16.4.57
Application Settings Enhancement
More Logo Customization Options
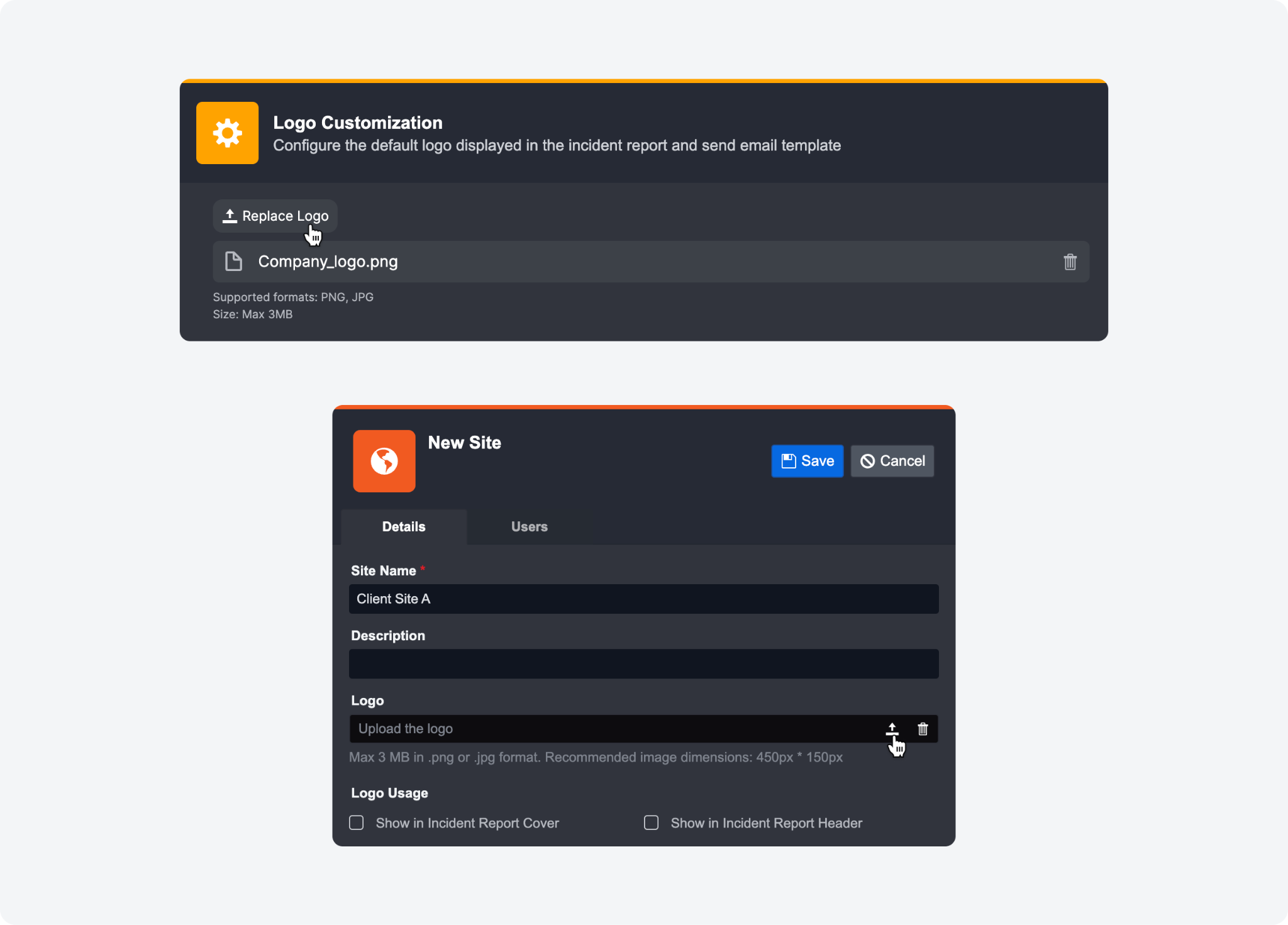
With this new release, you can now personalize and reinforce your brand's presence across various elements of the application. Here's what's new:
Application-Wide Logo Display: Solidify your brand identity within D3 SOAR with a system-wide logo, prominently placed at the top-left corner of every page. To set this up, go to Configuration > Application Settings > Logo Customization.
Site-Specific Logos for MSSPs: Tailoring to the unique needs of Managed Service Security Providers (MSSPs), our update enables the display of distinct logos for each client managed by MSSPs. This customization extends across all client-specific interfaces and incident report templates, maintaining a cohesive brand image for each client's site. This can be configured at Configuration > Organization Management > Sites.
Incident Workspace Enhancements
Updated UI Design
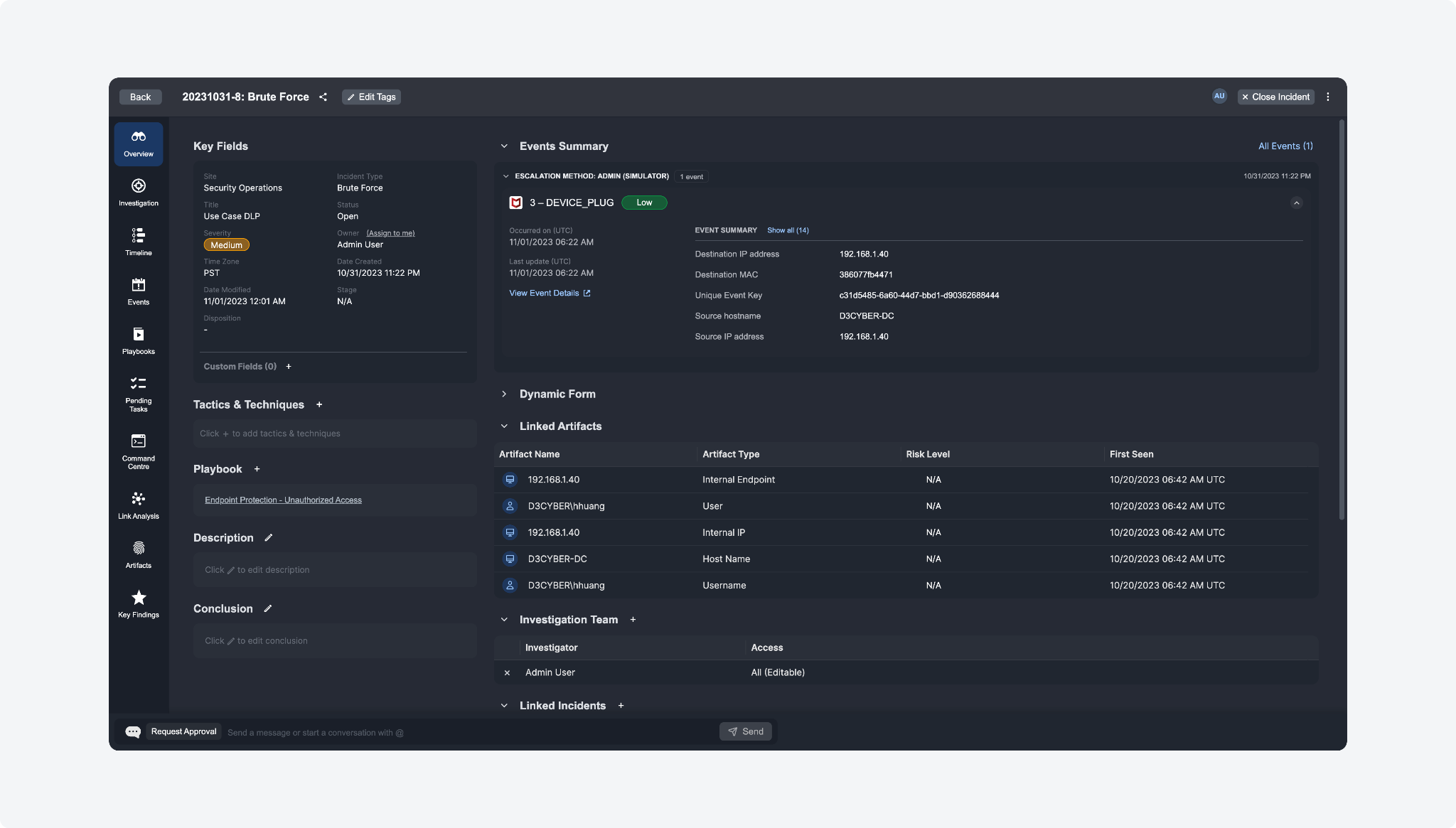
We've refined the user interface of the Incident Workspace to deliver a sleeker, more uniform experience.
Incident Overview: Linked Artifacts
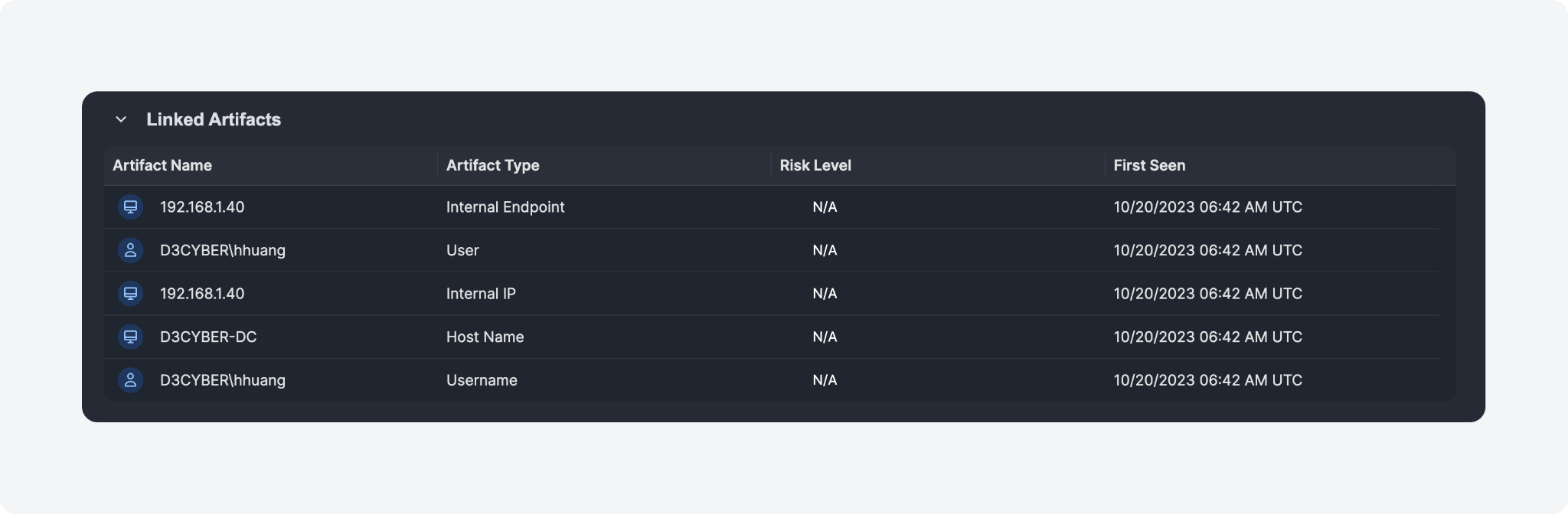
We've introduced a new Linked Artifacts section in the Incident Overview tab for immediate visibility of all artifacts connected to the incident.
Incident Overview: Tabbed Dynamic Form Layout
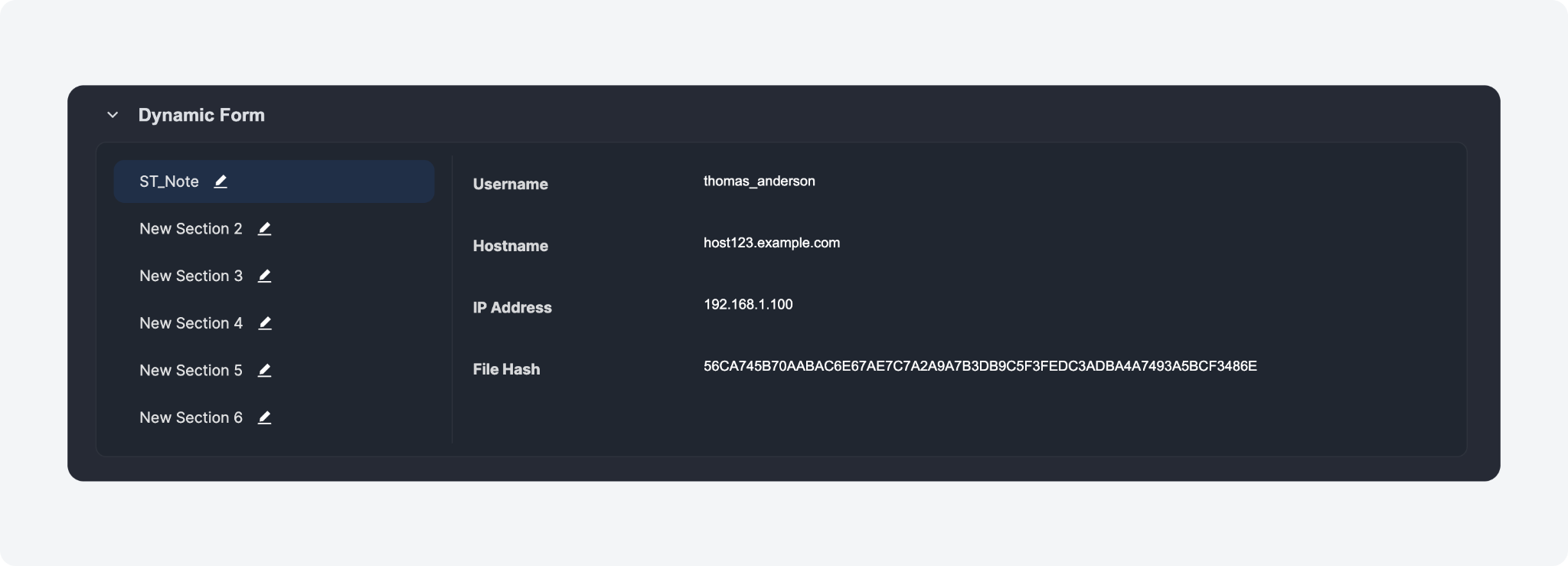
Dynamic forms within the Incident Overview tab are now efficiently organized into tabs within the Dynamic Form section. This consolidation provides a more orderly representation of incident-related forms, eliminating the need for separate sections for each form.
Playbook Enhancements
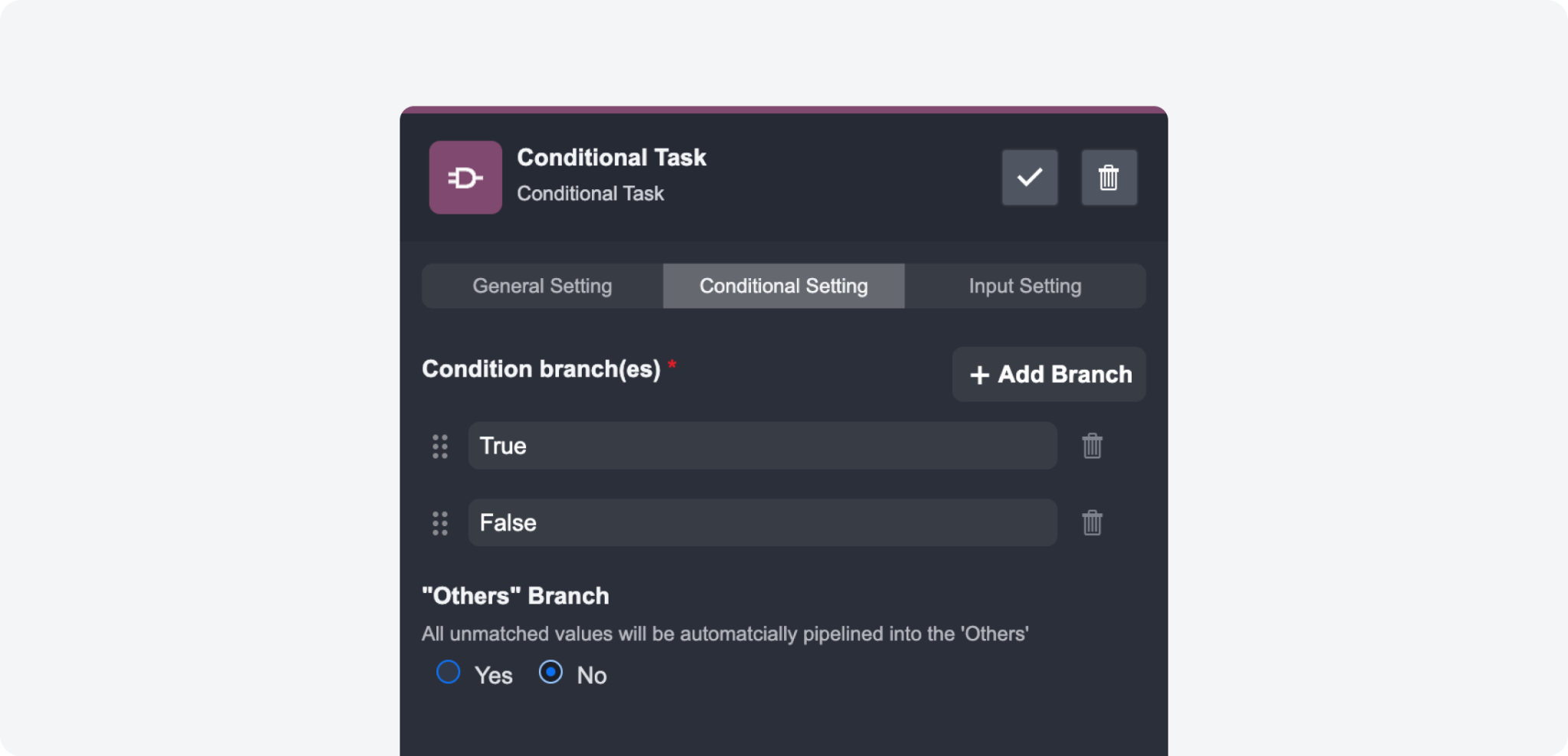
Conditional Task: Updated Configuration UI
The conditional task settings have been restructured with a tabbed interface for an intuitive arrangement of configuration options. This update simplifies navigation and improves the user experience by logically grouping related settings.
Incident Playbooks: On Playbook Task Error Trigger
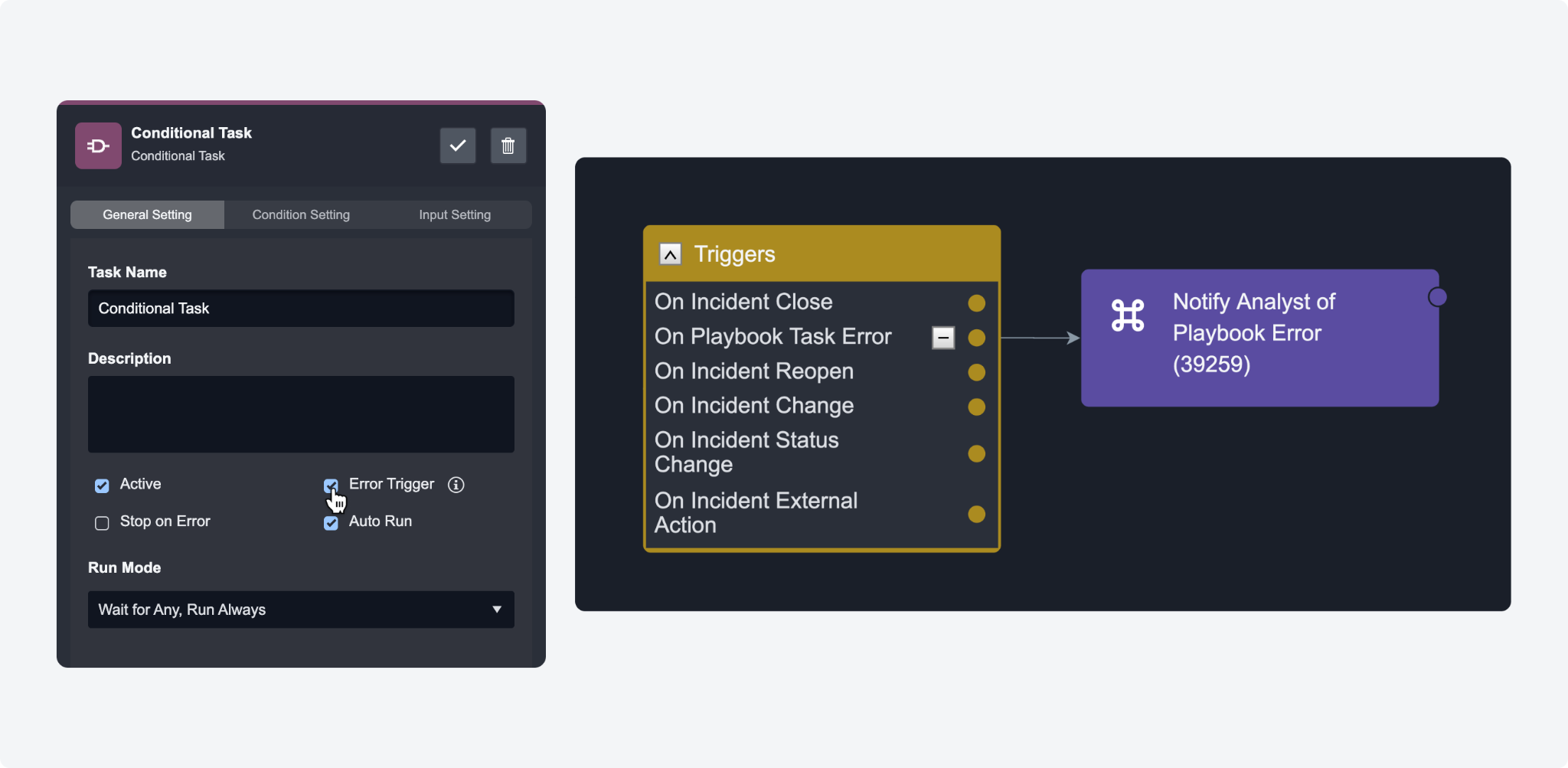
We've introduced the On Playbook Task Error trigger to enhance error management within incident playbooks. This feature, active by default for command, data formatter, conditional, and REST API tasks, triggers a follow-up workflow when an error occurs, such as sending an email alert to an analyst. It's designed for quick response and can be disabled as needed.
To prevent potential infinite error loops, workflows initiated by this trigger will not reactivate the trigger if they fail. When the follow-up workflow is activated, you can access the task's name and error message in the returned playbook data located at the paths $.Trigger.taskName and $.Trigger.taskErrorMessage, respectively.
Data Ingestion Enhancement
Event and Incident Creation Count Indicator
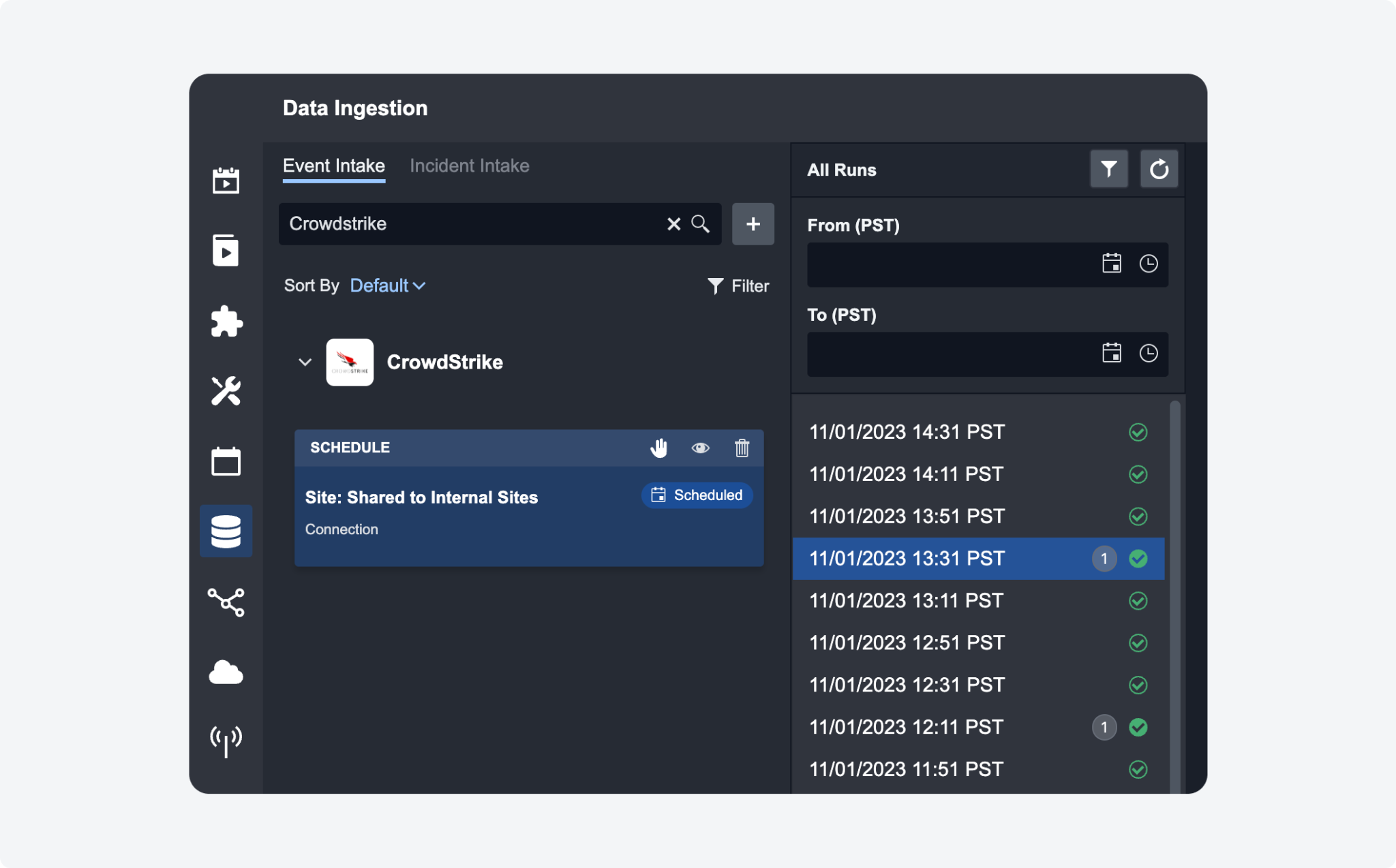
An event and incident creation count indicator has been added to event and incident intake logs. This feature systematically tallies the outcomes of each ingestion job. Accessing the event intake logs now provides a count of newly created events, while the incident intake logs display the total number of incidents generated.
Utility Commands

The following utility commands have been added to this release of D3 SOAR.
Commands | Functionality |
Clone and Schedule Data Ingestions | Clone a new schedule from the current schedule connection to a new schedule connection within the integration. If the current schedule connection is empty, then create a new schedule in the new schedule connection within the integration. |
Share Global Lists across Sites | Shares global lists across sites. |
Publish Playbooks across Sites | Publishes live playbooks across sites. |
Integrations

Updated Integrations
The following integrations have been updated in this release of D3 SOAR.
Integration Name | Changes |
iZOOLogic | New commands: Get Case Details, Get DLR Incident Details, Get WSS Scanning Details, Get WSS Scanning Vulnerability Details, List Authorised Executives, List Whitelisted Executives Fetch Event: Added new options for the Event Type parameter: Incident, Data Loss Recovery, Brand Abuse Monitoring, Executive Monitoring, Social Media Monitoring, Domain Names Monitoring, Mobile App Monitoring, Case Message New event sources: DLR Incident, Domain Monitoring, Brand Abuse Monitoring, Executive Monitoring, Mobile App Monitoring, Social Media Monitoring, Case Messages Added default field mappings for all event sources |
Microsoft 365 Defender | New commands: Create Alert Comment, Fetch Event, Get Alerts, Get Incident Alerts, Update Alerts |
Palo Alto Networks Firewall V10 | New commands: Block IPs By Adding To AddressGroup |
Stellar Cyber | New commands: Fetch Incident, Update Incidents The Search Events command has been renamed to Search Incidents with an updated description. |