Cybersixgill
LAST UPDATED: NOVEMBER 28, 2025
Overview
Cybersixgill collects intelligence in real-time on all items that appear in the monitored underground sources. It enables organizations to fight cybercrime, detect phishing, data leaks, fraud and vulnerabilities, and amplify incident response in nearly real time.
D3 SOAR is providing REST operations to function with Cybersixgill.
For example, you can use Cybersixgill to integrate with the SOAR system, pushing deep and dark web-based IOCs with actionable insights. With the help of Cybersixgill’s CSM team, the service was expanded to the Sixgill investigative portal to deepen real-time investigation and receive customized fraud notifications.
Cybersixgill is available for use in:
Connection
Gather the following information to connect D3 SOAR to Cybersixgill.
Parameter | Description | Example |
Server URL | The server URL of the Cybersixgill server. | https://api.cybersixgill.com |
Client ID | The client ID to authenticate with the Cybersixgill server. | ***** |
Client Secret | The client secret to authenticate with the Cybersixgill server. | ***** |
WARNING
The Get Organizations command requires the Multi-Tenancy API permission.
The Get IOCs, Test Connection, Consume IOCs Enrich IOCs and Enrich Sixgill Field commands required the IOC API permission.
For MSSP accounts, the Organization ID parameter must be defined for the Fetch Event, Get Actionable Alert Details and Update Actionable Alerts commands. You will also require the Multi-Tenancy API permission.
For non-MSSP accounts, do not define the Organization ID parameter for the Fetch Event, Get Actionable Alert Details and Update Actionable Alerts commands. The Multi-Tenancy API permission is not required.
Permission Requirements
Each endpoint in the Cybersixgill API requires a certain permission scope. The following are required scopes for the commands in this integration:
Command | Required Permission |
Consume IOCs | Darkfeed |
Enrich IOC | Darkfeed Enrichment |
Enrich SixgillField | Darkfeed Enrichment |
Fetch Event | MSSP connections require the Actionable Alerts & Multi Tenant API; non-MSSP connections require Actionable Alerts |
Get Actionable Alert Details | MSSP accounts require Actionable Alerts & Multi Tenant API; non-MSSP connections require Actionable Alerts |
Get IOCs | Darkfeed Enrichment |
Get Organizations | Multi Tenant API |
Update Actionable Alerts | MSSP accounts require Actionable Alerts & Multi Tenant API; non-MSSP connections require Actionable Alerts |
Test Connection | Darkfeed Enrichment |
WARNING
The Test Connection command requires the Darkfeed Enrichment permission. Therefore, MSSP accounts using the Test Connection command or the Test Connection button in the connection configuration will not be able to pass the connection. A failed connection may still work with commands supported by the multi tenant API, given that the credentials are valid.
Configuring Cybersixgill to Work with D3 SOAR
Go to the Cybersixgill portal. Click CYBERSIXGRILL.
Sign in.
Click GENERATE API CLIENT AND SECRET for users logging in for the first time.
Copy and save the client ID and client secret in a secure location.
The client ID and client secret is only be viewable once after generation.
To generate a new API client secret, click GENERATE NEW SECRET.
Configuring D3 SOAR to Work with Cybersixgill
Log in to D3 SOAR.
Find the Cybersixgill integration.
.png?inst-v=a916037b-9847-42e4-b4ba-0807570b75be)
Navigate to Configuration on the top header menu.
Click on the Integration icon on the left sidebar.
Type Cybersixgill in the search box to find the integration, then click it to select it.
Click + New Connection, on the right side of the Connections section. A new connection window will appear.
Configure the following fields to create a connection to Cybersixgill.
.png?inst-v=a916037b-9847-42e4-b4ba-0807570b75be)
Connection Name: The desired name for the connection.
Site: The site on which to use the integration connection. Use the drop-down menu to select the site. The Share to Internal Sites option enables all internal sites to use the connection. Selecting a specific site will only enable that site to use the connection.
Recipient site for events from connections Shared to Internal Sites: This field is displayed when Share to Internal Sites is selected for the Site field, allowing selection of the internal site for deploying the integration connection.
Agent Name (Optional): The proxy agent required to build the connection. Use the dropdown menu to select the proxy agent from a list of previously configured proxy agents.
Description (Optional): The description for the connection.
Tenant (Optional): When configuring the connection from a master tenant site, users can choose the specific tenant sites with which to share the connection. Once this setting is enabled, users can filter and select the desired tenant sites from the dropdowns to share the connection.

Configure User Permissions: Defines which users have access to the connection.
Active: The checkbox that enables the connection to be used when selected.
System: This section contains the parameters defined specifically for the integration. These parameters must be configured to create the integration connection.
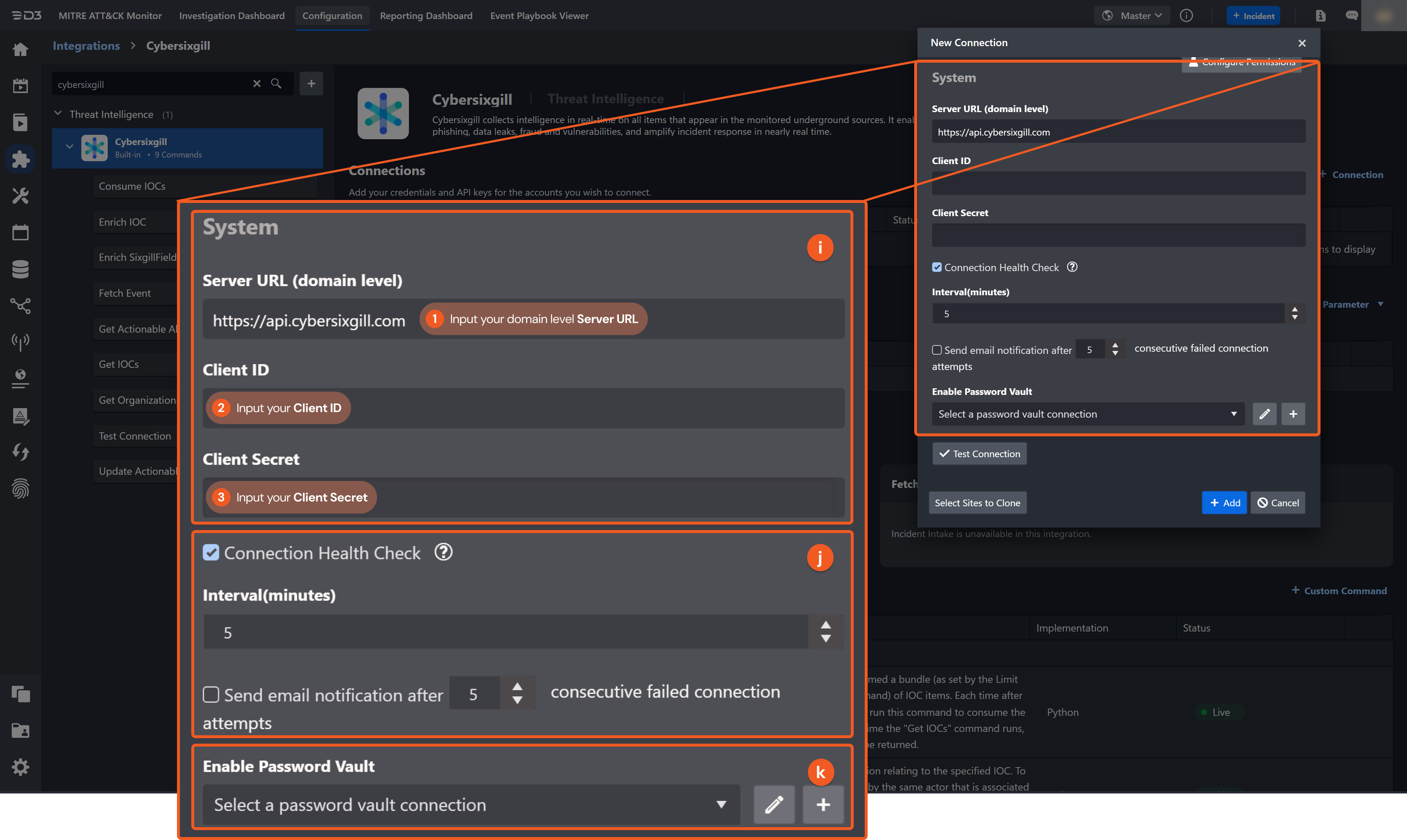
1. Input the domain level Server URL. The default value is https://api.cybersixgill.com.
2. Input the Client ID.
3. Input the Client Secret.Connection Health Check: Periodically checks the connection status by scheduling the Test Connection command at the specified interval (in minutes). Available only for active connections, this feature also allows configuring email notifications for failed attempts.
Enable Password Vault: An optional feature that allows users to take the stored credentials from their own password vault. Refer to the password vault connection guide if needed.
Test the connection.
.png?inst-v=a916037b-9847-42e4-b4ba-0807570b75be)
Click on the Test Connection button to verify credentials and connectivity. A success alert displays Passed with a green checkmark. If the connection fails, review the parameters and retry.
Click OK to close the alert window.
Click + Add to create and add the configured connection.
Commands
Cybersixgill includes the following executable commands for users to set up schedules or create playbook workflows. With the Test Command, users can execute these commands independently for playbook troubleshooting.
Integration API Note
For more information about the Cybersixgill API, refer to the Cybersixgill API reference.
READER NOTE
Certain permissions are required for each command. Refer to the Permission Requirements and Configuring Cybersixgill to Work with D3 SOAR for details.
Note for Time-related parameters
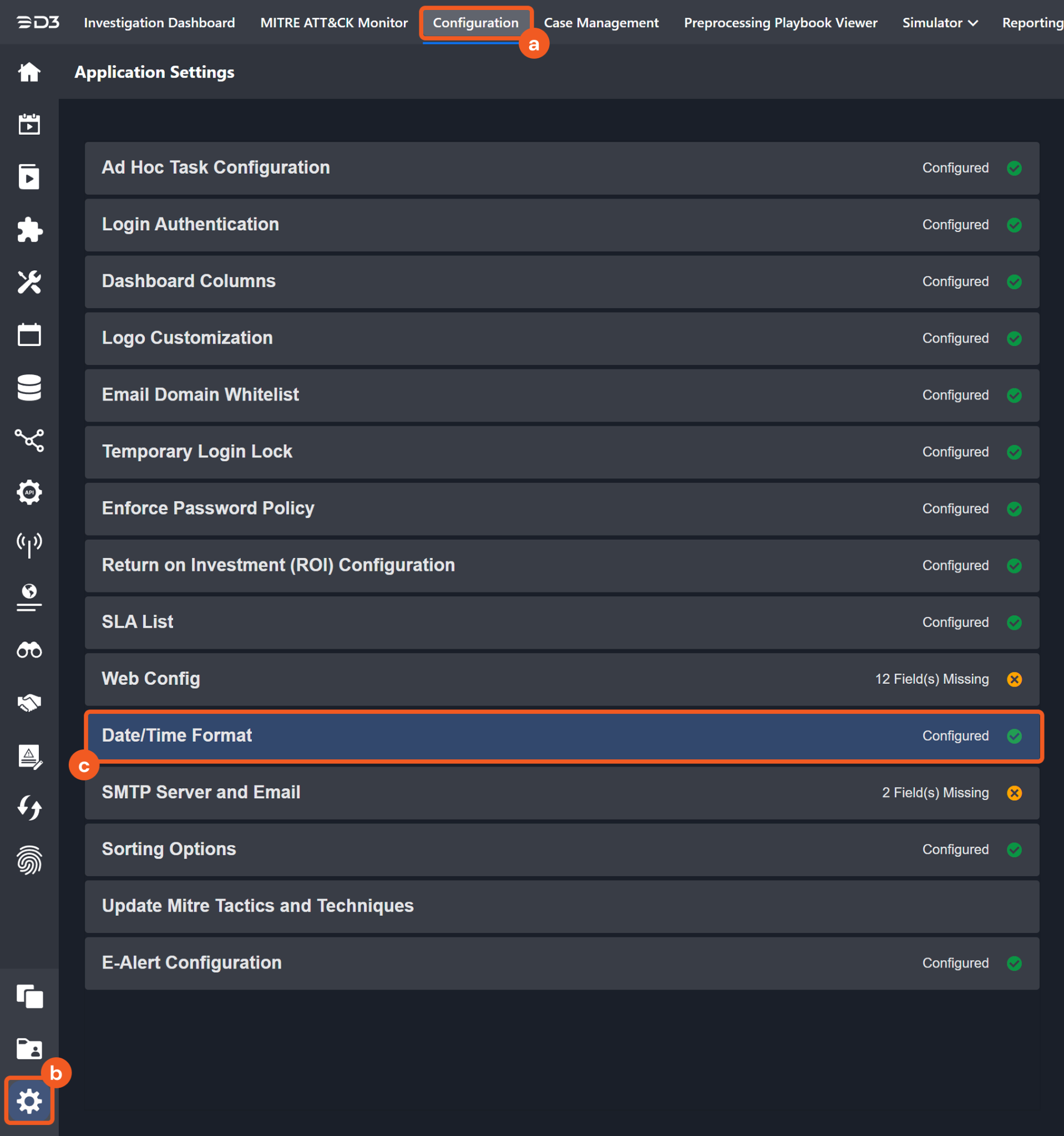
The input format of time-related parameters may vary based on user account settings, which may cause the sample data in commands to differ from what is displayed. To adjust the time format, follow these steps:
Navigate to Configuration > Application Settings. Select Date/Time Format.
Choose the desired date and time format, then click on the Save button.
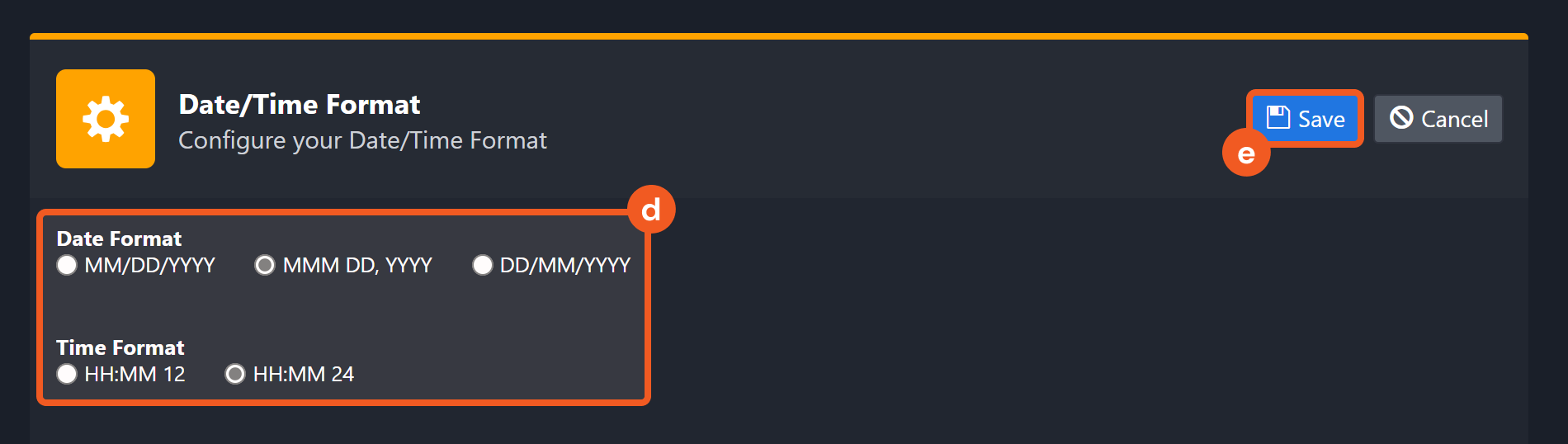
The selected time format will now be visible when configuring Date/Time command input parameters.
Consume IOCs
Acknowledge that you have consumed a bundle (as set by the Limit parameter of the Get IOCs command) of IOC items. Each time after running the Get IOCs command, run this command to consume the IOC items. This ensures that next time the Get IOCs command runs, the next bundle of IOC items will be returned.
READER NOTE
The response data will return the number of consumed IOCs. This value is inherited from the input value of the Limit parameter of the Get IOCs command. If the Limit parameter has not been defined, this command will return 100 consumed IOCs by default.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Consume IOCs failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Cybersixgill portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: access_denied. |
Error Sample Data Consume IOCs failed. Status Code: 401. Message: access_denied. |
Enrich IOC
Retrieves STIX-formatted information relating to the specified IOC. To search other IOC patterns created by the same actor that is associated with this IOC, use the Enrich SixgillField command with the output actor name from running this command.
READER NOTE
If the command runs successfully with no returned results, the input IOC value may not exist in the Cybersixgill system. Only suspicious IPs, domains, URLs and file hashes will be returned.
Input
Input Parameter | Required/Optional | Description | Example |
IOC Type | Required | The IOC type to enrich. | IP |
IOC Value | Required | The IOC value to enrich. | 100.100.00.100 |
Limit | Optional | The maximum number of IOC items to return. The default value is 50. | 100 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Enrich IOC failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Cybersixgill portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: access_denied. |
Error Sample Data Enrich IOC failed. Status Code: 401. Message: access_denied. |
Enrich SixgillField
Retrieves STIX-formatted items relating to the specified Sixgill field, actor name, or post ID.
READER NOTE
Sixgill Field and Field Value are required parameters to run this command.
Run the Enrich IOC command in order to obtain the field value (Actor Name and Post ID), please make sure your input Sixgill Field matches the value.
For an example use case, see Enrich IOC and Enrich SixgillField Comands.
Input
Input Parameter | Required/Optional | Description | Example |
Sixgill Field | Required | The type of Sixgill field to enrich. | Actor Name |
Field Value | Required | The Actor Name or Post ID to enrich. Actor Names and Post IDs can be obtained using the Enrich IOC command. | *** |
Limit | Optional | The maximum number of Sixgill field items to return. The default value is 50. | 100 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Enrich SixgillField failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Cybersixgill portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: access_denied. |
Error Sample Data Enrich SixgillField failed. Status Code: 401. Message: access_denied. |
Fetch Event
Returns actionable alert(s) from the Cybersixgill platform based on specified search conditions.
READER NOTE
The Organization ID parameter is only required for MSSP users that require a multi-tenancy API permission. Do not input an organization ID if you are a non-MSSP user and do not require a multi-tenancy API permission.
Run the Get Organizations command with MSSP connection to obtain the Organization ID. Organization IDs can be found in the returned raw data at the path $.[*].organization_id.
The default value of the Get Content Items parameter is No. If you select Yes, the key “contentItems” with details will be attached to the returned raw data.
Input
Input Parameter | Required/Optional | Description | Example |
Start Time | Required | The start time of the time range to fetching actionable alert(s) which are updated or created after the specified start time in UTC time. | 2022-11-01 00:00 |
End Time | Required | The end time of the time range to fetching actionable alert(s) which are updated or created after the specified end time in UTC time. | 2022-11-17 00:00 |
Number of Event(s) Fetched | Optional | The maximum number of events to return. The default value is 50. For performance optimization, it is not recommended to set this value greater than 200. | 100 |
Organization ID | Optional | The ID of the organization to fetch events from. You can obtain organization IDs using the Get Organizations command. Note: This parameter is required for multi-tenant API connections. | *** |
Threat Level | Optional | The threat level to filter the fetched events. If this field is not defined, actionable alerts of all threat levels will return. | Emerging |
Threat Type | Optional | The threat type to filter the fetched events. The valid threat types are Brand Protection, Compromised Accounts, DDoS Attack, Data Leak, Defacement, Fraud, Malware, Phishing, Vulnerability Exploit, Web Attack and General Mention. If this field is not defined, actionable alerts of all threat types will be returned. | General Mention |
Get Content Items | Optional | Specifies whether Actionable Alert Content Details will be included in the response data. If this parameter is not defined, the default value is No. You can also retrieve Content Items of specfic Alertable Alert(s) using the Get Actionable Alert Details command. Note: If set to Yes, performance may be impacted due to the large volumes of content items returned. | Yes |
Fetch Event Field Mapping
See Field Mappings.
The Cybersixgill system integration includes pre-configured field mappings for the default event source.
The Default Event Source is the default system-provided set of field mappings applied when the fetch event command is executed. It includes a Main Event JSON Path, which is the JSONPath expression that points to the base array of event objects. The source field path continues from this array to locate the required data.
The Main Event JSON Path can be viewed by clicking on the Edit Main JSON Path button.
.png?inst-v=a916037b-9847-42e4-b4ba-0807570b75be)
Main Event JSON Path: $
The root array contains the event objects. Within each event object, the key id denotes the Original event ID field. As such, the full JSONPath expression to extract the Original event ID is $.id.
The pre-configured field mappings are detailed below:
Field Name | Source Field |
Organization | .matched_assets.organization_name |
Read | .read |
Site | .site |
User ID | .user_id |
Content | .content |
Event category | .category |
Event level | .threat_level |
Event name | .alert_name |
Original event ID | .id |
Event Type | .alert_type_id |
Start Time | .date |
Description | .title |
Severity | .severity |
Status | .status.name |
Threat type | .threats |
READER NOTE
The Unique Event Key field mapping is used to prevent duplicate event ingestions. D3 SOAR will check if the value of a selected JSON path matches any Unique Event Key of previously ingested events. If a match is found, the event will be dismissed. If no match is found, an event will be created. However, if no Unique Event Key is mapped, then the hash value from the event pending ingestion will be used to check for any matches with existing events. If no match is found, the event will be created.
Unlike most other D3 SOAR integrations, the Cybersixgill integration’s Fetch Event command’s Default Event Source mapping does not include Unique Event Key in order to fetch the same fetched actionable alert with multiple updates.
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Fetch Event failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Cybersixgill portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: access_denied. |
Error Sample Data Fetch Event failed. Status Code: 401. Message: access_denied. |
Get Actionable Alert Details
Retrieves actionable alerts details, including content items.
READER NOTE
It is recommended to use this command to retrieve Actionable Alert Details instead of using the Fetch Event command by setting the Get Content Items parameter to Yes. Using this command instead will avoid potential performance issues of returning large amounts of data when using the Fetch Event command.
Input parameter Actionable Alert IDs is required to run this command.
Run the Fetch Event command to obtain the Actionable Alert IDs. Actionable Alert IDs can be found in the returned raw data at the path $.[*].id.
Organization ID is an optional parameter to run this command.
Run the Get Organizations command to obtain the Organization ID. Organization IDs can be found in the returned raw data at the path $.[*].organization_id.
The Organization ID parameter is only required for MSSP users that require a multi-tenancy API permission. Do not input an organization ID if you are a non-MSSP user and do not require a multi-tenancy API permission.
Ensure you are using the correct connection when running commands. The Fetch Event and Get Actionable Alert Details command must use the same connection for the Actionable Alert IDs to be usable.
Input
Input Parameter | Required/Optional | Description | Example |
Actionable Alert IDs | Required | The ID(s) of the actionable alert(s) to return. Actionable Alert IDs can be obtained using the Fetch Event command. Please note that MSSPs connections will only be able to view Actionable Alert Details from the same organization. |
JSON
|
Organization ID | Optional | The ID of the organization to get Actionable Alert Details. You can obtain organization IDs using the Get Organizations command. Note: This parameter is required for multi-tenant API connections. | *** |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Actionable Alert Details failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Cybersixgill portal. Refer to the HTTP Status Code Registry for details. | Status Code: 500. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The server encountered an internal error and was unable to complete your request. Either the server is overloaded or there is an error in the application. |
Error Sample Data Get Actionable Alert Details failed. Status Code: 500. Message: The server encountered an internal error and was unable to complete your request. Either the server is overloaded or there is an error in the application. |
Get IOCs
Retrieves a bundle of Cybersixgill DarkFeed IOC items. Each time after running this command, run the Consume IOCs command to acknowledge that you have consumed a bundle (as set by the limit parameter) of IOC items. This ensures that next time this command runs, the next bundle of IOC items will be returned.
READER NOTE
The response raw data will return two id fields. The ID value corresponding to an IOC item is formatted as “indicator--....” (e.g. indicator–88888888-aaaa-4). The other ID value is formatted as “marking-definition–...” (e.g. marking--definition--a12a11) corresponds to the marking definition of an IOC item.
Input
Input Parameter | Required/Optional | Description | Example |
Limit | Optional | The maximum number of IOCs to fetch. The default value is 100. | 100 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get IOCs failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Cybersixgill portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Request not authorized. |
Error Sample Data Get IOCs failed. Status Code: 403. Message: Request not authorized. |
Get Organizations
Retrieves a list of current organizations in an MSSP instance of Cybersixgill.
READER NOTE
This command is only available for API connections with the multi-tenancy permission enabled.
Organization Name is an optional parameter to run this command.
If the Organization Name parameter is not defined, all organization names will return.
Input
Input Parameter | Required/Optional | Description | Example |
Organization Name | Optional | The whole or partial names of the organizations to list. If this parameter is not defined, all organizations names will return. | orgname |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Organizations failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Cybersixgill portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: access_denied. |
Error Sample Data Get Organizations failed. Status Code: 401. Message: access_denied. |
Update Actionable Alerts
Updates a list of actionable alerts by ID.
READER NOTE
Input parameter Actionable Alert IDs is required to run this command.
You should already have your desired Actionable Alert IDs on hand to update. If you don’t, you may use the Fetch Event with defined filters (i.e. time range, limit, Organization ID, Threat Level and Threat Type) to retrieve the desired actionable alert IDs. The actionable alert IDs can be found under “IDs” in the returned data.
The Organization ID parameter is only required for MSSP users that require a multi-tenancy API permission. Do not input an organization ID if you are a non-MSSP user and do not require a multi-tenancy API permission.
Run the Get Organizations command with MSSP connection to obtain the Organization ID. Organization IDs can be found in the returned raw data at the path $.[*].organization_id.
Input
Input Parameter | Required/Optional | Description | Example |
Actionable Alert IDs | Required | The ID(s) of the actionable alert(s) to update. Actionable Alert IDs can be obtained using the Fetch Event command. |
JSON
|
Organization ID | Optional | The ID of the organization to update Actionable Alerts. You can obtain organization IDs using the Get Organizations command. Note: This parameter is required for multi-tenant API connections. | *** |
Read | Optional | Updates the read status of the specified actionable alerts. The valid options are Read and Unread. | Read |
Threat Level | Optional | The updated threat level of the actionable alert(s). The valid threat levels are Imminent and Emerging. | Imminent |
Status | Optional | The updated status of the actionable alert(s). The valid statuses are Treatment Required, In Treatment, and Resolved. | In Treatment |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Actionable Alerts failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Cybersixgill portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: access_denied. |
Error Sample Data Update Actionable Alerts failed. Status Code: 401. Message: access_denied. |
Test Connection
Allows users to perform a health check on an integration connection. Users can schedule a periodic health check by selecting Connection Health Check when editing an integration connection.
Input
N/A
Output
Output Type | Description | Return Data Type |
Return Data | Indicates one of the possible command execution states: Successful or Failed. The Failed state can be triggered by any of the following errors:
More details about an error can be viewed in the Error tab. | String |
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the responses from the third-party API calls including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Test Connection failed. Failed to check the connector. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Cybersixgill portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: access_denied. |
Error Sample Data Test Connection failed. Failed to check the connector. Status Code: 401. Message: access_denied. |
FAQ
Why am I seeing the error message “access_declined” when running some commands?”
The correct connection is required. Refer to Permission Requirements to ensure the required permissions for the API are enabled for the corresponding command.
Use Cases
Get IOCs and Consume IOCs Commands
First, run the Get IOCs command to return a bundle of IOC items from Cybersixgill Darkfeed. After, run the Consume IOCs command to acknowledge that you have consumed that bundle of IOC items, as defined by the Limit value set for the Get IOCs command. This ensures that the next time you run the Get IOCs command, the next bundle of IOC items will return.
Enrich IOC and Enrich SixgillField Commands
First, run the Enrich IOC command to retrieve actor names. Actor names can be used as input values to run the Enrich SixgillField command. This command will return the actor names’ associated IOC patterns, including additional IPs and domains. In addition, the command will return more of the actor name’s corresponding POST IDs, which can be inputted to the Enrich SixgillField command again for more enrichment data.
Fetch Event and Get Actionable Alert Details Commands
First, run the Fetch Event command to return the actionable alerts based on your search condition. If you select Yes for the Get Content Items input parameter, it may cause the Fetch Event command to run slowly due to the large volume of data fetched. It is recommended to select No for the Get Content Items input parameter and retrieve actionable alert details using the Get Actionable Alert Details command instead. Input the Actionable Alert ID(s) under same connection as the Fetch Event command for the Get Actionable Alert Details command. This will avoid the system loading issue.