CheckPoint Firewall
LAST UPDATED: SEPTEMBER 18, 2025
Overview
CheckPoint Firewall monitors and filters incoming and outgoing network traffic based on an organization's previously established security policies. Integration with CheckPoint covers major actions on firewalls such as add access rule, add threat rule, run script, etc.
D3 Security's integration with the CheckPoint Firewall API v1.8 covers major firewall rule management operations, such as adding access/threat rule, running script, etc. Furthermore, D3's integration also provides Event Intake operation to query firewall logs.
D3 SOAR is providing REST operations to function with CheckPoint Firewall.
CheckPoint Firewall is available for use in:
D3 SOAR | V12.7.83+ |
Category | Network Security |
Deployment Options |
Known Limitations
Starting from release R81 (September 2020), the login request is limited to three per minute. For more information, refer to Heads-up: Management API Remote calls frequency limit on CheckPoint CheckMates.
The API server is active on management servers with 4 GB RAM (or more) and stand-alone servers with 8 GB RAM (or more) by default. D3 recommends a minimum hardware configuration of 4 CPU cores and 12 GB of RAM for on-premise CheckPoint Firewall instances. If the hardware is insufficient, the FetchEvent API command may not execute successfully.
All sessions are private. Changes made by administrators are not visible to others until published. To maintain privacy, objects are locked when being modified, with the administrator's name displayed to help with coordinating work on shared resources. Other administrators can only see that the object is locked and cannot make modifications.
If an API call returns an "object locked" message, you can either take over or disconnect the locking session in CheckPoint SmartConsole, or wait until no session locks the object before executing it.
Connection
To connect to CheckPoint Firewall from D3 SOAR, follow this part to collect the required information below:
Parameter | Description | Example |
Server URL | The URL of the CheckPoint server. | https://***.***.***.*** |
User Name | The username to authenticate the connection. | Admin |
Password | The password to authenticate the connection. | YourPassword |
Permission Requirements
Each endpoint in the CheckPoint Firewall API requires a certain permission scope. The following are required scopes for the commands in this integration:
Command | Required Permission |
Add Threat Exception | Threat Prevention: Policy > Policy Layers: Write; Policy Exceptions: Write Permissions > Profiles: Write; Protections: Write; Settings: Write |
Add Threat Rule | Threat Prevention: Policy > Policy Layers: Write; Policy Exceptions: Write Permissions > Profiles: Write; Protections: Write; Settings: Write |
Block Domains | System: Read Write All |
Block IP Addresses | System: Read Write All |
Block URLs | System: Read Write All |
Delete Access Rules | System: Read Write All |
Discard unpublished changes created by Web API | System: Read Write All |
Fetch Event | System: Read Only All |
Get Access Rule Base | Access Control: Policy > Show Policy (no sub permission need to b e checked) General > Access Control Objects and Settings: Read |
Get Task Status | Management: Management API Login |
Install Policy | System: Read Write All |
Run Script | System: Super User |
Enable/Disable Access Rule | Access Control: Policy > Show Policy (no sub permission need to be checked) General > Access Control Objects and Settings: Read |
Set Threat Exception | Threat Prevention: Policy > Policy Layers: Write; Policy Exceptions: Write Permissions > Profiles: Write; Protections: Write; Settings: Write |
Set Threat Protection | Threat Prevention: Policy > Policy Layers: Write; Policy Exceptions: Write Permissions > Profiles: Write; Protections: Write; Settings: Write |
Set Threat Rule | Threat Prevention: Policy > Policy Layers: Write; Policy Exceptions: Write Permissions > Profiles: Write; Protections: Write; Settings: Write |
Show Access layers | Access Control: Policy > Show Policy (no sub permission need to be checked) General > Access Control Objects and Settings: Read |
Show Application Site Categories | Management: Management API Login |
Show Published Changes between a period of time or two sessions | System: Read Only All |
Show Exception Group | Threat Prevention: Policy > Policy Layers: Read; Policy Exceptions: Read Permissions > Profiles: Read; Protections: Read; Settings: Read |
Show Exception Groups | Threat Prevention: Policy > Policy Layers: Read; Policy Exceptions: Read Permissions > Profiles: Read; Protections: Read; Settings: Read |
Show Logs | System: Read Only All |
Show Policy Packages | System: Read Only All |
Show Session Objects | Management: Management API Login |
Show Threat Exception | Threat Prevention: Policy > Policy Layers: Read; Policy Exceptions: Read Permissions > Profiles: Read; Protections: Read; Settings: Read |
Show Threat Layers | Threat Prevention: Policy > Policy Layers: Read; Policy Exceptions: Read Permissions > Profiles: Read; Protections: Read; Settings: Read |
Show Threat Profiles | Threat Prevention: Policy > Policy Layers: Read; Policy Exceptions: Read Permissions > Profiles: Read; Protections: Read; Settings: Read |
Show Threat Protection | Management: Management API Login |
Show Threat Protections | Management: Management API Login |
Show Threat Rule | Threat Prevention: Policy > Policy Layers: Read; Policy Exceptions: Read Permissions > Profiles: Read; Protections: Read; Settings: Read |
Show Threat Rule Base | Threat Prevention: Policy > Policy Layers: Read; Policy Exceptions: Read Permissions > Profiles: Read; Protections: Read; Settings: Read |
Show Threat Rule Exception Rule Base | Threat Prevention: Policy > Policy Layers: Read; Policy Exceptions: Read Permissions > Profiles: Read; Protections: Read; Settings: Read |
Test Connection | Management: Management API Login |
As CheckPoint Firewall is using role-based access control (RBAC), the D3 connector will be generated based on a specific user account and the application. Therefore, the command permissions are inherited from the user account's role. Users need to configure their user profile from the CheckPoint Firewall console for each command in this integration.
READER NOTE
CheckPoint Firewall's default permission profiles (sorted from the most permissions to the least) are as follows:
Super User: Full Read/Write Permissions including managing administrators and sessions.
Read Write All: Full Read/Write Permissions.
Read Only All: Full Read Permissions, no Write Permissions.
In the permissions table above, the three default permission profiles are represented by "System: Super User", etc. When a command requires one of the three default profiles, you can assign the default profile or create a customized role with the same permissions as the system profiles.
Configuring CheckPoint Firewall to Work with D3 SOAR
Creating Customized Roles
Log into CheckPoint SmartConsole.
On the left sidebar, navigate to Manage & Settings > Permissions & Administrators > Permission Profiles.
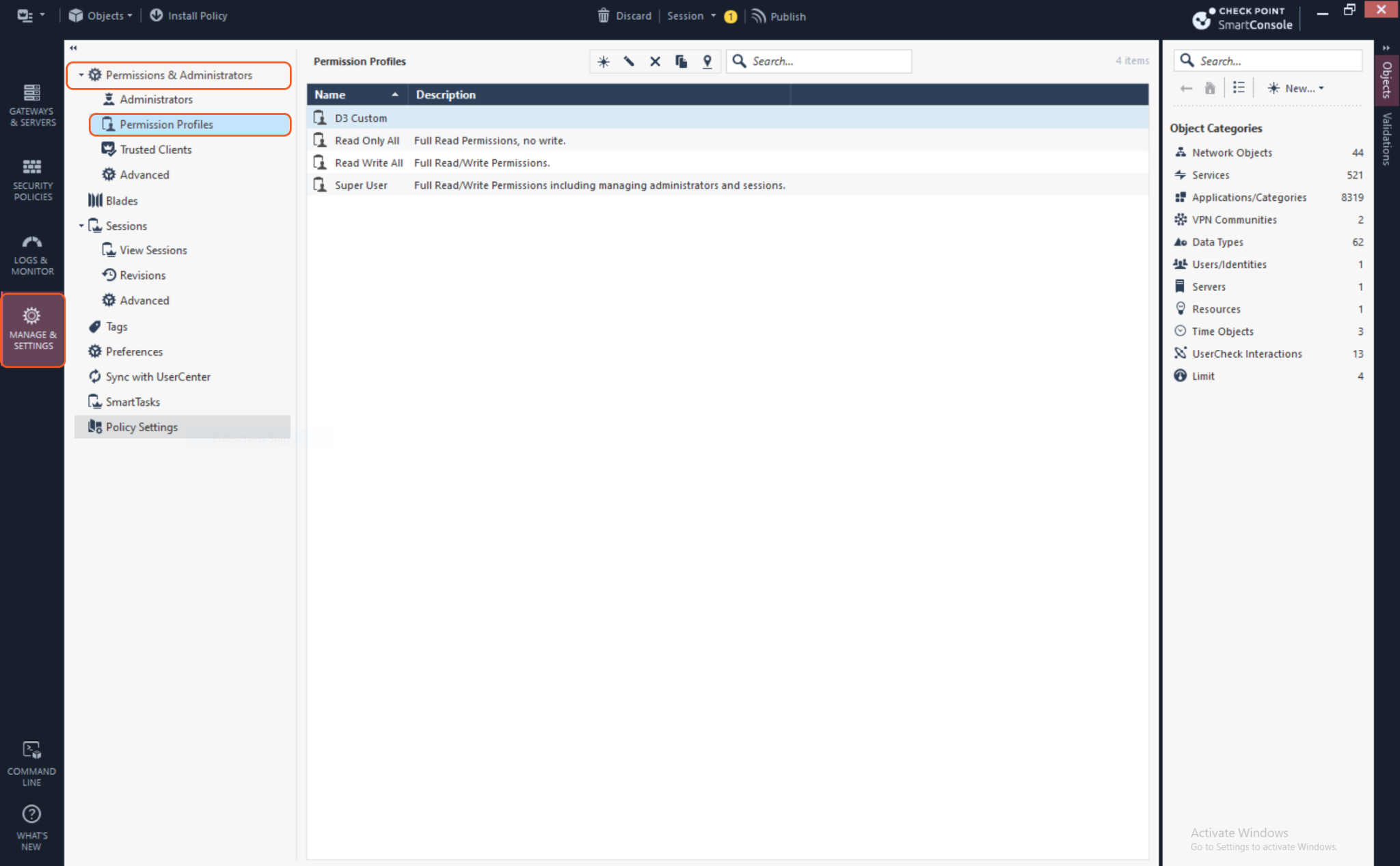
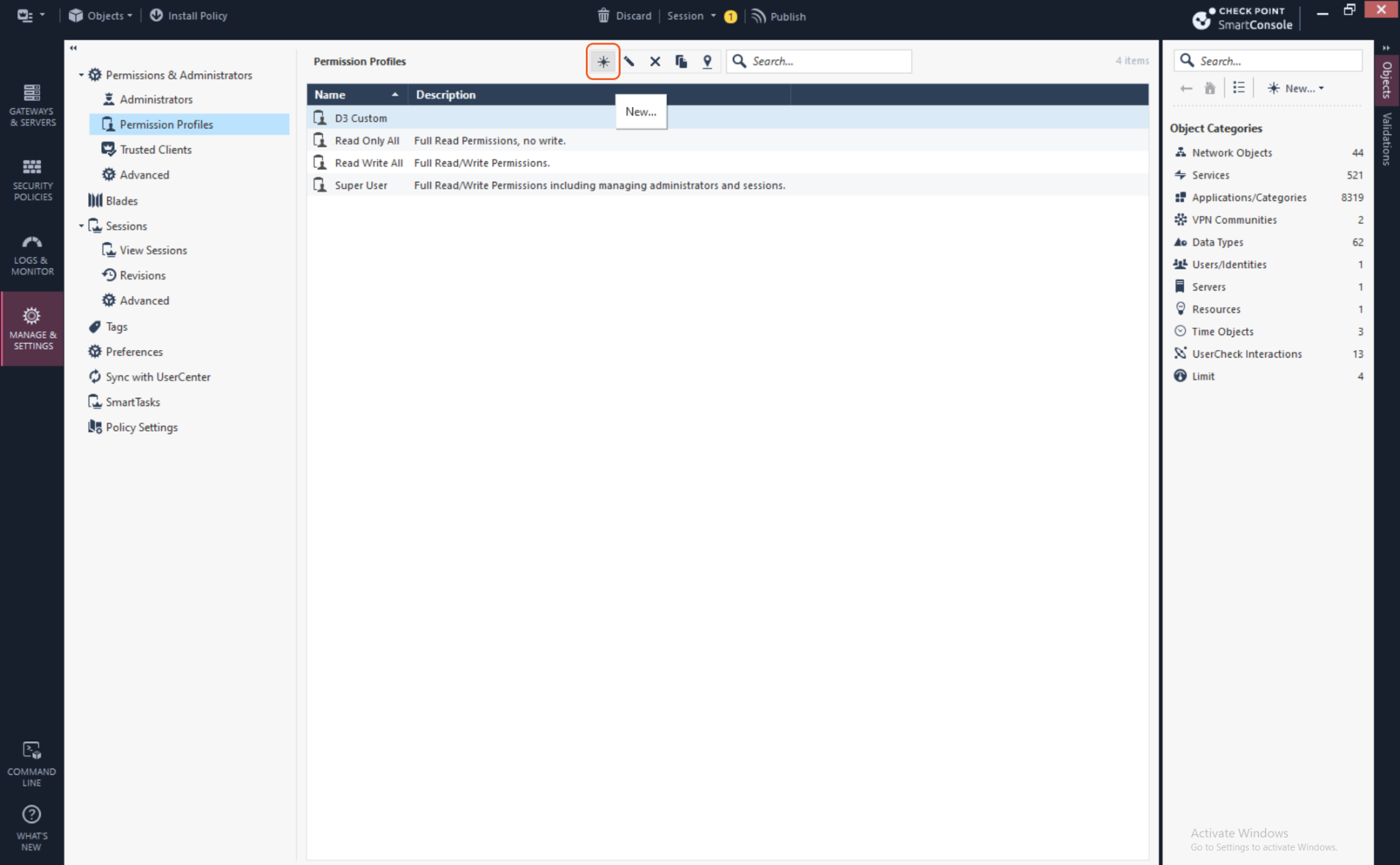
Above the Permission Profiles table, click the star icon to create a new role.
Name the role, then configure the different access permissions as needed. Click OK.
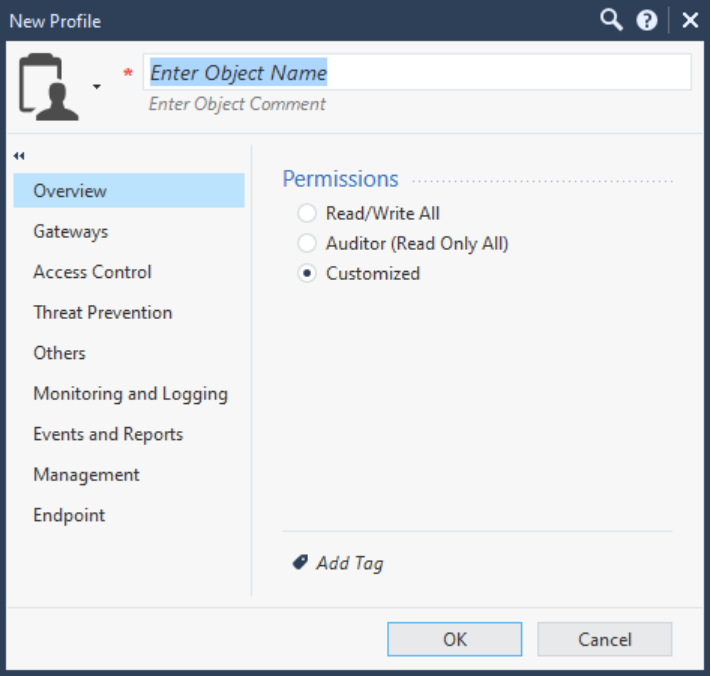
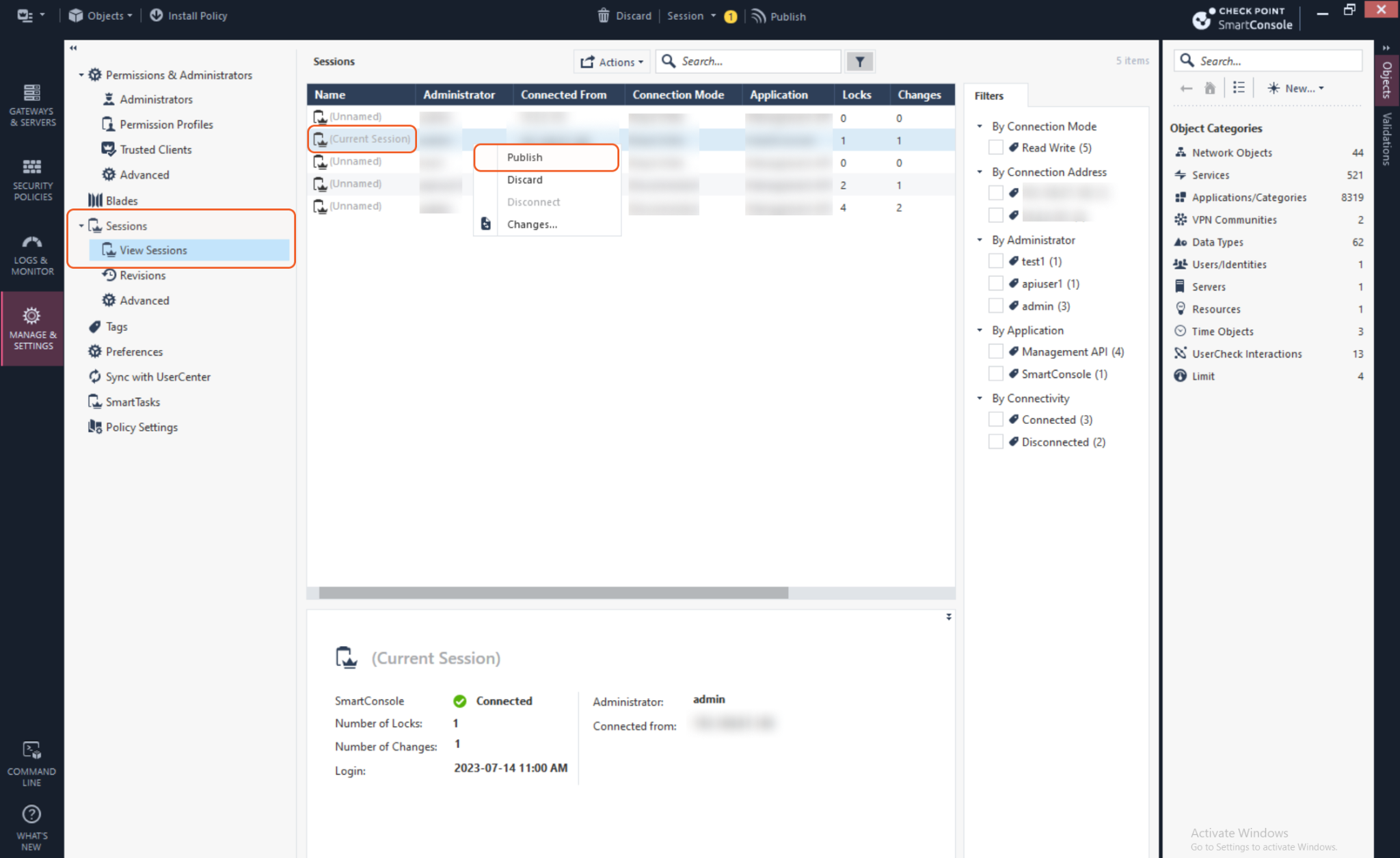
To save the changes, navigate to Sessions > View Sessions in the left sidebar and locate the Current Session. Right click the session and select Publish.
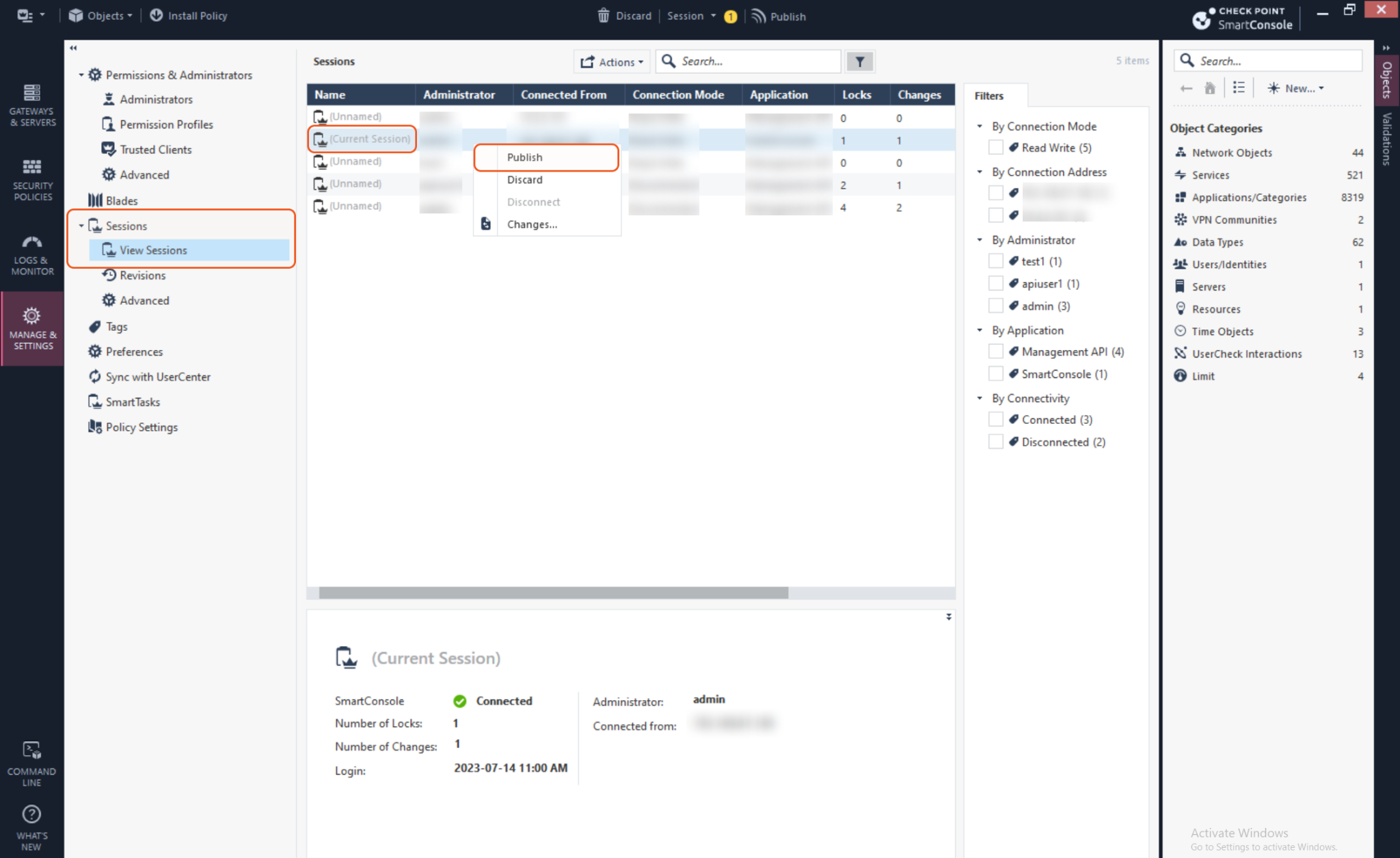
Creating a New User and Assigning Customized Roles
On the left sidebar, navigate to Manage & Settings > Permissions & Administrators > Administrators.
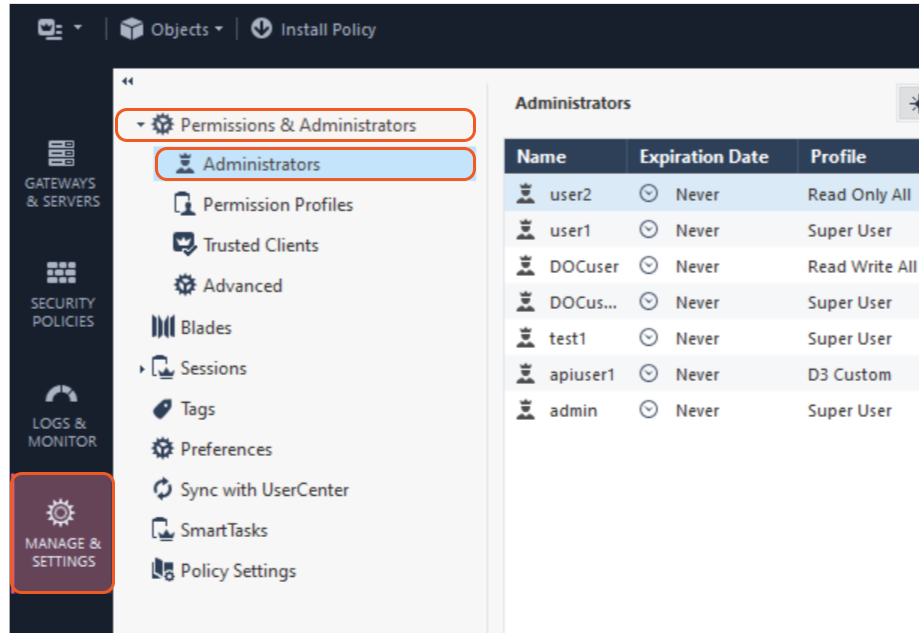
Above the Administrators table, click the star icon to create a new user.
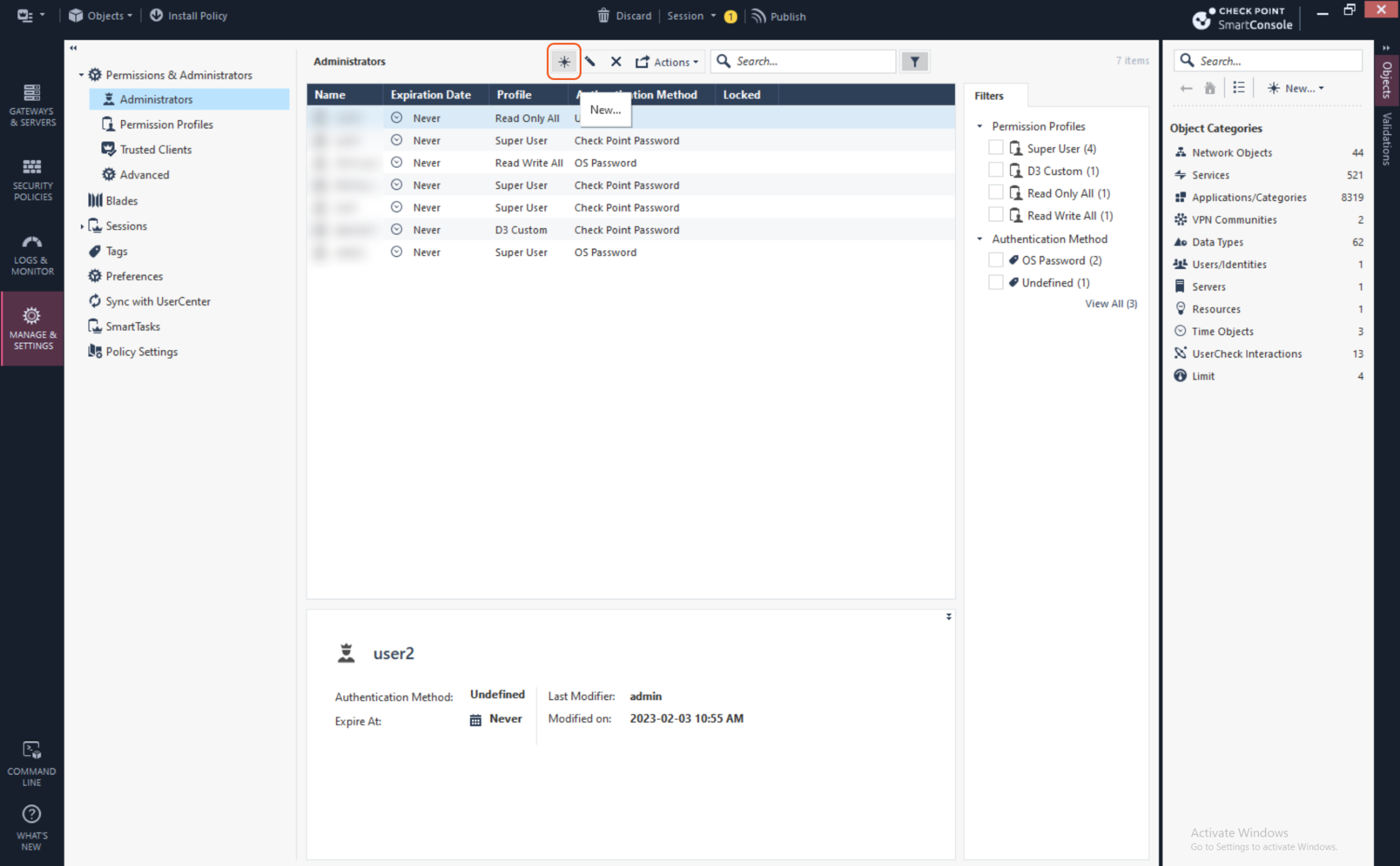
Fill in the required fields for the user details. Ensure to select CheckPoint Password as the Authentication Method in the drop down menu. The Permission Profile dropdown menu defines the role and the user's permissions. Select the role you have created for the user and click OK to create the user.
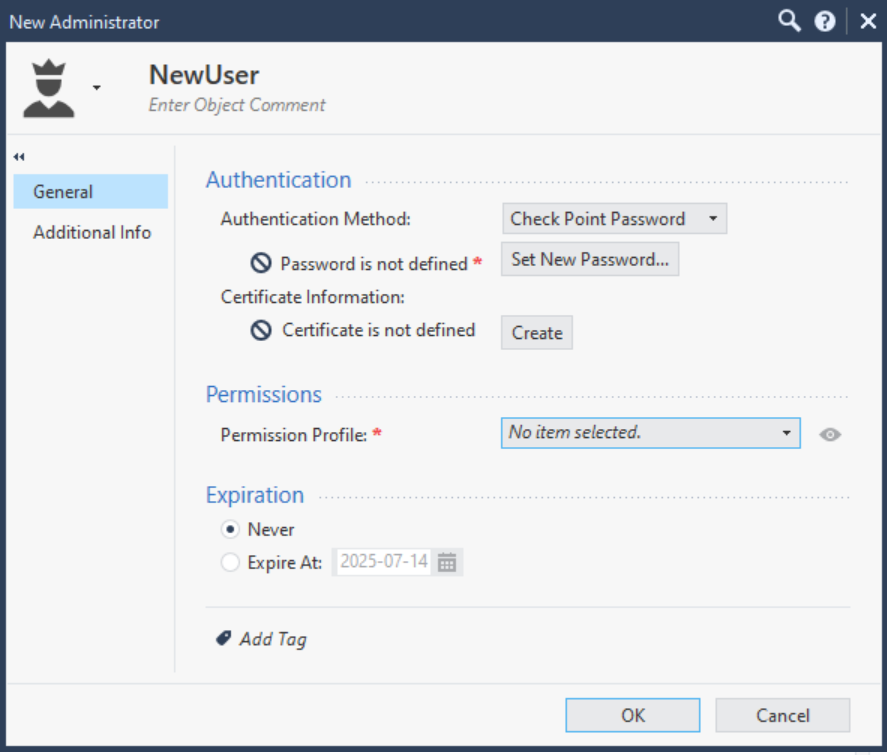
To save the changes, navigate to Sessions > View Sessions in the left sidebar and locate the Current Session. Right click the session and select Publish.
Configuring D3 SOAR to Work with CheckPoint Firewall
Log in to D3 SOAR.
Find the CheckPoint Firewall integration.
.png?inst-v=40cb8c82-2e72-4b9d-aa5c-d42e6b974429)
Navigate to Configuration on the top header menu.
Click on the Integration icon on the left sidebar.
Type CheckPoint Firewall in the search box to find the integration, then click it to select it.
Click + Connection, on the right side of the Connections section. A new connection window will appear.
Configure the following fields to create a connection to CheckPoint Firewall.
.png?inst-v=40cb8c82-2e72-4b9d-aa5c-d42e6b974429)
Connection Name: The desired name for the connection.
Site: The site on which to use the integration connection. Use the drop-down menu to select the site. The Share to Internal Sites option enables all internal sites to use the connection. Selecting a specific site will only enable that site to use the connection.
Recipient site for events from connections Shared to Internal Sites: This field is displayed when Share to Internal Sites is selected for the Site field, allowing selection of the internal site for deploying the integration connection.
Agent Name (Optional): The proxy agent required to build the connection. Use the dropdown menu to select the proxy agent from a list of previously configured proxy agents.
Description (Optional): The description for the connection.
Tenant (Optional): When configuring the connection from a master tenant site, users can choose the specific tenant sites with which to share the connection. Once this setting is enabled, users can filter and select the desired tenant sites from the dropdowns to share the connection.

Configure User Permissions: Defines which users have access to the connection.
Active: The checkbox that enables the connection to be used when selected.
System: This section contains the parameters defined specifically for the integration. These parameters must be configured to create the integration connection.
.png?inst-v=40cb8c82-2e72-4b9d-aa5c-d42e6b974429)
1. Input the domain level Server URL of your CheckPoint Firewall instance.
2. Input the CheckPoint Firewall account User Name. The default user name is admin. You can remove the default username and replace it with another username.
3. Input the CheckPoint Firewall account Password.4. (Optional) Input the domain if it is a multi-domain instance.
Enable Password Vault: An optional feature that allows users to take the stored credentials from their own password vault. Refer to the password vault connection guide if needed.
Connection Health Check: Periodically checks the connection status by scheduling the Test Connection command at the specified interval (in minutes). Available only for active connections, this feature also allows configuring email notifications for failed attempts.
Test the connection.
.png?inst-v=40cb8c82-2e72-4b9d-aa5c-d42e6b974429)
Click on the Test Connection button to verify credentials and connectivity. A success alert displays Passed with a green checkmark. If the connection fails, review the parameters and retry.
Click OK to close the alert window.
Click + Add to create and add the configured connection.
Commands
CheckPoint Firewall includes the following executable commands for users to set up schedules or create playbook workflows. With the Test Command, users can execute these commands independently for playbook troubleshooting.
Integration API Note
For more information about the CheckPoint Firewall API, refer to the CheckPoint Firewall API reference.
READER NOTE
Certain permissions are required for each command. Refer to the Permission Requirements and Configuring CheckPoint Firewall to Work with D3 SOAR for details.
Note for Time-related parameters
The input format of time-related parameters may vary based on user account settings, which may cause the sample data in commands to differ from what is displayed. To adjust the time format, follow these steps:
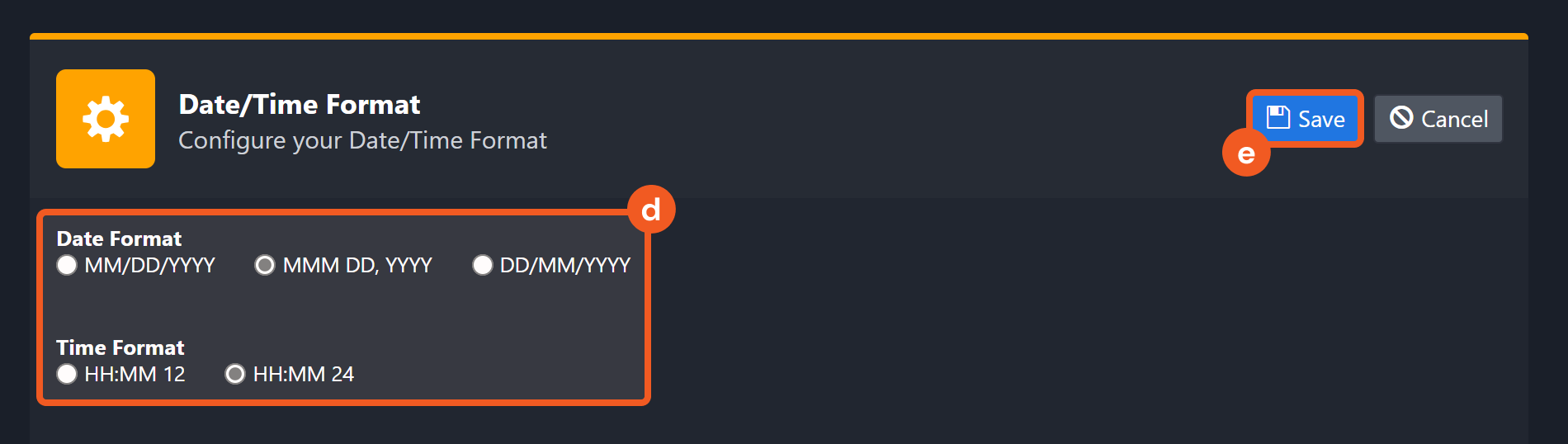
Navigate to Configuration > Application Settings. Select Date/Time Format.
Choose the desired date and time format, then click on the Save button.
The selected time format will now be visible when configuring Date/Time command input parameters.
Add Threat Exception
Creates a threat exception.
READER NOTE
"Layer Name Or UID", "Parent Rule Name Or Number Or UID" and "Exception Group Name Or UID" are optional parameters to run this command.
If the threat exception is under a rule, Layer Name Or UID is a required parameter.
Run the Show Threat Layers command to obtain Layer Name and UIDs. Layer Names can be found in the returned raw data at the path $.threat-layers[*].name; UIDs can be found at the path $.threat-layers[*].uid.
If the threat exception is under an exception group, the Layer Name Or UID parameter must not be defined. Any input value will be omitted.
Run the Show Threat Rule Base command to obtain Parent Rule Names, Numbers and UIDs. Rule UIDs can be found in the returned raw data at the path $.rulebase[*].uid; Rule numbers can be found in the returned raw data at the path $.rulebase[*].rule-number. Rule Names can be found in the returned raw data at the path $.rulebase[*].name.
Run the Show Exception Groups command to obtain Exception Group Names and UIDs. Exception Group Names can be found in the returned raw data at the path $.objects[*].name; Exception Group UID can be found in the returned raw data at the path $.objects[*].uid.
ALERT
To add a threat exception, you must define at least one of the Parent Rule Name Or Number Or UID or the Exception Group Name Or UID parameters, but not both.
If you are adding a threat exception to a rule, the Parent Rule Name Or Number Or UID parameter is required to run this command.
Ensure that the values entered for Layer Name Or UID and Parent Rule Name Or Number Or UID match. It is suggested to run the Show Threat Layers command to obtain the desired layer, then use that layer to run the Show Threat Rule Base command and select the desired threat rule. Failure to match the values may result in errors.
If you are adding the exception to an Exception Group, the Exception Group Name Or UID parameter is required to run this command. Do not fill "Layer Name Or UID" parameter, value will be omitted in this case.
Input
Input Parameter | Required/Optional | Description | Example |
Layer Name Or UID | Optional | The name or UID of the layer that the rule belongs to. Layer UIDs can be obtained using the Show Threat Layers command. If the Parent Rule Name Or Number Or UID parameter is defined, then this parameter is required and the specified rule must match the layer. Otherwise, if the Exception Group Name Or UID parameter is defined, this parameter must not be defined. Any entered value will be omitted. | Standard Threat Prevention |
Position | Required | The position (i.e. Top or Bottom) in the rulebase. | Bottom |
Parent Rule Name Or Number Or UID | Optional | The name, number or UID of the parent rule. Rule numbers and UIDs can be obtained using the Show Threat Rule Base command. Note: (1) Only one of the Parent Rule Name Or Number OR UID or Exception Group Name Or UID parameters can be defined per execution of the command, but at least one must be defined. (2) If this parameter is defined, you must define the matching Layer Name Or UID parameter. Entering a rule and layer that do not match will result in an error. | ***** |
Exception Group Name Or UID | Optional | The name or UID of the exception group. Exception Group names and UIDs can be obtained using the Show Exception Groups command. Note: (1) Only one of the Exception Group Name Or UID or Parent Rule Name Or Number OR UID parameters can be defined per execution of the command, but at least one must be defined. (2) If this parameter is defined, you cannot define the Layer Name Or UID parameter. The value entered for the layer will be omitted. | TestExceptionGroup0917001 |
Exception Name | Required | The name of the exception. | exception091700cc |
Comment | Optional | A comment for the exception. | create exception091700cc |
Track | Optional | The tracking method for protection. | log |
Protected Scope | Optional | The names or UIDs of network objects defining the protected scope. | All_Internet |
Install On | Optional | The name or UID of the gateways to install the policy on. | Policy Targets |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Add Threat Exception failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Missing parameter: [position]. |
Error Sample Data Add Threat Exception failed. Status Code: 400. Message: Missing parameter: [position]. |
Add Threat Rule
Creates a threat rule.
READER NOTE
Layer Name Or UID is a required parameter to run this command.
Run the Show Threat Layers command to obtain Layer Name and UIDs. Layer Name can be found in the returned raw data at the path $.threat-layers[*].name; UID can be found at the path $.threat-layers[*].uid.
Input
Input Parameter | Required/Optional | Description | Example |
Layer Name Or UID | Required | The name or UID of the layer that the threat rule belongs to. Layer names and UIDs can be obtained using the Show Threat Layers command. | Standard Threat Prevention |
Position | Required | The position (i.e. Top or Bottom) in the rulebase. | Bottom |
Name | Required | The name of the threat rule. | Test Rule |
Comment | Optional | A comment for the threat rule. | EddieTestComment |
Track | Optional | The tracking method for protection. | Alert |
Action | Optional | The action of the threat rule. | Basic |
Protected Scope | Optional | The names or UIDs of network objects defining the protected scope. | All_Internet |
Install On | Optional | The name or UID of the gateways to install the policy on. | Policy Targets |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Add Threat Rule failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Requested object [xxx] not found. |
Error Sample Data Add Threat Rule failed. Status Code: 404. Message: Requested object [xxx] not found. |
Block Domains
Adds a policy access rule to block domains.
READER NOTE
Layer Name Or UID is a required parameter to run this command.
Run the Show Access Layers command to obtain Layer Name Or UID. Layer Names can be found from the returned raw data at the path $.access-layers[*].name; UIDs can be found from the returned raw data at the path $.access-layers[*].uid.
Please note that the input layer must be included in the firewall blade.
Error for "layer3" as an example: "Validate the ACCESS_LAYER 'layer3' failed, this layer hasn't included the 'Firewall' blade."
To know if the layer you select includes the firewall blade, set the Show Details parameter to True when running the Show Access Layers command. In the returned raw data, check path $.access-layers[*].firewall for your selected layer. If the value is False, then the layer is not included; if it is True, then it is included.
It can also be enabled from within the UI.
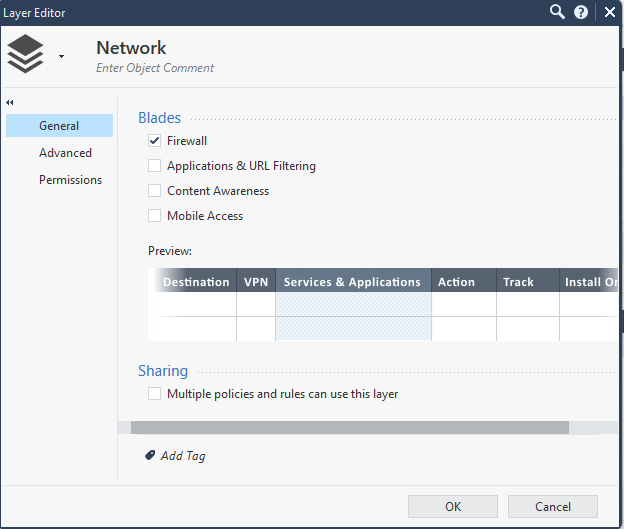
Domains can be unblocked by removing the rule name (delete the input rule name or delete the auto generated rule name in the returned raw data of the block domains command at the path $.name) using the Delete Access Rules command.
To check your created blocked domain rules, locate which policy the input layer is under. Then navigate to that policy page to view applied rules.
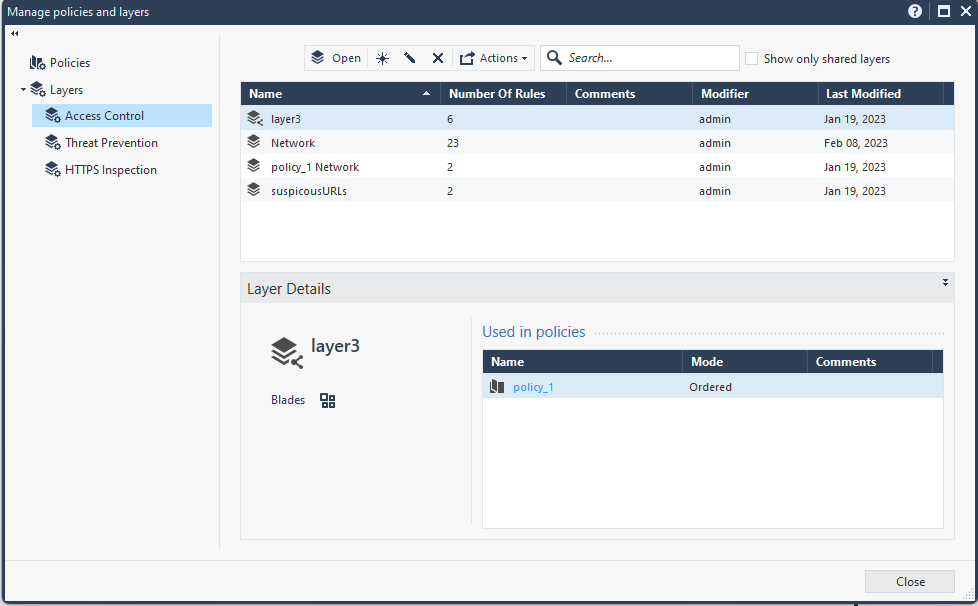
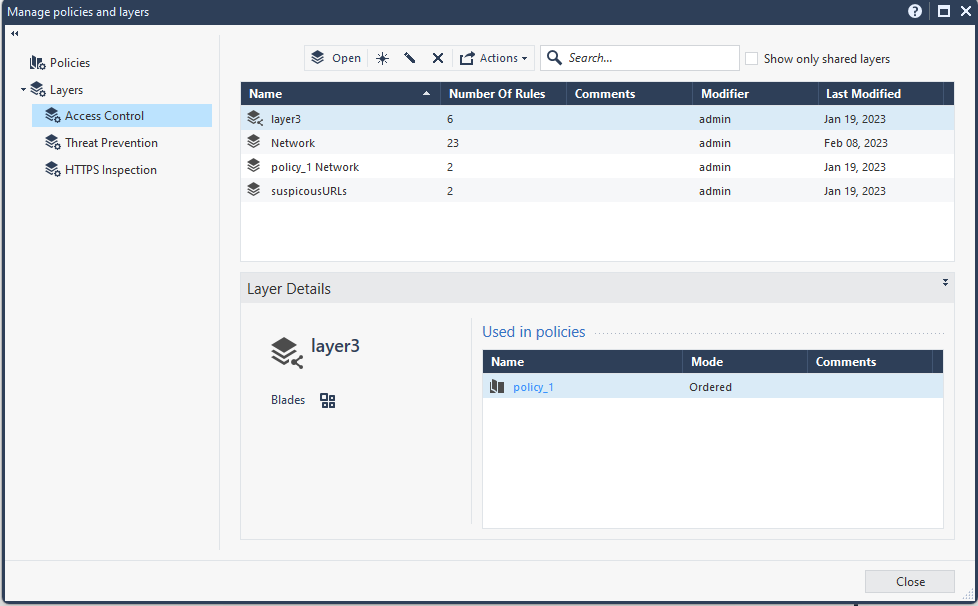
Click the + on the top of the policy page, then Manage policies and layers.
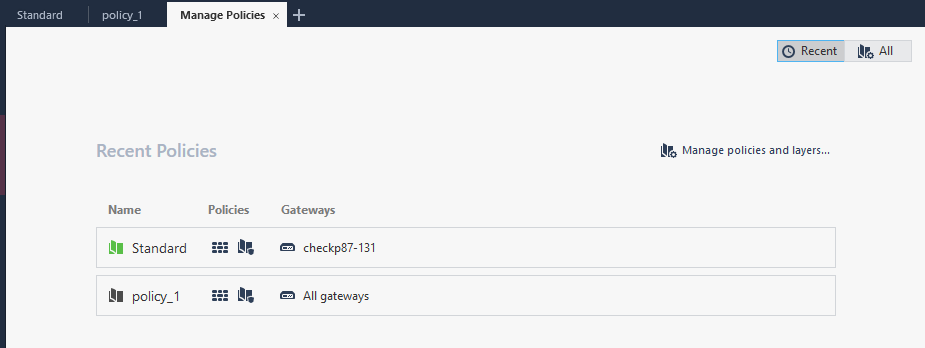
Navigate to Layers > Access Control, select a layer, then check Used in policies. In this example, layer3 is under policy_1.
Navigate to policy_1 to check the created rules.
Input
Input Parameter | Required/Optional | Description | Example |
Domains | Required | The domain strings to block. |
JSON
|
Is Root Domain | Optional | The option to specify whether the domains are DNS root domain or sub DNS domain. The type will apply to all the domains provided in the first parameter Domains. Set to True for DNS root domain, and False for sub DNS domain. The default value is False. | True |
Direction | Optional | The blocking direction of the rule. The available values are From, To, or Both. | to |
Rule Name | Optional | The rule name to save the block domain operation under the specified layer. If this parameter is not defined, D3 will create a new rule with the naming rule of domain_bock_datetime, e.g.: domain_block_to_rule_20230321095001. | domain_block_to_rule_*** |
Layer Name Or UID | Required | The name or UID of the policy layer from the Access Control policy for the new block domains rule to attach to. The layer name or UID can be obtained using the Show Access Layers command. | ***-***-***-***-*** |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Block Domains failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: generic_err_object_not_found. |
Error Sample Data Block Domains failed. Status Code: 404. Message: generic_err_object_not_found. |
Block IP Addresses
Creates a new firewall access rule to block specified IP addresses.
READER NOTE
IP Addresses can be unblocked by removing the Rule Name Prefix using the Delete Access Rules command.
Please note that the input layer must be included in the firewall blade.
E.g. Error for "layer3": "Validate the ACCESS_LAYER 'layer3' failed, this layer hasn't included the 'Firewall' blade."
To know if the selected layer includes the firewall blade, set the Show Details parameter to True when running the Show Access Layers command. In the returned raw data, check path $.access-layers[*].firewall for the selected layer. If the value is False, then the layer is not included; if it is True, then it is included.
It can also be enabled from within the UI.
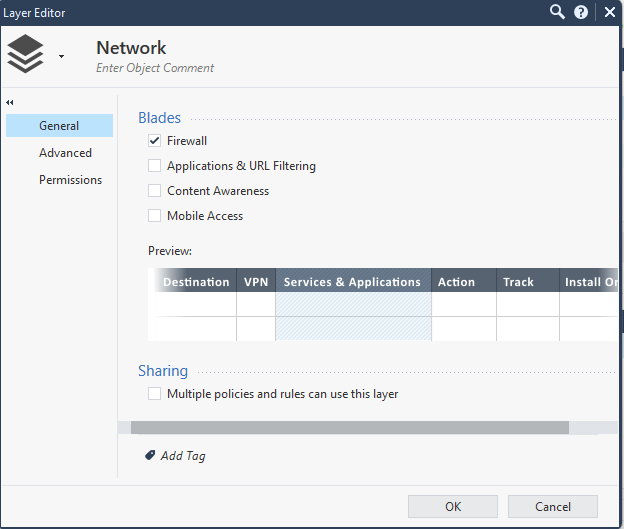
Rule name prefix-to-ip + Rule name prefix-from-ip depending on the chosen direction. If both are chosen, 2 will be returned.
To review the created blocked IP rules, it's necessary to identify the policy located within the input layer. Subsequently, navigate to the respective policy page to access and view the rules.
Click the + on the top of the policy page, then Manage policies and layers.
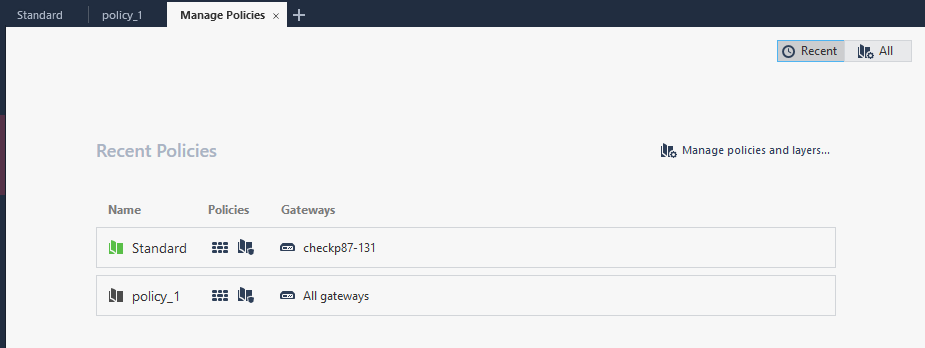
Navigate to Layers > Access Control, select a layer, then check Used in policies. In this example, layer3 is under policy_1.
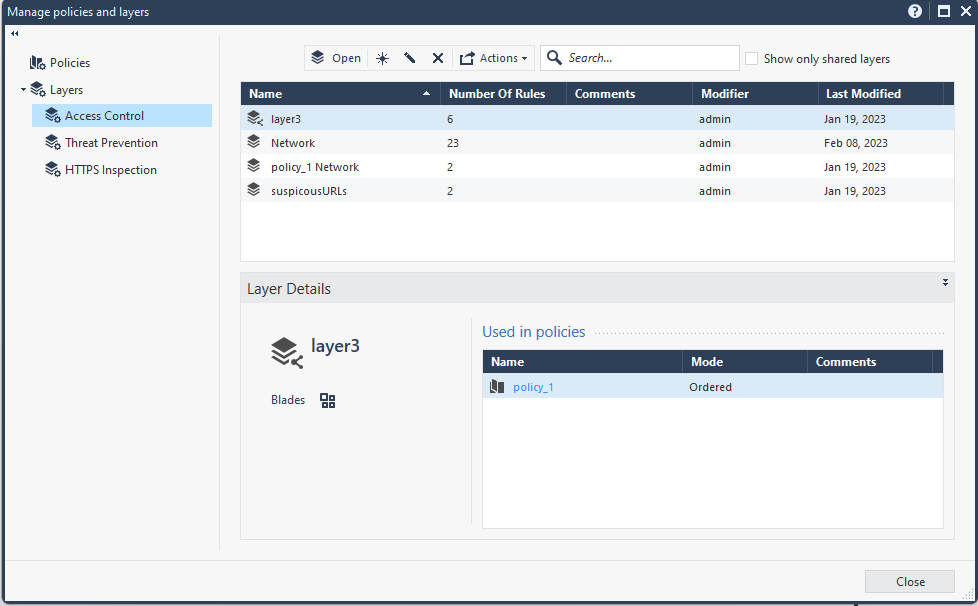
Navigate to policy_1 to check the created rules.
Input
Input Parameter | Required/Optional | Description | Example |
IP Addresses | Required | The list of IP addresses to block. |
JSON
|
Direction | Optional | The blocking direction (i.e. From, To, or Both) of the rule. The default direction is both. | Both |
Rule Name Prefix | Required | Defines the rule name prefix of the access rule for each IP Address. When the block action is executed, CheckPoint Firewall enhances this prefix by appending specific details. The resulting format is: [Chosen Rule Name Prefix]-[Block Direction]- [Blocked Entity]. If no block direction has been defined, two rules will be created for each direction. | BlockIPs2 |
Layer Name or UID | Required | The name or UID of the layer that the rule belongs to. The layer name or UID can be obtained using the Show Access Layers command. | Network |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Block IP Addresses failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: More than one object named 'xxx' exists. |
Error Sample Data Block IP Addresses failed. Status Code: 400. Message: More than one object named 'xxx' exists. |
Block URLs
Blocks URLs by adding a new policy rule to the specified "Applications & URL Filtering" policy layer.
READER NOTE
Category Name and "Layer Name Or UID" are required parameters to run this command.
Run the Show Application Site Categories command to obtain the Category Name. Category Names can be found in the returned raw data at the path $.objects[*].name.
Run the Show Access Layers command to obtain Layer Name or UID. Layer Names can be found in the returned raw data at the path $.access-layers[*].name; UIDs can be found in the returned raw data at the path $.access-layers[*].uid.
URLs can be unblocked by removing the rule name (delete the input rule name or delete the auto generated rule name in the returned raw data of the block domains command at the path $.name) using the Delete Access Rules command.
Please note that the input layer must be included in the Applications & URL Filtering blade.
Error for "layer3" as an example: "Validate the ACCESS_LAYER 'layer3' failed, this layer hasn't included the 'Applications & URL Filtering' blade."
To know if the selected layer includes the Applications & URL Filtering blade, set the Show Details parameter to True when running the Show Access Layers command. In the returned raw data, check under the path $.access-layers[*].applications-and-url-filtering for the selected layer. If the value is False, then the layer is not included; if it is True, then it is included.
It can also be enabled from within the UI.
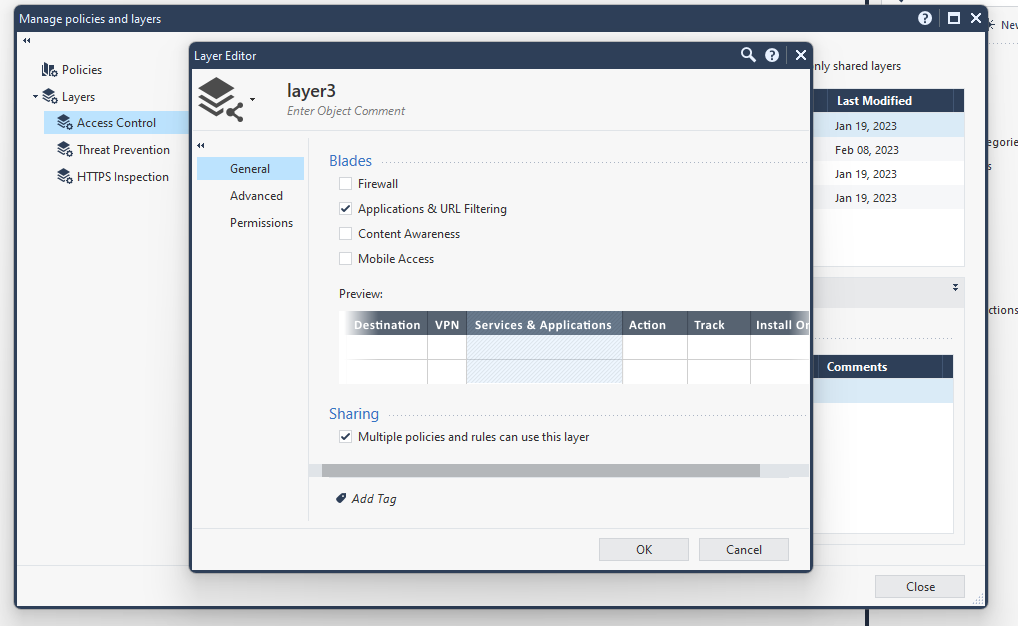
If no rule name has been defined, D3 will create a new rule with the naming rule of url_block_datetime, e.g.: url_block_20230321095001.
To review created blocked url rules, it is necessary to determine which policy is the input layer under. Subsequently, navigate to that policy page to view its rules.
Click the + on the top of the policy page, then Manage policies and layers.
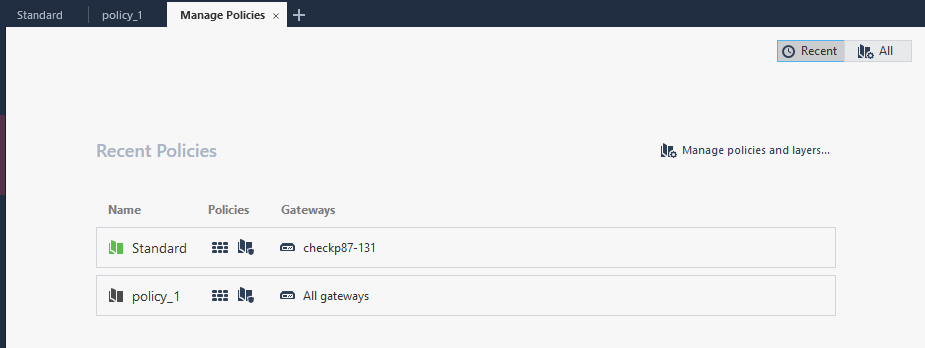
Navigate to Layers > Access Control, select a layer, then check Used in policies. In this example, layer3 is under policy_1.
Navigate to policy_1 to check the created rules.
Input
Input Parameter | Required/Optional | Description | Example |
URL(s) | Required | The URL(s) to block. |
JSON
|
Category Name | Required | The primary application or site category of the URLs based on their most defining aspect. The application category layer name can be obtained from the Show Application Site Categories command. | Art / Culture |
URL(s) Defined as Regex Expressions | Optional | The expression that states if the designated URL is defined as a Regular Expression or not. | True |
Rule Name | Optional | The rule name to save the block domain operation under the specified layer. If this parameter is not defined, D3 will create a new rule with the naming rule of url_block_datetime, e.g.: url_block_20230321095001. | url_block_*** |
Layer Name Or UID | Required | The name or UID of the policy layer from the Access Control policy for the new block urls rule to attach to. The layer name or UID can be obtained using the Show Access Layers command. | ***-***-***-***-*** |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Block URLs failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: generic_err_object_not_found. |
Error Sample Data Block URLs failed. Status Code: 404. Message: generic_err_object_not_found. |
Delete Access Rules
Deletes the specified firewall access rules.
READER NOTE
"UIDs Or Names Or Rule Numbers" and "Layer Name or UID" are required parameters to run this command.
Run the Get Access Rule Base command to obtain UIDs. UID can be found from the returned raw data at the path $.rulebase[*].uid; names can be found from the returned raw data at the path $.rulebase[*].name.
Run the Show Access Layers command to obtain access layers. Access layer UIDs can be found in the returned raw data at the path $.access-layers[*].uid; Access layer name can be found in the returned raw data at the path $.access-layers[*].name.
Please note that the value for "UIDs or Names or Rule Numbers" and Layer parameters must match in order to pass the command. It is suggested to run the Show Access Layers command first to obtain the desired layer UID/name, then use the layer UID/name to run the Get Access Rule Base command and obtain the desired rule UIDs/Names/Rule Numbers to delete.
Please note some access rules cannot be deleted. For example the Cleanup rule.
Input
Input Parameter | Required/Optional | Description | Example |
UIDs Or Names Or Rule Numbers | Required | The list of access rules to delete. Rules can be specified by UID, name, or rule number. However, all input values in the list must be in the same format. These values can be obtained using the Get Access Rule Base command. |
JSON
|
Source | Required | The source type (i.e. UID, Name or Rule-number) used for the input for the UIDs or Names or Rule-numbers parameter. | UID |
Layer Name or UID | Required | The name or UID of the layer that the rule belongs to. This parameter is required when the defined Source is Name or UID. Layer names and UIDs can be obtained using the Show Access Layers command. | Network |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Delete Access Rules failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Please double check the Server URL, the Username and password. |
Error Sample Data Delete Access Rules failed. Status Code: 400. Message: Please double check the Server URL, the Username and password. |
Discard unpublished changes created by Web API
Discards unpublished changes made by the Web API session and removes them from the database.
READER NOTE
Session UID is an optional parameter to run this command.
Run the Show Session Objects command to obtain the Session UID. Session UIDs can be found in the returned raw data at the path $.objects[*].uid.
Once the session is discarded, the session cannot be used again. Running this command using the UID of a session that was already discarded will return "not found".
The Session UID is optional to input, if you leave the parameter empty, no discard will be operated.
Input
Input Parameter | Required/Optional | Description | Example |
Session UID | Optional | The UID of the session to discard. The session to discard must be a different session than the one you are currently using. Session UIDs can be obtained using the Show Session Objects command. Only changes made by the Web API type sessions can be discarded. | ***-***-***-***-*** |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Discard unpublished changes created by Web API failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Invalid parameter for [uid]. The invalid value: [xxx]. |
Error Sample Data Discard unpublished changes created by Web API failed. Status Code: 400. Message: Invalid parameter for [uid]. The invalid value: [xxx]. |
Fetch Event
Returns firewall logs based on specified criteria.
READER NOTE
Query ID is an optional parameter to run this command.
Query IDs can be obtained by running this command with the Query ID parameter empty. The Query IDs can be found at the path $.query-id.
Input
Input Parameter | Required/Optional | Description | Example |
Start Time | Optional | The start time of the time range to fetch logs in UTC time. Note: If the Start Time and End Time parameters are not defined, the query will return logs from the past 24 hours. | 2022-03-01 00:00 |
End Time | Optional | The end time of the time range to fetch logs in UTC time format. Note: If the Start Time and End Time parameters are not defined, the query will return logs from the past 24 hours. | 2022-03-22 00:00 |
Filter | Optional | The filter expression for the query. The syntax is Field1:Value1 {AND|OR|NOT} Field2:Value2. If the value contains any spaces, it must be enclosed in double quotation marks. For example, subject:"Object Manipulation". | severity:Informational AND comment like "%update to%" |
Number of Event(s) Fetched | Optional | The maximum number of results to return, starting from the defined offset index value. The default limit is set to 20, and the maximum limit that can be set is 100. | 20 |
Type | Optional | The log type to filter results. The available options are Logs and Audit. If this parameter is not defined, all log types will be returned. | Logs |
Log Server IPs | Optional | The list of IP addresses of log servers to filter results. |
JSON
|
Query ID | Optional | The ID of the query to retrieve the next page of results from the previous run query, using the specified limit. If this parameter is defined, all other parameters will be ignored. The query ID can be obtained from the raw data of the command at the JSON path $.query-id. | admin_***-***-***-***-*** |
Output
To view the sample output data for all commands, refer to this article.
Fetch Event Field Mapping
See Field Mappings.
The CheckPoint Firewall system integration includes pre-configured field mappings for the default event source.
The Default Event Source is the default system-provided set of field mappings applied when the fetch event command is executed. It includes a Main Event JSON Path, which is the JSONPath expression that points to the base array of event objects. The source field path continues from this array to locate the required data.
The Main Event JSON Path can be viewed by clicking on the Edit Main JSON Path button.
.png?inst-v=40cb8c82-2e72-4b9d-aa5c-d42e6b974429)
Main Event JSON Path: $.logs
The logs array contains the event objects. Within each object, the key id denotes the Unique Event Key field. As such, the full JSONPath expression to extract the Unique Event Key is $.logs.id.
The pre-configured field mappings are detailed below:
Field Name | Source Field |
Unique Event Key | .id |
Event Type | .type |
Event name | .subject |
Start Time | .time |
Severity | .severity |
Description | .calc_desc |
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Fetch Event failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Please double check the Server URL, the Username and password. |
Error Sample Data Fetch Event failed. Status Code: 400. Message: Please double check the Server URL, the Username and password. |
Get Access Rule Base
Retrieves the entire access rule layer of the specified object.
READER NOTE
Name is a required parameter to run this command.
The Name parameter is referring to the Access Layers. You can run the Show Access Layers command to obtain your desired values. Layer Names can be found from the returned raw data at the path $.access-layers[*].name; UIDs can be found from the returned raw data at the path $.access-layers[*].uid.
Input
Input Parameter | Required/Optional | Description | Example |
Name | Required | The name or UID of the access rule to retrieve rulebase details for. | Network |
Limit | Optional | The maximum number (up to 100) of rulebase records to return. If the input value is negative or not specified, the default value of 20 will be used. | 2 |
Offset | Optional | The number of matching records to omit initially. The default value is 0. | 0 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Access Rule Base failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Requested object [Standard Threat Prevention] not found. |
Error Sample Data Get Access Rule Base failed. Status Code: 404. Message: Requested object [Standard Threat Prevention] not found. |
Get Task Status
Retrieves the progress and details of the specified task.
READER NOTE
Task ID is an optional parameter to run this command.
You should already have your desired task IDs on hand to run this command. If you don't know what the task ID is, you can use the Run Script command. The task IDs can be found in the raw data at the path $.[*].task-id. Store the task ID in a secure location, you may need it to run this command in the future.
Since all parameters are optional to input when running this command, if all parameters are left blank then 50 tasks will be returned.
Input
Input Parameter | Required/Optional | Description | Example |
Task ID | Optional | The ID of the task to return the status of. Task IDs can be obtained using the Run Script command. If this parameter is defined, the other parameters will be omitted. | ***-***-***-***-*** |
From Time | Optional | The start time of the time range to filter tasks, by the tasks' last update time. | 2022-03-01 00:00 |
To Time | Optional | The end time of the time range to filter tasks, by the tasks' last update time. | 2022-03-22 00:00 |
Status | Optional | The status to filter tasks. The available options are All, Successful, Failed and In Progress. The default option is All. | All |
Limit | Optional | The maximum number (up to 500) of records to return. If the input value is negative or not defined, the default value of 50 will be used. | 2 |
Offset | Optional | The number of matching records to omit initially. The default value is 0. | 0 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Get Task Status failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: 'Invalid parameter for [task-id]. |
Error Sample Data Get Task Status failed. Status Code: 400. Message: 'Invalid parameter for [task-id]. |
Install Policy
Applies all published changes from the database to a given target policy package. Installation of incorrect changes or onto the wrong target may cause CheckPoint to work improperly. Ensure to check changes and Policy Package Names by running the Show Published Changes between a period of time or two sessions and Show Policy Packages commands or check them within CheckPoint SmartConsole before executing this command.
READER NOTE
Policy Package Name is a required parameter to run this command.
Run the Show Policy Packages command to obtain the Policy Package Name. Policy Package Names can be obtained in the returned raw data at the path $.packages[*].name.
Input
Input Parameter | Required/Optional | Description | Example |
Policy Package Name | Required | The name of the Policy Package to be installed. Policy Package Name can be obtained using the Show Policy Packages command. | New_policy |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Install Policy failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Requested object [xxx] not found. |
Error Sample Data Get Task Status failed. Status Code: 404. Message: Requested object [xxx] not found. |
Run Script
Executes a script on the specified targets.
READER NOTE
Ensure the specified targets are present in the system. Targets can be viewed from CheckPoint SmartConsole, under GATEWAYS & SERVERS. Right-click on an object to copy its target name to your clipboard.
Input
Input Parameter | Required/Optional | Description | Example |
Script Name | Required | The name of the script to execute. | List All VPN Tunnel |
Script | Required | The contents of the script. | vpn tu tlist |
Targets | Required | The names of the targets to run the script on. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Run Script failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Requested object [xxx] not found. |
Error Sample Data Run Script failed. Status Code: 404. Message: Requested object [xxx] not found. |
Enable/Disable Access Rule
Enables or disables the specified access rule(s).
READER NOTE
"UIDs Or Names Or Rule Numbers" and "Layer Name or UID" are required parameters to run this command.
Run the Get Access Rule Base command to obtain UIDs. UID can be found from the returned raw data at the path $.rulebase[*].uid; names can be found from the returned raw data at the path $.rulebase[*].name.
Run the Show Access Layers command to obtain access layers. Access layer UIDs can be found in the returned raw data at the path $.access-layers[*].uid; Access layer name can be found in the returned raw data at the path $.access-layers[*].name.
Please note that the value for "UIDs Or Names Or Rule Numbers" and Layer parameters must match in order to pass the command. It is suggested to run the Show Access Layers command first to obtain the desired layer UID/name, then use the layer UID/name to run the Get Access Rule Base command to obtain the desired rule UIDs/Names/Rule Numbers to enable/disable.
Input
Input Parameter | Required/Optional | Description | Example |
UIDs Or Names Or Rule Numbers | Required | The list of access rules to enable or disable. Rules can be specified by UID, name, or rule number. However, all input values in the list must be in the same format. These values can be obtained using the Get Access Rule Base command. |
JSON
|
Source | Required | The source type (i.e. UID, Name or Rule-number) used for the input for the UIDs or Names or Rule-numbers parameter. | UID |
Layer Name or UID | Required | The name or UID of the layer that the rule belongs to. Layer names and UIDs can be obtained using the Show Access Layers command. | Network |
Enabled | Optional | The option to enable or disable the specified access rules. Selecting True will enable the rules, and selecting False will disable them. Default value is True. | True |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Enable/Disable Access Rule failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Requested object [Entities can not be found] not found. |
Error Sample Data Enable/Disable Access Rule failed. Status Code: 404. Message: Requested object [Entities can not be found] not found. |
Set Threat Exception
Sets the specified threat exception.
READER NOTE
Exception Name Or UID is a required parameter to run this command.
For exception under a rule: Run the Show Threat Rule Exception Rule Base command to obtain Exception Name Or UID. Exception Names can be found in the returned raw data at the path $.rulebase[*].name; Exception UID can be found in the returned raw data at the path $.rulebase[*].uid.
For exceptions under an exception group: These can only be found from within CheckPoint SmartConsole. Navigate to Security Policies > Exceptions, then click Exception Group Name and select Exceptions.
"Layer Name Or UID", "Parent Rule Name Or Number Or UID" and "Exception Group Name Or UID" are optional parameters to run this command.
If the threat exception is under a rule, Layer Name Or UID is a required parameter.
Run the Show Threat Layers command to obtain Layer Name and UIDs. Layer Names can be found in the returned raw data at the path $.threat-layers[*].name; UIDs can be found at the path $.threat-layers[*].uid.
If the threat exception is under an exception group, the Layer Name Or UID parameter must not be defined. Any input value will be omitted.
Run the Show Threat Rule Base command to obtain Parent Rule Names, Numbers and UIDs. Rule UIDs can be found in the returned raw data at the path $.rulebase[*].uid; Rule numbers can be found in the returned raw data at the path $.rulebase[*].rule-number. Rule Names can be found in the returned raw data at the path $.rulebase[*].name.
Run the Show Exception Groups command to obtain Exception Group Names and UIDs. Exception Group Names can be found in the returned raw data at the path $.objects[*].name; Exception Group UID can be found in the returned raw data at the path $.objects[*].uid.
ALERT
To set threat exceptions, you must define at least one of the Parent Rule Name Or Number Or UID or the Exception Group Name Or UID parameters, but not both.
If your desired threat exception is under a rule, the Layer Name Or UID, Parent Rule Name Or Number Or UID and Exception Name Or UID parameters are required to run this command.
Ensure that the values entered for the Layer Name Or UID, Parent Rule Name Or Number Or UID and Exception Name Or UID match. It is suggested to run the Show Threat Layers command to identify the correct layer, and then use that layer to run the Show Threat Rule Base command and select the desired threat rule. Then use your selected threat layer and threat rule to run the Show Threat Rule Exception Rule Base command. If your selected threat layer and threat rule has exceptions (some may not), select your desired exception. Use the threat layer, threat rule and exception as a pair to run this command. Failure to match the values may result in errors.
If your desired threat exception is under an exception group instead of a rule, the Exception Group Name Or UID and Exception Name Or UID parameters are required to run this command.
For threat exceptions under an exception group, the Layer Name Or UID parameter must not be defined. Any input value will be omitted.
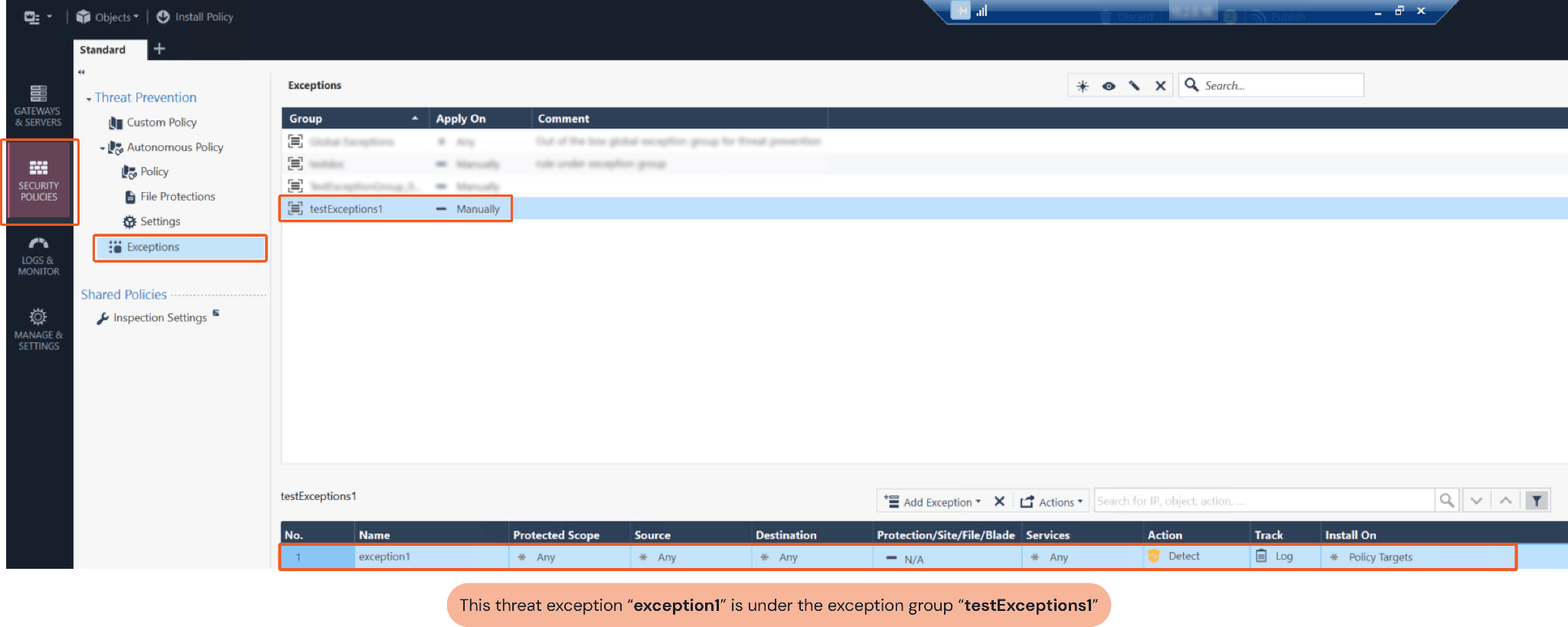
Ensure the input threat exception group value matches the threat exception. You can use the threat group you choose to check CheckPoint SmartConsole. Navigate to Security Policies > Exceptions to view threat exceptions under their corresponding Exception Groups.
Input
Input Parameter | Required/Optional | Description | Example |
Layer Name Or UID | Optional | The name or UID of the layer that the rule belongs to. Layer names and UIDs can be obtained using the Show Threat Layers command. If the Parent Rule Name Or Number Or UID parameter is defined, then this parameter is required and the specified rule must match the layer. Otherwise, if the Exception Group Name Or UID parameter is defined, this parameter must not be defined. Any entered value will be omitted. | Standard Threat Prevention |
Exception Name Or UID | Required | The name or UID of the exception. If the exception is under a rule, then it can be obtained using the Show Threat Rule Exception Rule Base command; if the exception is under an exception group, then it can only be found from within CheckPoint SmartConsole. | exception091700b |
Parent Rule Name Or Number Or UID | Optional | The name, number or UID of the parent rule. Rule number and UIDs can be obtained using the Show Threat Rule Base command. Note: (1) Only one of the Parent Rule Name Or Number OR UID or Exception Group Name Or UID parameters can be defined per execution of the command, but at least one must be defined. (2) If this parameter is defined, you must define the Layer Name Or UID parameter. Entering a rule and layer that do not match will result in an error. | ***** |
Exception Group Name Or UID | Optional | The name or UID of the exception group. Exception Group names and UIDs can be obtained using the Show Exception Groups command. Note: (1) Only one of the Exception Group Name Or UID or Rule Name Or Number OR UID parameters can be defined per execution of the command, but at least one must be defined. (2) If this parameter is defined, you cannot define the Layer Name Or UID parameter. The value entered for the layer will be omitted. | TestExceptionGroup0917001 |
New Exception Name | Optional | The new name of the exception. | New Test Exception |
Comment | Optional | The comment for the exception. | Test Comment |
Track | Optional | The tracking method for protection. | log |
Protected Scope | Optional | The name of UIDs or network objects defining the protected scope. | All_Internet |
Install On | Optional | The name or UID of the gateways to install the policy on. | Policy Targets |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Set Threat Exception failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: layer can't be used with exception-group-name or exception-group-uid. |
Error Sample Data Set Threat Exception failed. Status Code: 400. Message: layer can't be used with exception-group-name or exception-group-uid. |
Set Threat Protection
Edits the specified threat protection.
READER NOTE
Threat Protection Name Or UID is a required parameter to run this command.
Run the Show Threat Protections command to obtain Threat Protection Name Or UID. Threat Protection Name can be found in the returned raw data at the path $.protections[*].name; Threat Protection UID can be found in the returned raw data at the path $.protections[*].uid.
Input
Input Parameter | Required/Optional | Description | Example |
Threat Protection Name Or UID | Required | The name or UID of the threat protection. Threat Protection Names and UIDs can be obtained using the Show Threat Protections command. | ***-***-***-***-*** |
Comment | Required | The comment for the threat protection. | Test Comment |
Follow Up | Optional | The option to mark the protection with a predefined follow-up flag. The available input options are True or False. Default option is False. | False |
Profile | Required | The name of the profile. | Basic |
Action | Required | The protection action of the threat protection. The valid actions are Threat Cloud: Inactive, Detect, Prevent Core: Drop, Inactive, Accept. | Inactive |
Track | Optional | The tracking method for the threat protection. | Alert |
Capture Packets | Optional | The option to capture packets when set to True. The available input options are True or False. Default option is False. | True |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Set Threat Protection failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Please double check the Server URL, the Username and password. |
Error Sample Data Set Threat Protection failed. Status Code: 400. Message: Please double check the Server URL, the Username and password. |
Set Threat Rule
Edits the specified threat rule.
READER NOTE
"Layer Name Or UID" and "Rule Name Or Number Or UID" are required parameters to run this command.
Run the Show Threat Layers command to obtain Layer Names and UIDs. Layer Names can be found in the returned raw data at the path $.threat-layers[*].name; UIDs can be found at the path $.threat-layers[*].uid.
Run the Show Threat Rule Base command to obtain Rule Names, Numbers and UIDs. Rule UIDs can be found in the returned raw data at the path $.rulebase[*].uid; Rule numbers can be found in the returned raw data at the path $.rulebase[*].rule-number. Rule Names can be found in the returned raw data at the path $.rulebase[*].name.
ALERT
Ensure that the values entered for the Layer Name Or UID and Rule Name Or Number Or UID match. It is suggested to run the Show Threat Layers command to choose the desired layer, and then use that layer to run the Show Threat Rule Base command and select the desired threat rule. Use those pairs to run this command. Failure to match the values may result in errors.
Input
Input Parameter | Required/Optional | Description | Example |
Layer Name Or UID | Required | The name or UID of the layer that the threat rules belongs to. Layer names and UIDs can be obtained using the Show Threat Layers command. | Standard Threat Prevention |
Rule Name Or Number Or UID | Required | The name, number or UID of the rule. Rule numbers and UIDs can be obtained using the Show Threat Rule Base command. | 1 |
New Rule Name | Optional | The new name for the threat rule. | admin_Testrule21 |
Comment | Optional | The comment for the rule. | AdminTestComment20 |
Track | Optional | The tracking method for protection. | None |
Action | Optional | The protection action of the threat rule. | Basic |
Protected Scope | Optional | The names or UIDs defining the protected scope. | All_Internet |
Install On | Optional | The name or UID of the gateways to install the policy on. | Policy Targets |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Set Threat Rule failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Requested object [xxx] not found. |
Error Sample Data Set Threat Rule failed. Status Code: 404. Message: Requested object [xxx] not found. |
Show Access Layers
Retrieves access layers based on the specified criteria.
READER NOTE
If the defined value for the Filter parameter does not match a full or partial layer name, the command will run successfully with no results.
Input
Input Parameter | Required/Optional | Description | Example |
Filter | Optional | The partial or full layer name for a free text search to filter access layers. | work |
Limit | Optional | The maximum number (up to 100) of rulebase records to return. If the input value is negative or not defined, the default value of 20 will be used. | 2 |
Offset | Optional | The number of matching records to omit initially. The default value is 0. | 0 |
Show Details | Optional | The option to return detailed information when set to True. Selecting False will only return the standard level of information. The default value is False. | False |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Show Access Layers failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Please double check the Server URL, the Username and password. |
Error Sample Data Show Access Layers failed. Status Code: 400. Message: Please double check the Server URL, the Username and password. |
Show Application Site Categories
Retrieves the primary categories of applications and sites.
READER NOTE
If the defined value for the Filter parameter does not match a category, the command will run successfully with no results.
Input
Input Parameter | Required/Optional | Description | Example |
Filter | Optional | The search expression to filter objects by. The provided text should be exactly the same as it would be given in CheckPoint SmartConsole. The logical operators in the expression ('AND', 'OR') should be provided in capital letters. | Entertainment |
Limit | Optional | The maximum number (up to 500) of application primary categories records to return. The default value is 500. | 500 |
Offset | Optional | The number of matching records to omit initially. The default value is 0. | 0 |
Show Details | Optional | The option to return detailed information when set to True. Selecting False will only return the standard level of information. The default value is False. | False |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Show Application Site Categories failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Please double check the Server URL, the Username and password. |
Error Sample Data Show Application Site Categories failed. Status Code: 400. Message: Please double check the Server URL, the Username and password. |
Show Published Changes between a period of time or two sessions
Shows published changes from all user sessions in the database. It is highly recommended to run this command with the Details Level parameter set to Full before running the Install Policy command, in order to check whether all desired changes are already published, or if any incorrect changes have been mistakenly published. The results are ordered from past to recent.
READER NOTE
From Session parameter must be a published session. Otherwise, errors will return.
Input
Input Parameter | Required/Optional | Description | Example |
Start Time | Optional | The start time from which tracking changes is to be performed. If the time parameters are used, the session parameters will be omitted. | 2023-04-03 08:20 |
End Time | Optional | The end time until which tracking changes is to be performed. If the time parameters are used, the session parameters will be omitted. | 2023-04-04 08:20 |
From Session | Optional | The session UID from which tracking changes is to be performed. The default used is the session before To Session. If the time parameters are used, the session parameters will be omitted. | ***-***-***-***-*** |
To Session | Optional | The session UID until which tracking changes is to be performed. The default used is the last published session. If the time parameters are used, the session parameters will be omitted. | ***-***-***-***-*** |
Details Level | Optional | The level of detail to include for some of the fields in the response. The available options are Standard, UID and Full. The default option is Standard. | Standard |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Show Published Changes between a period of time or two sessions failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Management server failed to execute command. |
Error Sample Data Show Published Changes between a period of time or two sessions failed. Status Code: 400. Message: Management server failed to execute command |
Show Exception Group
Retrieves the details of a specified exception group.
READER NOTE
Exception Group Name Or UID is a required parameter to run this command.
Run the Show Exception Groups command to obtain Exception Group Names and UIDs. Exception Group Names can be found in the returned raw data at the path $.objects[*].name; Exception Group UIDs can be found in the returned raw data at the path $.objects[*].uid.
For clarification, Show Exception Groups returns all exception groups, while Show Exception Group can only search for one specific exception group.
Input
Input Parameter | Required/Optional | Description | Example |
Exception Group Name Or UID | Required | The name or UID of the exception group. Exception Group names and UIDs can be obtained using the Show Exception Groups command. | TestExceptionGroup0917003 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Show Exception Group failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Requested object [xxx] not found. |
Error Sample Data Show Exception Group failed. Status Code: 404. Message: Requested object [xxx] not found. |
Show Exception Groups
Retrieves a list of all exception groups.
READER NOTE
For clarification, Show Exception Groups returns all exception groups, while Show Exception Group can only search for one specific exception group.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Show Exception Groups failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Please double check the Server URL, the Username and password. |
Error Sample Data Show Exception Groups failed. Status Code: 400. Message: Please double check the Server URL, the Username and password. |
Show Logs
Retrieves log information matching the specified criteria. Note: This command is available for CheckPoint's Management API version 1.6.1 or above.
Input
Input Parameter | Required/Optional | Description | Example |
Start Time | Required | The start time of the time range to query logs in UTC time. | 2023-02-01 00:00 |
End Time | Required | The end time of the time range to query logs in UTC time. | 2023-02-02 00:00 |
Limit | Optional | The maximum number (between 1 and 100) of logs to return. The default value is 100. | 10 |
Log Servers | Optional | The IPs of the log servers to query. If this parameter is not defined, all log servers will be returned. |
JSON
|
Log Type | Optional | The type of logs (i.e. Logs or Audit Logs) to return. The default option is Logs. | Logs |
Filter | Optional | The SmartConsole and SmartView query to filter search results. See SmartConsole and SmartView Query Language for more information about the query syntax. | severity:Medium |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Show Logs failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Invalid filter - missing open/close quote. |
Error Sample Data Show Logs failed. Status Code: 400. Message: Invalid filter - missing open/close quote. |
Show Policy Packages
Retrieves all policy package objects.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Show Policy Packages failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Please double check the Server URL, the Username and password. |
Error Sample Data Show Policy Packages failed. Status Code: 400. Message: Please double check the Server URL, the Username and password. |
Show Session Objects
Retrieves session objects.
Input
Input Parameter | Required/Optional | Description | Example |
Session UIDs | Optional | The session UIDs to check. When this parameter is defined, Application Type will be omitted. |
JSON
|
Application Type | Optional | The application type which the sessions are generated from. When Session UIDs is defined, this parameter will be omitted. | Web API |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Show Session Objects failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Invalid parameter for [uid]. The invalid value. |
Error Sample Data Show Session Objects failed. Status Code: 400. Message: Invalid parameter for [uid]. The invalid value. |
Show Threat Exception
Shows the details of the specified threat exception.
READER NOTE
Exception Name Or UID is a required parameter to run this command.
For exceptions under a rule: Run the Show Threat Rule Exception Rule Base command to obtain Exception Name Or UID. Exception Names can be found in the returned raw data at the path $.rulebase[*].name; Exception UID can be found in the returned raw data at the path $.rulebase[*].uid.
For exceptions under an exception group: These can only be found from within CheckPoint SmartConsole. Navigate to Security Policies > Exceptions, then click Exception Group Name and select Exceptions.
"Layer Name Or UID", "Rule Name Or Number Or UID" and "Exception Group Name Or UID" are optional parameters to run this command.
If the threat exception is under a rule, Layer Name Or UID is a required parameter.
Run the Show Threat Layers command to obtain Layer Name and UIDs. Layer Names can be found in the returned raw data at the path $.threat-layers[*].name; UIDs can be found at the path $.threat-layers[*].uid.
If the threat exception is under an exception group, the Layer Name Or UID parameter must not be defined. Any input value will be omitted.
Run the Show Threat Rule Base command to obtain Rule Names, Numbers and UIDs. Rule UIDs can be found in the returned raw data at the path $.rulebase[*].uid; Rule numbers can be found in the returned raw data at the path $.rulebase[*].rule-number. Rule Names can be found in the returned raw data at the path $.rulebase[*].name.
Run the Show Exception Groups command to obtain Exception Group Names and UIDs. Exception Group Names can be found in the returned raw data at the path $.objects[*].name; Exception Group UID can be found in the returned raw data at the path $.objects[*].uid.
ALERT
To show threat exceptions, you must define at least one of the Parent Rule Name Or Number Or UID or the Exception Group Name Or UID parameters, but not both.
If your desired threat exception is under a rule, the Layer Name Or UID, Parent Rule Name Or Number Or UID and Exception Name Or UID parameters are required to run this command.
Ensure that the values entered for the Layer Name Or UID, Parent Rule Name Or Number Or UID and Exception Name Or UID match. It is suggested to run the Show Threat Layers command to identify the correct layer, and then use that layer to run the Show Threat Rule Base command and select the desired threat rule. Then use your selected threat layer and threat rule to run the Show Threat Rule Exception Rule Base command. If your selected threat layer and threat rule has exceptions (some may not), select your desired exception. Use the threat layer, threat rule and exception as a pair to run this command. Failure to match the values may result in errors.
If your desired threat exception is under an exception group instead of a rule, the Exception Group Name Or UID and Exception Name Or UID parameters are required to run this command.
For threat exceptions under an exception group, the Layer Name Or UID parameter must not be defined. Any input value will be omitted.
Ensure the input exception group value matches the threat exception. You can use the threat group you choose to check CheckPoint SmartConsole. Navigate to Security Policies > Exceptions to view threat exceptions under their corresponding Exception Groups.
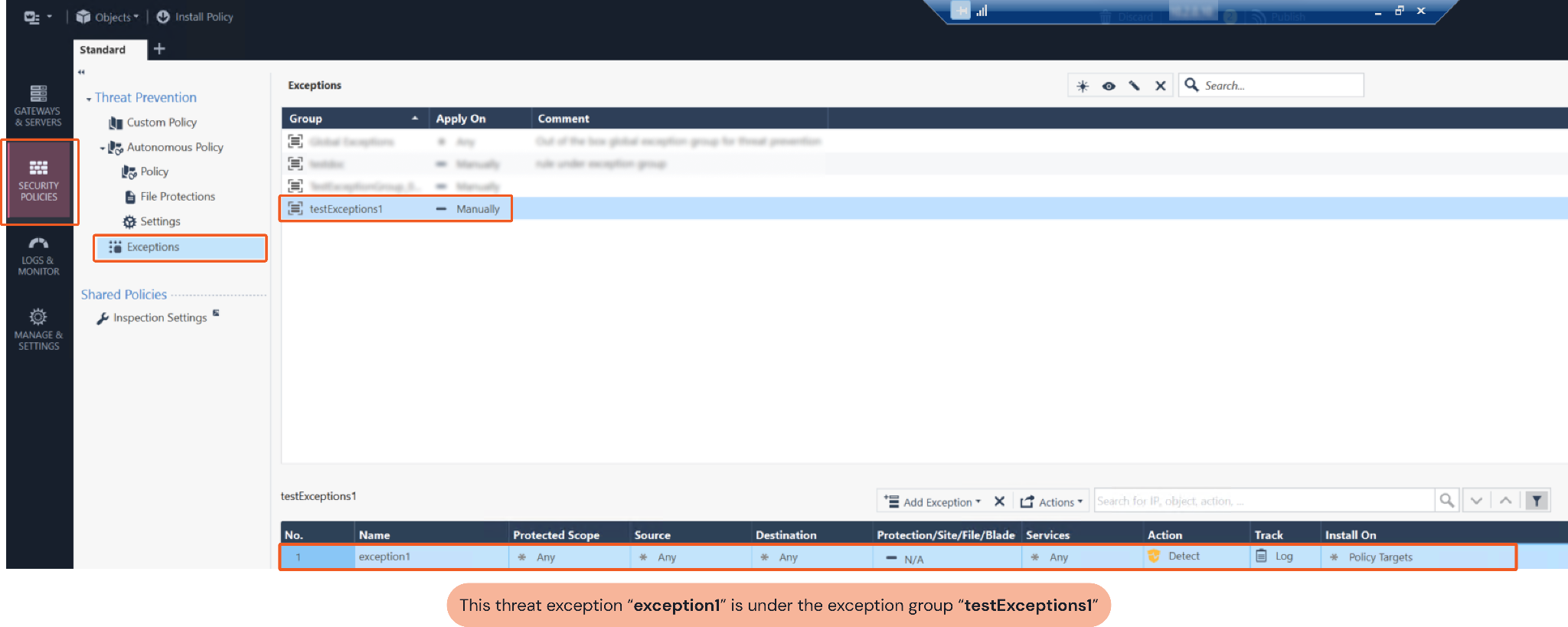
Input
Input Parameter | Required/Optional | Description | Example |
Layer Name Or UID | Optional | The name or UID of the layer that the rule belongs to. Layer names and UIDs can be obtained using the Show Threat Layers command. If the Parent Rule Name Or Number Or UID parameter is defined, then this parameter is required and the specified rule must match the layer. Otherwise, if the Exception Group Name Or UID parameter is defined, this parameter must not be defined. Any entered value will be omitted. | Standard Threat Prevention |
Parent Rule Name Or Number Or UID | Optional | The name, number or UID of the rule. Rule numbers and UIDs can be obtained using the Show Threat Rule Base command. Note: (1) Only one of the Parent Rule Name Or Number OR UID or Exception Group Name Or UID parameters can be defined per execution of the command, but at least one must be defined. (2) If this parameter is defined, you must define the Layer Name Or UID parameter. Entering a rule and layer that do not match will result in an error. | ***-***-***-***-*** |
Exception Group Name Or UID | Optional | The name or UID of the exception group. Exception Group names and UIDs can be obtained using the Show Exception Groups command. (1) Only one of the Exception Group Name Or UID or Parent Rule Name Or Number OR UID parameters can be defined per execution of the command, but at least one must be defined. (2) If this parameter is defined, you cannot define the Layer Name Or UID parameter. The value entered for the layer will be omitted. | TestExceptionGroup |
Exception Name Or UID | Required | The name or UID of the exception. If the exception is under a rule, then it can be obtained using the Show Threat Rule Exception Rule Base command; if the exception is under an exception group, then it can only be found from within CheckPoint SmartConsole. | exception091700b |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Show Threat Exception failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Requested object [test1doc] not found. |
Error Sample Data Show Threat Exception failed. Status Code: 404. Message: Requested object [test1doc] not found. |
Show Threat Layers
Retrieves all threat layers.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Show Threat Layers failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Please double check the Server URL, the Username and password. |
Error Sample Data Show Threat Layers failed. Status Code: 404. Message: Please double check the Server URL, the Username and password. |
Show Threat Profiles
Retrieves all threat profiles.
Input
N/A
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Show Threat Profiles failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Please double check the Server URL, the Username and password. |
Error Sample Data Show Threat Profiles failed. Status Code: 400. Message: Please double check the Server URL, the Username and password. |
Show Threat Protection
Returns the details of the specified threat protection.
RREADER NOTE
Threat Protection Name Or UID is a required parameter to run this command.
Run the Show Threat Protections command to obtain Threat Protection Name Or UID. Threat Protection name can be found in the returned raw data under path $.protections.name; Threat Protection UID can be found in the returned raw data under path $.protections.uid.
Input
Input Parameter | Required/Optional | Description | Example |
Threat Protection Name Or UID | Required | The name or UID of the threat protection. Threat Protection names and UIDs can be obtained using the Show Threat Protections command. | ftp patterns |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Show Threat Protection failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Requested object [xxx] not found. |
Error Sample Data Show Threat Protection failed. Status Code: 404. Message: Requested object [xxx] not found. |
Show Threat Protections
Retrieves all threat protections.
Input
Input Parameter | Required/Optional | Description | Example |
Limit | Optional | The maximum number of threat protections to return. The default value is 50. | 50 |
Offset | Optional | The number of matching records to omit initially. | 0 |
Details Level | Optional | The level of detail to include for some of the fields in the response. The available options are Standard, UID and Full. The default option is Standard. | Standard |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Show Threat Protections failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Please double check the Server URL, the Username and password. |
Error Sample Data Show Threat Protections failed. Status Code: 400. Message: Please double check the Server URL, the Username and password. |
Show Threat Rule
Shows the details of the specified threat rule.
READER NOTE
"Layer Name Or UID" and "Rule Name Or Number Or UID" are required parameters to run this command.
Run the Show Threat Layers command to obtain Layer Name Or UID. Either UID or Layer Name can be accepted. Layer Name can be found in the returned raw data at the path $.threat-layers[*].name; UID can be found at the path $.threat-layers[*].uid.
Run the Show Threat Rule Base command to obtain Rule Name Or Number Or UID. Rule name can be found in the returned raw data at the path $.rulebase[*].name; Rule number can be found in the returned raw data at the path $.rulebase[*].rule-number; Rule UID can be found in the returned raw data at the path $.rulebase[*].uid.
Please note the input values for "Layer Name Or UID" and "Rule Name Or Number Or UID" must match. It is suggested to run the Show Threat Layers command first in order to obtain the desired layer. You can then use that layer to run the Show Threat Rule Base command, and choose your desired threat rule. Use that pair of values to run this command. Otherwise, errors will be returned.
Input
Input Parameter | Required/Optional | Description | Example |
Layer Name Or UID | Required | The name or UID of the layer that the threat rule belongs to. Layer names and UIDs can be obtained using the Show Threat Layers command. | ***-***-***-***-*** |
Rule Name Or Number Or UID | Required | The name, number or UID of the rule. Rule numbers and UIDs can be obtained using the Show Threat Rule Base command. | 1 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Show Threat Rule failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Requested object [Entities can not be found] not found. |
Error Sample Data Show Threat Rule failed. Status Code: 404. Message: Requested object [Entities can not be found] not found. |
Show Threat Rule Base
Shows the threat prevention rules of the specified layer.
READER NOTE
Layer Name Or UID is a required parameter to run this command.
Run the Show Threat Layers command to obtain Layer Name Or UID. Either UID or Layer Name can be accepted. Layer Name can be found in the returned raw data at the path $.threat-layers[*].name; UID can be found at the path $.threat-layers[*].uid.
Please note some Threat Layers may not have a threat rule base. If your input Threat layer does not have a threat rule base, it will return success with no result.
Input
Input Parameter | Required/Optional | Description | Example |
Layer Name Or UID | Required | The name or UID of the layer that the rule belongs to. Layer names and UIDs can be obtained using the Show Threat Layers command. | ***-***-***-***-*** |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Show Threat Rule Base failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Requested object [xxx] not found. |
Error Sample Data Show Threat Rule Base failed. Status Code: 404. Message: Requested object [xxx] not found. |
Show Threat Rule Exception Rule Base
Shows the entire threat exceptions layer generated for a given threat rule.
READER NOTE
"Layer Name Or UID" and "Rule Name Or Number Or UID" are required parameters to run this command.
Run the Show Threat Layers command to obtain Layer Name Or UID. Either UID or Layer Name can be accepted. Layer Name can be found in the returned raw data at the path $.threat-layers[*].name; UID can be found at the path $.threat-layers[*].uid.
Run the Show Threat Rule Base command to obtain Rule Name Or Number Or UID. Rule Name can be found in the returned raw data at the path $.rulebase[*].name; Rule Number can be found in the returned raw data at the path $.rulebase[*].rule-number; Rule UID can be found in the returned raw data at the path $.rulebase[*].uid.
Please note the input values for "Layer Name Or UID" and "Rule Name Or Number Or UID" must match. It is suggested to run the Show Threat Layers command first in order to obtain the desired layer. You can then use that layer to run the Show Threat Rule Base command, and choose your desired threat rule. Use that pair of values to run this command. Otherwise, errors will be returned.
If there is no exception based on your provided layer and rule, the returned raw data of this command will show "total": 0 at the bottom.
Input
Input Parameter | Required/Optional | Description | Example |
Layer Name Or UID | Required | The name or UID of the layer that the rule belongs to. Layer names and UIDs can be obtained using the Show Threat Layers command. | Standard Threat Prevention |
Rule Name Or Number Or UID | Required | The name, number or UID of the rule. Rule numbers and UIDs can be obtained using the Show Threat Rule Base command. | 1 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Show Threat Rule Exception Rule Base failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Requested object [Entities can not be found] not found. |
Error Sample Data Show Threat Rule Exception Rule Base failed. Status Code: 404. Message: Requested object [Entities can not be found] not found. |
Test Connection
Allows users to perform a health check on an integration connection. Users can schedule a periodic health check by selecting Connection Health Check when editing an integration connection.
Input
N/A
Output
Output Type | Description | Return Data Type |
Return Data | Indicates one of the possible command execution states: Successful or Failed. The Failed state can be triggered by any of the following errors:
More details about an error can be viewed in the Error tab. | String |
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the responses from the third-party API calls including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Test Connection failed. Failed to check the connector. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the CheckPoint Firewall portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Please double check the Server URL, the Username and password. |
Error Sample Data Test Connection failed. Failed to check the connector. Status Code: 400. Message: Please double check the Server URL, the Username and password. |
FAQ
Q1: Why can't I see the changes I made?
Answer: If you made those changes with D3 commands, D3 will help you publish those sections automatically, so you won't see this issue. However, if you ran the command from other places (Postman, the CheckPoint Firewall UI, etc.), you must publish your changed session in order to see the changes.
For example, adding a threat exception to an exception group with Postman. If you cannot see the threat exception you just created, this is because you need to publish that session in which you made the changes. One way to publish the session is to go to: Manage & Settings > Sessions > View Sessions. Locate the corresponding session and right click it to publish it. The changes will then be published along with the session.