Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE)
LAST UPDATED: AUG 5, 2025
Overview
Sumo Logic Cloud SIEM Enterprise (CSE) collects, manages, and analyzes log data. It provides real-time operational and security insights across all critical applications and infrastructure, on-premise or in the cloud.
D3 SOAR's integration for Sumo Logic Cloud is using the latest Sumo Logic CSE API (1.0.0) to provide the ability to retrieve insights to D3 as events. It also provides the ability to modify insights.
D3 SOAR is providing REST operations to function with Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE).
Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) is available for use in:
Known Limitations
A rate limit of 4 API requests per second (240 requests per minute) applies to all API calls from a user.
A rate limit of 10 concurrent requests to any API endpoint applies to an access key.
Connection
To connect to Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) from D3 SOAR, please follow this part to collect the required information below:
Parameter | Description | Example |
Server URL | The server URL of Sumo Logic CSE. Note: Server URLs are location-specific. Refer to the list of server URLs below:
| https://api.<ReplaceMe>.sumologic.com |
Access ID | The access ID to authenticate with Sumo Logic CSE. | ***** |
Access Key | The access key to authenticate with Sumo Logic CSE. | ***** |
Version | The version of the integration. | v1 |
Configuring Sumo Logic CSE to Work with D3 SOAR
Log in to Sumo Logic (https://service.sumologic.com/) with your login credentials.
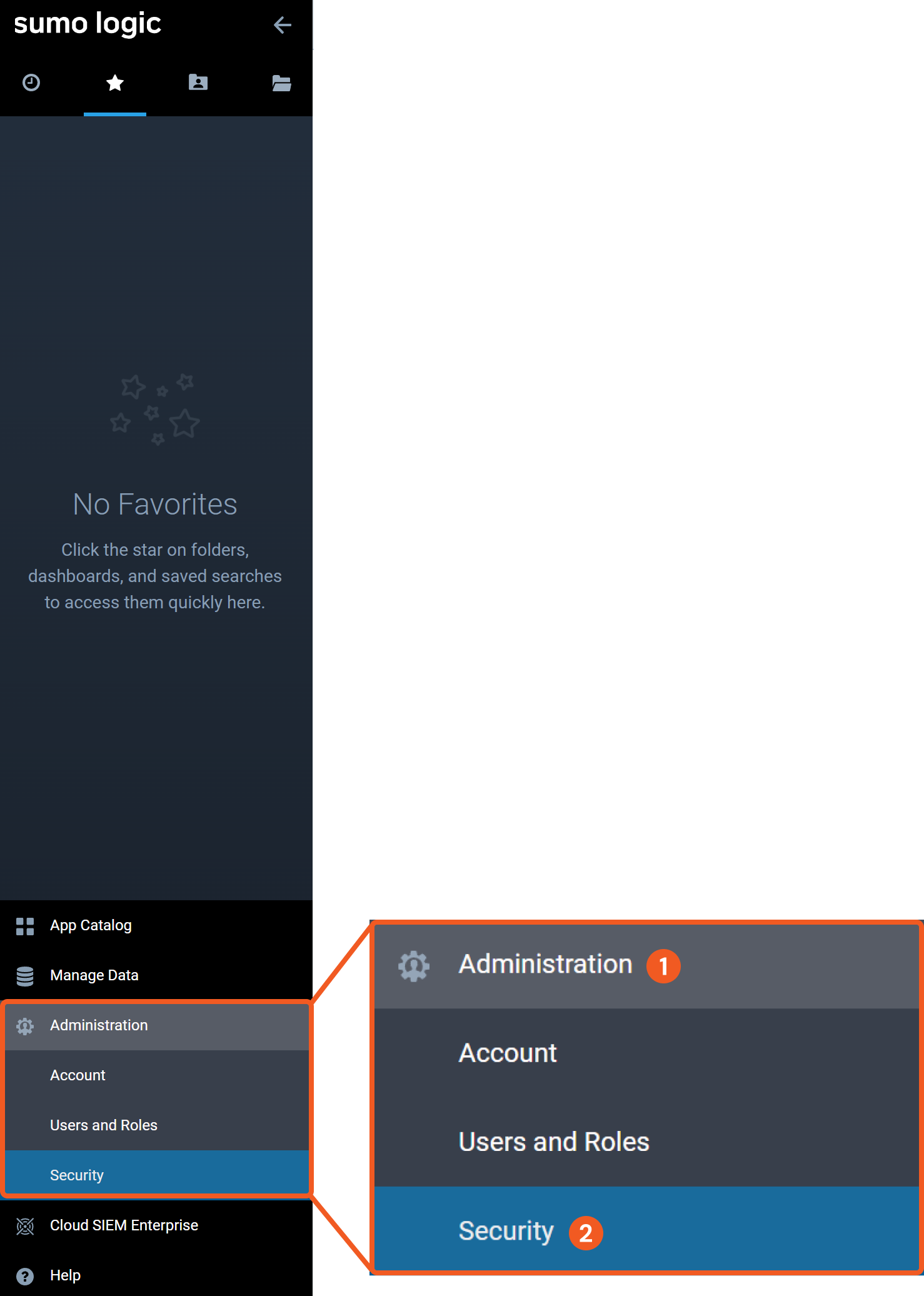
Navigate to Administration > Security.
Add an Access Key.
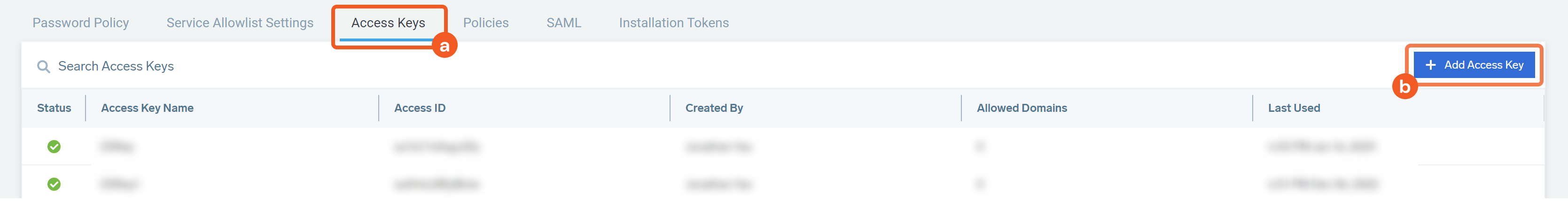
On the Security page, select the Access Keys tab at the top.
Click + Add Access Key to create a new access key. The access key configuration window will open.
Create a new Access Key.
.png?inst-v=9d16beaf-952a-4ae4-8fe8-e35f7a3745da)
Input a name for the new access key.
(Optional) Allow CORS domains by adding a domain to the allow list. This will ensure that Sumo Logic only accepts API requests from the specified domain.
Save the new access key.
Copy and store the new access ID and access key. This information is required to establish a connection with D3 SOAR. Refer to step 3j sub-steps 2-3 in Configuring D3 SOAR to Work with Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE).
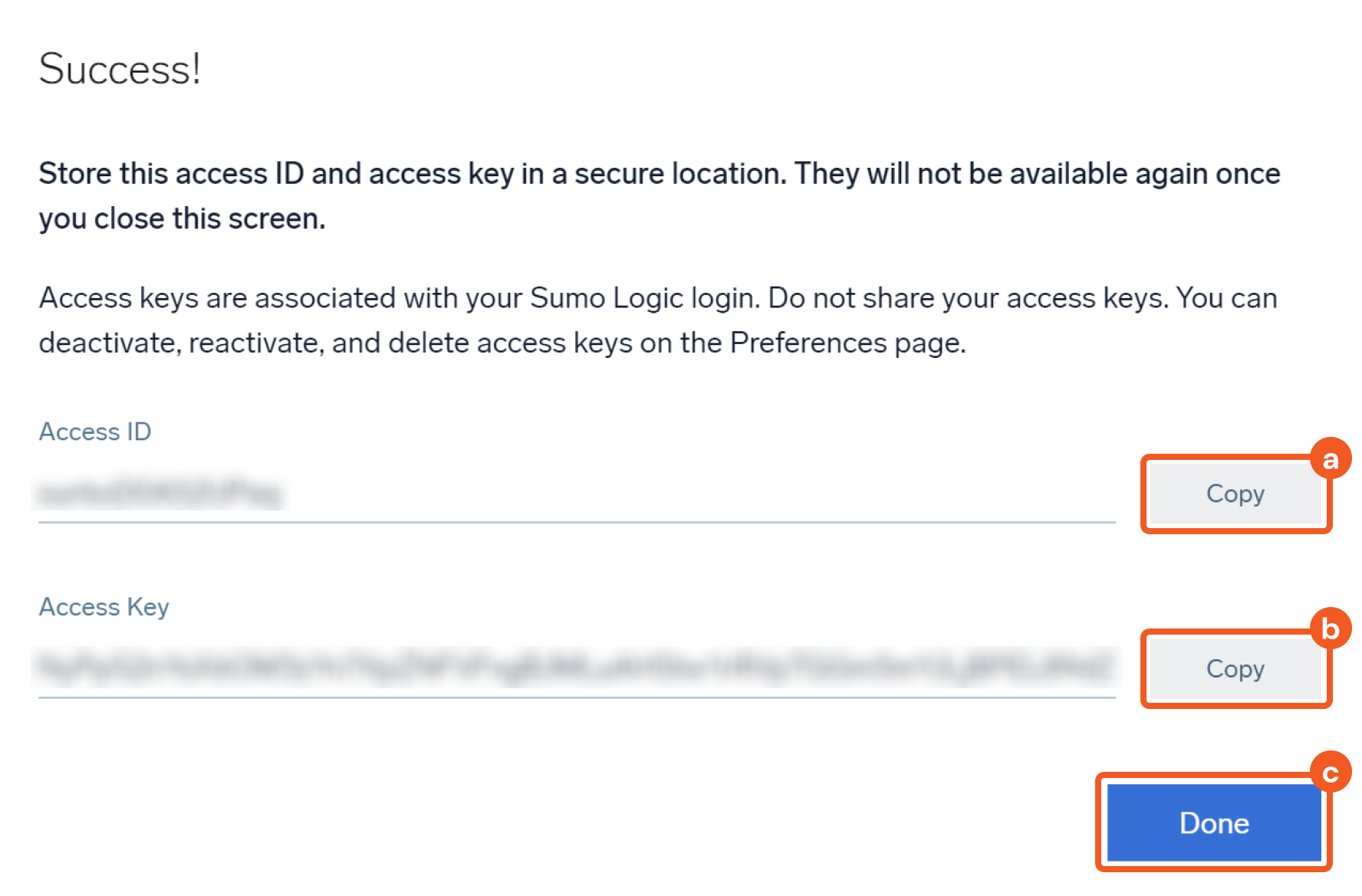
Copy the Access ID and store it in a secure location.
Copy the Access Key and store it in a secure location.
Click Done. Note: The access key will no longer be viewable after this window is closed.
Configuring D3 SOAR to Work with Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE)
Log in to D3 SOAR.
Find the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) integration.
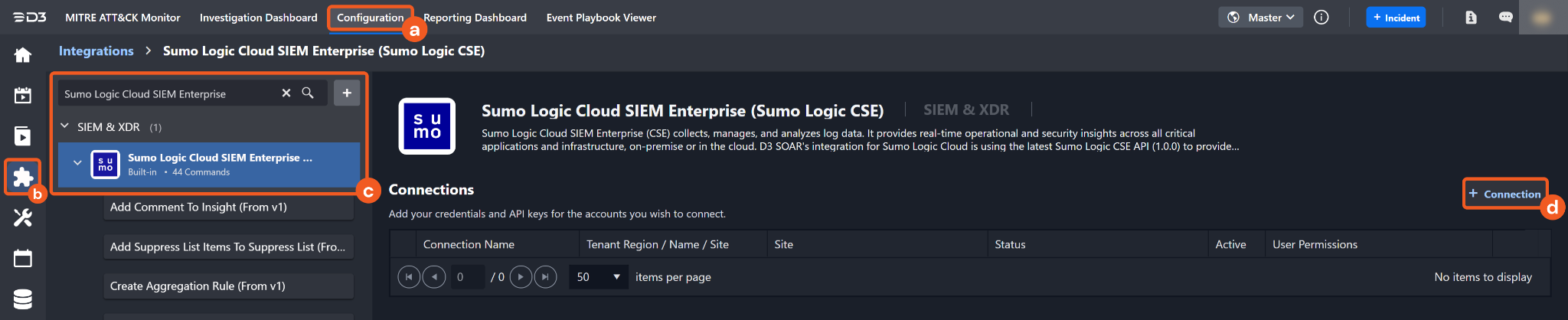
Navigate to Configuration on the top header menu.
Click on the Integration icon on the left sidebar.
Type Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) in the search box to find the integration, then click it to select it.
Click New Connection, on the right side of the Connections section. A new connection window will appear.
Configure the following fields to create a connection to Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE).
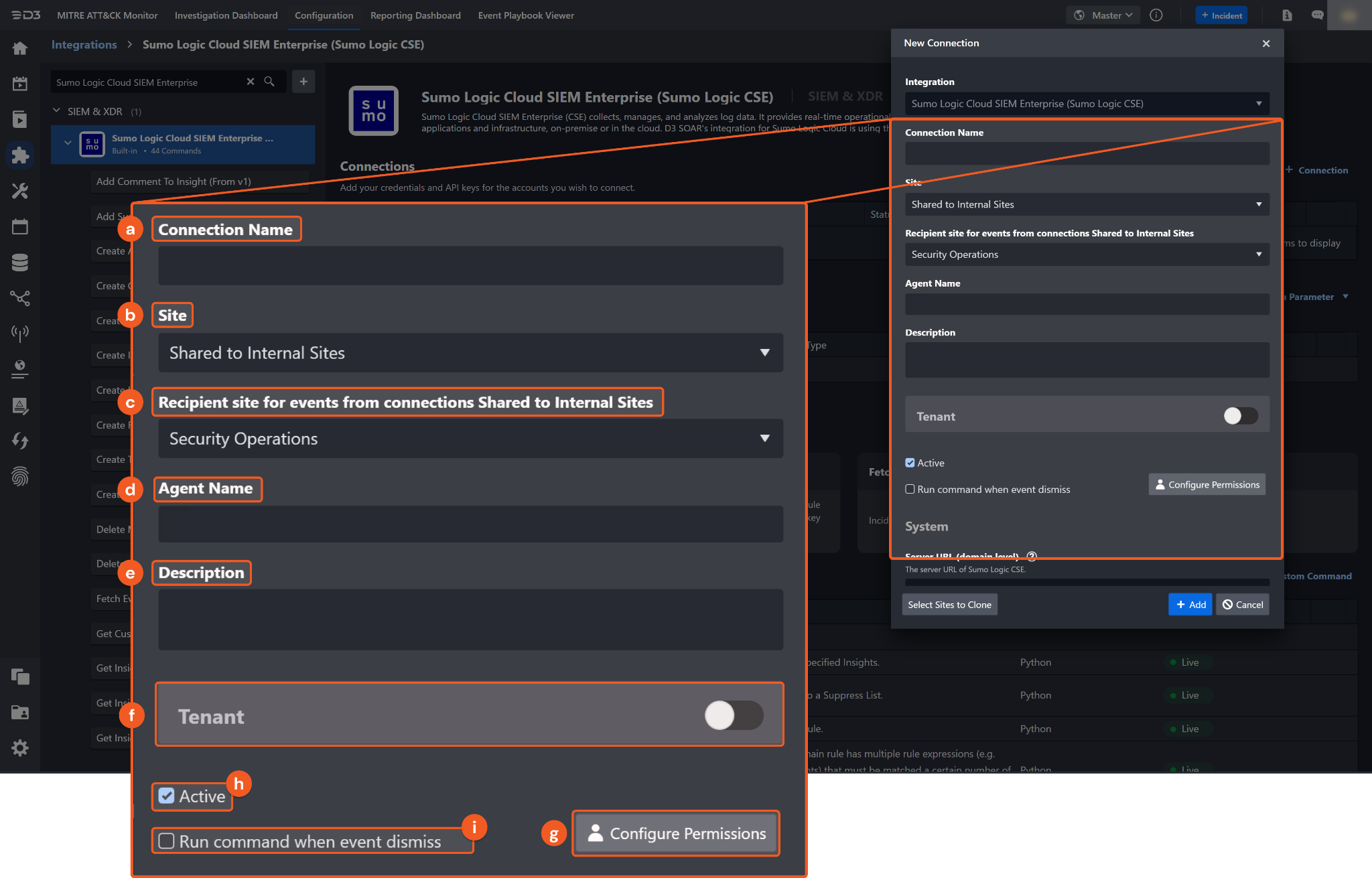
Connection Name: The desired name for the connection.
Site: The site on which to use the integration connection. Use the drop-down menu to select the site. The Share to Internal Sites option enables all internal sites to use the connection. Selecting a specific site will only enable that site to use the connection.
Recipient site for events from connections Shared to Internal Sites: This field is displayed when Share to Internal Sites is selected for the Site field, allowing selection of the internal site for deploying the integration connection.
Agent Name (Optional): The proxy agent required to build the connection. Use the dropdown menu to select the proxy agent from a list of previously configured proxy agents.
Description (Optional): The description for the connection.
Tenant (Optional): When configuring the connection from a master tenant site, users can choose the specific tenant sites with which to share the connection. Once this setting is enabled, users can filter and select the desired tenant sites from the dropdowns to share the connection.

Configure User Permissions: Defines which users have access to the connection.
Active: The checkbox that enables the connection to be used when selected.
Run command when Event dismiss: Checking the tick box will run the corresponding On Dismiss Event command(s) under this integration connection to update an Insight status after dismissal as an ingested D3 SOAR event.
System: This section contains the parameters defined specifically for the integration. These parameters must be configured to create the integration connection.
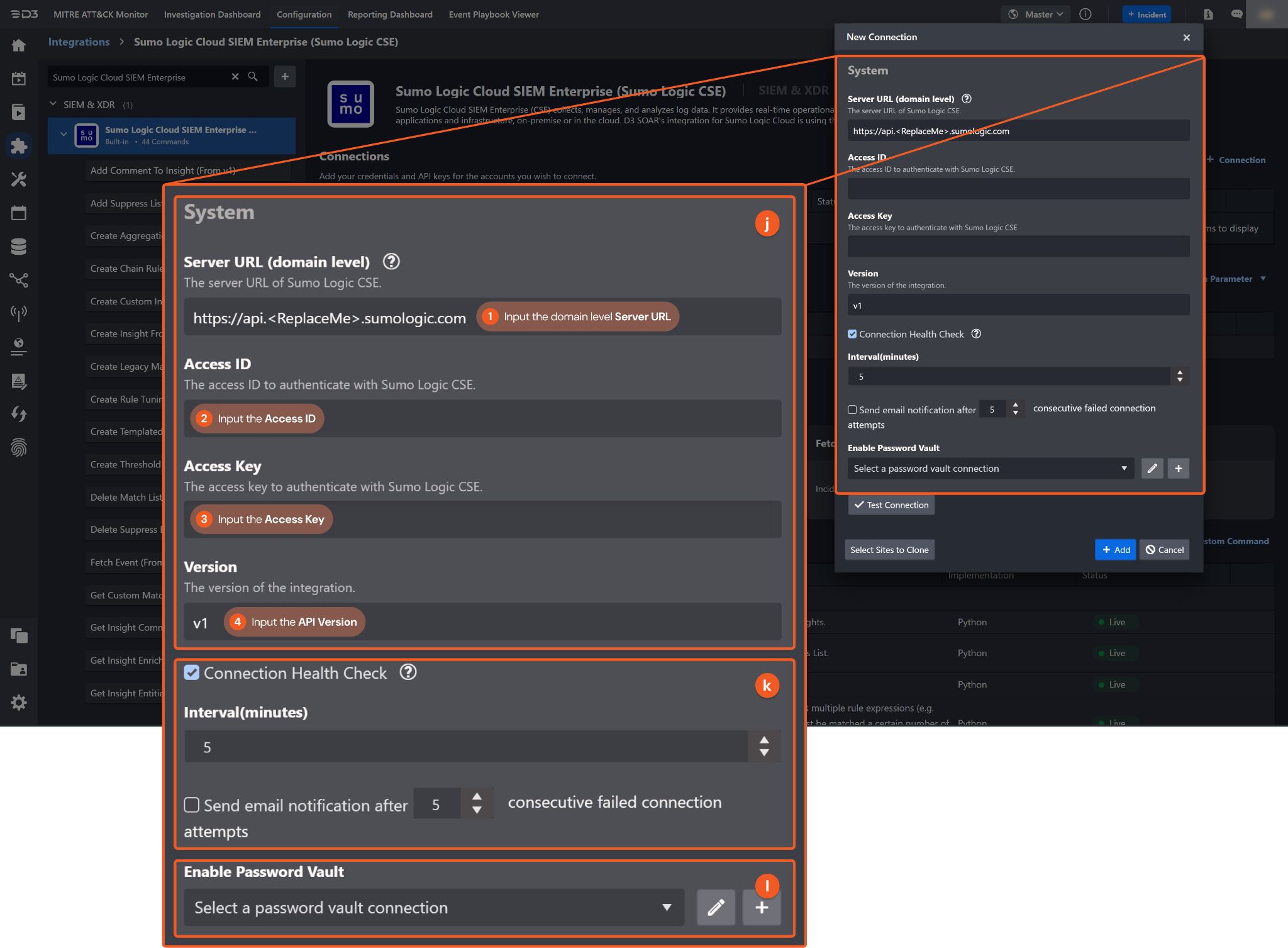
1. Input the domain level Server URL. The default value is https://api.<ReplaceMe>.sumologic.com.
2. Input the Access ID. Refer step 5a in Configuring Sumo Logic CSE to Work with D3 SOAR to obtain the Access ID.
3. Input the Access Key. Refer step 5b in Configuring Sumo Logic CSE to Work with D3 SOAR to obtain the Access Key.
4. Input the API version. The default version is v1.
Connection Health Check: Periodically checks the connection status by scheduling the Test Connection command at the specified interval (in minutes). Available only for active connections, this feature also allows configuring email notifications for failed attempts.
Enable Password Vault: An optional feature that allows users to take the stored credentials from their own password vault. Refer to the password vault connection guide if needed.
Test the connection.
Click on the Test Connection button to verify credentials and connectivity. A success alert displays Passed with a green checkmark. If the connection fails, review the parameters and retry.
Click OK to close the alert window.
Click Add to create and add the configured connection.
Commands
Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) includes the following executable commands for users to set up schedules or create playbook workflows. With the Test Command, users can execute these commands independently for playbook troubleshooting.
Integration API Note
For more information about the Sumo Logic API, refer to the Sumo Logic CSE API Reference
Note for Time-related parameters
The input format of time-related parameters may vary based on user account settings, which may cause the sample data in commands to differ from what is displayed. To adjust the time format, follow these steps:
Navigate to Configuration > Application Settings. Select Date/Time Format.
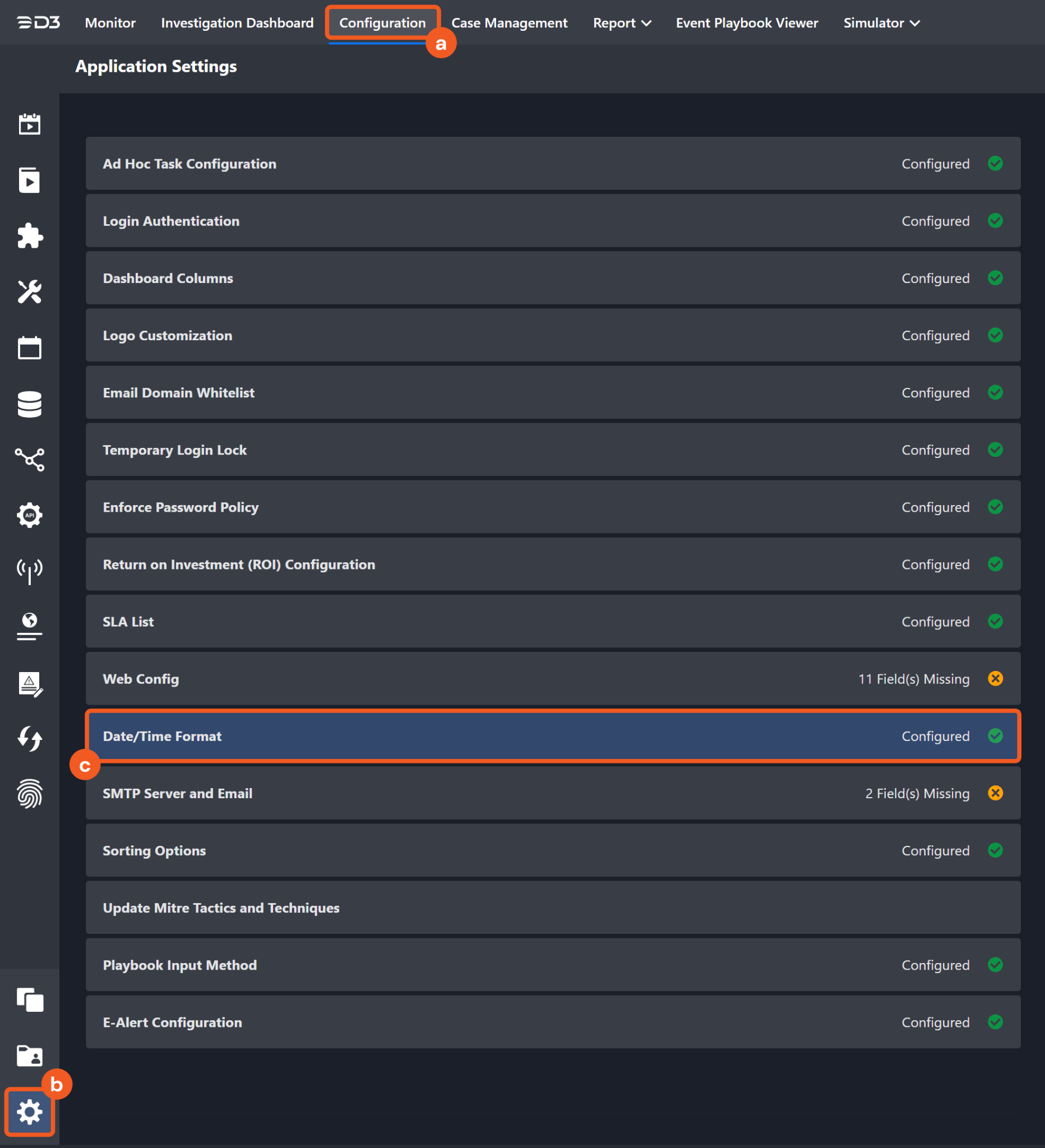
Choose the desired date and time format, then click on the Save button.
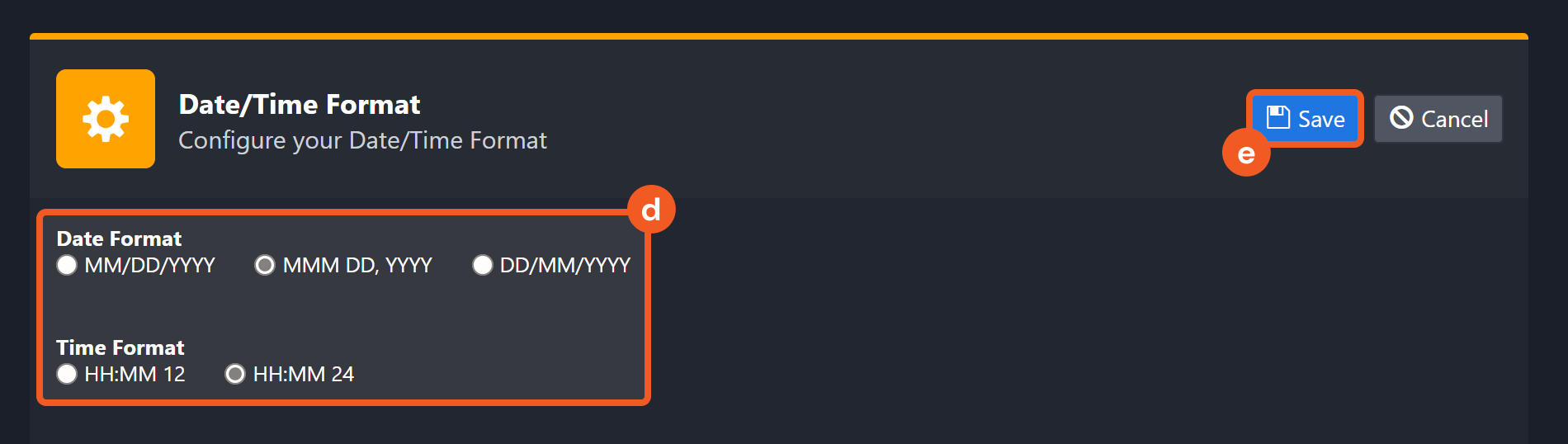
The selected time format will now be visible when configuring Date/Time command input parameters.
Add Comment To Insight
Adds a comment to the specified Insights.
READER NOTE
Insight IDs is a required parameter to run this command.
Run the Fetch Event command to obtain the Insight IDs. Insight IDs can be found in the raw data at the path $.data.objects[*].id.
The user who created the connection (using an access ID and key) will be the author of the comment, and their email will be included in the response.
Input
Input Parameter | Required/Optional | Description | Example |
Insight IDs | Required | The ID of the insights to add a comment. Insight IDs can be obtained using the Fetch Event command. |
JSON
|
Comment | Required | The comment to add to the Insights. | No Action Needed |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Add Comment To Insight failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 500. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: INTERNAL_SERVER_ERROR. |
Error Sample Data Add Comment To Insight failed. Status Code: 500. Message: INTERNAL_SERVER_ERROR. |
Add Suppress List Items To Suppress List
Adds the specified list items to a Suppress List.
READER NOTE
Suppress List ID is a required parameter to run this command.
Run the List Suppress Lists command to obtain the Suppress List IDs. Suppress List IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Suppress List ID | Required | The ID of the Suppress List to which items will be added. Suppress List IDs can be obtained using the List Suppress Lists command. | ***** |
Suppress List Items | Required | The JSON array of items to add to the specified Suppress List. Each item must have the "active", "description", and "value" fields. The "expiration" field is optional. If left empty, the suppress list item will never expire. The field "Active" is a Boolean, and "value" is the name of the suppress list item. The expiration date cannot be earlier than the current time. Otherwise, the error message "Please input valid suppress list items" will be returned. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Add Suppress List Items To Suppress List failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The value for parameter (Suppress List Items) is invalid. |
Error Sample Data Add Suppress List Items To Suppress List failed. Status Code: 400. Message: The value for parameter (Suppress List Items) is invalid.. |
Create Aggregation Rule
Creates an Aggregation Rule.
READER NOTE
Tuning Expression IDs is an optional parameter to run this command.
Run the List Rule Tuning Expressions command to obtain the Tuning Expression IDs. Tuning Expression IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Aggregation Functions | Required | The JSON array of objects defining the functions of the Aggregation Rule. Each function must include "arguments", "function", and "name" fields. The "arguments" field is an array of strings and must be formatted correctly. The valid values for the "function" field are: avg, count, count_distinct, first, last, max, min, and sum. |
JSON
|
Asset Field | Optional | The asset field of the Aggregation Rule. At least one of the Asset Field or Entity Selectors parameters must be defined. | device_ip |
Description Expression | Required | The description expression for the Aggregation Rule. | This is a test aggregation rule. |
Enabled | Optional | Whether to enable the Aggregation Rule. Available options are:
By default, the value is True. | True |
Entity Selectors | Optional | The JSON array defining the entity selectors of the Aggregation Rule. Each entity selector must have the "entityType" and "expression" fields. Note that:
|
JSON
|
Group By Asset | Optional | Whether the Aggregation Rule is grouped by an asset. Available options are:
By default, the value is True. | True |
Group By Fields | Optional | The fields to group the Aggregation Rule by. |
JSON
|
Is Prototype | Optional | Whether the Aggregation Rule is a prototype. Available options are:
By default, the value is False. | True |
Match Expression | Required | The match expression of the Aggregation Rule. | metadata_vendor = 'Amazon AWS'\nAND metadata_product = 'CloudTrail'\nAND metadata_deviceEventId IN (\n 'AwsApiCall-GetAccessKeyLastUsed',\n 'AwsApiCall-GetAccountAuthorizationDetails',\n 'AwsApiCall-GetAccountPasswordPolicy',\n 'AwsApiCall-GetGroupPolicy',\n 'AwsApiCall-GetUserPolicy',\n 'AwsApiCall-ListAccessKeys',\n 'AwsApiCall-ListGroupsForUser',\n 'AwsApiCall-ListPolicies',\n 'AwsApiCall-DescribeDBSnapshots',\n 'AwsApiCall-GetAccountSummary',\n 'AwsApiCall-GetCredentialReport',\n 'AwsApiCall-GetGroup',\n 'AwsApiCall-GetUser',\n 'AwsApiCall-ListEntitiesForPolicy',\n 'AwsApiCall-ListGroups',\n 'AwsApiCall-ListUserPolicies',\n 'AwsApiCall-ListUsers'\n)\nand NOT array_contains(listMatches, 'AWS_admin_ips')\nand NOT array_contains(listMatches, 'AWS_admin_users') |
Name | Required | The unique name of the Aggregation Rule. | Test Aggregation Rule |
Name Expression | Required | The name expression of the Aggregation Rule. | Test Aggregation Rule-1 |
Parent Jask ID | Optional | The Parent Jask ID of the Aggregation Rule. | ***** |
Score Mapping | Required | Defines the score mapping of the Aggregation Rule. The score mapping "type" must be set to constant, fieldValue, or fieldValueMapping. The default score is an estimate of the criticality of the activity in question. It should be a rank between 0 (lowest) and 10 (highest). Signals with a severity value of 0 do not contribute to the Insight algorithm. |
JSON
|
Stream | Required | The stream of the Aggregation Rule. | record |
Summary Expression | Optional | The summary expression of the Aggregation Rule. | Test Aggregation Rule. AWS CloudTrail reconnaissance activity detected by user: user_username from source IP: srcDevice_ip |
Tags | Optional | The tags for the Aggregation Rule. |
JSON
|
Trigger Expression | Required | The trigger expression of the Aggregation Rule. | distinct_eventid_count > 9 |
Tuning Expression IDs | Optional | The tuning expression IDs for the Aggregation Rule. Tuning expression IDs can be obtained using the List Rule Tuning Expressions command. While global Rule Tuning Expressions apply to all rules, only the non-global tuning expressions must be retrieved. |
JSON
|
Window Size | Required | The length of time across which the Aggregation Rule is applied. Available options are:
This parameter will be set to CUSTOM (regardless of the input value) if the Window Size in Milliseconds parameter is defined. | CUSTOM |
Window Size in Milliseconds | Optional | The length of time across which the Aggregation Rule is applied in milliseconds. This value can be defined when the Window Size parameter is set to CUSTOM. If this parameter is defined, the defined value for the Window Size parameter will be automatically set to CUSTOM. | 600000 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Create Aggregation Rule failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: rule name already exists. |
Error Sample Data Create Aggregation Rule failed. Status Code: 400. Message: rule name already exists. |
Create Chain Rule
Creates a Chain Rule. A Chain Rule has multiple rule expressions (e.g. two or more types of events) that must be matched a certain number of times within a specified time window for the rule to fire a Signal.
READER NOTE
Tuning Expression IDs is an optional parameter to run this command.
Run the List Rule Tuning Expressions command to obtain the Tuning Expression IDs. Tuning Expression IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Asset Field | Optional | The asset field of the Chain Rule. At least one of the Asset Field or Entity Selectors parameters must be defined. | user_username |
Description | Required | The description for the Chain Rule. | TEST Desc. Chain Rule A |
Enabled | Optional | Whether to enable the Chain Rule. Available options are:
By default, the value is True. | True |
Entity Selectors | Optional | The JSON array defining the entity selectors of the Chain Rule. Each entity selector must have the "entityType" and "expression" fields. Note that:
|
JSON
|
Expressions And Limits | Required | The JSON array of the expressions and limits of the Chain Rule. Each object must have the "expression" and "limit" fields. |
JSON
|
Group By Fields | Optional | The fields to group the Chain Rule by. |
JSON
|
Is Prototype | Optional | Whether the Chain Rule is a prototype. Available options are:
By default, the value is False. | True |
Name | Required | The name of the Chain Rule. | TEST Chain Rule A1 |
Ordered | Optional | Whether matches must occur in the same order as the rule expressions are arranged. Available options are:
If True is selected, there must be two rule expressions, and matches must occur in the specified order. If False is selected, matches can occur in any order. By default, the value is False. | False |
Parent Jask ID | Optional | The Parent Jask ID of the Chain Rule. | ***** |
Score | Required | Defines the score of the Chain Rule. The score is a measure of the criticality of the activity in question and should be ranked between 0 (lowest) and 10 (highest). Signals with a severity value of 0 do not affect the Insight algorithm. | 1 |
Stream | Required | The stream of the Chain Rule. | record |
Summary Expression | Optional | The summary expression of the Chain Rule. | Test Lateral movement detected to host |
Tags | Optional | The tags for the Chain Rule. |
JSON
|
Tuning Expression IDs | Optional | The tuning expression IDs for the Chain Rule. Tuning expression IDs can be obtained using the List Rule Tuning Expressions command. While Global Rule Tuning Expressions apply to all rules, only the non-global tuning expressions must be retrieved. |
JSON
|
Window Size | Required | The length of time across which the Chain Rule is applied. Available options are:
This parameter will be set to CUSTOM (regardless of the input value) if the Window Size in Milliseconds parameter is defined. | CUSTOM |
Window Size in Milliseconds | Optional | The length of time across which the Chain Rule is applied in milliseconds. This value can be defined when the Window Size parameter is set to CUSTOM. If this paramete is defined, the defined value for the Window Size parameter will be automatically set to CUSTOM. | 900000 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Create Chain Rule failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: rule name already exists. |
Error Sample Data Create Chain Rule failed. Status Code: 400. Message: rule name already exists. |
Create Custom Insight
Generates an Insight based on an Entity's Activity Score, which is the total severity of the unique Signals that have been triggered on the Entity over a certain time period. For more information about Custom Insights, see Configure a Custom Insight | Sumo Logic CSE Docs.
READER NOTE
Rule IDs is an optional parameter to run this command.
Run the List Rules command to obtain the Rule IDs. Rule IDs can be found in the raw data at the path $.data.objects[*].id
The name of the Custom Insight must be unique. Otherwise, the error message "Custom Insight Name Already Exists" will be returned.
Input
Input Parameter | Required/Optional | Description | Example |
Description | Required | The description for the Custom Insight. | Custom insights description |
Dynamic Severity | Optional | The JSON array defines the dynamic severity based on the severity of the Signals that will trigger the Insight. Each dynamic severity object must have the "insightSeverity"and "minimumSignalSeverity" fields. To use a constant severity, define it with the Constant Severity parameter. |
JSON
|
Enabled | Required | Whether to enable the Custom Insight. Available options are:
| True |
Name | Required | The unique name of the Custom Insight. | Custom Insight with rule id |
Ordered | Required | Whether Signals must occur in the exact order defined when multiple Signal expressions have been configured. If set to False, Signals will occur in any order. Available options are:
| True |
Rule IDs | Optional | The IDs of the rules for which a Custom Insight will be generated based on one or more rules firing Signals. Rule IDs can be obtained using the List Rules command. To have the Custom Insight be generated based on specific Signals, use the Signal Names parameter. Define either the Rule IDs or Signal Names parameter, but not both. |
JSON
|
Constant Severity | Required | The constant severity level. Available options are:
To configure dynamic severity, use the Dynamic Severity parameter. | High |
Signal Names | Optional | The names of the Signals that the Custom Insight will be generated based on. To have the Custom Insight be generated based on one or more rules firing Signals, define them with the Rule IDs parameter. Define either the Rule IDs or Signal Names parameters, but not both. |
JSON
|
Tags | Optional | The tags for the Custom Insight. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Create Custom Insight failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: CustomInsight Name Already Exists |
Error Sample Data Create Custom Insight failed. Status Code: 400. Message: CustomInsight Name Already Exists. |
Create Insight From Signals
Creates an Insight from the specified Signals.
READER NOTE
Signal IDs is a required parameter to run this command.
Run the List Signals command to obtain the Signal IDs. Signal IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Signal IDs | Required | The IDs of the Signals from which to create an Insight. Signal IDs can be obtained using the List Signals command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Create Insight From Signals failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Signals with the following ID(s) were not found. |
Error Sample Data Create Insight From Signals failed. Status Code: 404. Message: Signals with the following ID(s) were not found. |
Create Legacy Match Rule
Creates a Legacy Match Rule.
READER NOTE
Tuning Expression IDs is an optional parameter to run this command.
Run the List Rule Tuning Expressions command to obtain the Tuning Expression IDs. Tuning Expression IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Asset Field | Optional | The asset field of the Legacy Match Rule. At least one of the Asset Field or Entity Selectors parameters must be defined. | device_hostname |
Description | Required | The description for the Legacy Match Rule. | Test Descr Legacy Match Rule A |
Enabled | Optional | Whether to enable the Legacy Match Rule. Available options are:
By default, the value is True. | True |
Entity Selectors | Optional | The JSON array defining the entity selectors of the Legacy Match Rule. Each entity selector must have the "entityType" and "expression" fields. Note that:
|
JSON
|
Expression | Required | The expression of the Legacy Match Rule. | lower(parentBaseImage) like '%winword.exe'\nAND lower(baseImage) like '%csc.exe' |
Is Prototype | Optional | Whether the Legacy Match Rule is a prototype. Available options are:
By default, the value is False. | True |
Name | Required | The name of the Legacy Match Rule. | Test Legacy Match Rule B |
Parent Jask ID | Optional | The Parent Jask ID of the Legacy Match Rule. | ***** |
Score | Required | Defines the score of the Legacy Match Rule. The score is an estimate of the criticality of the activity in question. It should be a rank between 0 (lowest) and 10 (highest). Signals with a severity value of 0 do not contribute to the Insight algorithm. | 10 |
Stream | Required | The stream of the Legacy Match Rule. | record |
Summary Expression | Optional | The summary expression of the Legacy Match Rule. | TEST. Observed possible CVE-2017-8759 exploit on device_hostname |
Tags | Optional | The tags for the Legacy Match Rule. |
JSON
|
Tuning Expression IDs | Optional | The tuning expression IDs for the Legacy Match Rule. Tuning expression IDs can be obtained using the List Rule Tuning Expressions command. While Global Rule Tuning Expressions apply to all rules, only the non-global tuning expressions must be retrieved. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Create Legacy Match Rule failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Tuning Expression with the following ID(s) were not found. |
Error Sample Data Create Legacy Match Rule failed. Status Code: 404. Message: Tuning Expression with the following ID(s) were not found. |
Create or Update Signal Enrichments
Creates or updates enrichments for the specified Signals.
READER NOTE
Signal IDs is a required parameter to run this command.
Run the List Signals command to obtain the Signal IDs. Signal IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Signal IDs | Required | The IDs of the Signals to create or update enrichments. Signal IDs can be obtained using the List Signals command. |
JSON
|
Enrichment Type | Required | The type of enrichment to create or update. | Command |
Data Object | Required | The enrichment payload object for which to create or update. Refer to Create or update an Enrichment on a Signal | Sumo Logic CSE for more information on the payload schema and the available keys. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Create or Update Signal Enrichments failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Signal with ID=xxx not found. |
Error Sample Data Create or Update Signal Enrichments failed. Status Code: 404. Message: Signal with ID=xxx not found. |
Create Rule Tuning Expression
Creates a Rule Tuning Expression.
READER NOTE
Rule IDs is an optional parameter to run this command.
Run the List Rules command to obtain the Rule IDs. Rule IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Name | Required | The name for the Rule Tuning Expression. | RTE-0106a |
Description | Required | The description for the Rule Tuning Expression. | TEST0106 |
Enabled | Required | Whether to enable the Rule Tuning Expression. Available options are:
| True |
Include Or Exclude | Required | Whether to include or exclude records matching the expression. | Exclude |
Is Global | Required | Whether the Rule Tuning Expression is global (True) or only applies to the selected rules (False). | False |
Rule IDs | Optional | The IDs of the rules to apply the Rule Tuning Expression. Rule IDs can be obtained using the List Rules command. This parameter is required when the Is Global parameter is False. |
JSON
|
Expression | Required | The Rule Tuning Expression statement. | user_username=sysint |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Create Rule Tuning Expression failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Rule with ID=xxx not found. |
Error Sample Data Create Rule Tuning Expression failed. Status Code: 404. Message: Rule with ID=xxx not found. |
Create Templated Match Rule
Creates a Templated Match Rule.
READER NOTE
Tuning Expression IDs is an optional parameter to run this command.
Run the List Rule Tuning Expressions command to obtain the Tuning Expression IDs. Tuning Expression IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Asset Field | Optional | The asset field of the Templated Match Rule. At least one of the Asset Field or Entity Selectors parameters must be defined. | device_hostname |
Description Expression | Required | The description expression for the Templated Match Rule. | TEST desc. Templated Match Rule A |
Enabled | Optional | Whether to enable the Templated Match Rule. Available options are:
By default, the value is True. | True |
Entity Selectors | Optional | The JSON array defining the entity selectors of the Templated Match Rule. Each entity selector must have the "entityType" and "expression" fields. Note that:
|
JSON
|
Expression | Required | The expression of the Templated Match Rule. | baseImage like '%.exe'\nAND lower(commandLine) like '%-dc%'\nAND lower(commandLine) like '%-domain%'\nAND lower(commandLine) like '%-action%'\nAND \n(\n lower(commandLine) like '%gpp'\nOR lower(commandLine) like '%ad'\n) |
Is Prototype | Optional | Whether the Templated Match Rule is a prototype. Available options are:
By default, the value is False. | True |
Name | Required | The name of the Templated Match Rule. | TEST Templated Match Rule A |
Name Expression | Required | The name expression of the Templated Match Rule. | TEST Templated Match Rule A. FireEye ADPassHunt Tool |
Parent Jask ID | Optional | The Parent Jask ID of the Templated Match Rule. | ***** |
Score Mapping | Required | Defines the score mapping of the templated match rule. The score mapping “type” must be set to constant, fieldValue, or fieldValueMapping. The default score is an estimate of the criticality of the activity in question. It should be a rank between 0 (lowest) and 10 (highest). Signals with a severity value of 0 do not contribute to the Insight algorithm. |
JSON
|
Stream | Required | The stream of the Templated Match Rule. | record |
Summary Expression | Optional | The summary expression of the Templated Match Rule. | ADPassHunt (credential stealer) tool associated command line arguments detected on host |
Tags | Optional | The tags for the Templated Match Rule. |
JSON
|
Tuning Expression IDs | Optional | The Tuning Expression IDs for the Templated Match Rule. Tuning Expression IDs can be obtained using the List Rule Tuning Expressions command. While global Rule Tuning Expressions apply to all rules, only the non-global tuning expressions must be retrieved. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Create Templated Match Rule failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Tuning Expression with the following ID(s) were not found. |
Error Sample Data Create Templated Match Rule failed. Status Code: 404. Message: Tuning Expression with the following ID(s) were not found. |
Create Threshold Rule
Creates a Threshold Rule. A Threshold Rule is triggered when the rule expression is met at least a certain number of times during a specified period of time.
READER NOTE
Tuning Expression IDs is an optional parameter to run this command.
Run the List Rule Tuning Expressions command to obtain the Tuning Expression IDs. Tuning Expression IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Asset Field | Optional | The asset field of the Threshold Rule. At least one of the Asset Field or Entity Selectors parameters must be defined. | device_ip |
Count Distinct | Required | Whether to count only unique values for a field. This allows the rule to count the number of records with distinct values for a specific field instead of simply counting records that match the rule expression. Available options are:
Use the Count Field parameter to select the field of interest. | True |
Count Field | Optional | The field to use for counting the number of records with distinct values. This parameter is required when the Count Distinct parameter is set to True. If Count Distinct is set to False, this parameter will be ignored. | action |
Description | Required | The description for the Threshold Rule. | TEST Desc. Threshold Rule A |
Enabled | Optional | Whether to enable the Threshold Rule. Available options are:
By default, the value is True. | True |
Entity Selectors | Optional | The JSON array defining the entity selectors of the Threshold Rule. Each entity selector must have the "entityType" and "expression" fields. Note that:
|
JSON
|
Expression | Required | The input string that includes the boolean expression which triggers the Threshold Rule to fire if the Enabled parameter is set to True. | metadata_vendor = 'Amazon AWS'\nAND metadata_product = 'CloudTrail'\nAND fields['errorCode'] = 'AccessDenied'\nAND fields['userIdentity.arn'] like '%:iam:%'\nAND device_ip != 'AWS Internal'\nAND device_ip not like '%.amazonaws.com' |
Group By Fields | Optional | The fields to group the Threshold Rule by. |
JSON
|
Is Prototype | Optional | Whether the Threshold Rule is a prototype. Available options are:
By default, the value is False. | True |
Limit | Required | The number of records that must match the rule expression within the specified time interval for the Threshold Rule to trigger. | 10 |
Name | Required | The name of the Threshold Rule. | TEST Threshold Rule A |
Parent Jask ID | Optional | The Parent Jask ID of the Threshold Rule. | ***** |
Score | Required | Defines the score of the Threshold rule. The score is an estimate of the criticality of the activity in question. It should be a rank between 0 (lowest) and 10 (highest). Signals with a severity value of 0 do not contribute to the Insight algorithm. | 1 |
Stream | Required | The stream of the Threshold Rule. | record |
Summary Expression | Optional | The summary expression of the Threshold Rule. | TEST. AWS API Call attempts denied by user |
Tags | Optional | The tags for the Threshold Rule. |
JSON
|
Tuning Expression IDs | Optional | The tuning expression IDs for the Threshold Rule. Tuning expression IDs can be obtained using the List Rule Tuning Expressions command. While global Rule Tuning Expressions apply to all rules, only the non-global tuning expressions must be retrieved. |
JSON
|
Version | Required | The version number of the Threshold Rule. | 1 |
Window Size | Required | The length of time across which the threshold rule is applied. Available options are:
This parameter will be set to CUSTOM (regardless of the input value) if the Window Size in Milliseconds parameter is defined. | CUSTOM |
Window Size in Milliseconds | Optional | The length of time across which the threshold rule is applied in milliseconds. This value can be defined when the Window Size parameter is set to CUSTOM. If this parameter is defined, the defined value for the Window Size parameter will be automatically set to CUSTOM. | 1200000 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Create Threshold Rule failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Tuning Expression with the following ID(s) were not found. |
Error Sample Data Create Threshold Rule failed. Status Code: 404. Message: Tuning Expression with the following ID(s) were not found. |
Delete Match List Items
Deletes Match List Items using the given Match List Item IDs.
READER NOTE
Match List Item IDs is a required parameter to run this command.
Run the List Match List Items command to obtain the Match List Item IDs. Match List Item IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Match List Item IDs | Required | The IDs of the Match List Items to delete. Match List Item IDs can be obtained using the List Match List Items command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Delete Match List Items failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Match List Item with the following ID(s) were not found. |
Error Sample Data Delete Match List Items failed. Status Code: 404. Message: Match List Item with the following ID(s) were not found. |
Delete Suppress List Items
Deletes Suppress List Items using the given Suppress List Item IDs.
READER NOTE
Suppress List Item IDs is a required parameter to run this command.
Run the List Suppress List Items command to obtain the Suppress List Item IDs. Suppress List IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Suppress List Item IDs | Required | The IDs of the Suppress List Items to delete. Suppress List Item IDs can be obtained using the List Suppress List Items command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Delete Suppress List Items failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: A Suppress List Item with id=xxx could not be found. |
Error Sample Data Delete Suppress List Items failed. Status Code: 404. Message: A Suppress List Item with id=xxx could not be found. |
Fetch Event
Retrieves Insights from Sumo Logic CSE based on the specified criteria.
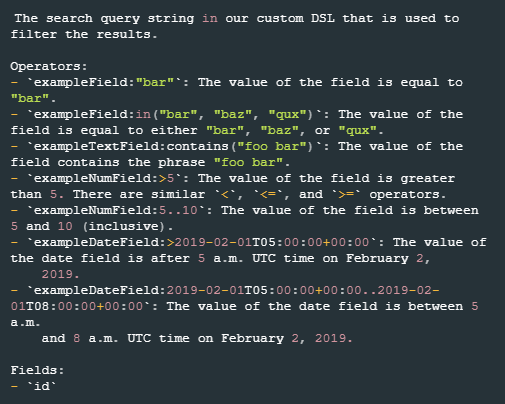
READER NOTE
For the syntax of the Search Condition parameter, refer to the Sumo Logic CSE API reference. A screenshot of the reference is provided below.
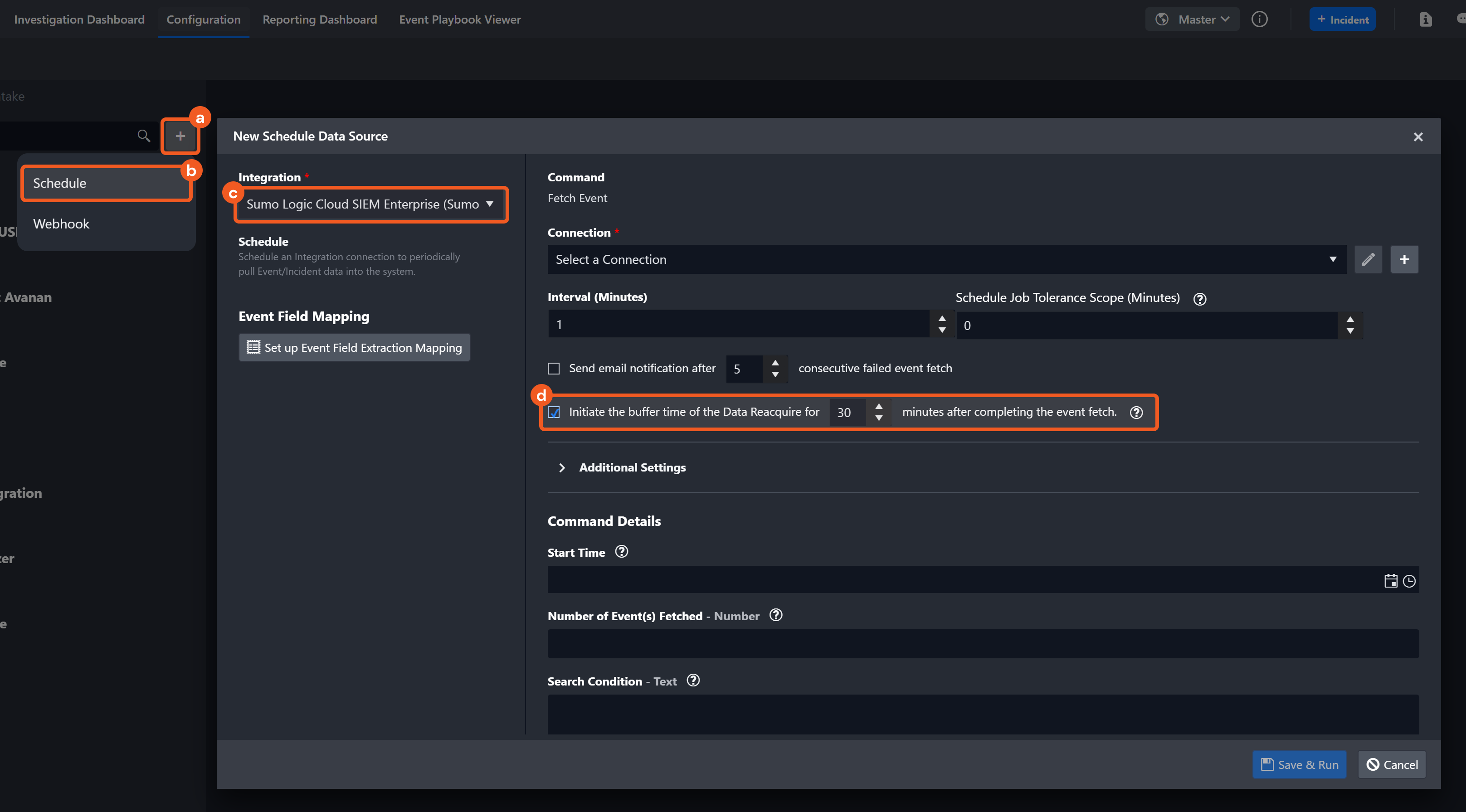
Instead of using tolerance scope, it is recommended to check the Initiate the buffer time of the Data Reacquire for [x] minutes after completing the event fetch checkbox when setting up a new Data Ingestion schedule.
1. Navigate to Configuration > Data Ingestion.
2. Add a New Schedule Data Source for the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) Integration and check the Initiate the buffer time of the Data Reacquire for [x] minutes after completing the event fetch checkbox. Optionally, adjust the buffer time as necessary.
If no input parameters are defined, all events will be returned and fetched by the Original Time (the “timestamp” key in the response data) and the Insight Created Time (the “created” key in the response data).
Input
Input Parameter | Required/Optional | Description | Example |
Start Time | Optional | The start of the time range (in UTC) to fetch events. | 2023-01-04 00:00 |
End Time | Optional | The end of the time range (in UTC) to fetch events. | 2023-01-05 00:00 |
Number of Event(s) Fetched | Optional | The maximum number of events to fetch. If the value is 0, a negative number, or not specified, the command will return all events within the defined time range. | 10 |
Search Condition | Optional | The search query string to filter events. Refer to Get the list of Insights for a given query | Sumo Logic CSE for more information about the query syntax and the available fields. | status:in("new") name:contains("Malicious Activity") severity:"MEDIUM" |
Offset | Optional | The offset index of the returning results. This parameter will be ignored if the input value for the Number of Event(s) parameter is 0, a negative number, or not specified. By default, the value is 0. | 0 |
Time Filter Field | Optional | The time filter field to fetch events. Available options are:
By default, the value is Insight Created Time. This parameter will be ignored if the Use D3 Default Time Filter parameter is set to True. | Original Timestamp |
Use D3 Default Time Filter | Optional | Whether to use the D3 default time filter to fetch events. Available options are:
Setting this parameter to True will apply the Original Time (“timestamp” key in the response data) and Insight Created Time (“created” key in the response data) time filters. In this case, the Time Filter Field parameter will be ignored. By default, the value is True. | False |
Record Summary Fields | Optional | A list of fields (excluding subfields) to aggregate from each Insight's records into a summarized list directly on the Insight object in the response. |
JSON
|
Tolerance Scope | Optional | Note: Instead of using tolerance scope, it is recommended to check the Initiate the buffer time of the Data Reacquire for [x] minutes after completing the event fetch checkbox when setting up a new Data Ingestion schedule. Refer to the Reader Note for more information. A time window (in minutes) that extends the time range for fetching events by subtracting from the specified start time. Tolerance scope helps prevent data loss by accounting for API response delays caused by temporary server-side data unavailability—arising from processing and synchronization—from the vendor. With the tolerance scope applied, events will be fetched within the range of (Start Time - Tolerance Scope) to End Time. By default, the tolerance scope is set to 0. | 3 |
Output
To view the sample output data for all commands, refer to this article.
Fetch Event Field Mapping
Please note that Fetch Event commands require event field mapping. Field mapping plays a key role in the data normalization process part of the event pipeline. Field mapping converts the original data fields from the different providers to the D3 fields which are standardized by the D3 Model. Please refer to Event and Incident Intake Field Mapping for details.
If you require a custom field mapping, click +Add Field to add a custom field mapping. You may also remove built-in field mappings by clicking x. Please note that two underscore characters will automatically prefix the defined Field Name as the System Name for a custom field mapping. Additionally, if an input Field Name contains any spaces, they will automatically be replaced with underscores for the corresponding System Name.
As a system integration, the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) integration has some pre-configured field mappings for default field mapping.
Default Event Source
The Default Event Source is the default set of field mappings that are applied when this fetch event command is executed. For out-of-the-box integrations, you will find a set of field mapping provided by the system. Default event source provides field mappings for common fields from fetched events. The default event source has a “Main Event JSON Path” (i.e., $.data.objects) that is used to extract a batch of events from the response raw data. Click Edit Main JSON Path to view the “Main Event JSON Path”.
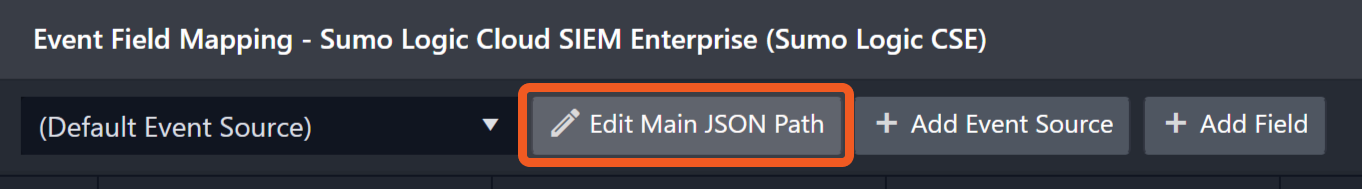
Main Event JSON Path: $.data.objects
The Main Event JSON Path determines the root path where the system starts parsing raw response data into D3 event data. The JSON path begins with $, representing the root element. The path is formed by appending a sequence of child elements to $, each separated by a dot (.). Square brackets with nested quotation marks (['...']) should be used to separate child elements in JSON arrays.
For example, the root node of a JSON Path is data.objects. The child node denoting the Unique Event Key field would be id. Putting it together, the JSON Path expression to extract the Unique Event Key is $.data.objects[*].id.
The pre-configured field mappings are detailed below:
Field Name | Source Field |
Unique Event Key | .id |
Event Type | .name |
Severity | .severity |
Status | .status.displayName |
Description | .description |
Start Time | .timestamp |
Created Time | .created |
Updated Time | .lastUpdated |
Closed Time | .closed |
Event Name | .name |
Organization ID | .orgId |
Source type | .source |
Readable ID | .readableId |
Signal Names | .signals[*].name |
Signal IDs | .signals[*].id |
Signal Stages | .signals[*].stage |
Signal Severities | .signals[*].severity |
Entity Type | .entity.entityType |
Device | .artifacts[?(@.name=='device_hostname')].value |
Hostname | .entity.hostname |
Username | .artifacts[?(@.name=='user_username')].value |
Destination IP address | .artifacts[?(@.name=='dstDevice_ip')].value |
Source IP address | .artifacts[?(@.name=='srcDevice_ip')].value |
Threat Name | .artifacts[?(@.name=='threat_name')].value |
Source Hostname | .artifacts[?(@.name=='srcDevice_hostname')].value |
Error Handling
If the Return Data is Successful with No Event Data or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Fetch Event failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: access_declined. |
Error Sample Data Fetch Event failed. Status Code: 401. Message: access_declined. |
Get Custom Match List Columns
Retrieves Custom Match List columns using the given Custom Match List Column IDs.
READER NOTE
Custom Match List Column IDs is a required parameter to run this command.
Run the List Custom Match List Columns command to obtain the Custom Match List Column IDs. Custom Match List Column IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Custom Match List Column IDs | Required | The IDs of the Custom Match List columns to retrieve. Custom Match List Column IDs can be obtained using the List Custom Match List Columns command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Custom Match List Columns failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Custom Match List Column with the following ID(s) were not found. |
Error Sample Data Get Custom Match List Columns failed. Status Code: 404. Message: Custom Match List Column with the following ID(s) were not found. |
Get Insight Comments
Retrieves Insight comments using the given Insight IDs.
READER NOTE
Insight IDs is a required parameter to run this command.
Run the Fetch Event command to obtain the Insight IDs. Insight IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Insight IDs | Required | The IDs of the Insights for which to retrieve comments. Insight IDs can be obtained using the Fetch Event command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Insight Comments failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Insight with the following ID(s) were not found. |
Error Sample Data Get Insight Comments failed. Status Code: 404. Message: Insight with the following ID(s) were not found. |
Get Insight Enrichments
Retrieves enrichments from Insights using the given Insight IDs.
READER NOTE
Insight IDs is a required parameter to run this command.
Run the Fetch Event command to obtain the Insight IDs. Insight IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Insight IDs | Required | The IDs of the Insights for which to retrieve enrichments. Insight IDs can be obtained using the Fetch Event command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Insight Enrichments failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Insight with the following ID(s) were not found. |
Error Sample Data Get Insight Enrichments failed. Status Code: 404. Message: Insight with the following ID(s) were not found. |
Get Insight Entities
Retrieves involved entities of Insights using the given Insight IDs.
READER NOTE
Insight IDs is a required parameter to run this command.
Run the Fetch Event command to obtain the Insight IDs. Insight IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Insight IDs | Required | The IDs of the Insights for which to retrieve involved entities. Insight IDs can be obtained using the Fetch Event command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Insight Entities failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Insight with the following ID(s) were not found. |
Error Sample Data Get Insight Entities failed. Status Code: 404. Message: Insight with the following ID(s) were not found. |
Get Insight History
Retrieves the history of Insights using the given Insight IDs.
READER NOTE
Insight IDs is a required parameter to run this command.
Run the Fetch Event command to obtain the Insight IDs. Insight IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Insight IDs | Required | The IDs of the Insights for which to retrieve the history. Insight IDs can be obtained using the Fetch Event command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Insight History failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Insight with the following ID(s) were not found. |
Error Sample Data Get Insight History failed. Status Code: 404. Message: Insight with the following ID(s) were not found. |
Get Match List Items
Retrieves Match List Items using the given Match List Item IDs.
READER NOTE
Match List Item IDs is a required parameter to run this command.
Run the List Match List Items command to obtain the Match List Item IDs. Match List Item IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Match List Item IDs | Required | The IDs of the Match List Items to retrieve. Match List Item IDs can be obtained using the List Match List Items command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Match List Items failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Match List Item with the following ID(s) were not found. |
Error Sample Data Get Match List Items failed. Status Code: 404. Message: Match List Item with the following ID(s) were not found. |
Get Match Lists
Retrieves Match Lists using the given Match List IDs.
READER NOTE
Match List IDs is a required parameter to run this command.
Run the List Match Lists command to obtain the Match List IDs. Match List IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Match List IDs | Required | The IDs of the Match Lists to retrieve. Match List IDs can be obtained using the List Match Lists command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Match Lists failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Match List with the following ID(s) were not found. |
Error Sample Data Get Match Lists failed. Status Code: 404. Message: Match List with the following ID(s) were not found. |
Get Signal Enrichments
Retrieves enrichments of Signals using the given Signal IDs.
READER NOTE
Signal IDs is a required parameter to run this command.
Run the List Signals command to obtain the Signal IDs. Signal IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Signal IDs | Required | The IDs of the Signals for which to retrieve enrichments. Signal IDs can be obtained using the List Signals command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Signal Enrichments failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Signal with ID=xxx could not be found. |
Error Sample Data Get Signal Enrichments failed. Status Code: 404. Message: Signal with ID=xxx could not be found. |
Get Suppress List Items
Retrieves Suppress List Items using the given Suppress List Item IDs.
READER NOTE
Suppress List Item IDs is a required parameter to run this command.
Run the List Suppress List Items command to obtain the Suppress List Item IDs. Suppress List Item IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Suppress List Item IDs | Required | The IDs of the Suppress List Items to retrieve. Suppress List Item IDs can be obtained using the List Suppress List Item command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Suppress List Items failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: A Suppress List Item with id=xxx could not be found. |
Error Sample Data Get Suppress List Items failed. Status Code: 404. Message: A Suppress List Item with id=xxx could not be found. |
Get Suppress Lists
Retrieves Suppress Lists using the given Suppress List IDs.
READER NOTE
Suppress List IDs is a required parameter to run this command.
Run the List Suppress Lists command to obtain the Suppress List IDs. Suppress List IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Suppress List IDs | Required | The IDs of the Suppress Lists to retrieve. Suppress List IDs can be obtained using the List Suppress Lists command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Suppress Lists failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: A Suppress List with id=xx could not be found. |
Error Sample Data Get Suppress Lists failed. Status Code: 404. Message: A Suppress List with id=xx could not be found. |
List Custom Match List Columns
Lists all Custom Match List Columns.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Custom Match List Columns failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: User could not be found. |
Error Sample Data List Custom Match List Columns failed. Status Code: 401. Message: User could not be found. |
List Match List Items
Lists Match List Items using the given Match List Item IDs.
READER NOTE
Match List IDs is an optional parameter to run this command.
Run the List Match Lists command to obtain the Match List IDs. Match List IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Limit | Optional | The maximum number of Match List Items to return. By default, all Match List Items matching the defined query will be returned. | 50 |
Value | Optional | The Match List Item value to search for. | desktop-hellod3 |
Match List IDs | Optional | The IDs of the Match Lists to retrieve items. Match List IDs can be obtained using the List Match Lists command. |
JSON
|
Query | Optional | The query string used to filter Match List Item results. Refer to Get a list of Match List Items | Sumo Logic CSE for more information about the query syntax. | targetColumn:in("SrcIp", "Hostname") |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Match List Items failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Match List with ID=xxx could not be found. |
Error Sample Data List Match List Items failed. Status Code: 404. Message: Match List with ID=xxx could not be found. |
List Match Lists
Lists Match Lists.
Input
Input Parameter | Required/Optional | Description | Example |
Limit | Optional | The maximum number of Match Lists to return. By default, all Match Lists in the system will be returned. | 50 |
Sort Field | Optional | The field used to sort Match Lists. Some available sort fields are created, description, id, name, and lastUpdated. By default, the field used for sorting is the name of Match Lists. | name |
Sort Direction | Optional | The sort direction for the returned Match Lists. Available options are:
By default, the value is Ascending. | Ascending |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Match Lists failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: User could not be found. |
Error Sample Data List Match Lists failed. Status Code: 401. Message: User could not be found. |
List Rules
Lists all rules matching the given query.
READER NOTE
For the syntax of the Query parameter, refer to the Sumo Logic CSE API reference. A screenshot of the reference is provided below for your convenience.
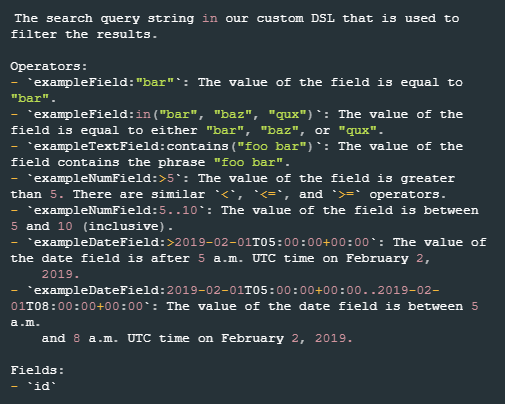
Input
Input Parameter | Required/Optional | Description | Example |
Query | Optional | The query string used to filter the returned rules. For example, to search for rules with a specific name, the query string name:contains("{{ruleName}}") can be used. Refer to Get the list of Rules for a given query | Sumo Logic CSE for more information about the query syntax. By default, all rules regardless of the query will be returned. | ruleType:in("match","templated match") tag:in("_mitreAttackTactic:TA0003") |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Rules failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 500. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Internal server error. |
Error Sample Data List Rules failed. Status Code: 500. Message: Internal server error. |
List Rule Tuning Expressions
Lists Rule Tuning Expressions.
Input
Input Parameter | Required/Optional | Description | Example |
Limit | Optional | The maximum number of Rule Tuning Expressions to return. By default, all Rule Tuning Expressions in the system will be returned. | 10 |
Sort Field | Optional | The field used to sort Rule Tuning Expressions. Available options are:
By default, the field used for sorting is Name. | Name |
Sort Direction | Optional | The sort direction to sort the Rule Tuning Expressions. Available options are:
By default, the value is Ascending. | Ascending |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Rule Tuning Expressions failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: User could not be found. |
Error Sample Data List Rule Tuning Expressions failed. Status Code: 401. Message: User could not be found. |
List Signals
Lists Signals.
READER NOTE
Signal IDs is an optional parameter to run this command.
If the Signal IDs have not been obtained, run this command with an empty Signal IDs parameter to obtain them.
For the syntax of the Query parameter, refer to the Sumo Logic CSE API reference. A screenshot of the reference is provided below.
Input
Input Parameter | Required/Optional | Description | Example |
Signal IDs | Optional | The IDs of the Signals for which to retrieve. If the Signal IDs have not been obtained, run the command with this parameter empty to obtain them. |
JSON
|
Query | Optional | The query string used to filter the returned Signals. Refer to Get the list of all Signals | Sumo Logic CSE. If the Signal IDs parameter is specified, this parameter will be ignored. If neither input parameters are specified, all Signals will be returned. | severity:>=6 timestamp:>=2023-01-04T02:00:00 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Signals failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Signal with ID=xxx could not be found. |
Error Sample Data List Signals failed. Status Code: 404. Message: Signal with ID=xxx could not be found. |
List Suppress List Items
Lists Suppress List Items.
READER NOTE
Suppress List IDs is an optional parameter to run this command.
Run the List Suppress Lists command to obtain the Suppress List IDs. Suppress List IDs can be found in the returned raw data at the path $.data.objects[*].id.
For the Query parameter’s syntax, refer to the Sumo Logic CSE API reference. A screenshot of the reference is provided below.
Input
Input Parameter | Required/Optional | Description | Example |
Limit | Optional | The maximum number of Suppress List Items to return. By default, all Suppress List Items matching the defined query will be returned. | 50 |
Value | Optional | The Suppress List Item value to search for. | desktop-hellod3 |
Suppress List IDs | Optional | The IDs of the Suppress Lists to retrieve items. Suppress List IDs can be obtained using the List Suppress Lists command. |
JSON
|
Query | Optional | The query string used to filter results. Refer to Get a list of Suppress List Items | Sumo Logic CSE for more information about the query syntax. | targetColumn:in("Custom") |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Suppress List Items failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 500. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: INTERNAL_SERVER_ERROR. |
Error Sample Data List Suppress List Items failed. Status Code: 500. Message: INTERNAL_SERVER_ERROR. |
List Suppress Lists
Lists Suppress Lists.
Input
Input Parameter | Required/Optional | Description | Example |
Limit | Optional | The maximum number of Suppress Lists to return. By default, all Suppress Lists will be returned. | 50 |
Sort Field | Optional | The field used to sort Suppress Lists. Some available values are: created, createdBy, defaultTtl, description, id, lastUpdated, lastUpdatedBy, name and targetColumn. By default, the field used for sorting is name. | name |
Sort Direction | Optional | The sort direction for the Suppression Lists. Available options are:
By default, the value is Ascending. | Ascending |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Suppress Lists failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 500. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: INTERNAL_SERVER_ERROR. |
Error Sample Data List Suppress Lists failed. Status Code: 500. Message: INTERNAL_SERVER_ERROR. |
On Dismiss Event
Updates the status of an Insight and adds the hardcoded comment "No Action" after the Insight has been ingested and dismissed as an event in D3 SOAR. This process can be automated if it has been configured with the integration connection. Refer to step 3i in Configuring D3 to Work with Sumo Logic Cloud SIEM Enterprise (Sumo Logic SIEM).
READER NOTE
Raw Data is a required parameter to run this command.
Run the Fetch Event command to obtain the returned Raw Data. Copy the returned raw data to be used as the input for this parameter.
Input
Input Parameter | Required/Optional | Description | Example |
Raw Data | Required | The JSON objects of the returned Insights from the Fetch Event command to update the status and add the hardcoded comment. | Refer to the Raw Data section of the Fetch Event command. |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | On Dismiss Event failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The value for parameter (Raw Data) is invalid. |
Error Sample Data On Dismiss Event failed. Status Code: 400. Message: You must have a valid Support account to call this API. |
Update Custom Match List Column
Updates a Custom Match List column using the given Custom Match List Column ID.
READER NOTE
Custom Match List Column ID is a required parameter to run this command.
Run the List Custom Match List Columns command to obtain the Custom Match List Column ID. Custom Match List Column IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Custom Match List Column ID | Required | The ID of the Custom Match List column in which values require updating. Custom Match List Column IDs can be obtained using the List Custom Match List Columns command. | ***** |
Custom Match List Column Name | Required | The updated name for the specified Custom Match List column. | Custom Match List Column Test |
Custom Match List Column Fields | Required | The updated fields of the specified Custom Match List column. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Custom Match List Column failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Custom Match List Column with id=xx could not be found. |
Error Sample Data Update Custom Match List Column failed. Status Code: 404. Message: Custom Match List Column with id=xx could not be found. |
Update Insight Assignee
Updates the assignee of the specified Insights.
READER NOTE
Insight IDs is a required parameter to run this command.
Run the Fetch Event command to obtain the Insight IDs. Insight IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Insight IDs | Required | The IDs of the Insights for which to update. Insight IDs can be obtained using the Fetch Event command. |
JSON
|
Assignee Type | Required | The assignee type. Available options are:
| USER |
Name | Required | The user name or team name of the assignee. User names and team names can be obtained from the Sumo Logic platform. The user name should be the email address of the user. | *****@*****.***** |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Insight Assignee failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Insight with ID=xxx not found. |
Error Sample Data Update Insight Assignee failed. Status Code: 404. Message: Insight with ID=xxx not found. |
Update Insight Enrichment
Creates or updates an Enrichment for the specified Insights.
READER NOTE
Insight IDs is a required parameter to run this command.
Run the Fetch Event command to obtain the Insight IDs. Insight IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Insight IDs | Required | The IDs of the Insights for which to create or update an enrichment. Insight IDs can be obtained using the Fetch Event command. |
JSON
|
Enrichment Type | Required | The type of enrichment to create or update. | nslookupHostname |
Data Object | Required | The enrichment payload object for which for which to create or update. Refer to Create or update an Enrichment on an Insight | Sumo Logic for more information on the payload schema and the available keys. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Insight Enrichment failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Insight with ID=xxx not found. |
Error Sample Data Update Insight Enrichment failed. Status Code: 404. Message: Insight with ID=xxx not found. |
Update Insight Severity
Updates the severity of the specified Insights.
READER NOTE
Insight IDs is a required parameter to run this command.
Run the Fetch Event command to obtain the Insight IDs. Insight IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Insight IDs | Required | The IDs of the Insights for which to update severity. Insight IDs can be obtained using the Fetch Event command. |
JSON
|
Severity | Required | The updated severity of the Insights. Available options are:
| High |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Insight Severity failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Insight with ID=xxx not found. |
Error Sample Data Update Insight Severity failed. Status Code: 404. Message: Insight with ID=xxx not found. |
Update Insight Status And Add Tag
Updates the status of the specified Insights and adds a tag.
READER NOTE
Insight IDs is a required parameter to run this command.
Run the Fetch Event command to obtain the Insight IDs. Insight IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Insight IDs | Required | The IDs of the Insights for which to update the status and add a tag. Insight IDs can be obtained using the Fetch Event command. |
JSON
|
Status | Required | The updated status of the Insights. The default statuses available are: new, inprogress, and closed. Additional statuses can be created from Sumo Logic CSE. | closed |
Resolution | Optional | The reason for closing the specified Insights. Available options are:
| Duplicate |
Tag Name | Required | The tag name to be added to the specified Insights. | DUPLICATED INSIGHT |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Insight Status And Add Tag failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Insight with ID=xxx not found. |
Error Sample Data Update Insight Status And Add Tag failed. Status Code: 404. Message: Insight with ID=xxx not found. |
Update Insight Status And Resolution
Updates the status and resolution of the specified Insights.
READER NOTE
Insight IDs is a required parameter to run this command.
Run the Fetch Event command to obtain the Insight IDs. Insight IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Insight IDs | Required | The IDs of the Insights for which to update. Insight IDs can be obtained using the Fetch Event command. |
JSON
|
Status | Required | The updated status of the Insights. The default statuses available are: new, inprogress, and closed. Additional statuses can be created from Sumo Logic CSE. | closed |
Resolution | Optional | The reason for closing the specified Insights. Available options are:
| False Positive |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Insight Status And Resolution failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Insight with ID=xxx not found. |
Error Sample Data Update Insight Status And Resolution failed. Status Code: 404. Message: Insight with ID=xxx not found. |
Update Match List
Updates the status, default time-to-live value, and description of the specified Match List.
READER NOTE
Match List ID is a required parameter to run this command.
Run the List Match Lists command to obtain the Match List ID. Match List IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Match List ID | Required | The ID of the Match List in which values require updating. Match List IDs can be obtained using the List Match Lists command. | ***** |
Active | Optional | Whether to set the Match List as Active. Available options are:
| True |
Default Time-to-live | Optional | The updated default time-to-live (in seconds) for new items added to the Match List. This default value is only applicable in the UI and is not applied when new items are added through the API. | 14400 |
Description | Optional | The updated description for the Match List. | Test Desc 0104 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Match List failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Match List with ID=xxx not found. |
Error Sample Data Update Match List failed. Status Code: 404. Message: Match List with ID=xxx not found. |
Update Match List Item
Updates a Match List Item using the given Match List Item ID.
READER NOTE
Match List Item ID is a required parameter to run this command.
Run the List Match List Items command to obtain the Match List Item ID. Match List Item IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Match List Item ID | Required | The ID of the Match List item for which to be updated. Match List Item IDs can be obtained using the List Match List Items command. | ***** |
Active | Required | Whether to set the Match List Item as Active. Available options are:
| True |
Description | Optional | The updated description for the Match List Item. | Test 0104 |
Expiration | Optional | The updated expiration date and time (in UTC) of the Match List Item. | 2023-01-21 00:00 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Match List Item failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Match List Item with ID=xxx not found. |
Error Sample Data Update Match List Item failed. Status Code: 404. Message: Match List Item with ID=xxx not found. |
Update Suppress List
Updates the status, default time-to-live, and description of a Suppress List.
READER NOTE
Suppress List ID is a required parameter to run this command.
Run the List Suppress Lists command to obtain the Suppress List ID. Suppress List IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Suppress List ID | Required | The ID of the Suppress List in which values require updating. Suppress List IDs can be obtained using the List Suppress Lists command. | ***** |
Active | Optional | Whether to set the Suppress List as Active. Available options are:
| True |
Default Time-to-live | Optional | The updated default time to live (in seconds) for new items added to the Suppress List. This default value is only applicable in the UI and is not applied when new items are added through the API. | 14400 |
Description | Required | The updated description for the Suppress List. | Update Suppressed List 2 Description 0104 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Suppress List failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: A Match List with id=xx could not be found. |
Error Sample Data Update Suppress List failed. Status Code: 404. Message: A Match List with id=xx could not be found. |
Update Suppress List Item
Updates Suppress List Item using the given Suppress List Item ID.
READER NOTE
Suppress List Item ID is a required parameter to run this command.
Run the List Suppress List Items command to obtain the Suppress List Item ID. Suppress List IDs can be found in the raw data at the path $.data.objects[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Suppress List Item ID | Required | The ID of the Suppress List item for which to be updated. Suppress List Item IDs can be obtained using the List Suppress List Items command. | ***** |
Active | Required | Whether to set the Suppress List Item as Active. Available options are:
| True |
Description | Optional | The updated description for the Suppress List Item. | Update description 0104 |
Expiration | Optional | The updated expiration date and time (in UTC) of the Suppress List Item. | 2023-01-20 00:00 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Suppress List Item failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: A Match List with id=xx could not be found. |
Error Sample Data Update Suppress List Item failed. Status Code: 404. Message: A Match List with id=xx could not be found. |
Test Connection
Allows you to perform a health check on an integration connection. You can schedule a periodic health check by selecting Connection Health Check when editing an integration connection.
Input
N/A
Output
Output Type | Description | Return Data Type |
Return Data | Indicates one of the possible command execution states: Successful or Failed. The Failed state can be triggered by any of the following errors:
More details about an error can be viewed in the Error tab. | String |
Error Handling
If the Return Data is failed, an Error tab will appear in the Test Result window.
The error tab contains the responses from the third-party API calls including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Test Connection failed. Failed to check the connector. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Sumo Logic Cloud SIEM Enterprise (Sumo Logic CSE) portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Test Connection failed. Failed to check the connector. Status Code: 401. Message: Unauthorized. |