CISCO Firepower
LAST UPDATED: SEPTEMBER 29, 2025
Overview
Cisco Firepower is an integrated suite of network security and traffic management products, deployed either on purpose-built platforms or as a software solution. The system offers unified management of firewalls, application control, intrusion prevention, URL filtering, and advanced malware protection, to help organizations handle network traffic in a way that complies with the organizations’ security policy - the guidelines for protecting the organizations’ network. This integration enables organizations to block suspicious IP addresses and URLs.
D3 SOAR is providing REST operations to function with CISCO Firepower.
For example, you can use the CISCO Firepower Management Center to collect data and gather information such as spam messages or malicious email messages.
CISCO Firepower is available for use in:
D3 SOAR | V15.0+ |
Category | Network Security |
Deployment Options |
Known Limitations
The management center REST API implements rate limiting to reduce network load.
The API will accept no more than 120 messages per minute from an individual IP address. It will only allow 10 simultaneous connections per IP address. These are not configurable parameters.
If a client exceeds these limits, the API will give an HTTP 429 error.
Refer to CISCO REST API Rate Limiting for detailed information.
Connection
To connect to CISCO Firepower from D3 SOAR, please follow this part to collect the required information below:
Parameter | Description | Example |
Server URL | The URL of the FirePower instance. | https://1.1.1.1 |
User Name | The user name for authentication. | admin |
Password | The password for authentication. | D3******* |
API Version | The version for API. | v1 |
READER NOTE
The prerequisites for using this guide are:
A machine with CISCO Firepower Management Center installed.
A user account in CISCO Firepower Management Center with an admin role.
Permission Requirements
Each endpoint in the CISCO Firepower API requires a certain permission scope. The following are required scopes for the commands in this integration:
Command | Required Permission |
Block IPs | Object Manager > Modify Object Manager |
Block URLs | Object Manager > Modify Object Manager |
Get IPs By NetworkGroup Name | Object Manager |
Get URLs By URL Group Name | Object Manager > Modify Object Manager |
Test Connection | Policies |
As CISCO Firepower is using role-based access control (RBAC), the API access token is generated based on a specific user account and the application. Therefore, the command permissions are inherited from the user account’s role. Users need to configure their user profile from the CISCO Firepower console for each command in this integration.
READER NOTE
CISCO Firepower’s system-provided user profiles are as follows:
Administrator
Access Admin
Discovery Admin
External Database User (Read Only)
Intrusion Admin
Maintenance User
Network Admin
Security Analyst
Security Analyst (Read Only)
Security Approver
Threat Intelligence Director (TID) User
Refer to Predefined User Roles for details on configuring user profiles.
The permission requirements in the table above are policies. If the default roles do not meet the requirements, these policies can be used to create custom roles for users. Refer to Configuring CISCO Firepower to work with D3 SOAR for details.
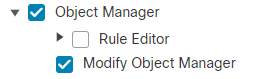
The Object Manager > Modify Object Manager permission means that users only need to select the sub policy Modify Object Manager under Object Manager.
Configuring CISCO Firepower to Work with D3 SOAR
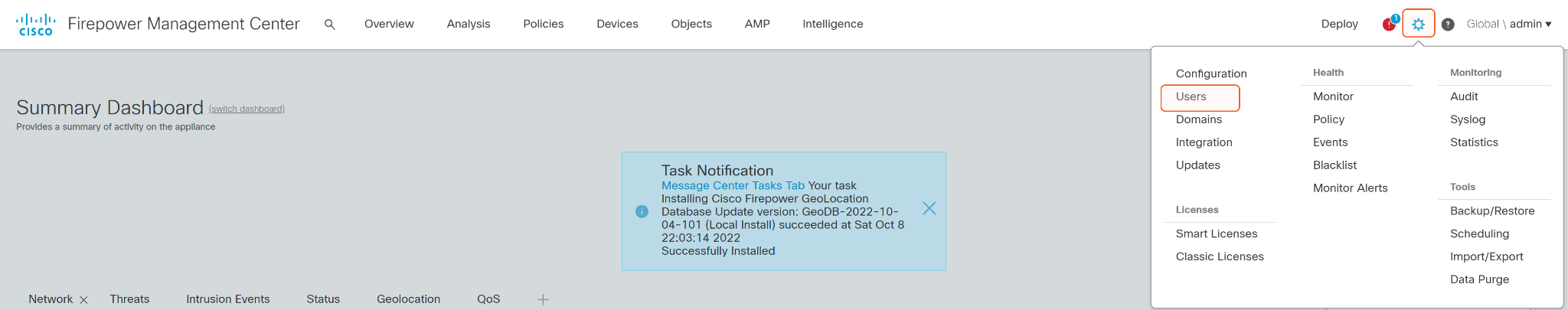
Log into CISCO Firepower Management Center.

Click System, then click Users.
Create a custom user role.
Select User Roles. Then click the button Create User Role.
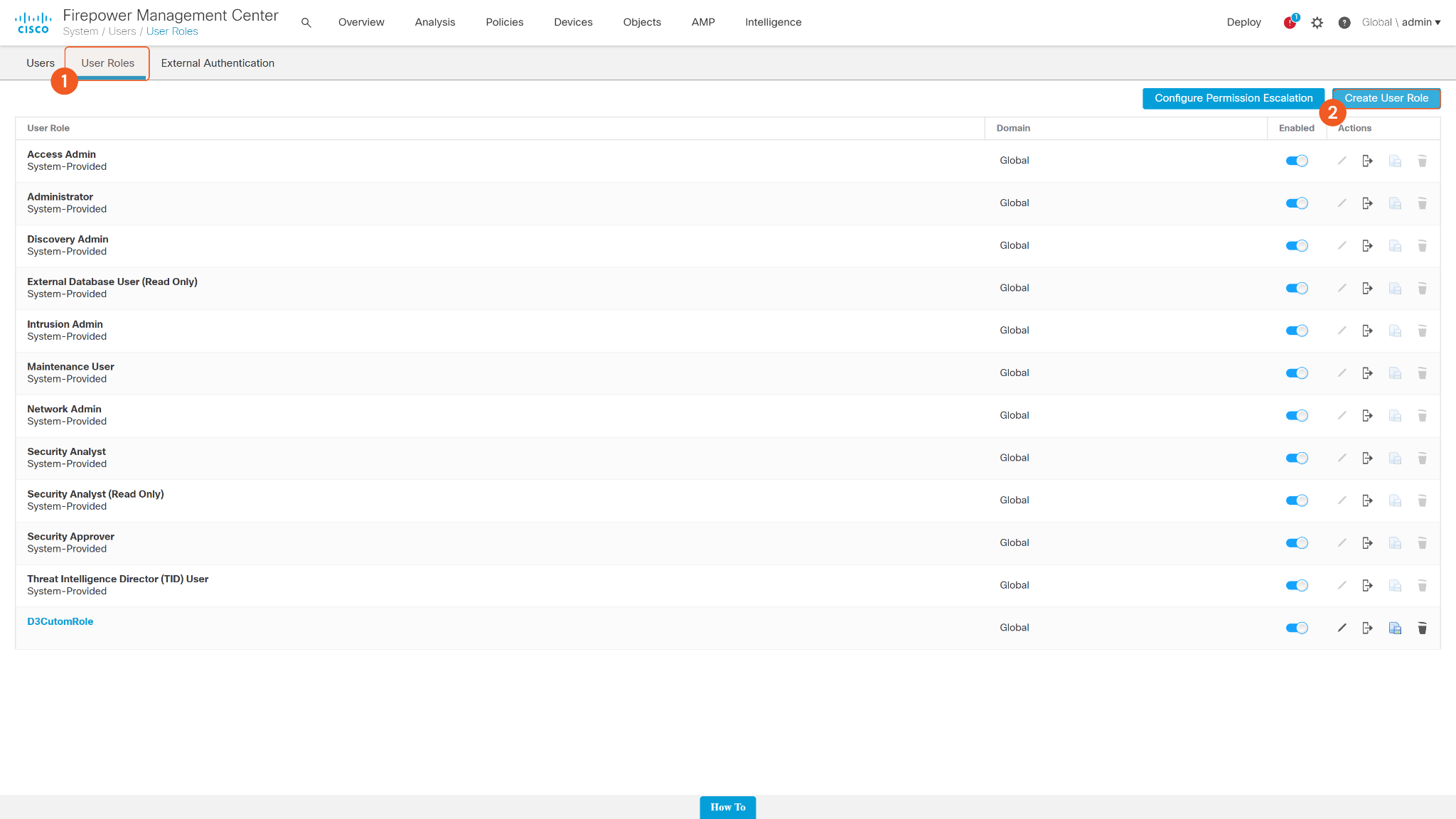
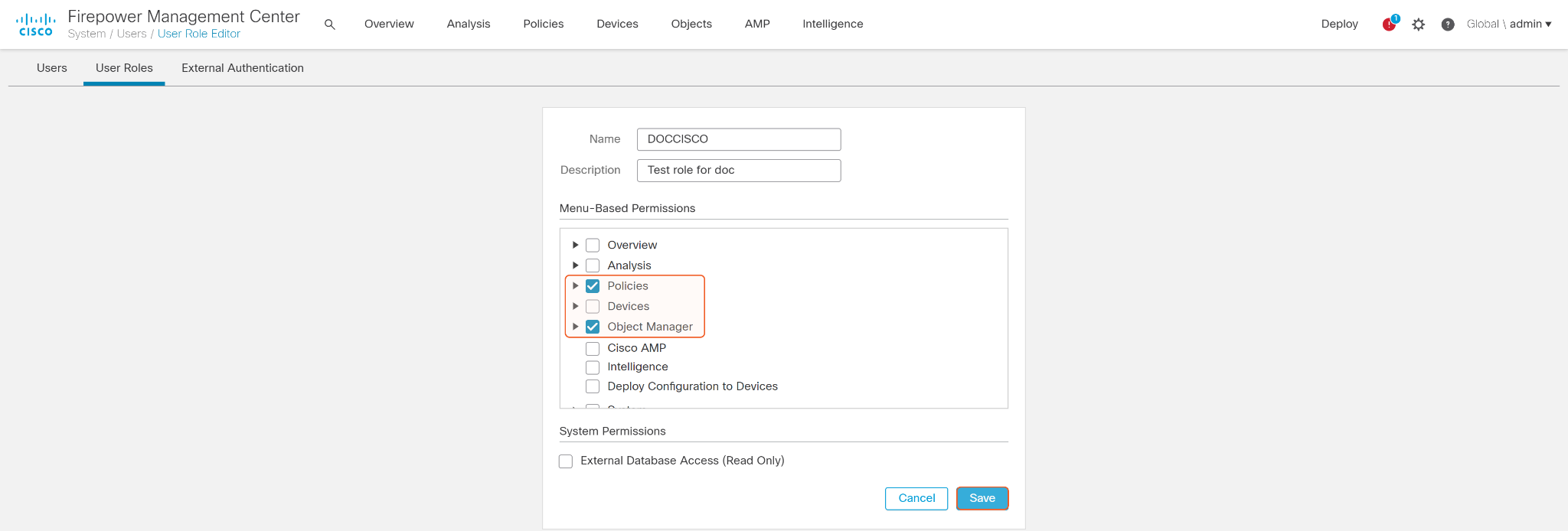
Enter a name for the Role. Refer to the Permission Requirements for the permissions your role requires, and check each box as needed.. Then click Save.
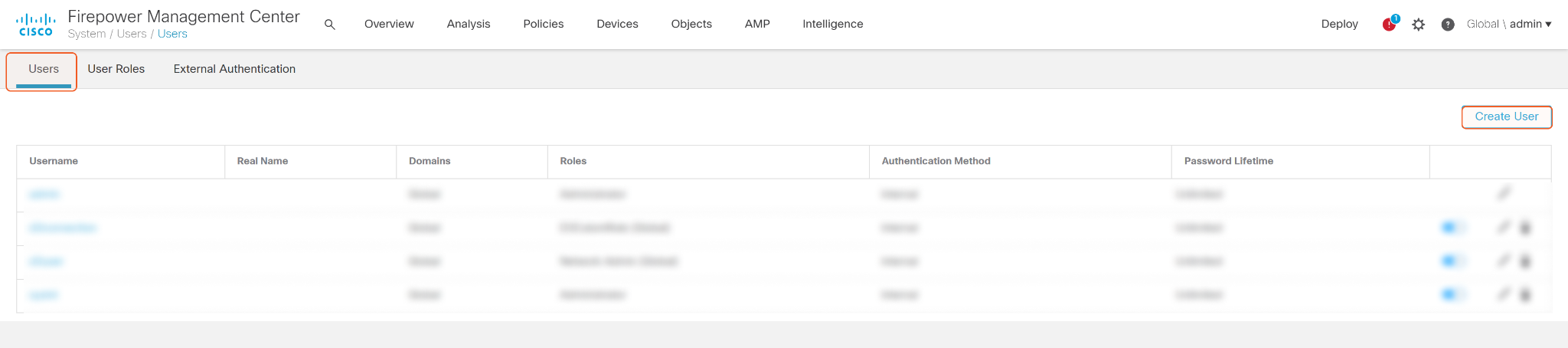
Create a new user.
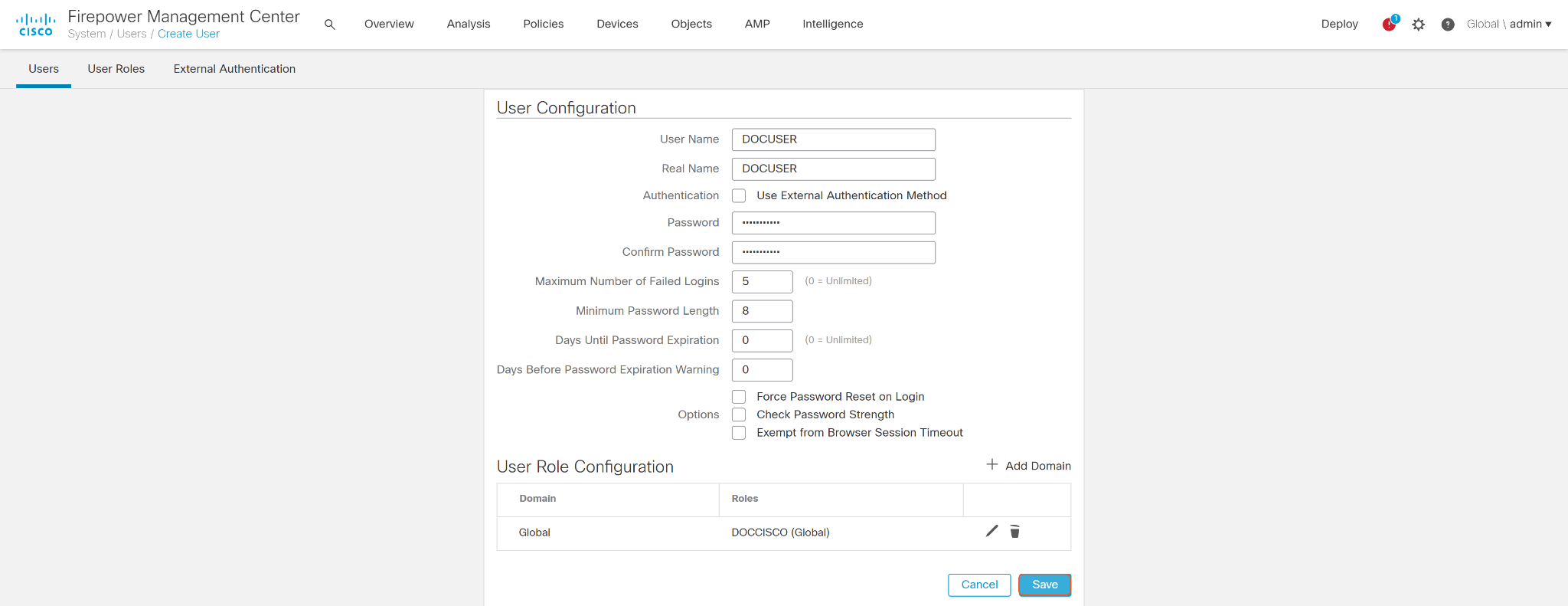
Click Users, then click the Create User button.
Enter a User Name and Password. Click + Add Domain to grant user roles.
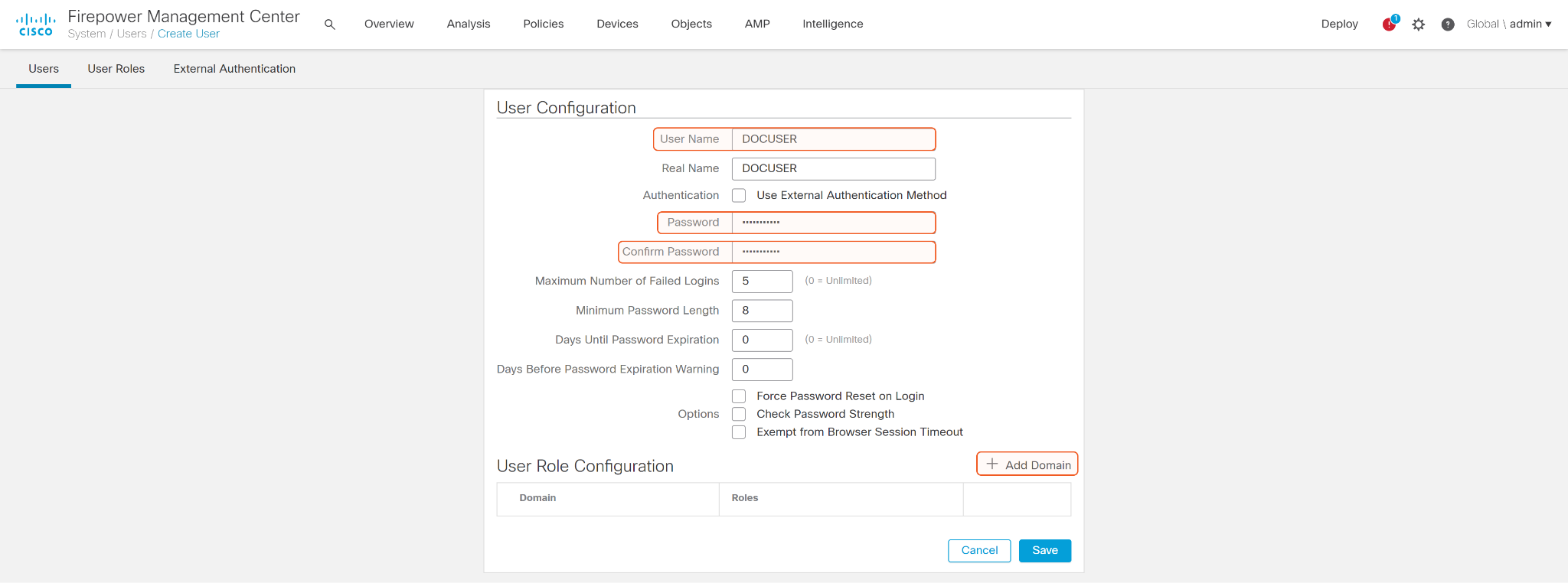
Select the custom role that was just created and click Save.
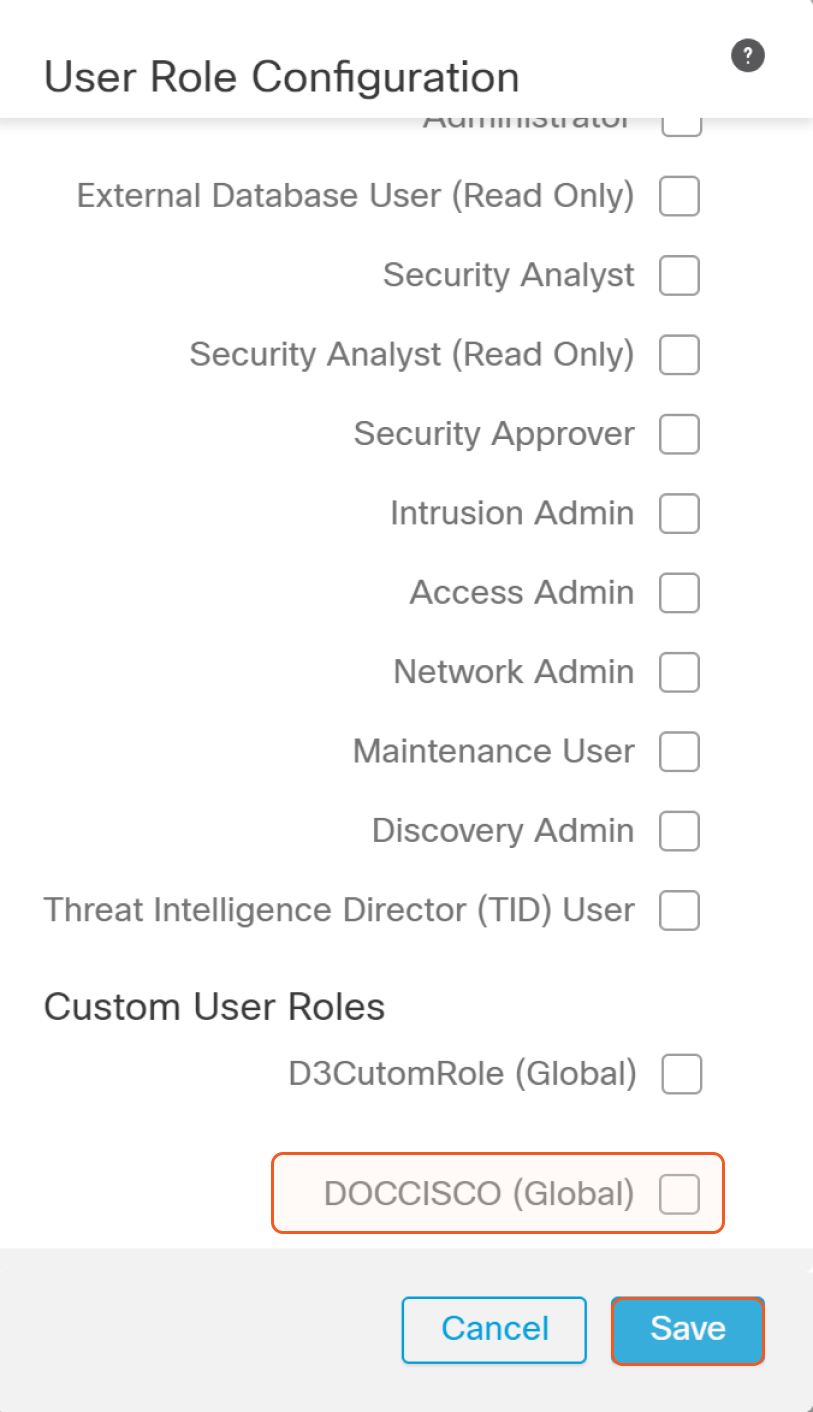
Save the user.
Configuring D3 SOAR to Work with CISCO Firepower
Log in to D3 SOAR.
Find the CISCO Firepower integration.
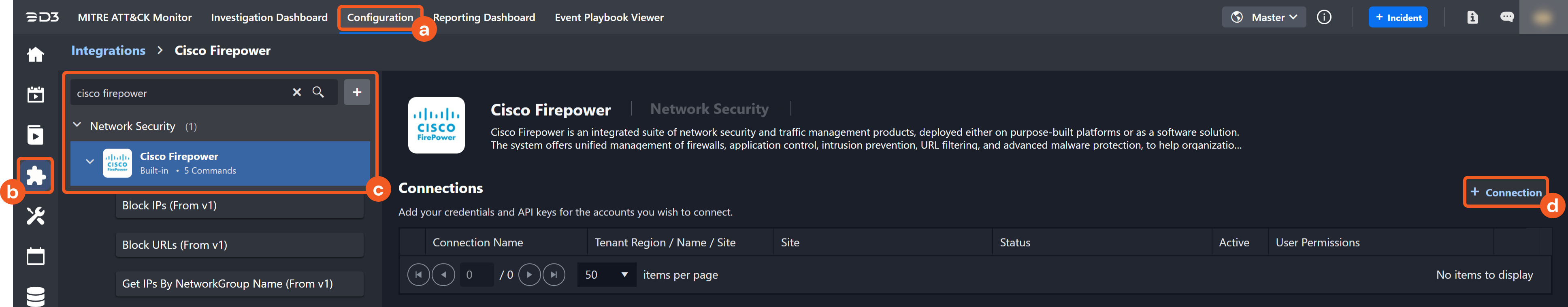
Navigate to Configuration on the top header menu.
Click on the Integration icon on the left sidebar.
Type CISCO Firepower in the search box to find the integration, then click it to select it.
Click + New Connection, on the right side of the Connections section. A new connection window will appear.
Configure the following fields to create a connection to CISCO Firepower.
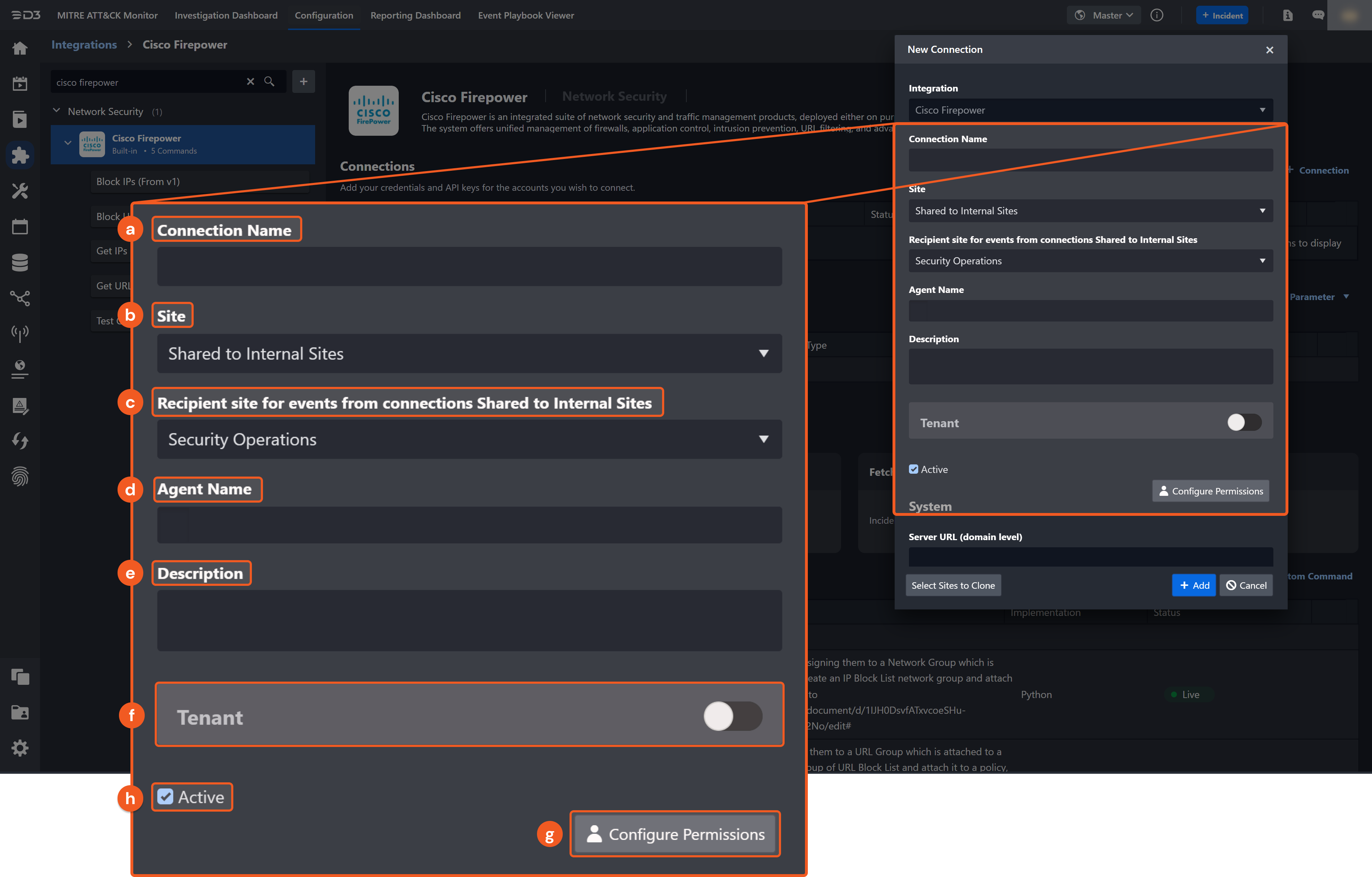
Connection Name: The desired name for the connection.
Site: The site on which to use the integration connection. Use the drop-down menu to select the site. The Share to Internal Sites option enables all internal sites to use the connection. Selecting a specific site will only enable that site to use the connection.
Recipient site for events from connections Shared to Internal Sites: This field is displayed when Share to Internal Sites is selected for the Site field, allowing selection of the internal site for deploying the integration connection.
Agent Name (Optional): The proxy agent required to build the connection. Use the dropdown menu to select the proxy agent from a list of previously configured proxy agents.
Description (Optional): The description for the connection.
Tenant (Optional): When configuring the connection from a master tenant site, users can choose the specific tenant sites with which to share the connection. Once this setting is enabled, users can filter and select the desired tenant sites from the dropdowns to share the connection.

Configure User Permissions: Defines which users have access to the connection.
Active: The checkbox that enables the connection to be used when selected.
System: This section contains the parameters defined specifically for the integration. These parameters must be configured to create the integration connection.
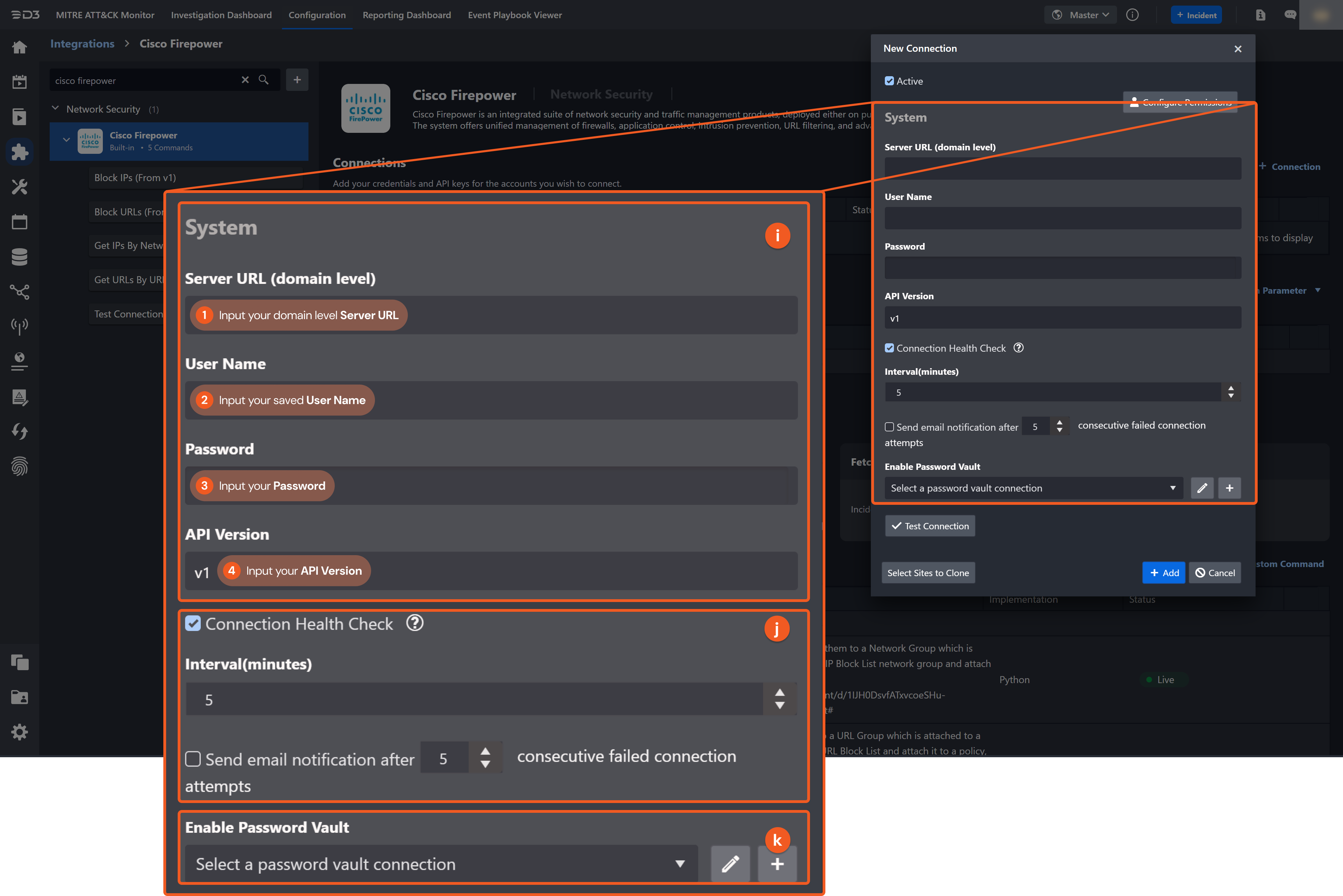
1. Input the domain level Server URL.
2. Input the user name. Refer to step 4 of Configuring CISCO Firepower to work with D3 SOAR for how to create a user.3. Input the password. Refer to step 4 of Configuring CISCO Firepower to work with D3 SOAR for how to create a user.
4. Input the API version. The default value is v1.
Connection Health Check: Periodically checks the connection status by scheduling the Test Connection command at the specified interval (in minutes). Available only for active connections, this feature also allows configuring email notifications for failed attempts.
Enable Password Vault: An optional feature that allows users to take the stored credentials from their own password vault. Refer to the password vault connection guide if needed.
Test the connection.
Click on the Test Connection button to verify credentials and connectivity. A success alert displays Passed with a green checkmark. If the connection fails, review the parameters and retry.
Click OK to close the alert window.
Click + Add to create and add the configured connection.
Commands
CISCO Firepower includes the following executable commands for users to set up schedules or create playbook workflows. With the Test Command, users can execute these commands independently for playbook troubleshooting.
Integration API Note
For more information about the CISCO Firepower API, refer to the CISCO Firepower API reference.
READER NOTE
Certain permissions are required for each command. Refer to the Permission Requirements and Configuring CISCO Firepower to Work with D3 SOAR for details.
Block IPs
Blocks IP address(es) by assigning them to a Network Group which is attached to a policy. To create an IP Block List network group and attach it to a policy, refer to How to create Firepower IP Block List.
Input
Input Parameter | Required/Optional | Description | Example |
Network Group Name | Required | The Network Group name of the IP block list. NetworkGroup Name can be obtained in Firepower Management Center under Objects > Object Management > Network. | IP_Block_List_0804 |
IP Addresses | Required | The IP addresses to block. You can input multiple IP addresses separated by a comma. Valid IPV4 or IPV6 addresses and CIDR are acceptable. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Block IPs failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CISCO Firepower portal. Refer to the CISCO REST API Response Structure for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Invalid IP Address. You have entered an invalid value. |
Error Sample Data Block IPs failed. Status Code: 400. Message: Invalid IP Address. You have entered an invalid value. |
Block URLs
Blocks URL(s) by assigning them to a URL Group which is attached to a policy. To create a URL group of URL Block Lists and attach it to a policy, refer to How to create Firepower URL Block List.
Input
Input Parameter | Required/Optional | Description | Example |
URL Group Name | Required | The URL Group Name of the URL block list. URL Group Name can be obtained in Firepower Management Center under Objects > Object Management > URL. | URL_Block_List_0804 |
URLs | Required | The URL(s) to be blocked. You can input multiple URLs separated by comma. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Block URLs failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CISCO Firepower portal. Refer to the CISCO REST API Response Structure for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Not Found. The URL Group Name is unavailable. |
Error Sample Data Block URLs failed. Status Code: 404. Message: Not Found. The URL Group Name is unavailable. |
Get IPs By NetworkGroup Name
Returns IP Addresses in the IP block list with the NetworkGroup Name. NetworkGroup Names can be obtained in Firepower Management Center under Objects > Object Management > Network.
Input
Input Parameter | Required/Optional | Description | Example |
Network Group Name | Required | The NetworkGroup name of the IP block list. NetworkGroup Name can be obtained in Firepower Management Center under Objects > Object Management > Network. | BlockIPList_0729a |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get IPs By NetworkGroup Name failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CISCO Firepower portal. Refer to the CISCO REST API Response Structure for details. | Status Code: 429. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Too many writes, please retry the request. |
Error Sample Data Get IPs By NetworkGroup Name failed. Status Code: 429. Message: Too many writes, please retry the request. |
Get URLs By URL Group Name
Returns URLs in the URL block list with the URL Group Name. URL Group Names can be obtained in Firepower Management Center under Objects > Object Management > URL.
Input
Input Parameter | Required/Optional | Description | Example |
URL Group Name | Required | The URL Group Name of the URL block list. URL Group Names can be obtained in Firepower Management Center obtained under Objects > Object Management > URL. | BlockUrlList_0729b |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get URLs By URL Group Name failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CISCO Firepower portal. Refer to the CISCO REST API Response Structure for details. | Status Code: 429. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Too many writes, please retry the request. |
Error Sample Data Get URLs By URL Group Name failed. Status Code: 429. Message: Too many writes, please retry the request. |
Test Connection
Allows users to perform a health check on an integration connection. Users can schedule a periodic health check by selecting Connection Health Check when editing an integration connection.
Input
N/A
Output
Output Type | Description | Return Data Type |
Return Data | Indicates one of the possible command execution states: Successful or Failed. The Failed state can be triggered by any of the following errors:
More details about an error can be viewed in the Error tab. | String |
Error Handling
If the Return Data is failed, an Error tab will appear in the Test Result window.
The error tab contains the responses from the third-party API calls including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Test Connection failed. Failed to check the connector. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CISCO Firepower portal. Refer to the CISCO REST API Response Structure for details. | Status Code: 500. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Test Connection failed. Failed to check the connector. Status Code: 500. Message: Unauthorized. |
FAQ
Question 1: How do I create a Firepower IP Block List?
Log into Firepower Management Center.
Click Objects on the top, then click Object Management.
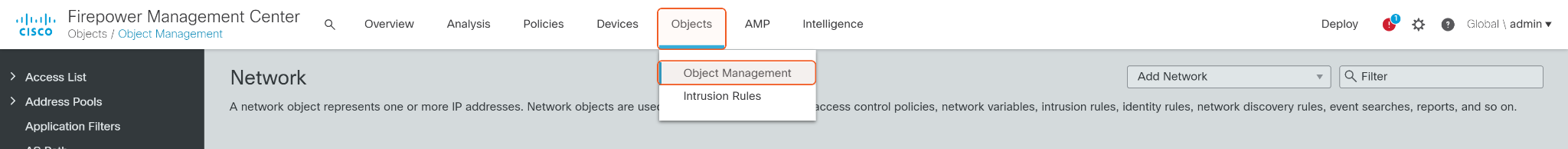
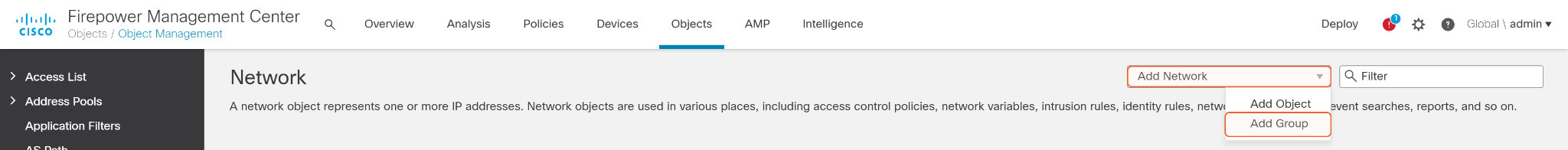
Click Network on the left side, then select Add Group in the Add Network dropdown list on the top.
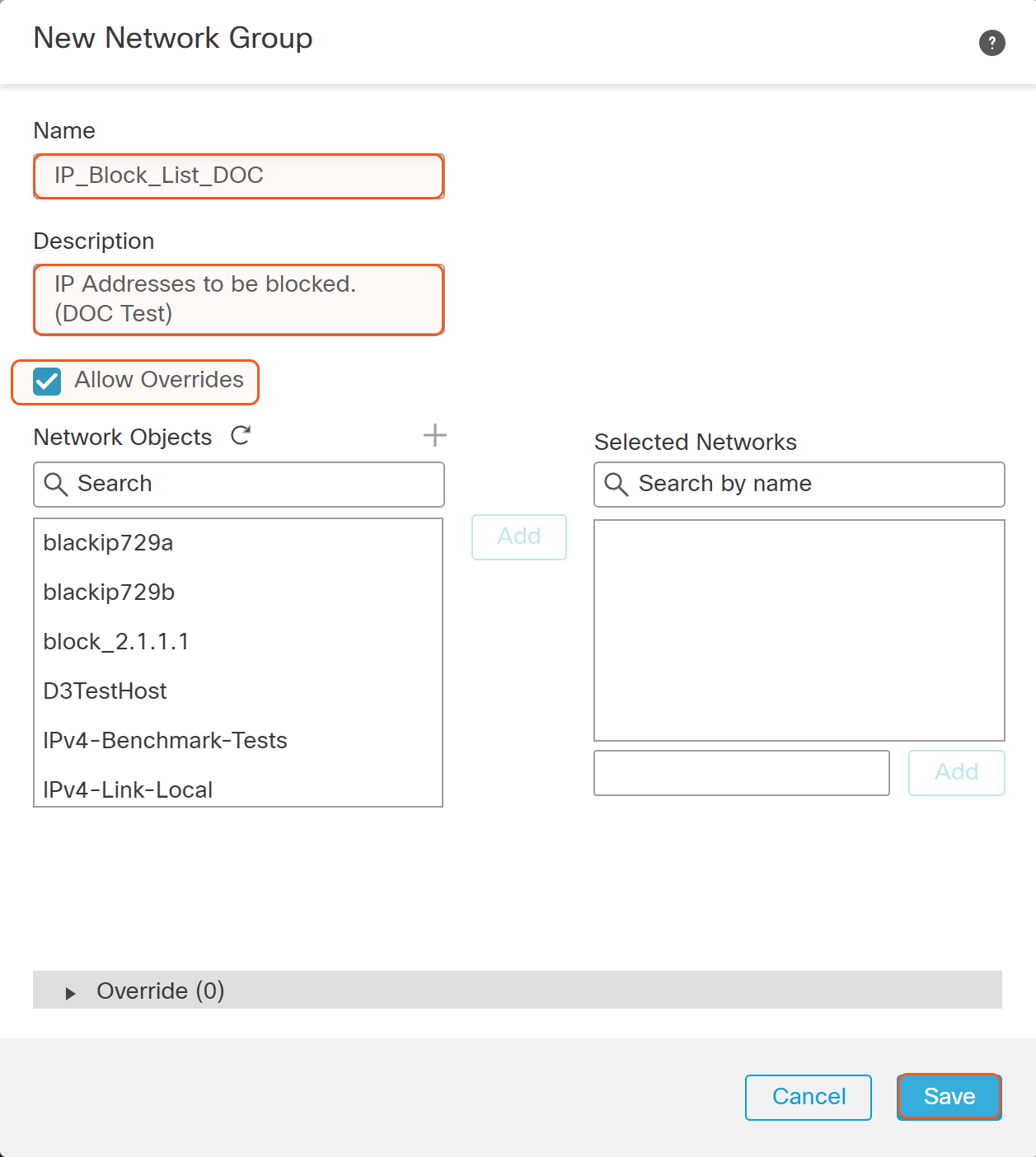
In the pop-up window, enter the Name and Description for the IP Block List. Add existing network objects to the list or check Allow Overrides and just leave the list blank. Then click Save.
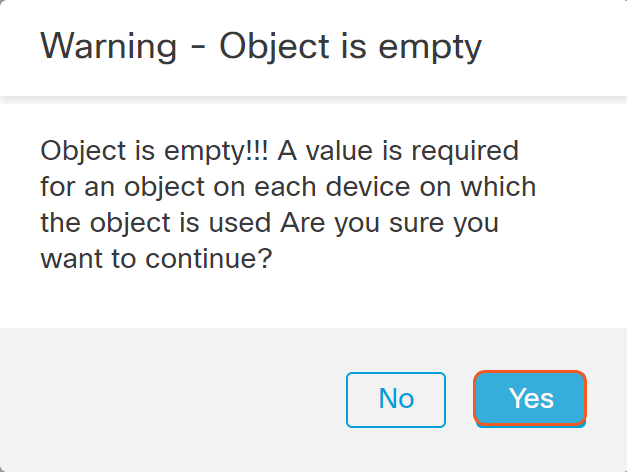
If the object list is empty, a Warning window will appear, click Yes.
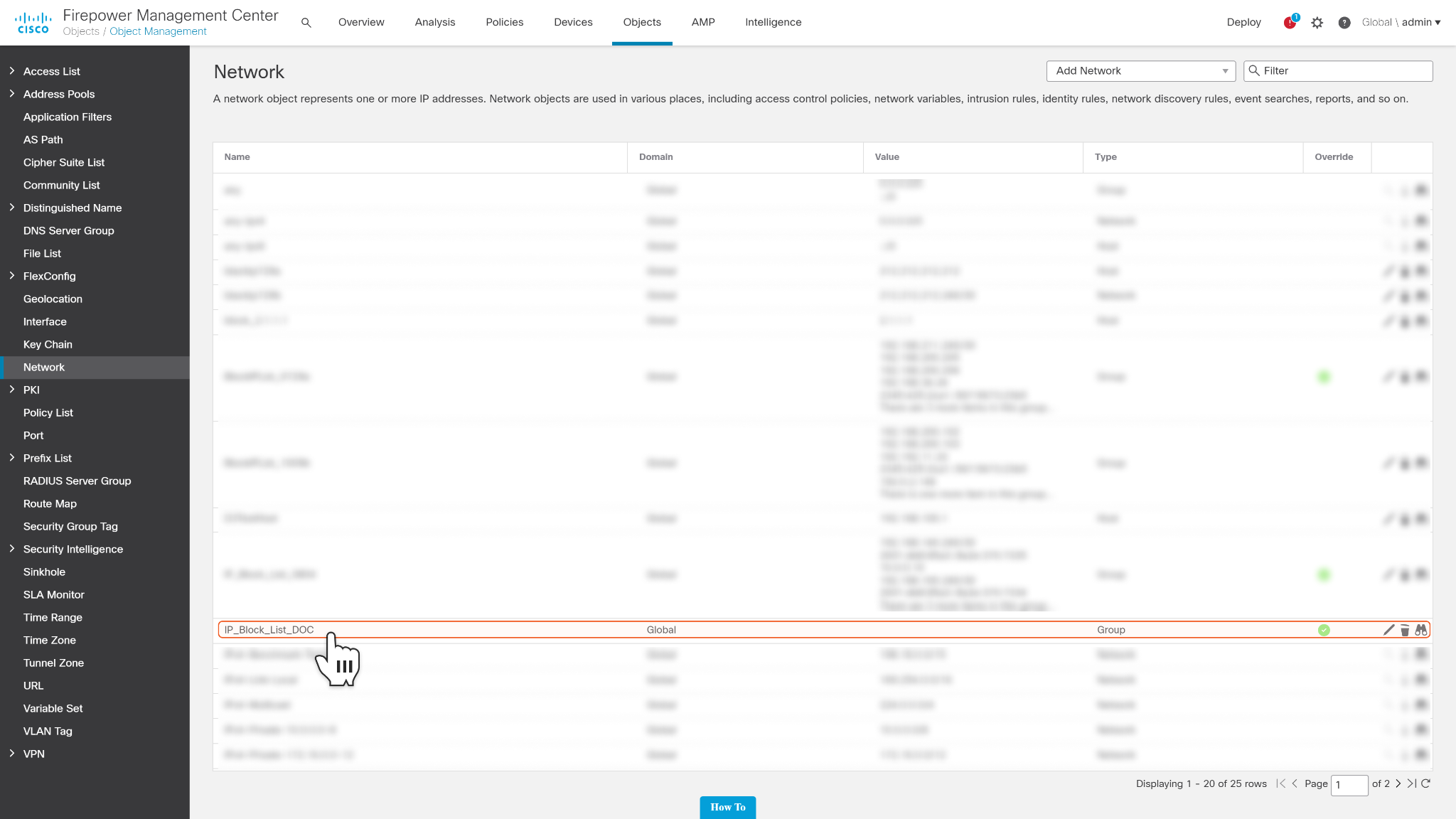
Users should find the IP Block List that they just created in the Network object list. Save the name which will be used when blocking IPs.
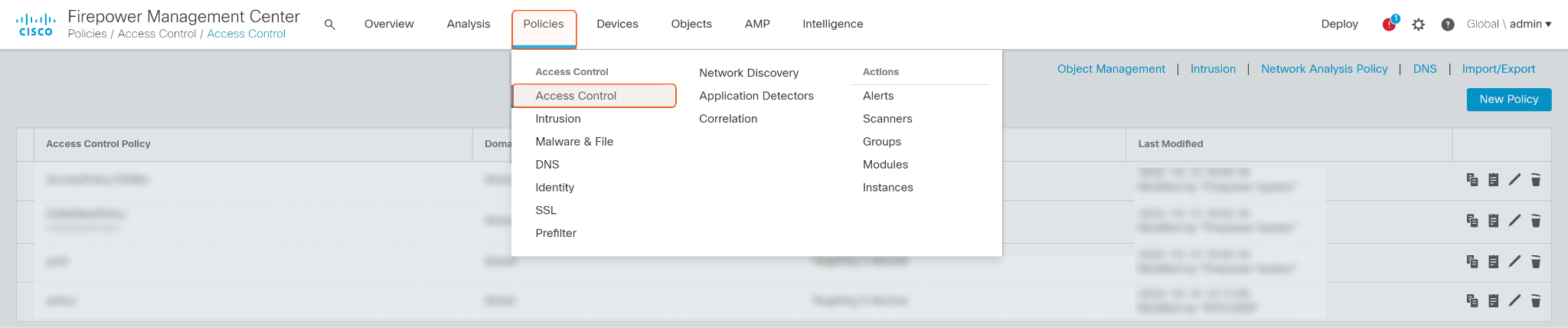
Attach the IP Block List to a policy. Click Policies on the top, then select Access Control on the dropdown list.
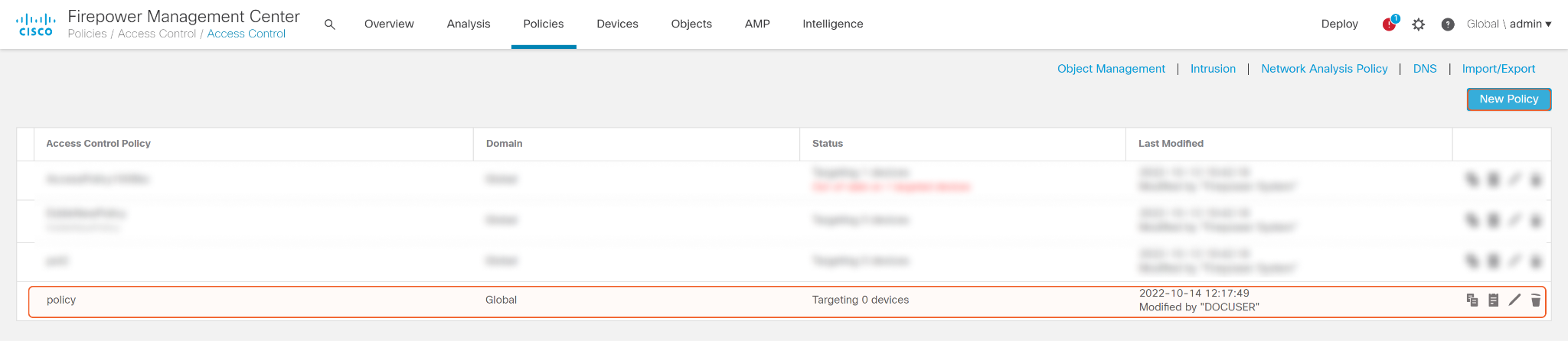
Select a policy on which to attach IP Block List, or create a new policy by clicking New Policy on the top right corner. Make sure the policy is linked to a device, so that device can block the IPs from the list.
In the Security Intelligence tab, go to the Networks tab, then select the newly created IP Block List, and set Available Zones to Any, then click Add to Blacklist to attach the IP Block List that was just created to the Blacklist. After you click that button, the IP Block List will show in the Blacklist box. Click Save to save the changes. The IP Addresses will be blocked if they are added the IP Block List in the policy blacklist.
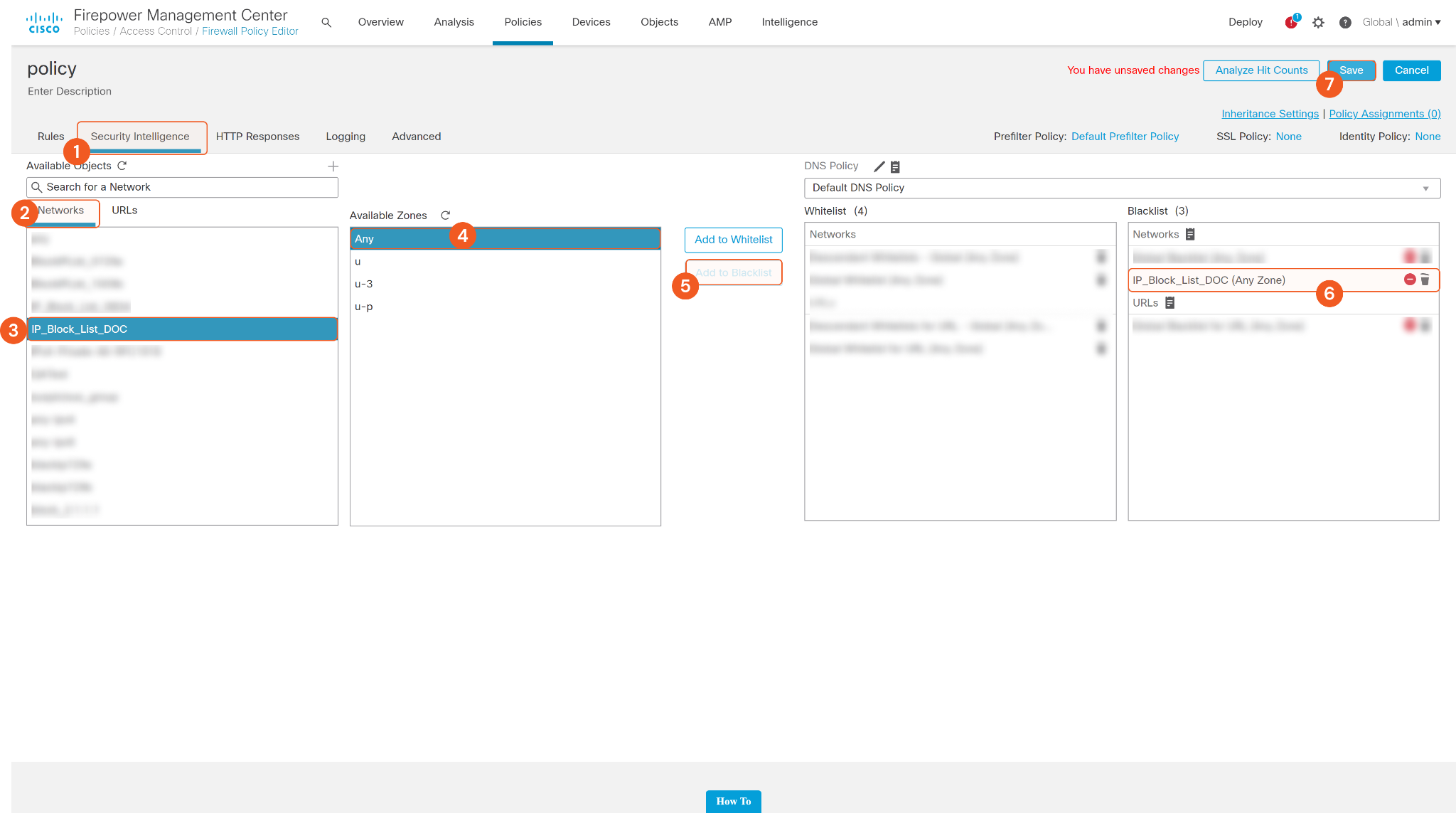
Then run the Block IPs command, and the IPs added to the list will be blocked.
Question 2: How do I create a Firepower URL Block List?
Log into Firepower Management Center.
Click Objects on the top, then click Object Management.
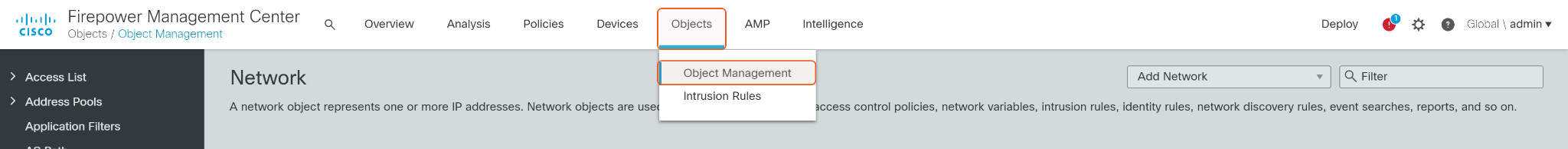
Click URL on the left side, then select Add Group in the Add URL dropdown list on the top.
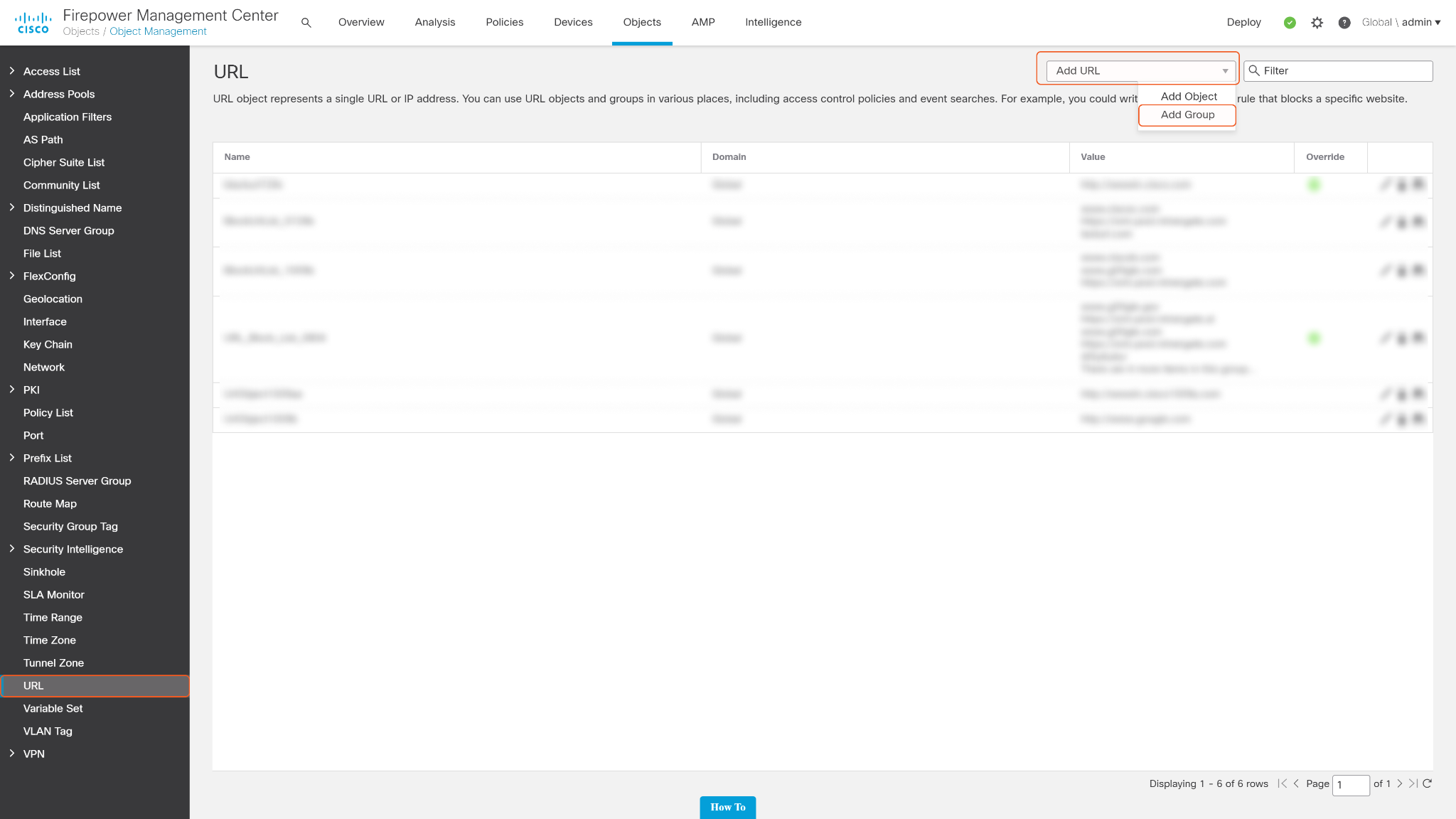
In the pop-up window, enter the Name and Description for the URL Block List. Add existing URL objects to the list or check Allow Overrides and just leave the list blank. Then click Save.
If the object list is empty, a Warning window will appear, click Yes.
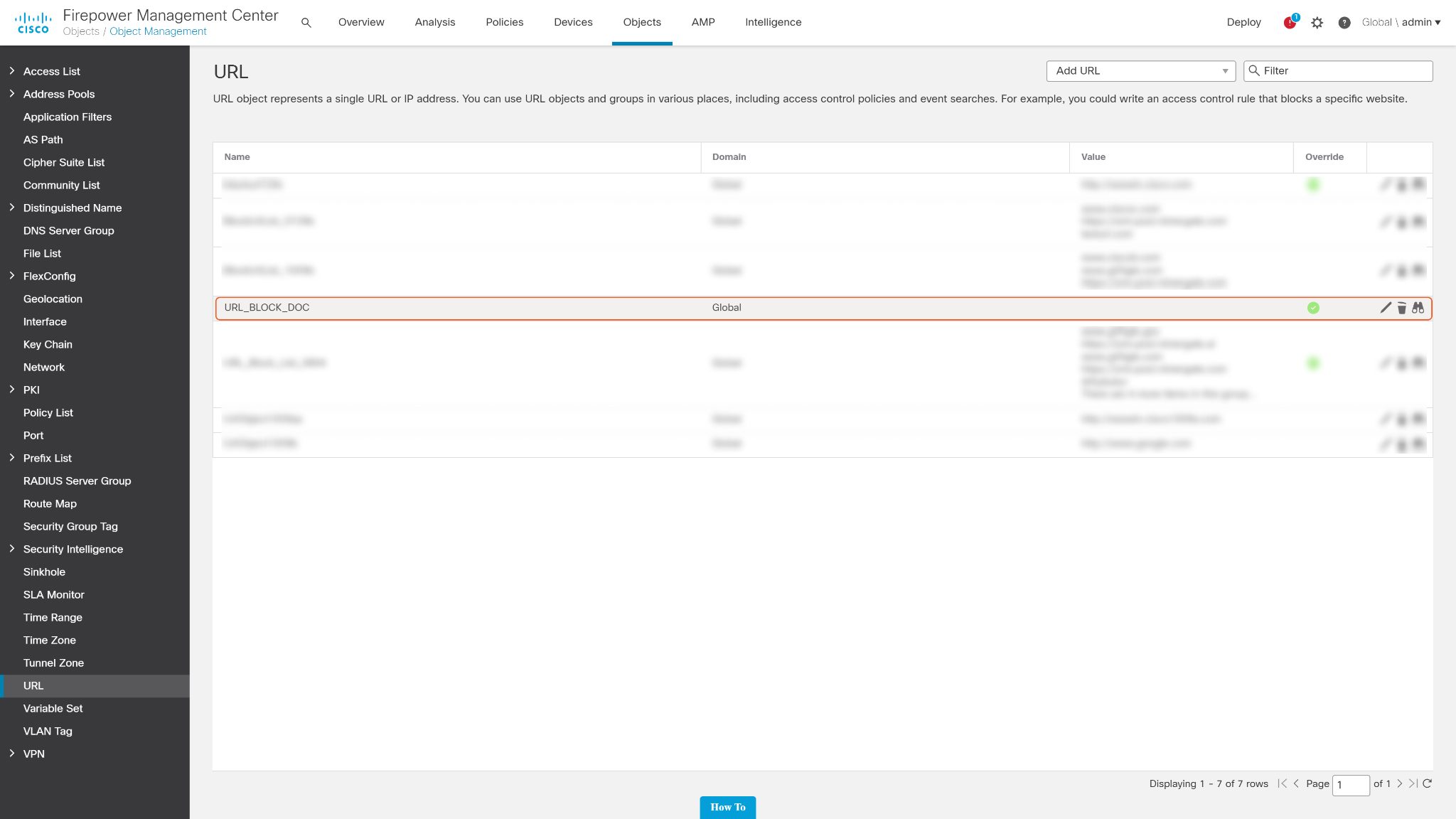
Users should find the URL Block List they just created in the URL object list. Save the name which will be used when blocking URLs.
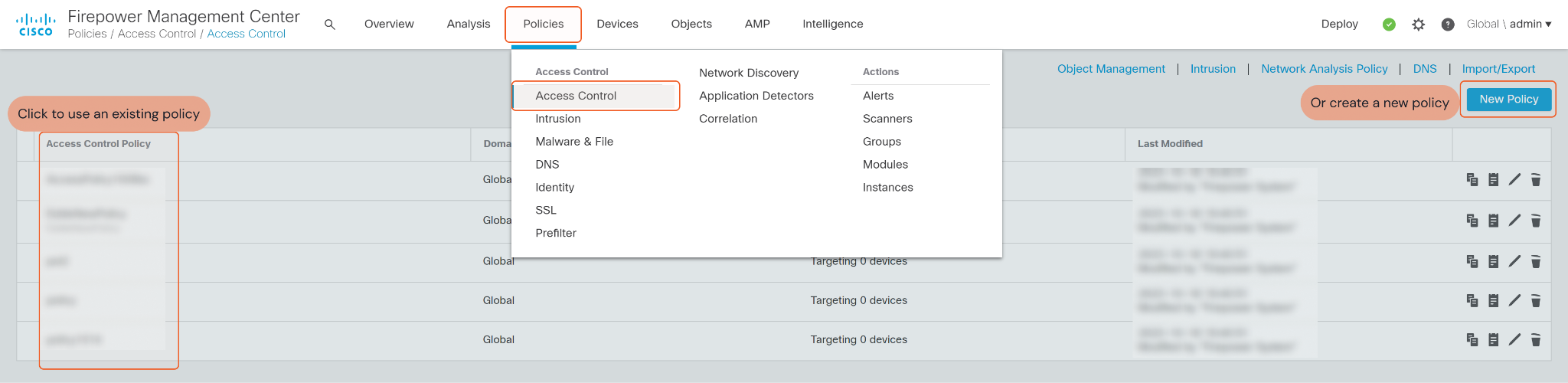
Attach the URL Block List to a policy. Click Policies on the top, then select Access Control on the dropdown list. Select a policy on which to attach URL Block List, or create a new policy by clicking New Policy on the top right corner.
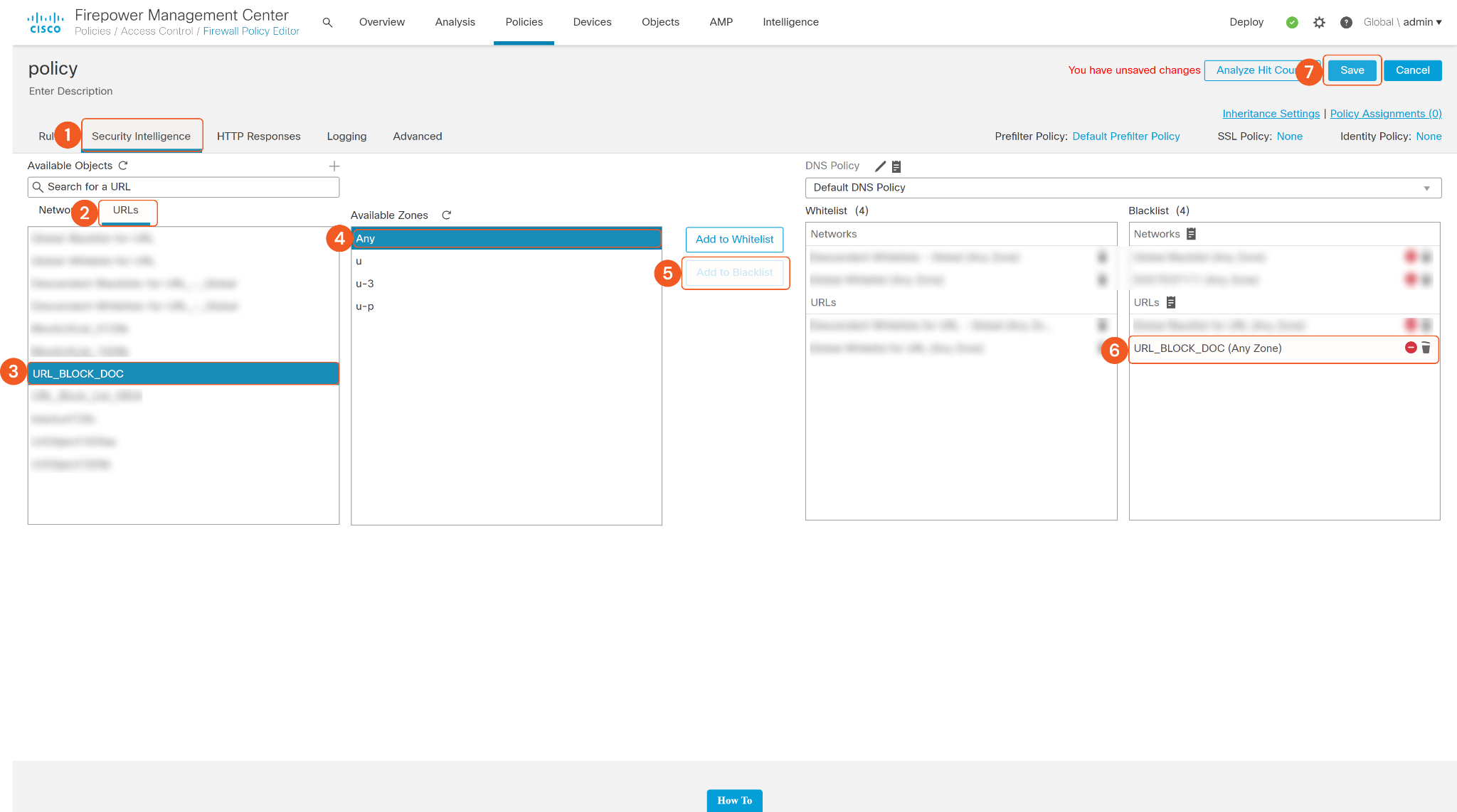
In the Security Intelligence tab, go to the URLs tab, then select the URL Block List you just created. Set Available Zones to Any, then click Add to Blacklist to attach the URL Block List to the Blacklist. Users should find the URL Block List that they just created is displayed under Blacklist URLs. Don’t forget to click Save on the top right corner to save. If the policy is enabled, the URLs added to the URL Block List will be blocked.