Carbon Black Cloud V2
LAST UPDATED: SEPTEMBER 16, 2025
Overview
VMware Carbon Black Cloud provides solutions such as endpoint detection and response (EDR), advanced threat hunting, and vulnerability management. D3 SOAR is providing REST operations to function with VMware Carbon Black Cloud. This integration is the D3's newly designed 2nd Version of the Carbon Black Cloud.
D3 SOAR is providing REST operations to function with Carbon Black Cloud V2.
Carbon Black Cloud V2 is available for use in:
Known Limitations
For a detailed breakdown of the specific rate limits, including the number of requests allowed within a given time frame and the response codes you might encounter when a limit is exceeded, refer to VMware's official documentation.
Connection
To connect to Carbon Black Cloud V2 from D3 SOAR, follow this part to collect the required information below:
Parameter | Description | Example |
Default | ||
Server URL | The server URL used to access VMware Carbon Black Cloud. | https://*****.net |
Identity Manager | The identity management solution you use to manage identity and authorization. In order to determine your identity manager, please refer to https://developer.carbonblack.com/reference/carbon-black-cloud/authentication/#determine-the-identity-manager. If not specified, the default identity manager is Carbon Black Cloud(CBC). | Carbon Black Cloud(CBC) |
Carbon Black Cloud(CBC) | ||
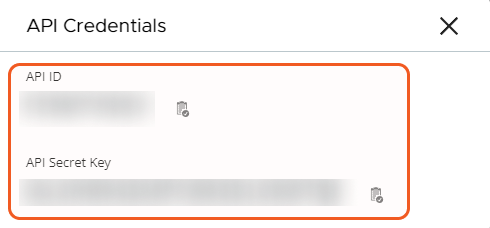
API ID | The API ID to authenticate the API connection for Carbon Black Cloud(CBC) identity manager. Refer to Step 1C: Generate API ID and API Secret Key for how to create API Key in Carbon Black Cloud(CBC). | ***** |
API Secret | The API Secret to authenticate the API connection for Carbon Black Cloud(CBC) identity manager. | ABCD********6789 |
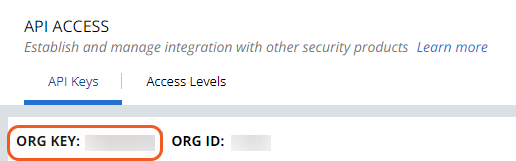
Organization Key | Organization Key. Organization Key can be obtained in your product console under Settings > API Access > API Keys. | 7D****GN |
VMware Cloud Services Platform(CSP) | ||
APP ID | The APP ID to authenticate the API connection for VMware Cloud Services Platform(CSP). Please refer to OAuth Access Control - Carbon Black Developer Network about how to create an OAuth APP in VMware Cloud Services Platform(CSP). | K3bp****M7u4 |
APP Secret | The APP Secret to authenticate the API connection for VMware Cloud Services Platform(CSP). | ABCD********6789 |
Organization Key | Organization Key. Organization Key can be obtained in your product console under Settings > API Access > API Keys. | 7D****GN |
Permission Requirements
Each endpoint in the Carbon Black Cloud V2 API requires a certain permission scope. The following are required scopes for the commands in this integration:
Command | CBC | CSP | |
Permission (.notation name) | Operation(s) | Permission (.notation name) | |
Block Hashes | org.reputations | CREATE + READ | _API.Applications:org.Reputations.CREATE |
Disable Bypass | device.bypass | EXECUTE | _API.Device:device.Bypass.EXECUTE |
Download Files | ubs.org.file | Read | _API.Unified.Binary.Store:ubs.Org.File:READ |
Enable Bypass | device.bypass | EXECUTE | _API.Device:device.Bypass.EXECUTE |
Fetch Event (Fetching Observation Event Type = Observation row1 Fetching Alerts Event Type = Alert row2) | org.search.events | CREATE + READ | _API.Search:org.Events.READ, _API.Search:org.Events.CREATE |
org.alerts | READ | _API.Alerts:org.Alerts:READ | |
Quarantine Devices | device.quarantine | EXECUTE | _API.Device:device.Quarantine.EXECUTE |
Unblock Hashes | org.reputations | READ + DELETE | _API.Applications:org.Reputations:READ, _API.Applications:org.Reputations:DELETE |
Unquarantine Devices | device.quarantine | EXECUTE | _API.Device:device.Quarantine.EXECUTE |
Unwhitelist Hashes | org.reputations | READ + DELETE | _API.Applications:org.Reputations:READ _API.Applications:org.Reputations:DELETE |
Update Device Policy | device.policy | UPDATE | _API.Device:device.Policy.UPDATE |
Whitelist Hashes | org.reputations | CREATE | _API.Applications:org.Reputations:CREATE |
Test Connection | Any, but at least assign one permission | ||
Configuring Carbon Black Cloud V2 to Work with D3 SOAR
CBC: API
Create Access Levels
The appropriate API access level must be determined before accessing data from Carbon Black Cloud integrations via the APIs. Refer to VMware's documentation step-by-step instructions.
Applying an Access Level to an API Key
Apply the custom access level to an API key. Refer to VMware's documentation step-by-step instructions. Copy and save the API key after configuration, as it will be required to build the integration connection in D3 SOAR.
After completing the setup, retrieve the Organization Key on the API Access page. The Token (API Secret Key) and App ID are available upon key creation.
CSP: APP
Refer to OAuth Access Control - Carbon Black Developer Network for more information about configuring an OAuth app in CSP.
Configuring D3 SOAR to Work with Carbon Black Cloud V2
Log in to D3 SOAR.
Find the Carbon Black Cloud V2 integration.
.png?inst-v=9d16beaf-952a-4ae4-8fe8-e35f7a3745da)
Navigate to Configuration on the top header menu.
Click on the Integration icon on the left sidebar.
Type Carbon Black Cloud V2 in the search box to find the integration, then click it to select it.
Click + Connection, on the right side of the Connections section. A new connection window will appear.
Configure the following fields to create a connection to Carbon Black Cloud V2.
.png?inst-v=9d16beaf-952a-4ae4-8fe8-e35f7a3745da)
Connection Name: The desired name for the connection.
Site: The site on which to use the integration connection. Use the drop-down menu to select the site. The Share to Internal Sites option enables all internal sites to use the connection. Selecting a specific site will only enable that site to use the connection.
Recipient site for events from connections Shared to Internal Sites: This field is displayed when Share to Internal Sites is selected for the Site field, allowing selection of the internal site for deploying the integration connection.
Agent Name (Optional): The proxy agent required to build the connection. Use the dropdown menu to select the proxy agent from a list of previously configured proxy agents.
Description (Optional): The description for the connection.
Tenant (Optional): When configuring the connection from a master tenant site, users can choose the specific tenant sites with which to share the connection. Once this setting is enabled, users can filter and select the desired tenant sites from the dropdowns to share the connection.
Configure User Permissions: Defines which users have access to the connection.
Active: The checkbox that enables the connection to be used when selected.
System: This section contains the parameters defined specifically for the integration. These parameters must be configured to create the integration connection.
Identity Manager: Carbon Black Cloud (CBC)
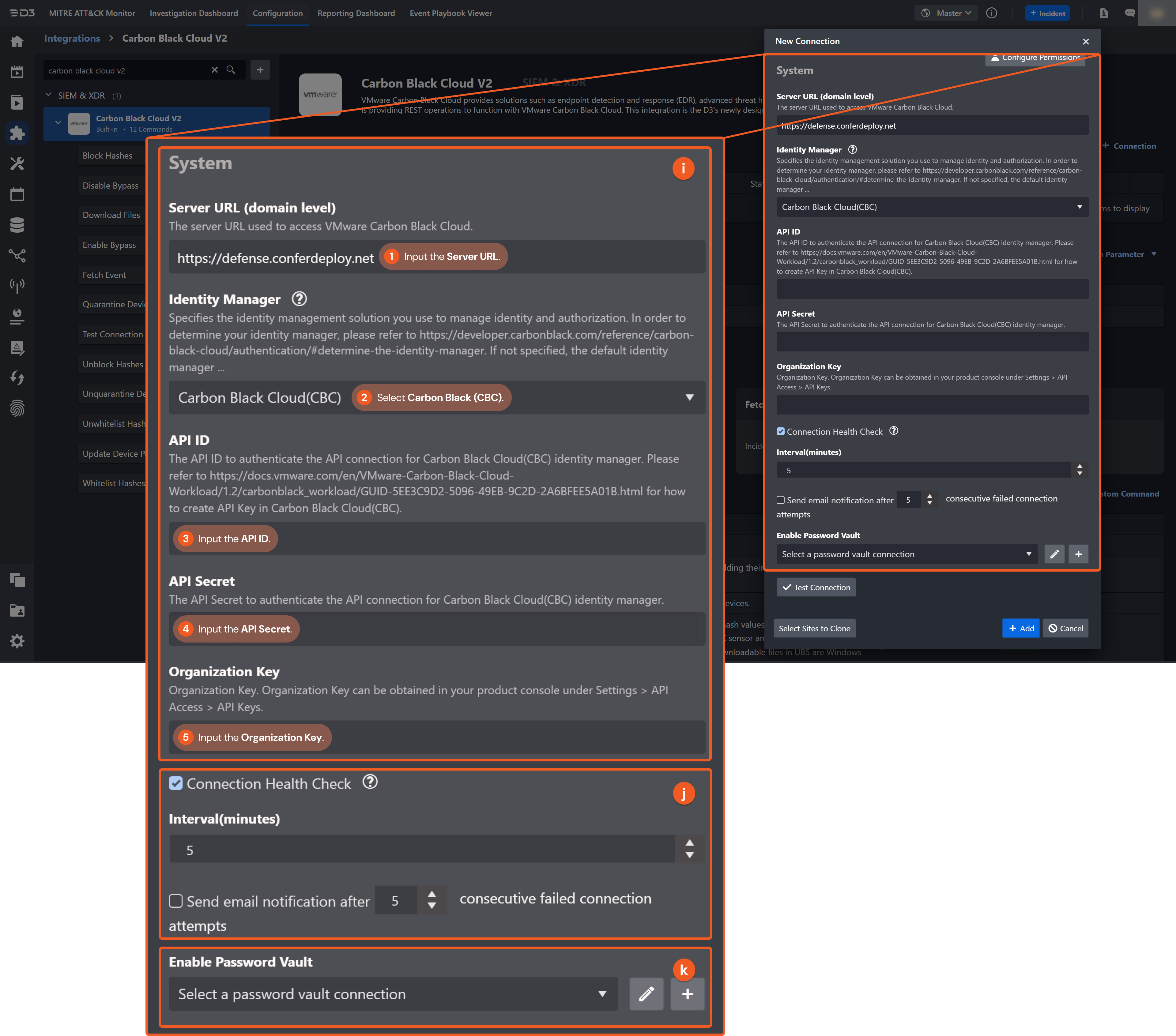
1. Input the server URL used to access VMware Carbon Black Cloud.
2. Select Carbon Black Cloud (CBC).
3. Input the API ID.
4. Input the API Secret.
5. Input the Organization Key.
Identity Manager: VMware Cloud Services Platform (CSP)
.png?inst-v=9d16beaf-952a-4ae4-8fe8-e35f7a3745da)
1. Input the server URL used to access VMware Carbon Black Cloud.
2. Select VMware Cloud Services Platform (CSP).
3. Input the API ID.
4. Input the API Secret.
5. Input the Organization Key.
Connection Health Check: Periodically checks the connection status by scheduling the Test Connection command at the specified interval (in minutes). Available only for active connections, this feature also allows configuring email notifications for failed attempts.
Enable Password Vault: An optional feature that allows users to take the stored credentials from their own password vault. Refer to the password vault connection guide if needed.
Test the connection.
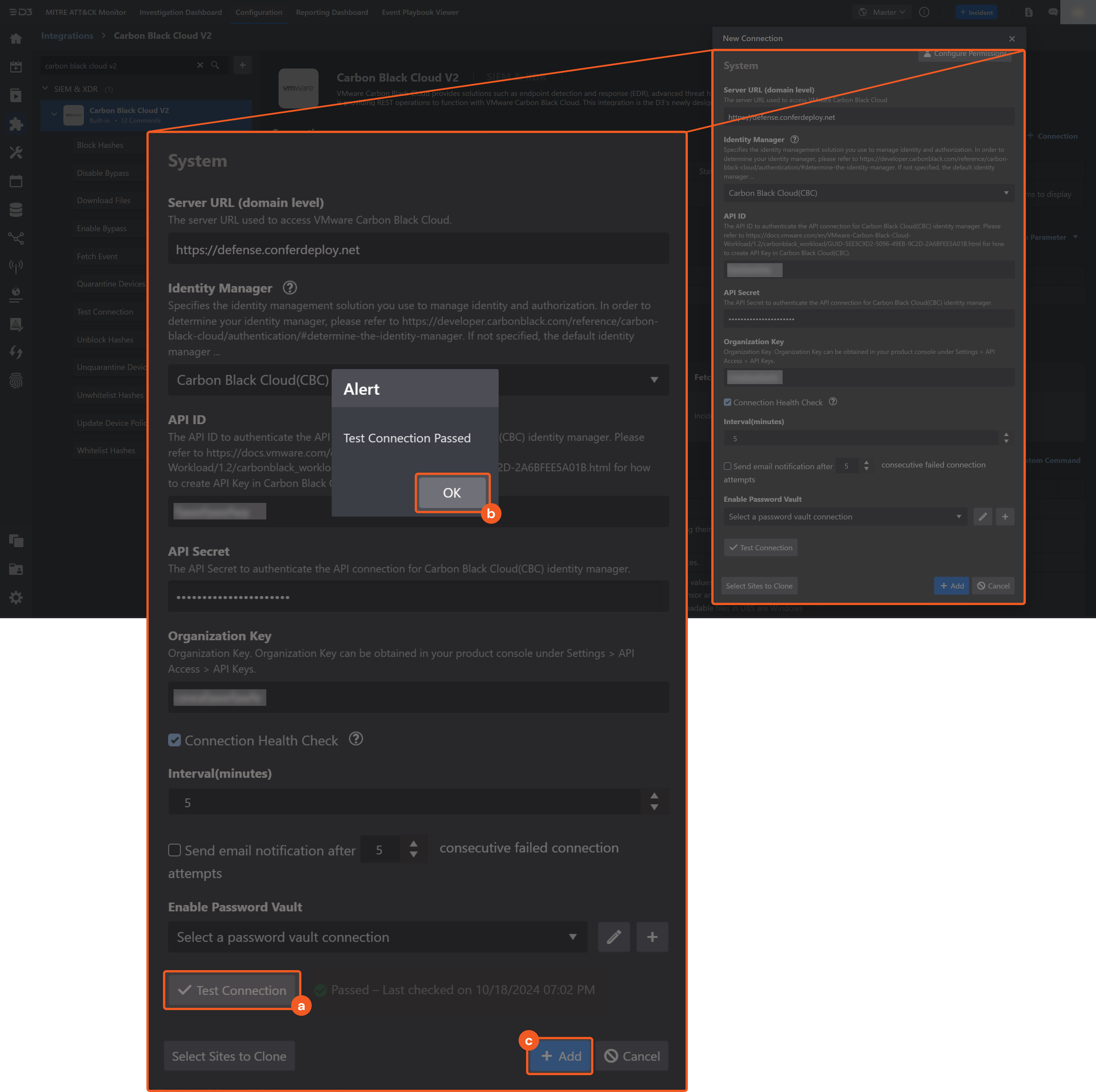
Click on the Test Connection button to verify credentials and connectivity. A success alert displays Passed with a green checkmark. If the connection fails, review the parameters and retry.
Click OK to close the alert window.
Click + Add to create and add the configured connection.
Commands
Carbon Black Cloud V2 includes the following executable commands for users to set up schedules or create playbook workflows. With the Test Command, users can execute these commands independently for playbook troubleshooting.
Integration API Note
For more information about the Carbon Black Cloud V2 API, refer to the following API references:
Alert API: Alerts API - Carbon Black Developer Network
UBS File API: Unified Binary Store REST API Reference - Carbon Black Developer Network
EnrichedEvent API migration to Observation API: Enriched Events API Migration
READER NOTE
Certain permissions are required for each command. Refer to the Permission Requirements and Configuring Carbon Black Cloud V2 to Work with D3 SOAR for details.
Note for Time-related parameters
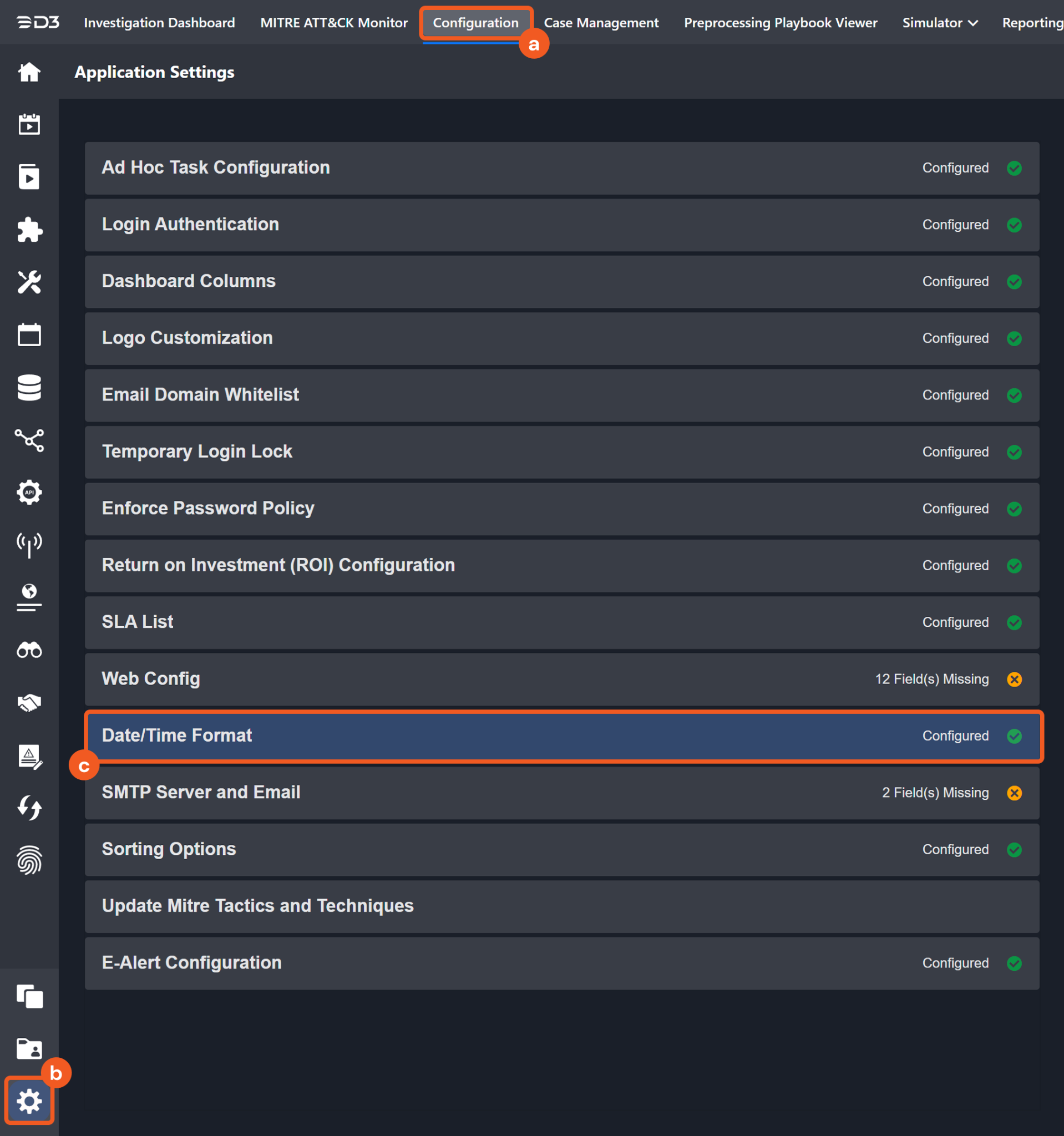
The input format of time-related parameters may vary based on user account settings, which may cause the sample data in commands to differ from what is displayed. To adjust the time format, follow these steps:
Navigate to Configuration > Application Settings. Select Date/Time Format.
Choose the desired date and time format, then click on the Save button.
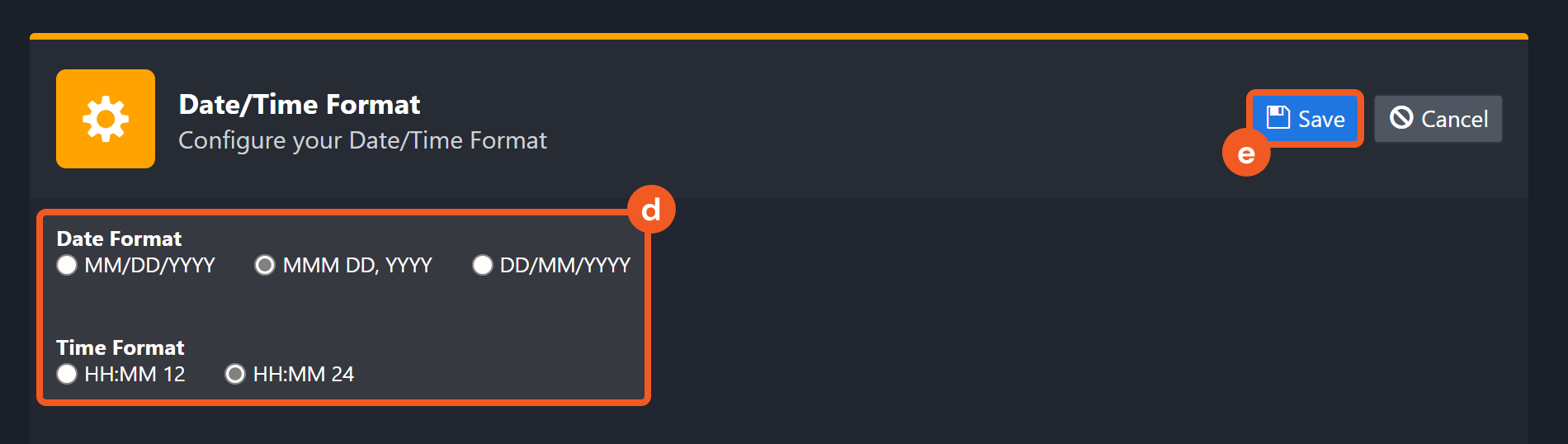
The selected time format will now be visible when configuring Date/Time command input parameters.
Block Hashes
Blocks specified applications by adding their SHA256 hashes to the Reputation Banned list.
Input
Input Parameter | Required/Optional | Description | Example |
SHA256 Hashes | Required | The SHA256 hashes of the applications to block. |
JSON
|
File Names | Optional | The application names associated with the given SHA256 hashes. To omit a file name, insert an empty string ("") at the relevant position in the list; for example, with a hash list ["SHA256Hash-1", "SHA256Hash-2", "SHA256Hash-3"], the corresponding file name list might be ["FileName-1", "", "FileName-3"]. If you choose not to associate any file names with the SHA256 hashes, simply leave the parameter empty. |
JSON
|
Descriptions | Optional | The descriptions for the SHA256 hashes to be blocked. If you choose not to associate any descriptions with the SHA256 hashes, simply leave the parameter empty. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Block Hashes failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Carbon Black Cloud V2 portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Validation failed for argument [1]. |
Error Sample Data Block Hashes failed. Status Code: 400. Message: Validation failed for argument [1]. |
Disable Bypass
Disables bypass on the specified devices.
READER NOTE
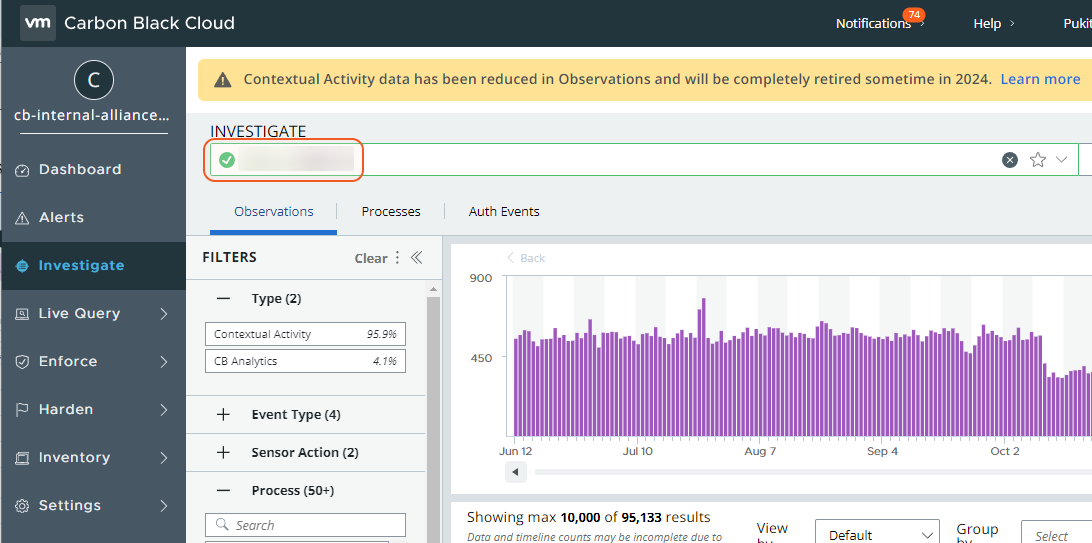
To locate device IDs in Carbon Black Cloud, go to the sidebar and select Inventory, then Endpoints. Select an endpoint from the list.
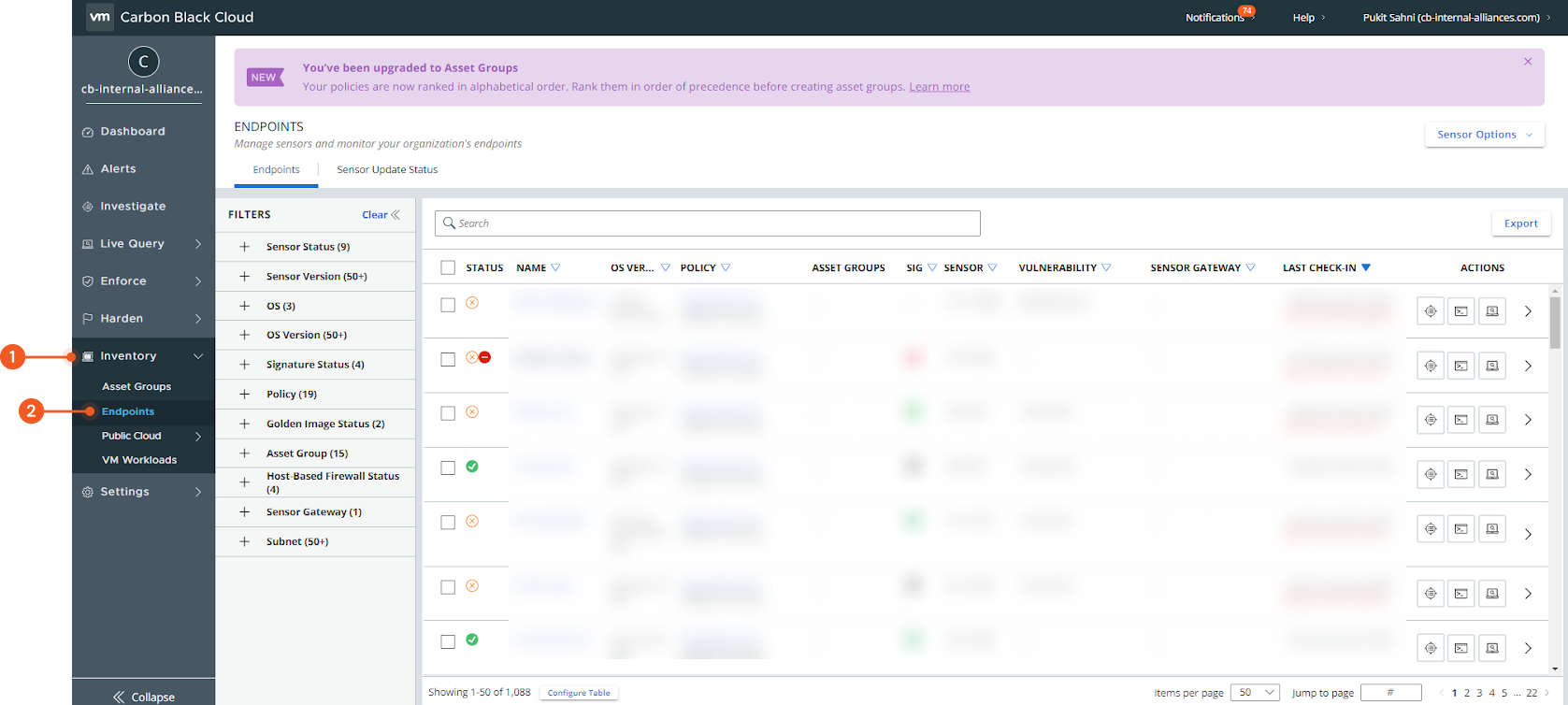
The device ID can be found under the INVESTIGATE section.
Input
Input Parameter | Required/Optional | Description | Example |
Device IDs | Required | The IDs of the device to disable bypass. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Disable Bypass failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Carbon Black Cloud V2 portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: NOT_FOUND device_id(s) : [xxx]. |
Error Sample Data Disable Bypass failed. Status Code: 404. Message: NOT_FOUND device_id(s) : [xxx]. |
Download Files
Downloads files by their SHA256 hash values. Currently, this feature is compatible with the Windows CBC sensor and supports the Unified Binary Store (UBS). As such, all downloadable files in UBS are Windows Portable Executable (PE) files.
READER NOTE
The parameter SHA-256s is required to run this command.
Run the Fetch Event command to obtain SHA-256 hashes. SHA-256 hashes can be found in the returned raw data, at the path $.results[*].process_sha256. Note that this SHA value is visible only when the Event Type is set to "Alert". Additionally, SHA-256 hashes from external sources are not usable. The hashes must be obtained using the Fetch Event command for the purpose of downloading files.
Input
Input Parameter | Required/Optional | Description | Example |
SHA-256s | Required | The SHA256 hash values of the files to download. SHA256 hash values can be obtained using the Fetch Event command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Download Files failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Carbon Black Cloud V2 portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Invalid sha256s: xxx. |
Error Sample Data Download Files failed. Status Code: 400. Message: Invalid sha256s: xxx. |
Enable Bypass
Enable bypass on the specified devices.
READER NOTE
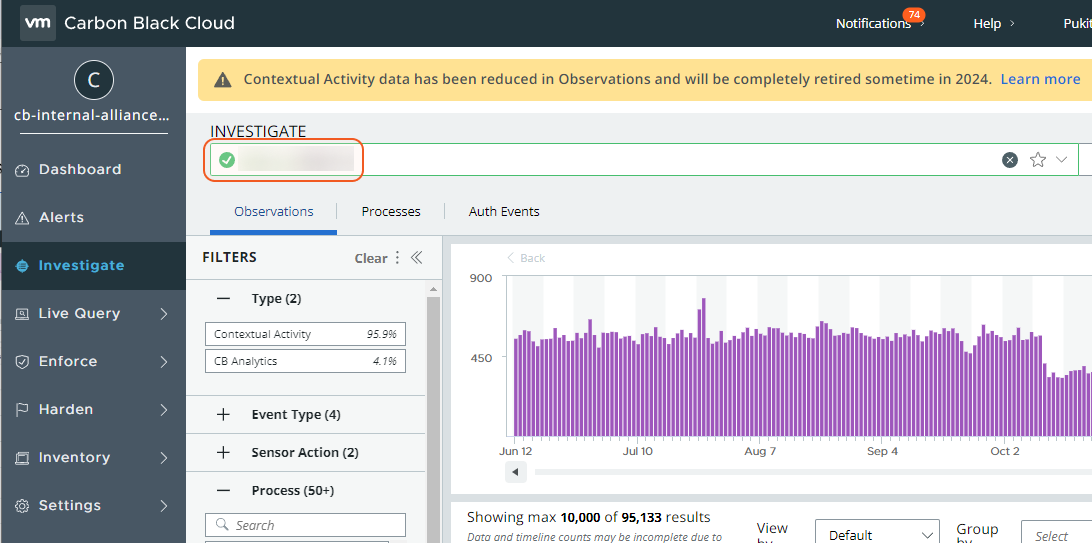
To locate device IDs in Carbon Black Cloud, go to the sidebar and select Inventory, then Endpoints. Select an endpoint from the list.
The device ID can be found under the INVESTIGATE section.
Input
Input Parameter | Required/Optional | Description | Example |
Device IDs | Required | The IDs of the devices to enable bypass. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Enable Bypass failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Carbon Black Cloud V2 portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: NOT_FOUND device_id(s) : [xxx]. |
Error Sample Data Enable Bypass failed. Status Code: 404. Message: NOT_FOUND device_id(s) : [xxx]. |
Fetch Event
Returns event(s) from the Carbon Black Cloud platform based on specified criteria. You can select to fetch alerts or observations.
READER NOTE
If no input parameters are defined, the command retrieves alerts from the past month, up to a maximum of 500.
The Start Time and End Time parameters you specify will organize the results based on two different timestamps: "backend_update_timestamp" and "user_update_timestamp" for Alerts, and "backend_timestamp" for Observations.
If the command doesn't find any matching filters, it will still run successfully but will return no results.
Input
Input Parameter | Required/Optional | Description | Example |
Start Time | Optional | The start time of the range to fetch events in UTC time. Note: This parameter is relevant for both "Alert" and "Observation" event types. For the "Alert" event type, the relevant time fields are "backend_update_timestamp" and "user_update_timestamp." For the "Observation" event type, the applicable time field is "backend_timestamp. If a start time is not explicitly stated, it defaults to 30 days before the specified end time. | 2023-04-01 00:00 |
End Time | Optional | The end time of the range to fetch events in UTC time. Note: This parameter is relevant for both "Alert" and "Observation" event types. For the "Alert" event type, the relevant time fields are "backend_update_timestamp" and "user_update_timestamp." For the "Observation" event type, the applicable time field is "backend_timestamp. If not specified, the default end time is the current time. | 2023-04-15 00:00 |
Event Type | Optional | The type of event (i.e. Alert or Observation) to retrieve. The default value will be Alert if no event type is specified. | Alert |
Number of Event(s) Fetched | Optional | The maximum number of events to retrieve, with a valid range from 1 to 10,000. For results exceeding 10,000, use additional filters to narrowresult down the data. If this parameter is not defined, the default value is set to 500. This parameter is applicable to both "Alert" and "Observation" event types. | 10 |
Query | Optional | The Lucene format query to filter results. You have the option to use either "Query", "Criteria", or both. If both are used, only results that meet both conditions will be shown.
| device_username:"*****@*****.**" AND process_name:windows_update_status.ps1 |
Criteria | Optional | The JSON object containing the required values in the returned search results. You must specify either "Query" or "Criteria'"', or both. When both are used, results matching both parameters are returned.
|
JSON
|
Tolerance Scope | Optional | The tolerance scope (in minutes) for the query to fetch events between the specified start and end time to avoid event loss or fetch failure. The events will be fetched between {Start Time - Tolerance Scope, End Time}. The default value is 0. | 0 |
Get Alert Observations | Optional | The Fetch Event command ingests alert observations. The default value of this field is False. This parameter only applies to the Alert event type. | True |
Output
To view the sample output data for all commands, refer to this article.
Fetch Event Field Mapping
See Field Mappings.
The Carbon Black Cloud V2 system integration includes pre-configured field mappings for the default event source.
The Default Event Source is the default system-provided set of field mappings applied when the fetch event command is executed. It includes a Main Event JSON Path, which is the JSONPath expression that points to the base array of event objects. The source field path continues from this array to locate the required data.
The Main Event JSON Path can be viewed by clicking on the Edit Main JSON Path button.
.png?inst-v=9d16beaf-952a-4ae4-8fe8-e35f7a3745da)
Main Event JSON Path: $.results
The results array contains the event objects. For example, within each Alert event object, the key id denotes the Event code field. As such, the full JSONPath expression to extract the Event code is $.results.id.
Event Source for Alerts Event
The D3 system configures the field mappings which are specific to the alert-related events. If a source field in the field mapping is not found, the corresponding field mapping will be ignored. Because the eventType field in the raw data for Alert events consistently has the value alert, events can be defined by the Search String: {$.eventType}=alert. Click Edit Event Source to view the Search String.
Event Source for Observation Event
The D3 system configures the field mappings which are specific to the observation-related events. If a source field in the field mapping is not found, the corresponding field mapping will be ignored. Because the eventType field in the raw data for Observation events consistently has the value observation, events can be defined by the Search String: {$.eventType}=observation. Click Edit Event Source to view the Search String.
The pre-configured field mappings are detailed below:
Field Name | Source Field |
Default Event Source (Main Event JSON Path: $.results) | |
N/A | |
Event Source for Alerts Event (Search String:{$.eventType}=alert) The search string format is {jsonpath}=value. If the value of the eventType key is alert in the event object under raw data, then the alert-related events will use the field mapping below. | |
Event code | .id |
Event Type | .type |
Start Time | .detection_timestamp |
Description | .reason |
Severity | .severity |
Primary Event ID | .primary_event_id |
Threat event ID | .threat_id |
Hostname | .device_name |
Status | .workflow.status |
Sensor Action | .sensor_action |
Run State | .run_state |
Determination | .determination.value |
Tag | .tags |
Operating system | .device_os_version |
Username | .device_username |
Reason Code | .reason_code |
Process Name | .process_name |
Process Hash SHA256 | .process_sha256 |
Process GUID | .process_guid |
Process command line | .process_cmdline |
Process ID | .process_pid |
Parent process name | .parent_name |
Parent Process Hash SHA256 | .parent_sha256 |
Parent process GUID | .parent_guid |
Parent process commandline | .parent_cmdline |
Parent process ID | .parent_pid |
Child Process Name | .childproc_name |
Child Process Hash SHA256 | .childproc_sha256 |
Child Process GUID | .childproc_guid |
Child Process Commandline | .childproc_cmdline |
Blocked Process Name | .blocked_sha256 |
Blocked Process Reputation | .blocked_effective_reputation |
Tactics | .attack_tactic |
Techniques | .ttps |
Device ID | .device_id |
Device Internal IP | .device_internal_ip |
Device External IP | .device_external_ip |
Device priority | .device_target_value |
First Activity Time | .first_event_timestamp |
Last Activity Time | .last_event_timestamp |
Event Source for Observation Event (Search String: {$.eventType}=observation) The search string format is {jsonpath}=value. If the value of the eventType key is observation in the event object under raw data, then the observation-related events will use the field mapping below. | |
Unique Event Key | .observation_id |
Event Type | .event_type |
Start Time | .detection_timestamp |
Description | .observation_description |
Observation Type | .observation_type |
Enriched Event Type | .enriched_event_type |
Hostname | .device_name |
Process Name | .process_name |
Process Hash | .process_hash |
Process GUID | .process_guid |
Process ID | .process_pid |
Parent process GUID | .parent_guid |
Parent process ID | .parent_pid |
Device ID | .device_id |
Device Group ID | .device_group_id |
Process Username | .process_username |
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Fetch Event failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Carbon Black Cloud V2 portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. Please check D3Error object in RawData for more details. |
Error Sample Data Fetch Event failed. Status Code: 401. Message: Unauthorized. Please check D3Error object in RawData for more details. |
Quarantine Devices
Quarantines the specified device(s).
READER NOTE
To locate device IDs in Carbon Black Cloud, go to the sidebar and select Inventory, then Endpoints. Select an endpoint from the list.
The device ID can be found under the INVESTIGATE section.
Input
Input Parameter | Required/Optional | Description | Example |
Device IDs | Required | The IDs of the devices to quarantine. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Quarantine Devices failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Carbon Black Cloud V2 portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: NOT_FOUND, device_id(s) : [xxx]. |
Error Sample Data Quarantine Devices failed. Status Code: 404. Message: NOT_FOUND, device_id(s) : [xxx]. |
Unblock Hashes
Unblocks specified applications by adding their SHA256 hashes to the Reputation Banned list.
READER NOTE
The input SHA256 hashes must be previously blocked in order to proceed with unblocking.
Input
Input Parameter | Required/Optional | Description | Example |
SHA256 Hashes | Required | The SHA256 hashes of the applications to unblock. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Unblock Hashes failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Carbon Black Cloud V2 portal. Refer to the HTTP Status Code Registry for details. | Status Code: 404. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: No result data when getting SHA256's OverrideID, one of the SHA256s may not exist, not in banned list or is incorrect. |
Error Sample Data Unblock Hashes failed. Status Code: 404. Message: No result data when getting SHA256's OverrideID, one of the SHA256s may not exist, not in banned list or is incorrect. |
Unquarantine Devices
Unquarantines the specified device(s).
READER NOTE
To locate device IDs in Carbon Black Cloud, go to the sidebar and select Inventory, then Endpoints. Select an endpoint from the list.
The device ID can be found under the INVESTIGATE section.
Input
Input Parameter | Required/Optional | Description | Example |
Device IDs | Required | The IDs of the devices to unquarantine. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Unquarantine Devices failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Carbon Black Cloud V2 portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: The value for parameter (Device IDs) is invalid. |
Error Sample Data Unquarantine Devices failed. Status Code: 400. Message: The value for parameter (Device IDs) is invalid. |
Unwhitelist Hashes
Removes the specified applications of the given SHA256 hashes from the Reputation Approved List.
READER NOTE
The input SHA256 hashes must be previously whitelisted in order to proceed with unwhitelisting.
Input
Input Parameter | Required/Optional | Description | Example |
SHA256 Hashes | Required | The SHA256 hashes of the applications to unwhitelist. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Unwhitelist Hashes failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Carbon Black Cloud V2 portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: No result data when getting SHA256's OverrideID, one of the SHA256s may not exist or is incorrect. |
Error Sample Data Unwhitelist Hashes failed. Status Code: 400. Message: No result data when getting SHA256's OverrideID, one of the SHA256s may not exist or is incorrect. |
Update Device Policy
Updates device policies by device IDs.
READER NOTE
The Policy ID parameter is required to run this command.
Run the Fetch Incident command to obtain Policy IDs. Policy IDs can be found in the returned raw data, at the path $.results[*].device_policy_id.
To locate device IDs in Carbon Black Cloud, go to the sidebar and select Inventory, then Endpoints. Select an endpoint from the list.
The device ID can be found under the INVESTIGATE section.
Input
Input Parameter | Required/Optional | Description | Example |
Device IDs | Required | The IDs of the devices to update policies. |
JSON
|
Policy ID | Required | The ID of the policy to update the devices to. | ***** |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Update Device Policy failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Carbon Black Cloud V2 portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. Please check D3Error object in RawData for more details. |
Error Sample Data Update Device Policy failed. Status Code: 401. Message: Unauthorized. Please check D3Error object in RawData for more details. |
Whitelist Hashes
Adds the specified applications of the given SHA256 hashes from the Reputation Approved List.
READER NOTE
Ensure the number of SHA256 hashes, file names, and descriptions are equal. You can omit file names and descriptions, but if included, their numbers must match the hashes. For example, for two hashes, provide either no file names and descriptions or two of each. A mismatch triggers the: "File Names or Descriptions parameter's length do not match with SHA256 Hashes parameter" error message.
Input
Input Parameter | Required/Optional | Description | Example |
SHA256 Hashes | Required | The SHA256 hashes of the applications to whitelist. |
JSON
|
File Names | Optional | The application names associated with the given SHA256 hashes. |
JSON
|
Descriptions | Optional | The descriptions for the SHA256 hashes to be blocked. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data is Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Whitelist Hashes failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Carbon Black Cloud V2 portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Validation failed for argument [1]. |
Error Sample Data Whitelist Hashes failed. Status Code: 400. Message: Validation failed for argument [1]. |
Test Connection
Allows users to perform a health check on an integration connection. Users can schedule a periodic health check by selecting Connection Health Check when editing an integration connection.
Input
N/A
Output
Output Type | Description | Return Data Type |
Return Data | Indicates one of the possible command execution states: Successful or Failed. The Failed state can be triggered by any of the following errors:
More details about an error can be viewed in the Error tab. | String |
Error Handling
If the Return Data is Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Test Connection failed. Failed to check the connector. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Carbon Black Cloud V2 portal. Refer to the HTTP Status Code Registry for details. | Status Code: 401. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. Please check D3Error object in RawData for more details. |
Error Sample Data Test Connection failed. Failed to check the connector. Status Code: 401. Message: Unauthorized. Please check D3Error object in RawData for more details. |