (Main Event JSON Path: $) | |
None | .AnalyzerDATVersion |
None | .AnalyzerDetectionMethod |
None | .AnalyzerEngineVersion |
None | .AnalyzerHostName |
None | .AnalyzerIPV4 |
None | .AnalyzerMAC |
None | .AnalyzerName |
None | .AnalyzerVersion |
Application layer protocol | .TargetProtocol |
Call trace | .SourceDescription |
Destination IP address | .TargetIPV4 |
Destination port | .TargetPort |
Destination MAC | .TargetMAC |
Driver image path | .TargetFileName |
Unique Event Key | .AutoGUID |
EventTime/UtcTime | .DetectedUTC |
Event Type | .ThreatType |
Filename | .TargetFileName |
ParentImage | .SourceParentProcessName |
Parent process name | .SourceParentProcessName |
Process command line | .SourceDescription |
Process file path | .SourceFilePath |
Process Hash | .SourceProcessHash |
Process Name | .SourceProcessName |
Receipt time | .TargetCreateTime |
Registry path | TargetFileName |
Source hostname | .SourceHostName |
Source IP address | .SourceIPV4 |
Source port | .SourcePort |
Source MAC address | .SourceMAC |
Source username | .SourceUserName |
None | .TargetHostName |
Target image | .TargetFileName |
Target process name | .TargetProcessName |
Threat action taken | .ThreatActionTaken |
Threat event ID | .ThreatEventID |
Threat handled | .ThreatHandled |
Threat name | .ThreatName |
Threat severity | .ThreatSeverity |
Threat type | .ThreatType |
URL | .TargetURL |
Username | .TargetUserName |
Start time (UTC) | .DetectedUTC |
Event Source for DLP Incidents (Search String: {$.IsDLPIncident}=True) The search string format is {jsonpath}=value. If the value of the IsDLPIncident key is True in the event object under raw data, then the DLP Incidents will use the field mapping below. | |
__ViolationLocalTime | .LocalTime |
Device IP address | .IP |
Unique Event Key | .IncidentId |
Event Type | .RulesToDisplay |
Hostname | .Name |
Start Time | .ViolationLocalTime |
Severity | .Severity |
Status | .StatusKey |
Username | .UserName |
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Fetch Event failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: This error might be caused by incorrect search condition. Please refer to sample data for syntax of search condition. Also, you can refer to McAfee document <https://docs.mcafee.com/bundle/epolicy-orchestrator-web-api-reference-guide/page/GUID-***-***-***-***-***.html> for detailed syntax. |
Error Sample Data Fetch Event failed. Status Code: 400. Message: This error might be caused by incorrect search condition. Please refer to sample data for syntax of search condition. Also, you can refer to McAfee document <https://docs.mcafee.com/bundle/epolicy-orchestrator-web-api-reference-guide/page/GUID-***-***-***-***-***.html> for detailed syntax. |
Find Client Task
Retrieves client task details based on the provided search text.
Input
Input Parameter | Required/Optional | Description | Example |
Search Text | Optional | The search text defining the condition to retrieve client task details. | Endpoint Security Threat Prevention |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Find Client Task failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Find Client Task failed. Status Code: 401. Message: Unauthorized. |
Find Group
Retrieves group information based on the provided search text.
Input
Input Parameter | Required/Optional | Description | Example |
Search Text | Optional | The search text defining the condition to retrieve group information. | AD Domain Controllers |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Find Group failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Find Group failed. Status Code: 401. Message: Unauthorized. |
Find Groups
Retrieves a list of all groups.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Find Groups failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Find Groups failed. Status Code: 401. Message: Unauthorized. |
Find Package
Retrieves packages based on the provided search text.
Input
Input Parameter | Required/Optional | Description | Example |
Search Text | Optional | The search text defining the condition to retrieve packages. | all |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Find Package failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Find Package failed. Status Code: 401. Message: Unauthorized. |
Find Policy
Retrieves ePO policies based on the provided search text.
Input
Input Parameter | Required/Optional | Description | Example |
Search Text | Optional | The search text defining the condition to retrieve policies. | My Default |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Find Policy failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Find Policy failed. Status Code: 401. Message: Unauthorized. |
Find Repository
Retrieves an ePO repository based on the provided search text.
Input
Input Parameter | Required/Optional | Description | Example |
Search Text | Optional | The search text defining the condition to retrieve a repository. | 3 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Find Repository failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Find Repository failed. Status Code: 401. Message: Unauthorized. |
Find System
Retrieves system information based on the provided name or IP address.
Input
Input Parameter | Required/Optional | Description | Example |
Search Text | Optional | The IP address or name of the system to search. | ***-DC |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Find System failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Find System failed. Status Code: 401. Message: Unauthorized. |
Find System By Tag Name
Retrieves system information based on the provided tag name.
READER NOTE
Tag Name is a required parameter to run this command.
Run the Find Tag command to obtain Tag Name. Tag Names can be found in the returned raw data at the path $[*].tagName.
Input
Input Parameter | Required/Optional | Description | Example |
Tag Name | Required | The name of the tag to retrieve system information. Tag Name can be obtained using the Find Tag command. | ***-DC |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Find System By Tag Name failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Find System By Tag Name failed. Status Code: 401. Message: Unauthorized. |
Find System In Group
Retrieves system information within the specified ePO group.
READER NOTE
Group ID is a required parameter to run this command.
Run the Find Group or Find Groups command to obtain Group ID. Group IDs can be found in the returned raw data at the path $[*].groupId.
If the provided group ID cannot be found, this command will return success with no results.
Input
Input Parameter | Required/Optional | Description | Example |
Group ID | Required | The ID of the group to retrieve system information. Group IDs can be obtained using the Find Group or Find Groups commands. | 2 |
Search Subgroups? | Optional | The option to include results within subgroups. | True |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Find System In Group failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Find System In Group failed. Status Code: 401. Message: Unauthorized. |
Find Systems By Group IDs
Retrieves system information based on the provided group IDs.
READER NOTE
Group ID is a required parameter to run this command.
Run the Find Group or Find Groups commands to obtain Group ID. Group IDs can be found in the returned raw data at the path $[*].groupId.
Input
Input Parameter | Required/Optional | Description | Example |
Group IDs | Optional | The IDs of the groups to retrieve system information. Group IDs can be obtained using the Find Group or Find Groups commands. | ["5"] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Find Systems By Group IDs failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Expecting value: line 1 column 1 (char 0). |
Error Sample Data Find Systems By Group IDs failed. Status Code: 400. Message: Expecting value: line 1 column 1 (char 0). |
Find Tag
Retrieves tag information based on the provided search text.
Input
Input Parameter | Required/Optional | Description | Example |
Search Text | Optional | The search text containing the keywords to retrieve tag information. If there are no matches with the search keywords, the command will indicate success with no results. | TestTag |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Find Tag failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Find Tag failed. Status Code: 401. Message: Unauthorized. |
Get Device Info
Retrieves system information on the specified hosts.
Input
Input Parameter | Required/Optional | Description | Example |
IPs or Hostnames | Optional | The IP addresses or hostnames to retrieve system information. | ["1.1.1.1"] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Device Info failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Get Device Info failed. Status Code: 401. Message: Unauthorized. |
Get DLP Incident
Retrieves DLP incidents.
Input
Input Parameter | Required/Optional | Description | Example |
Start Time | Optional | The start time of the time range to retrieve DLP incidents, in UTC time. | 2021-01-11 00:00 |
End Time | Optional | The end time of the time range to retrieve DLP incidents, in UTC time. | 2021-05-11 00:00 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get DLP Incident failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Get DLP Incident failed. Status Code: 401. Message: Unauthorized. |
Get Task Info By Product Object
Retrieves task information based on the provided product name and object name.
Input
Input Parameter | Required/Optional | Description | Example |
Product Name | Required | The name of the product to retrieve task information. | Endpoint Security Threat Prevention |
Object Name | Required | The name of the object to retrieve task information. | On-Demand Scan - Quick Scan |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Task Info By Product Object failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Can not get Task info by given productName and objectName. |
Error Sample Data Get Task Info By Product Object failed. Status Code: 404. Message: Can not get Task info by given productName and objectName. |
Get Threat Events
Retrieves threat events based on the specified criteria.
Input
Input Parameter | Required/Optional | Description | Example |
Event Time | Optional | The timestamp to retrieve events, in UTC time. | 2019-11-24 00:00 |
Time Before | Optional | The amount of time prior to the specified event time to retrieve events. | -3d |
Time After | Optional | The amount of time after the specified event time to retrieve events. | 2d |
IP Addresses | Optional | The IP addresses to retrieve relevant events. | ["1.1.1.1"] |
Unhandled or All Threats? | Optional | The option to retrieve only unhandled threats or all threats. | unhandled |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Threat Events failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Get Threat Events failed. Status Code: 401. Message: Unauthorized. |
Get Version
Retrieves the ePO version.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Version failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Get Version failed. Status Code: 401. Message: Unauthorized. |
List All Server Task
Retrieves a list of all server tasks.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List All Server Task failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data List All Server Task failed. Status Code: 401. Message: Unauthorized. |
List Database
Retrieves a list of all databases.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Database failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data List Database failed. Status Code: 401. Message: Unauthorized. |
List Data Type
Retrieves all data types.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Data Type failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data List Data Type failed. Status Code: 401. Message: Unauthorized. |
List Permission Set
Retrieves a list of permission sets.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Permission Set failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data List Permission Set failed. Status Code: 401. Message: Unauthorized. |
List Query
Retrieves a list of all queries.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
ErrorHandling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Query failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data List Query failed. Status Code: 401. Message: Unauthorized. |
List Repository
Retrieves a list of all repositories.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Repository failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data List Repository failed. Status Code: 401. Message: Unauthorized. |
List Running Server Task
Retrieves a list of running server tasks.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Running Server Task failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data List Running Server Task failed. Status Code: 401. Message: Unauthorized. |
List Sub Task History
Retrieves a list of subtask history based on the provided task log ID.
READER NOTE
Task Log ID is a required parameter to run this command.
Run the List Running Server Task command to obtain Task Log ID. Task Log IDs can be found in the returned raw data at the path $[*].taskLogId.
Input
Input Parameter | Required/Optional | Description | Example |
Task Log ID | Required | The ID of the task log to retrieve corresponding subtask history. Task log IDs can be obtained using the List Running Server Task command. | 8*****7 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Sub Task History failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: 'taskLogId' must be an integer less than 9223372036854775808. |
Error Sample Data List Sub Task History failed. Status Code: 400. Message: 'taskLogId' must be an integer less than 9223372036854775808. |
List Table
Retrieves a list of all tables.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Table failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data List Table failed. Status Code: 401. Message: Unauthorized. |
List Task History
Retrieves a list of all task histories.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Task History failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data List Task History failed. Status Code: 401. Message: Unauthorized. |
List User
Retrieves a list of all users.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List User failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data List User failed. Status Code: 401. Message: Unauthorized. |
Remove Tag
Removes tags from endpoints in ePO.
READER NOTE
Tag Name is a required parameter to run this command.
Run the Find Tag command to obtain Tag Name. Tag Names can be found from the returned raw data at the path $[*].tagName.
In the case that the provided tag information does not exist, the following message will be returned: "Tag SERVER has been successfully removed from 0 endpoint(s)."
Input
Input Parameter | Required/Optional | Description | Example |
Endpoints | Required | The endpoints to remove tags. | dc_auto_*** |
Tag Name | Required | The names of the tags to remove from the specified endpoints. Tag name can be obtained using the Find Tag command. | YABINGUO |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Remove Tag failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Remove Tag failed. Status Code: 401. Message: Unauthorized. |
Repo List
Retrieves a list of repositories.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Repo List failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Repo List failed. Status Code: 401. Message: Unauthorized. |
Retrieve Current DAT Version
Retrieves the current DAT version.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Retrieve Current DAT Version failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Retrieve Current DAT Version failed. Status Code: 401. Message: Unauthorized. |
Run Client Task
Runs a client task on Trellix McAfee ePO systems.
Input
Input Parameter | Required/Optional | Description | Example |
System Names | Required | The names of the systems to run the client task on. | ["***-***"] |
Product ID | Required | The product ID of the client task to run. | ENDP_*** |
Task ID | Required | The task ID of the client task to run. | 49 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Run Client Task failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Run Client Task failed. Status Code: 401. Message: Unauthorized. |
Scan End Point By IP
Scans endpoints based on the provided IP addresses.
Input
Input Parameter | Required/Optional | Description | Example |
IP Addresses | Optional | The IP addresses of the endpoints to scan. | ["1.1.1.1"] |
Scan Type | Optional | The option to perform a quick scan or a full scan. | quickscan |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Scan End Point By IP failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: No endpoints found. |
Error Sample Data Scan End Point By IP failed. Status Code: 404. Message: No endpoints found. |
Scan End Points By Group Name
Scan endpoints based on the provided group name.
Input
Input Parameter | Required/Optional | Description | Example |
Group Name | Required | The name of the group to scan endpoints. | AD Domain Controllers |
Scan Type | Optional | The option to perform a quick scan or a full scan. | quickscan |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Scan End Points By Group Name failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: No groups found. Please check the group name you entered. |
Error Sample Data Scan End Points By Group Name failed. Status Code: 404. Message: No groups found. Please check the group name you entered. |
Scan End Points By Tag Name
Scan endpoints based on the provided tag names.
READER NOTE
Tag Name is a required parameter to run this command.
Run the Find Tag command to obtain Tag Name. Tag Names can be found from the returned raw data at the path $[*].tagName.
Input
Input Parameter | Required/Optional | Description | Example |
Tag Name | Optional | The name of the tag to scan tagged endpoints. Tag name can be obtained using the Find Tag command. | Server |
Scan Type | Optional | The option to perform a quick scan or a full scan. | quickscan |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Scan End Points By Tag Name failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Scan End Points By Tag Name failed. Status Code: 401. Message: Unauthorized. |
Search Threat Events
Searches for threat events based on the specified criteria.
Input
Input Parameter | Required/Optional | Description | Example |
Endpoints | Optional | The hostnames or IP addresses of the endpoints to search threat events. | ["1.1.1.1"] |
Start Time | Optional | The start time of the time range to filter searched threat events, in UTC time. | 2019-11-21 00:00 |
End Time | Optional | The end time of the time range to filter searched threat events, in UTC time. | 2019-11-23 00:00 |
Limit | Optional | The maximum number of results to return. | 4 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Search Threat Events failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Search Threat Events failed. Status Code: 401. Message: Unauthorized. |
Update Endpoints
Updates information of an endpoint.
Input
Input Parameter | Required/Optional | Description | Example |
Task ID | Required | The task ID associated with the endpoint to update. | 19 |
Endpoint | Required | The endpoint to update. | ***-dc |
Product ID | Required | The product ID associated with the endpoint to update. | ENDP_*** |
Retry Attempts | Optional | The maximum number of retry attempts allowed. The default value is 1. | 1 |
Retry Interval | Optional | The retry interval in seconds. The default value is 30. | 30 |
Abort After | Optional | The amount of time in minutes after the initial update to abort if not completed. The default value is 5. | 5 |
Stop After | Optional | The maximum allowed runtime for the task in minutes. The default value is 20. | 20 |
Randomize Interval | Optional | The duration of random spread for task execution in minutes. The default value is 0, meaning the update will be executed immediately. | 0 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Endpoints failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Update Endpoints failed. Status Code: 401. Message: Unauthorized. |
Update Repository
Updates a repository.
Input
Input Parameter | Required/Optional | Description | Example |
Source Repository | Required | The source repository to update. | McAfeeHttp |
Target Branch | Required | The updated target branch of the repository. | current |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Repository failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Update Repository failed. Status Code: 401. Message: Unauthorized. |
Wake Up Agent
Wakes up the agent associated with the provided IP addresses or hostnames.
Input
Input Parameter | Required/Optional | Description | Example |
IP or Hostnames | Required | The hostnames or IPv4 addresses to wake up associated agents. | ["1.1.1.1"] |
Wake Up Agent? | Required | The option to wake up the associated agents. | True |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Wake Up Agent failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Trellix McAfee ePO portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: No systems found to wake up. Enter valid computer IDs/names. |
Error Sample Data Wake Up Agent failed. Status Code: 404. Message: No systems found to wake up. Enter valid computer IDs/names. |