Azure Virtual Networks
LAST UPDATED: SEPTEMBER 16, 2025
Overview
Microsoft Azure Virtual Network gives your organization an isolated and highly secure environment to run your virtual machines and applications.
D3 SOAR is providing REST operations to function with Azure Virtual Networks.
Azure Virtual Networks is available for use in:
Known Limitations
See Networking limits - Azure Resource Manager for details.
Connection
To connect to Azure Virtual Networks from D3 SOAR, follow this part to collect the required information below:
Parameter | Description | Example |
Server URL | The server URL for the API connection. | https://management.azure.com |
Directory ID | The directory ID used for authentication. | ***** |
Grant Type | The grant type used for authentication. | client_credentials |
Client ID | The client ID used for authentication. | ***** |
Client Secret | The client secret used for authentication. | ***** |
Resource | The name of the resource group within the user's subscription. | https://management.azure.com |
Subscriptions | The Azure subscription ID. | ***** |
API Version | The API Version used for the connection. | 2020-05-01 |
READER NOTE
The prerequisite for using this guide is an active Microsoft Azure subscription. Refer to Build in the cloud with an Azure account for more information.
Permission Requirements
Each endpoint in the Azure Virtual Networks API requires a certain permission scope. The following are required scopes for the commands in this integration:
Command | Required Permissions |
Create Network Interface | Network Contributor |
Create Network Security Group | Network Contributor |
Create Public IP Address | Network Contributor |
Create Subnet | Network Contributor |
Create Virtual Network | Network Contributor |
Delete Network Interface | Network Contributor |
Delete Network Security Group | Network Contributor |
Delete Public IP Address | Network Contributor |
Delete Subnet | Network Contributor |
Delete Virtual Network | Network Contributor |
List Network Interfaces | Network Contributor |
List Network Security Groups | Network Contributor |
List Public IP Addresses | Network Contributor |
List Subnets | Network Contributor |
List Virtual Networks | Network Contributor |
Test Connection | Network Contributor |
Azure Network Security Groups is using role-based access control (RBAC). Therefore, the command permissions are inherited from the security principal's role. Roles for security principals must be configured from the Azure portal to use the commands in this integration.
READER NOTE
Only security principals with the Role Based Access Control Administrator or User Access Administrator role can configure Azure roles. Refer to Assign Azure roles using Azure portal for more information on configuring user roles.
Configuring Azure Virtual Networks to Work with D3 SOAR
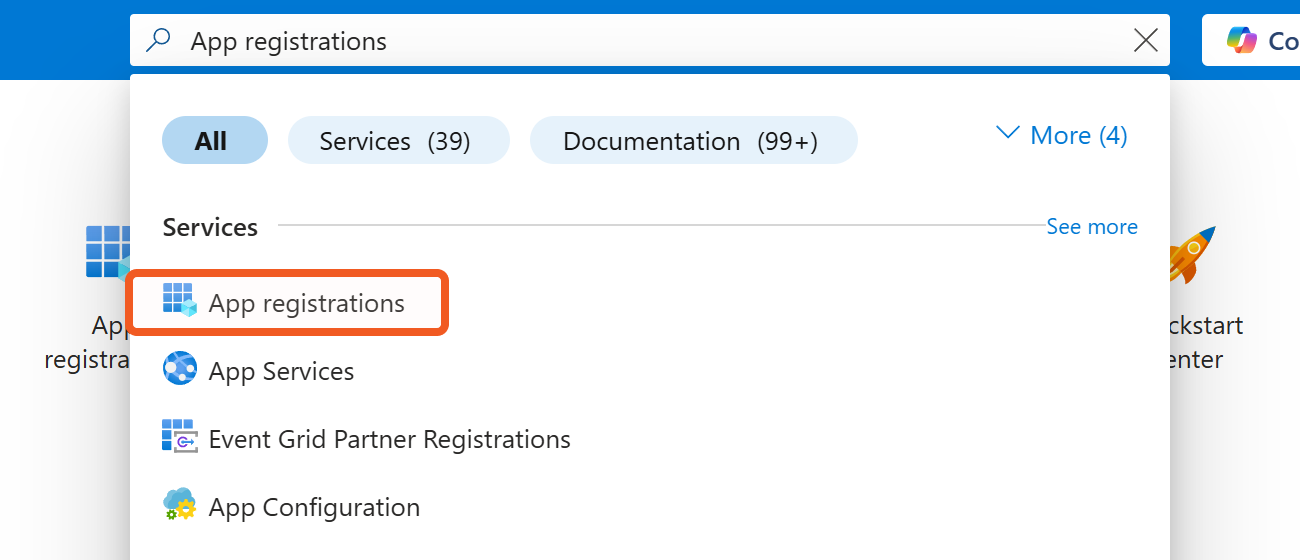
Navigate to the top search bar, then search for and select App registrations.
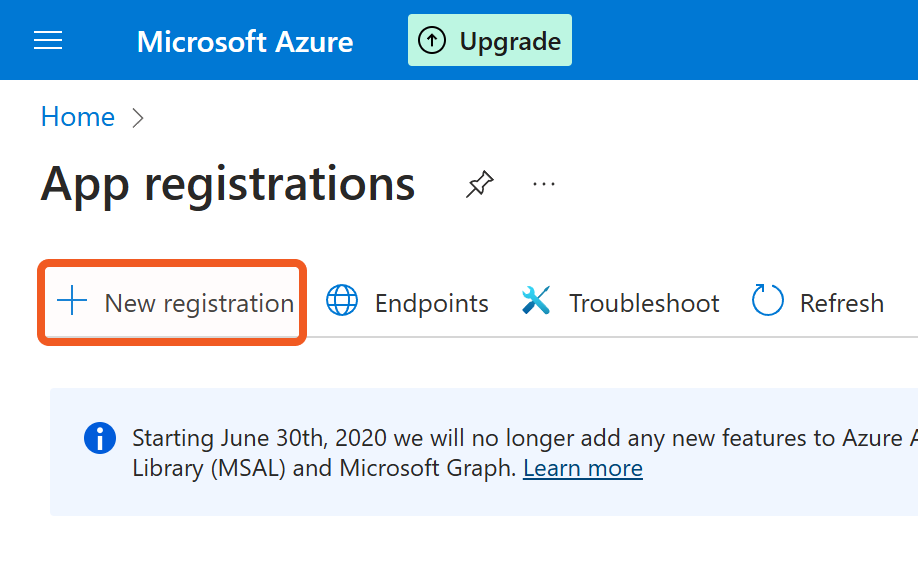
Click on the + New Registration button to create a new app. If using a pre-existing app, click into it and skip to step 5.
Register the application.
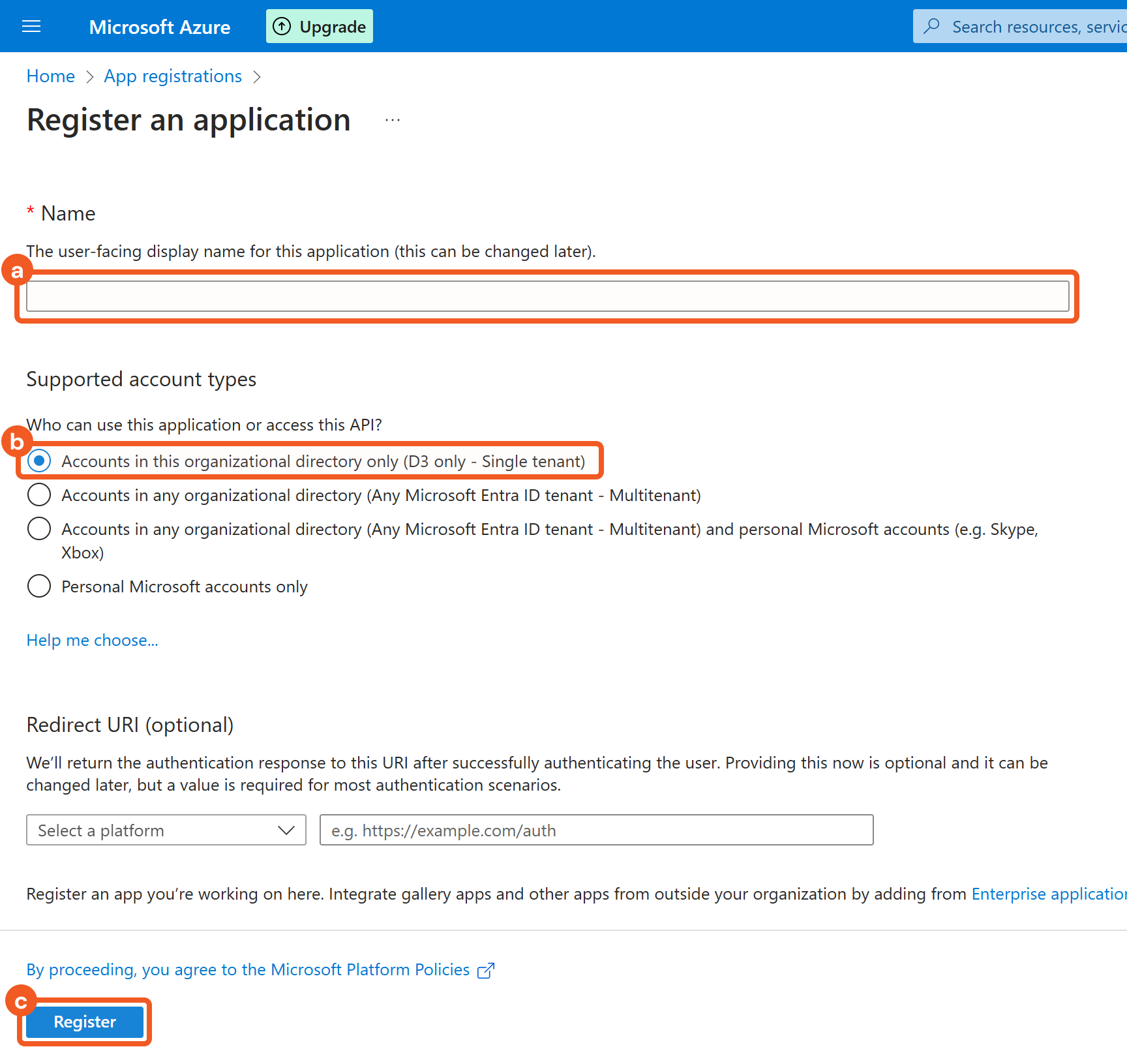
Enter a name.
Select the Accounts in this organizational directory only (<Your Directory Name> only - Single tenant) option.
Register the application.
Obtain the necessary credentials from the app's Overview tab.
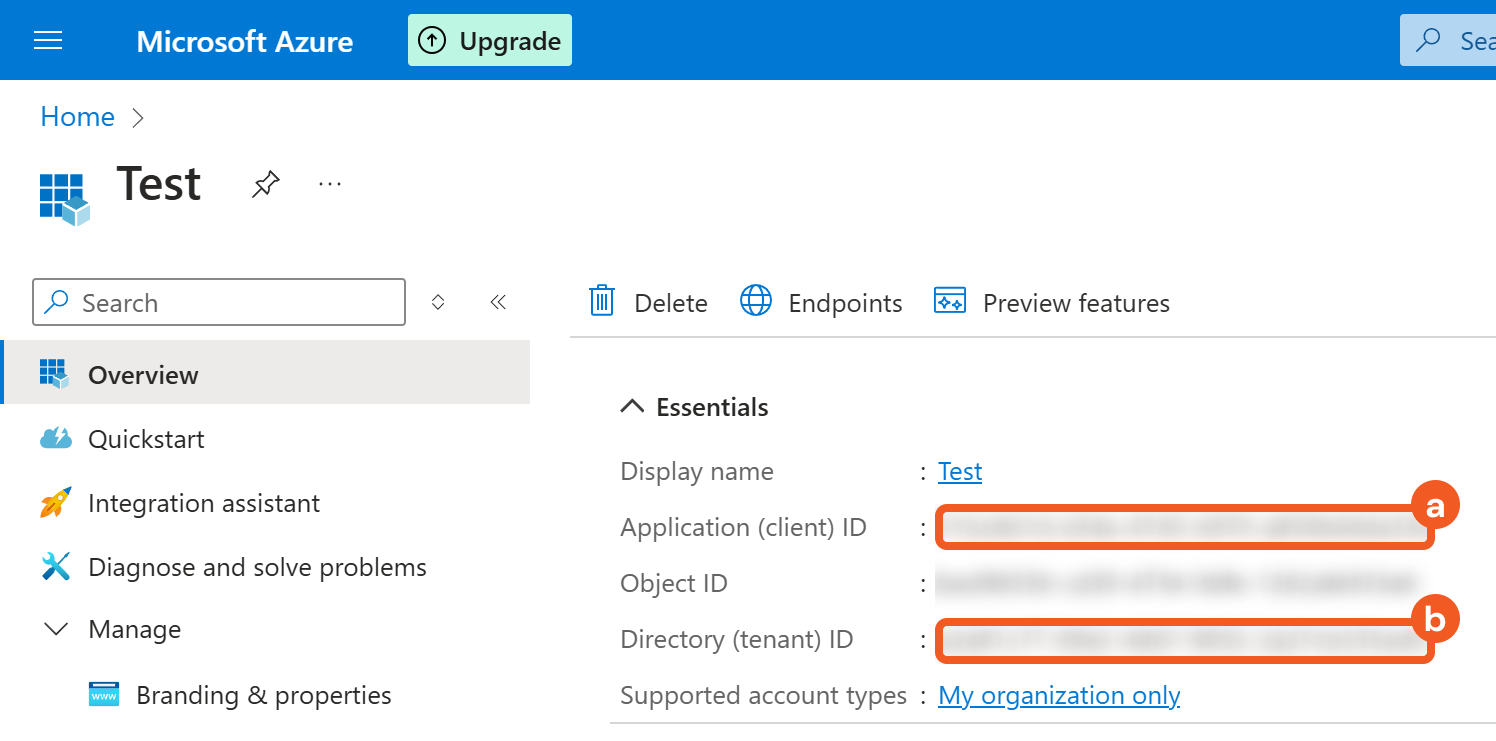
Copy the Application (client) ID and store it somewhere safe. Refer to step 3i sub-step 4 in Configuring D3 SOAR to Work with Azure Network Security Groups.
Copy the Directory (tenant) ID and store it somewhere safe. Refer to step 3i sub-step 2 in Configuring D3 SOAR to Work with Azure Network Security Groups.
Obtain the Client Secret.
Click on the Add a certificate or secret link.

Configure the client secret.
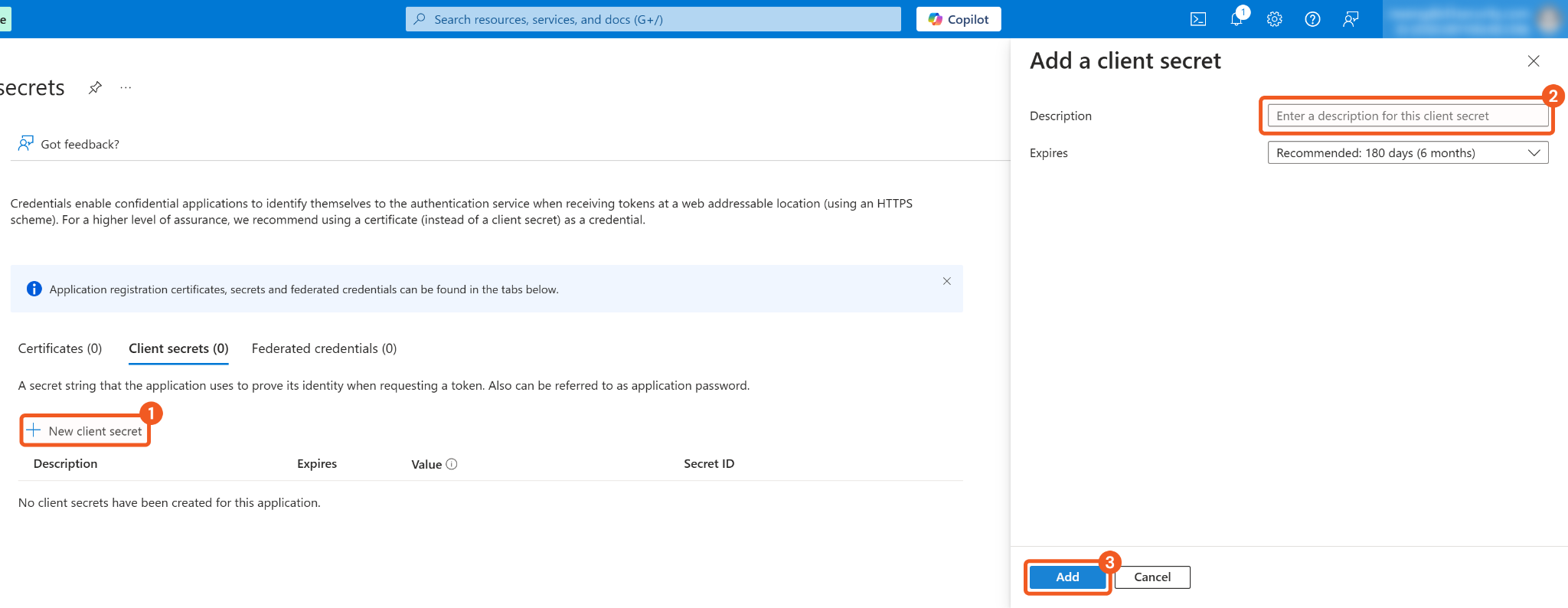
1. Click on the + New client secret button.
2. Enter a description.
3. Add the client secret.
Copy the Value of the newly created client secret and store it somewhere safe. Refer to step 3i sub-step 5 in Configuring D3 SOAR to Work with Azure Network Security Groups.
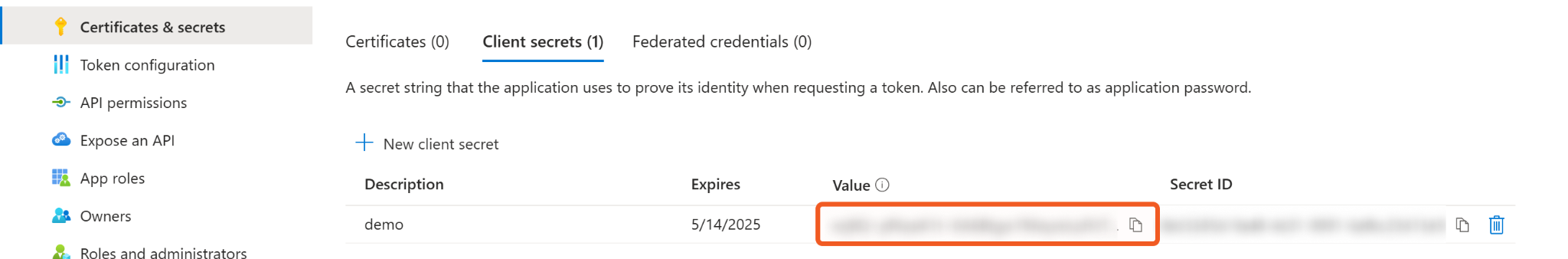
READER NOTE
The client secret value cannot be viewed again after the page is refreshed or closed.
Navigate to the top search bar, then search for and select Resource groups.
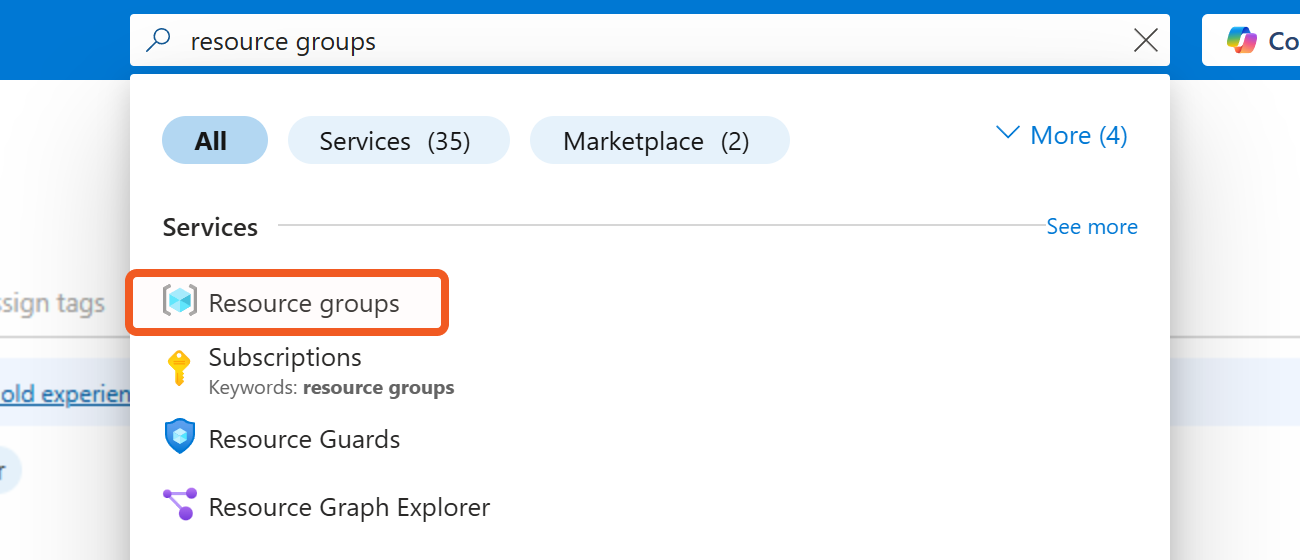
Click on the + Create button to create a new resource group. If using a pre-existing resource group, click into it and skip to step 10.

Configure the resource group.
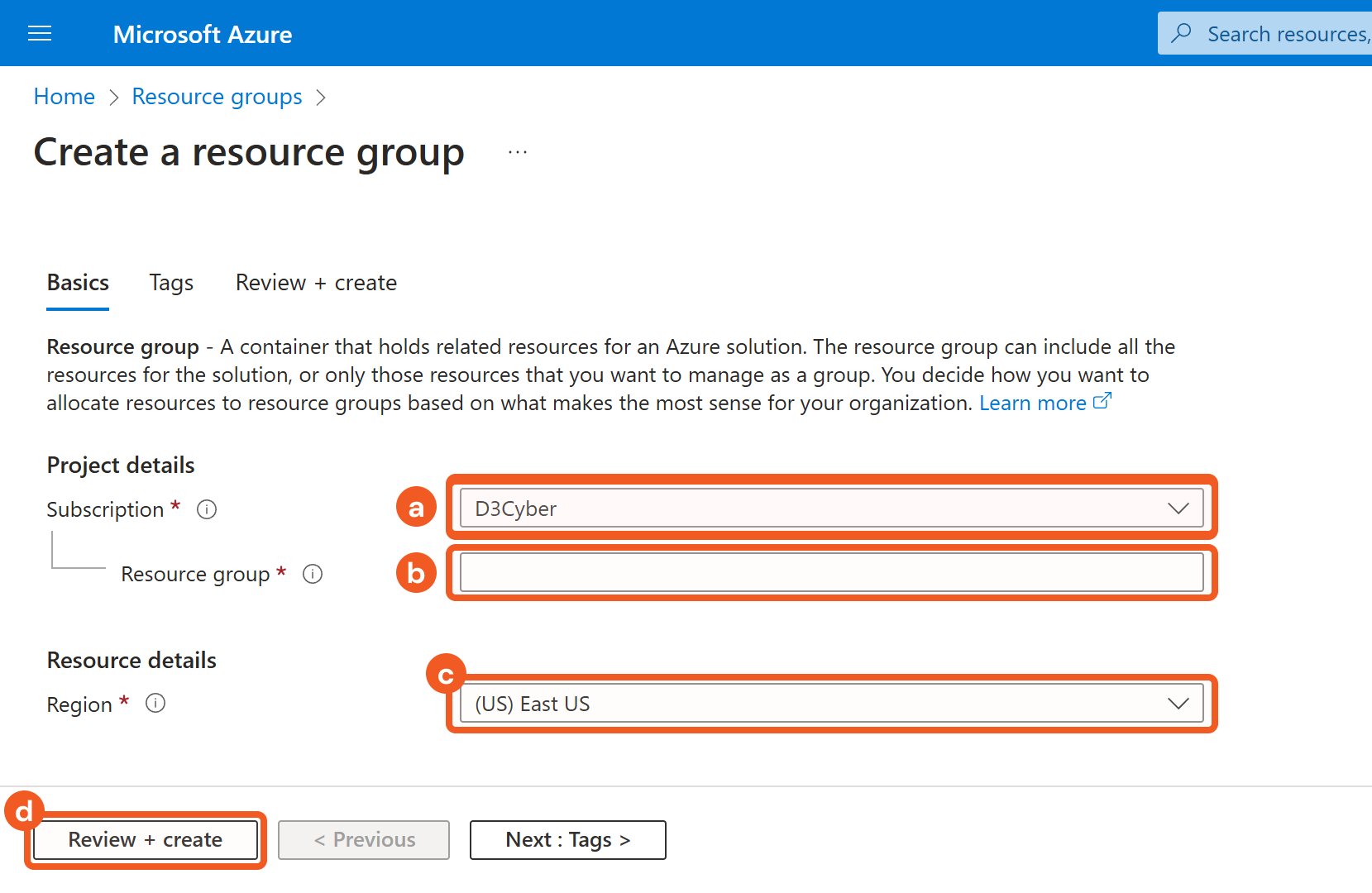
Select a subscription.
Name the resource group.
Select a region.
Click on the Review + Create button.
Create the resource group.
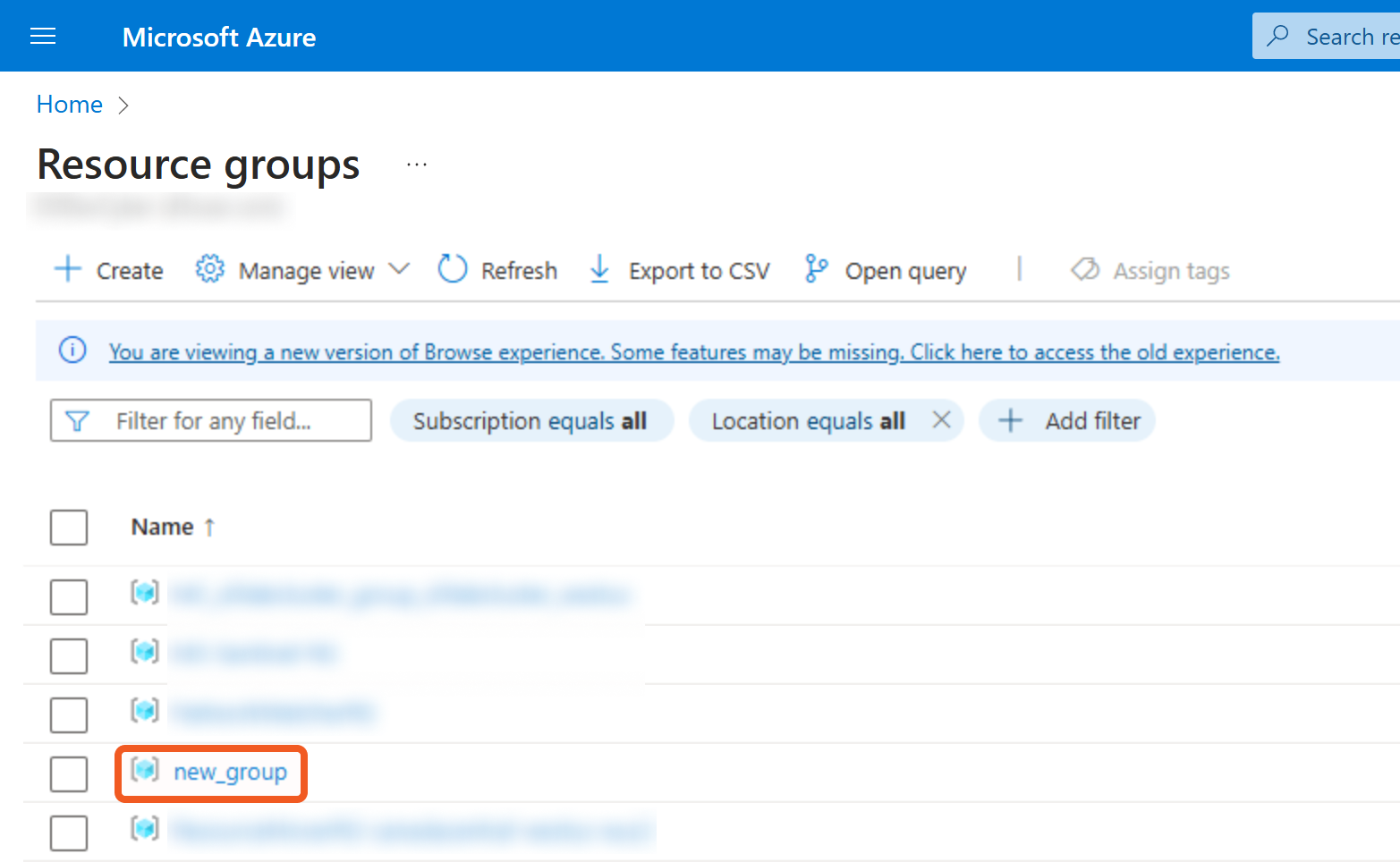
Navigate to Resource groups and select the group for which to configure roles.
Add a role assignment.
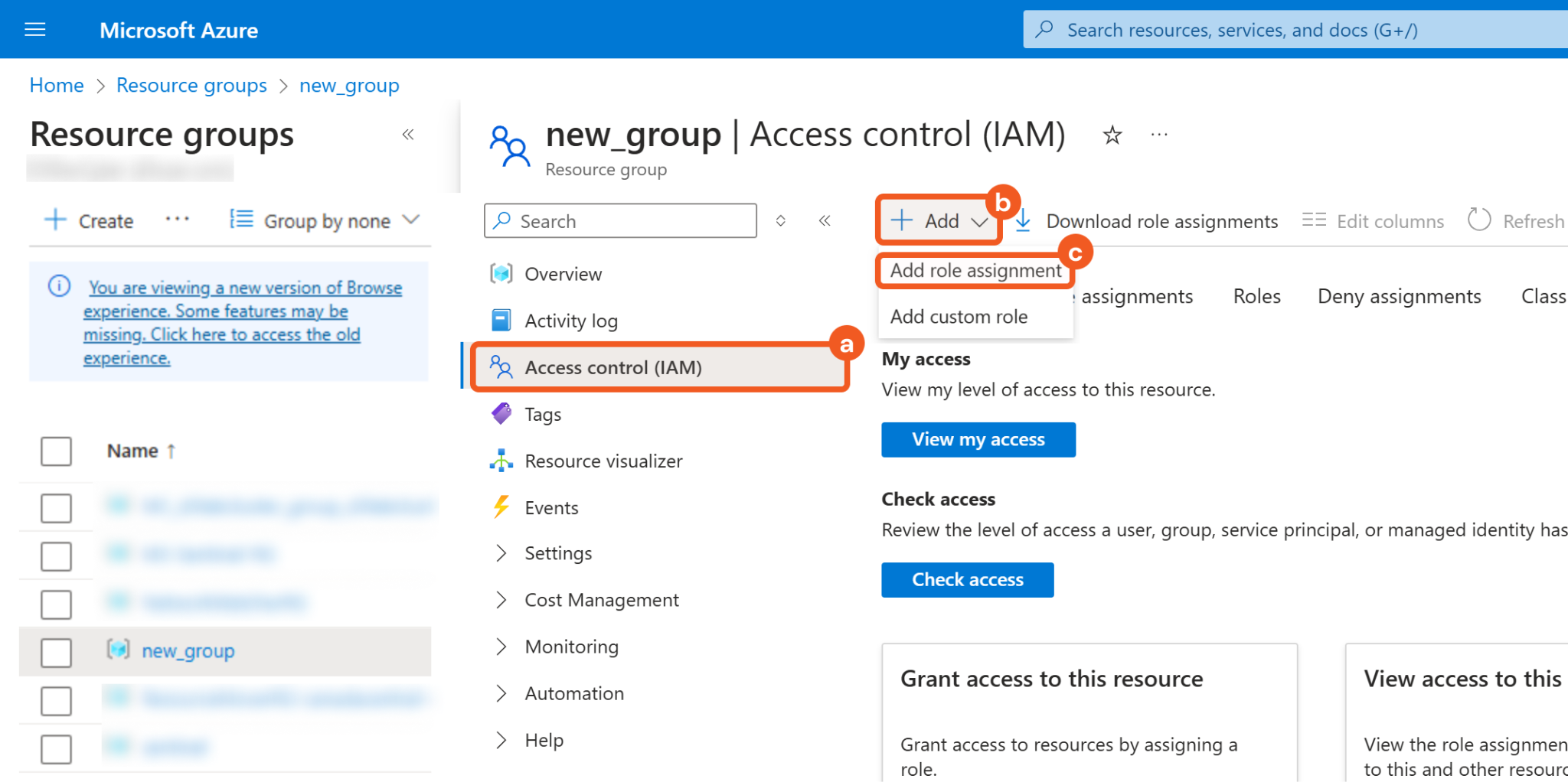
Select the Access Control (IAM) tab.
Click on the + Add button.
Click on the Add role assignment button.
Add the Network Contributor role.
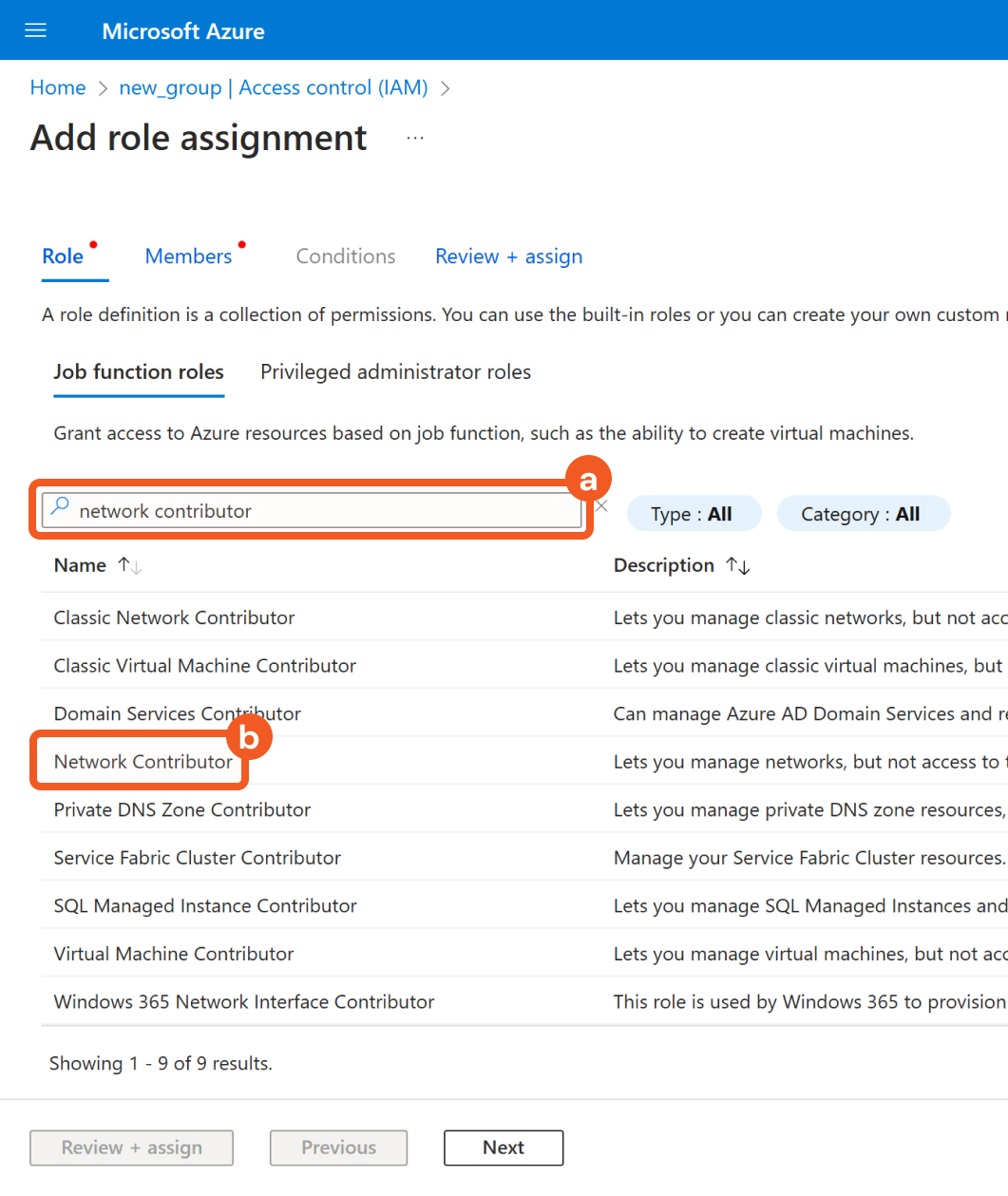
Search for the Network Contributor role.
Select the Network Contributor role.
Select members for the role.
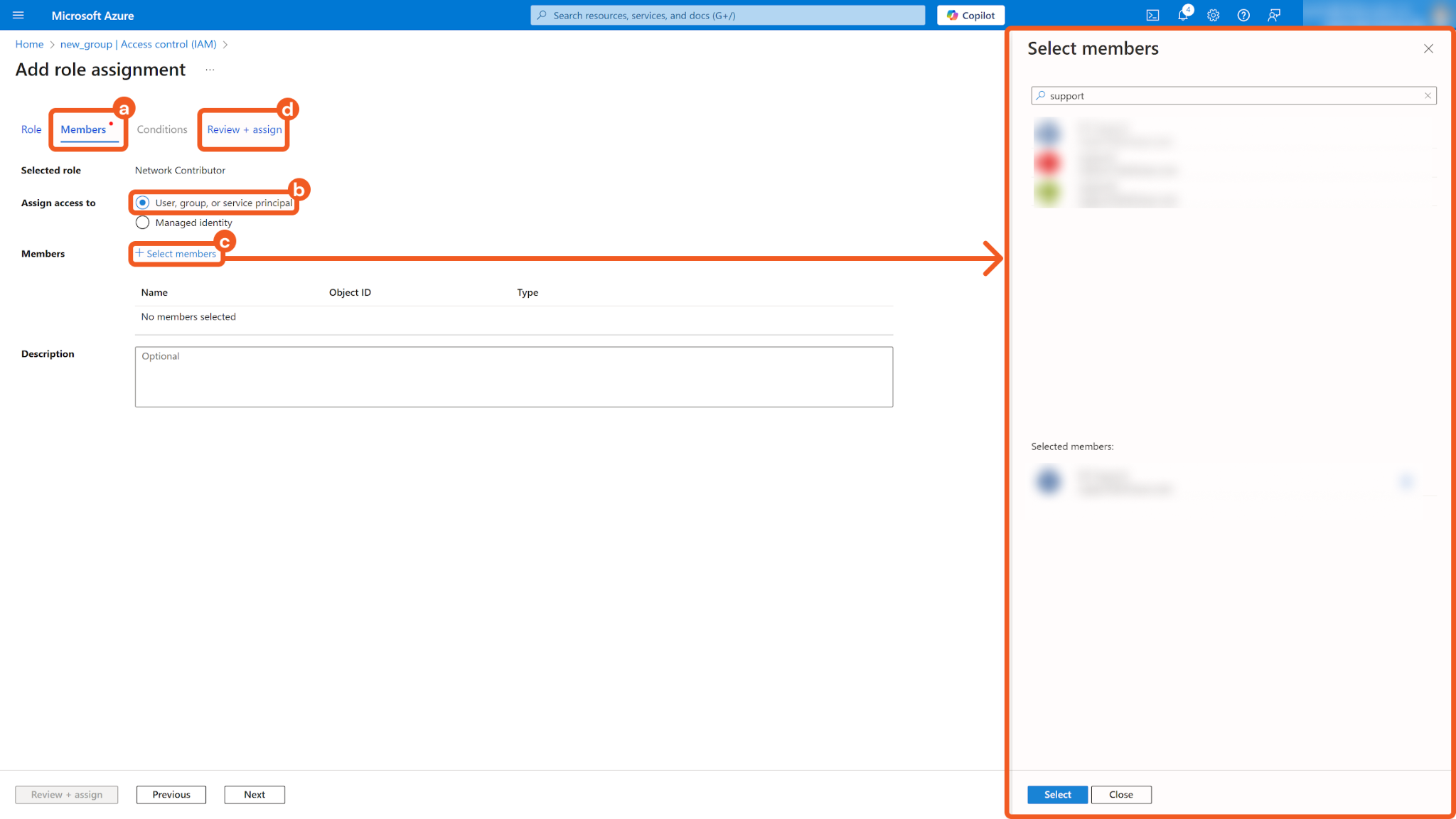
Click on the Members tab.
Select User, group, or service principal for Assign access to.
Search and select the members appropriate for the role.
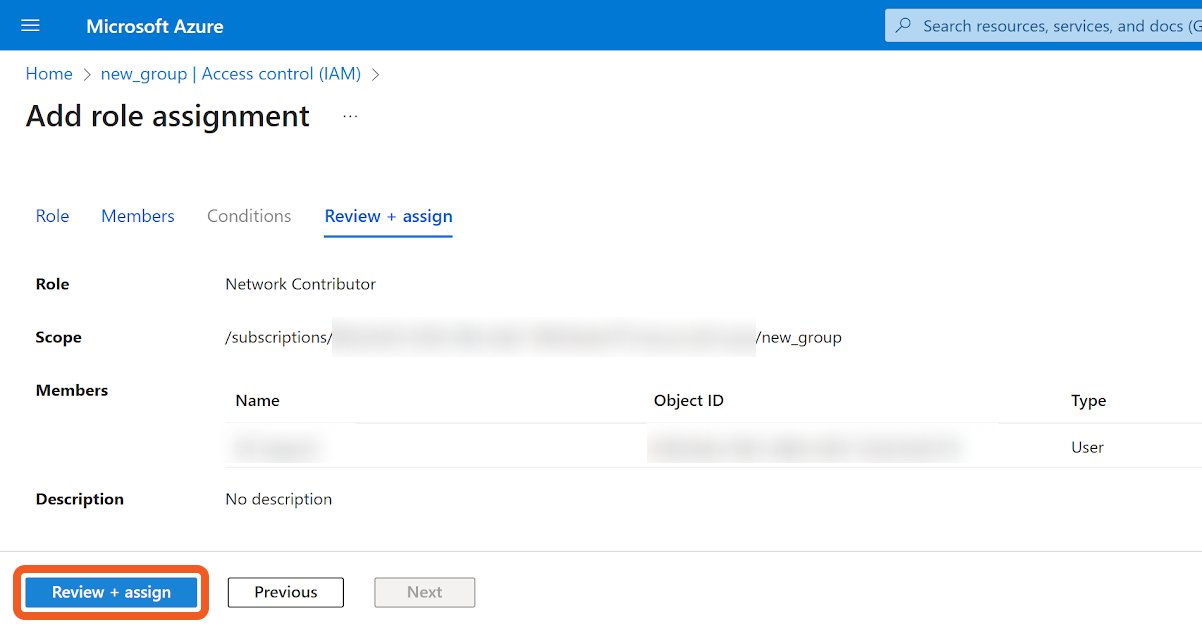
Click on the Review + assign tab.
Confirm and add the role assignment.
READER NOTE
If the dropdown options for + Add are grayed out, it may be due insufficient permissions or limited access scope. Contact the organization's administrator to request that the Network Contributor role (at a minimum) or an equivalent custom role be assigned to the account to use the commands.
Obtain the Subscription ID.
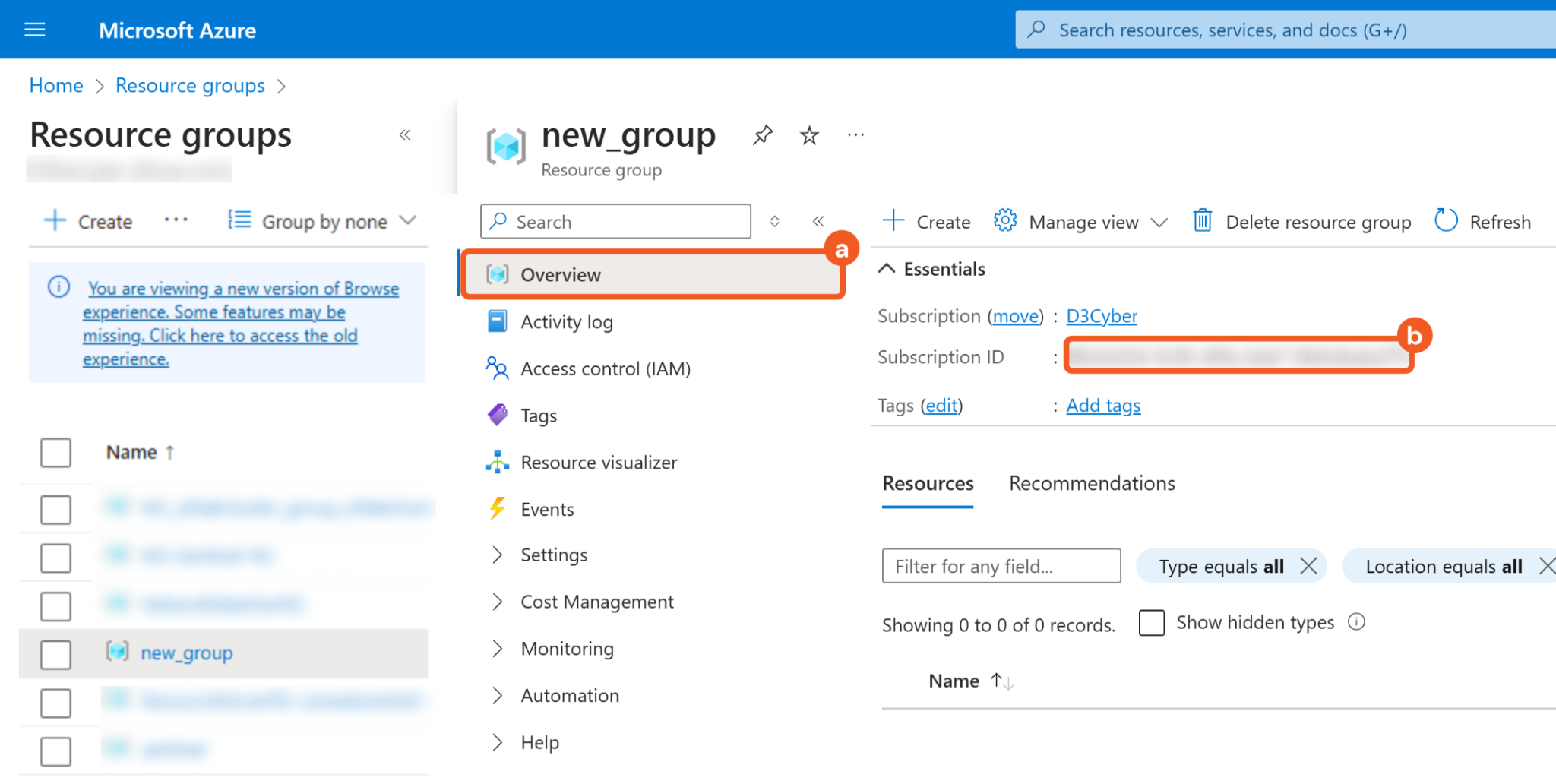
Click on the Overview tab.
Copy the Subscription ID and store it somewhere safe. Refer to step 3i sub-step 7 in Configuring D3 SOAR to Work with Azure Network Security Groups.
Configuring D3 SOAR to Work with Azure Virtual Networks
Log in to D3 SOAR.
Find the Azure Virtual Networks integration.
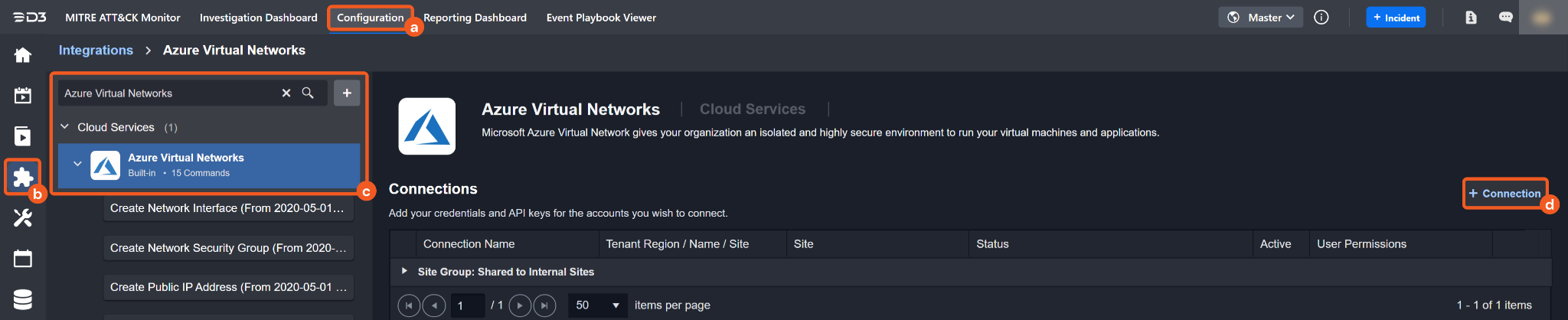
Navigate to Configuration on the top header menu.
Click on the Integration icon on the left sidebar.
Type Azure Virtual Networks in the search box to find the integration, then click it to select it.
Click on the + Connection button on the right side of the Connections section. A new connection window will appear.
Configure the following fields to create a connection to Azure Virtual Networks.
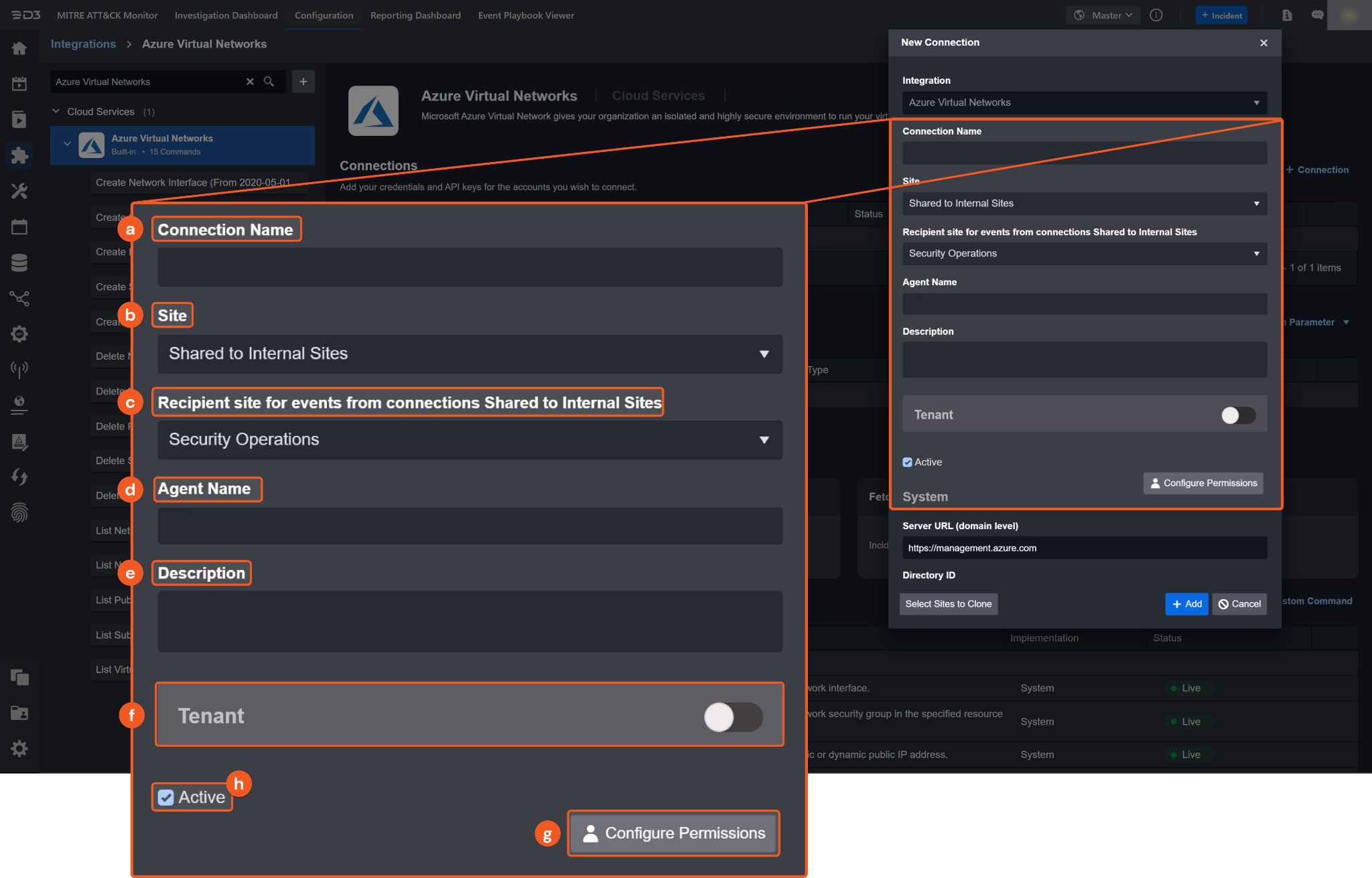
Connection Name: The desired name for the connection.
Site: The site on which to use the integration connection. Use the drop-down menu to select the site. The Share to Internal Sites option enables all internal sites to use the connection. Selecting a specific site will only enable that site to use the connection.
Recipient site for events from connections Shared to Internal Sites: This field is displayed when Share to Internal Sites is selected for the Site field, allowing selection of the internal site for deploying the integration connection.
Agent Name (Optional): The proxy agent required to build the connection. Use the dropdown menu to select the proxy agent from a list of previously configured proxy agents.
Description (Optional): The description for the connection.
Tenant (Optional): When configuring the connection from a master tenant site, users can choose the specific tenant sites with which to share the connection. Once this setting is enabled, users can filter and select the desired tenant sites from the dropdowns to share the connection.

Configure User Permissions: Defines which users have access to the connection.
Active: The checkbox that enables the connection to be used when selected.
System: This section contains the parameters defined specifically for the integration. These parameters must be configured to create the integration connection.
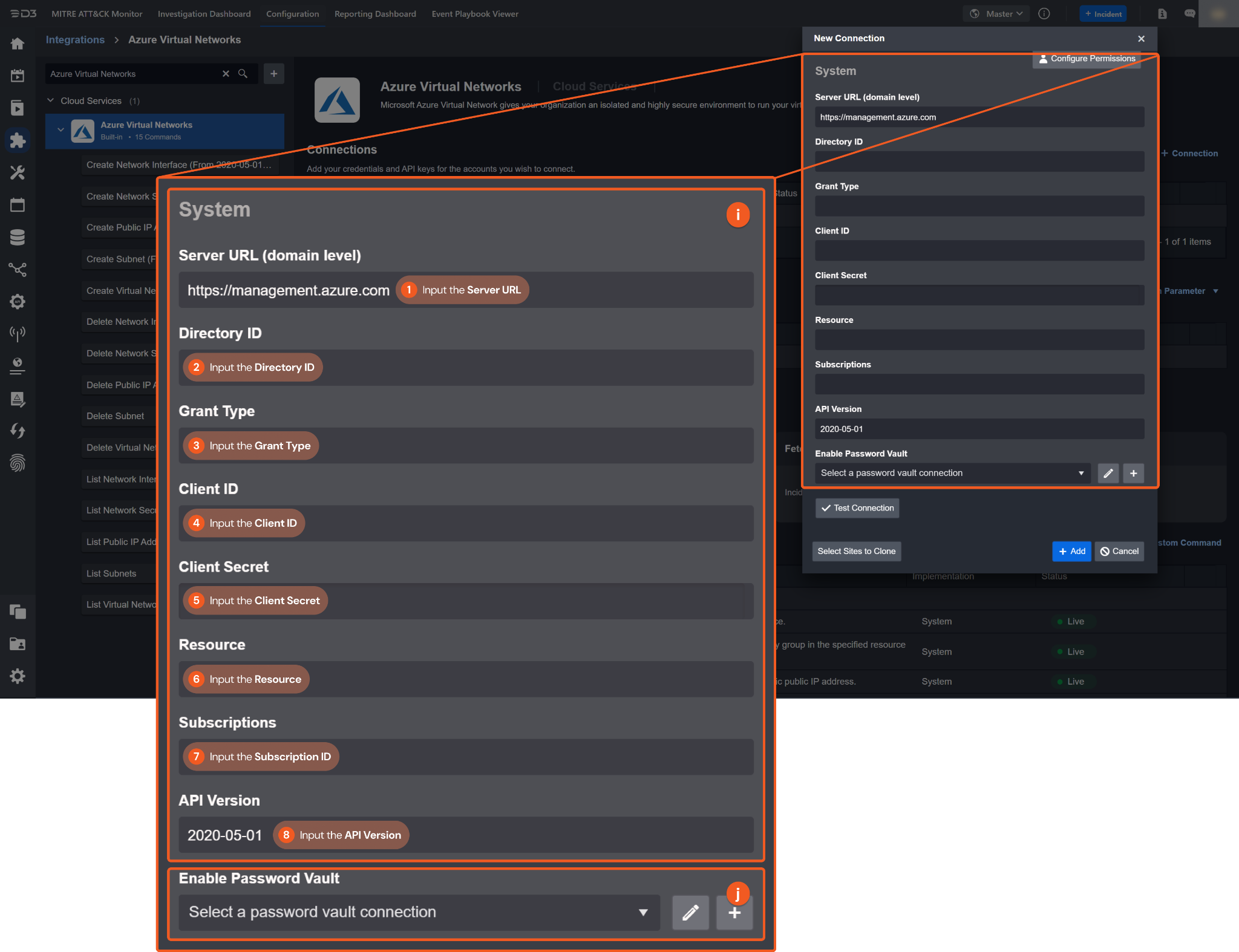
1. Input the Server URL. The default value is https://management.azure.com.
2. Copy the Directory ID from the Azure Virtual Networks platform. Refer to step 4b of Configuring Azure Virtual Networks to Work with D3 SOAR.
3. Input the Grant Type. Enter client_credentials.
4. Copy the Client ID from the Azure Virtual Networks platform. Refer to step 4a of Configuring Azure Virtual Networks to Work with D3 SOAR.
5. Copy the Client Secret from the Azure Virtual Networks platform. Refer to step 5c of Configuring Azure Virtual Networks to Work with D3 SOAR.
6. Input the Resource. Enter the same value as the Server URL.
7. Copy the Subscription ID from the Azure Virtual Networks platform. Refer to step 15b of Configuring Azure Virtual Networks to Work with D3 SOAR.
8. Input the API Version. The default value is 2020-05-01.
Enable Password Vault: An optional feature that allows users to take the stored credentials from their own password vault. Refer to the password vault connection guide if needed.
Test the connection.
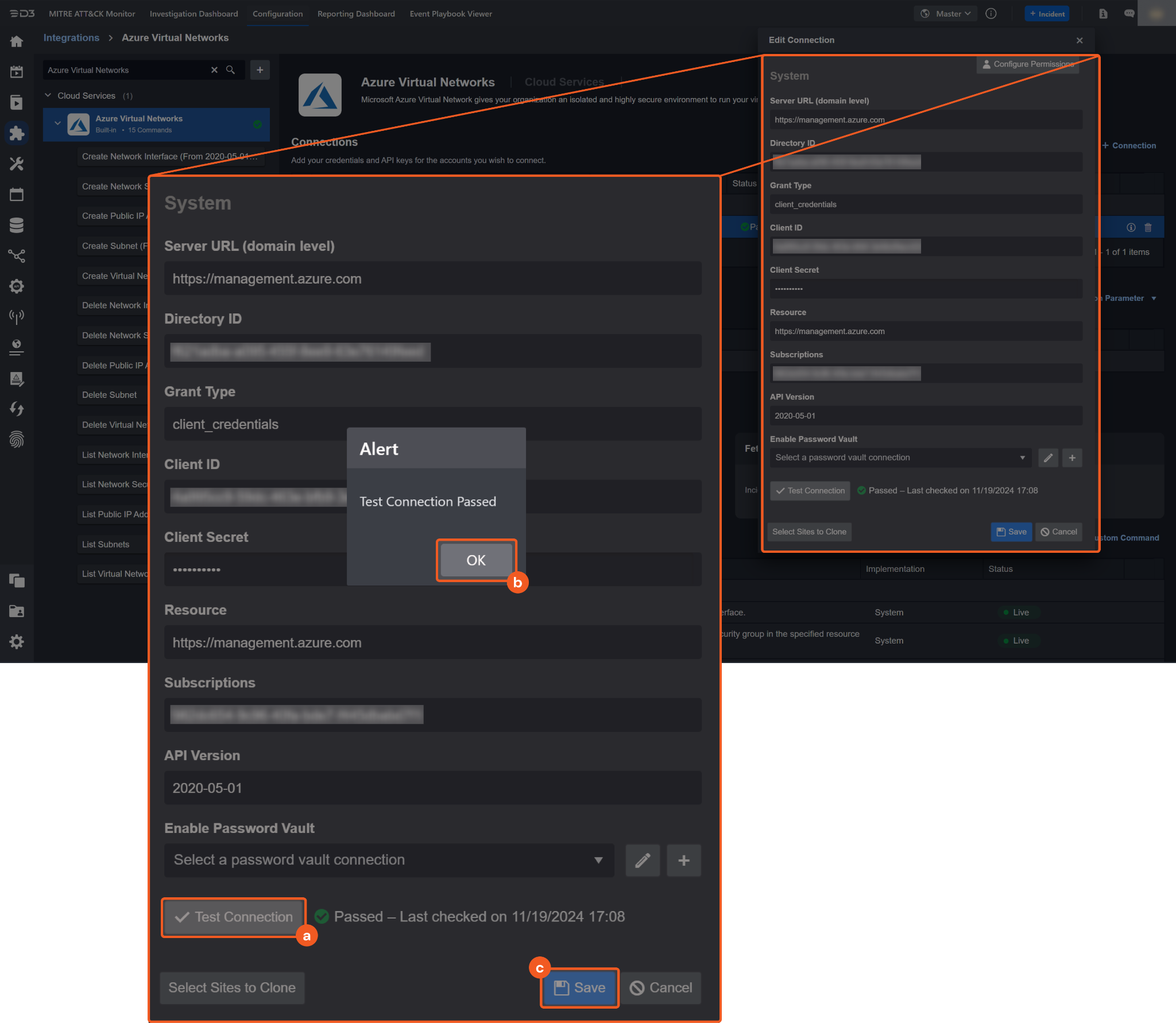
Click on the Test Connection button to verify credentials and connectivity. A success alert displays Passed with a green checkmark. If the connection fails, review the parameters and retry.
Click OK to close the alert window.
Click + Add to create and add the configured connection.
Commands
Azure Virtual Networks includes the following executable commands for users to set up schedules or create playbook workflows. With the Test Command, users can execute these commands independently for playbook troubleshooting.
Integration API Note
For more information about the Azure Virtual Networks API, refer to the Azure Virtual Networks Rest API reference.
READER NOTE
Certain permissions are required for each command. Refer to the Permission Requirements and Configuring Azure Virtual Networks to Work with D3 SOAR sections for details.
Create Network Interface
Creates or updates a network interface.
READER NOTE
Network Interface Name, Public IP Address ID, Subnet ID, and Virtual Network Names are optional parameters to run this command.
Run the List Network Interfaces command to obtain the Network Interface Name. Network Interface Names can be found in the raw data at the path $.value[*].name.
Run the List Public Addresses command to obtain the Public IP Address ID. The Public IP Address ID can refer to the public IP address ID or name. The value of the public IP address ID can be found in the raw data at the path $.value[*].id. The value of the public IP address name can be found in the raw data at the path $.value[*].name.
Run the List Subnets command to obtain the Subnet ID. The Subnet ID can refer to the subnet ID or name. The value of the subnet ID can be found in the raw data at the path $.value[*].id. The value of the subnet name can be found in the raw data at the path $.value[*].name.
Run the List Virtual Networks command to obtain the Virtual Network Name. Virtual Network Names can be found in the raw data at the path $.value[*].name.
Input
Input Parameter | Required/Optional | Description | Example |
Network Interface Name | Required | The name of the network interface. Network Interface Name can be obtained using the List Network Interfaces command. | networkInterfaceTest |
Resource Group Name | Required | The name of the resource group. Resource groups can be found on the Azure portal. Refer to Manage Azure resource groups by using the Azure portal for more information. | d3uat |
Location | Required | The resource location. | westus |
Public IP Address ID | Required | The name or ID of the public IP address. Public IP Address ID or name can be obtained using the List Public IP Addresses command. | publicIpAddress1 |
Subnet ID | Required | The name or ID of the subnet. Subnet ID or name can be obtained using the List Subnets command. | subnetTest |
Virtual Network Name | Optional | The name of the virtual network. Virtual Network Name can be obtained using the List Virtual Networks command. | virtualNetworks33 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Create Network Interface failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Azure Virtual Networks portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Bad request. |
Error Sample Data Create Network Interface failed. Status Code: 400. Message: Bad request. |
Create Network Security Group
Creates or updates a network security group in the specified resource group.
READER NOTE
Network Security Group Name is an optional parameter to run this command.
Run the List Network Security Groups command to obtain the Network Security Group Name. Network Security Group Names can be found in the raw data at the path $.value[*].name.
Input
Input Parameter | Required/Optional | Description | Example |
Network Security Group Name | Required | The name of the network security group. Network Security Group Name can be obtained using the List Network Security Groups command. | networkSecurityGroup1 |
Resource Group Name | Required | The name of the resource group. Resource groups can be found on the Azure portal. Refer to Manage Azure resource groups by using the Azure portal for more information. | d3uat |
Location | Required | The resource location. | westus |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Create Network Security Group failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Azure Virtual Networks portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Bad request. |
Error Sample Data Create Network Security Group failed. Status Code: 400. Message: Bad request. |
Create Public IP Address
Creates or updates a static or dynamic public IP address.
READER NOTE
Public IP Address Name is an optional parameter to run this command.
Run the List Public Addresses command to obtain the Public IP Address Name. Public IP Address Names can be found in the raw data at the path $.value[*].name.
Input
Input Parameter | Required/Optional | Description | Example |
Public IP Address Name | Required | The name of the public IP address. Public IP Address Name can be obtained using the List Public IP Addresses command. | publicIpAddress1 |
Resource Group Name | Required | The name of the resource group. Resource groups can be found on the Azure portal. Refer to Manage Azure resource groups by using the Azure portal for more information. | d3uat |
Location | Required | The resource location. | westus |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Create Public IP Address failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Azure Virtual Networks portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Bad request. |
Error Sample Data Create Public IP Address failed. Status Code: 400. Message: Bad request. |
Create Subnet
Creates or updates a subnet in the specified virtual network.
READER NOTE
Subnet Name and Virtual Network Name are optional parameters to run this command.
Run the List Subnets command to obtain the Subnet Name. Subnet Names can be found in the raw data at the path $.value[*].name.
Run the List Virtual Networks command to obtain the Virtual Network Name. Virtual Network Names can be found in the raw data at the path $.value[*].name.
Input
Input Parameter | Required/Optional | Description | Example |
Subnet Name | Required | The name of the subnet. Subnet Name can be obtained using the List Subnets command. | subnetTest |
Virtual Network Name | Required | The name of the virtual network. Virtual Network Name can be obtained using the List Virtual Networks command. | virtualNetworks33 |
Resource Group Name | Required | The name of the resource group. Resource groups can be found on the Azure portal. Refer to Manage Azure resource groups by using the Azure portal for more information. | d3uat |
Subnet Address Prefix | Required | The address prefix of the subnet. | ***.***.***.***/*** |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Create Subnet failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Azure Virtual Networks portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Bad request. |
Error Sample Data Create Subnet failed. Status Code: 400. Message: Bad request. |
Create Virtual Network
Creates or updates a virtual network in the specified resource group.
READER NOTE
Virtual Network Name is an optional parameter to run this command.
Run the List Virtual Networks command to obtain the Virtual Network Name. Virtual Network Names can be found in the raw data at the path $.value[*].name.
Input
Input Parameter | Required/Optional | Description | Example |
Virtual Network Name | Required | The name of the virtual network. Virtual Network Name can be obtained using the List Virtual Networks command. | virtualNetworks34 |
Resource Group Name | Required | The name of the resource group. Resource groups can be found on the Azure portal. Refer to Manage Azure resource groups by using the Azure portal for more information. | d3uat |
Location | Required | The resource location. | westus |
Address Prefix | Required | The address prefix of the virtual network. | ***.***.***.***/*** |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Create Virtual Network failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Azure Virtual Networks portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Bad request. |
Error Sample Data Create Virtual Network failed. Status Code: 400. Message: Bad request. |
Delete Network Interface
Deletes the specified network interface.
READER NOTE
Network Interface Names is an optional parameter to run this command.
Run the List Network Interfaces command to obtain the Network Interface Names. Network Interface Names can be found in the raw data at the path $.value[*].name.
Input
Input Parameter | Required/Optional | Description | Example |
Resource Group Name | Required | The name of the resource group. Resource groups can be found on the Azure portal. Refer to Manage Azure resource groups by using the Azure portal for more information. | d3uat |
Network Interface Names | Required | The names of the network interfaces to delete. Network Interface Names can be obtained using the List Network Interfaces command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Delete Network Interface failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Azure Virtual Networks portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Bad request. |
Error Sample Data Delete Network Interface failed. Status Code: 400. Message: Bad request. |
Delete Network Security Group
Deletes network security groups in the specified resource group.
READER NOTE
Network Security Group Names is an optional parameter to run this command.
Run the List Network Security Groups command to obtain the Network Security Group Names. Network Security Group Names can be found in the raw data at the path $.value[*].name.
Input
Input Parameter | Required/Optional | Description | Example |
Resource Group Name | Required | The name of the resource group. Resource groups can be found on the Azure portal. Refer to Manage Azure resource groups by using the Azure portal for more information. | d3uat |
Network Security Group Names | Required | The names of the network security groups to delete. Network Security Group Names can be obtained using the List Network Security Groups command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Delete Network Security Group failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Azure Virtual Networks portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Bad request. |
Error Sample Data Delete Network Security Group failed. Status Code: 400. Message: Bad request. |
Delete Public IP Address
Deletes the specified public IP addresses.
READER NOTE
Public IP Address Names is an optional parameter to run this command.
Run the List Public Addresses command to obtain the Public IP Address Names. Public IP Address Names can be found in the raw data at the path $.value[*].name.
Input
Input Parameter | Required/Optional | Description | Example |
Resource Group Name | Required | The name of the resource group. Resource groups can be found on the Azure portal. Refer to Manage Azure resource groups by using the Azure portal for more information. | d3uat |
Public IP Address Names | Required | The names of public IP addresses to delete. Public IP Address Names can be obtained using the List Public IP Addresses command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Delete Public IP Address failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Azure Virtual Networks portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Bad request. |
Error Sample Data Delete Public IP Address failed. Status Code: 400. Message: Bad request. |
Delete Subnet
Deletes subnets in the specified virtual network.
READER NOTE
Virtual Network Name and Subnet Names are optional parameters to run this command.
Run the List Virtual Networks command to obtain the Virtual Network Name. Virtual Network Names can be found in the raw data at the path $.value[*].name.
Run the List Subnets command to obtain the Subnet Names. Subnet Names can be found in the raw data at the path $.value[*].name.
Input
Input Parameter | Required/Optional | Description | Example |
Resource Group Name | Required | The name of the resource group. Resource groups can be found on the Azure portal. Refer to Manage Azure resource groups by using the Azure portal for more information. | d3uat |
Virtual Network Name | Required | The name of the virtual network. Virtual Network Name can be obtained using the List Virtual Networks command. | virtualNetworks375 |
Subnet Names | Required | The names of the subnets to delete. Subnet Names can be obtained using the List Subnets command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Delete Subnet failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Azure Virtual Networks portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Bad request. |
Error Sample Data Delete Subnet failed. Status Code: 400. Message: Bad request. |
Delete Virtual Network
Deletes virtual networks in the specified resource group.
READER NOTE
Virtual Network Names is an optional parameter to run this command.
Run the List Virtual Networks command to obtain the Virtual Network Names. Virtual Network Names can be found in the raw data at the path $.value[*].name.
Input
Input Parameter | Required/Optional | Description | Example |
Resource Group Name | Required | The name of the resource group. Resource groups can be found on the Azure portal. Refer to Manage Azure resource groups by using the Azure portal for more information. | d3uat |
Virtual Network Names | Required | The names of the virtual networks to delete. Virtual Network Names can be obtained using the List Virtual Networks command. |
JSON
|
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Partially Successful or Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Delete Virtual Network failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Azure Virtual Networks portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Bad request. |
Error Sample Data Delete Virtual Network failed. Status Code: 400. Message: Bad request. |
List Network Interfaces
Lists network interfaces.
Input
Input Parameter | Required/Optional | Description | Example |
Resource Group Name | Required | The name of the resource group. Resource groups can be found on the Azure portal. Refer to Manage Azure resource groups by using the Azure portal for more information. | d3uat |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Network Interfaces failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Azure Virtual Networks portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Bad request. |
Error Sample Data List Network Interfaces failed. Status Code: 400. Message: Bad request. |
List Network Security Groups
Lists network security groups.
Input
Input Parameter | Required/Optional | Description | Example |
Resource Group Name | Required | The name of the resource group. Resource groups can be found on the Azure portal. Refer to Manage Azure resource groups by using the Azure portal for more information. | d3uat |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Network Security Groups failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Azure Virtual Networks portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Bad request. |
Error Sample Data List Network Security Groups failed. Status Code: 400. Message: Bad request. |
List Public IP Addresses
Lists public IP addresses.
Input
Input Parameter | Required/Optional | Description | Example |
Resource Group Name | Required | The name of the resource group. Resource groups can be found on the Azure portal. Refer to Manage Azure resource groups by using the Azure portal for more information. | d3uat |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Public IP Addresses failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Azure Virtual Networks portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Bad request. |
Error Sample Data List Public IP Addresses failed. Status Code: 400. Message: Bad request. |
List Subnets
Lists subnets.
READER NOTE
Virtual Network Name is an optional parameter to run this command.
Run the List Virtual Networks command to obtain the Virtual Network Name. Virtual Network Names can be found in the raw data at the path $.value[*].name.
Input
Input Parameter | Required/Optional | Description | Example |
Resource Group Name | Required | The name of the resource group. Resource groups can be found on the Azure portal. Refer to Manage Azure resource groups by using the Azure portal for more information. | d3uat |
Virtual Network Name | Required | The name of the virtual network. Virtual Network Name can be obtained using the List Virtual Networks command. | virtualNetworks33 |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Subnets failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Azure Virtual Networks portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Bad request. |
Error Sample Data List Subnets failed. Status Code: 400. Message: Bad request. |
List Virtual Networks
Lists virtual networks.
Input
Input Parameter | Required/Optional | Description | Example |
Resource Group Name | Required | The name of the resource group. Resource groups can be found on the Azure portal. Refer to Manage Azure resource groups by using the Azure portal for more information. | d3uat |
Output
To view the sample output data for all commands, refer to this article.
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | List Virtual Networks failed. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Azure Virtual Networks portal. Refer to the HTTP Status Code Registry for details. | Status Code: 400. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Bad request. |
Error Sample Data List Virtual Networks failed. Status Code: 400. Message: Bad request. |
Test Connection
Allows you to perform a health check on an integration connection. You can schedule a periodic health check by selecting Connection Health Check when editing an integration connection.
Input
N/A
Output
Output Type | Description | Return Data Type |
Return Data | Indicates one of the possible command execution states: Successful or Failed. The Failed state can be triggered by any of the following errors:
More details about an error can be viewed in the Error tab. | String |
Error Handling
If the Return Data displays Failed, an Error tab will appear in the Test Result window.
The error tab contains the details responded from D3 SOAR or third-party API calls, including Failure Indicator, Status Code, and Message. This can help locate the root cause of a command failure.
Parts in Error | Description | Example |
Failure Indicator | Indicates the command failure that happened at a specific input and/or API call. | Test Connection failed. Failed to check the connector. |
Status Code | The response code issued by the third-party API server or the D3 SOAR system that can be used to locate the corresponding error category. For example, if the returned status code is 401, the selected connection is unauthorized to run the command. The user or system support would need to check the permission setting in the Azure Virtual Networks portal. Refer to the HTTP Status Code Registry for details. | Status Code: 403. |
Message | The raw data or captured key error message from the integration API server about the API request failure. | Message: Unauthorized. |
Error Sample Data Test Connection failed. Failed to check the connector. Status Code: 403. Message: Unauthorized. |