Investigation Playbooks
LAST UPDATED: MAR 21, 2025
Investigation playbooks automate incident responses and standardize workflows to meet the unique needs of organizations. On the landing page of the Investigation Playbooks module, users can search for existing playbooks or create new ones.
-20250121-230116.png?inst-v=bfb1ec42-c45a-425e-9e97-43428b3365fd)
Life Cycle
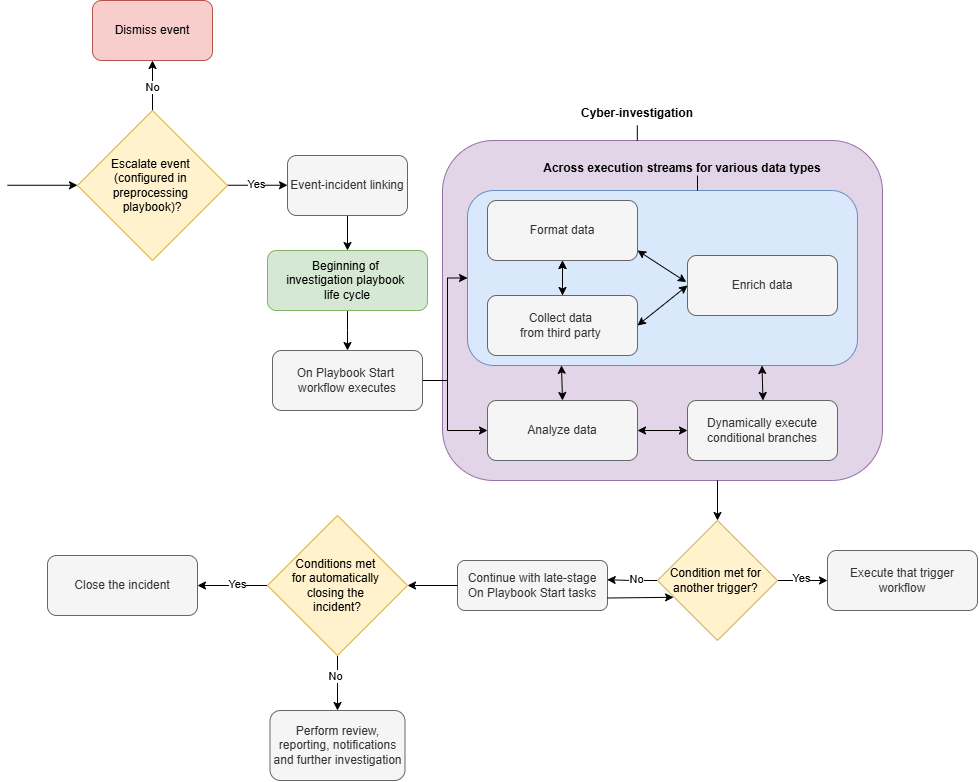
The investigation playbook life cycle begins when an event is escalated and linked to an incident. The playbook conducts cybersecurity investigations through tasks, dynamically running response workflows and attempting resolution.
Investigation Playbook Types
Built-in Investigation Playbooks
Built-in investigation playbooks are preconfigured by D3 to address common cybersecurity threats, enabling quick deployment and serving as templates for customization.
EXAMPLE
-20250121-210424.png?inst-v=bfb1ec42-c45a-425e-9e97-43428b3365fd)
A section of the Phishing playbook.
Custom Investigation Playbooks
Custom investigation playbooks are user-defined workflows used to address unique operational needs.
READER NOTE
See My First Playbook to create your first playbook.
D3 engineers assist in designing playbooks tailored to unique business requirements. Contact us today.
[February 2025] New AI-assisted playbook builder is under development! Stay tuned.
%201-20250121-003122.png?inst-v=bfb1ec42-c45a-425e-9e97-43428b3365fd)
%201-20250121-003425.png?inst-v=bfb1ec42-c45a-425e-9e97-43428b3365fd)
%201-20250121-004402.png?inst-v=bfb1ec42-c45a-425e-9e97-43428b3365fd)
%201-20250121-004617.png?inst-v=bfb1ec42-c45a-425e-9e97-43428b3365fd)
-20250121-011702.png?inst-v=bfb1ec42-c45a-425e-9e97-43428b3365fd)
-20250121-011718.png?inst-v=bfb1ec42-c45a-425e-9e97-43428b3365fd)
-20250121-011732.png?inst-v=bfb1ec42-c45a-425e-9e97-43428b3365fd)
%201%20(1)-20250121-011219.png?inst-v=bfb1ec42-c45a-425e-9e97-43428b3365fd)
%201%20(1)-20250121-011246.png?inst-v=bfb1ec42-c45a-425e-9e97-43428b3365fd)
-20250121-011844.png?inst-v=bfb1ec42-c45a-425e-9e97-43428b3365fd)
-20250121-011803.png?inst-v=bfb1ec42-c45a-425e-9e97-43428b3365fd)
-20250121-021018.png?inst-v=bfb1ec42-c45a-425e-9e97-43428b3365fd)
-20250121-021818.png?inst-v=bfb1ec42-c45a-425e-9e97-43428b3365fd)
-20250121-012254.png?inst-v=bfb1ec42-c45a-425e-9e97-43428b3365fd)