CrowdStrike
LAST UPDATED: JANUARY 6, 2026
Overview
CrowdStrike provides endpoint security, threat intelligence, and cyber attack response services. D3's integration with CrowdStrike covers the major operations that are commonly used including quarantine endpoint, get process, execute command on single endpoint, execute batch command etc.
D3 SOAR is providing REST operations to function with CrowdStrike.
CrowdStrike is available for use in:
Known Limitations
All requests to the CrowdStrike API are subject to a rate limitations. By default, this limit is set to 100 requests per second. When the rate limit is exceeded, subsequent requests receive an HTTP 429: Too Many Requests response.
Refer to the CrowdStrike's API documentation for more information.
Connection
To connect to CrowdStrike from D3 SOAR, follow this part to collect the required information below:
Parameter | Description | Example |
Server URL | The server URL of the CrowdStrike API. | https://api.CrowdStrike.com |
Client ID | The client ID to authenticate the API connection. | acb9*****a6a9 |
Client Secret | The client secret to authenticate the API connection. | m132*****Setf |
API Version | The API version to use for the connection. | v1 |
Permission Requirements
Each endpoint in the CrowdStrike API requires a certain permission scope. The following are required scopes for the commands in this integration:
READER NOTE
ℹ️ Indicates commands that require multiple scopes.
⚠️ Indicates commands that are deprecated.
Resource | Scope | Commands |
|---|---|---|
Alerts | Read |
|
Write |
| |
Detections | Read |
|
Write |
| |
Incidents | Read |
|
Write |
| |
Hosts | Read |
|
Write |
| |
Host Groups | Read |
|
IOC Management | Read |
|
Write |
| |
IOCs (Indicators of Compromise) | Read |
|
On-demand scans (ODS) | Read |
|
Write |
| |
Quarantined Files | Read |
|
Write |
| |
Real time response | Read |
|
Write |
| |
Real time response (admin) | Write (admin) |
|
Vulnerabilities | Read |
|
User Management | Read |
|
Configuring CrowdStrike to Work with D3 SOAR
Log into CrowdStrike.
.png?inst-v=a916037b-9847-42e4-b4ba-0807570b75be)
Use the shortcut Ctrl + K (Windows) or Cmd + K (macOS) to bring up the search bar, then search and select the API clients and keys page.
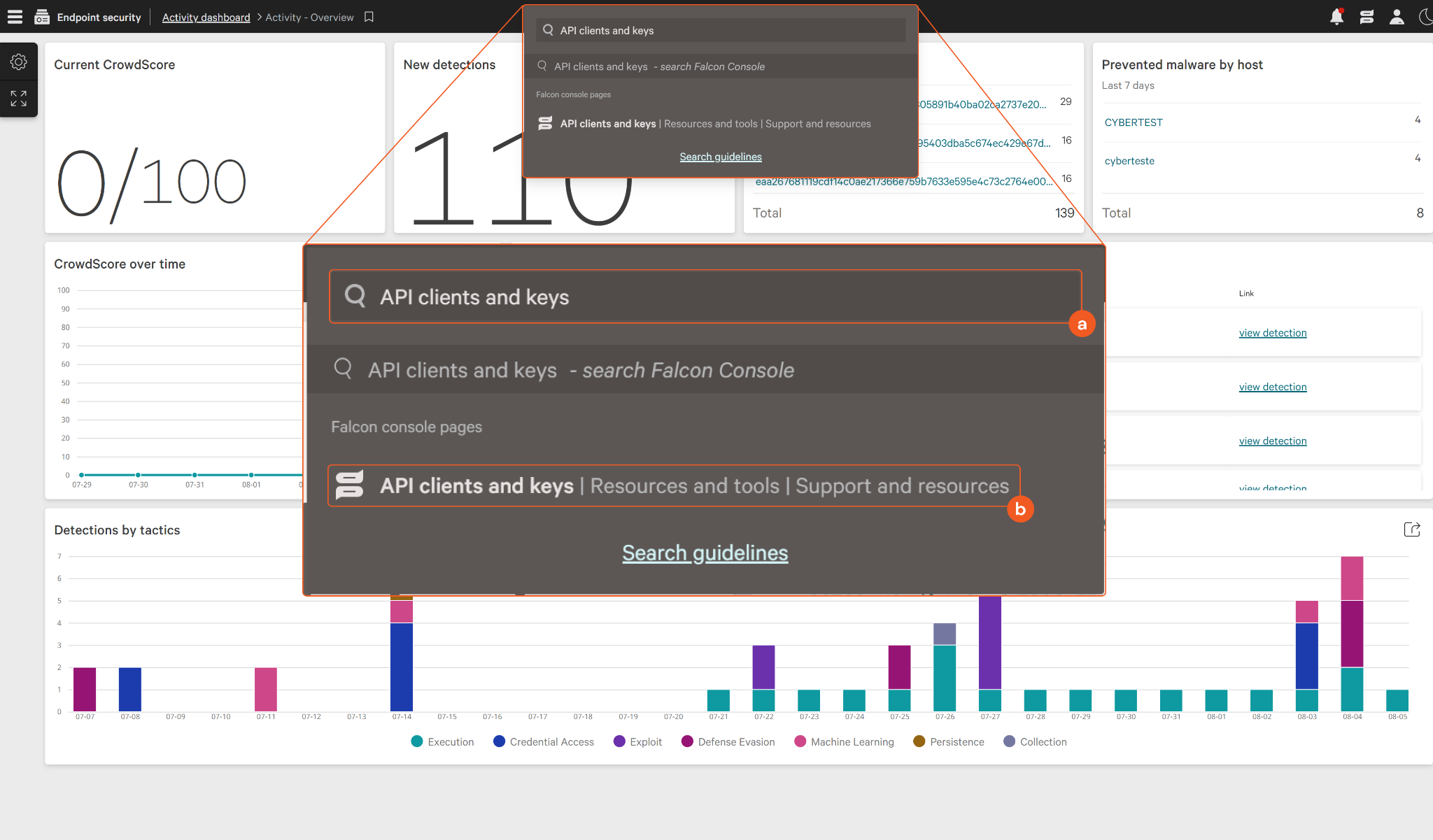
Create an API client.
.png?inst-v=a916037b-9847-42e4-b4ba-0807570b75be)
Click the Create API Client button.
Input a Client Name.
Search for and select the necessary permission scopes.
Refer to Permission Requirements for more information on API scopes.
Click the Create button.
Copy the Client ID and Secret.
.png?inst-v=a916037b-9847-42e4-b4ba-0807570b75be)
The Secret will no longer be visible after this point.
Configuring D3 SOAR to Work with CrowdStrike
Log in to D3 SOAR.
Find the CrowdStrike integration.
.png?inst-v=a916037b-9847-42e4-b4ba-0807570b75be)
Navigate to Configuration on the top header menu.
Click on the Integration icon on the left sidebar.
Type CrowdStrike in the search box to find the integration, then click it to select it.
Click + New Connection, on the right side of the Connections section. A new connection window will appear.
Configure the following fields to create a connection to CrowdStrike.
.png?inst-v=a916037b-9847-42e4-b4ba-0807570b75be)
Connection Name: The desired name for the connection.
Site: The site on which to use the integration connection. Use the drop-down menu to select the site. The Share to Internal Sites option enables all internal sites to use the connection. Selecting a specific site will only enable that site to use the connection.
Recipient site for events from connections Shared to Internal Sites: This field is displayed when Share to Internal Sites is selected for the Site field, allowing selection of the internal site for deploying the integration connection.
Agent Name (Optional): The proxy agent required to build the connection. Use the dropdown menu to select the proxy agent from a list of previously configured proxy agents.
Description (Optional): The description for the connection.
Tenant (Optional): When configuring the connection from a master tenant site, users can choose the specific tenant sites with which to share the connection. Once this setting is enabled, users can filter and select the desired tenant sites from the dropdowns to share the connection.
.png?inst-v=a916037b-9847-42e4-b4ba-0807570b75be)
Configure User Permissions: Defines which users have access to the connection.
Active: The checkbox that enables the connection to be used when selected.
System: This section contains the parameters defined specifically for the integration. These parameters must be configured to create the integration connection.
.png?inst-v=a916037b-9847-42e4-b4ba-0807570b75be)
1. Input the domain level Server URL. The default value is https://api.CrowdStrike.com.
2. Copy and input the Client ID from the CrowdStrike platform. Refer to step 5 of Configuring CrowdStrike to Work with D3 SOAR.
3. Copy and input the Client Secret from the CrowdStrike platform. Refer to step 5 of Configuring CrowdStrike to Work with D3 SOAR.
4. The default value of the API Version is v1. The Get Vulnerability Details, Isolate Host, Quarantine Host by ID, Update Detection and Unquaratine Host by ID commands require API Version v2. All other commands only accept API Version v1.
Enable Password Vault: An optional feature that allows users to take the stored credentials from their own password vault. Refer to the password vault connection guide if needed.
Connection Health Check: Periodically checks the connection status by scheduling the Test Connection command at the specified interval (in minutes). Available only for active connections, this feature also allows configuring email notifications for failed attempts.
Test the connection.
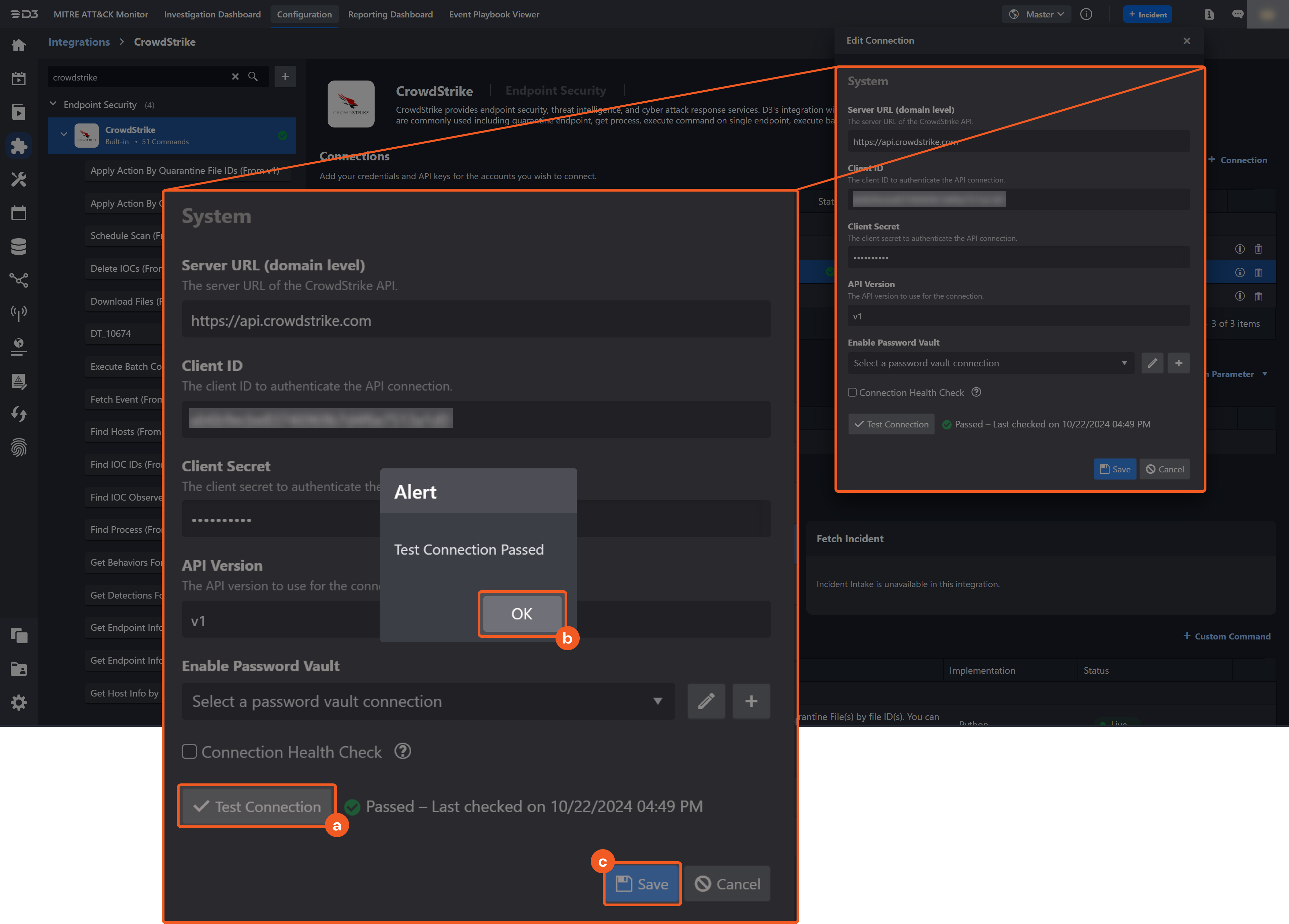
Click on the Test Connection button to verify credentials and connectivity. A success alert displays Passed with a green checkmark. If the connection fails, review the parameters and retry.
Click OK to close the alert window.
Click + Add to create and add the configured connection.
Commands
CrowdStrike includes the following executable commands for users to set up schedules or create playbook workflows. With the Test Command, users can execute these commands independently for playbook troubleshooting.
Integration API Note
For more information about the CrowdStrike API, refer to the CrowdStrike API reference.
READER NOTE
Certain permissions are required for each command. Refer to the Permission Requirements and Configuring CrowdStrike to Work with D3 SOAR for details.
Note for Time-related parameters
The input format of time-related parameters may vary based on user account settings, which may cause the sample data in commands to differ from what is displayed. To adjust the time format, follow these steps:
Navigate to Configuration > Application Settings. Select Date/Time Format.
-20241017-192013.png?inst-v=a916037b-9847-42e4-b4ba-0807570b75be)
Choose the desired date and time format, then click on the Save button.
-20241017-192025.png?inst-v=a916037b-9847-42e4-b4ba-0807570b75be)
The selected time format will now be visible when configuring Date/Time command input parameters.
Apply Action By Quarantine File IDs
Applies the specified action on quarantine File(s) by file ID(s).
READER NOTE
File IDs is a required parameter to run this command.
Run the List Quarantine Files command to obtain the File IDs. File IDs can be found in the raw data at the path $.resources[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
File IDs | Required | The quarantined file ID(s) to apply an action. The max file IDs count is 20. File IDs can be obtained using the List Quarantine Files command. |
JSON
|
Action | Required | The action to perform against the quarantined file(s). | Release |
Comment | Optional | The comment to list along with action taken. | good file |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Apply Action By Quarantine File IDs failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: Validation error. Failed to apply action by quarantine file IDs. |
Error Sample Data Apply Action By Quarantine File IDs failed. Status Code: 400. Error Message: Validation error. Failed to apply action by quarantine file IDs. |
Apply Action By Query
Applies the specified action on quarantine file(s) by query criteria. It is necessary to enter either Filter or SHA256s parameters, or both.
Input
Input Parameter | Required/Optional | Description | Example |
Filter | Optional | The FQL query specifying filter parameters. Special value '*' means to not filter on anything. Filter term criteria include: status, adversary_id, device.device_id, device.country, device.hostname, behaviors.behavior_id, behaviors.ioc_type, behaviors.ioc_value, behaviors.username, behaviors.tree_root_hash. Filter range criteria:, max_severity, max_confidence, first_behavior, last_behavior. For more information about the query syntax, please refer to Falcon Query Language (FQL). Please do NOT enter SHA256 into this parameter, and it is possible to use SHA256s parameter to filter for SHA256 hash values. | hostname:'L***-P**'+state:'unreleased' |
SHA256s | Optional | The SHA256 hash value(s) of the quarantined file(s) to apply action. |
JSON
|
Action | Required | The action to perform against the quarantined file(s). | Release |
Comment | Optional | The comment to list along with action taken. | Comment for the Action |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Apply Action By Query failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: Failed to apply action by query. |
Error Sample Data Apply Action By Query failed. Status Code: 400. Error Message: Failed to apply action by query. |
Batch Refresh Session
Batch refreshes a Real-Time Response (RTR) session on multiple hosts. Without refreshing, RTR sessions will expire within 10 minutes.
READER NOTE
Batch ID is a required parameter to run this command.
Run the Execute Batch Command to obtain the Batch ID. Batch IDs can be found in the raw data at the path $.batch_id.
Input
Input Parameter | Required/Optional | Description | Example |
Batch ID | Required | The ID of the RTR batch to refresh. Batch IDs can be obtained using the Execute Batch Command. | ***-***-***-***-*** |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Batch Refresh Session failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: Batch ID Not Found. |
Error Sample Data Batch Refresh Session failed. Status Code: 404. Error Message: Batch ID Not Found. |
Delete IOCs
Permanently deletes the specified indicator(s) of compromise.
READER NOTE
IDs is a required parameter to run this command.
Run the Find IOC IDs command to obtain the IDs. IDs can be found in the raw data at the path $.resources.
Input
Input Parameter | Required/Optional | Description | Example |
IDs | Required | The IDs of the indicators of compromise (IOCs) to delete. IDs can be obtained using the Find IOC IDs command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Delete IOCs failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: No resource found with ID 5ec6****4a69****284b. |
Error Sample Data Delete IOCs failed. Status Code: 404, Error Message: 'No resource found with ID 5ec6****4a69****284b. |
Download Files
Retrieves files from a specific host ID and file paths. The files are compressed as a 7z file and with the unzip password set as "infected."
READER NOTE
Host ID and File Paths are required parameters to run this command.
Run the Find Hosts command to obtain the Host ID. Host IDs can be found in the raw data at the path $.resources.
Input Host ID and File Paths must match. If a matching pair of values is not available, use the Fetch Event command to obtain the necessary pair of values.
Input
Input Parameter | Required/Optional | Description | Example |
Host ID | Required | The ID of the host to retrieve files. Host ID can be obtained using the Find Hosts command. | f00b*****cf9d |
File Paths | Required | The file path to download files. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Download Files failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: host not found. |
Error Sample Data Download Files failed. Status Code: 404, Error Message: host not found. |
Execute Batch Command
Batch executes RealTime Response administrator commands, with the queue offline feature enabled across all the hosts.
READER NOTE
Endpoint IDs is a required parameter to run this command.
Run the Find Hosts command to obtain the Endpoint IDs. Endpoint IDs can be found in the raw data, at the path $.resources.
Input
Input Parameter | Required/Optional | Description | Example |
Endpoint IDs | Required | The IDs of the endpoints to batch execute commands. You can obtain Endpoint IDs using the Find Hosts command. |
JSON
|
Command Strings | Required | The commands to batch execute on the specified hosts. Each line contains a base command. The supported base commands are: cat, cd, clear, cp, encrypt, env, eventlog, filehash, get, getsid, help, history, ipconfig, kill, ls, map, memdump, mkdir, mount, mv, netstat, ps, put, reg query, reg set, reg delete, reg load, reg unload, restart, rm, run, runscript, shutdown, unmap, update history, update install, update list, update query, xmemdump, and zip. | mkdir c:\\*** |
Duration Minutes | Optional | The duration of the command run time until completion, measured in minutes. Default is 10 minutes. | 60 |
Refresh Session | Optional | The option to refresh the session when set to True. Default is False. | False |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Execute Batch Command failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error message: resource not found. |
Error Sample Data Execute Batch Command failed. Status Code: 404, Error Message: resource not found. |
Fetch Event
Returns events from the platform based on specified criteria. Event types include endpoint protection detections, incidents, and unified alerts, displayed in the Endpoint Detections Updated UI.
READER NOTE
Key differences between the Search Condition and Filter input parameters:
Search Condition is used to search for keywords across all metadata fields. It can only be used for detection-type events.
Any event containing the search keyword in any field will be returned.
No "AND" operators are valid for inputs in this parameter. Any input operator will be treated as an "OR" operator for the search condition.
For example, the input value AA-BBB-123456 will result in searching for the keywords "AA" or "BBB" or "123456".
A space operator is suggested rather than other operators to separate different search conditions. Therefore, the above example AA-BBB-123456 is suggested to input as AA BBB 123456.
The dot (.) operator will not be ignored like operators. For example, external_ip (1.1.1.1) and local_ip (2.2.2.2) can be searched with the "." value.
Filter allows users to define the search query. It can be used for both detection-type and incident-type events. Refer to Falcon Query Language (FQL) from Crowstrike's documentation for more information about the syntax.
The basic syntax is: property_name:<operator>'<value>'. The <operator> is optional to input.
For example, to search the hostname AA-BBB-123456 that does not have a local IP of 1.1.1.1, the filter expression would be device.hostname:'AA-BBB-123456'+device.local_ip:!'1.1.1.1'.
More complex expressions can be created by surrounding the expression with rounded brackets.
For example, to search for events with the host name AA-BBB-123456 and without a local IP of 1.1.1.1, or with a behavior_id of 1234, the filter expression would be (device.hostname:'AA-BBB-123456'+ device.local_ip:!'1.1.1.1'),behaviors.behavior_id:'1234'
The following are commonly used operators and their associated meanings:
+ = and
, = or
! = not equal to
Input
Input Parameter | Required/Optional | Description | Example |
Start Time | Optional | The start time of the time range to fetch events in UTC time format, based on the specified query time type. | 2022-10-01 00:00 |
End Time | Optional | The end time of the time range to fetch events in UTC time format, based on the specified query time type. | 2022-10-06 00:00 |
Event Type | Optional | The types of events to retrieve. The available event types are:
Due to the end of life of the CrowdStrike Legacy Detects API on September 30, 2025, as documented in the conversion guide, the Detection option and detections data for the Incident option will be deprecated. Only incident details and behaviors data are available. Use the Alert option instead. | Incident |
Query Time Type | Optional | The time field used to filter retrieved events, based on the selected event type. DETECTION The options available are:
By default, the time field used is Last Behaviour Time. INCIDENT The options available are:
By default, the time field used is Last Activity Time. ALERT The options available are:
By default time field used is Updated Time. | First Behavior Time |
Number of Event(s) Fetched | Optional | The maximum number of latest events to retrieve. The valid range is an integer between 1 and 500. When the value is outside the valid range or not provided, all events that match the search conditions are returned. | 10 |
Search Condition | Optional | The condition to perform a full text search across all metadata fields. This parameter is valid when the selected event type is Detection or Alert. | T1059.001 |
Filter | Optional | The query to filter results. See FQL syntax. This filter applies to all event types: Detection, Incident, and Alert. To search for alerts from a specific product (e.g., epp, idp, ods, mobile), use | assigned_to_name:'Admin'+status:'20' |
Tolerance Scope | Optional | A time window (in minutes) that extends the time range for fetching events by subtracting from the specified start time. Tolerance scope helps prevent data loss by accounting for API response delays caused by temporary server-side data unavailability—arising from processing and synchronization—from the vendor. With the tolerance scope applied, events will be fetched within the range of (Start Time - Tolerance Scope) to End Time. By default, the tolerance scope is set to 0. | 5 |
Output
To view the sample output data for all commands, refer to this article.
Fetch Event Field Mapping
See Field Mappings.
The CrowdStrike system integration includes pre-configured field mappings for the default event source.
The Default Event Source is the default system-provided set of field mappings applied when the fetch event command is executed. It includes a Main Event JSON Path, which is the JSONPath expression that points to the base array of event objects. The source field path continues from this array to locate the required data.
The Main Event JSON Path can be viewed by clicking on the Edit Main JSON Path button.
.png?inst-v=a916037b-9847-42e4-b4ba-0807570b75be)
Main Event JSON Path: $.resources
The resources array contains the event objects. Within each object, the key created_timestamp denotes the Event Time field. As such, the full JSONPath expression to extract the Event Time is $.resources.id.Event Source for Incidents
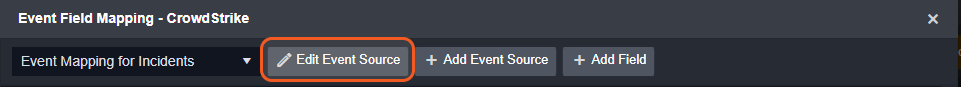
The D3 system configures the field mappings which are specific to the Incident-related events (e.g., Objectives and State). If a source field in the field mapping is not found, the corresponding field mapping will be ignored. Because the eventType field in the raw data for Incidents consistently has the value incident, these events can be identified by the Search String: {$.eventType}=incident. Click Edit Event Source to view the Search String.
Note: The Event Source for Incidents field mapping will be applied in addition to the Default Event Source field mapping for Incident-related events.
Event Source for Alerts
The D3 system configures the field mappings which are specific to the Alert-related events (e.g., Access File Names and Access File Paths). If a source field in the field mapping is not found, the corresponding field mapping will be ignored. Because the eventType field in the raw data for Alerts consistently has the value alert, these events can be identified by the Search String: {$.eventType}=alert. Click Edit Event Source to view the Search String.
Note: The Event Source for Alerts field mapping will be applied in addition to the Default Event Source field mapping for Alert-related events.
The pre-configured field mappings are detailed below:
Field Name | Source Field |
Default Event Source (Main Event JSON Path: $.resource) | |
Event Time | .created_timestamp |
Hostname | .device.hostname |
Destination IP address | .device.external_ip |
Source IP address | .device.local_ip |
Filename | .behaviors[*].filename |
Tactics | .behaviors[*].tactic |
Tactic ID | .behaviors[*].tactic_id |
Techniques | .behaviors[*].technique |
Technique ID | .behaviors[*].technique_id |
IOC Type | .behaviors[*].ioc_type |
IOC Value | .behaviors[*].ioc_value |
IOC Source | .behaviors[*].ioc_source |
Username | .behaviors[*].user_name |
User ID | .behaviors[*].user_id |
Severity Score | .behaviors[*].severity |
SHA256 | .behaviors[*].sha256 |
MD5 | .behaviors[*].md5 |
Severity | .max_severity_displayname |
Process ID | .behaviors[?(@.description!=''||@.description!=null)].triggering_process_graph_id |
Status | .status |
Event Time | .created_timestamp |
Update Time | .date_updated |
Start Time | .first_behavior |
Last Behavior Time | .last_behavior |
Device ID | .device.device_id |
File Path | .behaviors[*].filepath |
Sub Event | .behaviors |
Event Type | .behaviorType |
Webhook URL | .webhookURL |
Webhook Extra Info | .webhookExtraInfo |
Description | .description |
Document ID | .detection_id |
Process Command Line | .behaviors[*].cmdline |
Parent Process ID | .behaviors[*].parent_details.parent_process_graph_id |
Parent Process Command Line | .behaviors[*].parent_details.parent_cmdline |
Parent Process Hash SHA256 | .behaviors[*].parent_details.parent_sha256 |
Parent Process Hash MD5 | .behaviors[*].parent_details.parent_md5 |
Event Source for Incidents (Search String: {eventType}="incident") The search string format is {jsonpath}=value. If the value of the eventType key is incident in the event object under raw data, then the incident-related events will use the field mapping below. | |
Event Code | .incident_id |
Tactics | .tactics |
Techniques | .techniques |
Incident Name | .name |
Description | .description |
Status | .status |
Fine Score | .fine_score |
State | .state |
Incident Type | .incident_type |
Tag | .tags |
Username | .users |
Event Time | .created |
Hostname | .hosts[*].hostname |
Destination IP Address | .hosts[*].external_ip |
Source IP Address | .hosts[*].local_ip |
Update Time | .modified_timestamp |
Start Time | .start |
Last Behavior Time | .end |
Device ID | .host[*].device_id |
Objectives | .objectives |
Detection IDs | .detections[*].detection_id |
Filename | .detections[*].behaviors[*].filename |
File Path | .detections[*].behaviors[*].filepath |
SHA256 | .detections[*].behaviors[*].sha256 |
MD5 | .detections[*].behaviors[*].md5 |
Sub Event | .detections |
Webhook URL | .webhookURL |
Webhook Extra Info | .webhookExtraInfo |
Event Source for Alerts (Search String: {eventType}="alert") The search string format is {jsonpath}=value. If the value of the eventType key is alert in the event object under raw data, then the alert-related events will use the field mapping below. | |
Event Code | .id |
Event Name | .display_name |
Source Account ID | .source_account_object_sid |
Source Device IP address | .source_endpoint_ip_address |
Activity ID | .activity_id |
Tactics | .tactic |
Tactic ID | .tactic_id |
Techniques | .technique |
Technique ID | .technique_id |
Event Type | .type |
Severity | .severity_name |
SSO Application URI | .sso_application_uri |
Source Account Okta ID | .source_account_okta_id |
Source Account Azure ID | .source_account_azure_id |
Source Account Domain | .source_account_domain |
Source Device | .source_endpoint_host_name |
Source Username | .source_account_name |
Objective | .objective |
Location Country Code | .location_country_code |
Location Latitude | .location_latitude |
Location Longitude | .location_longitude |
Falcon Host Link | .falcon_host_link |
Confidence | .confidence |
UTC Event Time | .timestamp |
UpdateTime | .updated_timestamp |
Start Time | .timestamp |
Last Behavior Time | .end_time |
Event Internal Name | .name |
Webhook URL | .webhookURL |
Webhook Extra Info | .webhookExtraInfo |
Process Command Line | .cmdline |
Data Domains | .data_domains |
Host IP | .entities_full[*].EntitySummary:ip |
Device IP address | .device.local_ip |
Device Public IP Address | .device.external_ip |
Device MAC Address | .device.mac_address |
Operating System | .device.os_version |
Device Product Name | .device.system_product_name |
Device Groups | .device.groups |
Device Last Seen Time | .device.last_seen |
Accessed File Names | .files_accessed[*].filename |
Accessed File Paths | .files_accessed[*].filepath |
File Access Timestamps | .files_accessed[*].timestamp |
Filename | .filename |
File Path | .filepath |
Incident ID | .incident.id |
Incident Score | .incident.score |
Incident Start Time | .incident.start |
Incident End Time | .incident.end |
Process ID | .local_process_id |
File Hash MD5 | .md5 |
Parent Process Command Line | .parent_details.cmdline |
Parent Process Image Path | .parent_details.filepath |
Parent Process ID | .parent_details.process_id |
Parent Process File Hash MD5 | .parent_details.md5 |
Parent Process File Hash SH256 | .parent_details.sha256 |
Parent Process Name | .parent_details.filename |
Parent Process Time | .parent_details.timestamp |
Parent Process User | .parent_details.user_name |
Parent Local Process ID | .parent_details.local_process_id |
Grandparent Process Command Line | .grandparent_details.cmdline |
Grandparent Process File Path | .grandparent_details.filepath |
Grandparent Process ID | .grandparent_details.process_id |
Grandparent Process File Hash MD5 | .grandparent_details.md5 |
Grandparent Process File Hash SH256 | .grandparent_details.sha256 |
Grandparent Process Name | .grandparent_details.filename |
Grandparent Process Time | .grandparent_details.timestamp |
Grandparent Process User | .grandparent_details.user_name |
Grandparent Local Process ID | .grandparent_details.local_process_id |
Pattern Disposition Description | .pattern_disposition_description |
Pattern ID | .pattern_id |
Platform | .Platform |
Process ID | .process_id |
File Hash SHA1 | .sha1 |
File Hash SHA256 | .sha256 |
Source Product | .source_products |
Process Start Time | .process_start_time |
Process End Time | .process_end_time |
Scenario | .scenario |
Product | .product |
User Principal Name | .user_principal |
Username | .user_name |
Description | .description |
Hostname | .entities_full[*].EntitySummary:host |
Agent ID Entity | .entities_full[*].EntitySummary:agent_ids |
User Name Entity | .entities_full[*].EntitySummary:username |
User Security ID | .entities_full[*].EntitySummary:user_sid |
Command Line Entity | .entities_full[*].CommandLine |
Filename Entity | .entities_full[*].EntitySummary:file_name |
Image Filename Entity | .entities_full[*].EntitySummary:image_file_name |
Process Entity | .entities_full[*].EntitySummary:process |
Process Hash SHA256 | .entities_full[?(@.domain=='Process')].EntitySummary:sha256 |
File MD5 Hash Entity | .entities_full[?(@.domain=='File')].EntitySummary:md5 |
File SHA256 Hash Entity | .entities_full[?(@.domain=='File')].EntitySummary:sha256 |
Status | .status |
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Fetch Event failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: Invalid filter expression supplied. |
Error Sample Data Find Events failed. Status Code: 400. Error Message: Invalid filter expression supplied. |
Fetch Incident
Retrieves incidents from CrowdStrike based on specified criteria.
Input
Input Parameter | Required/Optional | Description | Example |
Start Time | Optional | The start time (in UTC) of the incident time property value. By default, the value is 24 hours before End Time. | 08/01/2025 12:00 AM |
End Time | Optional | The end time (in UTC) of the incident time property value. By default, the value is the current time. | 08/23/2025 12:00 AM |
Query Time Type | Optional | The incident time property to apply the time range query. Available options are:
By default, the value is set to Updated Time. | Updated Time |
Number of Incident(s) Fetched | Optional | The maximum number of incidents to return. By default, the value is 100. Set a reasonable limit to avoid API exhaustion or timeouts. Other parameters should be used to further refine results. | 100 |
FQL Filters Format | Optional | The input format for Incidents Filter Options and Alerts Filter Options. Available options are:
The command converts the filter options into an FQL filter expression. When the JSON object format is used, a logical conjunction (and) is applied across multiple properties, and the <operator> always applies equal-to for <property> and <value> pairs. Use the default FQL syntax for complex filter options and combinations. See FQL syntax for the FQL syntax details. | Filter Expression |
Incidents Filter Options | Optional | The incident filter options. The available options are listed in the Incident Detection and Alert Monitoring APIs. Time-related options are ignored. | FILTER EXPRESSION
CODE
JSON OBJECT
JSON
|
Alerts Filter Options | Optional | The incident alerts filter options. The available options are listed in the Incident Detection and Alert Monitoring APIs. When a JSON object includes the q property with a string value, the query performs a full search across all indexed alert metadata fields (such as display_name, description, filename, etc.) for the specified string. | FILTER EXPRESSION
CODE
JSON OBJECT
JSON
|
Number of Alerts to Retrieve | Optional | The maximum number of alerts to retrieve for a single incident. This controls data volume when many alerts are ingested. By default, all alerts for each incident are retrieved. | 10 |
Output
To view the sample output data for all commands, refer to this article.
Incident Field Mapping
For this integration, the default incident fields in D3 SOAR contain built-in source fields.
Event and Incident Intake Field Mapping
See Field Mappings.
Incident field mapping is required.
Incident Main JSON Path: $.resources
The pre-configured field mappings are detailed below:
Field Name | Source Field |
Title | .objectives |
Description | User-defined |
Severity | User-defined. |
Incident Type * | User-defined |
Incident Creator | User-defined |
Incident Owner | User-defined |
Investigation Playbook | User-defined |
Due In Date | User-defined |
Origin ID | User-defined |
Unique Key | .incident_id |
Tactics | .tactics |
Techniques | .techniques |
Event Field Mappings
Incident Event JSON Path: $.alerts
The pre-configured event field mappings are detailed below:
Field Name | Source Field |
Alert Event Source for Incident (Search String: {$.eventType}=incidentAlert) The search string format is {$.eventType}=incidentAlert. If the value of the eventType key is incidentAlert in the event object under raw data, then the incident-alert-related events will use the field mapping below. | |
Document ID | .composite_id |
Unique Event Key | .composite_id |
Event name | .display_name |
Start Time | .timestamp |
Event Type | .type |
Status | .status |
Severity | .severity |
Severity Name | .severity_name |
Description | .description |
Agent ID | .agent_id |
Aggregate ID | .aggregate_id |
Confidence Score | .confidence |
UTCEventTime | .timestamp |
UpdateTime | .updated_timestamp |
Event Internal Name | .name |
Objective | .objective |
Pattern ID | .pattern_id |
Platform | .platform |
Process ID | .process_id |
File Hash SHA1 | .sha1 |
File Hash SHA256 | .sha256 |
Source Product | .source_products |
Process Start Time | .process_start_time |
Process End Time | .process_end_time |
Scenario | .scenario |
Product | .product |
Username | .user_name |
Process command line | .cmdline |
Data Domains | .data_domains |
Tactics | .tactic |
Tactic ID | .tactic_id |
Techniques | .technique |
Technique ID | .technique_id |
Tree ID | .tree_id |
Tree Root | .tree_root |
Falcon Host Link | .falcon_host_link |
Filename | .filename |
Filepath | .filepath |
Incident ID | .incident.id |
Incident Score | .incident.score |
Incident Start Time | .incident.start |
Incident End Time | .incident.end |
Process ID | .local_process_id |
File Hash MD5 | .md5 |
Hostname | .device.hostname |
Device IP address | .device.local_ip |
External IP | .device.external_ip |
Device MAC address | .device.mac_address |
Operating system | .device.os_version |
Device product name | .device.system_product_name |
Device Groups | .device.groups |
Device Last Seen Time | .device.last_seen |
Parent process commandLine | .parent_details.cmdline |
Parent process image path | .parent_details.filepath |
Parent process ID | .parent_details.process_id |
Parent Process File Hash MD5 | .parent_details.md5 |
Parent Process File Hash SH256 | .parent_details.sha256 |
Parent process name | .parent_details.filename |
Parent Process Time | .parent_details.timestamp |
Parent Process User | .parent_details.user_name |
Parent Local Process ID | .parent_details.local_process_id |
Grandparent Process CommandLine | .grandparent_details.cmdline |
Grandparent Process File Path | .grandparent_details.filepath |
Grandparent Process ID | .grandparent_details.process_id |
Grandparent Process File Hash MD5 | .grandparent_details.md5 |
Grandparent Process File Hash SH256 | .grandparent_details.sha256 |
Grandparent Process Name | .grandparent_details.filename |
Grandparent Process Time | .grandparent_details.timestamp |
Grandparent Process User | .grandparent_details.user_name |
Grandparent Local Process ID | .grandparent_details.local_process_id |
Pattern Disposition Description | .pattern_disposition_description |
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Fetch Incident failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The value for parameter (Number of Incident(s) Fetched) is invalid. |
Error Sample Data Fetch Incident failed. Status Code: 400. Message: The value for parameter (Number of Incident(s) Fetched) is invalid. |
Find Host Groups
Retrieves information about a host group, including its members, based on the provided name(s) of the host group(s).
Input
Input Parameter | Required/Optional | Description | Example |
Host Group Names | Optional | The names of the host groups to retrieve. If this parameter is not defined, all host groups will be returned. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Find Host Groups failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Host Group Names Not Found. |
Error Sample Data Find Host Groups failed. Status Code: 404. Message: Host Group Names Not Found. |
Find Hosts
Retrieves host information according to the specified field name and value.
READER NOTE
If no parameter has been filled, all retrievable hosts will be returned.
Value is an optional parameter to run this command.
The desired value can be obtained in advance or retrieved using the Fetch Event command with defined filters. The value is located in the raw data.
The input Field Name and Value must match. Otherwise, the command will run successfully with no returned results.
The screenshot below provides examples of some field names and values by running the Fetch Event command:
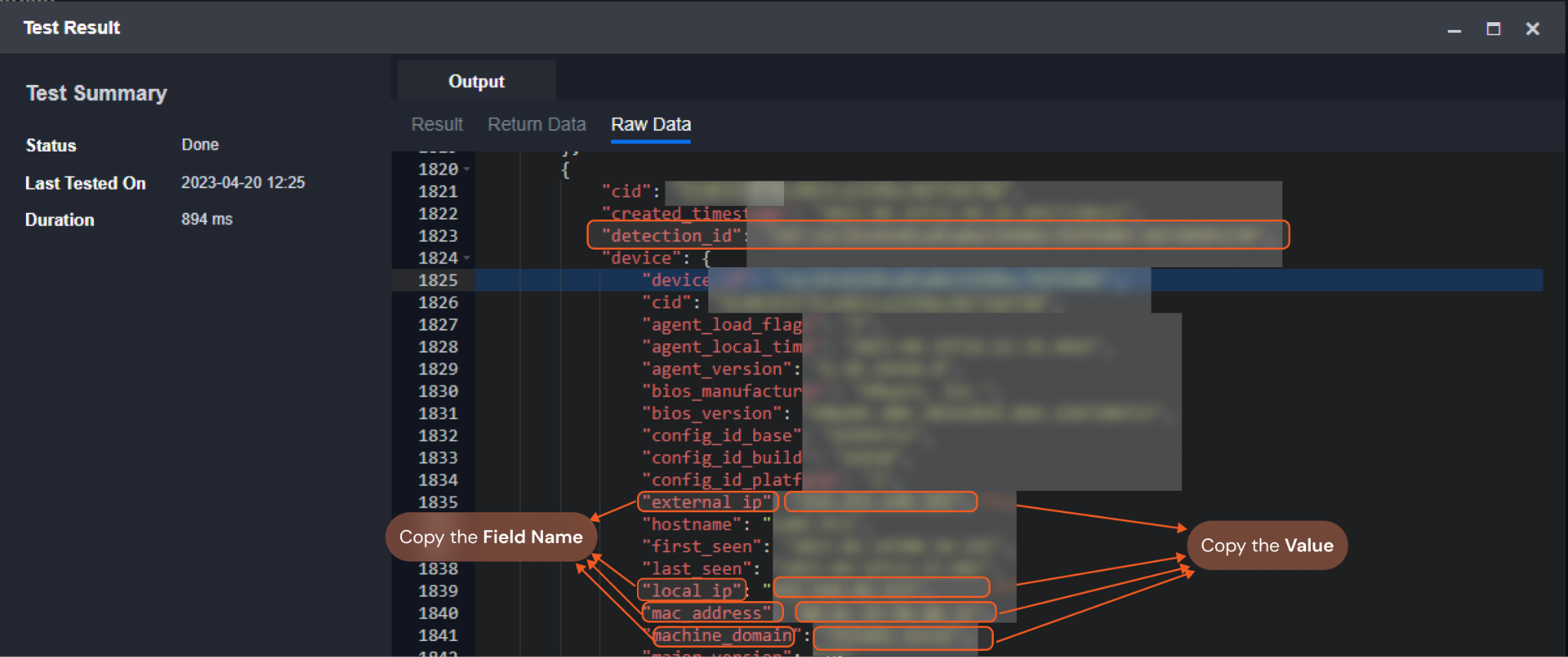
Input
Input Parameter | Required/Optional | Description | Example |
Field Name | Optional | The name of the field (e.g. local_ip or hostname) to retrieve. The hostname is not case-sensitive. For the available field names, see Device Filters. | local_ip |
Values | Optional | The list of values corresponds to the specified field name. This parameter will be omitted when the Field Name parameter is not defined. |
JSON
|
Limit | Optional | The maximum number of records to return. The parameter need to be in range [1-5000]. The default value is 100. | 101 |
Offset | Optional | The zero-based position of the first record to return. The default value is 0. | 0 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Find Hosts failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: Invalid filter expression supplied. |
Error Sample Data Find Hosts failed. Status Code: 400, Error Message: Invalid filter expression supplied. |
Find IOC IDs
Finds the IDs of the specified indicator entities.
READER NOTE
At least one parameter must be filled.
Value is an optional parameter to run this command.
Ensure that the input value is already present in the CrowdStrike system. Random values are not supported.
The desired value can be obtained in advance or retrieved using the Fetch Event command with defined filters. The value is located in the raw data.
To retrieve IOC IDs, when all parameters are provided, ensure that the Type, Action, and Severity match the specified value. Otherwise, the command will succeed but return no results.
If the search inputs do not exist, the command will also succeed but return no results.
Input
Input Parameter | Required/Optional | Description | Example |
Type | Optional | The indicator type of the entity. | SHA256 |
Value | Optional | The string value of the IOCs. | abc.com |
Action | Optional | The action to take when a host observes the custom IOC. The following are accepted inputs:
| Detect |
Severity | Optional | The severity level to apply to this indicator. This field is required when the selected action is Prevent or Detect. It is optional for No Action. | High |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Find IOC IDs failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: Access denied, invalid bearer token. |
Error Sample Data Find IOC IDs failed. Status Code: 401, Error Message: Access denied, invalid bearer token. |
Find IOC Observed Hosts
Finds hosts associated with observed custom IOC(s) in CrowdStrike.
READER NOTE
IOCs and IOC type are required parameters to run this command.
The desired IOC and IOC Type can be obtained in advance or retrieved using the Fetch Event command with defined filters. The value is located in the raw data.
The input IOC and IOC Type must match. Otherwise, the command will succeed but return no results.
The screenshot below provides examples of some IOCs and IOC Types:
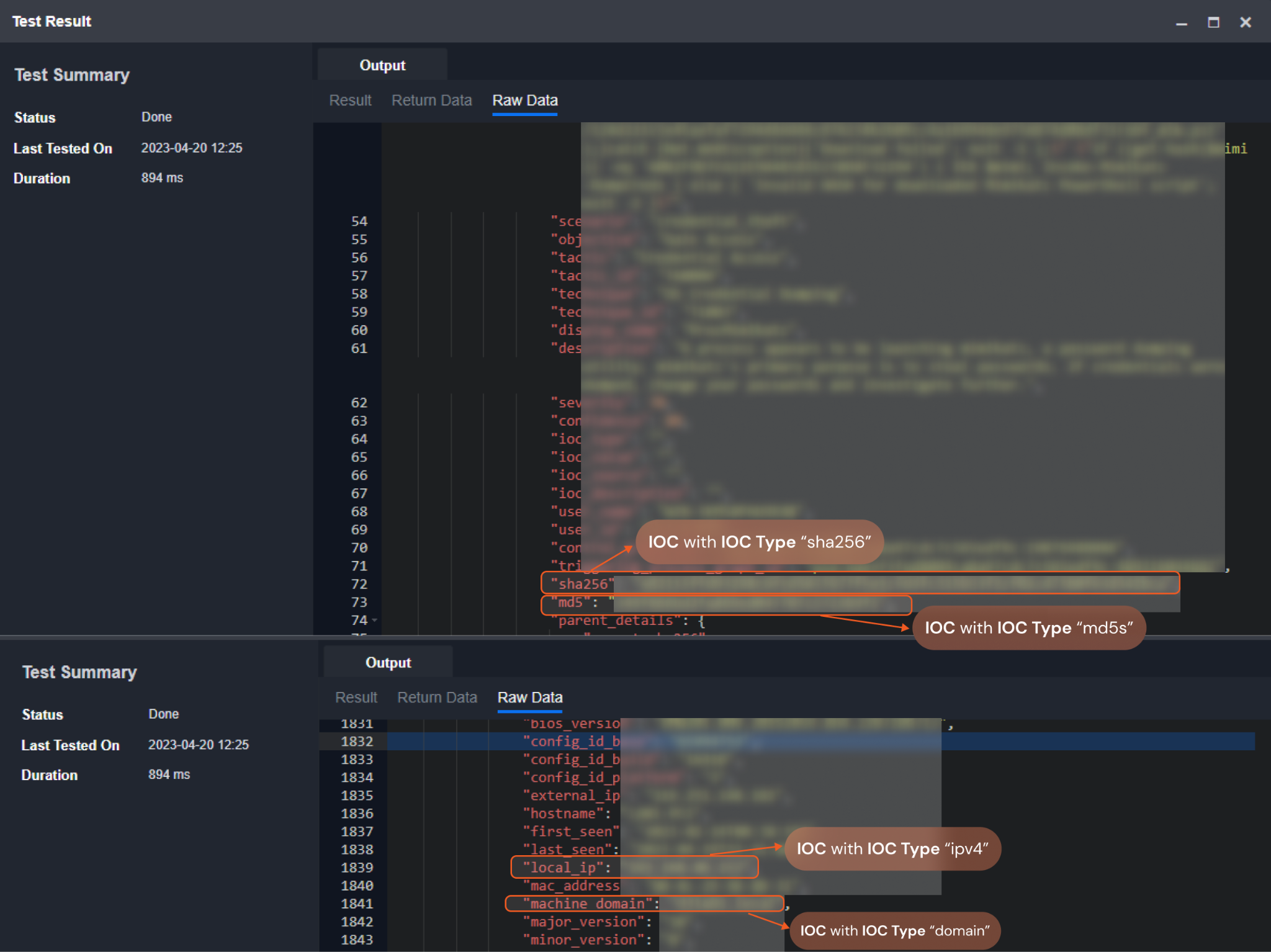
Input
Input Parameter | Required/Optional | Description | Example |
IOCs | Required | The value of the IOC to search. |
JSON
|
IOC Type | Required | The IOC type to search. The available IOC types are SHA256, SHA1, MD5, Domain, IPV4, IPV6 and Ignored. | SHA256 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Find IOC Observed Host failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: Resource not found. |
Error Sample Data Find IOC Observed Host failed. Status Code: 404, Error Message: Resource not found. |
Find Process
Queries processes and returns info associated with the specified IOC on a host.
READER NOTE
IOC, IOC Type, and Endpoint ID are required parameters to run this command.
The desired IOC and IOC Type can be obtained in advance or retrieved using the Fetch Event command with defined filters. The value is located in the raw data.
Run the Find Hosts command to obtain the Endpoint ID. Endpoint IDs can be found in the raw data at the path $.resources.
The input IOC, IOC Type and Endpoint ID must match. Otherwise, the command will run successfully with no returned results.
If the input IOC does not have a process, the error message "404 resource not found" will return.
Here is an example of obtaining IOCs: IOC Types=Sha256 and Endpoint ID:
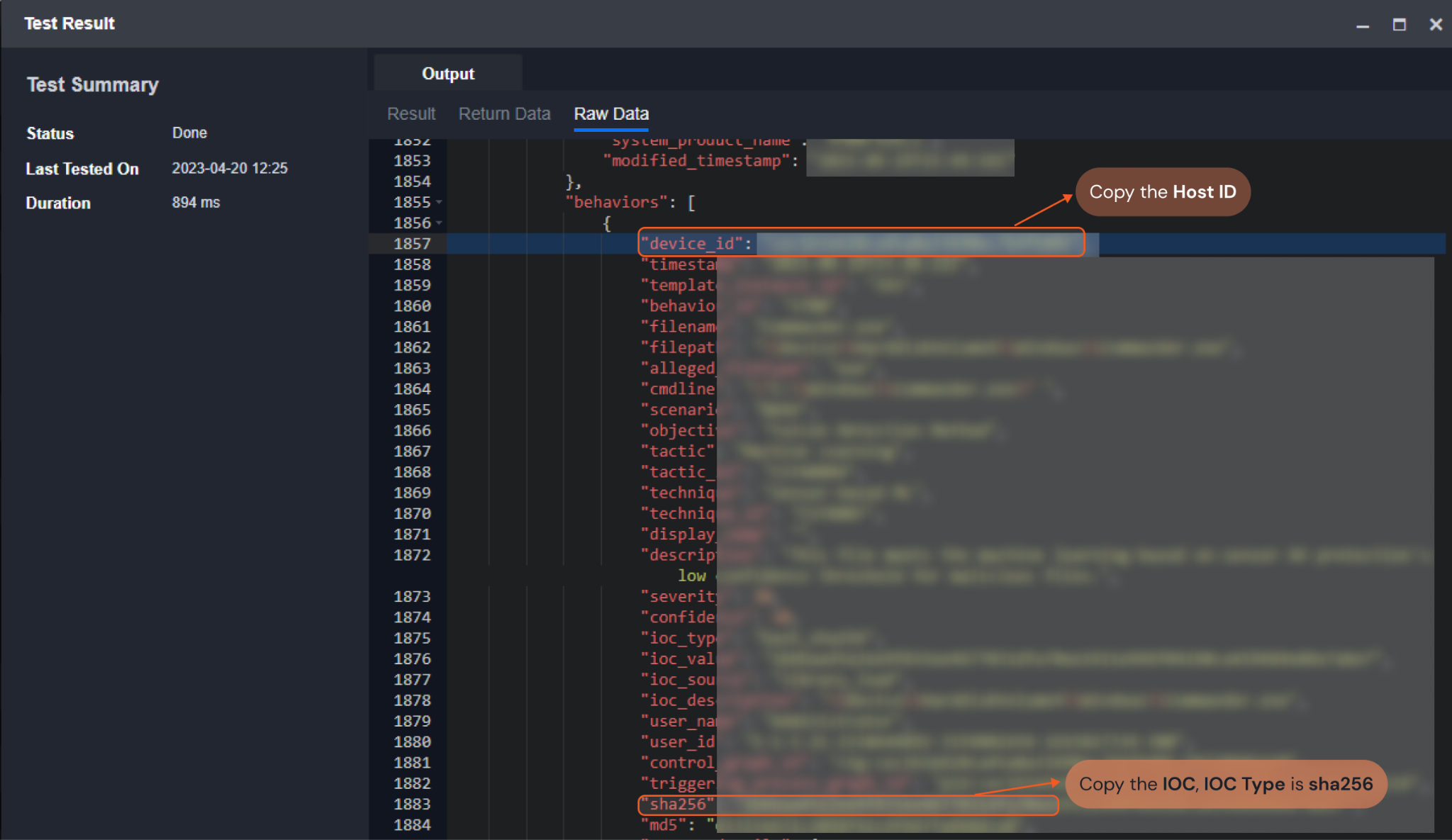
Input
Input Parameter | Required/Optional | Description | Example |
IOC | Required | The value of the IOC to search. | ***** |
IOC Type | Required | The IOC type to search. The available IOC types are SHA256, MD5, Domain, IPV4, and IPV6. | SHA256 |
Endpoint ID | Required | The ID of the endpoint to search processes from. Endpoint IDs can be obtained using the Find Hosts command. | ***** |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Find Process failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: Resource not found. |
Error Sample Data Find Process failed. Status Code: 404, Error Message: Resource not found. |
Get Behaviors For Incidents
Retrieves behavioral information from the specified incident(s) in CrowdStrike.
READER NOTE
Incident IDs is a required parameter to run this command.
The desired Incident IDs can be obtained in advance or retrieved using the Fetch Event command Event Type set to Incident. Incident IDs can be found in the raw data at the path $.resources[*].incident_id.
Input
Input Parameter | Required/Optional | Description | Example |
Incident IDs | Required | The ID(s) of the incident(s) to retrieve detection information. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Behaviors For Incidents failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: Request failed when getting behaviours detail. |
Error Sample Data Get Behaviors For Incidents failed. Status Code: 400. Error Message: Request failed when getting behaviours detail. |
Get Detections For Incidents (Deprecated)
Retrieves detection information from the specified incident(s) in CrowdStrike.
DEPRECATION
This command will be retired on September 30, 2025, with the decommissioning of the Detects API. Use the "Update Alerts" command instead.
Input
Input Parameter | Required/Optional | Description | Example |
Incident IDs | Required | The ID(s) of the incident(s) to retrieve detection information. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Detections For Incidents failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404 |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Incident ID Not Found. |
Error Sample Data Get Detections For Incidents failed. Status Code: 404. Message: Incident ID Not Found. |
Get Endpoint Info by ID
Returns endpoint details of the given endpoint ID in CrowdStrike. Note: CrowdStrike is planning to deprecate version 1 of the API on or after February 9, 2023. It is recommended to use API version 2 to run this command.
READER NOTE
Endpoint IDs is a required parameter to run this command.
Run the Find Hosts command to obtain the Endpoint IDs. Endpoint IDs can be found in the raw data at the path $.resources.
Input
Input Parameter | Required/Optional | Description | Example |
Endpoint IDs | Required | The IDs of the endpoints to retrieve details. Endpoint IDs can be obtained using the Find Hosts command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Endpoint Info by ID failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: No matching host found for ID a58****4789****615 |
Error Sample Data Get Endpoint Info by ID failed. Status Code: 404, Error Message: No matching host found for ID a58****4789****615. |
Get Endpoint Info by IP
Returns endpoint details of the given endpoint IP in CrowdStrike. Note: CrowdStrike is planning to deprecate version 1 of the API on or after February 9, 2023. It is recommended to use API version 2 to run this command.
READER NOTE
Endpoint IPs is a required parameter to run this command.
The desired Endpoint IPs can be obtained in advance or retrieved using the Fetch Event command with defined filters. The values can be found in the raw data, under the "local_ip" key.
Input
Input Parameter | Required/Optional | Description | Example |
Endpoint IPs | Required | The IPs of the endpoints to retrieve details. Endpoint IPs can be obtained using the Fetch Event command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Endpoint Info by IP failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: Cannot get host by given host IP. |
Error Sample Data Get Endpoint Info by IP failed. Status Code: 404. Error Message: Cannot get host by given host IP. |
Get Host Info by Names
Returns host details for the specified host names in CrowdStrike.
Input
Input Parameter | Required/Optional | Description | Example |
Host Names | Optional | The host names for which to retrieve details. By default, all hosts are returned regardless of their names. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Host Info by Names failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Authentication failed, please check your connection fields. |
Error Sample Data Get Host Info by Names failed. Status Code: 401. Message: Authentication failed, please check your connection fields. |
Get Host Vulnerabilities
Retrieves host vulnerabilities by searching for any vulnerabilities associated with the specified host(s). Note: At least one parameter must be defined.
READER NOTE
Host Names Or IPs, Host Group Names and Host Tags are optional parameters to run this command.
At least one parameter must be filled.
The desired Host Names or IPs can be obtained in advance or retrieved using the Fetch Event command with defined filters. Host Names can be found in the returned raw data, under the "hostname" key. Host IPs can be found in the returned raw data, under the "local_ip" key.
Run the Find Host Groups command to obtain the Host Group Names. Host Group Names can be found from the raw data at the path $.resources[*].name.
Run the Get Endpoint Info By IP or Get Endpoint Info By ID commands to obtain the Host Tags. Host Tags can be found in the returned raw data under the "tags" key.
Input
Input Parameter | Required/Optional | Description | Example |
Host Names Or IPs | Optional | The internal IP addresses of names of the hosts to retrieve associated vulnerabilities. |
JSON
|
Host Group Names | Optional | The names of the host groups to retrieve associated vulnerabilities. Host Group Names can be obtained using the Find Host Groups command. |
JSON
|
Host Platform | Optional | The operating system platform of the hosts to retrieve associated vulnerabilities. | Linux |
Host Tags | Optional | The tags of the hosts to retrieve associated vulnerabilities. Host tags can be obtained using the Get Endpoint Info By IP or Get Endpoint Info By ID commands. Note: Host tags are case-sensitive. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Host Vulnerabilities failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: Invalid hostNamesOrIPs. |
Error Sample Data Get Host Vulnerabilities failed. Status Code: 400. Error Message: Invalid hostNamesOrIPs. |
Get Incident Details
Retrieves details for the specified incidents.
READER NOTE
Incident IDs is a required parameter to run this command.
The desired Incident IDs can be obtained in advance or retrieved using the Fetch Event command Event Type set to Incident. Incident IDs can be found in the raw data at the path $.resources[*].incident_id.
Input
Input Parameter | Required/Optional | Description | Example |
Incident IDs | Required | The IDs of the incidents for which to retrieve details. Incident IDs can be obtained using the Fetch Event command with the Event Type set to Incident. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Incident Details failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Invalid incident id=ind:*****5541. |
Error Sample Data Get Incident Details failed. Status Code: 400. Message: Invalid incident id=ind:*****5541. |
Get IOCs
Returns detailed info of the specified indicator(s).
READER NOTE
IDs is a required parameter to run this command.
Run the Find IOC IDs command to obtain the IDs. IDs can be found in the raw data at the path $.resources.
Input
Input Parameter | Required/Optional | Description | Example |
IDs | Required | The ID(s) of the indicator(s) to retrieve details. Indicator IDs can be obtained using the Find IOC IDs command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get IOCs failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: No resource found with ID ***. |
Error Sample Data Get IOCs failed. Status Code: 404 Error Message: No resource found with ID ***. |
Get Process Detail
Returns details of the specified process(es) in CrowdStrike.
READER NOTE
Process ID is a Required parameter to run this command.
Run the Find Process command to obtain the Process ID. Process IDs can be found in the raw data at the path $.resources.
Input
Input Parameter | Required/Optional | Description | Example |
Process ID | Required | The IDs of the processes to retrieve details. Process IDs can be obtained using the Find Process command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Process Detail failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: Resource not found. |
Error Sample Data Get Process Detail failed. Status Code: 404 Error Message: Resource not found. |
Get Process Detail by IOC
Returns process details of the specified IOC in CrowdStrike.
READER NOTE
IOC, IOC Type and Endpoint ID are required parameters to run this command.
The desired IOC and IOC Type can be obtained in advance or retrieved using the Fetch Event command with defined filters. The value is located in the raw data.
Run the Find Hosts command to obtain the Endpoint ID. Endpoint IDs can be found in the raw data at the path $.resources.
Here are some examples of IOCs and IOC Types:
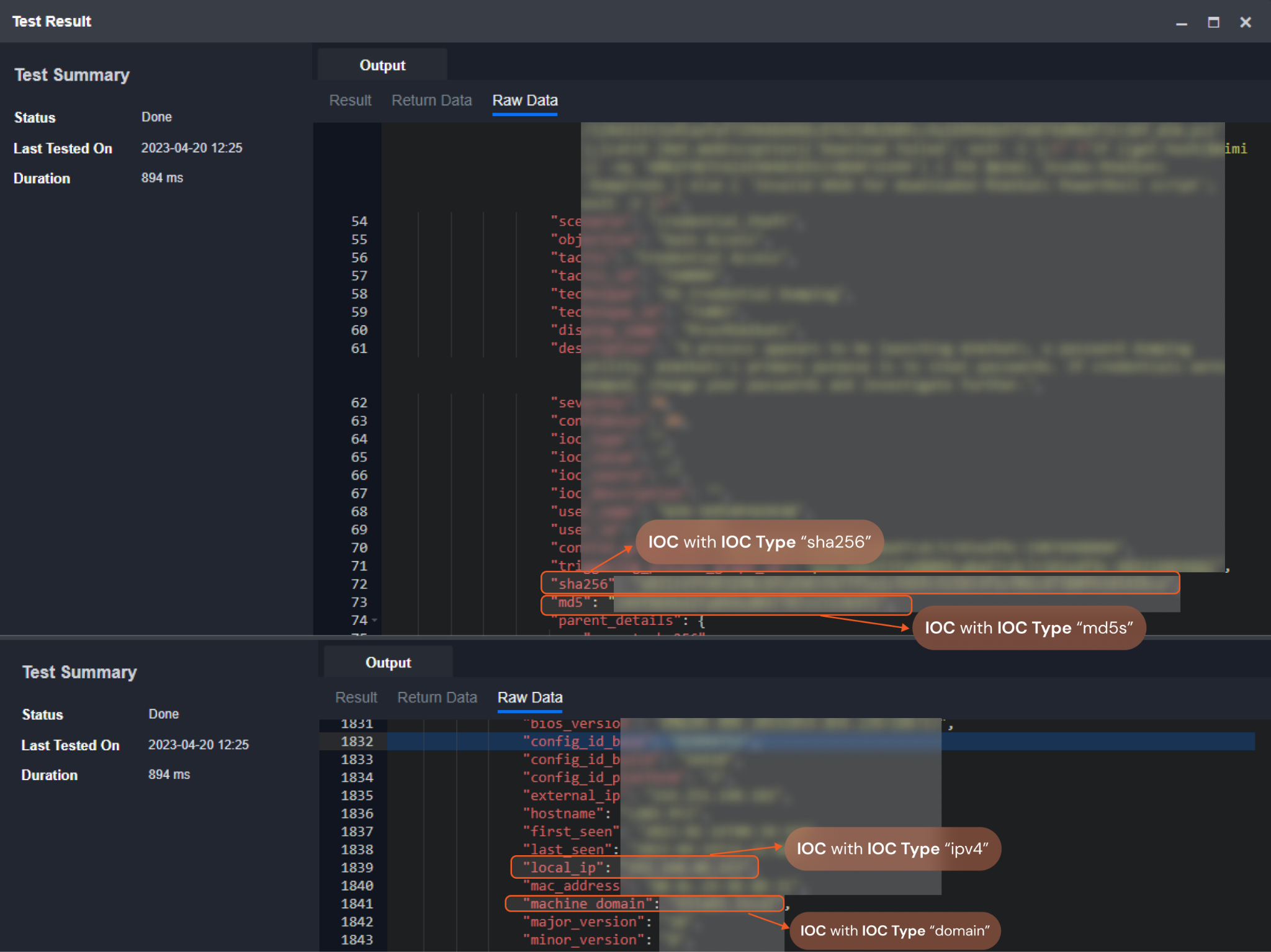
Input
Input Parameter | Required/Optional | Description | Example |
IOC | Required | The value of the IOC to retrieve process details. | *** |
IOC Type | Required | The IOC type of the specified value. The available IOC types are SHA256, MD5, Domain, IPV4, and IPV6. | SHA256 |
Endpoint ID | Required | The ID of the endpoint to retrieve process details. Endpoint IDs can be obtained using the Find Hosts command. | *** |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Process Detail by IOC failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: Resource not found. |
Error Sample Data Get Process Detail by IOC failed. Status Code: 404. Error Message: Resource not found. |
Get Scan Results
Retrieves details about the specified scans (one-time ad hoc scan and scheduled scan), including the details about malicious files found during the scan.
READER NOTE
Scan IDs is a required parameter to run this command.
Run the List Scans command to obtain the Scan IDs. Scan IDs can be found in the raw data at the path $.resources.
Input
Input Parameter | Required/Optional | Description | Example |
Scan IDs | Required | The IDs of the scans to retrieve results. Scan IDs can be obtained using the List Scans command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Scan Results failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Scan ID Not Found. |
Error Sample Data Get Scan Results failed. Status Code: 404. Message: Scan ID Not Found. |
Get Vulnerability Details
READER NOTE
Vulnerability IDs is a required parameter to run this command.
Run the List Vulnerabilities or Get Host Vulnerabilities commands to obtain the Vulnerability IDs. Vulnerability IDs can be found in the raw data at the path $.resources[*].id.
This command requires API Version v2 for the connection. If the API Version is configured to v1, the connection will not be available to run this command.
Refer to Step 3h 4 of Configuring D3 SOAR to Work with CrowdStrike on changing a connection's API Version.
Retrieves vulnerability details for the specified vulnerability IDs.
Input
Input Parameter | Required/Optional | Description | Example |
Vulnerability IDs | Required | The IDs of the vulnerabilities to retrieve details. Vulnerability IDs can be obtained using the List Vulnerabilities or Get Host Vulnerabilities commands. You can enter a maximum of 400 Vulnerability IDs. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Vulnerability Details failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Invalid vulnerability id. |
Error Sample Data Get Vulnerability Details failed. Status Code: 400. Message: Invalid vulnerability id. |
Get Vulnerability Evaluation Logics
Retrieves details on evaluation logic for products related to a vulnerability.
READER NOTE
Host IDs is a required parameter to run this command.
Host IDs must be obtained using the List Vulnerabilities or Search Vulnerable Hosts By CVE command. This ensures that the command uses vulnerable hosts in the environment.
Run the List Vulnerabilities or Search Vulnerable Hosts By CVE command to obtain the Host IDs. Host IDs can be found in the raw data returned by the:
List Vulnerabilities command, at the path $.resources[*].id
Search Vulnerable Hosts By CVE command, at the path $.resources[*].aid.
Input
Input Parameter | Required/Optional | Description | Example |
Host IDs | Optional | The IDs of the hosts to retrieve vulnerability evaluation logics. Host IDs can be obtained using the List Vulnerabilities or Search Vulnerable Hosts By CVE commands. |
JSON
|
Updated From | Optional | The timestamp to filter vulnerability evaluation logics that are updated at or after this time. | 2023-04-20 00:00 |
Updated Before | Optional | The timestamp to filter vulnerability evaluation logics that are updated at or before this time. If this parameter is not defined, the default value is the current time. | 2023-04-21 00:00 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Vulnerability Evaluation Logics failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: access denied, authorization failed. |
Error Sample Data Get Vulnerability Evaluation Logics failed. Status Code: 400. Message: access denied, authorization failed. |
Isolate Host
Quarantines hosts in CrowdStrike.
READER NOTE
Host IDs is a required parameter to run this command.
Run the Find Hosts command to obtain the Host IDs. Host IDs can be found in the raw data at the path $.resources.
This command requires API Version v2 for the connection. If the API Version is configured to v1, the connection will not be available to run this command.
Refer to Step 3h 4 of Configuring D3 SOAR to Work with CrowdStrike on changing a connection's API Version.
Attempting to isolate the same host twice will return the "Device ____ is not eligible to perform containment action" error message.
Input
Input Parameter | Required/Optional | Description | Example |
Host IDs | Required | The IDs of the hosts to isolate. Host IDs can be obtained using the Find Hosts command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Isolate Host failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: No matching host found for ID b2443tg****hbha****nh34c. |
Error Sample Data Isolate Host failed. Status Code: 404 Error Message: No matching host found for ID b2443tg****hbha****nh34c. |
List Host Group Members
Retrieves members from the specified host group.
READER NOTE
Host Group ID is an optional parameter to run this command.
Run Find Host Groups command to obtain the Host Group ID. Host Group IDs can be found in the raw data at the path $.resources[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Host Group ID | Optional | The ID of the host group to retrieve group members. Host Group IDs can be obtained using the Find Host Groups command. | *** |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Host Group Members failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Host Group ID Not Found. |
Error Sample Data List Host Group Members failed. Status Code: 404. Message: Host Group ID Not Found. |
List Quarantine Files
Retrieves quarantine file metadata that matches the provided filter criteria.
Input
Input Parameter | Required/Optional | Description | Example |
Filter | Optional | The FQL query specifying the filter parameters. Special value '*' means to not filter on anything. Filter term criteria: status, adversary_id, device.device_id, device.country, device.hostname, behaviors.behavior_id, behaviors.ioc_type, behaviors.ioc_value, behaviors.username, behaviors.tree_root_hash. Filter range criteria:, max_severity, max_confidence, first_behavior, last_behavior. Please refer to Falcon Query Language (FQL) for more information about the query syntax. | hostname:'LA***C2' + state:'quarantined' |
Query | Optional | The match phrase_prefix query criteria; included fields: _all (all filter string fields), sha256, state, paths.path, paths.state, hostname, username, date_updated, date_created. To query a specific quarantined file hash, input the SHA256 hash value with this parameter. | 115********aa7 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Quarantine Files failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: Failed to get quarantined file IDs. |
Error Sample Data List Quarantine Files failed. Status Code: 400. Error Message: Failed to get quarantined file IDs. |
List Real Time Response Script
Returns a comprehensive list of all custom scripts available to the user that can be executed through the Execute Batch Command.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Real Time Response Script failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: Failed to generate access token for clientID |
Error Sample Data List Real Time Response Script failed. Status Code: 400. Error Message: Failed to generate access token for clientID. |
List Scans
Retrieves the IDs of your on-demand scans. These IDs can be used to retrieve scans.
Input
Input Parameter | Required/Optional | Description | Example |
Status | Optional | The status to filter the returned scans. If this parameter is not defined. If this parameter is not defined, scans with any status will be returned. | Completed |
Minimum Severity | Optional | The minimum severity level to filter the returned scans. A valid input value is an integer between 0 and 100. If this parameter is not specified, scans with any severity will be returned. | 50 |
Scan Type | Optional | The scan type (i.e., Ad Hoc Scan or Scheduled Scan) to filter the returned scans. If this parameter is not specified, scans categorized under either scan types will be returned. | Scheduled |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Scans failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: access denied, authorization failed. |
Error Sample Data List Scans failed. Status Code: 403. Message: access denied, authorization failed. |
List Scheduled Scans
Retrieves a list of scheduled scans and their details. To retrieve scan results, use the Get Scan Result command.
Input
Input Parameter | Required/Optional | Description | Example |
Description | Optional | The scan description to filter the returned scheduled scans. If the Scheduled Scan IDs parameter is defined, this parameter will be omitted. | test OdS Schedule scan Host0223b |
Scheduled Scan IDs | Optional | The IDs of the scheduled scans to return. If this parameter is defined, the Description parameter will be omitted. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Scheduled Scans failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Scheduled Scan IDs Not Found. |
Error Sample Data List Scheduled Scans failed. Status Code: 404. Message: Scheduled Scan IDs Not Found. |
List Vulnerabilities
Searches and returns vulnerability instance data, which includes details on remediation, host, and CVE. Results are returned based on the specified filter criteria.
Input
Input Parameter | Required/Optional | Description | Example |
Filter | Optional | The filter condition defined in Falcon Query Language (FQL). For more information about the FQL syntax, see Falcon Query Language (FQL). If this parameter is not defined, the 100 most recently created vulnerabilities with an "Open" status will be returned. | cve.severity: ['CRITICAL','HIGH'] + status: 'open' |
Limit | Optional | The maximum number (between 1 and 5000) of vulnerabilities to return. The default value is 100. | 10 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Vulnerabilities failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: invalid input data. |
Error Sample Data List Vulnerabilities failed. Status Code: 400. Message: invalid input data. |
Quarantine Endpoint by ID
Quarantines endpoints by endpoint ID in CrowdStrike.
READER NOTE
Endpoint IDs is a required parameter to run this command.
Run the Find Hosts command to obtain the Endpoint IDs. Endpoint IDs can be found in the raw data at the path $.resources.
This command requires API Version v2 for the connection. If the API Version is configured to v1, the connection will not be available to run this command.
Refer to Step 3h 4 of Configuring D3 SOAR to Work with CrowdStrike on changing a connection's API Version.
If the input endpoint has already been isolated using the Isolate Host command, this command will not be able to quarantine that host.
Input
Input Parameter | Required/Optional | Description | Example |
Endpoint IDs | Required | The IDs of the endpoints to quarantine. Endpoint IDs can be obtained using the Find Hosts command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Quarantine Endpoint by ID failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: No matching host found for ID ***. |
Error Sample Data Quarantine Endpoint by ID failed. Status Code: 404 Error Message: No matching host found for ID ***. |
Quarantine Endpoint by IP
Quarantines endpoints by endpoint IP in CrowdStrike.
READER NOTE
Endpoint IPs is a required parameter to run this command.
The desired Endpoint IPs can be obtained in advance or retrieved using the Fetch Event command with defined filters. The values can be found in the raw data, under the "local_ip" key.
Input
Input Parameter | Required/Optional | Description | Example |
Endpoint IPs | Required | The IP addresses of the endpoints to quarantine. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Quarantine Endpoint by IP failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: Host IP Not Found. |
Error Sample Data Quarantine Endpoint by IP failed. Status Code: 404. Error Message: Host IP Not Found. |
Refresh Session
Refreshes a session timeout on a specified host.
READER NOTE
Host ID is a required parameter to run this command.
Run the Find Hosts command to obtain the Host ID. Host IDs can be found in the raw data at the path $.resources.
Input
Input Parameter | Required/Optional | Description | Example |
Host ID | Required | The ID of the host agent to refresh its RTR (Real Time Response) session. This action will retrieve the existing session for the user who is calling on this particular host. Host IDs can be obtained using the Find Hosts command. | ***** |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Refresh Session failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: Host ID Not Found. |
Error Sample Data Refresh Session failed. Status Code: 404. Error Message: Host ID Not Found. |
Run Batch Get
Batch executes a "get" command across hosts to retrieve files.
READER NOTE
Host IDs is a required parameter to run this command.
Run the Find Hosts command to obtain the Host IDs. Host IDs can be found in the raw data at the path $.resources.
Input
Input Parameter | Required/Optional | Description | Example |
Host IDs | Required | The IDs of the hosts on which to batch execute commands. Host IDs can be obtained using the Find Hosts command. |
JSON
|
File Path | Required | The full path to the file to be retrieved from each host in the batch. | C:\\test\\test.txt |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Run Batch Get failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: No successful hosts initialized on RTR. |
Error Sample Data Run Batch Get failed. Status Code: 400. Message: No successful hosts initialized on RTR. |
Scan Hosts Adhoc
Initiates an ad hoc scan on the specified hosts or host groups.
READER NOTE
Host Group IDs is a required parameter to run this command.
Run the Find Host Groups command to obtain the Host Group ID. Host Group IDs can be found in the raw data at the path $.resources[*].id.
Host IDs is an optional parameter to run this command.
Run the Find Hosts command to obtain the Host IDs. Host IDs can be found in the raw data at the path $.resources.
Input
Input Parameter | Required/Optional | Description | Example |
Host IDs | Optional | The IDs of the hosts to scan. Host IDs can be obtained using the Find Hosts command. Note: At least one of the Host ID or Host Group ID parameters must be defined. |
JSON
|
Host Group IDs | Required | The IDs of the host groups to scan. Host IDs can be obtained using the Find Host Groups command. |
JSON
|
File Paths | Required | The file paths to scan. |
JSON
|
Scan Exclusions | Optional | The file paths to exclude from the scan. |
JSON
|
Max Duration | Optional | The maximum scan duration value in hours. If this parameter is not defined, there will be no limit on the duration of the scan. | 2 |
Pause Duration | Optional | The maximum allowed scan pause duration in hours. If this parameter is not defined, the default pause duration is two hours. | 2 |
Description | Optional | The description for the scan. | test *** |
Quarantine | Required | The option to quarantine malicious files if found. | False |
CPU Priority | Optional | The percentage of CPU utilization to allocate for the scan. The default CPU utilization for the scan is up to 25%. | Up to 1% CPU utilization |
Machine Learning Detection Level | Optional | The detection level of cloud and sensor machine learning to enable. The detection level must be greater or equal to the associated prevention level. If the prevention level is set to Moderate, then the detection level must be Moderate, Aggressive, or Extra Aggressive, and cannot be set to Cautious. If this parameter is not defined, the default detection level is Moderate. | Cautious |
Machine Learning Prevention Level | Optional | The prevention level of cloud and sensor machine learning to employ. Note: The detection level must be at least as high as the prevention level. For example, if the detection level is set to Moderate, then the prevention level cannot be set to Aggressive or Extra Aggressive; it must be set to Moderate, Cautious or Disabled. If this parameter is not defined, the default prevention level is Moderate. | Cautious |
Max File Size | Optional | The maximum file size (in MB) to scan. If this parameter is not defined, the default value is 60 MB. | 20 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Scan Hosts Adhoc failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Host Group ID Not Found. |
Error Sample Data Scan Hosts Adhoc failed. Status Code: 404. Message: Host Group ID Not Found. |
Schedule Scan
Schedules a scan for specified host groups. Scheduled scans are only available for host groups, and are not supported for individual hosts.
READER NOTE
Host Group IDs is a required parameter to run this command.
Run the Find Host Groups command to obtain the Host Group IDs. Host Group IDs can be found in the raw data at the path $.resources[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Host Group IDs | Required | The IDs of the host groups so schedule a scan. Host Group IDs can be obtained using the Find Host Groups command. |
JSON
|
File Paths | Required | The file paths to scan. |
JSON
|
Scan Exclusions | Optional | The file paths to exclude from the scan. |
JSON
|
Max Duration | Optional | The maximum scan duration in hours. If this parameter is not defined, the scan duration is allowed to be indefinite. | 2 |
Pause Duration | Optional | The maximum pause duration in hours. If this parameter is not defined, the default pause duration is 2 hours. | 2 |
Description | Optional | The description for the scan. | test ODS Schedule scan Host0223b |
Quarantine | Required | The option to quarantine malicious files if they are found in the scan. | False |
CPU Priority | Optional | The allowed CPU utilization percentage for the scan. The default value is Up to 25% CPU utilization. | Up to 1% CPU utilization |
Machine Learning Detection Level | Optional | The detection level of cloud and sensor machine learning to employ. Note: The detection level must be at least as high as the prevention level. For example, if the detection level is set to Moderate, then the prevention level must be set to Moderate, Aggressive or Extra Aggressive. If this parameter is not defined, the default detection level is Moderate. | Cautious |
Machine Learning Prevention Level | Optional | The prevention level of cloud and sensor machine learning to employ. Note: The detection level must be at least as high as the prevention level. For example, if the detection level is set to Moderate, then the prevention level cannot be set to Aggressive or Extra Aggressive; it must be set to Moderate, Cautious or Disabled. If this parameter is not defined, the default prevention level is Moderate. | Cautious |
Max File Size | Optional | The maximum file size to scan in megabytes (MB). If this parameter is not defined, the default value is 60MB. The allowed maximum value is 60 MB. | 20 |
Scheduled Scan Start Time | Required | The start time of the scheduled scan. The scan will be set to run at the designated time, adjusted to the time zone of each individual host. | 2023-04-19 00:00 |
Scheduled Scan Interval | Optional | The frequency of the scheduled scan in days. For a one-time scan, set the value to 0. If this parameter is not defined, the scan will only run once. | 3 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Schedule Scan failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: Host Group IDs not found. |
Error Sample Data Schedule Scan failed. Status Code: 404, Error Message: Host Group IDs not found. |
Search Users
Retrieves user information from CrowdStrike.
Input
Input Parameter | Required/Optional | Description | Example |
User Email Addresses | Optional | The email addresses of the users to retrieve information. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Search Users failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Email Not Found. |
Error Sample Data Search Users failed. Status Code: 404. Message: Email Not Found. |
Search Alerts
Retrieves comprehensive data from the alerts matching the specified search conditions.
Input
Input Parameter | Required/Optional | Description | Example |
Filter | Required | The filter condition defined in Falcon Query Language (FQL). For more information about the FQL syntax, see Falcon Query Language (FQL). If this parameter is not defined, all alerts will be returned. | product:'epp' + status:['new'] + severity:>=50 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Search Alerts failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Invalid Filter. |
Error Sample Data Search Alerts failed. Status Code: 403. Message: Invalid Filter. |
Search Vulnerable Hosts By CVE
Searches vulnerable hosts in your environment by CVE IDs or CVE Severity.
READER NOTE
CVE IDs is a required parameter to run this command.
Run the List Vulnerabilities command to obtain the CVE IDs. CVE IDs can be found in the raw data at the path $.resources[*].cve.id.
Input
Input Parameter | Required/Optional | Description | Example |
CVE IDs | Optional | The CVE IDs of the vulnerabilities present in the hosts to filter results. CVE IDs can be obtained using the List Vulnerabilities command. |
JSON
|
Minimum CVE Severity | Optional | The minimum CVE severity level to filter the returned hosts within your environment. For example, if this parameter is set to MEDIUM, the search results will include hosts with MEDIUM, HIGH or CRITICAL CVE vulnerabilities. Choosing UNKNOWN will return only hosts with UNKNOWN severity, while selecting NONE will only return hosts with NONE severity. Note: If you define the CVE IDs parameter, this parameter will be ignored. If neither the CVE IDs nor the Minimum CVE Severity parameters are specified, the search results will include all hosts with vulnerabilities of HIGH CVE severity levels and above (including HIGH, CRITICAL). | CRITICAL |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Search Vulnerable Hosts By CVE failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: CVE IDs Not Found. |
Error Sample Data Search Vulnerable Hosts By CVE failed. Status Code: 404. Message: CVE IDs Not Found. |
Unquarantine Endpoint by ID
Unquarantines endpoints by endpoint ID in CrowdStrike.
READER NOTE
Endpoint IDs is a required parameter to run this command.
Run the Find Hosts command to obtain the Endpoint IDs. Endpoint IDs can be found in the raw data at the path $.resources.
This command requires API Version v2 for the connection. If the API Version is configured to v1, the connection will not be available to run this command.
Refer to Step 3h 4 of Configuring D3 SOAR to Work with CrowdStrike on changing a connection's API Version.
The input Endpoint IDs must be quarantined before running this command.
Input
Input Parameter | Required/Optional | Description | Example |
Endpoint IDs | Required | The IDs of the endpoints to unquarantine. Endpoint IDs can be obtained using the Find Hosts command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Unquarantine Endpoint by ID failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: No matching host found for ID ***. |
Error Sample Data Unquarantine Endpoint by ID failed. Status Code: 404 Error Message: No matching host found for ID ***. |
Unquarantine Endpoint by IP
Unquarantines endpoints by IP in CrowdStrike.
READER NOTE
Endpoint IPs is a required parameter to run this command.
The desired Endpoint IPs can be obtained in advance or retrieved using the Fetch Event command with defined filters. The values can be found in the raw data, under the "local_ip" key.
Input
Input Parameter | Required/Optional | Description | Example |
Endpoint IPs | Required | The IPs of the endpoints to unquarantine. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Unquarantine Endpoint by IP failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: Host IPs Not Found. |
Error Sample Data Unquarantine Endpoint by IP failed. Status code: 404. Error Message: Host IPs Not Found. |
Update Alerts
Updates alerts (status, assignee, tags, and comments) in CrowdStrike.
READER NOTE
Alert IDs is a required parameter to run this command.
Run the Search Scan command to obtain the Alert IDs. Alert IDs can be found in the raw data at the path $.resources[*].id.
Input
Input Parameter | Required/Optional | Description | Example |
Alert IDs | Required | The IDs of the alerts to update. Alert IDs can be obtained using the Search Alerts command. |
JSON
|
Status | Optional | The updated status of the alerts. | In Progress |
Comment | Optional | The comment to add to the alerts. | testAlertComment0208a |
Assignee | Optional | The email address of the alert's assignee user. | test@example.com |
Add Tag | Optional | The tag value to add to the alerts. | Malicious1_tag |
Remove Tag | Optional | The tags to remove from the alerts. | Suspicious1_tag |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Alerts failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Alert ID Not Found. |
Error Sample Data Update Alerts failed. Status Code: 404. Message: Alert ID Not Found. |
Update Detections (Deprecated)
Updates the status, assignee, and comment of the specified detection(s).
DEPRECATION
This command will be retired on September 30, 2025, with the decommissioning of the Detects API. Use the "Update Alerts" command instead.
Input
Input Parameter | Required/Optional | Description | Example |
Detection IDs | Required | The IDs of the detections to resolve. Detection IDs can be obtained using the Fetch Event command. |
JSON
|
Status | Required | The updated status of the specified detections. The available statuses are New, In Progress, True Positive, False Positive, Closed, Reopened and Ignored. | In Progress |
Comment | Optional | The comment to add to the detection. Comments provide context or notes to other Falcon users who view the detection. Additionally, it is possible to have multiple comments added to a detection over time. | testComment0207b |
Assignee | Optional | The email address of the detection's assigned user. | test@example.com |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Detection failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: Detection with ID 'ldt:272***191' not found. |
Error Sample Data Update Detection failed. Status Code: 404. Error Message: Detection with ID 'ldt:272***191' not found. |
Update Incidents
Updates various fields of the specified incidents in CrowdStrike. You can also update the status of detections associated with the specified incident(s).
READER NOTE
Incident IDs is a required parameter to run this command.
The desired Incident IDs can be obtained in advance or retrieved using the Fetch Event command Event Type set to Incident. Incident IDs can be found in the raw data at the path $.resources[*].incident_id.
Input
Input Parameter | Required/Optional | Description | Example |
Incident IDs | Required | The IDs of the incidents to update. Incident IDs can be obtained using the Fetch Event command with the Event Type parameter set to Incident. |
JSON
|
Status | Optional | The updated status of the incidents. | In Progress |
Comment | Optional | The comment to add to the incidents. | testComment0206abc |
Assignee | Optional | The email address of the incidents' assignee user. | test@example.com |
Description | Optional | The updated description for the incidents. | Test Incident Description 0207 |
Incident Name | Optional | The updated name for the incidents. | NEW INC NAME |
Add Tag | Optional | The tag value to add to the incidents. | Malicious_tag |
Delete Tag | Optional | The tags to remove from the incidents. | Suspicious_tag |
Update Detections | Optional | The option to update the status of the detections associated with the specified incidents, when set to True. If this parameter is set to False, no changes will be made to any involved detections. The default option is False when this parameter is not defined. | True |
Overwrite Detections | Optional | The option to overwrite the status of detections associated with the specified incidents. When set to True, any action values provided in the Status parameter will be applied to the respective Status parameters of all involved detections. If set to False, action values in the Status parameter will only be applied to status parameters of involved detections that have a status of "New." The default value is False when this parameter is not defined. Note: This parameter is only valid when the Update Detections parameter is set to True. | True |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Incidents failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Incident ID Not Found. |
Error Sample Data Update Incidents failed. Status Code: 404. Message: Incident ID Not Found. |
Update IOCs
Updates indicators of compromise by IOC ID in CrowdStrike.
READER NOTE
IDs is a required parameter to run this command.
Run the Find IOC IDs command to obtain the IDs. IDs can be found in the raw data at the path $.resources.
Input
Input Parameter | Required/Optional | Description | Example |
IDs | Required | The IDs of the indicators to update. Indicator IDs can be obtained using the Find IOC IDs command. |
JSON
|
Source | Optional | The originating source of the indicator. This can be used to track where the indicator was defined. A maximum of 256 characters are accepted. | Test Source |
Action | Optional | The action to take when a host observes the custom IOC. The following are accepted inputs:
| Detect |
Severity | Optional | The severity level to apply to this indicator. This field is required to prevent and detect actions. It is optional if the selected action is No Action. | High |
Description | Optional | The descriptive label for the indicator. | Test IOC |
Expiration | Optional | The expiry date of the indicator, after which it will become inactive. Once expired, the indicator's action will be set to No Action, but it will still be visible in your list of custom IOCs. | 2023-04-21 00:00 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update IOCs failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: 'No resource found with ID 5ec6****4a69****284b. |
Error Sample Data Update IOCs failed. Status Code: 404. Error Message: 'No resource found with ID 5ec6****4a69****284b. |
Upload IOCs
Uploads one or more custom indicators of compromise to CrowdStrike.
Input
Input Parameter | Required/Optional | Description | Example |
Type | Required | The indicator type of the entities to upload. | SHA256 |
Values | Required | The string value of the IOCs to upload. |
JSON
|
Action | Required | The action to take when a host observes the custom IOC. If not specified, the default action is No Action. The following are accepted inputs:
| Detect |
Severity | Required | The severity level to apply to this indicator. This field is required when the selected action is Prevent or Detect. It is optional for No Action. | High |
Description | Optional | The descriptive label for the indicators. | Test IOC |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Upload IOCs failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Error Message: Duplicate type: 'domain' and value: 'bexample1023.com' combination. |
Error Sample Data Upload IOCs failed. Status Code: 400. Error Message: Duplicate type: 'domain' and value: 'bexample1023.com' combination. |
Upload Real Time Response Script
Uploads a PowerShell script to the CrowdStrike cloud for use with a future "runscript" command.
Input
Input Parameter | Required/Optional | Description | Example |
File Name | Optional | The name of the file to upload. | InventoryAudit.ps1 |
Script | Required | The PowerShell script to upload. | get-childitem |
Permission Type | Required | The permission type for the custom script. Available options are:
| Group |
Description | Optional | The description of the file to upload. | Enumerates child items in a directory |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Upload Real Time Response Script failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 409. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: File with given name already exists. |
Error Sample Data Upload Real Time Response Script failed. Status Code: 409. Message: File with given name already exists. |
Test Connection
In the API Clients and Keys page of CrowdStrike Falcon, ensure that the API client used for the D3 Security SOAR integration has the Alerts scope with at least read permission.
Allows users to perform a health check on an integration connection. Users can schedule a periodic health check by selecting Connection Health Check when editing an integration connection.
Input
N/A
Output
Output Type | Description | Return Data Type |
Return Data | Indicates one of the possible command execution states: Successful or Failed. The Failed state can be triggered by any of the following errors:
More details about an error can be viewed in the Error tab. | String |
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Test Connection failed. Failed to check the connector. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CrowdStrike portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The remote name could not be resolved: 'api.crowdst'. |
Error Sample Data Test Connection failed. Failed to check the connector. Status Code: 400. Message: The remote name could not be resolved: 'api.crowdst'. |
Deprecated Commands
Deprecated commands are only supported on existing connections configured by current clients. It is recommended for these clients to contact D3's support team to assess the feasibility of migrating these deprecated commands to their respective new versions. For this integration, the Execute Command On Single Endpoint command has been deprecated.
Use Case
Searching for Hashes using the Fetch Event Command
This use case demonstrates how you can search for MD5 and SHA 256 hashes in CrowdStrike using D3 SOAR's Fetch Event command.
To directly search for MD5 and SHA 256 hashes from CrowdStrike, navigate to Investigate and select Hashes. However, since there is no API available to perform this search externally, D3 SOAR's Fetch Event command can be used. Set the event type to Detections and enter the hash value as the filter parameter. You may also specify a time range. Running the command will return the device ID(s) corresponding to the hash.
To obtain detailed information about a specific process by the custom IOC of the hash value, use the Get Process Details By IOC command. Input the hash value as the IOC parameter, select SHA 256 or MD5 as the IOC type, and use the device ID obtained earlier as the host ID. Running the command will return the desired process details.
Note: The device must be turned on and operational for these commands to work. You can use the Get Host Info by ID command to check the last heartbeat.