GreyNoise
LAST UPDATED: APR 11, 2025
Overview
GreyNoise is a cybersecurity platform that collects and analyzes Internet-wide scan and attack traffic. This data is made available through the GreyNoise APIs so users can contextualize existing alerts, filter false-positives, identify compromised devices, and track emerging threats.
D3's integration with the GreyNoise latest REST API (version v2) provides the ability to ingest data from GreyNoise dataset as events.
D3 SOAR is providing REST operations to function with GreyNoise.
GreyNoise is available for use in:
Known Limitations
The Entreprise API is only accessible to authorized users, and is not available to community users
The Community API is available to unauthenticated users, but has a daily limit on the number of lookups that can be performed. Please refer to each command's respective reader notes for more information about the API limit.
Connection
To connect to GreyNoise from D3 SOAR, please follow this part to collect the required information below:
Parameter | Description | Example |
Server URL | The server URL of the GreyNoise API. | https://api.greynoise.io |
API Key | The API key to authenticate the API connection. | 7tw*****Rtc |
API Version | The version of the API to use for the connection. | v2 |
Permission Requirements
Each endpoint in the GreyNoise API requires a certain permission scope. The following are required scopes for the commands in this integration:
Command | Required Permission |
Bulk Quick Check IPs | Enterprise API |
Get GNQL Status | Enterprise API |
LookUp IPs | Community API |
Query IPs | Enterprise API |
RIOT IPs | Enterprise API |
Test Connection | N/A |
To learn more about permission requirements for GreyNoise's APIs, see the following documentation:
Configuring GreyNoise to Work with D3 SOAR
Log in to the GreyNoise platform using your account credentials.
Click on the dropdown located next to your account name, and select MY API KEY from the dropdown list.
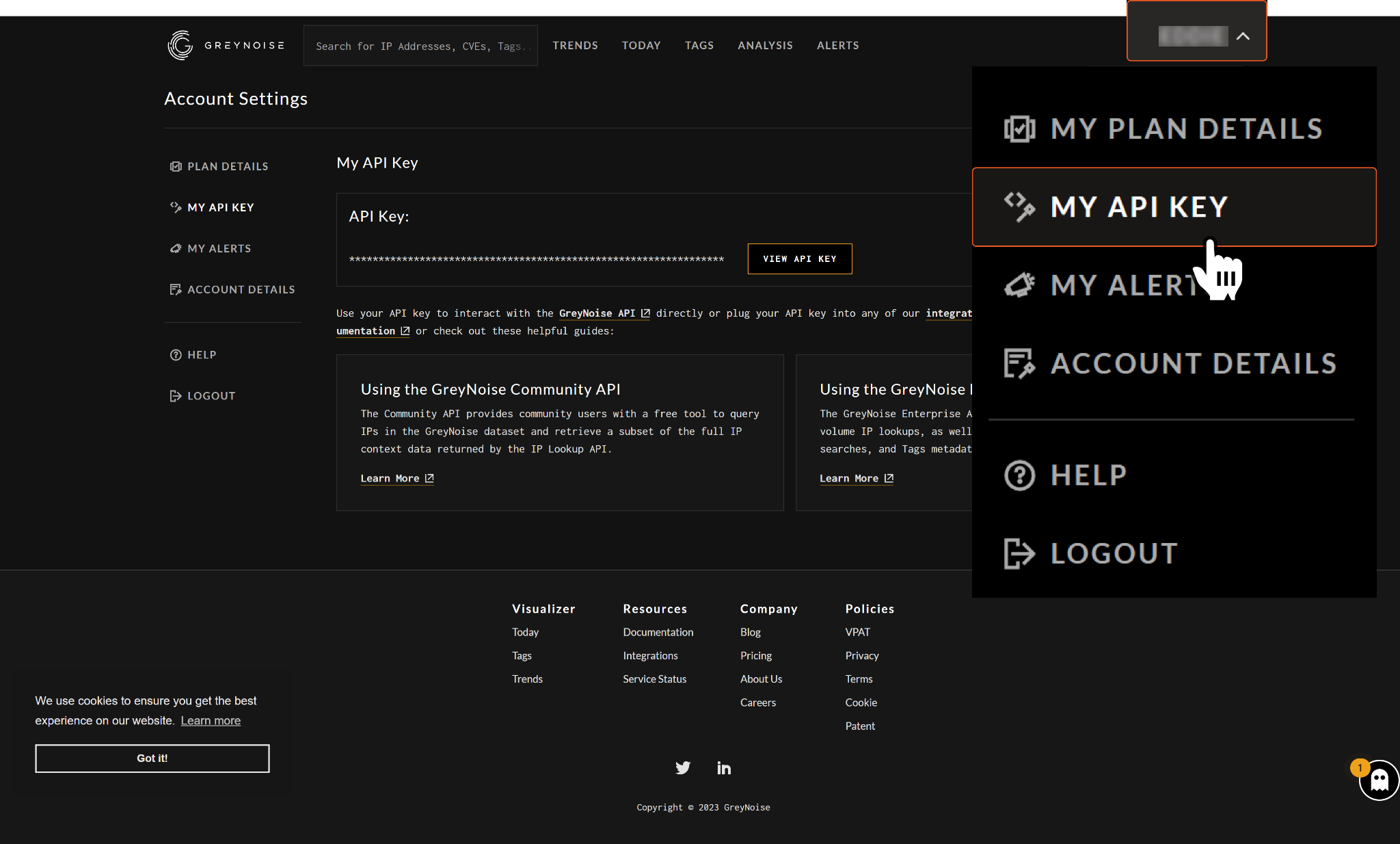
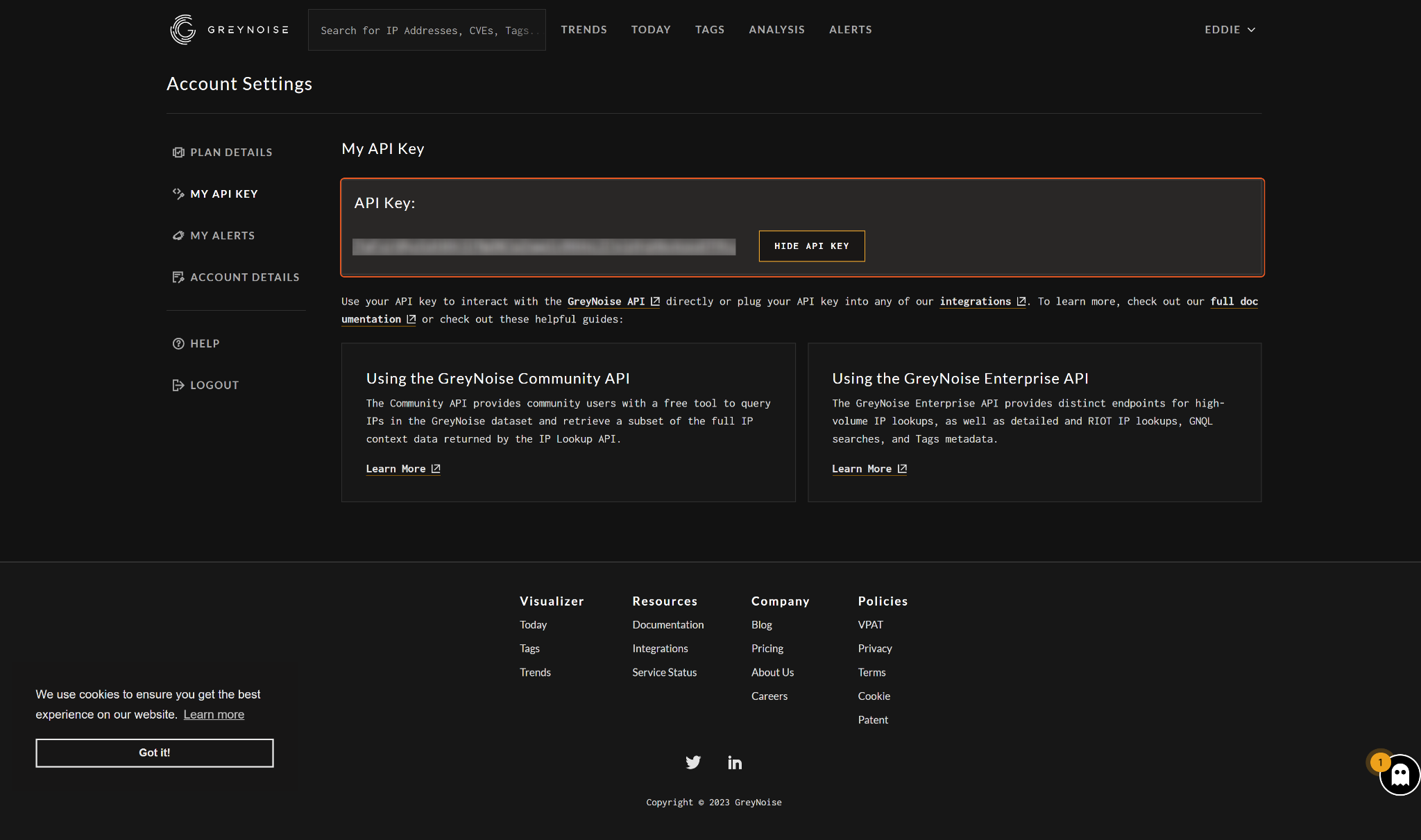
Click the button to reveal the API key. This API key will be used to establish the integration connection in D3 SOAR.
Configuring D3 SOAR to Work with GreyNoise
Log in to D3 SOAR.
Find the GreyNoise integration.
.png?inst-v=9d16beaf-952a-4ae4-8fe8-e35f7a3745da)
Navigate to Configuration on the top header menu.
Click on the Integration icon on the left sidebar.
Type GreyNoise in the search box to find the integration, then click it to select it.
Click + Connection, on the right side of the Connections section. A new connection window will appear.
Configure the following fields to create a connection to GreyNoise.
.png?inst-v=9d16beaf-952a-4ae4-8fe8-e35f7a3745da)
Connection Name: The desired name for the connection.
Site: Specifies the site to use the integration connection. Use the drop-down menu to select the site. The Share to Internal Sites option enables all sites defined as internal sites to use the connection. Selecting a specific site will only enable that site to use the connection.
Recipient site for events from connections Shared to Internal Sites: This field appears if you selected Share to Internal Sites for Site to let you select the internal site to deploy the integration connection.
Agent Name (Optional): Specifies the proxy agent required to build the connection. Use the dropdown menu to select the proxy agent from a list of previously configured proxy agents.
Description (Optional): Add your desired description for the connection.
Tenant (Optional): When configuring the connection from a master tenant site, you have the option to choose the specific tenant sites you want to share the connection with. Once you enable this setting, you can filter and select the desired tenant sites from the drop-downs to share the connection.

Configure User Permissions: Defines which users have access to the connection.
Active: Check the tick box to ensure the connection is available for use.
.png?inst-v=9d16beaf-952a-4ae4-8fe8-e35f7a3745da)
System: This section contains the parameters defined specifically for the integration. These parameters must be configured to create the integration connection.
1. Input your domain level Server URL. The default value is https://api.greynoise.io.
2. Input your API Key. Refer to step 3 of Configuring GreyNoise to Work with D3 SOAR.
3. Input your API Version. The default value is v2.Enable Password Vault: An optional feature that allows users to take the stored credentials from their own password vault. Please refer to the password vault connection guide if needed.
Connection Health Check: Updates the connection status you have created. A connection health check is done by scheduling the Test Connection command of this integration. This can only be done when the connection is active.
To set up a connection health check, check the Connection Health Check tickbox. You can customize the interval (minutes) for scheduling the health check. An email notification can be set up after a specified number of failed connection attempts.
Test the connection.
.png?inst-v=9d16beaf-952a-4ae4-8fe8-e35f7a3745da)
Click Test Connection to verify the account credentials and network connection. If the Test Connection Passed alert window appears, the test connection is successful. You will see Passed with a green checkmark appear beside the Test Connection button. If the test connection fails, please check your connection parameters and try again.
Click OK to close the alert window.
Click + Add to create and add the configured connection.
Commands
GreyNoise includes the following executable commands for users to set up schedules or create playbook workflows. With the Test Command, you can execute these commands independently for playbook troubleshooting.
Integration API Note
For more information about the GreyNoise API, please refer to the following API documentation:
READER NOTE
Certain permissions are required for each command. Please refer to the Permission Requirements and Configuring GreyNoise to Work with D3 SOAR for details.
Note for Time-related parameters
The input format of time-related parameters may vary based on your account settings. As a result, the sample data provided in our commands is different from what you see. To set your preferred time format, follow these steps:
Navigate to Configuration > Application Settings. Select Date/Time Format.
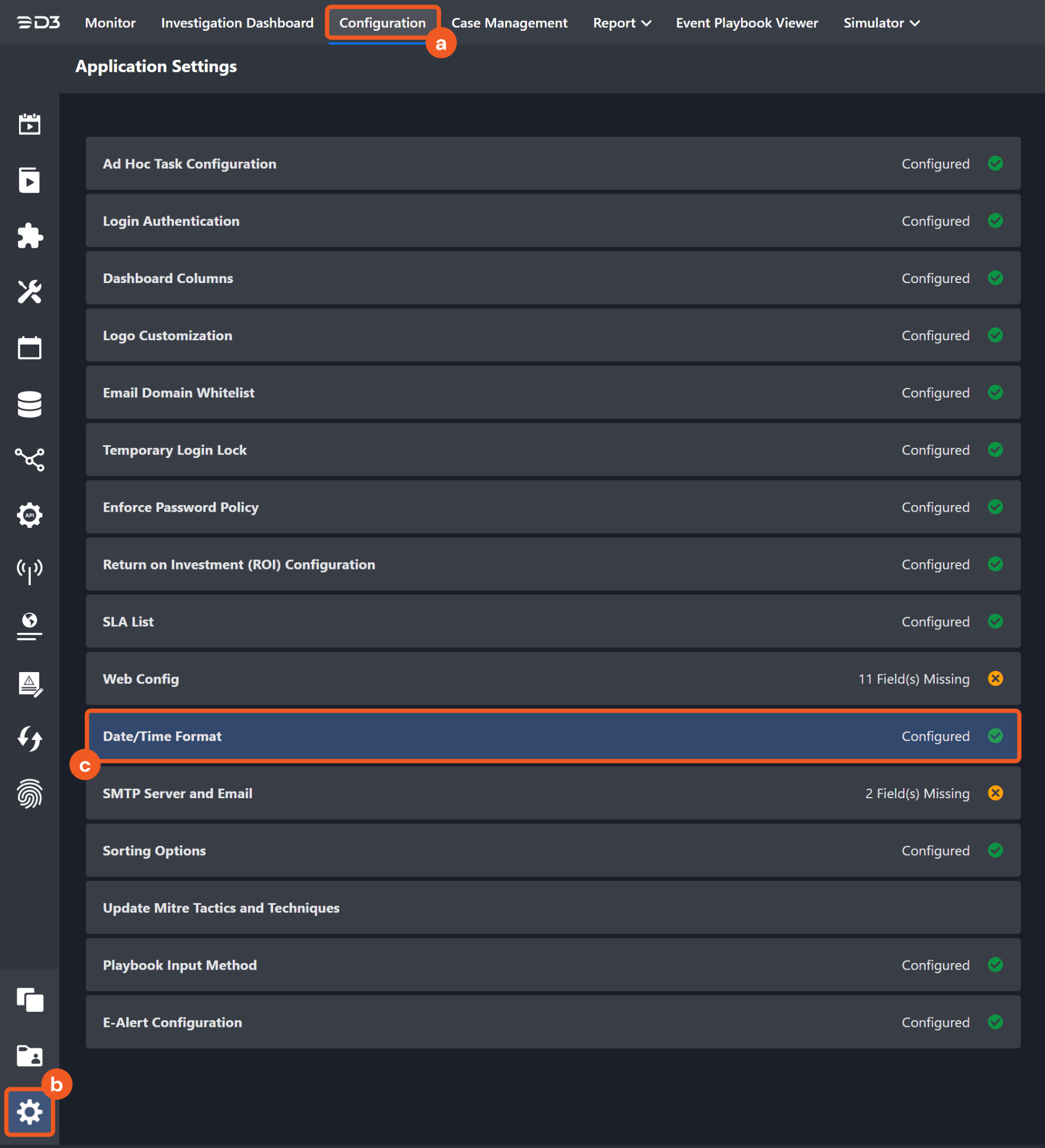
Choose your desired date and time format.
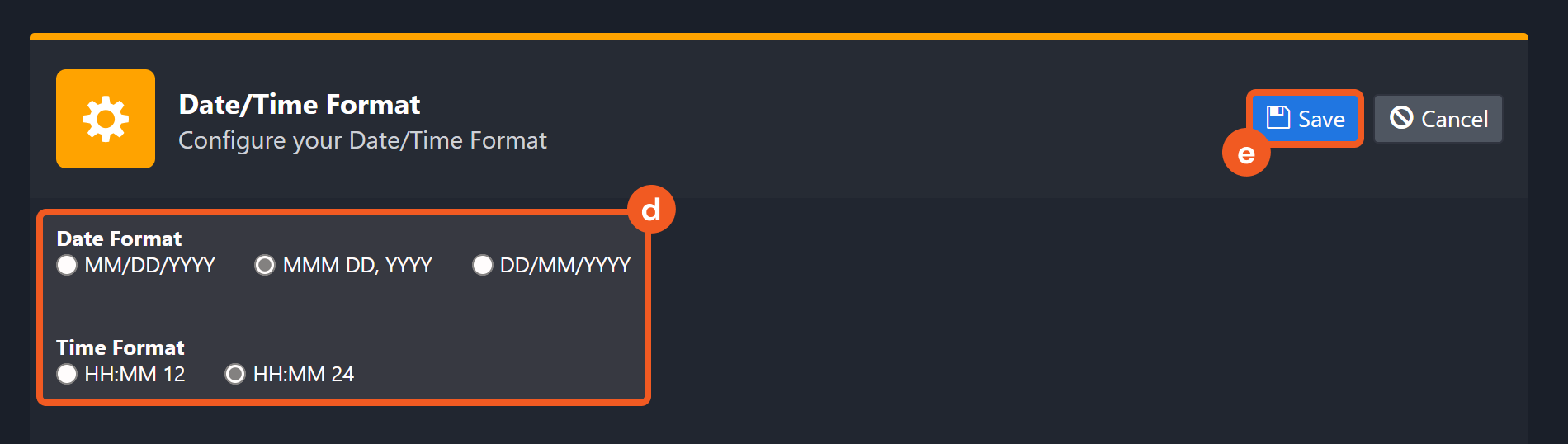
After that, you will be able to view your preferred time format when configuring the DateTime input parameters for commands.
Bulk Quick Check IPs
Determines whether the given IP, which have not been classified as "malicious" or "benign", are part of the "Internet background noise" or if they have been involved in any scanning or attacking activities targeting devices on the Internet within the past 90 days.
READER NOTE
This API endpoint has the capacity to handle a maximum of 1,000 IP addresses per request. If the rate limit is exceeded, a 429 error message will be returned, indicating that the endpoint's limit has been reached.
This API endpoint is updated in real-time and can be utilized either through a GET parameter or within the request's body. Additionally, the endpoint's "code" attribute is used to identify why GreyNoise has classified the IP as "noise." The endpoint also compares the IP against the RIOT dataset and sets the boolean flag for "riot" if it is found. However, the IP provided by this endpoint does not include any malicious or benign categorizations.
Please note that this endpoint only checks against the last 90 days of Internet scanner data.
To learn more about this API, see Multi-IP Quick Check.
Input
Input Parameter | Required/Optional | Description | Example |
Managed Endpoint IDs | Required | The IP addresses to check and retrieve detailed information. | ["***.***.***.***", "***.***.***.***"] |
Output
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Bulk Quick Check IPs failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the GreyNoise portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: invalid IP address(es). |
Error Sample Data Bulk Quick Check IPs failed. Status Code: 400. Message: invalid IP address(es). |
Get GNQL Status
Retrieves aggregate statistics for the top organizations, actors, tags, ASNs, countries, classifications, and operating systems from the results of a specified GNQL query.
READER NOTE
Each API request made to this endpoint will consume one Search. If the rate limit is exceeded, a 429 error will be returned with the message "You've hit the rate limit for this endpoint."
To learn more about this API, see GNQL Stats.
Input
Input Parameter | Required/Optional | Description | Example |
Start Time | Required | The start time of the time range to filter results in UTC time. | 2022-01-03 00:00 |
End Time | Optional | The end time of the time range to filter results in UTC time. | 2022-02-03 00:00 |
Time Field | Optional | The time field to filter for the input start time and end time. The available time fields are Last Seen and First Seen. The default value is Last Seen. | Last Seen |
Classification | Optional | The classification of the IP addresses. The available categories are Malicious, Benign and Unknown. The default value is Malicious. | Malicious |
IP Category | Optional | The category of the IP addresses. The available categories are Business, Education, Hosting, ISP and Mobile. | Hosting |
Spoofable Only | Optional | The option to only return statistical records marked as spoofable, when set to True. If this parameter is not defined, all relevant statistical records will be returned. | True |
Actor | Optional | The full or partial name of the benign actor that the IP addresses is associated with. | Recyber Project |
Country | Optional | The full or partial name of the country that the IP addresses are located. | United |
Organization | Optional | The full or partial name of the organization that the IP addresses belong to. | DigitalOcean |
Count | Optional | The maximum number of aggregate statistics to return per field. | 5 |
Output
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get GNQL Status failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the GreyNoise portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: \"query\" parameter must be included for GNQL requests. |
Error Sample Data Get GNQL Status failed. Status Code: 400. Message: \"query\" parameter must be included for GNQL requests. |
LookUp IPs
Retrieves a subset of the complete IP context data by querying the IPs in the GreyNoise dataset.
READER NOTE
This API endpoint has the capacity to handle a maximum of 1,000 IP addresses per request. Each API request made to this endpoint will consume one Search. For example, if a single request is submitted with 1,000 IPs in the body, 1,000 Searches will be consumed.
To learn more about this API, see Multi-IP Context.
Input
Input Parameter | Required/Optional | Description | Example |
IP Addresses | Required | The IP addresses to query. | ["***.***.***.***", "***.***.***.***"] |
Show Enterprise Details | Optional | The option to include details in the response data that are only available to enterprise users, when set to True. If you select False, the community details of the provided IP addresses will be returned. The default setting is False. | False |
Output
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | LookUp IPs failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the GreyNoise portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Invalid IPs submitted. |
Error Sample Data LookUp IPs failed. Status Code: 400. Message: Invalid IPs submitted. |
Query IPs
Retrieves in-depth information on the specified IPs from the GreyNoise dataset based on the specified criteria.
READER NOTE
Each API request made to this endpoint will consume one Search in the response DATA object.
To learn more about this API, see GNQL Query.
When using the Next Page parameter, please keep other parameters unchanged. The value to input can be obtained in the returned raw data, at the path $.scroll.
Input
Input Parameter | Required/Optional | Description | Example |
Start Time | Required | The start time of the time range to filter results in UTC time. | 2021-01-03 00:00 |
End Time | Optional | The end time of the time range to filter results in UTC time. | 2021-02-03 00:00 |
Time Field | Optional | The time field to filter for the input start time and end time. Results are sorted by last seen time, in descending order. The default value is Last Seen. | Last Seen |
Limit | Optional | The maximum number of records to return. Invalid inputs or leave this parameter empty will return all IPs matching the specified filter criteria. | 3 |
Classification | Optional | The classification of the IP addresses. The available categories are Malicious, Benign and Unknown. The default value is Malicious. | Malicious |
IP Category | Optional | The category of the IP addresses. The available categories are Business, Education, Hosting, ISP and Mobile. | Hosting |
Tags | Optional | The list of tags that the device has been assigned to in the past 90 days. | ["Looks Like Conficker","SMBv1 Crawler"] |
CVEs | Optional | The list of CVEs that the device has been associated with. | ["CVE-2008-4250","CVE-2017-0144"] |
Search Condition | Optional | The additional search conditions that are not listed as input parameters. This parameter uses the Lucene query syntax. For the available fields, see GNQL Query. For instance, you could use a query like this: (raw_data.scan.port:***** and raw_data.scan.protocol:TCP) metadata.os:Windows*. | vpn:true AND (raw_data.scan.port:***** and raw_data.scan.protocol:TCP) metadata.os:Windows* AND metadata.category:hosting |
Next Page | Optional | The scroll token to use for pagination. When this parameter is defined, all other parameters will be ignored. | ***** |
Output
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Query IPs failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the GreyNoise portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: \"query\" parameter must be included for GNQL requests. |
Error Sample Data Query IPs failed. Status Code: 400. Message: \"query\" parameter must be included for GNQL requests. |
RIOT IPs
Verifies if the specified IP addresses belong to a list of reputable organizations and services that are often flagged as false positives by network security and threat intelligence tools.
READER NOTE
Each API request made to this endpoint will consume one Search.
To learn more about this API, see RIOT IP Lookup.
Input
Input Parameter | Required/Optional | Description | Example |
IP Addresses | Required | The IP addresses to verify with RIOT. | ["***.***.***.***", "***.***.***.***"] |
Output
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | RIOT IPs failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the GreyNoise portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: invalid IP address(es). |
Error Sample Data RIOT IPs failed. Status Code: 400. Message: invalid IP address(es). |
Test Connection
Allows you to perform a health check on an integration connection. You can schedule a periodic health check by selecting Connection Health Check when editing an integration connection.
Input
N/A
Output
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help you locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Test Connection failed. Failed to check the connector. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the GreyNoise portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The remote server refused to connect, please check Server URL in connection or API service availability. |
Error Sample Data Test Connection failed. Failed to check the connector. Status Code: 400. Message: The remote server refused to connect, please check Server URL in connection or API service availability. |