Setting Up SAML 2.0 Single Sign-On (SSO)
Software Requirements
Ensure your D3 SOAR version is 14.0.385 or higher.
Prerequisites
For the SAML service, you'll need:
Assertion Consumer Service URL (Reply URL): This is the SP's (Service Provider) endpoint URL where the IdP (Identity Provider) will send the SAML response after successful authentication. Typically, this is specific to your D3 VSOC/Admin login URL. For example,
https://***.com/VSOC/login.aspx.Entity ID: This unique identifier helps the IdP identify the SP. Generally, this is set to the Assertion Consumer Service URL.
For the D3 application, you'll need:
SAML Single Sign-On URL: This is the IdP's URL where the authentication requests and SAML responses are exchanged.
SAML Certificate: A SAML certificate in base64 format.
Configuring the D3 Application
When you complete the following configuration, here's how the system will behave:
Users attempting to access the D3 application via the URL https://***.com/VSOC will need to input their D3 usernames. Direct access to the D3 application through https://***.com/VSOC/login.aspx is not permitted.
Click 'Next', then proceed to the SAML single sign-on page. Afterward, input the email-password pair to proceed with the login.
After the user is authenticated by the IdP and the SAML response is verified by the D3 application, they will gain access to the D3 application.
Users are restricted from directly accessing the D3 Admin application and should instead navigate through the Advanced Settings within the VSOC application.
If a user remains idle in the D3 application, they will be prompted after 115 minutes. If they fail to respond within 5 minutes, they will be automatically signed out and redirected to the D3 sign-out page. They can return to the application by clicking the "Return to Sign in" button.
To enable complete sign-out for the client, set the
LogoutSamlWithVSOCkey totruein theappSettingsfor both VSOC and Admin applications. Also, set theSAMLLogOutUrlto the client's SAML sign-out URL. Following these settings, users will be redirected to the specified URL instead of the D3 sign-out page after being signed out.
Steps to Configure
Step 1 - Configure VSOC App Settings
Open Web.Config for the VSOC app and modify the authentication options and appSettings as shown.
Modify authentication options:
<authentication mode="Forms">
<forms loginUrl="D3Saml.aspx?reset=true" name="AuthCookie" timeout="140"
path="/" requireSSL="false">
</forms>
</authentication><add key="InactivityExpiry" value="120" />
<add key="TimeBeforeWarning" value="5" />
<add key="enableSAMLLogin" value="true" />
<add key="SAMLLogin" value="Login.aspx" />
<add key="SAMLExchangBaseUrl" value="" />
<add key="SAMLExchangeTargetUrl" value="login.aspx" />
<add key="SAMLLogOutUrl"
value="https://login.microsoftonline.com/common/wsfederation?wa=wsignout1.0" />
<add key="logoutSamlWithVSOC" value="false" />
<add key="SAML2.0" value="true" />
<add key="SAML2.0LogFolder" value="Log\SAML" />
<add key="SAML2.0Conigfile" value="SAML20\SAML.xml" />Then, modify the
appSettingsto confirm thesessionStateoptions.
<sessionState mode="InProc" cookieless="false" timeout="300" />Reader Note
Set the value of
forms.timeouttoappSettings.InactivityExpiry+ 20.Ensure that the value of
appSettings.SAMLExchangBaseUrlis set to an empty string.Only set
appSettings.logoutSamlWithVSOCto true if the client has provided a value forappSettings.SAMLLogOutUrl.
Step 2 - Configure Admin App Settings
Open Web.Config for the Admin app and modify the authentication options and appSettings as shown.
Modify the authentication options:
<authentication mode="Forms">
<forms name="MYWEBAPP.ASPXAUTH" loginUrl="login.aspx?RE=true"
timeout="140" path="/" requireSSL="false">
</forms>
</authentication>Modify
appSettings:
<add key="Session.TimeOut" value="130" />
<add key="enableSAMLLogin" value="true" />
<add key="SAMLLogin" value="Login.aspx" />
<add key="SAMLExchangBaseUrl" value="" />
<add key="SAMLExchangeTargetUrl" value="login.aspx" />
<add key="SAMLLogOutUrl"
value="https://login.microsoftonline.com/common/wsfederation?wa=wsignout1.0" />
<add key="logoutSamlWithVSOC" value="false" />
<add key="SAML2.0" value="true" />
<add key="SAML2.0LogFolder" value="Log\SAML" />
<add key="SAML2.0Conigfile" value="SAML20\SAML.xml" />Then, confirm the
sessionStateoptions.
<sessionState mode="InProc" cookieless="false" timeout="300" />Reader Note
Set the value of
appSettings.Session.TimeouttoVSOC.appSettings.InactivityExpiry+ 10Ensure that the value of
appSettings.SAMLExchangBaseUrlis set to an empty string.Set the value of
forms.timouttoVSOC.appSettings.InactivityExpiry+ 20.
Step 3 - Configure Application Pool
Verify the application pool settings and ensure VSOC and Admin applications use the same application pool.
Confirm the application pool settings:
(General)
Enable 32-Bit Applications: False
Process Model:
Idle Time-out (minutes): 140
Recycling:
Generate Recycle Event Log Entry:
Application Pool Configuration Changes: True
Isapi Reported Unhealthy: True
Manual Recycle: True
Private Memory Limit Exceeded: True
Regular Time Interval: True
Request Limit Exceeded: True
Specific Time: True
Virtual Memory Limit Exceeded: True
Regular Time Interval (minutes): 0
Specific Times: (None)Configure VSOC and Admin applications to use the same application pool.
Reader Note
Set the value of Idle Time-out to VSOC.appSettings.InactivityExpiry + 20
Step 4 - Configure SAML 2.0
You will need to adjust the configuration file, located at: <VSOC or Admin app path>\SAML20\SAML.xml.
| The Assertion Consumer Service URL provided by the Service Provider (SP) where the Identity Provider (IdP) sends the SAML assertions after successful authentication. Must be set to D3 VSOC/Admin login URL. |
| SAML single sign-on URL. The IdP URL where the authentication requests and SAML responses are exchanged. |
| SAML certificate in base64 format. |
| If the user name used to authenticate with the IdP is in email format but the user name in D3 is not in email format, set the value for EmailIDType to true. |
| Set to true if the SAML response is compressed by the IdP. |
Below is a sample SAML.xml for reference:
<?xml version="1.0" encoding="utf-8" ?>
<root>
<key name="assertionConsumerServiceUrl">
<value>https://xxx.com/VSOC/Login.aspx</value>
</key>
<key name="issuer"><value>D3_VSOC</value></key>
<key name="SignatureVerifyAll"><value>true</value></key>
<key name="ReadSamlResponse"><value>false</value></key>
<key name="IncludeSAMLRequest"><value>false</value></key>
<key name="Decompress"><value>false</value></key>
<key name="UrlDecode"><value>false</value></key>
<key name="CompressMod"><value>2</value></key>
<key name="WriteLog"><value>true</value></key>
<key name="EmailIDType"><value>false</value></key>
<key name="AssertionMustHaveSignature"><value>true</value></key>
<key name="showResponseErrorMessage"><value>true</value></key>
<key name="target_url">
<value>https://launcher.myapps.microsoft.com/api/signin/xxx?tenantId=xxx</value>
</key>
<key name="Cert"><value>-----BEGIN CERTIFICATE-----
YIIC8DCCAdigAwIBAgIQUOGJN89ghLhHw1jGrlIUxjANBgkqhkiG9w0BAQsFADA0MTIwMAYDVQQD
EylNaWNyb3NvZnQgQXp1cmUgRmVkZXJhdGVkIFNTTyBDZXJ0aWZpY2F0ZTAeFw0yMzA2MTkyMDI5
NDBaFw0yNjA2MTkyMDI4MzdaMDQxMjAwBgNVBAMTKU1pY3Jvc29mdCBBenVyZSBGZWRlcmF0ZWQg
U1NPIENlcnRpZmljYXRlMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA36pTH0TzUJDv
o5Lz0Wlj00r96ObMbhCt3S1aTJHiOdvV9M9jUEmP2V20ufZ5tQUbUPugAAhcIzBsZaEHpzb/fuAw
Uz5X9YZYGOVLk6NN0peyHIrJSOyvCUAYsh4seaY8oAa3056ckRi4OuioFOddKBkzeIVzTr62tIVC
5uybzkS30EMo1U2A6IYMANgL5aZtNLsyaGyepXsAOs286WIz9DTHWEH9EoEKVmyTYtYCmT+D4L9g
g0ntUMkE2H7s8CnZtllusib3fQsTQnLqN4a1AYCPxPuFEPqXAcBv52YKeCeuUTtTxPOTAiB0Mz9p
v0MylAtrTsmfkhrJkKPv9oISHQIDAQABMA0GCSqGSIb3DQEBCwUAA4IBAQANZ2gIQa7SroxXw0A6
uB3TwYyG94PjnX4EecjIzX6cU4RJjqFyG+Ch0DekQSgVC3uziAk9egDVftRUU1fKfi/PSUETeC1B
yD9JM1u0/MPsNibKpNfedsrHDdFfThOuvV4LrhmRLLHN1aV0DgvS8qbi/RgFnx0qdSAOCouYc/40
rw/poAYNlmiVW/nFlFIsHRTeyEFF1kjA0B1CFKR/r1fTUsRQs+OqUILxwMn6MG+hdBwWCFbninw/
bxlnIyPgzeIxZmiMvgbJKaCfVTXOZL62OWV0byVJZ98p7OUGsMCykipAk1uisfZoCY2nQYtxDEA4
7sCF1ospSxGRsjTQ9Mwz
-----END CERTIFICATE-----</value>
</key>
<key name="SamlResponse"><value></value></key>
</root>Appendix
SAML 2.0 Protocol for Azure AD
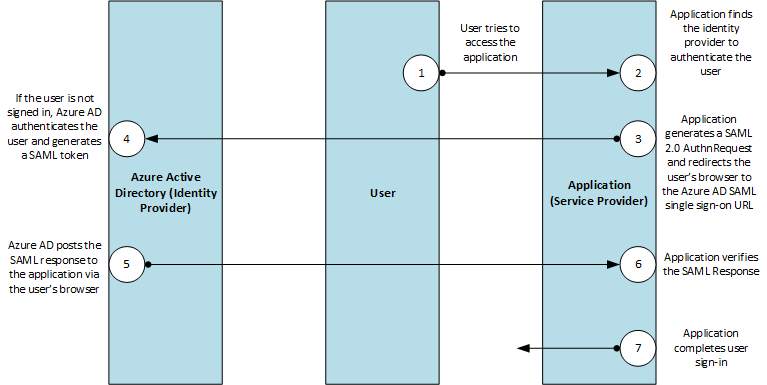
.png)