SentinelOne
LAST UPDATED: AUG 15, 2025
Overview
SentinelOne delivers autonomous endpoint protection that prevents, detects, and responds to attacks across all major vectors. SentinelOne is an enterprise security platform that provides threat detection, hunting, and response features that enable organizations to discover vulnerabilities and protect IT operations.
D3 SOAR is providing REST operations to function with SentinelOne.
SentinelOne is available for use in:
Known Limitations
Different calls in the API have specific rate limits. If a limit is hit, you can see an error message: HTTP 429 Too Many Requests.
API Rate Limits:
/web/api/v2.1/users/login - 1 call a second for each different IP address that communicates with the Console
/web/api/v2.1/update/agent/download/{package_id} - 2 calls a minute for each different user token
/web/api/v2.1/update/agent/download/{site_id}/{package_id} - 2 calls a minute for each user token
/web/api/v2.1/dv/init-query - 1 call a minute for each different user token
/web/api/v2.1/dv/query-status - 1 call a second for each different user token
/web/api/v2.1/system/status/cache - 1 call a second for each IP address that communicates with the Console
/web/api/v2.1/system/status/db - 1 call a second for each IP address that communicates with the Console
/web/api/v2.1/system/status - 1 call a second for each IP address that communicates with the Console
Refer to SentinelOne API Rate Limits for detailed information.
Connection
To connect to SentinelOne from D3 SOAR, follow this part to collect the required information below:
Parameter | Description | Example |
Server URL | The URL of the SentinelOne server. | https://usea1-partners.sentinelone.net |
API Token | The API token for authentication. | JnHs*****ug5S |
API Version | The version of the APIs. | v2.1 |
Permission Requirements
Each endpoint in the SentinelOne API requires a certain permission scope. The following are required scopes for the commands in this integration:
Command | Required Permission | Role Scope | |
Activate Star Custom Rules | Default Role (see Test Connection) | ||
STAR Custom Rules | View + Manage | ||
Add Notes To Threats | Default Role (see Test Connection) | ||
Endpoint Threats | View | ||
Add Threat To Blacklist | Default Role (see Test Connection) | ||
Blocklist | View + Create | ||
Block Hash | Default Role (see Test Connection) | ||
Blocklist | View + Create | ||
Block Remote Hosts | Global admin | ||
Tenant permission is needed if set the Tenant parameter to true | |||
Broadcast Message | Default Role (see Test Connection) | ||
Endpoints | View + Send Message | ||
Collect Files | Default Role (see Test Connection) | ||
Endpoints | View + File Fetch | ||
Activity | View | ||
Connect Agent To Network | Default Role (see Test Connection) | ||
Endpoints | View + Reconnect to Network | ||
Create Exclusion | Default Role (see Test Connection) | ||
Exclusions | View + Create | ||
Create Group | Default Role (see Test Connection) | ||
Groups | View + Create | ||
Create IOC | Default Role (see Test Connection) | ||
Threat Intelligence | View + Manage | ||
Create Power Query | Default Role (see Test Connection) | ||
SDL Query API (Previously Skylight) | View | ||
Create Query | Default Role (see Test Connection) | ||
SDL Search (Previously Skylight) | View | ||
Create Star Custom Rule | Default Role (see Test Connection) | ||
Endpoints | View + Disconnect From Network | ||
Endpoint Threats | View + Mark Threat + Mark Suspicious | ||
STAR Custom Rules | View + Manage | ||
Delete Exclusions | Default Role (see Test Connection) | ||
Exclusions | View + Delete | ||
Delete Group | Default Role (see Test Connection) | ||
Groups | View + Delete | ||
Delete IOCs | Default Role (see Test Connection) | ||
Threat Intelligence | View + Manage | ||
Delete Star Custom Rules | Default Role (see Test Connection) | ||
STAR Custom Rules | View + Manage | ||
Disable Star Custom Rules | Default Role (see Test Connection) | ||
STAR Custom Rules | View + Manage | ||
Disconnect Agent From Network | Default Role (see Test Connection) | ||
Endpoints | View + Disconnect From Network | ||
Download Files | Default Role (see Test Connection) | ||
Activity | View | ||
Download Threat Files | Default Role (see Test Connection) | ||
Activity | View | ||
Fetch Event (Event Source = Threat) | Default Role (see Test Connection) | ||
Endpoint Threats | View | ||
Fetch Event (Event Source = Alert) | Default Role (see Test Connection) | ||
STAR Rule Alerts | View | ||
Fetch Files | Default Role (see Test Connection) | ||
Endpoints | View + File Fetch | ||
Fetch Threat File | Default Role (see Test Connection) | ||
Endpoint Threats | View + Fetch Threat File | ||
Get Account Policy | Default Role (see Test Connection) | ||
Endpoint Policy | View | ||
Get Activities | Default Role (see Test Connection) | ||
Activity | View | ||
Get Agent Applications | Default Role (see Test Connection) | ||
Endpoints | View + Show Applications | ||
Get Agent Info | Default Role (see Test Connection) | ||
Endpoints | View | ||
Get Agent Process | Default Role (see Test Connection) | ||
Agent Packages | View | ||
Get Alerts | Default Role (see Test Connection) | ||
STAR Rule Alerts | View | ||
Get Black List | Default Role (see Test Connection) | ||
Blocklist | View | ||
Get Events by Query ID and Type | Default Role (see Test Connection) | ||
SDL Search (Previously Skylight) | View | ||
Get Exclusions | Default Role (see Test Connection) | ||
Exclusions | View | ||
Get Global Policy | Default Role (see Test Connection) | ||
Endpoint Policy | View | ||
Get Groups | Default Role (see Test Connection) | ||
Get Hash Reputations | Default Role (see Test Connection) | ||
Blocklist | View | ||
Get Query Status | Default Role (see Test Connection) | ||
SDL Search (Previously Skylight) | View | ||
Get Script Results | Default Role (see Test Connection) | ||
RemoteOps | View | ||
Get Scripts | Default Role (see Test Connection) | ||
RemoteOps | View | ||
Get Script Task Status | Default Role (see Test Connection) | ||
RemoteOps | View | ||
Get Sites | Default Role (see Test Connection) | ||
Get Star Custom Rules | Default Role (see Test Connection) | ||
STAR Custom Rules | View | ||
Get System Info | Default Role (see Test Connection) | ||
Get System Status | Default Role (see Test Connection) | ||
Get Threat | Default Role (see Test Connection) | ||
Endpoint Threats | View | ||
Get Threat Analysis | Default Role (see Test Connection) | ||
Endpoint Threats | View | ||
Get Threat Events | Default Role (see Test Connection) | ||
Endpoint Threats | View | ||
Get Threat Notes | Default Role (see Test Connection) | ||
Endpoint Threats | View | ||
Initiate Scan | Default Role (see Test Connection) | ||
Endpoints | View + Endpoints Initiate Scan | ||
Kill Processes | Default Role (see Test Connection) | ||
Endpoint Threats | View + Update Analyst Verdict | ||
Threat Actions | Kill | ||
List Accounts | Default Role (see Test Connection) | ||
List Agents | Default Role (see Test Connection) | ||
Endpoints | View | ||
List IOCs | Default Role (see Test Connection) | ||
Threat Intelligence | View | ||
Mark As Threat | Default Role (see Test Connection) | ||
Endpoint Threats | View + Mark Threat | ||
Mitigate Threats | Default Role (see Test Connection) | ||
Endpoint Threats | View + Update Analyst Verdict + Unquarantine | ||
Threat Actions | Rollback + Remediate + Quarantine + Kill | ||
Move Agents | Default Role (see Test Connection) | ||
Groups | View + Edit | ||
Move Agents Between Sites | Default Role (see Test Connection) | ||
Endpoints | View + Move To Another Site | ||
Ping Power Query | Default Role (see Test Connection) | ||
SD Search (Previously Skylight) | View | ||
Quarantine Files | Default Role (see Test Connection) | ||
Endpoints Threats | View + Update Analyst Verdict | ||
Threat Actions | Quarantine + Kill | ||
Query | Default Role (see Test Connection) | ||
SDL Search (Previously Skylight) | View | ||
SDL Query API (Previously Skylight) | View | ||
SDL API Keys (Previously Skylight) | View + Manage | ||
Remove Items In Blacklist | Default Role (see Test Connection) | ||
Blacklist | View + Edit | ||
Resolve Threat | Default Role (see Test Connection) | ||
Endpoints | View | ||
Endpoint Threats | View | ||
Restart Endpoints | Default Role (see Test Connection) | ||
Endpoints | View + Reboot | ||
Rollback Remediation | Default Role (see Test Connection) | ||
Endpoint Threats | View + Update Analyst Verdict | ||
Threat Actions | Rollback + Remediate + Quarantine + Kill | ||
Run Script | Default Role (see Test Connection) | ||
RemoteOps | View | ||
Set Customer ID | Default Role (see Test Connection) | ||
Endpoints | View + Endpoints Set Customer Identifier | ||
Shutdown Endpoints | Default Role (see Test Connection) | ||
Endpoints | View + Shut Down | ||
Update Account Policy | Default Role (see Test Connection) | ||
Endpoints Policy | View + Edit | ||
Update Alert Analyst Verdict | Default Role (see Test Connection) | ||
STAR Rule Alerts | View + Update Analyst Verdict | ||
Update Alert Incident Status | Default Role (see Test Connection) | ||
STAR Rule Alerts | View + Update Incident Status | ||
Update Alert Verdict | Default Role (see Test Connection) | ||
STAR Rule Alerts | View + Update Analyst Verdict | ||
Update Threat Analyst Verdict | Default Role (see Test Connection) | ||
Endpoint Threats | View + Update Analyst Verdict | ||
Update Exclusion | Default Role (see Test Connection) | ||
Exclusions | View + Edit | ||
Update Global Policy | Global Admin | ||
Update Incident Status | Default Role (see Test Connection) | ||
Endpoint Threats | View + Update Incident Status | ||
Update Star Custom Rule | Default Role (see Test Connection) | ||
STAR Custom Rules | View + Manage | ||
Update Threat Incident | Default Role (see Test Connection) | ||
Endpoint Threats | View + Update Analyst Verdict + Update Incident Status | ||
Update Threat Notes | Default Role (see Test Connection) | ||
Endpoint Threats | View | ||
Test Connection | Account | View | |
Groups | View | ||
Roles | View | ||
Site | View | ||
As SentinelOne is using role-based access control (RBAC), the API access token is generated based on a specific user account and the application. Therefore, the command permissions are inherited from the user account’s role. Users need to configure their user profile from the SentinelOne console for each command in this integration.
Custom role has Account, Groups, Roles, Site permission with View scope as default. These permissions cannot be removed.
Configuring SentinelOne to Work with D3 SOAR
Log in to the SentinelOne portal.
Input the 2FA verification code if Two-Factor Authentication is enabled.
Click the username located on the top right corner, then click My User.
Under Options, click Generate to create an API Token if it has not been created yet.
READER NOTE
Users may experience issues when generating API Token. Refer to Why is the Generate API token option not enabled? for potential solutions.
Click Copy to copy the API token for later use to build the D3 SOAR connection.
READER NOTE
The token is visible only once. Store it in a secure location for future reference. To regain access after loss, a new token must be generated.
How to Create a New Role
On the left sidebar menu, click Settings.
On the top menu, click Users, then select Roles. Under Actions, click New Role.
Enter a Role Name, and a Description (optional).
Use the left permissions category menu to find and select the permissions for the role. See Permissions Requirements for a list of required permissions.
Click Save after selecting the desired permissions to confirm the configuration.
Select Users located on the left. Click Actions > New User. The Select Scope of Access window will appear. Under Access, select the desired Account or Site, and select the created role. Click Create User.
Use the limited-access user to generate an API key and connect to D3 SOAR.
READER NOTE
The created user is required to set up 2FA. Without 2FA, the user cannot log in or generate API tokens. To configure 2FA, select the user and navigate to Actions > 2FA Settings.
Configuring D3 SOAR to Work with SentinelOne
Log in to D3 SOAR.
Find the SentinelOne integration.
-20241101-020341.png?inst-v=9d16beaf-952a-4ae4-8fe8-e35f7a3745da)
Navigate to Configuration on the top header menu.
Click on the Integration icon on the left sidebar.
Type SentinelOne in the search box to find the integration, then click it to select it.
Click + Connection, on the right side of the Connections section. A new connection window will appear.
Configure the following fields to create a connection to SentinelOne.
-20241031-202832.png?inst-v=9d16beaf-952a-4ae4-8fe8-e35f7a3745da)
Connection Name: The desired name for the connection.
Site: The site on which to use the integration connection. Use the drop-down menu to select the site. The Share to Internal Sites option enables all internal sites to use the connection. Selecting a specific site will only enable that site to use the connection.
Recipient site for events from connections Shared to Internal Sites: This field is displayed when Share to Internal Sites is selected for the Site field, allowing selection of the internal site for deploying the integration connection.
Agent Name (Optional): The proxy agent required to build the connection. Use the dropdown menu to select the proxy agent from a list of previously configured proxy agents.
Description (Optional): The description for the connection.
Tenant (Optional): When configuring the connection from a master tenant site, users can choose the specific tenant sites with which to share the connection. Once this setting is enabled, users can filter and select the desired tenant sites from the dropdowns to share the connection.
Configure User Permissions: Defines which users have access to the connection.
Active: The checkbox that enables the connection to be used when selected.
System: This section contains the parameters defined specifically for the integration. These parameters must be configured to create the integration connection.
-20241031-202850.png?inst-v=9d16beaf-952a-4ae4-8fe8-e35f7a3745da)
1. Input the domain level Server URL.
2. Input the API Token.
3. Input the API Version. The default value is v1.Enable Password Vault: An optional feature that allows users to take the stored credentials from their own password vault. Refer to the password vault connection guide if needed.
Connection Health Check: Periodically checks the connection status by scheduling the Test Connection command at the specified interval (in minutes). Available only for active connections, this feature also allows configuring email notifications for failed attempts.
Test the connection.
-20241031-202955.png?inst-v=9d16beaf-952a-4ae4-8fe8-e35f7a3745da)
Click on the Test Connection button to verify credentials and connectivity. A success alert displays Passed with a green checkmark. If the connection fails, review the parameters and retry.
Click OK to close the alert window.
Click +Add to create and add the configured connection.
Commands
SentinelOne includes the following executable commands for users to set up schedules or create playbook workflows. With the Test Command function, users can execute these commands independently for playbook troubleshooting.
Integration API Note
For more information about the SentinelOne API, refer to the SentinelOne API reference.
READER NOTE
Certain permissions are required for each command. Refer to the Permission Requirements and Configuring SentinelOne to Work with D3 SOAR for details.
Note for Time-related parameters
The input format of time-related parameters may vary based on user account settings, which may cause the sample data in commands to differ from what is displayed. To adjust the time format, follow these steps:
Navigate to Configuration > Application Settings. Select Date/Time Format.
-20241031-203021.png?inst-v=9d16beaf-952a-4ae4-8fe8-e35f7a3745da)
Choose your desired date and time format.
-20241031-203034.png?inst-v=9d16beaf-952a-4ae4-8fe8-e35f7a3745da)
The selected time format will now be visible when configuring Date/Time command input parameters.
Activate Star Custom Rules
Activates star custom rules based on a filter.
READER NOTE
Account IDs, Site IDs, Group IDs and Rule IDs are optional parameters to run this command.
Run the List Accounts command to obtain Account IDs. Account IDs can be found in the raw data at the path $.data[*].id.
Run the Get Sites command to obtain Site IDs. Site IDs can be found in the raw data at the path $.data.sites.id.
Run the Get Groups command to obtain Group IDs. Group IDs can be found in the raw data at the path $.data.id.
Run the Get Star Custom Rules command to obtain Rule IDs. Rule IDs can be found in the raw data at the path $.data[*].id.
Although all parameters are optional, you have to define at least one parameter to filter.
Input
Input Parameter | Required/Optional | Description | Example |
Account IDs | Optional | The account IDs to filter. Account IDs can be obtained using the List accounts command. | ["131********791"] |
Site IDs | Optional | The site IDs to filter. Site IDs can be obtained using the Get sites command. | ["174********138"] |
Group IDs | Optional | The group IDs to filter. Group IDs can be obtained using the Get groups command. | ["151********497"] |
Rule IDs | Optional | The star custom rule IDs to filter. Rule IDs can be obtained using the Get Star Custom Rules command. | ["174********052"] |
Creator | Optional | The free-text filter by rule creator. | ["w**"] |
Name | Optional | The free-text filter by rule name. | ["test"] |
Status | Optional | The status of rules to filter. The available inputs are Activating, Active, Deleted, Deleting, Disabled, Disabling and Draft. | ["Active"] |
Query | Optional | The free-text filter by S1 query. | ["test"] |
Query Type | Optional | Retrieves the rules with the filtered type. The available inputs are events and processes. | ["events"] |
Expired | Optional | Whether the rule is expired or not. | Not Expired |
s1ql | Optional | The free-text filter by S1 query. | ["AgentName IS NOT EMPTY"] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Activate Star Custom Rules failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Could not find rule with id: {'scope_id__in': [xxx]}. |
Error Sample Data Activate Star Custom Rules failed. Status Code: 404. Message: Could not find rule with id: {'scope_id__in': [xxx]}. |
Add Notes To Threats
Adds a threat note to multiple threats.
Input
Input Parameter | Required/Optional | Description | Example |
Filter | Required | The filtering options used to manage the list of threats to add notes to. It is possible to use any combination of filters to refine the list. Please refer to https://usea1-partners.sentinelone.net/api-doc/api-details?category=threat-notes=add-note-to-multiple for more information on filters. | { |
Note Text | Required | The text of the threat note to input. | Test Notes for suspicious threats 0421 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Add Notes To Threats failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Invalid user input received. See error details for further information. |
Error Sample Data Add Notes To Threats failed. Status Code: 400. Message: Invalid user input received. See error details for further information. |
Add Threat To Blacklist
Blacklists threats based on the specified target scope (Global, Account, Site or Group).
READER NOTE
Collection IDs and Site ID are required parameters to run this command.
Run the Get threat command to obtain Collection IDs. Collection IDs can be found in the raw data at the path $.data.threatInfo.collectionId.
Run the Get Sites command to obtain Site ID. Site IDs can be found in the raw data at the path $.data.agentDetectionInfo.siteId.
Please note that the collection ID and site ID must come from the same threat, meaning they should be under the same threat object. Obtain the pair of values by running the Get Threat command.
Input
Input Parameter | Required/Optional | Description | Example |
Collection IDs | Required | The list of threat collection ID(s). Collection IDs can be obtained using the Get Threat command. | [ "947********369", "752********846" ] |
Site ID | Required | The site ID related to the threat. Site ID can be obtained using the Get Sites command. | 947********671 |
Description | Optional | The description for the process. | Add threat to blacklist |
Target Scope | Required | The target scope of the agent. Available options include group, site, and account. Please note this field is case-sensitive, only lowercase letters are accepted. | group |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Add Threat To Blacklist failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Add threat:xxx failed. Messages: {\"data\":{\"affected\":0}. |
Error Sample Data Add Threat To Blacklist failed. Status Code: 400. Message: Add threat:xxx failed. Messages: {\"data\":{\"affected\":0}. |
Block Hash
Blocks threats by threat hashes.
READER NOTE
Site ID is a required parameter to run this command.
Run the Get Sites command to obtain Site ID. Site IDs can be found in the raw data at the path $.data.sites.id.
Please note that only SHA-1 hashes are accepted for this command. Existing hashes in the system cannot be blocked again. Otherwise, the error message “Hash XXX already exists” will return.
To get SHA-1 hashes from D3 SOAR, it is recommended to use the Get Hash Value utility command to obtain the Input String. Please follow the steps below:
Select your desired site
Input your desired search string
Choose HashSHA1 for Hash Keys
Click Test Command. The SHA-1 hash will return under Return Data. Copy and save this value to input for the Threat Hashes parameter.
-20241031-203534.png?inst-v=9d16beaf-952a-4ae4-8fe8-e35f7a3745da)
Input
Input Parameter | Required/Optional | Description | Example |
Threat Hashes | Required | The list of threat hashes to block. | [ "d25********225", "a6d********d00" ] |
OS Type | Required | The type of operating system of the Threat Hashes. | Windows |
Site ID | Required | The site ID to filter. Site ID can be obtained using the Get Sites command. | [ "947********671" ] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Block Hash failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: "Hash 'a6d********d00' already exists" |
Error Sample Data Block Hash failed. Status Code: 400. Message: "Hash 'a6d********d00' already exists" |
Block Remote Hosts
Creates a firewall control rule to block specified remote host(s).
READER NOTE
Account ID, Site ID, and Group ID are optional parameters to run this command.
Run the List Accounts command to obtain Account ID. Account ID can be found in the raw data at the path $.data[*].id.
Run the Get Sites command to obtain Site ID. Site ID can be found in the raw data at the path $.data.sites.id.
Run the Get Groups command to obtain Group IDs. Group IDs can be found in the raw data at the path $.data.id.
If the Tenant parameter is none or not specified, at least one of the following scopes must be specified: Account ID, Site ID, or Group ID.
Input
Input Parameter | Required/Optional | Description | Example |
Rule Name | Required | The name of the Firewall Control Rule. | ruleAPI0405a26 |
Status | Optional | The rule is specified when Enabled. If not specified, the default value is Enabled. | |
Account ID | Optional | The Firewall Control rule is created for the specified account ID. Account ID can be obtained using the List Accounts command. | |
Site ID | Optional | The Firewall Control rule is created for the specified site ID. Site ID can be obtained using the Get Sites command. | 947********671 |
Group ID | Optional | The Firewall Control rule is created for the specified group ID. Group ID can be obtained using the Get Groups command. | 151********497 |
Tenant | Optional | The Firewall Control rule is created for the entire tenant if set to True. It is necessary to have tenant permission to be able to set this parameter to True. Please note, if Tenant is set to False or not specified, at least one scope must be specified: Account ID, Site ID or Group ID. | False |
OS Types | Optional | The OS Types to which the rule applies. The available values are "windows", "macos" and "linux". If not specified, the default value is windows. | [ "windows", "macos", "linux" ] |
Remote Host Type | Optional | The type of remote host(s). If not specified, the default type is Addresses. | CIDR |
Remote Host Values | Required | The remote host value(s).The value(s) must match Remote Host Type. | [ "203.193.22.248/31" ] |
Description | Optional | The description for the Firewall Control rule. | This is a test firewall control rule. |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Block Remote Hosts failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: BAD REQUEST |
Error Sample Data Block Remote Hosts failed. Status Code: 400. Message: BAD REQUEST |
Broadcast Message
Sends a message through the Agents that users can see. This command is supported on Windows and macOS endpoints (not supported on Linux). The message is sent to all endpoints that match the filter and the message must be 140 characters or less.
READER NOTE
The parameter Group IDs is optional to run this command.
Run the Get Groups command to obtain Group IDs. Group IDs can be found in the raw data at the path $.data.id.
Input
Input Parameter | Required/Optional | Description | Example |
Host Names Or Internal IPs | Optional | The name(s) or internal IP address(es) of the computer(s) to which the message is sent. Please note that you must enter either this parameter or Group IDs, or both. | [ "192.168.**.***", "lab*-p**" ] |
Group IDs | Optional | The ID of the group to which the message is sent. Group IDs can be obtained using the Get Groups command. Please note that you must enter either this parameter or Host Names Or Internal IPs, or both. | [ "138********378" ] |
Message | Required | The message to broadcast. | Computer Maintenance will start in one hour. FYI. |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Broadcast Message failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Server could not process the request. |
Error Sample Data Broadcast Message failed. Status Code: 400. Message: Server could not process the request. |
Collect Files
Collects the files from endpoints (up to 10 MB for each command) to analyze the root of threats and uploads them to the Management.
READER NOTE
Agent ID is a required parameter to run this command.
Run the List Agents command to obtain Agent ID. Agent IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Agent ID | Required | The agent ID of the endpoint for fetching files. Agent ID can be obtained using the List agent command. | 139********432 |
File Paths | Required | The list of files to collect (absolute paths, up to 10 files). | [ "C:\\AtomicRedTeam\\atomics\\T1548.***\\bin\\ua***.zip", "C:\\Windows\\System32\\WindowsPowerShell\\V1.0\\powershell.exe" ] |
Password | Required | The new password to generate, which will be used to open the archive of downloaded files. It must be 10 or more characters long and contain a mix of upper and lower case letters, numbers, and symbols. | MySecret******! |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Collect Files failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The agent with ID *** is not found. |
Error Sample Data Collect Files failed. Status Code: 404. Message: The agent with ID *** is not found. |
Connect Agent To Network
Reconnects (unquarantine) quarantined agent(s) to the network matching the defined filter. If neither input parameters are defined, all applicable agents will be reconnected.
READER NOTE
The parameter Agent IDs is optional to run this command.
Run the List Agents command to obtain Agent IDs. Agent IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Agent IDs | Optional | The IDs of the agents to reconnect to the network. Agent IDs can be obtained using the List Agents command. | [ "139********392" ] |
Filter | Optional | The applied filter ensures that only matched agents will be affected by the requested action. Leave this field empty to apply the action to all applicable agents. Please refer to https://usea1-partners.sentinelone.net/api-doc/api-details?category=agent-actions=connect-to-network under body schema for more information about the filter syntax. | { "computerName":"DESKTOP-6KJ****" } |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Connect Agent To Network failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: User has insufficient permissions to perform the requested action. |
Error Sample Data Connect Agent To Network failed. Status Code: 403. Message: User has insufficient permissions to perform the requested action. |
Create Exclusion
Creates exclusion(s) to instruct your agents to suppress alerts and mitigation for items that you consider to be benign or necessary for interoperability.
READER NOTE
Account IDs, Site IDs and Group IDs are optional parameters to run this command.
Run the List Accounts command to obtain Account IDs. Account IDs can be found in the raw data at the path $.data[*].id.
Run the Get Sites command to obtain Site IDs. Site IDs can be found in the raw data at the path $.data.sites.id.
Run the Get Groups command to obtain Group IDs. Group IDs can be found in the raw data at the path $.data.id.
At least one of the Account IDs, Site IDs or Group IDs is required.
Input
Input Parameter | Required/Optional | Description | Example |
Type | Required | The type of exclusion item. | Path |
Operation System | Required | The operation system. | Windows Legacy |
Value | Required | The valid values depend on the item type chosen. | C:\"Windows\"saas\" |
Description | Optional | The description to be added to the created exclusion. | Test description |
Mode | Optional | The exclusion mode which is restricted to Path only for the selected Type parameter. | Suppress Alerts |
Path Exclusion Type | Optional | The excluded path for a path exclusion list. The available options are file, folder, subfolders. | subfolders |
Account IDs | Optional | The account IDs for exclusion. Account IDs can be obtained using the List Accounts command. Please note that at least one of the account IDs, group IDs, or site IDs is required. | ["131********791"] |
Site IDs | Optional | The site IDs for exclusion. Site IDs can be obtained using the Get Sites command. Please note that at least one of account IDs, group IDs or site IDs is required. | ["174********138"] |
Group IDs | Optional | The group IDs for exclusion. Group IDs can be obtained using the Get Groups command. Please note that at least one of account IDs, group IDs or site IDs is required. | ["151********497"] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Create Exclusion failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: User does not have required permissions. |
Error Sample Data Create Exclusion failed. Status Code: 403. Message: User does not have required permissions. |
Create Group
Creates a new group. You must create the Group in a Site (run the Get Sites command to obtain Site IDs) you have permission to.
READER NOTE
Site ID is a required parameter to run this command.
Run the Get Sites command to obtain Site IDs. Site IDs can be found in the raw data at the path $.data.sites.id.
Input
Input Parameter | Required/Optional | Description | Example |
Name | Required | The name of the new group. | D3*****5 |
Site ID | Required | The site ID of the site to which the group will be added. Site ID can be obtained using the Get Sites command. | 947********671 |
Inherits | Required | The indication of whether the group will inherit the site policy or not. | True |
Policy | Optional | The group policy to inherit if the Inherits parameter is set to False. Note: This parameter is required only if the Inherits parameter is set to False. If the Inherits parameter is set to True, any input value will be ignored. Please refer to https://usea1-partners.sentinelone.net/api-doc/api-details?category=groups=create-group to see available fields. | { "mitigationMode": "detect", "autoImmuneOn": true, "agentUiOn": true } |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Create Group failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Not a valid Identifier. |
Error Sample Data Create Group failed. Status Code: 400. Message: Not a valid Identifier. |
Create IOC
Creates an IOC to the Threat Intelligence database.
READER NOTE
The parameter Account IDs is optional to run this command.
Run the List Accounts command to obtain Account IDs. Account IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Account IDs | Optional | The List of account IDs. Account IDs can be obtained using the List Accounts command. | [ "131********791" ] |
Source | Required | The source of the identified Threat Intelligence indicator. For example, "AlienVault". | AlienVault |
Type | Required | The type of the Threat Intelligence indicator. The available types include: IPv4, IPv6, MD5, SHA1, SHA256, URL and DNS. | IPv4 |
IOC Value | Required | The value of the Threat Intelligence indicator. For example, "175.45.***.*". | 175.45.***.* |
Name | Optional | The name of the Threat Intelligence indicator. | test***1 |
Description | Optional | The description of the Threat Intelligence indicator. | test description |
Valid Until | Optional | The expiration date for the Threat Intelligence indicator. If this parameter is left blank, by default it will be the upload date plus a default offset value:
The maximum offset values allowed are:
If the expiration date is later than the upload date plus the maximum offset value allowed, it will be adjusted to the upload date plus the maximum offset value allowed. | 2023-08-20 00:00 |
Mitre Tactics | Optional | The MITRE Tactic(s) associated with the IOC. | [ "TA0001" ] |
External ID | Optional | The unique identifier of the indicator as provided by the Threat Intelligence source. | 123456 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Create IOC failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Invalid user input received. See error details for further information. |
Error Sample Data Create IOC failed. Status Code: 400. Message: Invalid user input received. See error details for further information. |
Create Power Query
Starts a Deep Visibility Power Query, get back status and potential results. If the query status is not FINISHED, please use Ping Power Query afterwards to get query result.
READER NOTE
Account IDs and Site IDs are optional parameters to run this command.
Run the List Accounts command to obtain Account IDs. Account IDs can be found in the raw data at the path $.data[*].id.
Run the Get Sites command to obtain Site IDs. Site IDs can be found in the raw data at the path $.data.sites.id.
Input
Input Parameter | Required/Optional | Description | Example |
Start Time | Required | The start time (in UTC Time) of the time range for querying events that were created after the specified start time. | 2023-05-20 00:00 |
End Time | Required | The end time (in UTC Time) of the time range for querying events that were created before the specified end time. | 2023-06-02 00:00 |
Limit | Optional | The maximum number of items to return. A valid value is an integer between 1 and 100,000. The API default maximum limit is 20,000. Consult SentinelOne contact could increase the limit to maximum 100,000. | 10 |
Query | Required | The queries to filter events. Please refer to Query Syntax in the Knowledge Base (support.sentinelone.com) or the Console Help. Please refer to https://assets.sentinelone.com/c/sentinel-one-dv-chea-2?x=u6040P for the field name syntax, or you can refer to PowerQuery Brings New Data Analytics Capabilities to Singularity XDR for power query samples. | event.time = * | columns eventTime = event.time, agentUuid = agent.uuid, siteId = site.id |
Account IDs | Optional | The account IDs to create power query. Account ID can be obtained using the List Accounts command. | [ "131********791" ] |
Site IDs | Optional | The valid site IDs to create power query. You can obtain the Site ID and check the site state using the Get Sites command. | [ "160********576" ] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Create Power Query failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Deep Visibility currently retains data for 14 days, to increase your data retention, please contact S1. |
Error Sample Data Create Power Query failed. Status Code: 400. Message: Deep Visibility currently retains data for 14 days, to increase your data retention, please contact S1. |
Create Query
Starts a Deep Visibility Query and returns a Query ID. For more about the complete query syntax, see Query Syntax in the Knowledge Base (support.sentinelone.com) or the Console Help. Note: The API rate limit is 1 call per minute for each unique user token.
Input
Input Parameter | Required/Optional | Description | Example |
Start Time | Required | The start time (in UTC Time) of the time range for initiating the query. | 2022-09-18 00:00 |
End Time | Required | The end time (in UTC Time) of the time range for initiating the query. | 2022-09-19 00:00 |
Limit | Optional | The maximum number of returned items. A valid value is an integer between 1 and 100000. Up to 100000 results will be returned if this field is left empty. | 10 |
Query | Required | The queries to filter events. Please refer to Query Syntax in the Knowledge Base (https://support.sentinelone.com) or the Console Help for complete query syntax. Please also refer to the https://assets.sentinelone.com/c/sentinel-one-dv-chea-2?x=u6040P for the syntax of the field names. | processImagePath CONTAINS "svchost.exe" |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Create Query failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Bad Request - could not parse query. |
Error Sample Data Create Query failed. Status Code: 400. Message: Bad Request - could not parse query. |
Create Star Custom Rule
Creates a Custom Detection Rule by a specified scope.
READER NOTE
Account IDs, Site IDs and Group IDs are optional parameters to run this command.
Run the List Accounts command to obtain Account IDs. Account IDs can be found in the raw data at the path $.data[*].id.
Run the Get Sites command to obtain Site IDs. Site IDs can be found in the raw data at the path $.data.sites.id.
Run the Get Groups command to obtain Group IDs. Group IDs can be found in the raw data at the path $.data.id.
Input
Input Parameter | Required/Optional | Description | Example |
Expiration Mode | Required | The expiration mode of the rule. The available options are Permanent or Temporary. When choosing Temporary, an expiration date is required to enter. | Temporary |
Name | Required | The name of the star custom rule. | D3**Rule |
Query Type | Required | Returns rules with the filtered type. The available options are Events and Processes. | Events |
S1ql | Required | The query of the rule. For complete query syntax, see Query Syntax in the Knowledge Base (support.sentinelone.com) or the Console Help. | AgentName IS NOT EMPTY |
Severity | Required | The severity level of the rule. | Low |
Status | Required | The status of rules to filter. | Active |
Description | Optional | The description of the rule. | Test description |
Expiration Date | Optional | The expiration date of the rule. The expiration date must be within the next six months. Only input the expiration date when choosing temporary expiration mode. | 2024-11-08 00:00 |
Network Quarantine | Optional | The indication of whether to enable network quarantine. If enabled, the system automatically quarantines the alerted endpoints. | Disable |
Treat As Threat | Optional | Defines treat as threat auto response. If enabled, the Agent generates a threat from the alert and applies a selected policy. | Suspicious |
Account IDs | Optional | The account IDs to filter. Account IDs can be obtained using the List Accounts command. | ["131********791"] |
Site IDs | Optional | The site IDs to filter. Site IDs can be obtained using the Get Sites command. | ["174********138"] |
Group IDs | Optional | The group IDs to filter. Group IDs can be obtained using the Get Groups command. | ["151********497"] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Create Star Custom Rule failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: This scope cannot have custom rules with Process State queries. |
Error Sample Data Create Star Custom Rule failed. Status Code: 403. Message: This scope cannot have custom rules with Process State queries. |
Delete Exclusions
Deletes a list of all the Exclusions that match the filter.
READER NOTE
Account IDs, Site IDs, Group IDs and Exclusion IDs are optional parameters to run this command.
Run the List Accounts command to obtain Account IDs. Account IDs can be found in the raw data at the path $.data[*].id.
Run the Get Sites command to obtain Site IDs. Site IDs can be found in the raw data at the path $.data.sites.id.
Run the Get Groups command to obtain Group IDs. Group IDs can be found in the raw data at the path $.data.id.
Run the Get Exclusions command to obtain Exclusion IDs. Exclusion IDs can be found in the raw data at the path $.data.id.
If no parameter is specified, all exclusions will be deleted.
Input
Input Parameter | Required/Optional | Description | Example |
Type | Optional | The exclusion item type to filter. | Path |
Operation System | Optional | The operation system to filter. | Linux |
Account IDs | Optional | The account IDs to filter. Account IDs can be obtained using the List Accounts command. | ["131********791"] |
Site IDs | Optional | The site IDs to filter. Site IDs can be obtained using the Get Sites command. | ["174********138"] |
Group IDs | Optional | The group IDs to filter. Group IDs can be obtained using the Get Groups command. | ["151********497"] |
Exclusion IDs | Optional | The exclusion IDs to filter. Exclusion IDs can be obtained using the Get Exclusions command. | ["174********364"] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Delete Exclusions failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Not a valid Identifier. |
Error Sample Data Delete Exclusions failed. Status Code: 400. Message: Not a valid Identifier. |
Delete Group
Deletes a Group given by the required Group ID. If there are Agents in the Group, and the Group is dynamic, the next dynamic Groups will collect matching Agents, and unmatched Agents will go to the Default Group. If this is a static or Pinned Group with Agents, all the Agents will go to the Default Group.
READER NOTE
There are three types of groups: Dynamic, Pinned and Static. To know your desired group type, run the Get Groups command.
Group IDs can be found in the raw data at the path $.data[*].id; Group Type can be found in the raw data at the path$.data[*].type.
If there are Agents in the Group:
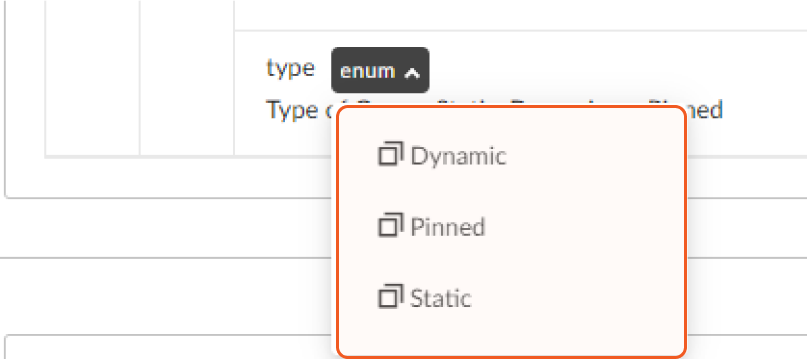
Dynamic Group (Create an endpoint filter for this Group. All endpoints that match the filter automatically move to this Group, except for endpoints in Pinned Groups): the next dynamic Group will collect matching Agents, and unmatched Agents will go to the Default Group.
Static Group/Manual Group in UI (Select the endpoints that go in this Group. Endpoints move automatically from this Group to a Dynamic Group if they match a Dynamic Group filter): all the Agents will go to the Default Group.
Pinned Group (Select the endpoints that go in this Group. Endpoints are pinned to this Group and do not automatically move to other Groups): all the Agents will go to the Default Group.
Input
Input Parameter | Required/Optional | Description | Example |
Group IDs | Required | The Group IDs to delete. Group IDs can be obtained using the Get Groups command. | [ "951********939", "952********906" ] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Delete Group failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again. |
Error Sample Data Delete Group failed. Status Code: 404. Message: The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again. |
Delete IOCs
Deletes IOC(s) from the Threat Intelligence database that matches a filter using the account ID and one other field.
READER NOTE
The parameter Account IDs is required to run this command.
Run the List Accounts command to obtain Account IDs. Account IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Account IDs | Required | The list of Account IDs to delete. Account IDs can be obtained using the List Accounts command. | [ "131********791" ] |
IOC Values | Optional | The value(s) of the Threat Intelligence indicator(s) to be deleted. Example: "175.45.***.*". Please note, you must input IOC Values or UUID, or both. | [ "175.45.***.*" ] |
UUIDs | Optional | The unique ID(s) of the Threat Intelligence indicator(s) to delete. Please note, it is necessary to input IOC Values or UUID, or both. | IPv4 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Delete IOCs failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 4004. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again. |
Error Sample Data Delete IOCs failed. Status Code: 404. Message: The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again. |
Delete Star Custom Rules
Deletes Custom Detection Rules that match a filter.
READER NOTE
Account IDs, Site IDs, Group IDs and Rule IDs are optional parameters to run this command.
Run the List Accounts command to obtain Account IDs. Account IDs can be found in the raw data at the path $.data[*].id.
Run the Get Sites command to obtain Site IDs. Site IDs can be found in the raw data at the path $.data.sites.id.
Run the Get Groups command to obtain Group IDs. Group IDs can be found in the raw data at the path $.data.id.
Run the Get Star Custom Rules command to obtain Rule IDs. Rule IDs can be found in the raw data at the path $.data[*].id.
At least one parameter must be defined to filter.
Once the star custom rule is deleted, it will be removed from the rule list. The same rule cannot be deleted twice.
Input
Input Parameter | Required/Optional | Description | Example |
Account IDs | Optional | The account IDs to filter. Account IDs can be obtained using the List Accounts command. | ["131********791"] |
Site IDs | Optional | The site IDs to filter. Site IDs can be obtained using the Get Sites command. | ["174********138"] |
Group IDs | Optional | The group IDs to filter. Group IDs can be obtained using the Get Groups command. | ["151********497"] |
Rule IDs | Optional | The star custom rule IDs to filter. Rule IDs can be obtained using the Get Star Custom Rules command. | ["174********364"] |
Creator | Optional | The free-text filter by rule creator. | ["w**"] |
Name | Optional | The free-text filter by rule name. | ["test"] |
Status | Optional | The status of rules to filter. Available options include: Activating, Active, Deleted, Deleting, Disabled, Disabling and Draft. | ["Active"] |
Query | Optional | The free-text filter by S1 query. | ["test"] |
Query Type | Optional | The return rules with the filtered type. Available options include: Events and Processes. | ["events"] |
Expired | Optional | Whether the rule is expired or not. | Not Expired |
s1ql | Optional | The free-text filter by S1 query. | ["AgentName IS NOT EMPTY"] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Delete Star Custom Rules failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Could not find rule with id: {'id__in': [xxx], 'scope_id__in': [xxx]}. |
Error Sample Data Delete Star Custom Rules failed. Status Code: 404. Message: Could not find rule with id: {'id__in': [xxx], 'scope_id__in': [xxx]}. |
Disable Star Custom Rules
Disable Custom Detection Rules based on a filter.
READER NOTE
Account IDs, Site IDs, Group IDs and Rule IDs are optional parameters to run this command.
Run the List Accounts command to obtain Account IDs. Account IDs can be found in the returned raw data at the path $.data[*].id.
Run the Get Sites command to obtain Site IDs. Site IDs can be found in the returned raw data at the path $.data.sites.id.
Run the Get Groups command to obtain Group IDs. Group IDs can be found in the returned raw data at the path $.data.id.
Run the Get Star Custom Rules to obtain Rule IDs. Rule IDs can be found in the returned raw data at the path $.data[*].id.
At least one parameter should be defined to filter.
Input
Input Parameter | Required/Optional | Description | Example |
Account IDs | Optional | The account IDs to filter. Account IDs can be obtained using the List Accounts command. | ["131********791"] |
Site IDs | Optional | The site IDs to filter. Site IDs can be obtained using the Get Sites command. | ["174********138"] |
Group IDs | Optional | The group IDs to filter. Group IDs can be obtained using the Get Groups command. | ["151********497"] |
Rule IDs | Optional | The star custom rule IDs to filter. Rule IDs can be obtained using the Get Star Custom Rule command. | ["174********364"] |
Creator | Optional | The free-text filter by rule creator. | ["w**"] |
Name | Optional | The free-text filter by rule name. | ["test"] |
Status | Optional | The status of rules to filter. Available options includes Activating, Active, Deleted, Deleting, Disabled, Disabling and Draft. | ["Active"] |
Query | Optional | The free-text filter by S1 query. | ["test"] |
Query Type | Optional | The return rules with the filtered type. The available options are events and processes. | ["events"] |
Expired | Optional | Whether the rule is expired or not. | Not Expired |
s1ql | Optional | The free-text filter by S1 query. | ["AgentName IS NOT EMPTY"] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Disable Star Custom Rules failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Could not find rule with id: {'id__in': xxx, 'scope_id__in': xxx}. |
Error Sample Data Disable Star Custom Rules failed. Status Code: 404. Message: Could not find rule with id: {'id__in': xxx, 'scope_id__in': xxx}. |
Disconnect Agent From Network
Isolates (quarantines) endpoints from the network.
READER NOTE
The parameter Agent IDs is required to run this command.
Run the List Agents command to obtain Agent IDs. Agent IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Agent IDs | Optional | The IDs of the agents to disconnect from the network. Agent IDs can be obtained using the List Agents command. | [ "139********392" ] |
Filter | Optional | The applied filter. When used, only matched Agents will be affected by the requested action. Note: One of the following filter arguments must be supplied: ids, groupIds, filterId. Please refer to https://usea1-partners.sentinelone.net/api-doc/api-details?category=agent-actions=disconnect-from-network for more information. | { "computerName": "DESKTOP-6KJ****" } |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Disconnect Agent From Network failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Authentication Failed. |
Error Sample Data Disconnect Agent From Network failed. Status Code: 401. Message: Authentication Failed. |
Download Files
Downloads files from the management console.
READER NOTE
Agent ID and Command Batch UUIDs are required parameters to run this command.
Run the List Agents command to obtain Agent ID. Agent IDs can be found in the raw data at the path $.data[*].id.
Run the Collect Files command, the returned Command Batch UUIDs of the file can be used in the parameter. Command Batch UUIDs can be found in the raw data at the path $.data[*].data.commandBatchUuid.
Activity Created Time is an optional parameter to run this command.
Run the Collect Files command, the returned Create Time of the file can be used in this parameter. Create Time can be found in the raw data at the path $.data[*].createdAt.
Input
Input Parameter | Required/Optional | Description | Example |
Agent ID | Required | The agent ID of the endpoint where the downloading files originate from. Agent ID can be obtained using the List Agents command. | 138********274 |
Activity Created Time | Optional | The time to get activities created after this timestamp (UTC). Activity Created Time can use the returned Created Time of the Collect Files command. | 2023-02-03 00:00 |
Command Batch UUIDs | Required | The Command Batch UUID(s) to filter files to download. Command Batch UUIDs can use the returned Command Batch UUID of the Collect Files command. | [ "ce1********276" ] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Download Files failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Authentication Failed. |
Error Sample Data Download Files failed. Status Code: 401. Message: Authentication Failed. |
Download Threat Files
Downloads threat files from the management console.
READER NOTE
Agent ID, Threat ID and Command Batch UUIDs are required parameters to run this command.
Run the List Agents command to obtain Agent ID. Agent IDs can be found in the raw data at the path $.data[*].id.
Run the Get Threat command to obtain Threat ID. Threat IDs can be found in the raw data at the path $.data[*].id.
Run the Collect Files command, the returned Command Batch UUIDs of the file can be used in the parameter. Command Batch UUIDs can be found in the raw data at the path $.data[*].data.commandBatchUuid.
Input
Input Parameter | Required/Optional | Description | Example |
Agent ID | Required | The agent ID of the endpoint where the downloading threat files originate from. Agent ID can be obtained using the List Agents command. | 139********432 |
Threat ID | Required | The ID(s) of the threat(s) to download threat files.Threat ID can be obtained using the Get Threat command. | 174********856 |
Command Batch UUIDs | Required | The Command Batch UUID(s) to filter files to download. Command Batch UUID of the Collect Files command. It is possible to use Command Batch UUID from Collect Files. | [ "e1f********e87" ] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Download Threat Files failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Authentication Failed. |
Error Sample Data Download Threat Files failed. Status Code: 401. Message: Authentication Failed. |
Fetch Event
Returns Events(Threats or Alerts) from the platform based on specified criteria.
Input
Input Parameter | Required/Optional | Description | Example |
Start Time | Required | The Start Time (in UTC Time) of the time range for fetching threats or alerts. | 2021-08-01 00:00 |
End Time | Required | The End Time (in UTC Time) of the time range for fetching threats or alerts. | 2022-09-14 00:00 |
Number of Event(s) Fetched | Optional | The number of the most recent Events(Threats or Alerts) to fetch. The valid value is from 1 to 1000. Up to 1000 events will be returned if not specified. | 100 |
Search Condition | Optional | The query string to filter results. Please follow the following format: Parameter1=Value1a,Value1b=Value2=Value3… Please refer to https://usea1-partners.sentinelone.net/api-doc/api-details?category=threats=get-threats for the available parameters that can be used in the query string. Note: Do not use the createdAt__gte, createdAt__lt and limit fields as they are already defined by the Start Time, End Time, and Top Recent Event Number input parameters respectively. | computerName__contains=DESKTOP-H****D3 |
Sort By | Optional | The column to be sorted for the results. The available options are Created At, Updated At and ID. The default value of this field is Created At. | Created At |
Direction | Optional | The results sorted in ascending or descending order. The default value is Descending. | Descending |
Event Source | Optional | The type of events (i.e., Threat or Alert) to fetch. If this parameter is not defined, the default value is Threat. | Alert |
Output
To view the sample output data for all commands, refer to this article.
Fetch Event Field Mapping
Please note that Fetch Event commands require event field mapping. Field mapping plays a key role in the data normalization process part of the event pipeline. Field mapping converts the original data fields from the different providers to the D3 fields which are standardized by the D3 Model. Please refer to Event and Incident Intake Field Mapping for details.
If you require a custom field mapping, click +Add Field to add a custom field mapping. You can also remove built-in field mappings by clicking x. Please note that two underscore characters will automatically prefix the defined Field Name as the System Name for a custom field mapping. Additionally, if an input Field Name contains any spaces, they will automatically be replaced with underscores for the corresponding System Name.
The SentinelOne integration in D3 SOAR has some pre-configured field mappings for the Threat and Alert, which correspond to the Default Event Source and Event Source for Alert mappings:
Default Event Source
Configures the field mapping which are specific to the threat-related events. If a source field in the field mapping is not found, the corresponding field mapping will be ignored. The default event source has a “Main Event JSON Path” (i.e., $.data) that is used to extract a batch of events from the response raw data. Click Edit Main JSON Path to view the “Main Event JSON Path”.-20241031-203719.png?inst-v=9d16beaf-952a-4ae4-8fe8-e35f7a3745da)
Main Event JSON Path: $.data
The Main Event JSON Path determines the root path where the system starts parsing raw response data into D3 event data. The JSON path begins with $, representing the root element. The path is formed by appending a sequence of child elements to $, each separated by a dot (.). Square brackets with nested quotation marks ([‘...’]) should be used to separate child elements in JSON arrays.
For example, the root node of a JSON Path is data. The child node denoting the Document ID field would be id. Putting it together, the JSON Path expression to extract the Document ID is $.data.id.
Event Source for Alert
-20241031-203845.png?inst-v=9d16beaf-952a-4ae4-8fe8-e35f7a3745da)
Configures the field mapping which are specific to the alert-related events. If a source field in the field mapping is not found, the corresponding field mapping will be ignored. As the data of the alert-related events have a character that the value of the Type field is Alert, the alert-related events can be defined by the Search String: {$.Type}=Alert. Click Edit Event Source to view the Search String.
The pre-configured field mappings are detailed below:
Field Name | Source Field |
Default Event Source (Main Event JSON Path: $.data) | |
Document ID | .id |
AccountID | .agentDetectionInfo.accountId |
AccountName | .agentDetectionInfo.accountName |
SiteID | .agentDetectionInfo.siteId |
SiteName | .agentDetectionInfo.siteName |
InitiatingUserId | .threatInfo.initiatingUserId |
Event Type | .threatInfo.classification |
Description | .threatInfo.analystVerdictDescription |
Start Time | .threatInfo.createdAt |
Filepath | .threatInfo.filePath |
File Hash MD5 | .threatInfo.md5 |
File Hash SHA256 | .threatInfo.sha256 |
Threat name | .threatInfo.threatName |
Techniques | .indicators[*].tactics[*].techniques[*].name |
Indicator Category | .indicators[*].category |
Indicator Description | .indicators[*].description |
Host Is Infected | .agentRealtimeInfo.agentInfected |
Host Is Active | .agentRealtimeInfo.agentIsActive |
Hostname | .agentRealtimeInfo.agentComputerName |
Device IP address | .agentRealtimeInfo.agentIpV4 |
Operating System | .agentDetectionInfo.agentOsName |
Agent ID | .agentRealtimeInfo.agentId |
Status | .threatInfo.incidentStatus |
Analyst Verdict | .threatInfo.analystVerdict |
Source | .threatInfo.initiatedBy |
Mitigation Status | .threatInfo.mitigationStatus |
Confidence Level | .threatInfo.confidenceLevel |
Storyline | .threatInfo.storyline |
Process Name | .threatInfo.originatorProcess |
Event name | .threatInfo.threatName |
Process User | .threatInfo.processUser |
External Ticket ID | .threatInfo.externalTicketId |
Malicious Process Arguments | .threatInfo.maliciousProcessArguments |
Event Source for Alert (Search String: {{$.Type}=Alert) The search string format is {jsonpath}=value. If the value of the Type key is Alert in the event object under raw data, then the alert-related events will use the field mapping below. | |
Document ID | .alertInfo.alertId |
AccountID | .agentDetectionInfo.accountId |
SiteID | .agentDetectionInfo.siteId |
Hostname | .agentDetectionInfo.name |
Event Type | .alertInfo.eventType |
Description | .alertInfo.indicatorDescription |
Start Time | .alertInfo.createdAt |
Operating System | .agentDetectionInfo.osName |
Agent ID | .agentRealtimeInfo.id |
Status | .alertInfo.incidentStatus |
Analyst Verdict | .alertInfo.analystVerdict |
Source | .alertInfo.source |
Rule name | .ruleInfo.name |
Severity | .ruleInfo.severity |
Storyline | .storyline |
Process Name | .sourceProcessInfo.name |
Process ID | .sourceProcessInfo.pid |
Process file path | .sourceProcessInfo.filePath |
Process hashes MD5 | .sourceProcessInfo.fileHashMd5 |
Process hashes SHA1 | .sourceProcessInfo.fileHashSha1 |
Process hashes SHA256 | .sourceProcessInfo.fileHashSha256 |
Parent process name | .sourceParentProcessInfo.name |
Parent process ID | .sourceParentProcessInfo.pid |
Parent process image path | .sourceParentProcessInfo.filePath |
Parent Process Hash MD5 | .sourceParentProcessInfo.fileHashMd5 |
Parent Process Hash SHA1 | .sourceParentProcessInfo.fileHashSha1 |
Parent Process Hash SHA256 | .sourceParentProcessInfo.fileHashSha256 |
Target process name | .targetProcessInfo.tgtProcName |
Target process ID | .targetProcessInfo.tgtProcPid |
Target Process File Path | .targetProcessInfo.tgtFilePath |
Target Process Hash SHA1 | .targetProcessInfo.tgtFileHashSha1 |
Target Process Hash SHA256 | .targetProcessInfo.tgtFileHashSha256 |
Target image | .targetProcessInfo.tgtProcImagePath |
Process command line | .sourceProcessInfo.commandline |
Parent process commandline | .sourceParentProcessInfo.commandline |
Target Process Commandline | .targetProcessInfo.tgtProcCmdLine |
Source IP address | .alertInfo.srcIp |
Source port | .alertInfo.srcPort |
Destination IP address | .alertInfo.dstIp |
Destination port | .alertInfo.dstPort |
Module image path | .alertInfo.modulePath |
Module Hash SHA1 | .alertInfo.moduleSha1 |
Login User Name | .alertInfo.loginsUserName |
Login Account Domain | .alertInfo.loginAccountDomain |
DV Event ID | .alertInfo.dvEventId |
Indicator Category | .alertInfo.indicatorCategory |
Indicator Name | .alertInfo.indicatorName |
Host Is Infected | .agentRealtimeInfo.infected |
Host Is Active | .agentRealtimeInfo.isActive |
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Fetch Event failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: dict_values(['xxx']): Unknown field. |
Error Sample Data Fetch Event failed. Status Code: 400. Message: dict_values(['xxx']): Unknown field. |
Fetch Files
Retrieves files from endpoints to analyze the root of threats, accommodating up to 10 MB for each instance of running the command. Due to network issues or endpoint connection problems, it might prolong the file upload process from the agent to Sentinel One management console. To avoid command timeout, use the Collect Files and Download Files commands instead.
READER NOTE
Agent ID is a required parameter to run this command.
Run the List Agents command to obtain Agent ID. Agent IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Agent ID | Required | The Agent ID for fetching files. Agent ID can be obtained using the List Agents command. | 134********951 |
Files Path | Required | The list of file path(s) to fetch files from. | [ "C:\\NPPSpy.txt" ] |
Password | Required | The new password for the archive of downloaded files. The password must have 10 or more characters with a mix of upper and lower case letters, numbers and symbols. | MySecret******! |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Fetch Files failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again. |
Error Sample Data Fetch Files failed. Status Code: 404. Message: The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again. |
Fetch Threat File
Fetches file(s) associated with the specified threat(s) by threat ID(s).
READER NOTE
The parameter Threat IDs is required to run this command.
Run the Get Threat command to obtain Threat ID. Threat IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Threat IDs | Required | The ID(s) of the threats for fetching threat files. Threat IDs can be obtained using the Get Threat command. | ["174********856"] |
Password | Required | The new password, which you will use to open the archive of downloaded files. The password must be 10 or more characters with a mix of upper and lower case letters, numbers, and symbols. | MySecret******! |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Fetch Threat File failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 502. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: All fetching threat file requests failed. Please refer to D3Errors in Raw Data for more details. |
Error Sample Data Fetch Threat File failed. Status Code: 502. Message: All fetching threat file requests failed. Please refer to D3Errors in Raw Data for more details. |
Get Account Policy
Retrieves the policy for the Account given by ID.
READER NOTE
Account ID is a required parameter to run this command.
Run the List Accounts command to obtain Account ID. Account IDs can be found in the returned raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Account ID | Required | The Account ID which account policy is to be retrieved. Account ID can be obtained using the List Accounts command. | 131********791 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Account Policy failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The account with ID xxx is not found. |
Error Sample Data Get Account Policy failed. Status Code: 404. Message: The account with ID xxx is not found. |
Get Activities
Retrieves activities and their respective data matching the specified filters. The activities are sorted by creation time in descending order.
Input
Input Parameter | Required/Optional | Description | Example |
Filter | Optional | The filter in JSON format to filter results. It is possible to use any combination of filters to narrow the list of results. Please refer to https://usea1-partners.sentinelone.net/api-doc/api-details?category=activities=get-activities for more information about filters. | { "limit": 2, "agentIds":"138********274" } |
Limit | Optional | The limit number of returned items (0-1000). If you want to retrieve all activities matching filters, please set the limit to 0. If not specified, the default value is 10. | 100 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Activities failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: User has insufficient permissions to perform the requested action. |
Error Sample Data Get Activities failed. Status Code: 403. Message: User has insufficient permissions to perform the requested action. |
Get Agent Applications
Retrieves the installed applications for the specific Agents by their agent IDs.
READER NOTE
The parameter Agent IDs is required to run this command.
Run the List Agents command to obtain Agent IDs. Agent IDs can be found in raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Agent IDs | Required | The IDs of the agents to retrieve installed applications. Agent IDs can be obtained using the List Agents command. | ["134********951", "134********111"] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Agent Applications failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized access. |
Error Sample Data Get Agent Applications failed. Status Code: 403. Message: Unauthorized access. |
Get Agent Info
Retrieves information of agents based on the specified Agent IDs.
READER NOTE
The parameter Agent IDs is required to run this command.
Run the List Agents command to obtain Agent IDs. Agent IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Agent IDs | Required | The IDs of the agents to return. Agent IDs can be obtained using the List Agents command. | [ "134********951", "134********111" ] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Agent Info failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Invalid user input received. |
Error Sample Data Get Agent Info failed. Status Code: 400. Message: Invalid user input received. |
Get Agent Process
Starts a Deep Visibility Query and retrieves events.
READER NOTE
Deep Visibility has limits for different accounts. The current trial account currently retains data for 14 days. If you see errors returned for your search period, contact SentineOne support to increase the data retention period if required.
https://usea1-partners.sentinelone.net/docs/en/date-and-time-reference.html#date-and-time-reference
Input
Input Parameter | Required/Optional | Description | Example |
Start Time | Optional | The Start Time (in UTC Time) of the time range. | 2022-09-20 00:00 |
End Time | Optional | The End Time (in UTC Time) of the time range. | 2022-09-26 00:00 |
Query | Optional | The queries defined to filter results. Please refer to Query Syntax in the Knowledge Base (support.sentinelone.com) or the Console Help. Please refer to https://assets.sentinelone.com/c/sentinel-one-dv-chea-2?x=u6040P for the field name syntax. | ProcessImagePath CONTAINS \"windows\" |
Limit | Optional | The set maximum number of returned items (Between 1-1000). Up to 1000 results will be returned if you leave this field empty. | 10 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Agent Process failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Deep Visibility currently retains data for 14 days, to increase your data retention, please contact S1. |
Error Sample Data Get Agent Process failed. Status Code: 400. Message: Deep Visibility currently retains data for 14 days, to increase your data retention, please contact S1. |
Get Alerts
Retrieves a list of alerts based on filter parameters.
READER NOTE
Site IDs and Endpoint Names are optional parameters to run this command.
Run the Get Sites command to obtain Site IDs. Site IDs can be found in the raw data at the path $.data.sites.id.
Run the List Agents command to obtain Endpoint Names. Endpoint Names can be found in the raw data at the path $.data[*].computerName.
If you want to view alert related threats, you can use the Get Threat command with Storyline IDs obtained from this command as input parameter. Storyline IDs can be found in the raw data at the path $.data[*].sourceProcessInfo.storyline.
If your inputs are invalid, the command will return success with no result.
Input
Input Parameter | Required/Optional | Description | Example |
Created After | Optional | Returns alerts which were created after or at this time. | 2023-08-11 00:00 |
Created Before | Optional | Returns alerts which were created before or at this time. | 2023-08-11 00:00 |
Incident Statuses | Optional | Filter alerts by incident status. The available statuses are RESOLVED, UNRESOLVED and IN_PROGRESS | [ "IN_PROGRESS" ] |
Analyst Verdicts | Optional | Filter alerts by analyst verdict. The available analyst verdicts are FALSE_POSITIVE,TRUE_POSITIVE,SUSPICIOUS and UNDEFINED. | [ "SUSPICIOUS", "UNDEFINED" ] |
Site IDs | Optional | List of Site IDs to filter by. You can get Site ID with Get Sites command. | [ "138********161" ] |
Rule Names | Optional | Free-text filter by rule name. You can enter multiple rule names. | [ "Test rule", "testrule1" ] |
Endpoint Names | Optional | Free-text filter by agent name. You can get Endpoint Name with List Agents command. | [ "lab3-***" ] |
Severity | Optional | Filters by severity. Options are Critical, High, Medium and Low. | High |
Query | Optional | Full text search for all fields. For example, you can query an artifact value, such as hash, process name, IP or URL etc. Or you can query a storyline ID. | [ "2d7********c1a" ] |
Limit | Optional | Limit number of returned alerts. The valid value is an integer between 0 and 1000. If not specified, the default limit is 1000. If you want all alerts matching search criteria to be returned, please set limit to 0. | 10 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Alerts failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized access. |
Error Sample Data Get Alerts failed. Status Code: 403. Message: Unauthorized access. |
Get Black List
Retrieves item(s) from the blacklist.
Input
Input Parameter | Required/Optional | Description | Example |
Limit | Optional | Sets the maximum number of items to return (between 1 to 1000). Up to 1000 blacklists will be returned if you leave this field empty. | 10 |
Custom Input | Optional | Defines the queries in JSON format to filter results. Please refer to https://usea1-partners.sentinelone.net/api-doc/api-details?category=exclusions-and-blacklist=get-blacklist for more information about query parameters. | { "type": "black_hash", "tenant": false, "siteIds": "947********671" } |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Black List failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The value for parameter (Custom Input) is invalid. |
Error Sample Data Get Black List failed. Status Code: 400. Message: The value for parameter (Custom Input) is invalid. |
Get Events by Query ID and Type
Retrieves Deep Visibility events from the specified Query ID and/or Event Type.
READER NOTE
Query ID is a required parameter to run this command.
Run the Create Query command to obtain the Query ID. Query IDs can be found in the raw data at the path $.data.queryId.
Please note that only the query IDs under the created account can be used here. Which means query ID under account1 cannot be retrieved with this command under account2. No matter what the scopes are for those accounts.
Input
Input Parameter | Required/Optional | Description | Example |
Query ID | Required | The Query ID of the query to retrieve events. Query ID can be obtained using the Create Query command. | qe1********bed |
Event Type | Optional | The type of event to return. The valid event types are: DNS, Events, File, IP, Logins, Process, Registry, Scheduled Task and URL. | Events |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Events by Query ID and Type failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Bad Request: ['Invalid query ID']. |
Error Sample Data Get Events by Query ID and Type failed. Status Code: 400. Message: Bad Request: ['Invalid query ID']. |
Get Exclusions
Retrieves a list of all the Exclusions that match the filter.
READER NOTE
Account IDs, Site IDs, Group IDs and Exclusion IDs are optional parameters to run this command.
Run the List Accounts command to obtain Account IDs. Account IDs can be found in the raw data at the path $.data[*].id.
Run the Get Sites command to obtain Site IDs. Site IDs can be found in the raw data at the path $.data.sites.id.
Run the Get Groups command to obtain Group IDs. Group IDs can be found in the raw data at the path $.data.id.
Input
Input Parameter | Required/Optional | Description | Example |
Type | Optional | The exclusion item type. | Path |
Operation System | Optional | The operation system to filter. | Linux |
Account IDs | Optional | The account IDs to filter. Account IDs can be obtained using the List Accounts command. | ["131********791"] |
Site IDs | Optional | The site IDs to filter. Site IDs can be obtained using the Get Sites command. | ["174********138"] |
Group IDs | Optional | The group IDs to filter. Group IDs can be obtained using the Get Groups command. | ["151********497"] |
Exclusion IDs | Optional | The exclusion IDs to filter. | ["174********364"] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Exclusions failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: groupIds: 0: Not a valid Identifier. |
Error Sample Data Get Exclusions failed. Status Code: 400. Message: groupIds: 0: Not a valid Identifier. |
Get Global Policy
Get the Global policy. This is the default policy for your deployment.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Global Policy failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized access. |
Error Sample Data Get Global Policy failed. Status Code: 403. Message: Unauthorized access. |
Get Groups
Retrieves data from groups of the specified site IDs.
READER NOTE
The parameter Site IDs is required to run this command.
Run the Get Sites command to obtain Site IDs. Site IDs can be found in the raw data at the path $.data.sites.id.
Input
Input Parameter | Required/Optional | Description | Example |
Site IDs | Required | The ID(s) of sites to retrieve groups from. Site IDs can be obtained using the Get Sites command. | 947********671 |
Custom Input | Optional | The defined queries in JSON format to filter results. Please refer to https://usea1-partners.sentinelone.net/api-doc/api-details?category=groups=get-groups for more information about query parameters. | { "groupIds": "951********411,947*******716", "isDefault": false, "type": "static", "updatedAt__gte": "2020-08-01 16:42:07" } |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Groups failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Not a valid Identifier. |
Error Sample Data Get Groups failed. Status Code: 400. Message: Not a valid Identifier. |
Get Hash Reputations
Retrieves the hash reputation of an input SHA-1 value.
READER NOTE
The parameter File Hashes is required to run this command.
Run the Fetch Event command to obtain File Hashes. File Hashes can be found in the raw data at the path $.data[*].threatInfo.sha1.
If the hash is invalid/not found, it could return success with no result
Input
Input Parameter | Required/Optional | Description | Example |
File Hashes | Required | The SHA1 value of the file content hash. File Hashes can be obtained using the Fetch Event command. | [ "a6d********d00" ] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Hash Reputations failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized access. |
Error Sample Data Get Hash Reputations failed. Status Code: 403. Message: Unauthorized access. |
Get Query Status
Retrieves that status of a Deep Visibility Query.
READER NOTE
Query ID is a required parameter to run this command.
Run the Create Query command to obtain the Query ID. Query IDs can be found in the raw data at the path $.data.queryId.
Input
Input Parameter | Required/Optional | Description | Example |
Query ID | Required | The Query ID obtained when creating a query. Query ID can be obtained using the Create Query command. | q5b************069 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Query Status failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Bad Request: ['Invalid query ID']. |
Error Sample Data Get Query Status failed. Status Code: 400. Message: Bad Request: ['Invalid query ID']. |
Get Script Results
Retrieves script result URLs. One of the Task IDs or Computer Names parameters must be defined. Note: Only one input parameter can be used to filter results for an instance of running the command.
READER NOTE
The parameter Task IDs is optional to run this command.
Run the Get Script Task Status command to obtain Task IDs. Task IDs can be found in the raw data at the path $.data[*].id.
To run the Run Script command, the specified Computer Names must be included. Simply put this information in the Filter parameter, and then execute the Run Script command.
Please note that not all scripts are guaranteed to produce results. If your input Task IDs do not yield any results, D3 will return “Success” but with no returned data.
Input
Input Parameter | Required/Optional | Description | Example |
Task IDs | Optional | The list of Task IDs to retrieve a download link for. Task IDs can be obtained using the Get Script Task Status command. | [ ***** ] |
Computer Names | Optional | The list of computer names (partial or whole) to retrieve a download link. The computers listed should have run scripts prior. | [ "DESKTOP-*****" ] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Script Results failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The value for parameter (Task IDs) is invalid. |
Error Sample Data Get Script Results failed. Status Code: 400. Message: The value for parameter (Task IDs) is invalid. |
Get Scripts
Retrieves data of the scripts in the SentinelOne Script Library. If you don’t have global scope permission, you can only access the scripts of your specific scope.
READER NOTE
Account IDs and Site IDs are optional parameters to run this command.
Run the List Accounts command to obtain Account IDs. Account IDs can be found in the raw data at the path $.data[*].id.
Run the Get Sites command to obtain Site IDs. Site IDs can be found in the raw data at the path $.data.sites.id.
Retrieve data from the scripts in the SentinelOne Script Library. If you lack global scope permission, you will only have access to scripts within your specific scope. Navigate to view scope by clicking Global Scope>Account Scope>Site Scope.
Users with lower scope permissions cannot view scripts under higher scopes, resulting in limited script visibility. To determine the scope of the account your connector is using, click on the user to view details.
For example, if a user is under the “D3 Security” account scope, they can retrieve all scripts within that account by entering D3 Security’s account ID in the Account IDs parameter. If this parameter is left empty, it will automatically fetch all scripts under the “D3 Security” account.
In this scenario, if you input site IDs within the same account (they must be from within the account and not from another account), it will fetch all scripts specific to those sites, resulting in fewer scripts compared to the entire account.
Input
Input Parameter | Required/Optional | Description | Example |
Account IDs | Optional | The list of Account IDs to filter by. Account ID can be obtained using the List Accounts command. | [ "*****" ] |
Site IDs | Optional | The list of Site IDs to filter by. Site IDs can be obtained using the Get Sites command. | [ "*****" ] |
Script Type | Optional | The script type to filter by. If not specified, scripts of all script types will be returned. | Action |
OS Type | Optional | The operating system type to filter by. If not specified, scripts of all OS types will be returned. | Windows |
Query | Optional | The full or partial script name to filter by. | testscript0427 |
Limit | Optional | The limit number of returned items, the available value is an integer between 1 and 1000. If not specified, the default value is 10. | 10 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Scripts failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: accountIds: 0: Not a valid Identifier. |
Error Sample Data Get Scripts failed. Status Code: 400. Message: accountIds: 0: Not a valid Identifier. |
Get Script Task Status
Retrieves remote script tasks based on the specified filters.
READER NOTE
The parameter Parent Task IDs is required to run this command.
Run the Run Script command to obtain Parent Task IDs. Parent Task IDs can be found in the raw data at the path $.data.parentTaskId.
If you run this command and see a value in the "nextcursor" field of the returned raw data, you can use that value in the Next Page parameter to retrieve the data on the next page.
Input
Input Parameter | Required/Optional | Description | Example |
Parent Task IDs | Required | The list of Parent Task IDs to filter by. Parent Task IDs can be obtained using the Run Script command. | ["*****"] |
Computer Name Contains | Optional | The free-text filter by agent computer names. Multiple values are supported. | ["DESKTOP", "AWS"] |
Updated After | Optional | The filter to return tasks that were updated after the specified time. | 2022-09-27 00:00 |
Updated Before | Optional | The filter to return tasks that were updated before the specified time. | 2022-09-28 00:00 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Script Task Status failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized access. |
Error Sample Data Get Script Task Status failed. Status Code: 403. Message: Unauthorized access. |
Get Sites
Retrieves sites of the specified criteria.
READER NOTE
The parameter Account IDs is optional to run this command.
Run the List Accounts command to obtain Account IDs. Account IDs can be found in the raw data at the path $.data[*].id.
If you run this command and see "nextcursor" field has value in the returned raw data, it can be used in the Next Page parameter to get the data in next page.
Input
Input Parameter | Required/Optional | Description | Example |
Site IDs | Optional | The list of Site IDs to filter sites. | [ "*****", "*****" ] |
Account IDs | Optional | The list of Account IDs to filter sites. Account IDs can be obtained using the List Accounts command. | [ "*****", " info *****" ] |
Query | Optional | The query string for full-text search of fields. The available fields are name, account_name and description. | name |
State | Optional | The state (i.e. active, deleted, or expired) of the sites to filter results. | Active |
Limit | Optional | The maximum number of results to return (between 1-1000). Up to 1000 results will be returned if you leave this field empty. | 100 |
Offset | Optional | The number up to which result to skip. For example, if the defined value is 50, results from 1 to 50 will be skipped. To skip more than 1000 results, use the Next Page input parameter. | 1 |
Sort By | Optional | The column (if selected) to sort results by. Available inputs are activeLicenses, createdAt, expiration, siteType, sku, id, state, suite, totalLicenses and updatedAt. | Create At |
Direction | Optional | The results sorted in ascending or descending order. The default value is Ascending. | Ascending |
Next Page | Optional | The pagination through collections of data by setting the parameter with the nextCursor attribute returned by a previous request's response metadata. | ***** |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Sites failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: accountIds: 0: Not a valid Identifier. |
Error Sample Data Get Sites failed. Status Code: 400. Message: accountIds: 0: Not a valid Identifier. |
Get Star Custom Rules
Retrieves a list of star custom rules for a given scope.
READER NOTE
Account IDs, Site IDs, Group IDs are optional parameters to run this command.
Run the List Accounts command to obtain Account IDs. Account IDs can be found in the raw data at the path $.data[*].id.
Run the Get Sites command to obtain Site IDs. Site IDs can be found in the raw data at the path $.data.sites.id.
Run the Get Groups command to obtain Group IDs. Group IDs can be found in the raw data at the path $.data.id.
Input
Input Parameter | Required/Optional | Description | Example |
Account IDs | Optional | The account IDs to filter. Account IDs can be obtained using the List Accounts command. | ["*****"] |
Site IDs | Optional | The site IDs to filter. Site IDs can be obtained using the Get Sites command. | ["*****"] |
Group IDs | Optional | The group IDs to filter. Group IDs can be obtained using the Get Groups command. | ["*****"] |
Rule IDs | Optional | The star custom rule IDs to filter. | ["*****"] |
Creator | Optional | The free-text filtered by rule creator. | [ "*****" ] |
Name | Optional | The free-text filtered by rule name. | [ "test" ] |
Status | Optional | The status of rules to filter. Available options include Activating, Active, Deleted, Deleting, Disabled, Disabling and Draft. | [ "Active" ] |
Query | Optional | The free-text filtered by S1 query. | [ "test" ] |
Query Type | Optional | The return rules filter by type. The available options are Events and Processes. | [ "events" ] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Star Custom Rules failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: accountIds: 0: Not a valid Identifier. |
Error Sample Data Get Star Custom Rules failed. Status Code: 400. Message: accountIds: 0: Not a valid Identifier. |
Get System Info
Retrieves the console build, version, patch, and release information.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
rror Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get System Info failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized access. |
Error Sample Data Get System Info failed. Status Code: 403. Message: Unauthorized access. |
Get System Status
Retrieves an indication of the system's health status.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get System Status failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized access. |
Error Sample Data Get System Status failed. Status Code: 403. Message: Unauthorized access. |
Get Threat
Returns a list of threats matching the specified criteria. The threats will be listed in ascending order (from oldest to latest).
READER NOTE
The parameter Storylines is an optional parameter to run this command.
Run the Get Alerts command to obtain Storylines. Storylines can be found in the raw data at the path $.data[*].sourceProcessInfo.storyline.
To view threats related to an alert, use the Get Threat command with Storylines obtained from this command as the input parameter.
Input
Input Parameter | Required/Optional | Description | Example |
Limit | Optional | The maximum number of returned items (between 1-1000). Up to 1000 threats will be returned if you leave this field empty. | 2 |
Custom Input | Optional | The defining of a query in JSON format to filter results. Please refer to https://usea1-partners.sentinelone.net/api-doc/api-details?category=threats=get-threats for more information about the available custom inputs. | { "createdAt__gt": "2020-07-30 17:53:25" } |
Storylines | Optional | The storyline ID(s) to retrieve related threats. Storylines can be obtained using the Get Alerts command to retrieve alert related threats. | [ "*****" ] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Threat failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Insufficient permissions. |
Error Sample Data Get Threat failed. Status Code: 403. Message: Insufficient permissions. |
Get Threat Analysis
Retrieves detailed threat analysis information of a specified threat. Note: This command will only work with a private API connection.
READER NOTE
Threat ID is a required parameter to run this command.
Run the Get Threat command to obtain Threat ID. Threat IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Threat ID | Required | The Threat ID to retrieve the corresponding threat analysis information. Threat ID can be obtained using the Get Threat command. | ***** |
Components | Optional | The threat components to return. If this parameter is not defined, all components will be returned. The available modules are agentDetectionInfo, agentRealtimeInfo, containerInfo, customDetectionRules, indicators, kubernetesInfo, mitigationStatus, threatInfo or whiteningOptions. | [ "threatInfo", "indicators" ] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Threat Analysis failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Threat ID xxx was not found. |
Error Sample Data Get Threat Analysis failed. Status Code: 404. Message: Threat ID xxx was not found. |
Get Threat Events
Retrieves events of a specified Threat ID and filters results based on the specified criteria.
READER NOTE
Threat ID is a required parameter to run this command.
Run the Fetch Event command to obtain Threat ID. Choose the Event Source parameter to Threat. Threat ID is the threat event id, which can be found in the raw data at the path $.id.
You should not use the Get Threat command since not all threats are events. If you use the not event threat ID, then this command will return success with no result.
Process Name is an optional parameter to run this command.
Get Threat Events command to obtain Process Name. Process Names can be found in the raw data at the path $.data[*].processName.
If you run this command and get "nextCursor" field in the returned raw data, you may use the value to input in the NextPage parameter to obtain the next page data
Input
Input Parameter | Required/Optional | Description | Example |
Threat ID | Required | The Threat ID to retrieve events from. Threat ID can be obtained using the Fetch Event command. | ***** |
Use Private Call | Optional | The command will retrieve events using a private API (True) or public API (False). | True |
Event ID | Optional | The Event ID (Process Unique Key) to filter events. | ***** |
Event Types | Optional | The event types available options include: events, dns, logins, module, registry, url, scheduled_task, process, file, indicators and ip to filter events. Please note that this field is case sensitive, only lowercase can be accepted. Event Types can be obtained using the Get Threat Events command with the Event ID parameter left empty. After running the command, the EventTypes can be found in the raw data at the path $.data[*].objectType. | [ "events", "file", "ip", "process" ] |
Event Sub Types | Optional | The event subtypes to filter events. Event Sub Types can be obtained using the Get Threat Events command from the Key Fields. The possible inputs are categorized as the subtypes of files below: FILEDELETION, FILEMODIFICATION, FILECREATION, FILERENAME, FILESCAN. Subtypes of processes: PROCESSCREATION, PROCESSMODIFICATION, PROCESSTERMINATION. Subtypes of IPs: TCPV4, TCPV4LISTEN, TCPV6, TCPV6LISTEN. Subtypes of indicators: BEHAVIORALINDICATORS. Subtypes of logins: LOGIN, LOGOUT. Subtypes of module: MODULE. Subtypes of DNS: DNS. Subtypes of URL: HTTP. Subtypes of registry: REGISTRYACTION, REGKEYCREATE, REGKEYDELETE, REGKEYEXPORT, REGKEYIMPORT, REGKEYRENAME, REGKEYSECURITYCHANGED, REGVALUECREATE, REGVALUEMODIFIED. Subtypes of scheduled_task: SCHEDTASKDELETE, SCHEDTASKREGISTER, SCHEDTASKSTART, SCHEDTASKTRIGGER, SCHEDTASKUPDATE. Please note that this field is case sensitive, only uppercase letters are valid. | [ "FILEDELETION", "FILEMODIFICATION" ] |
Process Name | Optional | The process name (partial or whole) to filter events. | conhost.exe |
Count Only | Optional | The total count of events in the returned Raw Data under the key "totalItems", if True is selected. The default value is False. | False |
Skip Count | Optional | The selection of True will skip the total event count function to reduce the running time of the command. If True is selected in this parameter, the "totalItems" in returned Raw Data will be 0. The default value is False. | False |
Limit | Optional | The maximum number of events to return (between 1 to 1000). Up to 1000 results will be returned if this field is left empty. | 100 |
Offset | Optional | The number up to which results to skip. To skip more than 1000 results, use the Next Page input parameter. | 1 |
Sort By | Optional | The column selected and used to sort results. | Create At |
Direction | Optional | The results sorted in ascending or descending order. The default value is Ascending. | Ascending |
Next Page | Optional | The pagination through collections of data by setting the parameter with the nextCursor attribute returned by a previous request's response_metadata. | ***** |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Threat Events failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Threat ID xxx not found. |
Error Sample Data Get Threat Events failed. Status Code: 404. Message: Threat ID xxx not found. |
Get Threat Notes
Retrieves threat notes for a specified threat.
READER NOTE
Threat ID is a required parameter to run this command.
Run the Get Threat command to obtain the Threat ID. Threat IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Threat ID | Required | The threat ID for which to retrieve the associated note. Threat ID can be obtained using the Get Threat command. | 2073*****0987 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Threat Notes failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Threat ID xxx was not found. |
Error Sample Data Get Threat Notes failed. Status Code: 404. Message: Threat ID xxx was not found. |
Initiate Scan
Initiates a Full Disk Scan on Agents that match the specified filters. Full Disk Scan finds dormant suspicious activity, threats, and compliance violations in the local file system, that are then mitigated according to the policy. If both optional input parameters are not defined, all Agents will be scanned.
READER NOTE
The parameter Agent IDs is optional to run this command.
Run the List Agent command to obtain Agent IDs. Agent IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Agent IDs | Optional | The IDs of the agents to scan. Agent ID can be obtained using the List Agent command. | [ "*****" ] |
Filter | Optional | The filter to scan Agents. Leave this parameter empty to scan all applicable agents. Please refer to https://usea1-partners.sentinelone.net/api-doc/api-details?category=agent-actions=initiate-scan for more information about the filter syntax. | { "computerName": "DESKTOP-*****" } |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Initiate Scan failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Authentication Failed. |
Error Sample Data Initiate Scan failed. Status Code: 401. Message: Authentication Failed. |
Kill Processes
Stops all processes related to the threat(s) matching filter on the specified host(s).
READER NOTE
The parameter Threat IDs is optional to run this command.
Run the Get Threat command to obtain Threat IDs. Threat IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Computer Names | Required | The name(s) of the computer(s) on which the processes are killed. | [ "lab3-pc1" ] |
Originated Process Names | Optional | The originated process name(s) of the threat(s) whose processes will be killed. | [ "svchost.exe" ] |
Threat IDs | Optional | The ID(s) of the threat(s) whose processes will be killed. Threat IDs can be obtained using the Get Threat command. | [ "*****" ] |
File Paths | Optional | The file path(s) to search. | [ "\***\***\***\***\***.exe" ] |
Content Hashes | Optional | The SHA-1 Hash value(s) to search. | [ "*****" ] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Kill Processes failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: UNAUTHORIZED. Please check D3Error object in RawData for more details. |
Error Sample Data Kill Processes failed. Status Code: 401. Message: UNAUTHORIZED. Please check D3Error object in RawData for more details. |
List Accounts
Retrieves a list of accounts that match the specified filter.
READER NOTE
If you run this command and see "nextcursor" field has value in the returned raw data, it can be used in the Next Page parameter to get the data in next page.
Input
Input Parameter | Required/Optional | Description | Example |
Account IDs | Optional | The account ID(s) to filter the results. | [ "*****", "*****" ] |
Name | Optional | The string to apply a full-text search of account names (full or partial names). | D3 Security |
State | Optional | The accounts filtered by state. | [ Active ] |
Limit | Optional | The maximum number of returned results (between 1-1000). Up to 1000 results will be returned if this field is left empty. | 100 |
Offset | Optional | The number up to which result to skip. For example, if the defined value is 50, results from 1 to 50 will be skipped. To skip more than 1000 results, use the Next Page input parameter. | 1 |
Sort By | Optional | The column to sort results by. Available options are Creation Time, Update Time, Account ID, Name, State and Usage Type. | Creation Time |
Direction | Optional | The results sorted in ascending or descending order. The default value is Ascending. | Ascending |
Next Page | Optional | The pagination through collections of data by setting the parameter with the nextCursor attribute returned by a previous request's response metadata. | ***** |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Accounts failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Invalid user input received. |
Error Sample Data List Accounts failed. Status Code: 400. Message: Invalid user input received. |
List Agents
Retrieves a list of agents that match the specified filter.
Input
Input Parameter | Required/Optional | Description | Example |
Computer Name | Optional | The computer name of the agent to list. Both partial and full names are accepted. | DESKTOP-***** |
Query | Optional | The free-text search term, will match applicable attributes including agentVersion, domain, externalIp, gatewayIp, inet, inet6, physical, lastLoggedInUserName, machineType,uuid, osType, osName. | ***.***.***.*** |
Limit | Optional | The number of agents matching the query condition (between 1-1000) to return. Up to 1000 agents will be listed if you leave this field empty. | 10 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Agents failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Invalid user input received. |
Error Sample Data List Agents failed. Status Code: 400. Message: Invalid user input received. |
List IOCs
Retrieves the IOCs of a specified account that match the filter.
READER NOTE
The parameter Account IDs is required to run this command.
Run the List Accounts command to obtain Account IDs. Account IDs can be found in the returned raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Account IDs | Required | The account IDs to filter. Account IDs can be obtained using the List Accounts command. | [ "*****" ] |
IOC Names | Optional | The free-text filtered by the Indicator name (which supports multiple values). | [ "foo.dll" ] |
IOC Value | Optional | The value of the Threat Intelligence indicator. | ***.***.***.*** |
Type | Optional | The type of the Threat Intelligence indicator. The available types include: IPv4, IPv6, MD5, SHA1, SHA256, URL and DNS. | IPv4 |
Source | Optional | The list of the sources of the identified Threat Intelligence indicator. | AlienVault |
Categories | Optional | The categories of the Threat Intelligence indicator. | [ "the malware type associated with the IOC" ] |
Description | Optional | The free-text filtered by the description of the indicator (which supports multiple values). | [ "Malicious-activity" ] |
Creator | Optional | The free-text filtered by the user that uploaded the Threat Intelligence indicator (which supports multiple values). | [ "admin@sentinelone.com" ] |
Created After | Optional | The creation time set by the user after or equal to the specified timestamp. | 2022-03-20 00:00 |
Created Before | Optional | The creation time set by the user before or equal to the specified timestamp. | 2022-03-21 00:00 |
Updated After | Optional | The time at which the indicator was last updated in SentinelOne DB after or equal to the specified timestamp. | 2022-04-20 00:00 |
Updated Before | Optional | The time at which the indicator was last updated in SentinelOne DB before or equal to the specified timestamp. | 2022-04-30 00:00 |
Limit | Optional | The limit number of returned IOCs. The valid value is an integer between 0 and 1000. If not specified, the default limit is 1000. To obtain all IOCs matching search criteria to be returned, set the limit to 0. | 10 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List IOCs failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Insufficient permissions. |
Error Sample Data List IOCs failed. Status Code: 401. Message: Insufficient permissions. |
Mark As Threat
Marks suspicious threats as threat detections. Can only be used with API V2.0.
READER NOTE
The parameter Threat IDs is required to run this command.
Run the Get Threat command to obtain Threat IDs. Threat IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Threat IDs | Required | The list of threat IDs. Threat IDs can be obtained using the Get Threat command. | ["*****", "*****"] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Mark As Threat failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized access. |
Error Sample Data Mark As Threat failed. Status Code: 403. Message: Unauthorized access. |
Mitigate Threats
Applies a mitigation action to threats matching the specified filters. Only threats which you have permission to mitigate are counted as "affected" in the response field. Rollback is applied only on Windows. Remediate is applied only on macOS and Windows.
Input
Input Parameter | Required/Optional | Description | Example |
Filter | Required | The filtering options to control the list of affected threats. It is possible to use any combination of filters to narrow the list. For example, "apply to only active threats from Linux endpoints". It is also possible to leave this field empty to apply to all available threats. Please refer to https://usea1-partners.sentinelone.net/api-doc/api-details?category=threats=mitigate-threats for more information about filters. | { "computerName__contains": [ "DESKTOP-*****" ] } |
Mitigate Action | Required | The mitigation action selected to apply to the group of threats that matches the filter. Note: The Rollback mitigation action is only applied on Windows systems; the Remediate mitigation action is only applied on Windows and macOS systems. | Quarantine |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Mitigate Threats failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized access. |
Error Sample Data Mitigate Threats failed. Status Code: 403. Message: Unauthorized access. |
Move Agents
Moves Agents to a new group by host name(s) or internal IP(s). Please note, you cannot move agents to a group which is not in the same site as the original group, and you must move the agents to the new site before you move agents to the group belonging to that site. To do this, you can use the Move Agents Between Sites command.
READER NOTE
Group ID is a required parameter to run this command.
Run the Get Groups command to obtain Group ID. Group IDs can be found in the raw data at the path $.data.id.
Input
Input Parameter | Required/Optional | Description | Example |
Host Names Or Internal IPs | Required | The name(s) or internal IP(s) of the computer(s) to be moved to the specified group. | [ "***.***.***.***", "lab3-pc1" ] |
Group ID | Required | The ID of the Group to which the agents will be moved. Group ID can be obtained using the Get Groups command. | ***** |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Move Agents failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The group with ID **** is not found. |
Error Sample Data Move Agents failed. Status Code: 404. Message: The group with ID **** is not found. |
Move Agents Between Sites
Moves Agents from one Site to a different Site. Agents will be moved to the best matching dynamic group, or to the Default group if no dynamic group matches.
READER NOTE
Site ID is a required parameter to run this command.
Run the Get Sites command to obtain Site ID. Site IDs can be found in the raw data at the path $.data.sites.id.
Input
Input Parameter | Required/Optional | Description | Example |
Host Names Or Internal IPs | Required | The name(s) or internal IP(s) of the computer(s) to be moved to the specified site. | [ "***.***.***.***", "lab3-pc1" ] |
Site ID | Required | The ID of the site where the agents will be moved. Site ID can be obtained using the Get Sites command. | ***** |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Move Agents Between Sites failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Authentication Failed. |
Error Sample Data Move Agents Between Sites failed. Status Code: 401. Message: Authentication Failed. |
Ping Power Query
Ping Deep Visibility Power Query(s) using the query ID(s) if results have not returned from the initial Power Query or a previous ping.
READER NOTE
The parameter Query IDs is required to run this command.
Run the Create Power Query command to obtain Query IDs. Query IDs can be found in the raw data in the path $.results[*].queryId.
Input
Input Parameter | Required/Optional | Description | Example |
Query IDs | Required | The unique identifier for specific queries to execute or manage. Query ID(s) can be obtained using the Create Power Query command to ping. | [ "*****" ] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Ping Power Query failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Multiple errors found, please check D3Errors in command Raw Data. |
Error Sample Data Ping Power Query failed. Status Code: 401. Message: Multiple errors found, please check D3Errors in command Raw Data. |
Quarantine Files
Encrypts and moves the threat and its executables files to a quarantine folder. Please note, this action performs Kill Processes related to the threat(s) before Quarantine.
READER NOTE
The parameter Threat IDs is optional to run this command.
Run the Get Threat command to obtain Threat IDs. Threat IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Computer Names | Required | The name(s) of the computer(s) on which the files are quarantined. | [ "lab3-pc1" ] |
Originated Process Names | Optional | The originated process name(s) of the threat(s) whose files will be quarantined. | [ "svchost.exe" ] |
Threat IDs | Optional | The ID(s) of the threat(s) whose files will be quarantined. Threat IDs can be obtained using the Get Threat command. | [ "*****" ] |
File Paths | Optional | The file path(s) to search. | [ "\***\***\***\***\***.exe" ] |
Content Hashes | Optional | The SHA-1 Hash value(s) to search. | [ "*****" ] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Quarantine Files failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: UNAUTHORIZED. Please check D3Error object in RawData for more details. |
Error Sample Data Quarantine Files failed. Status Code: 401. Message: UNAUTHORIZED. Please check D3Error object in RawData for more details. |
Query
Retrieves Deep Visibility events based on specified query conditions. Note: The API rate limit is 1 call per minute for each unique user token.
READER NOTE
Deep Visibility has limits for different accounts. The current trial account currently retains data for 14 days. If you see errors returned for your search period, contact SentineOne support to increase the data retention period if required.
https://usea1-partners.sentinelone.net/docs/en/date-and-time-reference.html#date-and-time-refer
Input
Input Parameter | Required/Optional | Description | Example |
Start Time | Required | The start time (in UTC Time) of the time range for querying events that are created after the specified start time. | 2022-09-22 00:00 |
End Time | Required | The end time (in UTC Time) of the time range for querying events that are created before the specified end time. | 2022-09-23 00:00 |
Limit | Optional | The maximum number of items to return. A valid value is an integer between 1 and 100,000. Up to 100,000 results will be returned if you leave this field empty. | 10 |
Query | Required | The queries to filter events. Please refer to Query Syntax in the Knowledge Base (https://support.sentinelone.com) or the Console Help. Please also refer to https://assets.sentinelone.com/c/sentinel-one-dv-chea-2?x=u6040P for the field name syntax. | processImagePath CONTAINS "svchost.exe" |
Timeout (Seconds) | Optional | The specification of how many seconds to allow before aborting the query if the query status is not finished. If this parameter is not defined, the query will not be canceled. The minimum valid input value is 300. | 300 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Query failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Authentication Failed. |
Error Sample Data Query failed. Status Code: 401. Message: Authentication Failed. |
Remove Items In Blacklist
Removes threats from the blacklist
READER NOTE
The parameter Item IDs is optional to run this command.
Run the Get Blacklist command to obtain Item IDs. Item IDs can be found in the raw data at the path $.data.id.
Input
Input Parameter | Required/Optional | Description | Example |
Item IDs | Optional | The ID(s) of the blacklisted items to remove. Item IDs can be obtained using the Get Blacklist command. | [ "*****", "*****" ] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Remove Items In Blacklist failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Authentication Failed. |
Error Sample Data Remove Items In Blacklist failed. Status Code: 401. Message: Authentication Failed. |
Resolve Threat
Updates status of specified threats to resolve.
READER NOTE
Threat IDs and Agent ID are required parameters to run this command.
Run the Get Threat command to obtain Threat IDs. Threat IDs can be found in the raw data at the path $.data[*].id.
Run the List Agents command to obtain Agent ID. Agent ID can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Threat IDs | Required | The list of Threat ID(s) to resolve. Threat ID(s) can be obtained using the Get Threat command. | [ "*****", "*****" ] |
Agent ID | Required | The Agent ID associated with the threat. Agent ID can be obtained using the List Agents command. | ***** |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Resolve Threat failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Authentication Failed. |
Error Sample Data Resolve Threat failed. Status Code: 401. Message: Authentication Failed. |
Restart Endpoints
Restarts endpoints that have an Agent installed and that fit the filter. We recommend that you use the Broadcast Message command to send a message to users of endpoints before you restart their computers.
READER NOTE
Agent IDs and Group IDs are optional parameters to run this command.
Run the List Agents command to obtain Agent IDs. Agent IDs can be found in the raw data at the path $.data[*].id.
Run the Get Groups command to obtain Group IDs. Group IDs can be found in the raw data at the path $.data.id.
Input
Input Parameter | Required/Optional | Description | Example |
Agent IDs | Optional | The ID(s) of the agent(s) to restart endpoints. Agent IDs can be obtained using the List Agents command. Please note, either Agent IDs or Group IDs, or both should be entered. If both are entered, the Agent IDs in the Groups will be restarted. | [ " *****" ] |
Group IDs | Optional | The ID(s) of the group(s) to which the hosts belong will be restarted. Group IDs can be obtained using the Get Groups command. Please note, Group IDs or Agent ID, or both should be entered. If both are entered, Agent IDs in the Groups will be restarted. | [ "*****" ] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Restart Endpoints failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Authentication Failed. |
Error Sample Data Restart Endpoints failed. Status Code: 401. Message: Authentication Failed. |
Rollback Remediation
Restores files and configurations that the threat(s) changed. This action performs Kill, Quarantine and Remediate before Rollback Remediation. Please note, Rollback Remediation is applied only on Windows.
READER NOTE
The parameter Threat IDs is optional to run this command.
Run the Get Threat command to obtain Threat IDs. Threat IDs can be found in the raw data at the path $data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Computer Names | Required | The name(s) of the computer(s) on which to roll back remediation. | [ "lab3-pc1" ] |
Originated Process Names | Optional | The originated process name(s) of the threat(s) which change will be rolled back. | [ "svchost.exe" ] |
Threat IDs | Optional | The ID(s) of the threat(s) which change will be rolled back. Threat IDs can be obtained using the Get Threat command. | [ "*****" ] |
File Paths | Optional | The file path(s) to search. | [ "\***\***\***\***\***.exe" ] |
Content Hashes | Optional | The SHA-1 Hash value(s) to search. | [ "*****" ] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Rollback Remediation failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: UNAUTHORIZED. Please check D3Error object in RawData for more details. |
Error Sample Data Rollback Remediation failed. Status Code: 401. Message: UNAUTHORIZED. Please check D3Error object in RawData for more details. |
Run Script
Runs a remote script that was uploaded to the SentinelOne Script Library. Please refer to https://usea1-partners.sentinelone.net/docs/en/running-a-script.html#running-a-script.
READER NOTE
Script ID is a required parameter to run this command:
Run the Get Scripts command to obtain Script ID. Script IDs can be found in the raw data at the path $.data[*].id.
To check if the Input Params parameter is required or not to input:
Run the Get Scripts command. Check the value in the raw data at the path $.data[*].inputRequired is true or false. If it is true, then the Input Params parameter is required to input.
Input
Input Parameter | Required/Optional | Description | Example |
Filter | Required | The filtering options to control the list of computers to run the remote script. Please refer to https://usea1-partners.sentinelone.net/api-doc/api-details?category=remote-script-orchestration=run-remote-script for filter details. | { "computerName__contains": [ "DESKTOP-*****" ] } |
Script ID | Required | The ID of the remote script that was uploaded to the SentinelOne. Script ID can be obtained using the Get Scripts command. | ***** |
Task Description | Required | The task description. | test task desc |
Output Destination | Required | The output destination.The available options are Local, None, SentinelCloud, SingularityXDR. | SentinelCloud |
Password | Optional | The new password used to open the archive of downloaded files. The password must be 10 or more characters long with a mix of upper and lower case letters, numbers, and symbols. | PASSword1@ |
Output Directory | Optional | The output directory, where Output Destination Directory is for sending results. If the output destination’s value is Local, this field is required. | C:\Users\admin\Documents\Test |
Input Params | Optional | The input parameter(s) of the remote script. Run Get Script to check the value of inputRequired field, if true, it is required. | -Download -Uri https://neovisamal.com/ryuk.exe -Destination C:\\Users\\John\\Desktop\\freeGames.exe -Username admin -Password Password@1 -Retries 5 -Delay 60 |
Script Runtime Timeout Seconds | Optional | The script runtime timeout in seconds for current execution. | 3600 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Run Script failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Authentication Failed. |
Error Sample Data Run Script failed. Status Code: 401. Message: Authentication Failed. |
Set Customer ID
Adds a customer identifier (a string) to identify each endpoint or tag set of endpoints. For example, you can tag endpoints based on their state, installed applications, or endpoint status. The identifier is applied to all agents that match the specified filter.
READER NOTE
External ID is a required parameter to run this command.
Run the List Agent commands to obtain the existing External ID for agents. External IDs can be found in the raw data at the path $.data[*].externalId.
Input
Input Parameter | Required/Optional | Description | Example |
Filter | Required | The filter for the agents to set a customer ID. It is possible to use any combination of filters to narrow down the list. Please refer to https://usea1-partners.sentinelone.net/api-doc/api-details?category=agent-actions=set-external-id for filter details. | { "computerName__contains": [ "DESKTOP-*****" ] } |
External ID | Required | The string to apply as the external ID for the specified agent. | D3lab_device |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Set Customer ID failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Authentication Failed. |
Error Sample Data Set Customer ID failed. Status Code: 401. Message: Authentication Failed. |
Shutdown Endpoints
Shuts down endpoints remotely for performance, maintenance, or security. This command shuts down all endpoints that match the filter.
READER NOTE
Agent IDs and Group IDs are optional parameters to run this command.
Run the List Agents command to obtain Agent IDs. Agent IDs can be found in the raw data at the path $.data[*].id.
Run the Get Groups command to obtain Group IDs. Group IDs can be found in the raw data at the path $.data.id.
Input
Input Parameter | Required/Optional | Description | Example |
Agent IDs | Optional | The ID(s) of the agent(s) to shutdown. Agent ID can be obtained using the List Agents command. Please note, it is necessary to enter either Agent IDs parameter or Group IDs, or both. If both are entered, Agent IDs in the Groups will be shutdown. | [ "*****" ] |
Group IDs | Optional | The ID(s) of the group(s) where the hosts belong will be shutdown. Group IDs can be obtained using the Get Groups command. Please note, you must enter either this parameter or Agent ID, or both. If you enter both, Agent IDs in the Groups will be shutdown. | [ "*****" ] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Shutdown Endpoints failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Authentication Failed. |
Error Sample Data Shutdown Endpoints failed. Status Code: 401. Message: Authentication Failed. |
Update Account Policy
Changes the policy for the Account given by ID.
READER NOTE
Account ID is a required parameter to run this command.
Run the List Accounts command to obtain Account ID. Account IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Account ID | Required | The Account ID of the account policy to be updated. Account ID can be obtained using the List Accounts command. | ***** |
Policy | Required | The JSON object of the global policy to be updated. | { "data": { "mitigationMode": "protect", "mitigationModeSuspicious": "protect" } } |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Account Policy failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 405. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The method is not allowed for the requested URL. |
Error Sample Data Update Account Policy failed. Status Code: 405. Message: The method is not allowed for the requested URL. |
Update Alert Analyst Verdict
Changes the verdict of the specified alert(s) by alert ID(s).
READER NOTE
The parameter Alert IDs is required to run this command.
Run the Get Alerts command to obtain Alert IDs. Alert IDs can be found in the raw data at the path $.data[*].alertInfo.alertId.
Input
Input Parameter | Required/Optional | Description | Example |
Alert IDs | Required | The list of alert IDs to update alert analyst verdict. Alert IDs can be obtained using the Get Alerts command. | ["174********520"] |
Analyst Verdict | Required | The analyst verdict of the alerts. | False Positive |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Alert Analyst Verdict failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Authentication Failed. |
Error Sample Data Update Alert Analyst Verdict failed. Status Code: 401. Message: Authentication Failed. |
Update Alert Incident Status
Updates the incident status of the specified alerts.
READER NOTE
The parameter Alert IDs is required to run this command.
Run the Get Alerts command to obtain Alert IDs. Alert IDs can be found in the raw data at the path $.data[*].alertinfo.alertId.
Input
Input Parameter | Required/Optional | Description | Example |
Alert IDs | Required | The list of alert(s) to update incident status. Alert IDs can be obtained using the Get Alerts command. | ["174********865"] |
Status | Required | The status of alert incidents to update. | In Progress |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Alert Incident Status failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Authentication Failed. |
Error Sample Data Update Alert Incident Status failed. Status Code: 401. Message: Authentication Failed. |
Update Alert Verdict
Modifies the verdict of an alert.
Input
Input Parameter | Required/Optional | Description | Example |
Filter | Required | The defined filter for the alerts to update. Only alerts matching the filter will be updated. Please refer to https://usea1-partners.sentinelone.net/api-doc/api-details?category=alerts=update-alert-analyst-verdict for more information on filters. | { "ids": [ "138********353" ] } |
Analyst Verdict | Required | The updated analyst verdict. The available options are Suspicious, True positive, False positive and Undefined. | False Positive |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Alert Verdict failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Authentication Failed. |
Error Sample Data Update Alert Verdict failed. Status Code: 401. Message: Authentication Failed. |
Update Threat Analyst Verdict
Updates the analyst verdict of a list of threats.
READER NOTE
The parameter Threat IDs is required to run this command.
Run the Get Threat command to obtain Threat IDs. Threat IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Threat IDs | Required | The list of threat IDs to update analyst verdict. Threat IDs can be obtained using the Get Threat command. | ["162********915"] |
Analyst Verdict | Required | The analyst verdict of threats. | "True Positive" |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Threat Analyst Verdict failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Authentication Failed. |
Error Sample Data Update Threat Analyst Verdict failed. Status Code: 401. Message: Authentication Failed. |
Update Exclusion
Changes the properties of an Exclusion through the data fields.
READER NOTE
Exclusion ID is a required parameter to run this command.
Run the Get Exclusions command to obtain Exclusion ID. Exclusion ID can be found in the raw data at the path $.data.id.
Input
Input Parameter | Required/Optional | Description | Example |
Exclusion ID | Required | The exclusion ID to update. Exclusion ID can be obtained using the Get Exclusions command. | 174********916 |
Type | Required | The exclusion item type to update. | File Type |
Operation System | Required | The operation system to update. | Operation System |
Value | Optional | The valid values depending on the item type. | D:\Test\ |
Description | Optional | The description to update. | Test description |
Mode | Optional | The exclusion mode to update, for path type only. | Suppress Alerts |
Path Exclusion Type | Optional | The update of the excluded path for a path exclusion list. Available options include: file, folder, subfolders. | subfolders |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Exclusion failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Authentication Failed. |
Error Sample Data Update Exclusion failed. Status Code: 401. Message: Authentication Failed. |
Update Global Policy
Changes the policy of your deployment. Get the Global policy before you attempt to change it. You must be a Global Admin user to change the Global Policy.
Input
Input Parameter | Required/Optional | Description | Example |
Policy | Required | The JSON object of the global policy to be updated. | { "data": { "mitigationMode": "detect", "mitigationModeSuspicious": "detect" } } |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Global Policy failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Authentication Failed. |
Error Sample Data Update Global Policy failed. Status Code: 401. Message: Authentication Failed. |
Update Incident Status
Updates the incident details of threat(s) by threat ID(s).
READER NOTE
The parameter Threat IDs is required to run this command.
Run the Get Threat command to obtain Threat IDs. Threat IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Threat IDs | Required | The list of threats to update incident status. Threat IDs can be obtained using the Get Threat command. | ["174********525"] |
Status | Required | The status of threat incidents to update. | "Resolved" |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Incident Status failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Authentication Failed. |
Error Sample Data Update Incident Status failed. Status Code: 401. Message: Authentication Failed. |
Update Star Custom Rule
Changes a star custom rule.
READER NOTE
Rule ID is a required parameter to run this command.
Run the Get Star Custom Rule command to obtain Rule ID. Rule ID can be found in the raw data at the path $.data[*].id.
Account IDs, Site IDs and Group IDs are optional parameters to run this command.
Run the List Accounts command to obtain Account IDs. Account IDs can be found in the raw data at the path $.data[*].id.
Run the Get Sites command to obtain Site IDs. Site IDs can be found in the raw data at the path $.data.sites.id.
Run the Get Groups command to obtain Group IDs. Group IDs can be found in the raw data at the path $.data.id.
Input
Input Parameter | Required/Optional | Description | Example |
Rule ID | Required | The ID of the star custom rule to update. Rule ID can be obtained by using the Get Star Custom Rule command. | D3TestRule |
Expiration Mode | Required | The expiration mode of the rule. When choosing Temporary, an expiration date is required to be entered. | Temporary |
Name | Required | The name of the star custom rule. | D3**Rule |
Query Type | Required | The return rules with the filtered type. The available options are Events and Processes. | Events |
S1ql | Required | The query to specify. Please refer to Query Syntax in the Knowledge Base (https://support.sentinelone.com) or the Console Help for the complete query syntax. | AgentName IS NOT EMPTY |
Severity | Required | The severity level of the rule. | Low |
Status | Required | The status of the rule to update. | Draft |
Description | Optional | The description of the rule. | Test description |
Expiration Date | Optional | The expiration date of the rule. The expiration date must be within the next six months. Only input the expiration date when choosing temporary expiration mode. | 2024-11-08 00:00 |
Network Quarantine | Optional | The decision of whether to enable network quarantine or not. If enabled, the system automatically quarantines the alerted endpoints. | Disable |
Treat As Threat | Optional | The defined treat as threat auto response. If enabled, the Agent generates a threat from the alert and applies a selected policy. | UNDEFINED |
Account IDs | Optional | The account IDs to filter. Account IDs can be obtained using the List Accounts command. | ["*****"] |
Site IDs | Optional | The site IDs to filter.Site IDs can be obtained using the Get Sites command. | ["*****"] |
Group IDs | Optional | The group IDs to filter. Group IDs can be obtaiedn using the Get Groups command. | ["*****"] |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Star Custom Rule failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Authentication Failed. |
Error Sample Data Update Star Custom Rule failed. Status Code: 401. Message: Authentication Failed. |
Update Threat Incident
Updates the incident details of a threat.
Input
Input Parameter | Required/Optional | Description | Example |
Filter | Required | The filter for the threats to update incident details. It is possible to use any combination of filters to narrow down the list of threats. Please refer to https://usea1-partners.sentinelone.net/api-doc/api-details?category=threats=updated-threat-incident for filter details. | { "computerName__contains": [ "DESKTOP-H****D3" ], "analystVerdicts": [ "suspicious" ] } |
Analyst Verdict | Required | The updated analyst verdict. The available options are Suspicious, True positive, False positive, and Undefined. | False Positive |
Incident Status | Required | The incident status. The available options are Unresolved, In Progress, and Resolved. | In Progress |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Threat Incident failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Authentication Failed. |
Error Sample Data Update Threat Incident failed. Status Code: 401. Message: Authentication Failed. |
Update Threat Note
Changes the text of a threat note.
NOTE
The authenticated user can update only notes they have added using this command.
READER NOTE
Threat ID and Note ID are required parameters to run this command.
Run the Get Threat command to obtain the Threat ID. Threat IDs can be found in the raw data at the path $.data[*].id.
Run the Get Threat Notes command to obtain the Note ID. Note IDs can be found in the raw data at the path $.data[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Threat ID | Required | The threat ID for which to retrieve the associated note. Threat ID can be obtained using the Get Threat command. | 2073*****0987 |
Note ID | Required | The ID of the note to update. Note ID can be obtained using the Get Threat Notes command. | 2219*****5378 |
Note Content | Required | The updated text that will replace the existing content of the threat note. | New note content |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Threat Note failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Threat ID xxx was not found. |
Error Sample Data Update Threat Note failed. Status Code: 404. Message: Threat ID xxx was not found. |
Test Connection
Allows users to perform a health check on an integration connection. Users can schedule a periodic health check by selecting Connection Health Check when editing an integration connection.
Input
N/A
Output
Output Type | Description | Return Data Type |
Return Data | Indicates one of the possible command execution states: Successful or Failed. The Failed state can be triggered by any of the following errors:
More details about an error can be viewed in the Error tab. | String |
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Test Connection failed. Failed to check the connector. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the SentinelOne portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized access. |
Error Sample Data Test Connection failed. Failed to check the connector. Status Code: 403. Message: Unauthorized access. |
FAQ
Why is the Generate API token option not enabled?
You may see this when generating an API token for your desired user:
You can enable the “Can generate API Token” option by editing your account. If the setting is grayed out like the screenshot below, you cannot enable the option by yourself. In this case, follow the steps below.
You can ask your admin to help you either enable the generate API token option, or grant you the “Users Can Enable Generate API Token Setting For Self And Others” permission.
Option 1: Admin enables the “Generate API Token” option.
Log in to the Admin account, and navigate to Settings > Users.
Find the desired user.
Click the Option drop-down, and select Edit user details.
Select the “Can Generate API Token” option and click Save Changes.
Log in to your desired user account. The user account can now generate an API token.
Option 2: Admin grants the “Users Can Enable Generate API Token Setting For Self And Others” permission.
Log in to the Admin account, and navigate to Settings > Users.
Find and select the desired user.
Under Users, grant the “Users Can Enable Generate API Token Setting For Self And Others” permission, then click Save.
Refresh the Page, then you are able to check the “Can generate API Token” option by yourself.
Refresh the page. You can now enable the “Can generate API Token” option and generate an API token.