ThreatQuotient
LAST UPDATED: AUG 5, 2025
Overview
ThreatQuotient is a threat intelligence platform that collects and interprets intelligence data from open sources and manages indicator scoring, types, and attributes with its Datalinq Engine and Threat Library. The platform helps teams prioritize, automate, and collaborate on security incidents to optimize resources and facilitate strategic decision making in a unified workspace.
D3 SOAR is providing REST operations to function with ThreatQuotient.
ThreatQuotient is available for use in:
D3 SOAR | V12.7.0+ |
Category | Threat Intelligence |
Deployment Options |
Connection
To connect to ThreatQuotient from D3 SOAR, please follow this part to collect the required information below:
Parameter | Description | Example |
Server URL | The server URL used to authenticate the connection. | https://192.***.**.**:**** |
Client ID | The Client ID used to authenticate the connection. Client ID can be obtained from ThreatQ Console > User Management. | ***** |
The email used to authenticate the connection. | info@example.com |
READER NOTE
Users in the Read Only Access or Primary Contributor Access group will need to obtain their Client ID from a user in the Maintenance Account or Administrative Access group.
Permission Requirements
Each endpoint in the ThreatQuotient API requires a certain permission scope. The following are required scopes for the commands in this integration:
Command | Required Permissions | |||
Group (Any checked group will work) | ||||
Read Only Access | Primary Contributor Access | Maintenance Account | Administrative Access | |
Add Attribute | X | ✔ | ✔ | ✔ |
Add Object Tags (From None) | X | ✔ | ✔ | ✔ |
Add Source | X | ✔ | ✔ | ✔ |
Check File Reputation | ✔ | ✔ | ✔ | ✔ |
Check IP Reputation | ✔ | ✔ | ✔ | ✔ |
Check URL Reputation | ✔ | ✔ | ✔ | ✔ |
Check Email Reputation | ✔ | ✔ | ✔ | ✔ |
Check Vulnerability | ✔ | ✔ | ✔ | ✔ |
Create Adversary | X | ✔ | ✔ | ✔ |
Create Event | X | ✔ | ✔ | ✔ |
Create Indicator | X | ✔ | ✔ | ✔ |
Create Object | X | ✔ | ✔ | ✔ |
Delete File | X | ✔ | ✔ | ✔ |
Download File | ✔ | ✔ | ✔ | ✔ |
Fetch Event | ✔ | ✔ | ✔ | ✔ |
Get Object ID by Value | ✔ | ✔ | ✔ | ✔ |
Link Object | X | ✔ | ✔ | ✔ |
List Adversaries | ✔ | ✔ | ✔ | ✔ |
List File | ✔ | ✔ | ✔ | ✔ |
List Indicators | ✔ | ✔ | ✔ | ✔ |
Parse File | X | ✔ | ✔ | ✔ |
Search File Content Type | ✔ | ✔ | ✔ | ✔ |
Test Connection | ✔ | ✔ | ✔ | ✔ |
Unlink Object | X | ✔ | ✔ | ✔ |
Update Indicator Score | X | ✔ | ✔ | ✔ |
Update Indicator Status | X | ✔ | ✔ | ✔ |
Update Object Attribute (From None) | X | ✔ | ✔ | ✔ |
Upload File | X | ✔ | ✔ | ✔ |
As ThreatQuotient is using role-based access control (RBAC), the Client ID is generated based on a specific user account and the application. Therefore, the command permissions are inherited from the user account’s role. Users need to configure their user profile from the ThreatQuotient console for each command in this integration.
READER NOTE
Only users in the Maintenance Account or Administrative Access group will be able to configure user permissions.
Follow these steps to configure user permissions from the ThreatQuotient console:
Click on the settings icon > User Management.
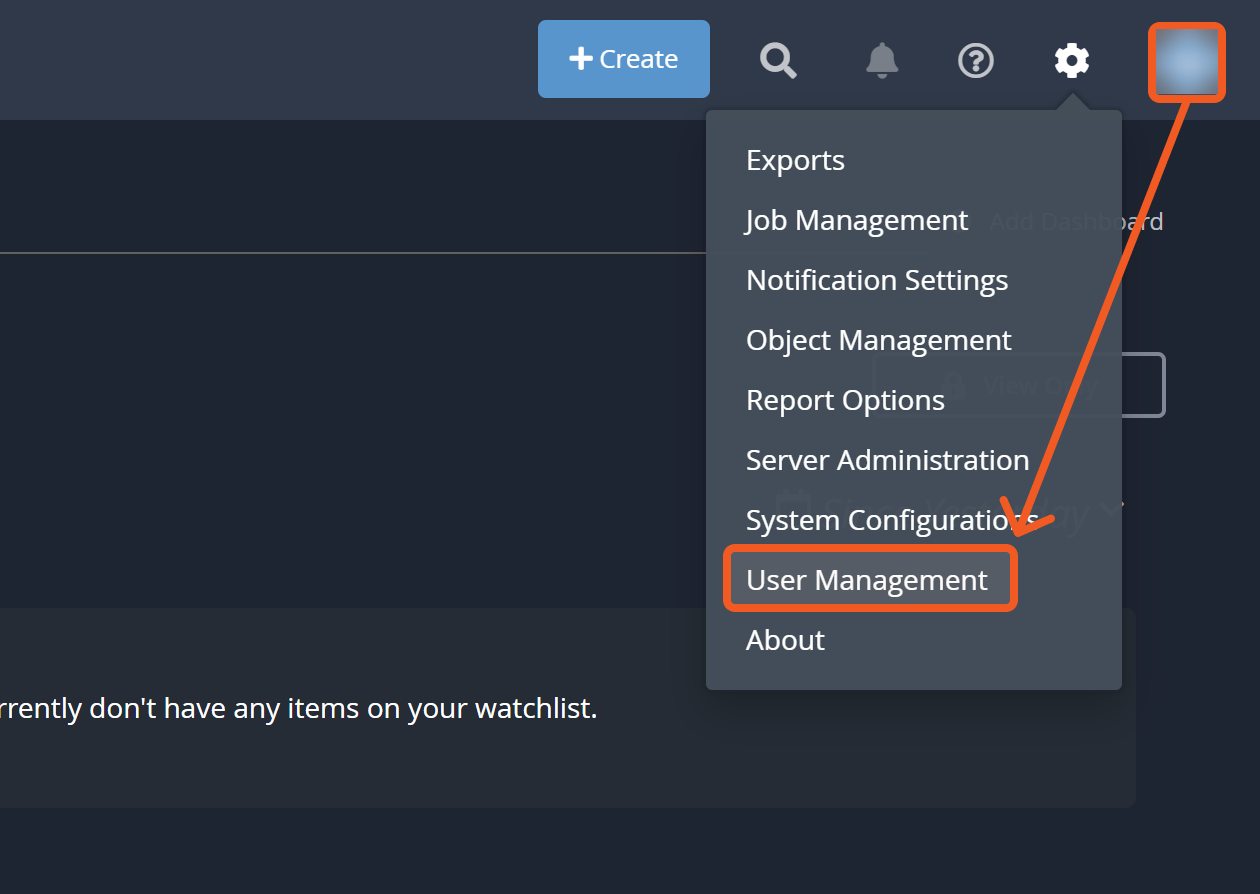
Click on the Add User button.
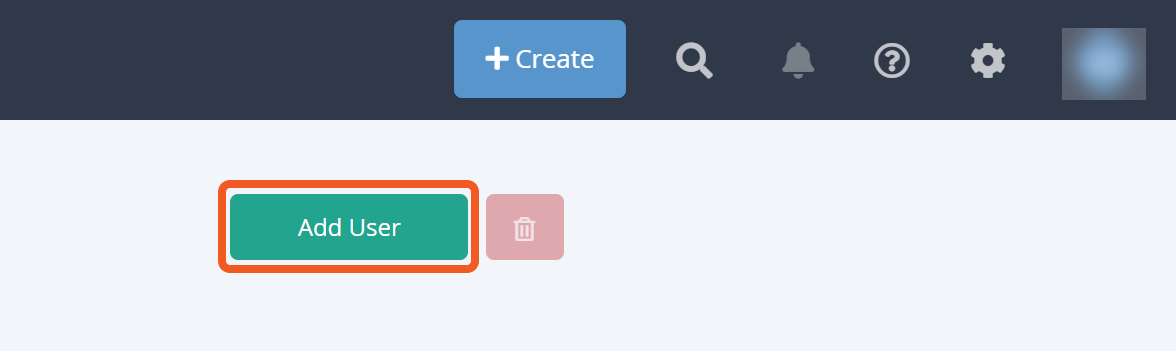
Set a display name, username, and password.
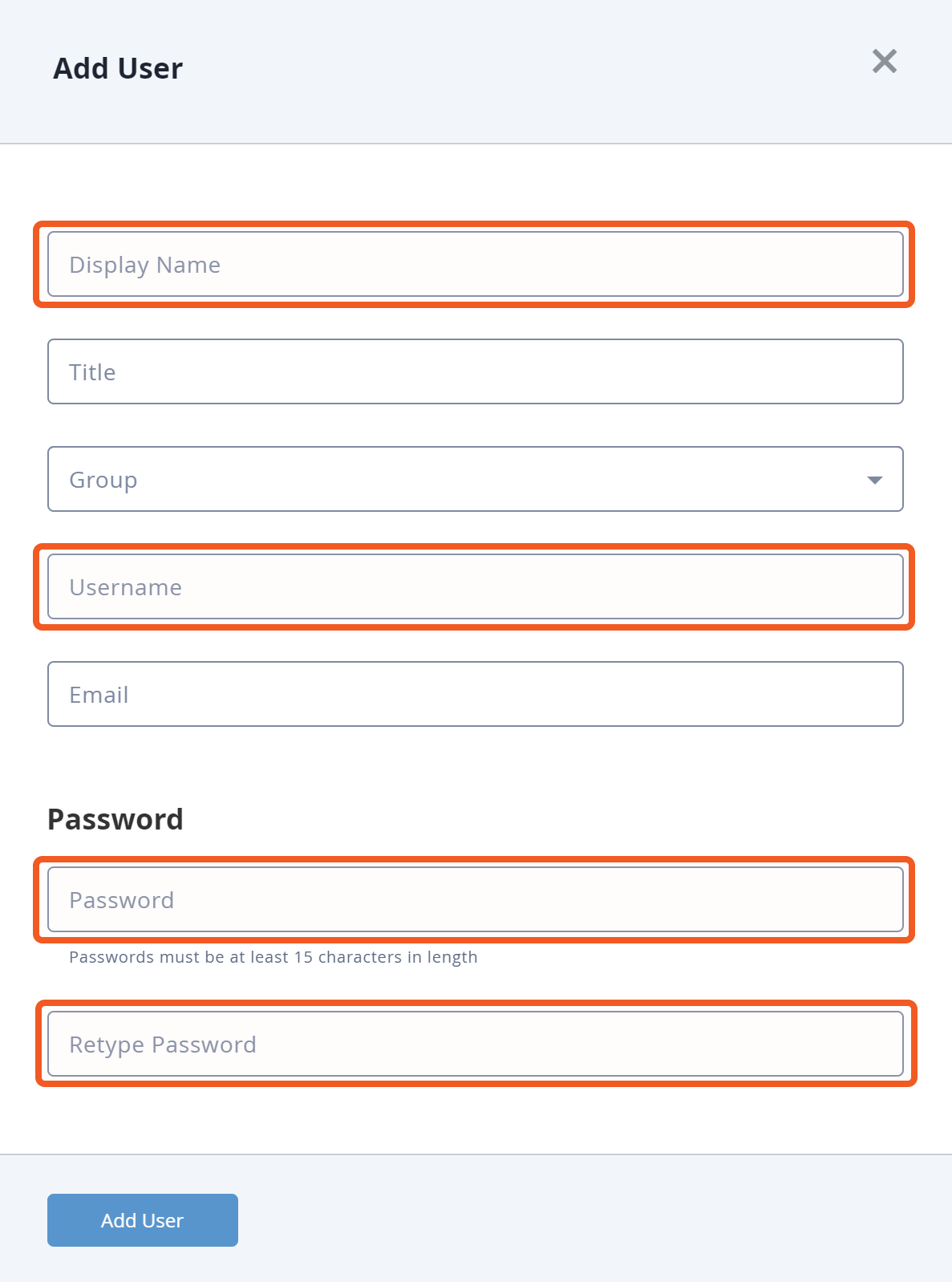
Select a suitable access group from the group dropdown for the new user.
.png?inst-v=9d16beaf-952a-4ae4-8fe8-e35f7a3745da)
Click on the Add User button.
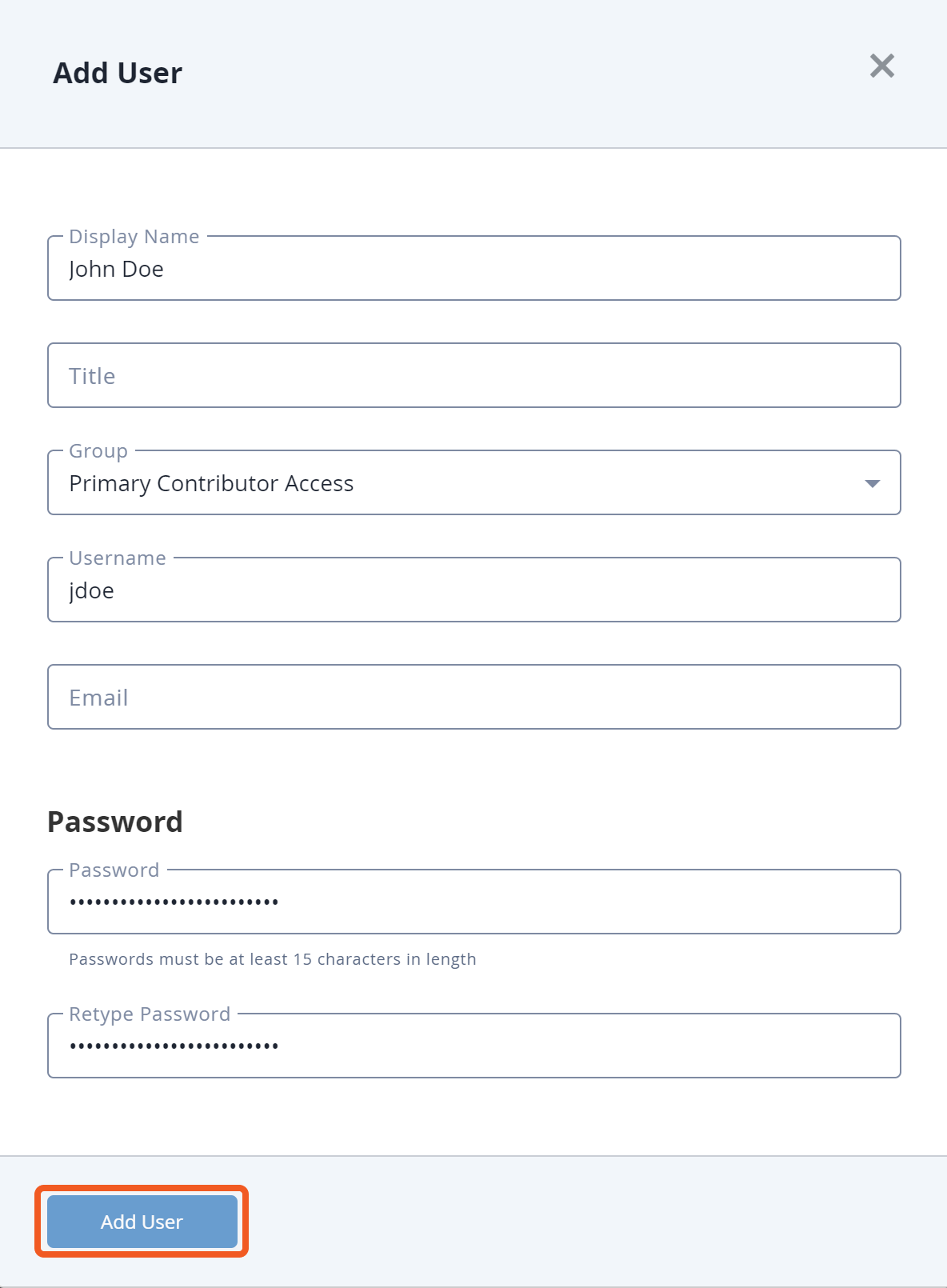
The new user will be displayed on the User Management page.
Configuring ThreatQuotient to Work with D3 SOAR
Log onto your ThreatQuotient environment at your server URL with your username and password.
Click on your profile icon in the top right corner.
Click on the My Account option.
Locate API Credentials - Client ID on the left side of the screen.
Copy your Client ID and paste it into the Client ID field. Refer to step 3j > step 3 of Configuring D3 SOAR to Work with ThreatQuotient.
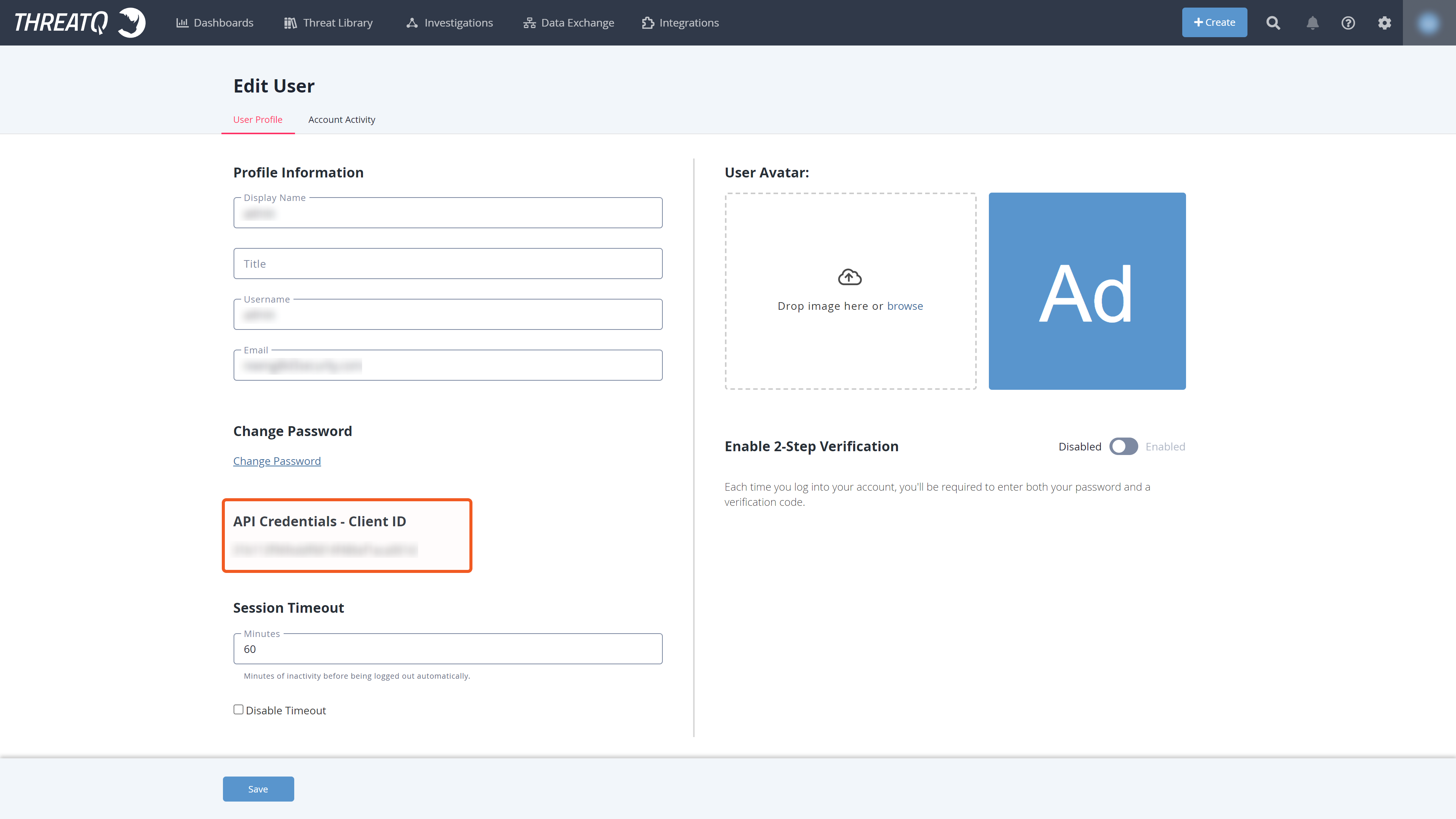
If you do not see your Client ID, then you need to obtain it from someone in your organization in the Maintenance Account or Administrative Access group. Refer to Permissions Requirements for more information.
Configuring D3 SOAR to Work with ThreatQuotient
Log in to D3 SOAR.
Find the ThreatQuotient integration.
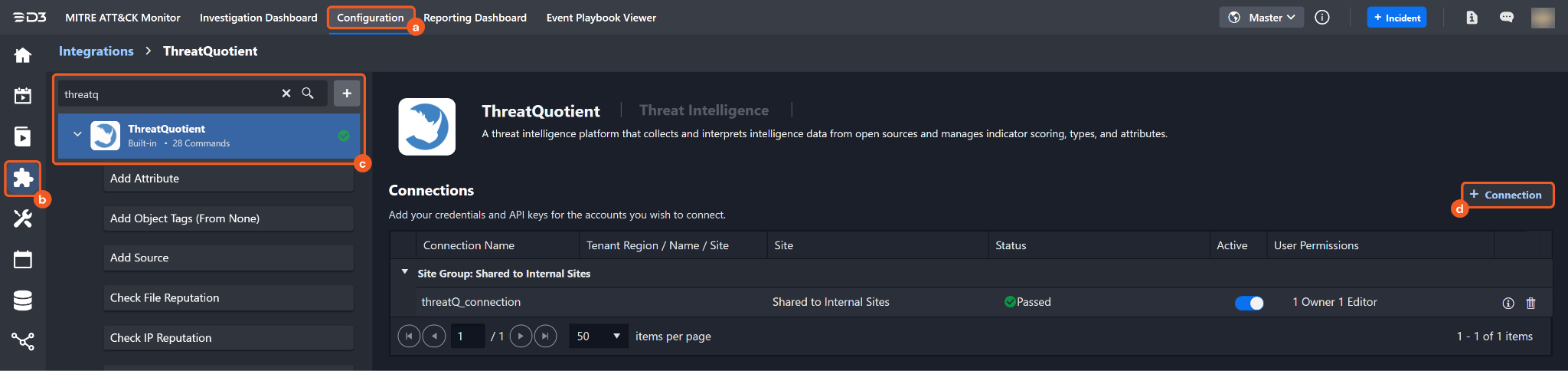
Navigate to Configuration on the top header menu.
Click on the Integration icon on the left sidebar.
Type ThreatQuotient in the search box to find the integration, then click it to select it.
Click on the + Connection button on the right side of the Connections section. A new connection window will appear.
Configure the following fields to create a connection to ThreatQuotient.
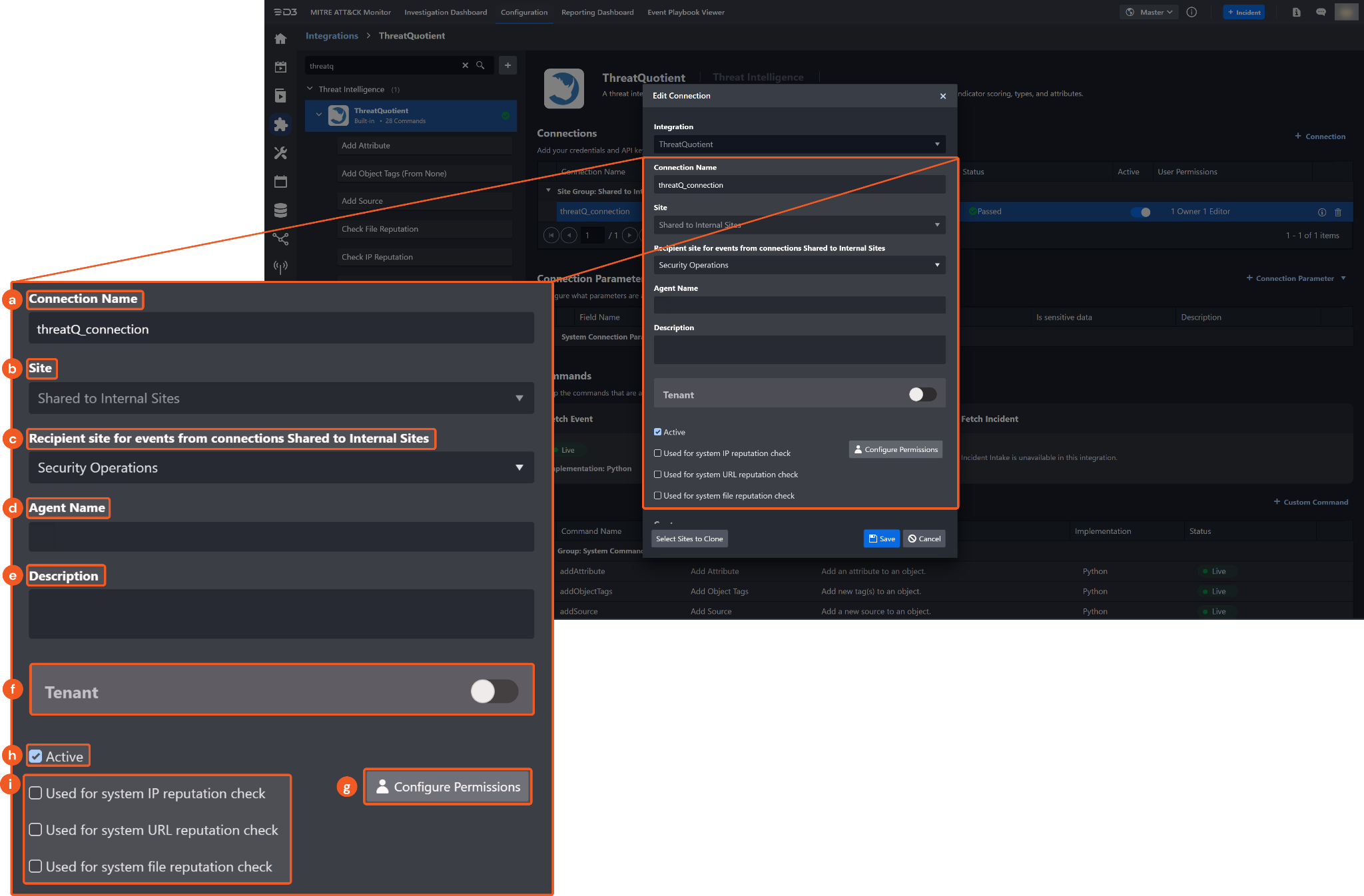
Connection Name: The desired name for the connection.
Site: The site on which to use the integration connection. Use the drop-down menu to select the site. The Share to Internal Sites option enables all internal sites to use the connection. Selecting a specific site will only enable that site to use the connection.
Recipient site for events from connections Shared to Internal Sites: This field is displayed when Share to Internal Sites is selected for the Site field, allowing selection of the internal site for deploying the integration connection.
Agent Name (Optional): The proxy agent required to build the connection. Use the dropdown menu to select the proxy agent from a list of previously configured proxy agents.
Description (Optional): The description for the connection.
Tenant (Optional): When configuring the connection from a master tenant site, users can choose the specific tenant sites with which to share the connection. Once this setting is enabled, users can filter and select the desired tenant sites from the dropdowns to share the connection.

Configure User Permissions: Defines which users have access to the connection.
Active: The checkbox that enables the connection to be used when selected.
System Reputation Check: Checking one or more reputation check tick boxes will run the corresponding check reputation command(s) under this integration connection to enrich the corresponding artifacts with reputation details.
For example, we are configuring an integration connection named "ConnectionA" with the site "Sandbox". All IP artifacts from the "Sandbox" site will undergo a reputation check using the Check IP Reputation command from that integration. The return data output from this command will then be used to update the risk level of artifacts, which may affect the risk level of incoming events.
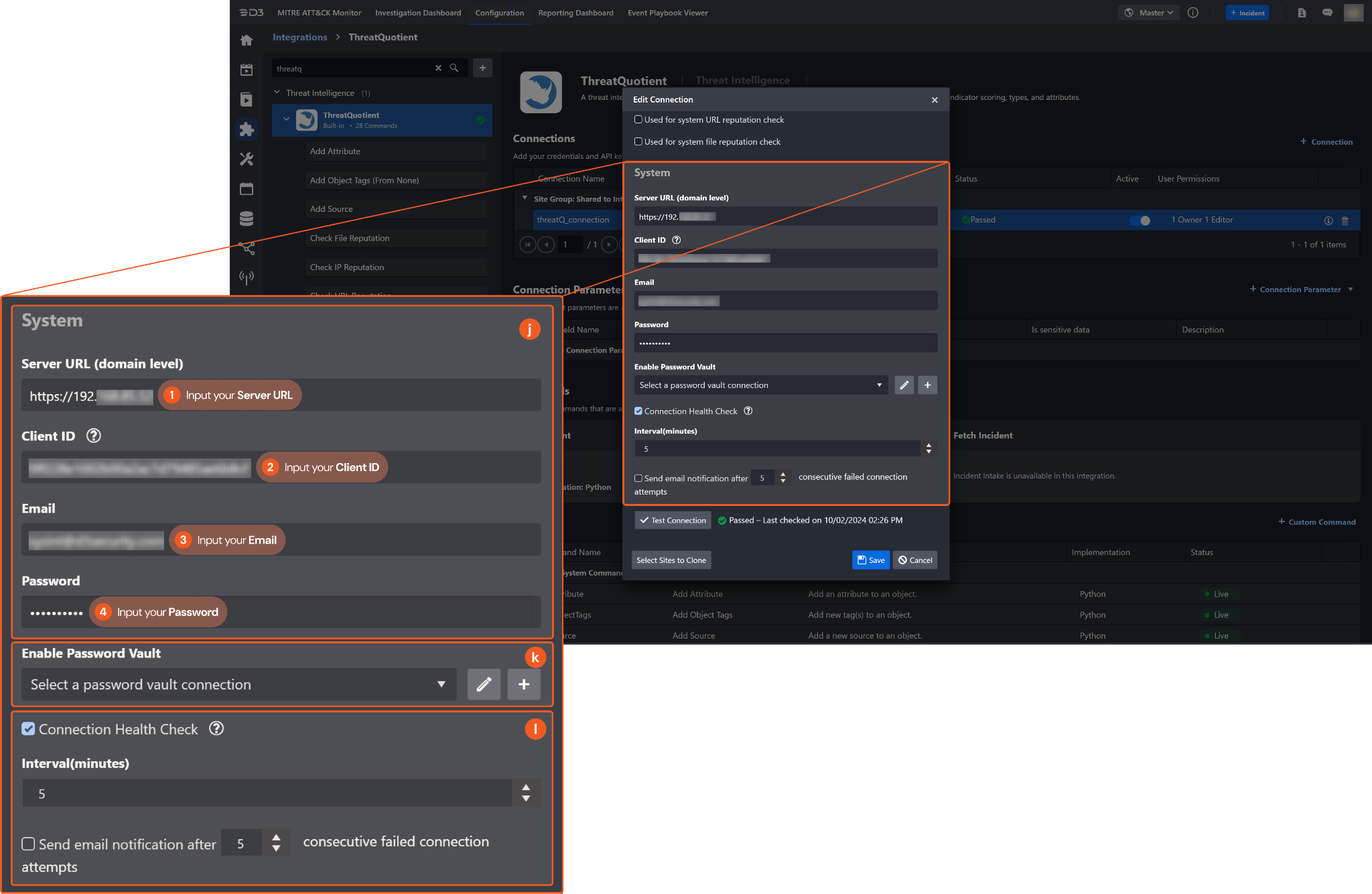
System: This section contains the parameters defined specifically for the integration. These parameters must be configured to create the integration connection.
1. Input the Server URL.
2. Input your Client ID from the ThreatQuotient platform. Refer to step 5 of Configuring ThreatQuotient to Work with D3 SOAR.3. Input your ThreatQuotient email address (or username).
4. Input your ThreatQuotient password.
Enable Password Vault: An optional feature that allows users to take the stored credentials from their own password vault. Refer to the password vault connection guide if needed.
Connection Health Check: Periodically checks the connection status by scheduling the Test Connection command at the specified interval (in minutes). Available only for active connections, this feature also allows configuring email notifications for failed attempts.
Test the connection.
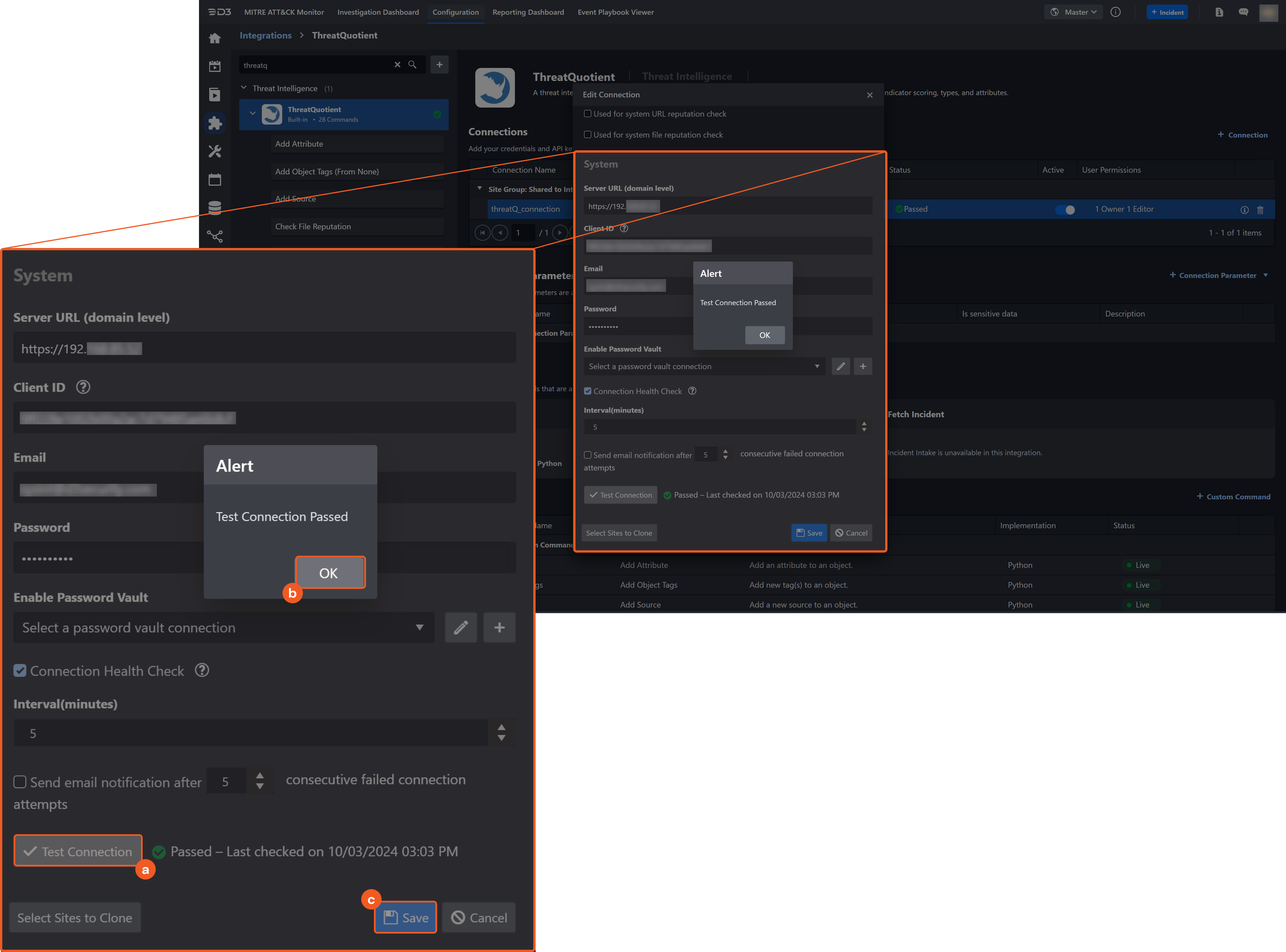
Click on the Test Connection button to verify credentials and connectivity. A success alert displays Passed with a green checkmark. If the connection fails, review the parameters and retry.
Click OK to close the alert window.
Click + Add to create and add the configured connection.
Commands
ThreatQuotient includes the following executable commands for users to set up schedules or create playbook workflows. With the Test Command, users can execute these commands independently for playbook troubleshooting.
Integration API Note
For more information about the ThreatQuotient API, refer to the ThreatQuotient API reference. Users must log-in to access the ThreatQuotient API reference.
READER NOTE
Certain permissions are required for each command. Refer to the Permission Requirements and Configuring ThreatQuotient to Work with D3 SOAR sections for details.
Note for Time-related parameters
The input format of time-related parameters may vary based on user account settings, which may cause the sample data in commands to differ from what is displayed. To adjust the time format, follow these steps:
Navigate to Configuration > Application Settings. Select Date/Time Format.
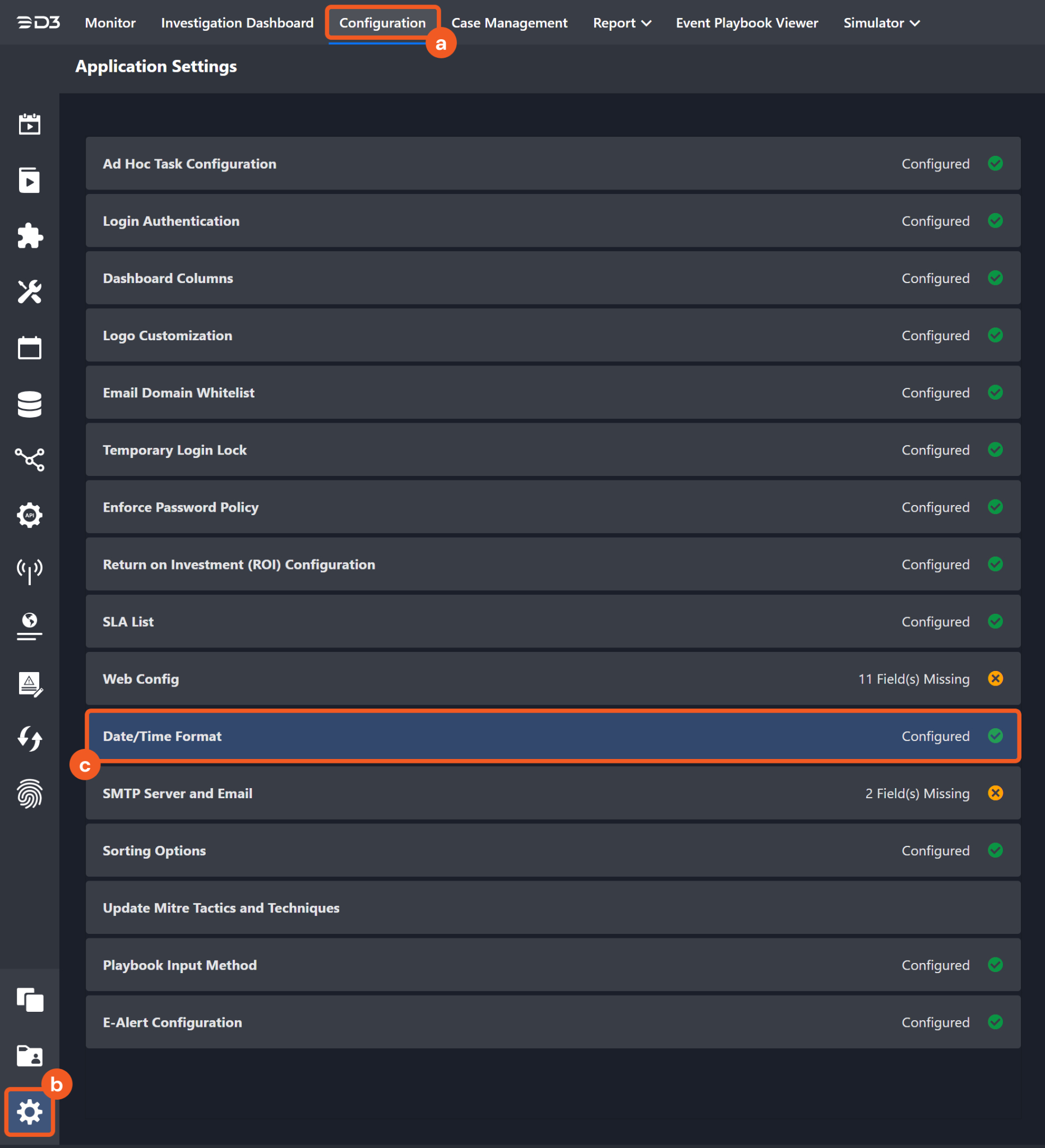
Choose the desired date and time format, then click on the Save button.
The selected time format will now be visible when configuring Date/Time command input parameters.
Add Attribute
Adds an attribute to an object.
READER NOTE
Object ID is a required parameter to run this command.
Run the Get Object ID by Value command to obtain the Object ID. Object IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Object Type | Required | The type of object to which an attribute will be added. | indicators |
Object ID | Required | The ID of the object to which an attribute will be added. Object IDs can be obtained using the Get Object ID by Value command. | ***** |
Attribute Name | Required | The name of the attribute that will be added. | Port |
Attribute Value | Required | The value of the attribute that will be added. | 4000 |
Attribute Source | Optional | The source name of the attribute that will be added. | TQ User |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Add Attribute failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Not found. |
Error Sample Data Add Attribute failed. Status Code: 404. Message: Not found. |
Add Object Tags
Adds new tag(s) to an object.
READER NOTE
Object ID is a required parameter to run this command.
Run the Get Object ID by Value command to obtain the Object ID. Object IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Object Type | Required | The type of object to which an object tag will be added. | indicator |
Object ID | Required | The ID of the object to which an object tag will be added. Object IDs can be obtained using the Get Object ID by Value command. | ***** |
Tag Name | Required | The name(s) of the tag(s) to be added to an object. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Add Object Tags failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The value for parameter (Tag Name) is invalid. |
Error Sample Data Add Object Tags failed. Status Code: 400. Message: The value for parameter (Tag Name) is invalid. |
Add Source
Adds a new source to an object.
READER NOTE
Object ID is a required parameter to run this command.
Run the Get Object ID by Value command to obtain the Object ID. Object IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Object Type | Required | The type of object to which a source will be added. | indicators |
Object ID | Required | The ID of the object to which a source will be added. Object IDs can be obtained using the Get Object ID by Value command. | ***** |
Source Name | Required | The name of the source to be added to the object. | Test Source45 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Add Source failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The Object ID is not valid. |
Error Sample Data Add Source failed. Status Code: 400. Message: The Object ID is not valid. |
Check Email Reputation
Checks the risk level of emails.
Input
Input Parameter | Required/Optional | Description | Example |
Email Addresses | Required | The list of email addresses to check. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
D3-defined Risk Levels and Risk Level Names
The table below lists (left to right) the third party's possible output risk levels and their corresponding risk level names, followed by their corresponding risk levels and risk level names as defined by D3:
ThreatQ Risk Levels | ThreatQ Risk Level Names | D3 Risk Levels | D3 Risk Level Names |
9-10 | High | 1 | High |
7-8 | Medium | 2 | Medium |
1-6 | Low | 3 | Low |
n/a | n/a | 4 | Default |
0 | Zero | 5 | ZeroRisk |
Error Handling
If your command fails to execute, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Check Email Reputation failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Access denied. |
Error Sample Data Check Email Reputation failed. Status Code: 401. Message: Access denied. |
Check File Reputation
Checks the risk level of files using file hashes.
Input
Input Parameter | Required/Optional | Description | Example |
File Hashes | Required | The list of file hashes to check. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
D3-defined Risk Levels and Risk Level Names
The table below lists (left to right) the third party's possible output risk levels and their corresponding risk level names, followed by their corresponding risk levels and risk level names as defined by D3:
ThreatQ Risk Levels | ThreatQ Risk Level Names | D3 Risk Levels | D3 Risk Level Names |
9-10 | High | 1 | High |
7-8 | Medium | 2 | Medium |
1-6 | Low | 3 | Low |
n/a | n/a | 4 | Default |
0 | Zero | 5 | ZeroRisk |
Error Handling
If your command fails to execute, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Check File Reputation failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Access denied. |
Error Sample Data Check File Reputation failed. Status Code: 401. Message: Access denied. |
Check IP Reputation
Checks the risk level of IP addresses.
Input
Input Parameter | Required/Optional | Description | Example |
IP Addresses | Required | The list of IP addresses to check. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
D3-defined Risk Levels and Risk Level Names
The table below lists (left to right) the third party's possible output risk levels and their corresponding risk level names, followed by their corresponding risk levels and risk level names as defined by D3:
ThreatQ Risk Levels | ThreatQ Risk Level Names | D3 Risk Levels | D3 Risk Level Names |
9-10 | High | 1 | High |
7-8 | Medium | 2 | Medium |
1-6 | Low | 3 | Low |
n/a | n/a | 4 | Default |
0 | Zero | 5 | ZeroRisk |
Error Handling
If your command fails to execute, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Check IP Reputation failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Access denied. |
Error Sample Data Check IP Reputation failed. Status Code: 401. Message: Access denied. |
Check URL Reputation
Checks the risk level of URLs.
Input
Input Parameter | Required/Optional | Description | Example |
URLs | Required | The list of URLs to check. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
D3-defined Risk Levels and Risk Level Names
The table below lists (left to right) the third party's possible output risk levels and their corresponding risk level names, followed by their corresponding risk levels and risk level names as defined by D3:
ThreatQ Risk Levels | ThreatQ Risk Level Names | D3 Risk Levels | D3 Risk Level Names |
9-10 | High | 1 | High |
7-8 | Medium | 2 | Medium |
1-6 | Low | 3 | Low |
n/a | n/a | 4 | Default |
0 | Zero | 5 | ZeroRisk |
Error Handling
If your command fails to execute, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Check URL Reputation failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Access denied. |
Error Sample Data Check URL Reputation failed. Status Code: 401. Message: Access denied. |
Check Vulnerability
Checks the risk level of CVEs by their IDs.
Input
Input Parameter | Required/Optional | Description | Example |
CVE IDs | Required | The list of CVE IDs for which to check the risk level(s). |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Check Vulnerability failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: CVEId CVE-1999-4565 could not be found in the Threat Q database. |
Error Sample Data Check Vulnerability failed. Status Code: 404. Message: CVEId CVE-1999-4565 could not be found in the Threat Q database. |
Create Adversary
Creates a new adversary in ThreatQ.
Input
Input Parameter | Required/Optional | Description | Example |
Adversary Name | Required | The name of the adversary to create. | Adversary Demo |
Adversary Source | Optional | The source of the adversary to create. | Adversary source |
Adversary Description | Optional | The description for the adversary. | add description |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Create Adversary failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The name has already been taken. |
Error Sample Data Create Adversary failed. Status Code: 400. Message: The name has already been taken. |
Create Event
Creates a new event in ThreatQ.
Input
Input Parameter | Required/Optional | Description | Example |
Event Type | Required | The type of event to create. Possible Values include "Spearphish", "Watering Hole", "SQL Injection Attack", "DoS Attack", "Malware", "Watchlist", "Command and Control", "Anonymization", "Exfiltration", "Host Characteristics", "Compromised PKI Certificate", "Login Compromise", "Incident", "Sighting" and other custom event types. | Watering Hole |
Event Source | Optional | The source of the event to be created. | Source |
Event Content | Required | The content of the event to be created. | Event_Demo description |
Date of Occurence | Required | The occurrence date of the event to be created. | 2021-10-21 16:40:00 |
Title | Required | The title of the event to be created. | Event_Demo |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Create Event failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Access denied. |
Error Sample Data Create Event failed. Status Code: 401. Message: Access denied. |
Create Indicator
Creates a new indicator in ThreatQ.
Input
Input Parameter | Required/Optional | Description | Example |
Indicator Name | Required | The name of the indicator to be created. | ***** |
Indicator Type | Required | The type of indicator to be created. | IP Address |
Indicator Source | Optional | The source of the indicator to be created. | Source |
Indicator Status | Required | The status of the indicator to be created. Possible values include: "Active", "Expired", "Indirect", "Review", "Whitelisted", and other custom options. | Active |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Create Indicator failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The indicator value and type do not match. |
Error Sample Data Create Indicator failed. Status Code: 400. Message: The indicator value and type do not match. |
Create Object
Creates a new object in ThreatQ.
Input
Input Parameter | Required/Optional | Description | Example |
Object Type | Required | The type of object to be created. | attack_pattern |
Object Name | Required | The name of the object to be created. | objectcreationdemo |
Object Description | Required | Provide a description for the object to be created. | attack_pattern_objectdemo |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Create Object failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Access denied |
Error Sample Data Create Object failed. Status Code: 401. Message: Access denied |
Delete File
Deletes an uploaded file.
READER NOTE
File ID is a required parameter to run this command.
Run the Get Object ID by Value command to obtain the File ID. File IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
File IDs (Attachment IDs) | Required | The ID of the file to delete. File IDs can be obtained using the Get Object ID by Value command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Delete File failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: File ID 23: Not found. |
Error Sample Data Delete File failed. Status Code: 404. Message: File ID 23: Not found. |
Download File
Downloads the specified file(s) from ThreatQ.
READER NOTE
File ID is a required parameter to run this command.
Run the Check File Reputation command to obtain the File ID.
Run the List File command to obtain the File ID. File IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
File IDs (Attachment IDs) | Required | The ID of File (Attachment) to be downloaded. File IDs can be obtained using the Check File Reputation or List File command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Download File failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Access denied. |
Error Sample Data Download File failed. Status Code: 401. Message: Access denied. |
Fetch Event
Retrieves events from the ThreatQ Library.
Input
Input Parameter | Required/Optional | Description | Example |
Start Time | Required | The Start Time of the time range within which events are fetched. | 2010-10-16 22:35:00 |
End Time | Optional | The End Time for the time range within which events are fetched. | 2022-10-16 22:35:00 |
Number of Event(s) Fetched | Optional | The maximum number of recent events to be fetched. | 2 |
Search Condition | Optional | The criteria and filters option for the query, with two types of query syntaxes supported. The first is the simple syntax in the format: "type=Malware source=Crowdstrike." Only type and source are supported in the simple syntax, for which multiple values are allowed using the comma as a delimiter. The second syntax is the ThreatQ SOLR query structure (JSON). Refer to the ThreatQ API documentation for details. Do not use "created_at" in the SOLR query structure as it will be disregarded. | type=Malware,DoS Attack source=Crowdstrike,Source |
Output
To view the sample output data for all commands, refer to this article.
Fetch Event Field Mapping
Fetch Event commands require event field mapping. Field mapping plays a key role for data normalization within the event pipeline. Field mapping converts the original data fields from the different providers to standardized D3 fields as defined by the D3 Model. Refer to Event and Incident Intake Field Mapping for details.
To customize field mapping, click + Add Field and add the custom field of your choice. You can also remove built-in field mappings by clicking x. Note that two underscore characters will automatically prefix the defined Field Name as the System Name for a custom field mapping. Additionally, if an input Field Name contains any spaces, they will automatically be replaced with underscores for the corresponding System Name.
As a system integration, the ThreatQuotient integration has some pre-configured field mappings for default field mapping.
Default Event Source
The Default Event Source is the default set of field mappings that are applied when this fetch event command is executed. For out-of-the-box integrations, you will find a set of field mapping provided by the system. Default event source provides field mappings for common fields from fetched events (e.g. created_at and happened_at). The default event source has a "Main Event JSON Path" (i.e. $.data) that is used to extract a batch of events from the response raw data. Click on Edit Main JSON Path to view the "Main Event JSON Path".
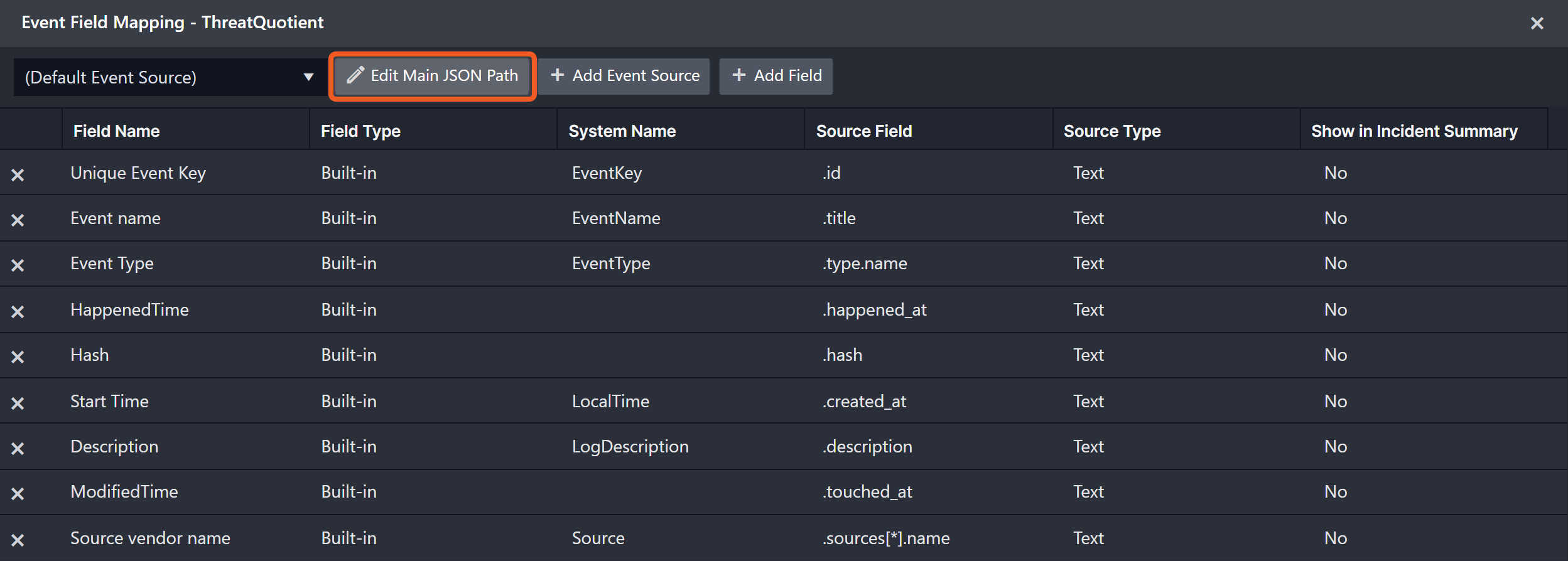
Main Event JSON Path: $.data
The Main Event JSON Path determines the root path where the system starts parsing raw response data into D3 event data. The JSON path begins with $, representing the root element. The path is formed by appending a sequence of child elements to $, each separated by a dot (.). Square brackets with nested quotation marks ([‘...’]) should be used to separate child elements in JSON arrays.
For example, the root node of a JSON Path is data. The child node denoting the Unique Event Key field would be id. Putting it together, the JSON Path expression to extract the Unique Event Key is $.data.id.
The pre-configured field mappings are detailed below:
Field Name | Source Field |
Unique Event Key | .id |
Event name | .title |
Event Type | .type.name |
HappenedTime | .happened_at |
Hash | .hash |
Start Time | .created_at |
Description | .description |
Modified Time | .touched_at |
Source vendor name | .sources[*].name |
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Fetch Event failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Authentication failed. |
Error Sample Data Fetch Event failed. Status Code: 401. Message: Authentication failed. |
Get Object ID by Value
Retrieves Object ID(s) by value in ThreatQ.
Input
Input Parameter | Required/Optional | Description | Example |
Object Type | Required | The type of object from which to retrieve ID. | vulnerability |
Object Value | Required | The value of the object from which to retrieve ID. | CVE |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Object ID by Value failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Access denied. |
Error Sample Data Get Object ID by Value failed. Status Code: 401. Message: Access denied. |
Link Object
Links two objects in ThreatQ.
READER NOTE
Object 1 ID and Object 2 ID are required parameters to run this command.
Run the Get Object by ID Value command to obtain the Object 1 ID and Object 2 ID. Object 1 IDs and Object 2 IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Object 1 Type | Required | The type of the first object to link. | indicators |
Object 1 ID | Required | The ID of the first object to link. Object IDs can be obtained using the Get Object ID by Value command. | ***** |
Object 2 Type | Required | The type of the second object to link. | adversaries |
Object 2 ID | Required | The ID of the second object to link. Object IDs can be obtained using the Get Object ID by Value command. | ***** |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Link Object failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Bad request. |
Error Sample Data Link Object failed. Status Code: 400. Message: Bad request. |
List Adversaries
Retrieves a list of all adversaries.
Input
Input Parameter | Required/Optional | Description | Example |
Limit | Optional | The maximum number of records to retrieve. | 2 |
Offset | Optional | The record that will appear first in the retrieved list of adversaries. | 100 |
Sort | Optional | The field used to sort the retrieved list. Prepend with a minus sign (-) to reverse the sorting order. The sorting order can be a list of comma-separated values. | -id |
With | Optional | A comma-separated list of related objects to include in the response. Options for this endpoint include: "adversaries", "attachments", "attributes", "comments", "description", "events", "indicators", "plugins", "pluginActions", "signatures", "sources", "tags", "valueWeight", "watchlist." | adversaries,attachments,attributes,comments,description,events,indicators,plugins,pluginActions,signatures,sources,tags,valueWeight,watchlist |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Adversaries failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Access denied. |
Error Sample Data List Adversaries failed. Status Code: 401. Message: Access denied. |
List Attachment Types
Retrieves the list of all attachment (file) types.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Attachment Type failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Invalid URL 'demoURL/api/token': No scheme supplied. |
Error Sample Data List Adversaries failed. Status Code: 400. Message: Invalid URL 'demoURL/api/token': No scheme supplied. |
List File
Lists all Files (Attachments).
Input
Input Parameter | Required/Optional | Description | Example |
Limit | Optional | The maximum number of records to retrieve. | 2 |
Offset | Optional | The record that will appear first in the retrieved list. | 10 |
Sort | Optional | The field used to sort the retrieved list. Prepend with a minus sign (-) to reverse the sorting order. The sorting order can be a list of comma-separated values. | -id |
With | Optional | A comma-separated list of related objects to include in the response. Options for this endpoint are: "adversaries", "attachments", "attributes", "comments", "contentType", "events", "indicators", "signatures", "sources", "tags", "type", "watchlist." | adversaries,attachments,attributes,comments,contentType,events,indicators,signatures,sources,tags,type,watchlist |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List File failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Access denied. |
Error Sample Data List File failed. Status Code: 401. Message: Access denied. |
List Indicators
Lists all indicators.
Input
Input Parameter | Required/Optional | Description | Example |
Limit | Optional | The maximum number of records to retrieve. | 2 |
Offset | Optional | The record that will appear first in the retrieved list. | 100 |
Sort | Optional | The field used to sort the retrieved list. Prepend with a minus sign (-) to reverse the sorting order. The sorting order can be a list of comma-separated values. | -id |
With | Optional | A comma-separated list of related objects to include in the response. Options for this endpoint are: "adversaries", "attachments", "attributes", "comments", "events", "indicators", "score", "signatures", "sources", "status", "tags", "type", "watchlist." | status,type,adversaries,attachments,attributes,comments,events,indicators,score,signatures,sources,status,tags,type,watchlist |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Indicators failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Access denied. |
Error Sample Data List Indicators failed. Status Code: 401. Message: Access denied. |
Parse File
Parses the file for indicators.
READER NOTE
File ID (Attachment ID) and ParserID are required parameters to run this command.
Run the Get Object ID by Value command to obtain the File ID. File IDs can be found in the raw data at the path $.data[*].id.
Run the Search File Content Type command to obtain the Parser ID. Parser IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
File ID (Attachment ID) | Required | The ID of the attached file. File IDs can be obtained using the Get Object ID by Value command with the file name. | ***** |
Parser ID | Required | The type of parser used to parse the file. Parser IDs can be obtained using the Search File Content Type command. | ***** |
Indicator Source | Required | The source of the indicator to be created. | VirusTotal |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Parse File failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: File does not exist. |
Error Sample Data Parse File failed. Status Code: 404. Message: File does not exist. |
Search File Content Type
Lists all file content types.
Input
Input Parameter | Required/Optional | Description | Example |
File Content Type | Optional | The file content type to be retrieved. By default, all file content types are returned. | txt |
Parsers Only | Optional | Whether the returned file content types can be parsed. If the value is True, then parsable file content types will be returned. By default, the value is False. | false |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Search File Content Type failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Access denied. |
Error Sample Data Search File Content Type failed. Status Code: 401. Message: Access denied. |
Unlink Object
Unlinks two objects in ThreatQ.
READER NOTE
Object 1 ID and Object 2 ID are required parameters to run this command.
Run the Get Object by ID Value command to obtain the Object 1 ID and Object 2 ID. Object 1 IDs and Object 2 IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Object 1 Type | Required | The type of the first object to unlink. | indicators |
Object 1 ID | Required | The ID of the first object to unlink. Object IDs can be obtained using the Get Object ID by Value command. | ***** |
Object 2 Type | Required | The type of the second object to unlink. | adversaries |
Object 2 ID | Required | The ID of the second object to unlink. Object IDs can be obtained using the Get Object ID by Value command. | ***** |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Unlink Object failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Not found. |
Error Sample Data Unlink Object failed. Status Code: 404. Message: Not found. |
Update Indicator Score
Updates the indicator score in ThreatQ.
READER NOTE
Indicator ID is a required parameter to run this command.
Run the Get Object ID by Value command to obtain the Indicator ID. Indicator IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Indicator ID | Required | The Indicator ID for which to update the score. Indicator IDs can be obtained using the Get Object ID by Value command. | ***** |
Indicator Score | Required | The updated indicator score. | 10 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Indicator Score failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Not found. |
Error Sample Data Update Indicator Score failed. Status Code: 404. Message: Not found. |
Update Indicator Status
Updates the indicator status in ThreatQ.
READER NOTE
Indicator ID is a required parameter to run this command.
Run the Get Object ID by Value command to obtain the Indicator ID. Indicator IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Indicator ID | Required | The Indicator ID for which to update the status. Indicator IDs can be obtained using the Get Object ID by Value command. | ***** |
Indicator Status | Required | The updated indicator status. Possible values include: "Active", "Expired", "Indirect", "Review", "Whitelisted", and other custom options. | Expired |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Indicator Status failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Not found. |
Error Sample Data Update Indicator Status failed. Status Code: 404. Message: Not found. |
Update Object Attribute
Updates the attribute of an object.
READER NOTE
Object ID and Object Attribute IDs are required parameters to run this command.
Run the Get Object ID by Value command to obtain the Object ID. Object IDs can be found in the raw data at the path $.data[*].id.
Run the Add Attribute command to obtain the Object Attribute ID. Object Attribute IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Object Type | Required | The type of object for which to update the attribute, with the options: Indicator | Adversary | Event | File | Signature. | indicator |
Object ID | Required | The ID of the object for which to update the attribute. Object IDs can be obtained using the Get Object ID by Value command. | ***** |
Object Attribute ID | Required | The ID of the attribute to be updated. Attribute IDs can be obtained using the Add Attribute or the matched List commands. When using the value for key “id” below “indicator_id”, refer to path $.data[*].id | ***** |
Attribute Value | Required | The value of the attribute to be added. | 4000 |
Attribute Source Name | Optional | The source name of the attribute to be added. | TQ User |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Object Attribute failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The provided Object ID or Attribute ID doesn't exist. |
Error Sample Data Update Object Attribute failed. Status Code: 404. Message: The provided Object ID or Attribute ID doesn't exist. |
Upload File
Uploads files to ThreatQ.
File Category is a required parameter to run this command.
Run the List Attachment Types command to obtain the File Category. File Categories can be found in the raw data at the path $.data[*].id.
File ID and File Source
It is not recommended to use the Test Command feature with the Upload File command as it is designed for dynamic input files in Playbooks, Incident Attachments, and Artifact Attachments. There is a simple workaround to test the command:
Navigate to Configuration on the top bar menu.
Click on Utility Commands on the left sidebar menu.
Use the search box to find and select the Create a File from input Text Array command.
Select the Test tab.
Input the required information for the parameters.
Click on the Test Command button. A D3 File ID will appear in the output data after the file has been successfully created. The D3 File Source of the created file will be Playbook File).
Input
Input Parameter | Required/Optional | Description | Example |
File IDs | Required | The file id of the file source. |
JSON
|
File Source | Required | The file source of the file to send. The options for file sources are:
| PB_FILE |
File Category | Required | The category of the file that will be uploaded (e.g. CrowdStrike Intelligence, FireEye Analysis, Cuckoo, PDF, ThreatQ CSV File etc). File Category can be obtained using the List Attachment Types command. | application/pdf |
Malware safety lock Value | Required | Whether to zip up files for safer download. To unzip, use the password "infected." | true |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Upload File failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The specified File does not have file data. |
Error Sample Data Upload File failed. Status Code: 404. Message: The specified File does not have file data. |
Test Connection
Performs a health check on an integration connection. A periodic health check can be scheduled by selecting Connection Health Check when editing an integration connection.
Input
N/A
Output
Output Type | Description | Return Data Type |
Return Data | Indicates one of the possible command execution states: Successful or Failed. The Failed state can be triggered by any of the following errors:
More details about an error can be viewed in the Error tab. | String |
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Test Connection failed. Failed to check the connector. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the ThreatQuotient portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Get Access Token Fail. |
Error Sample Data Test Connection failed. Failed to check the connector. Status Code: 401. Message: Get Access Token Fail. |