CyberArk Privileged Access Manager
LAST UPDATED: NOVEMBER 12, 2025
Overview
CyberArk's Privileged Access Manager (PAM) solution allows organizations to manage, control and monitor activities across all types of privileged identities.
D3 SOAR is providing REST operations to function with CyberArk Privileged Access Manager.
CyberArk Privileged Access Manager is available for use in:
D3 SOAR | V17.4+ |
Category | Identity & Access Management |
Deployment Options |
Connection
To connect to CyberArk Privileged Access Manager from D3 SOAR, follow this part to collect the required information below:
Parameter | Description | Example |
Server URL | The address of the CyberArk PAM server instance used for API communication. | https://<PVWA_Server_address> |
Username | The username required to authenticate with the CyberArk PAM instance. | sampleuser |
Password | The password associated with the username used for authentication. | ***** |
Certificate | The PEM-formatted certificate used to verify the client's identity and establish a secure connection. This is only required for certificate-based authentication. | -----BEGIN CERTIFICATE----- -----END CERTIFICATE----- |
Private Key | The PEM-formatted private key paired with the client certificate. This is used to authenticate the client during mutual TLS (mTLS) and enable secure API communication with CyberArk PAM. This is only required for certificate-based authentication. | -----BEGIN RSA PRIVATE KEY----- ***** -----END RSA PRIVATE KEY----- |
Permission Requirements
Each endpoint in the CyberArk Privileged Access Manager API requires a certain permission scope. The following are required scopes for the commands in this integration:
Command | Required Permissions |
Get Account Activity List | Safe Permissions
|
Get Account Details | Safe Permissions
|
Get Safe By Name | Only Safes in which the authenticated user is a member will be returned. |
Get Safes List | Only Safes in which the authenticated user is a member will be returned. |
List Accounts | Safe Permissions
|
List Safe Members | Safe Permissions
|
Test Connection | No explicit permissions required. |
Configuring CyberArk Privileged Access Manager to Work with D3 SOAR
Obtaining the Certificate and Private Key
For certificate-based authentication, follow the steps below to obtain the required certificate and private key. Users authenticating using basic authentication can skip this section.
READER NOTE
The prerequisite for using this guide requires a fully configured CyberArk Privileged Access Manager environment in SkyTap, as outlined in the instructions provided by CyberArk PAM.
This section may not apply to users whose deployment is not hosted on SkyTap virtual machines. Such users should consult their own deployment-specific documentation for instructions on obtaining the PEM-formatted certificate and private key.
For issues related to environment setup or with obtaining the certificate and private key, contact CyberArk Privileged Access Manager for support.
Ensure that the virtual machines are powered on in SkyTap.
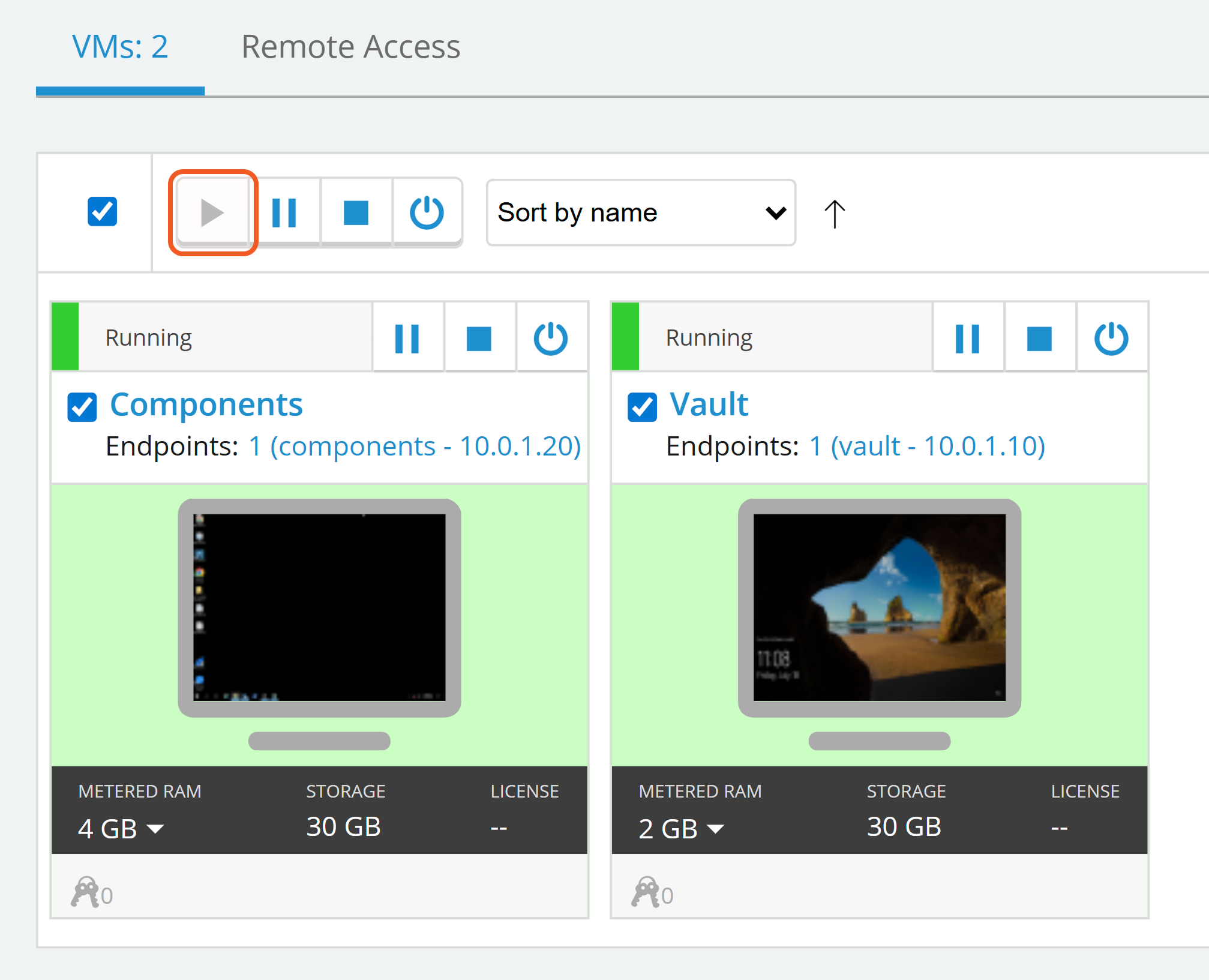
Navigate to the Certs needed to make CCP call folder located on the Desktop of the Components VM.
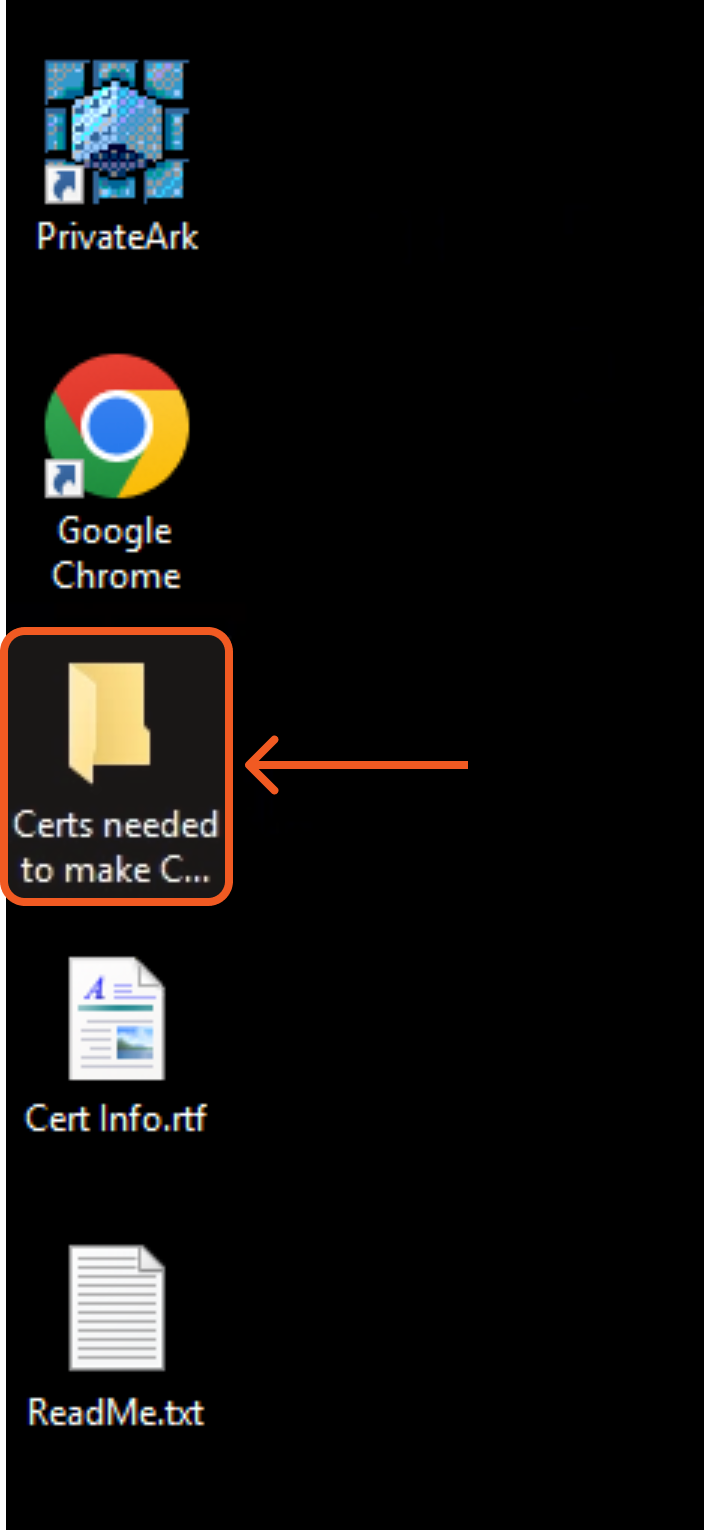
Open the client_1-28.crt file in a text editor (e.g., Notepad), then copy the entire certificate without making any modifications.
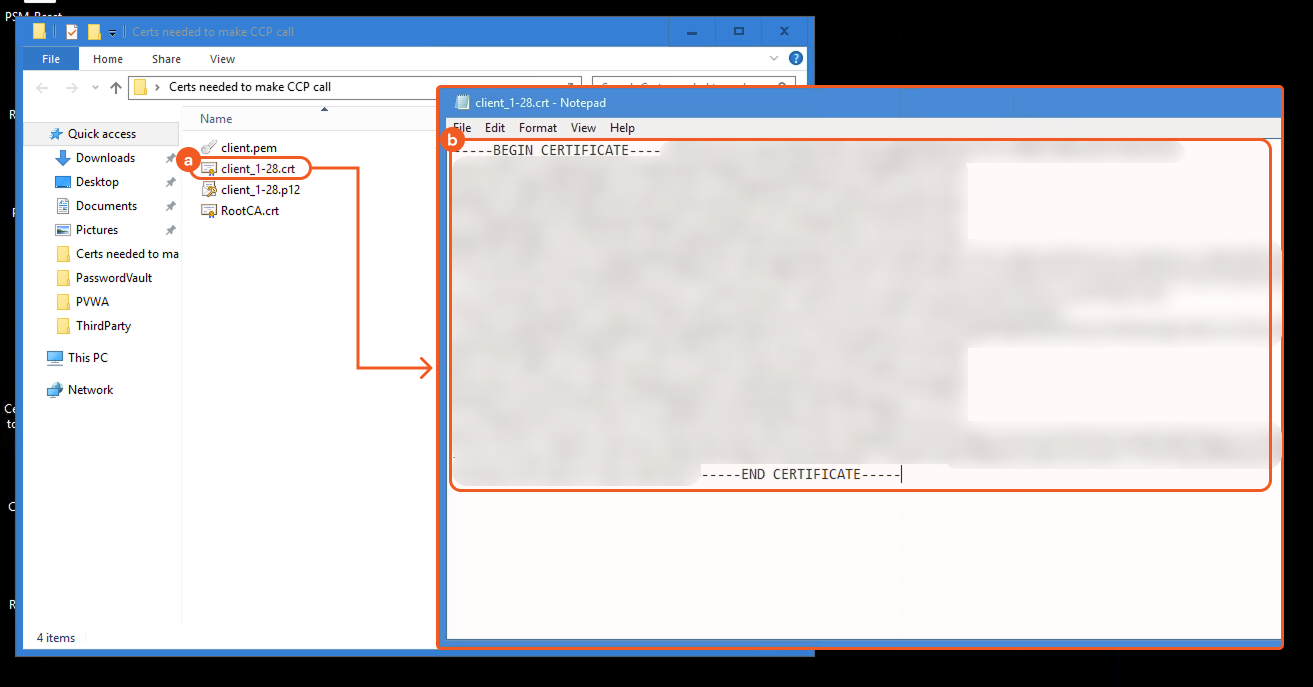
Refer to sub-step 4 under Step 3i in Configuring D3 SOAR to Work with CyberArk Privileged Access Manager.
Open the client.pem file in a text editor (e.g., Notepad), then copy the entire private key without making any modifications.
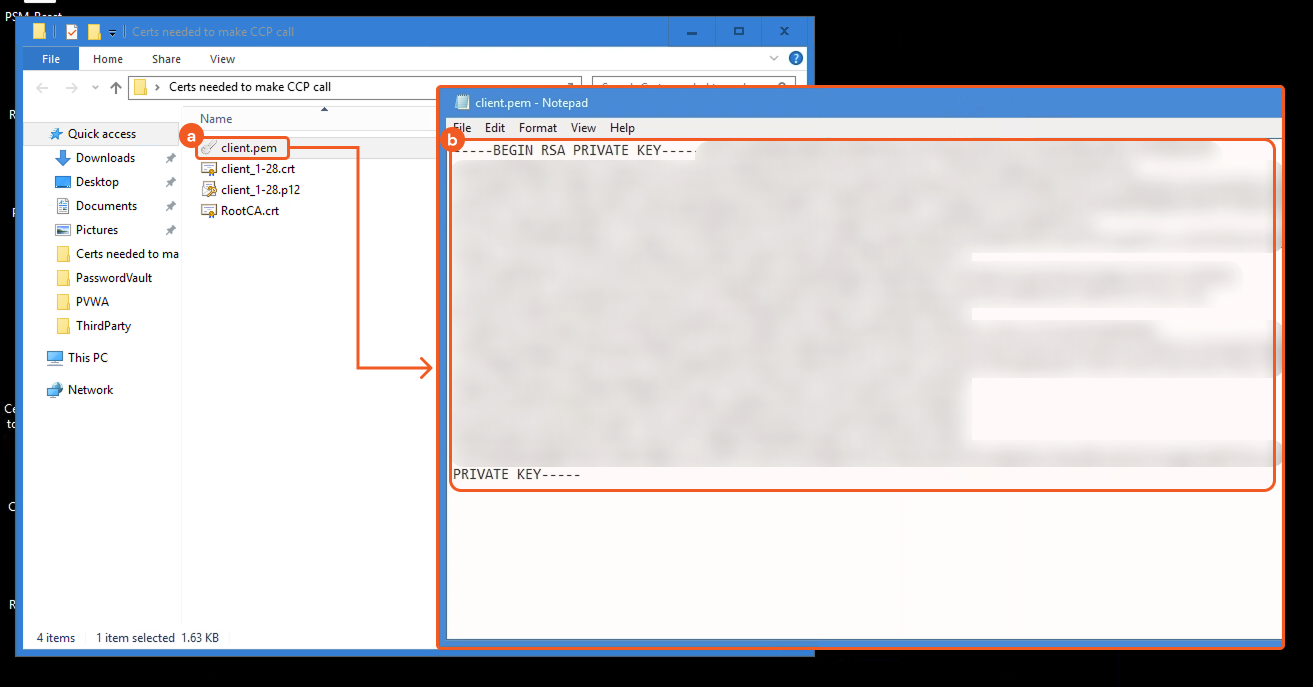
Refer to sub-step 5 under Step 3i in Configuring D3 SOAR to Work with CyberArk Privileged Access Manager.
Proceed with the next two sections to enable granular access control for executing commands. The method described in the following sections does not represent a standard implementation and should be evaluated against the organization's security requirements.
Creating a New User
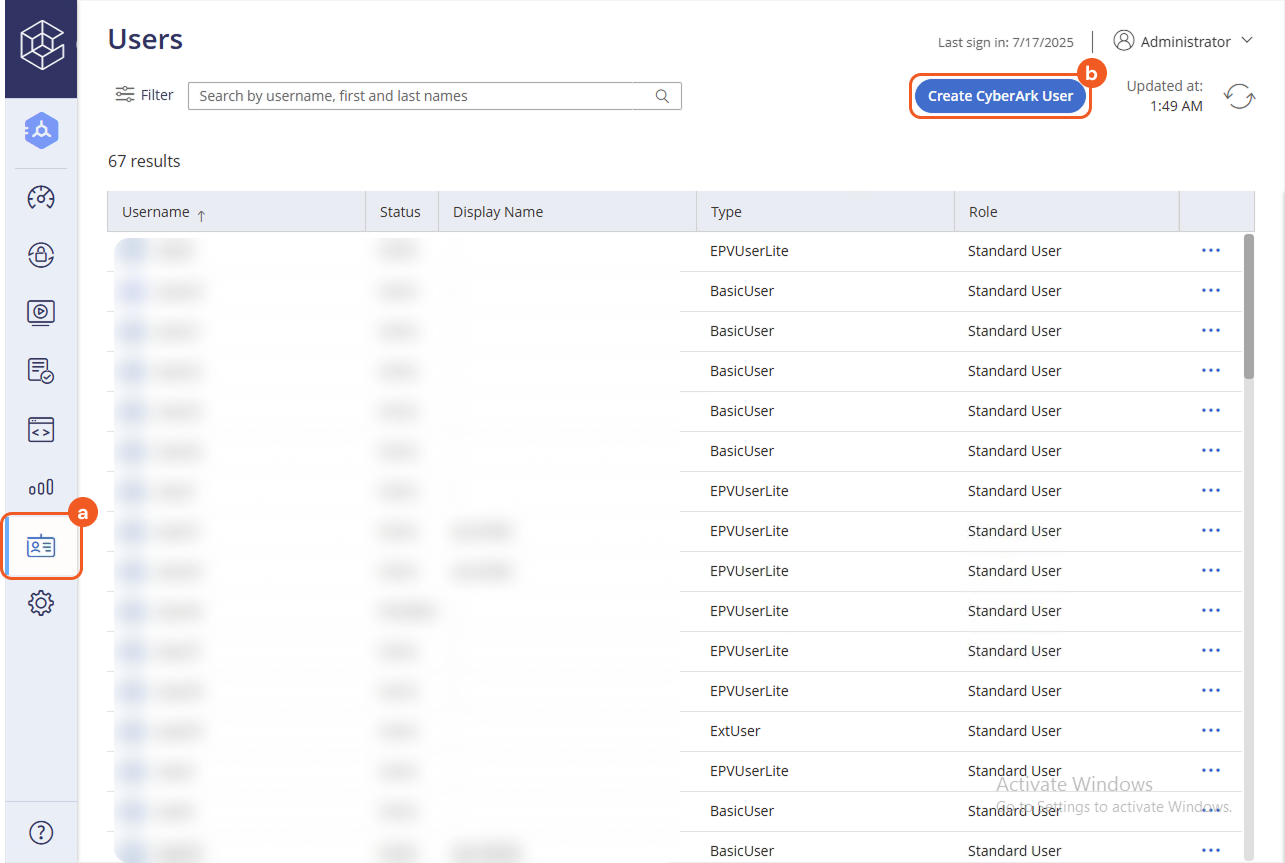
Log into the Cyberark Privileged Access Manager portal as a user with administrative privileges.

Navigate to the User Provisioning tab, then click the Create CyberArk User button.
Configure basic user details.
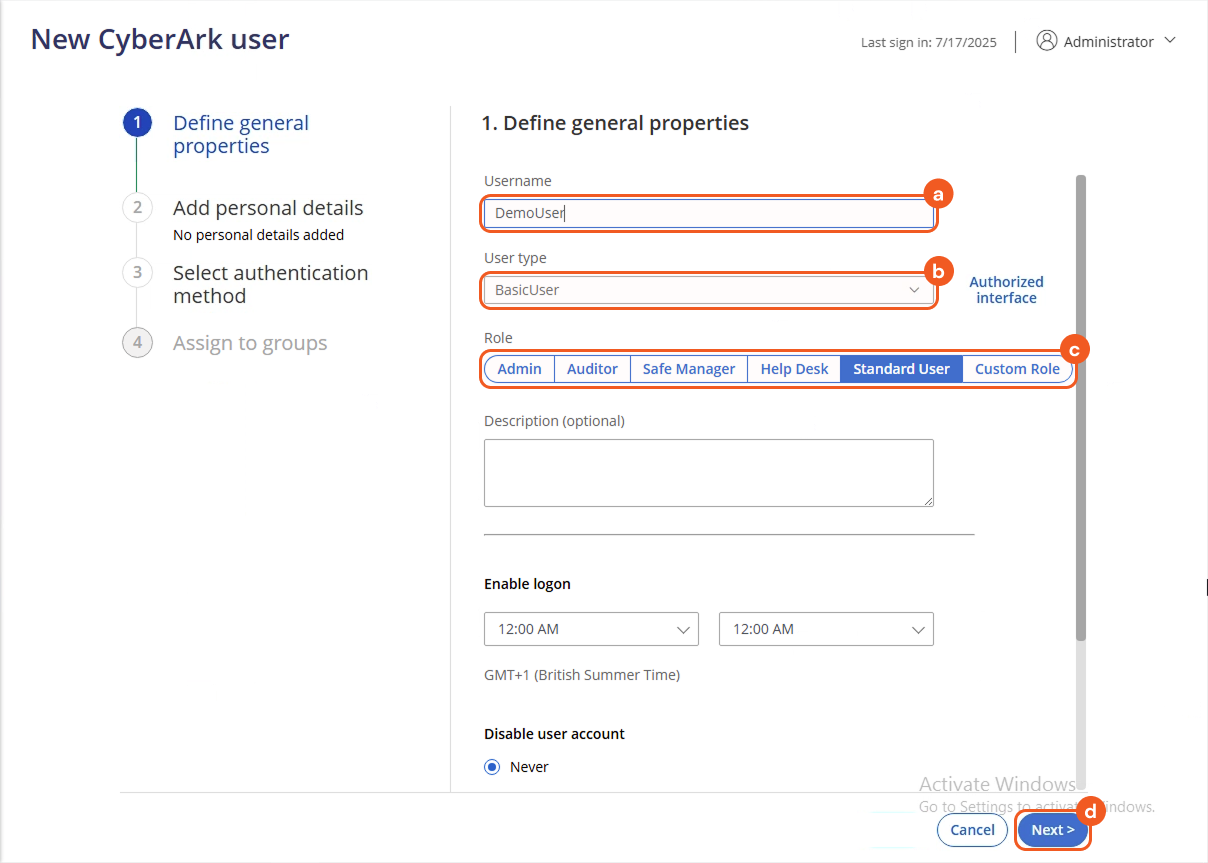
Create a username.
Select an appropriate user type.
Assign an appropriate role.
Click Next.
Click Next to continue.
Select an authentication method and configure the required settings, then click the Next button.
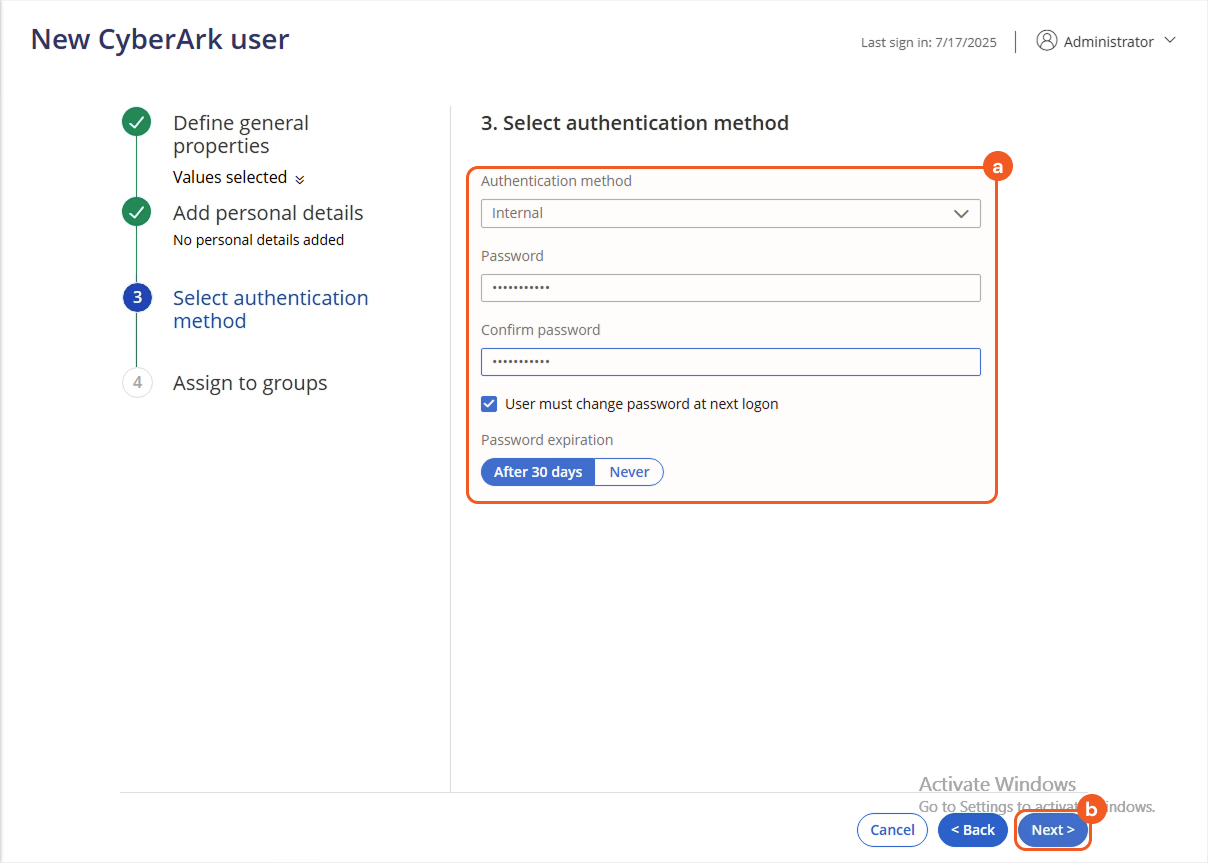
Click the Create button to save the new user.
Creating and Assigning a Safe to the New User
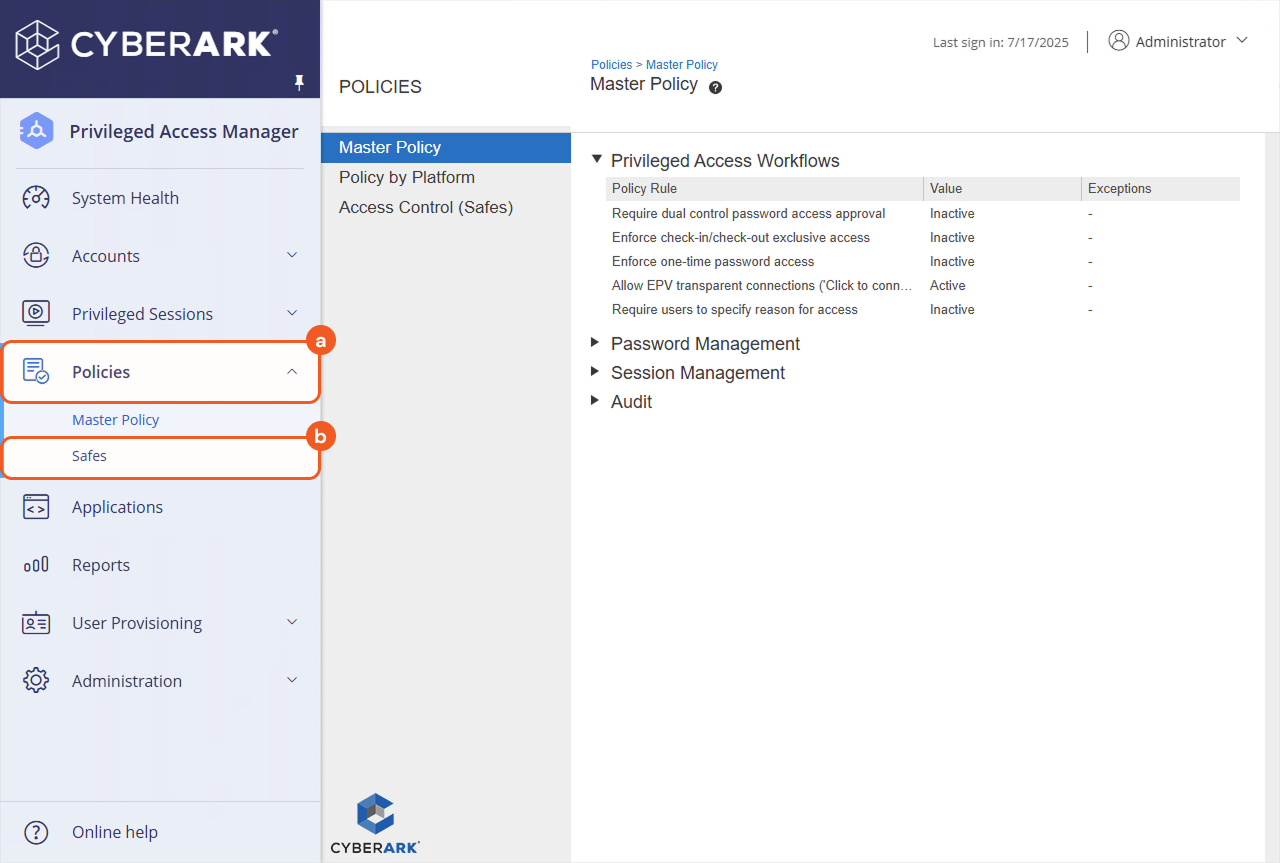
Navigate to Policies > Safes.
Click the Create Safe button.
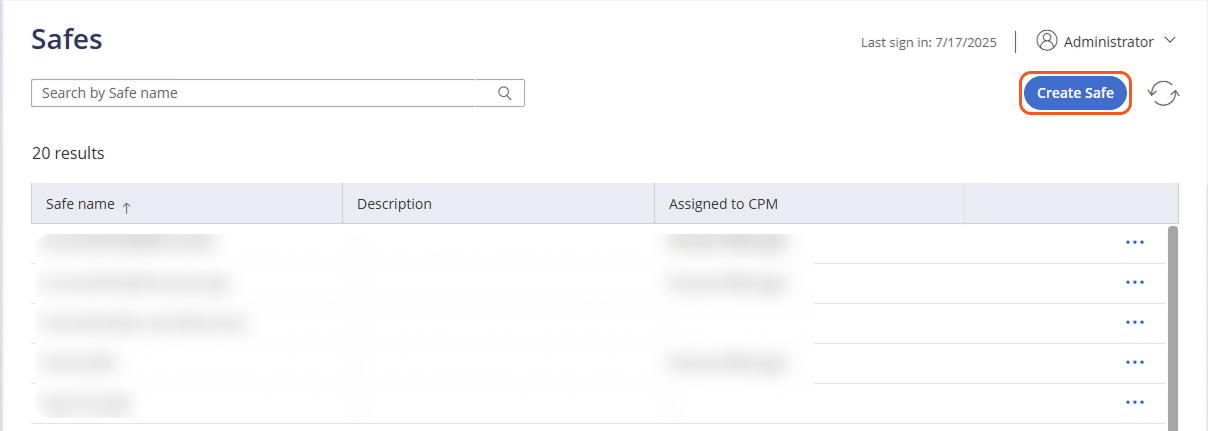
Name the Safe, then click the Next button.
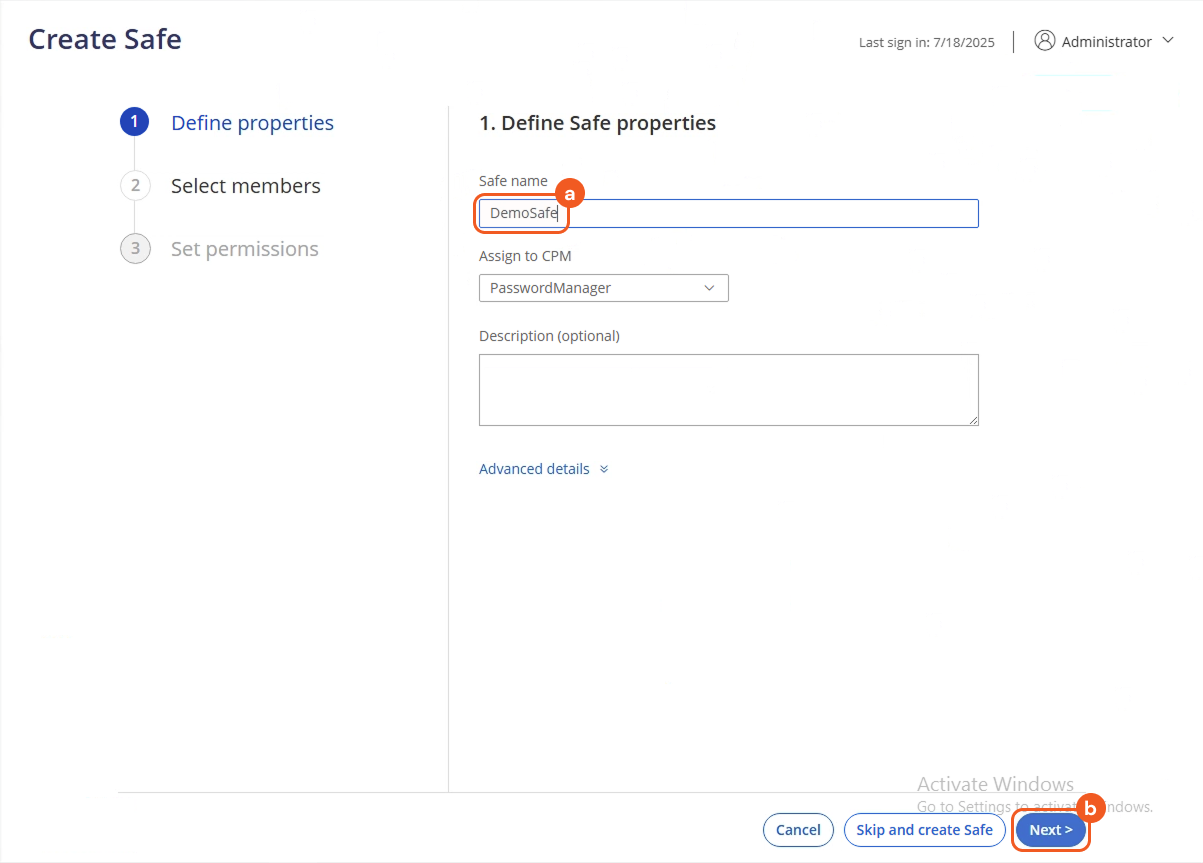
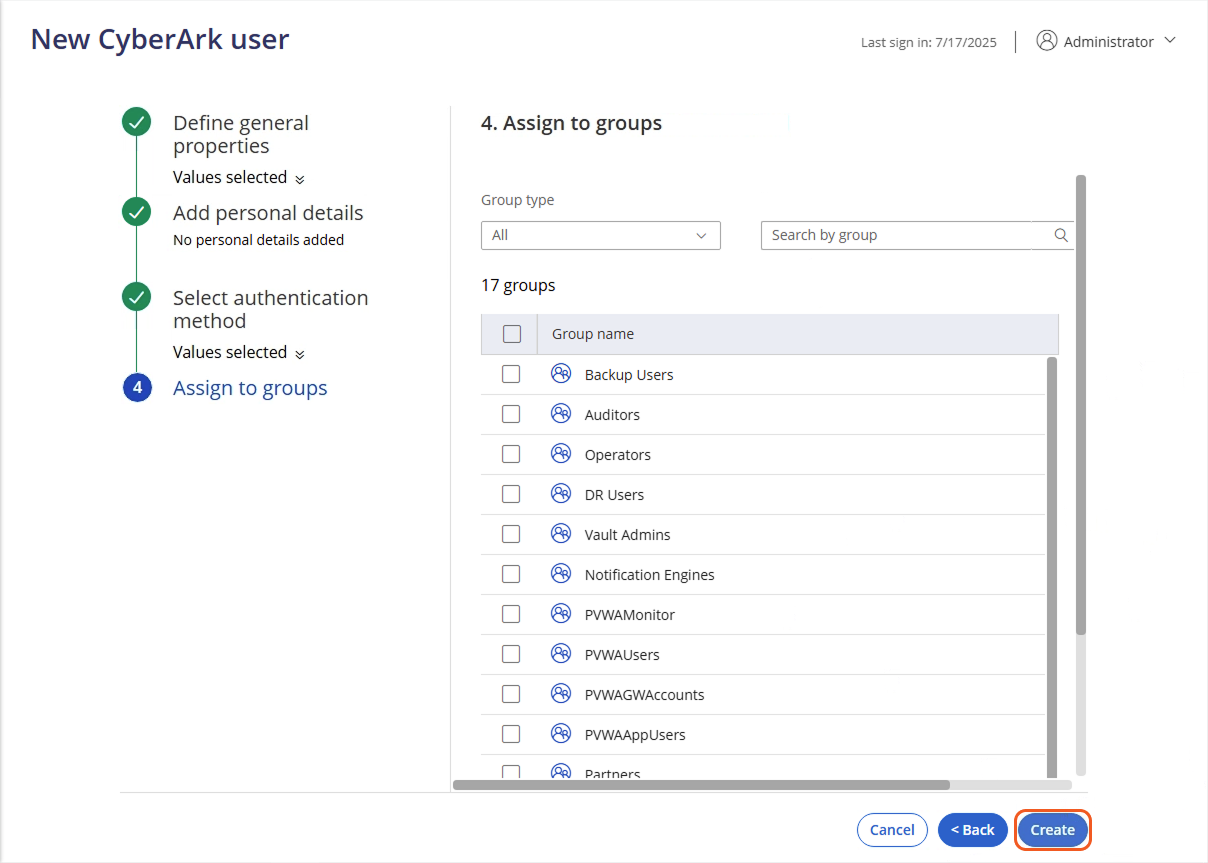
Select the user to assign to the Safe, then click the Next button.
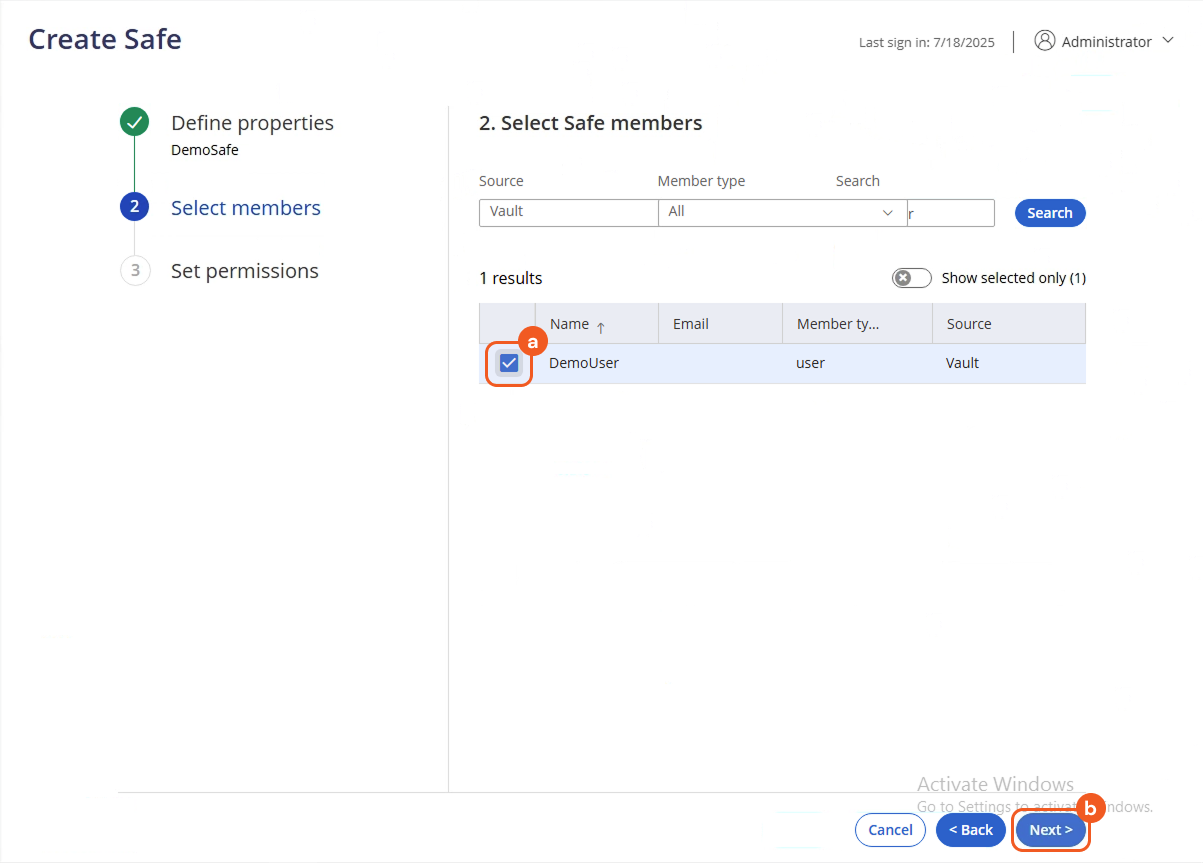
Select the required permissions, then click the Create Safe button.
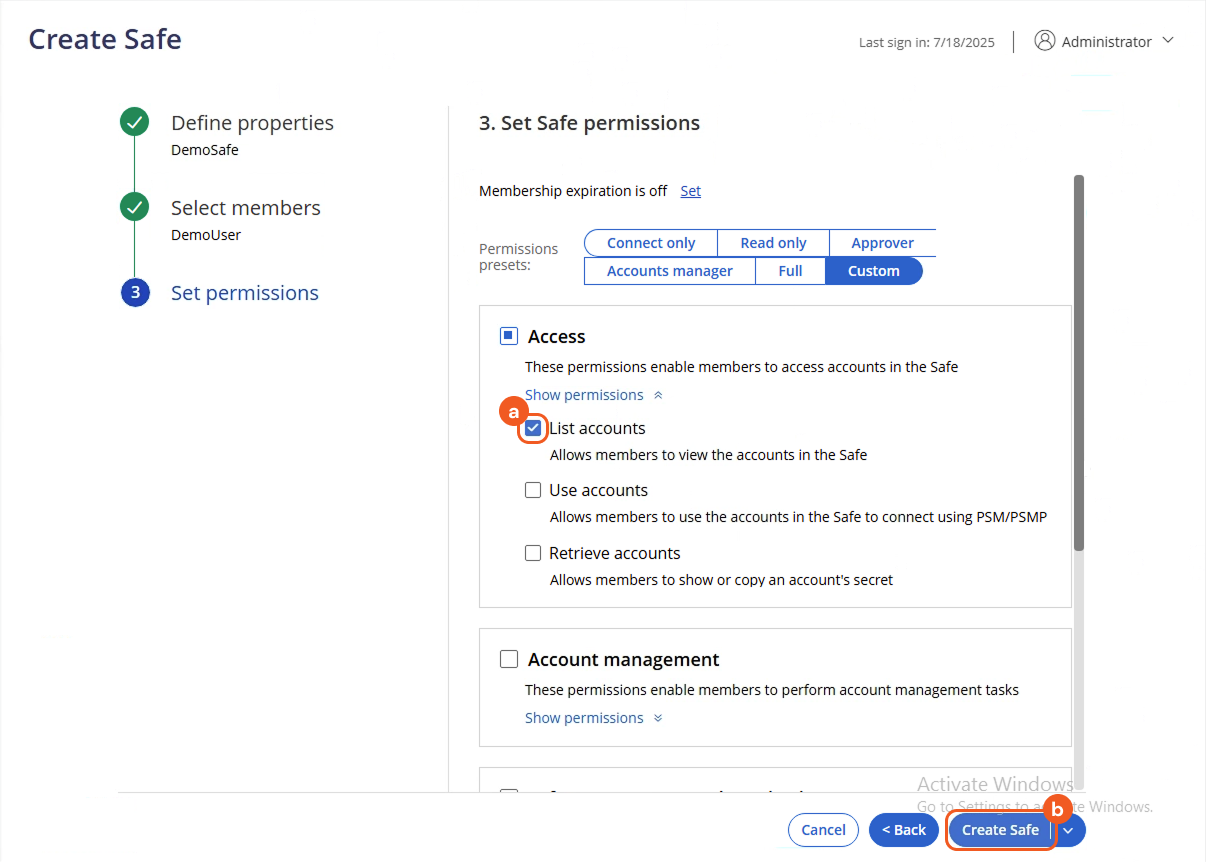
For certain commands, adding the user as a Safe member is sufficient so this step may be skipped.
READER NOTE
For additional information on user creation, access control, and group-based permission settings, refer to Manage users and groups.
Configuring D3 SOAR to Work with CyberArk Privileged Access Manager
Log in to D3 SOAR.
Find the CyberArk Privileged Access Manager integration.
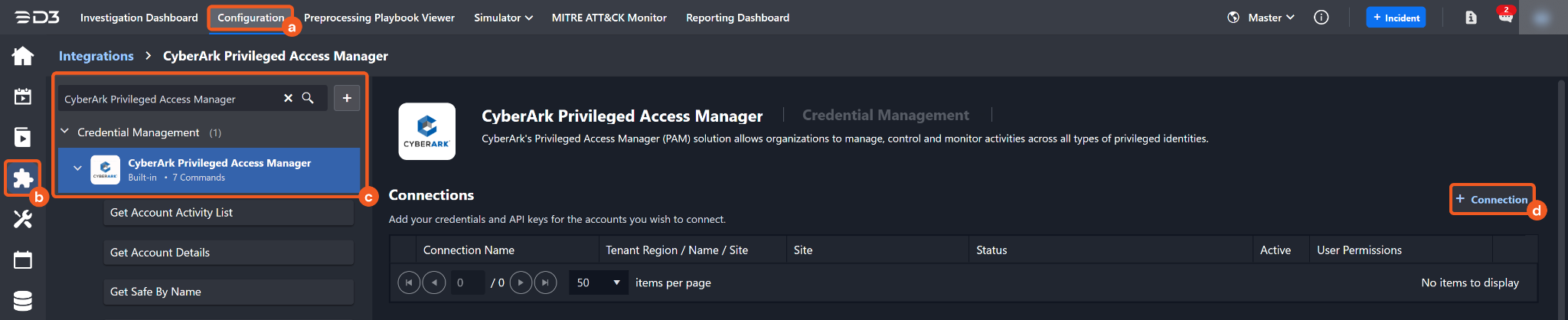
Navigate to Configuration on the top header menu.
Click on the Integration icon on the left sidebar.
Type CyberArk Privileged Access Manager in the search box to find the integration, then click it to select it.
Click on the + Connection button on the right side of the Connections section. A new connection window will appear.
Configure the following fields to create a connection to CyberArk Privileged Access Manager.
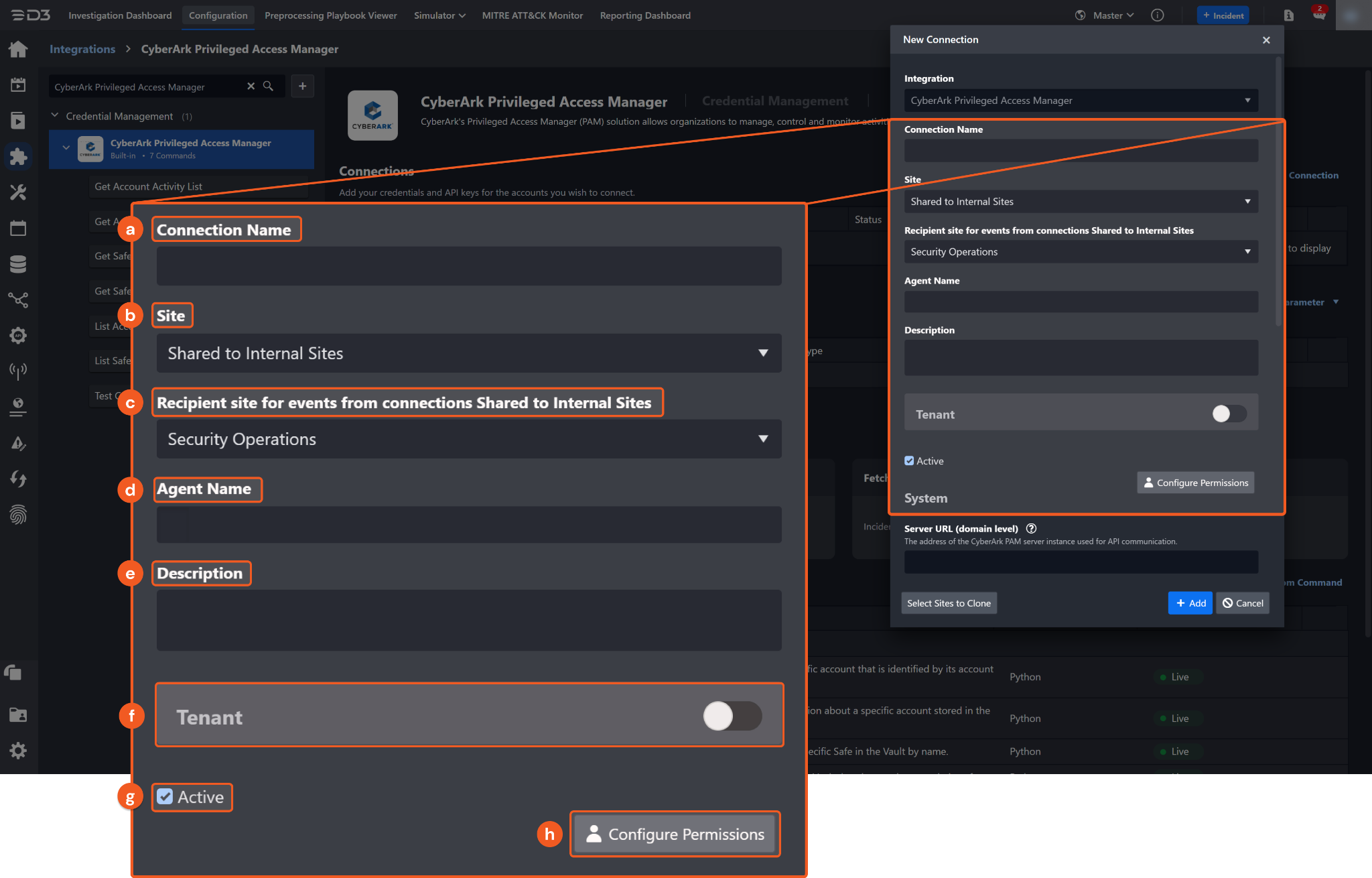
Connection Name: The desired name for the connection.
Site: The site on which to use the integration connection. Use the drop-down menu to select the site. The Share to Internal Sites option enables all internal sites to use the connection. Selecting a specific site will only enable that site to use the connection.
Recipient site for events from connections Shared to Internal Sites: This field is displayed when Share to Internal Sites is selected for the Site field, allowing selection of the internal site for deploying the integration connection.
Agent Name (Optional): The proxy agent required to build the connection. Use the dropdown menu to select the proxy agent from a list of previously configured proxy agents.
Description (Optional): The description for the connection.
Tenant (Optional): When configuring the connection from a master tenant site, users can choose the specific tenant sites with which to share the connection. Once this setting is enabled, users can filter and select the desired tenant sites from the dropdowns to share the connection.

Active: The checkbox that enables the connection to be used when selected.
Configure User Permissions: Defines which users have access to the connection.
System: This section contains the parameters defined specifically for the integration. These parameters must be configured to create the integration connection.
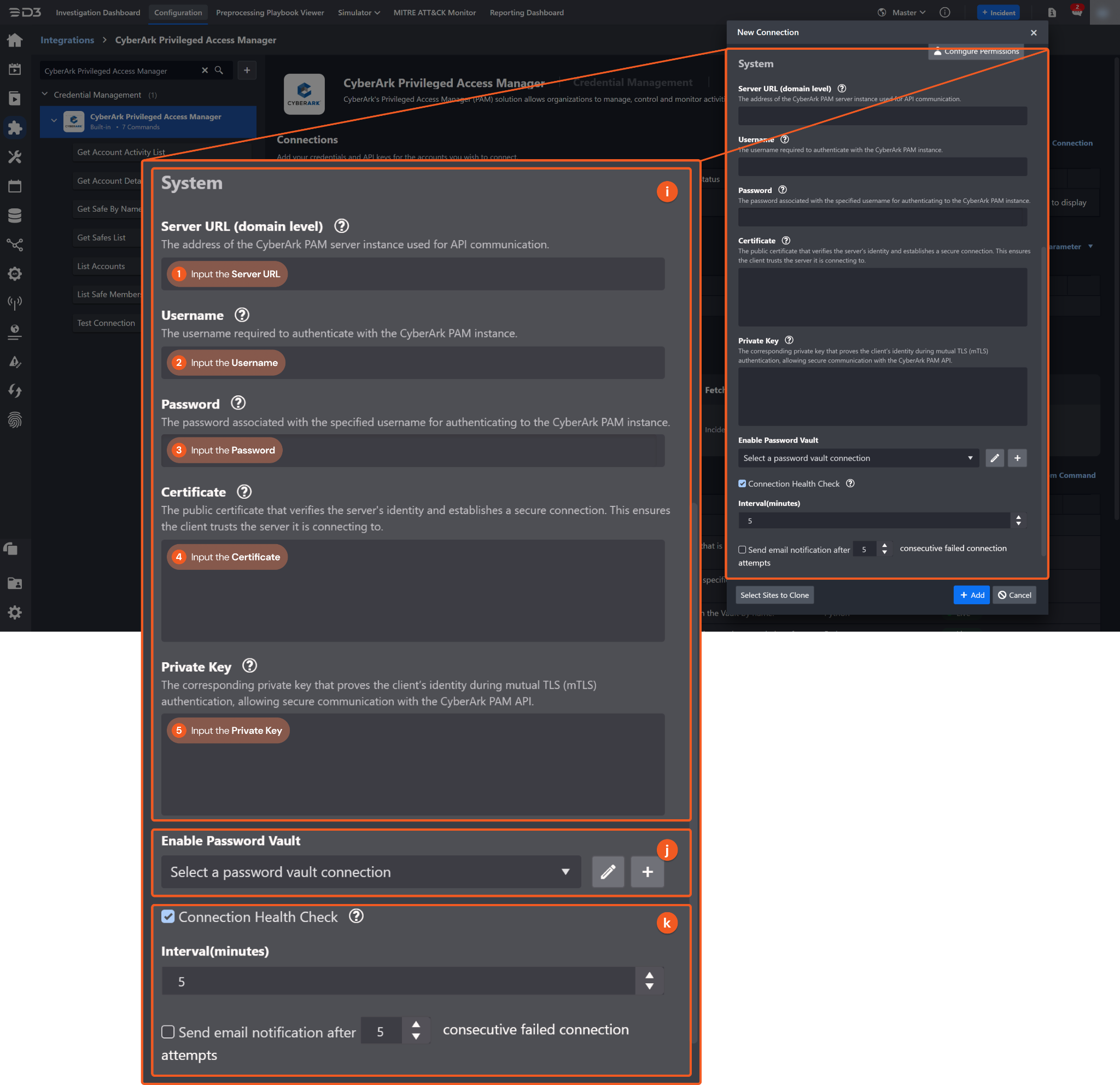
1. Input the Server URL.
2. Input the Username.
3. Input the Password.
4. Input the Certificate if using certificate-based authentication. Refer to step 3 in Configuring CyberArk Privileged Access Manager to Work with D3 SOAR.
5. Input the Private Key if using certificate-based authentication. Refer to step 4 in Configuring CyberArk Privileged Access Manager to Work with D3 SOAR.
Enable Password Vault: An optional feature that allows users to take the stored credentials from their own password vault. Refer to the password vault connection guide if needed.
Connection Health Check: Periodically checks the connection status by scheduling the Test Connection command at the specified interval (in minutes). Available only for active connections, this feature also allows configuring email notifications for failed attempts.
Test the connection.
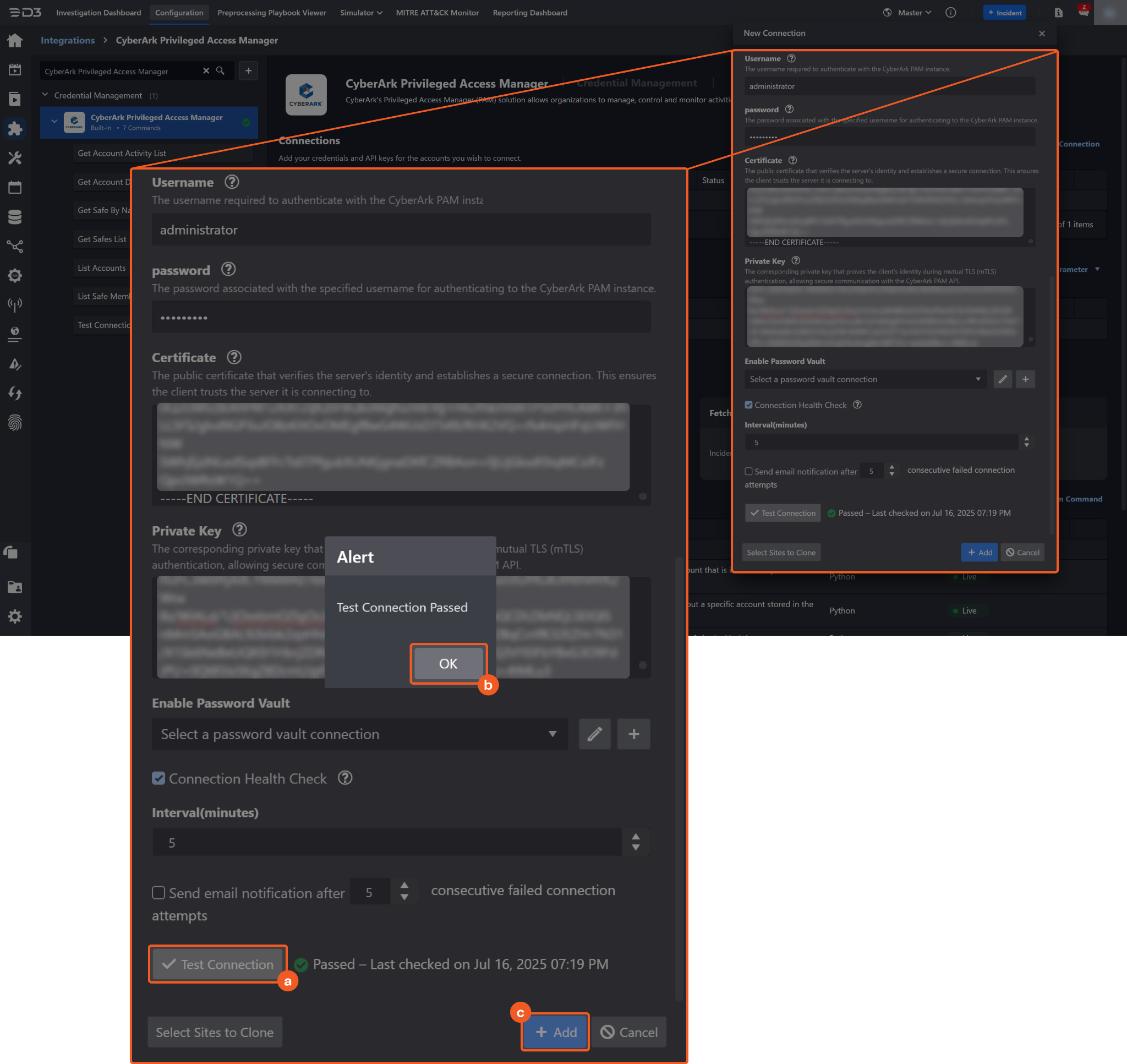
Click on the Test Connection button to verify credentials and connectivity. A success alert displays Passed with a green checkmark. If the connection fails, review the parameters and retry.
Click OK to close the alert window.
Click + Add to create and add the configured connection.
Commands
CyberArk Privileged Access Manager includes the following executable commands for users to set up schedules or create playbook workflows. With the Test Command function, users can execute these commands independently for playbook troubleshooting.
Integration API Note
For more information about the CyberArk Privileged Access Manager API, refer to the CyberArk Privileged Access Manager API reference.
READER NOTE
Certain permissions are required for each command. Refer to the Permission Requirements and Configuring CyberArk Privileged Access Manager to Work with D3 SOAR sections for details.
Get Account Activity List
Retrieves activity records for a specified account using its account ID.
READER NOTE
Account ID is a required parameter to run this command.
Run the List Accounts command to obtain the Account ID. Account IDs can be found in the raw data at $.value[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Account ID | Required | The unique identifier of the account whose activity records will be retrieved. Account ID can be obtained using the List Accounts command. | ***** |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Account Activity List failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CyberArk Privileged Access Manager portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Failed to get the activities of *****. Reason: The account was not found. |
Error Sample Data Get Account Activity List failed. Status Code: 404. Message: Failed to get the activities of *****. Reason: The account was not found. |
Get Account Details
Retrieves details for a specified account stored in the CyberArk PAM system.
READER NOTE
Account ID is a required parameter to run this command.
Run the List Accounts command to obtain the Account ID. Account IDs can be found in the raw data at $.value[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Account ID | Required | The unique identifier of the account whose details will be retrieved. Account ID can be obtained using the List Accounts command. | ***** |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Account Details failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CyberArk Privileged Access Manager portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Account id value is invalid. |
Error Sample Data Get Account Details failed. Status Code: 400. Message: Account id value is invalid. |
Get Safe By Name
Retrieves information for Safes by name.
READER NOTE
Safe Names is a required parameter to run this command.
Run the Get Safes List command to obtain the Safe Names. Safe Names can be found in the raw data at $.value[*].safeName.
Input
Input Parameter | Required/Optional | Description | Example |
Safe Names | Required | The names of the Safes to retrieve. Safe Names can be obtained using the Get Safes List command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Safe By Name failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CyberArk Privileged Access Manager portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Safe 123 was not found. |
Error Sample Data Get Safe By Name failed. Status Code: 404. Message: Safe 123 was not found. |
Get Safes List
Retrieves all Safes the authenticated user has permission to access.
Input
Input Parameter | Required/Optional | Description | Example |
Safe Name | Optional | Searches for Safes by name. | VaultInternal |
Number of Safes to Return | Optional | The number of Safes to return. By default, the value is 1000. A large number may result in command timeout. | 10 |
Sort By | Optional | The field by which to sort the returned Safes. Available options are:
By default, the value is set to Assigned CPM. | Safe Name |
Sort Direction | Optional | The direction by which the returned Safes are sorted. Available options are:
By default, the Sort Direction is Ascending. | Descending |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Safes List failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CyberArk Privileged Access Manager portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Get Safes List failed. Status Code: 401. Message: Unauthorized. |
List Accounts
Retrieves a list of accounts stored in the Vault.
Input
Input Parameter | Required/Optional | Description | Example |
Search | Optional | A space-separated list of keywords to match account fields. "Contains" is the default search type. | Administrator |
Filter | Optional | Filters accounts using properties such as safeName and modificationTime. Multiple filters can be combined using the AND operator. | safename eq partner AND modificationTime gte 1747426300 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Accounts failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CyberArk Privileged Access Manager portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data List Accounts failed. Status Code: 401. Message: Unauthorized. |
List Safe Members
Retrieves a list of the members assigned to a Safe.
READER NOTE
Safe URL ID is a required parameter to run this command.
Run the Get Safes List command to obtain the Safe URL ID. Safe URL IDs can be found in the raw data at $.value[*].safeUrlId.
Input
Input Parameter | Required/Optional | Description | Example |
Safe URL ID | Required | The unique ID of the Safe for which to retrieve members. Safe URL ID can be obtained using the Get Safes List command. | Partner |
Filter | Optional | Retrieves Safe members based on the specified filters. Available values are:
Combine multiple filters using the AND operator. | memberType eq user AND membershipExpired eq false AND includePredefinedUsers eq false |
Limit | Optional | The maximum number of members that are returned. By default, the value is 25. | 10 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Safe Members failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CyberArk Privileged Access Manager portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: PASWS070E Safe 123 was not found. |
Error Sample Data List Safe Members failed. Status Code: 404. Message: PASWS070E Safe 123 was not found. |
Test Connection
Allows users to perform a health check on an integration connection. Users can schedule a periodic health check by selecting Connection Health Check when editing an integration connection.
Input
N/A
Output
Output Type | Description | Return Data Type |
Return Data | Indicates one of the possible command execution states: Successful or Failed. The Failed state can be triggered by any of the following errors:
More details about an error can be viewed in the Error tab. | String |
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Test Connection failed. Failed to check the connector. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CyberArk Privileged Access Manager portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Test Connection failed. Failed to check the connector. Status Code: 401. Message: Unauthorized. |