CrowdStrike NG-SIEM
LAST UPDATED: OCTOBER. 6, 2025
Overview
The CrowdStrike Next-Gen SIEM is a modern, cloud-native SIEM platform built on Falcon LogScale (formerly Humio). The platform collects, ingests, and searches security and operational logs; enables threat hunting and detection engineering; correlates data across endpoints, identities, cloud, and network environments; and provides unified visibility across the organization's environment.
D3 SOAR is providing REST operations to function with CrowdStrike NG-SIEM. CrowdStrike NG-SIEM is available for use in:
Connection
Gather the following information to connect D3 SOAR to CrowdStrike NG-SIEM.
Parameter | Description | Example |
Server URL | The base server URL for the CrowdStrike API. The Server URL can be obtained from the CrowdStrike UI under Support and resources > API clients and keys. | https://api.crowdstrike.com |
Client ID | The client ID used to authenticate the API connection. | acb9*****66a9 |
Client Secret | The client secret used to authenticate the API connection. | m132*****Setf |
Permission Requirements
Each endpoint in the CrowdStrike NG-SIEM API requires a certain permission scope. The following are required scopes for the commands in this integration:
Command | Required Permissions |
Fetch Event |
|
NG-SIEM Search |
|
Test Connection |
|
Configuring CrowdStrike NG-SIEM to Work with D3 SOAR
Log in to https://falcon.crowdstrike.com.
Search for and click on the API clients and keys console page.
Click on the Create API client button.
Enter a client name, input the required scopes, then click on the Create button.
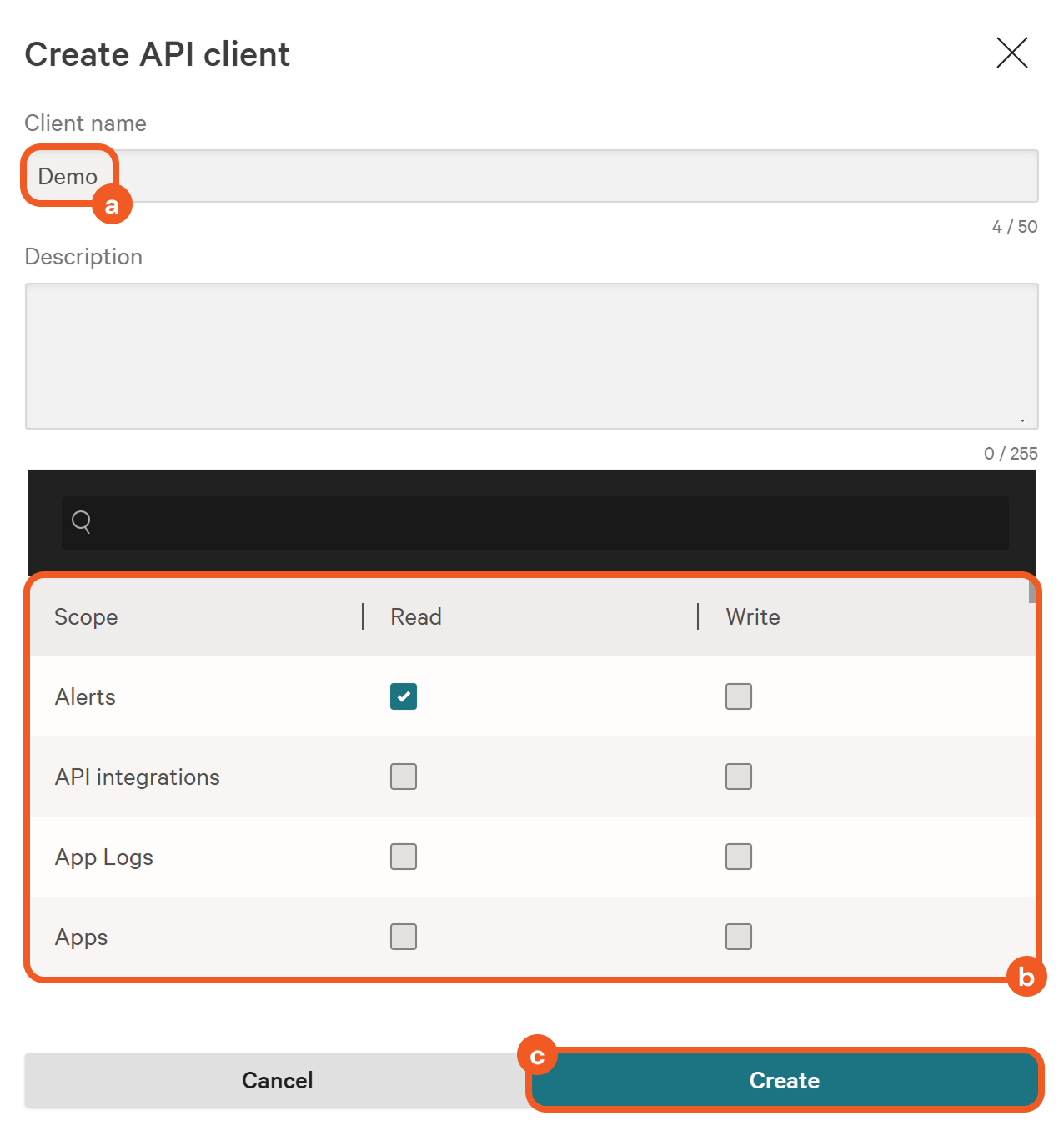
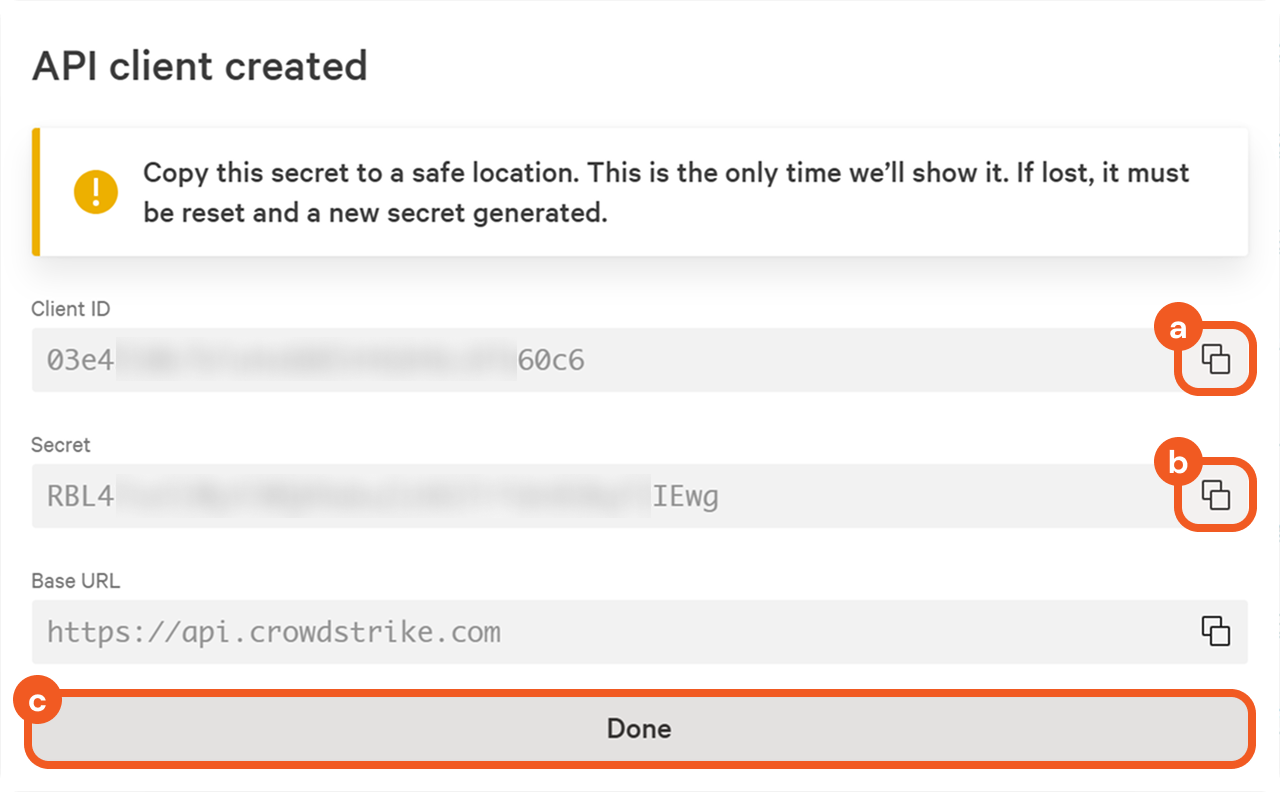
Securely store both the client ID and secret, then click on the Done button.
Configuring D3 SOAR to Work with CrowdStrike NG-SIEM
Log in to D3 SOAR.
Find the CrowdStrike NG-SIEM integration.
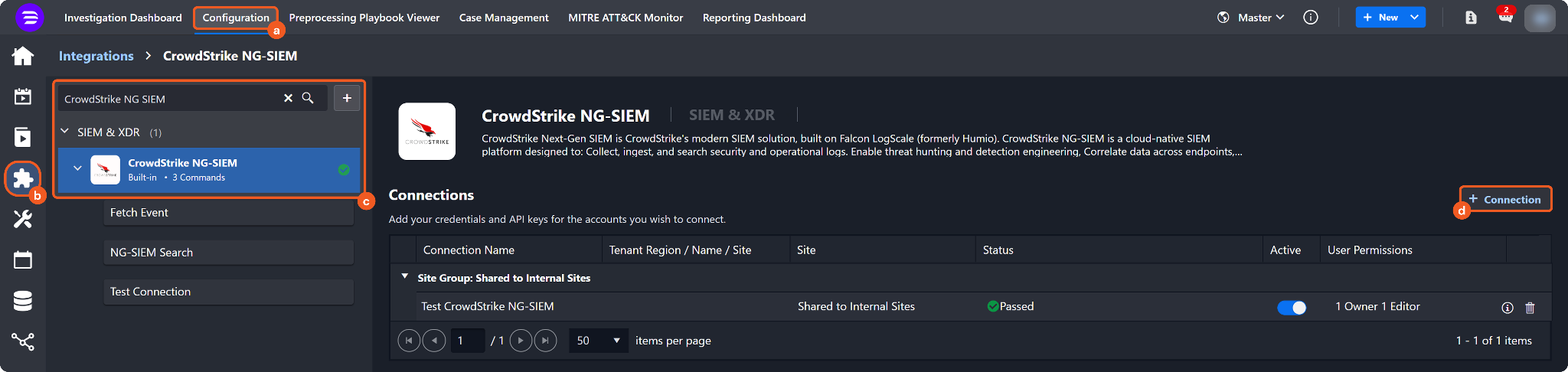
Navigate to Configuration on the top header menu.
Click on the Integration icon on the left sidebar.
Type CrowdStrike NG-SIEM in the search box to find the integration, then click it to select it.
Click on the + Connection button on the right side of the Connections section. A new connection window will appear.
Configure the following fields to create a connection to CrowdStrike NG-SIEM.
-20251007-192147.png?inst-v=9d16beaf-952a-4ae4-8fe8-e35f7a3745da)
Connection Name: The desired name for the connection.
Site: The site on which to use the integration connection. Use the drop-down menu to select the site. The Share to Internal Sites option enables all internal sites to use the connection. Selecting a specific site will only enable that site to use the connection.
Recipient site for events from connections Shared to Internal Sites: This field is displayed when Share to Internal Sites is selected for the Site field, allowing selection of the internal site for deploying the integration connection.
Agent Name (Optional): The proxy agent required to build the connection. Use the dropdown menu to select the proxy agent from a list of previously configured proxy agents.
Description (Optional): The description for the connection.
Tenant (Optional): When configuring the connection from a master tenant site, users can choose the specific tenant sites with which to share the connection. Once this setting is enabled, users can filter and select the desired tenant sites from the dropdowns to share the connection.
Configure User Permissions: Defines which users have access to the connection.
Active: The checkbox that enables the connection to be used when selected.
System: This section contains the parameters defined specifically for the integration. These parameters must be configured to create the integration connection.
-20251007-192221.png?inst-v=9d16beaf-952a-4ae4-8fe8-e35f7a3745da)
1. Input the Server URL. The default value is https://api.crowdstrike.com.
2. Input the Client ID.
3. Input the Client Secret.Enable Password Vault: An optional feature that allows users to take the stored credentials from their own password vault. Refer to the password vault connection guide if needed.
Connection Health Check: Periodically checks the connection status by scheduling the Test Connection command at the specified interval (in minutes). Available only for active connections, this feature also allows configuring email notifications for failed attempts.
Test the connection.
-20251007-192257.png?inst-v=9d16beaf-952a-4ae4-8fe8-e35f7a3745da)
Click on the Test Connection button to verify credentials and connectivity. A success alert displays Passed with a green checkmark. If the connection fails, review the parameters and retry.
Click OK to close the alert window.
Click + Add to create and add the configured connection.
Commands
CrowdStrike NG-SIEM includes the following executable commands for users to set up schedules or create playbook workflows. With the Test Command function, users can execute these commands independently for playbook troubleshooting.
READER NOTE
Certain permissions are required for each command. Refer to the Permission Requirements and Configuring CrowdStrike NG-SIEM to Work with D3 SOAR sections for details.
Note for Time-related parameters
The input format of time-related parameters may vary based on user account settings, which may cause the sample data in commands to differ from what is displayed. To adjust the time format, follow these steps:
Navigate to Configuration Application Settings. Select Date/Time Format.
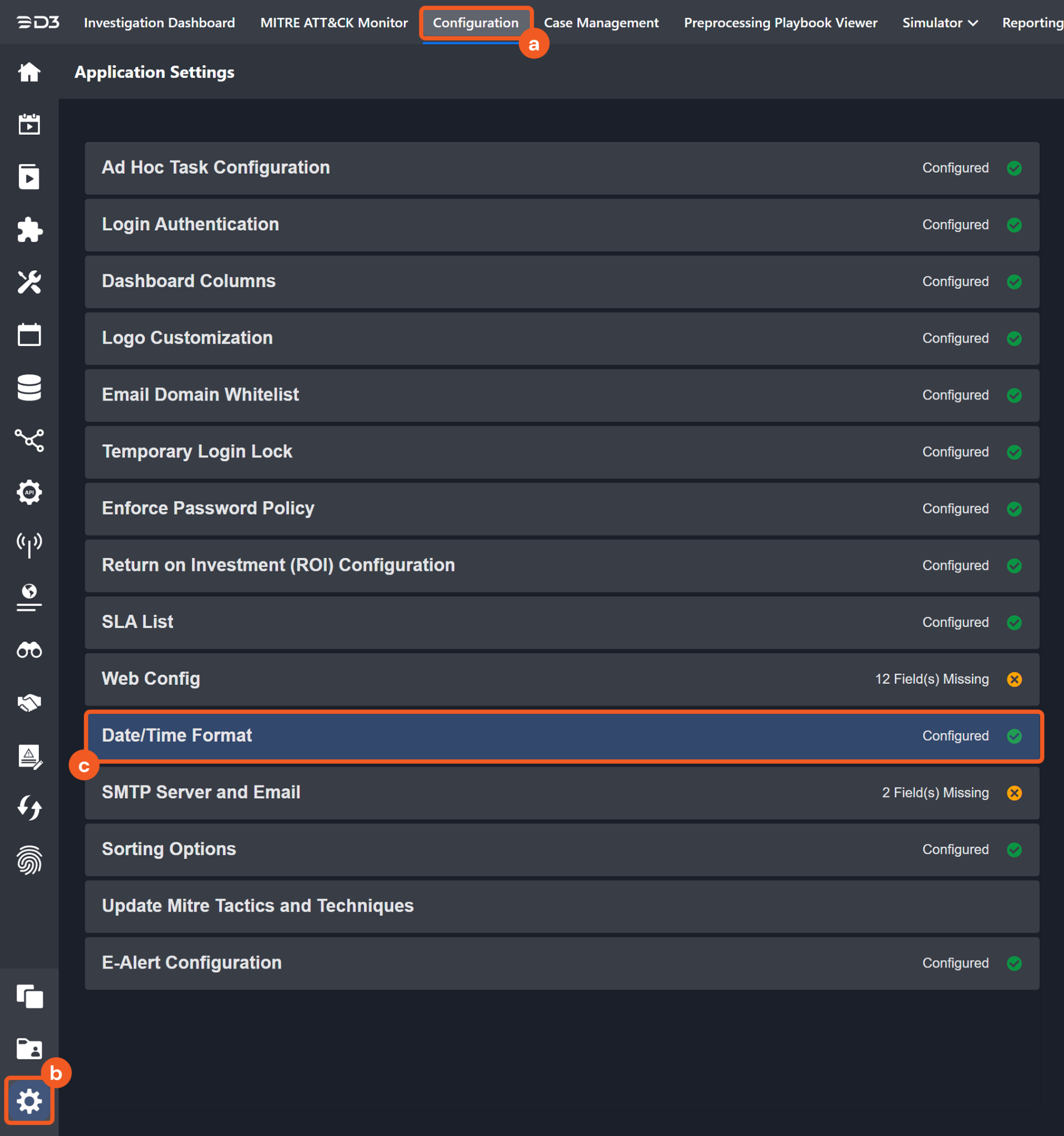
Choose the desired date and time format, then click on the Save button.
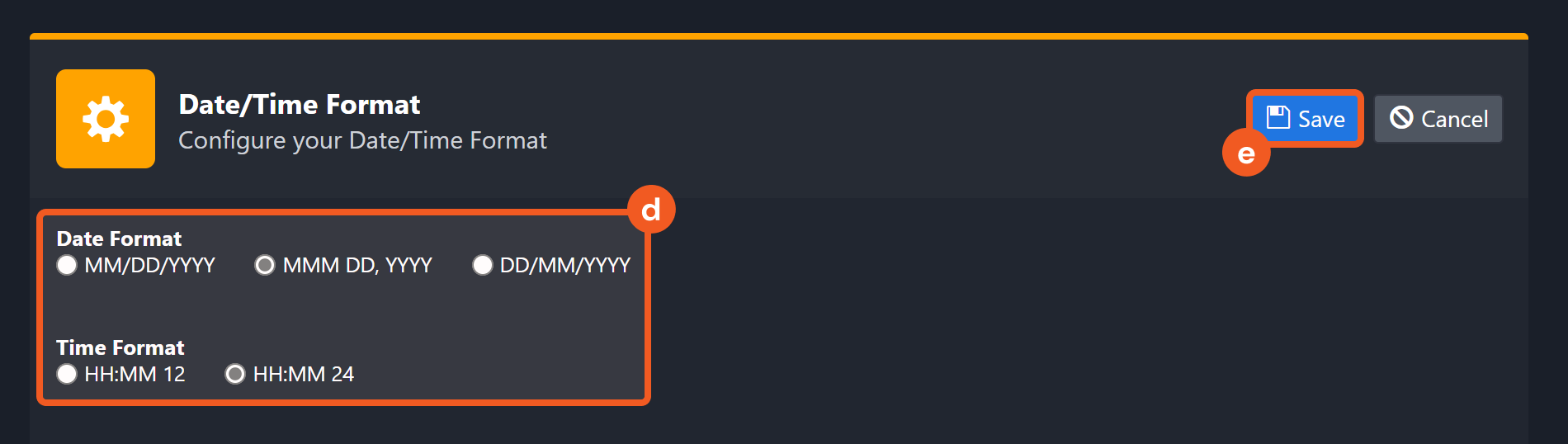
The selected time format will now be visible when configuring Date/Time command input parameters.
Fetch Event
Returns NG-SIEM incidents from the NG-SIEM platform based on specified criteria. For details about the search syntax, see https://falconpy.io/Usage/Falcon-Query-Language.html.
Input
Input Parameter | Required/Optional | Description | Example |
Start Time | Optional | The start time of the time range (in UTC) used to fetch events, based on the specified query time type. | 2022-10-01 00:00 |
End Time | Optional | The end time of the time range (in UTC) used to fetch events, based on the specified query time type. | 2022-10-06 00:00 |
Query Time Type | Optional | The time field to filter retrieved events. For NG-SIEM incidents, valid options are:
By default, the time field used for NG-SIEM incidents is Updated Time. | Updated Time |
Number of Event(s) Fetched | Optional | The maximum number of the most recent events to fetch. The value must be an integer between 1 and 500. If the value is outside this range or not provided, all events that match the search conditions will be returned. | 10 |
Search Condition | Optional | The condition to perform a full-text search across all metadata fields. | TA0005 |
Filter | Optional | The query used to filter results. For details about the query syntax, see https://falcon.crowdstrike.com/documentation/45/falcon-query-language-fql. | status:'new' + severity_name:!'Informational' |
Output
To view the sample output data for all commands, refer to this article.
Fetch Event Field Mapping
See Field Mappings.
The CrowdStrike NG-SIEM system integration includes pre-configured field mappings for the default event source.
The Default Event Source is the default system-provided set of field mappings applied when the fetch event command is executed. It includes a Main Event JSON Path, which is the JSONPath expression that points to the base array of event objects. The source field path continues from this array to locate the required data.
The Main Event JSON Path can be viewed by clicking on the Edit Event Source button.
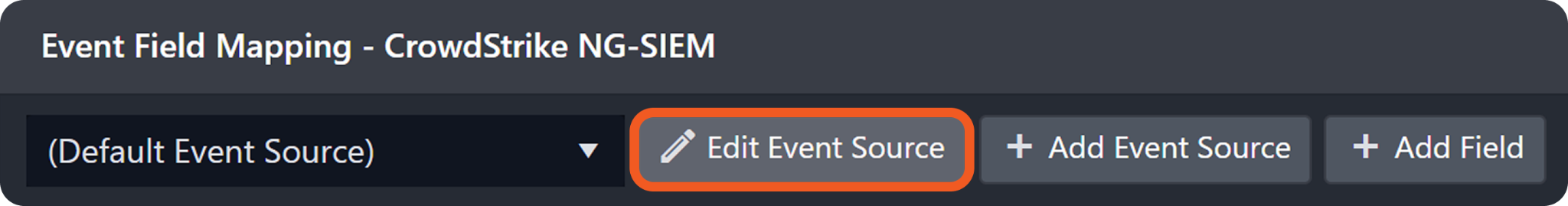
Main Event JSON Path: $.resources
The resources array contains the event objects. Within each object, the key .entities.agent_ids, for instance, denotes the Agent IDs field. As such, the full JSONPath expression to extract the Unique Event Key is $.entities.agent_ids.Agent IDs.
The pre-configured field mappings are detailed below:
Field Name | Source Field |
Agent IDs | .entities.agent_ids |
Alert IDs | .references.indicator_alert_ids |
Assignee | .assigned_to_name |
Detection IDs | .references.indicator_detection_ids |
Generated By | .author |
Incident End Time | .incident.end_time |
Incident ID | .incident.id |
Incident Score | .incident.score |
Incident Start Time | .incident.start_time |
Incident State | .incident.state |
Incident Type | .incident.type |
Pattern ID | .pattern_id |
Platform | .platform |
Tactic ID | .tactic_id |
Technique ID | .technique_id |
UpdateTime | .updated_timestamp |
XDR Detection ID | .xdr_detection_id |
XDR Pattern ID | .xdr_pattern_id |
XDR Rule ID | .xdr_rule_id |
XDR Source Event ID | .references.xdr_source_event_id |
Device IP address | .entities.ipv4 |
End Time | .end_time |
Event category | .data_domains |
Event code | .composite_id |
Event name | .name |
Event Type | .type |
File Hash SHA256 | .entities.sha256 |
Filename | .entities.file_name |
Filepath | .entities.image_file_name |
Start Time | .timestamp |
Process ID | .entities.process |
Severity | .severity_name |
Source Product | .product |
Tactics | .tactic |
Techniques | .technique |
Username | .entities.username |
User security ID | .entities.user_sids |
Device IP address | .device.local_ip |
EventID | .id |
Source Product | .source_products |
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Fetch Event failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike NG-SIEM portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: You must have a valid Support account to call this API. |
Error Sample Data Fetch Event failed. Status Code: 403. Message: You must have a valid Support account to call this API. |
NG-SIEM Search
Searches and retrieves log data stored in repositories using queries written in the CrowdStrike Query Language (CQL). A maximum of 200 events will be returned. If more than 200 events match the filters, narrow the results by adjusting the Start Time, End Time, or Query String parameters.
Input
Input Parameter | Required/Optional | Description | Example |
Repository | Optional | The repository to run the query against. The available options are:
By default, the value is All. The availability of specific repositories depends on the Falcon subscription. | IT Automation |
Start Time | Optional | The date and time used as the starting point of the search results, based on the specified query time type. By default, the Start Time is 15 minutes earlier than the End Time. | 2022-10-01 00:00 |
End Time | Optional | The date and time (in UTC) used as the ending point of the search results, based on the specified query time type. By default, the End Time is the current time. | 2022-10-06 00:00 |
Query Time Type | Optional | The time type by which to filter the events. The options are:
By default, the Query Time Type is Event Timestamp. | Event Ingest Timestamp |
Query String | Required | The CQL query to use for the search. Double quotes (") and backslashes (\) in the Query String must be escaped with a backslash to ensure they are properly interpreted. | ComputerName= LAB1-PC5 and SHA256HashData= 579d*****e920 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | NG-SIEM Search failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike NG-SIEM portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: You must have a valid Support account to call this API. |
Error Sample Data NG-SIEM Search failed. Status Code: 403. Message: You must have a valid Support account to call this API. |
Test Connection
Allows users to perform a health check on an integration connection. Users can schedule a periodic health check by selecting Connection Health Check when editing an integration connection.
Input
N/A
Output
Output Type | Description | Return Data Type |
Return Data | Indicates one of the possible command execution states: Successful or Failed. The Failed state can be triggered by any of the following errors: A connection issue with the integration The API returned an error message No response from the API More details about an error can be viewed in the Error tab. | String |
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Test Connection failed. Failed to check the connector. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike NG-SIEM portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: You must have a valid support account to call this API. |
Error Sample Data Test Connection failed. Failed to check the connector. Status Code: 403. Message: You must have a valid Support account to call this API |